+
+jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.
-```
+
Path to vulnerable library: /app/src/main/webapp/resources/js/jquery-1.11.2.min.js
+
-```
-Release Version: v2.1.0-beta-11-g1f6e12cc5
-Git Commit Hash: 1f6e12cc55e534bf514eef212f1091a91b8592c9
-Git Branch: HEAD
-UTC Build Time: 2018-07-04 06:31:26
-GoVersion: go version go1.10.1 linux/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-```
-",1,panic when multiply very big decimal with a very small decimal what did you do select what did you expect to see what did you see instead error mysql server has gone away no connection trying to reconnect conn go lastcmd select runtime error index out of range goroutine github com pingcap tidb server clientconn run home robi code go src github com pingcap tidb server conn go panic home robi src runtime panic go github com pingcap tidb types decimalmul home robi code go src github com pingcap tidb types mydecimal go github com pingcap tidb expression builtinarithmeticmultiplydecimalsig evaldecimal home robi code go src github com pingcap tidb expression builtin arithmetic go github com pingcap tidb expression scalarfunction evaldecimal home robi code go src github com pingcap tidb expression scalar function go github com pingcap tidb expression scalarfunction eval home robi code go src github com pingcap tidb expression scalar function go github com pingcap tidb expression foldconstant home robi code go src github com pingcap tidb expression constant fold go github com pingcap tidb expression foldconstant home robi code go src github com pingcap tidb expression constant fold go github com pingcap tidb expression newfunction home robi code go src github com pingcap tidb expression scalar function go github com pingcap tidb plan expressionrewriter binaryoptoexpression home robi code go src github com pingcap tidb plan expression rewriter go github com pingcap tidb plan expressionrewriter leave home robi code go src github com pingcap tidb plan expression rewriter go github com pingcap tidb ast binaryoperationexpr accept home robi code go src github com pingcap tidb ast expressions go github com pingcap tidb plan planbuilder rewritewithpreprocess home robi code go src github com pingcap tidb plan expression rewriter go github com pingcap tidb plan planbuilder rewrite home robi code go src github com pingcap tidb plan expression rewriter go github com pingcap tidb plan planbuilder buildprojection home robi code go src github com pingcap tidb plan logical plan builder go github com pingcap tidb plan planbuilder buildselect home robi code go src github com pingcap tidb plan logical plan builder go github com pingcap tidb plan planbuilder build home robi code go src github com pingcap tidb plan planbuilder go github com pingcap tidb plan optimize home robi code go src github com pingcap tidb plan optimizer go github com pingcap tidb executor compiler compile home robi code go src github com pingcap tidb executor compiler go github com pingcap tidb session session execute home robi code go src github com pingcap tidb session session go what version of tidb are you using tidb server v or run select tidb version on tidb release version beta git commit hash git branch head utc build time goversion go version linux race enabled false tikv min version alpha ,1
-272008,8494701283.0,IssuesEvent,2018-10-29 00:00:03,containous/traefik,https://api.github.com/repos/containous/traefik,closed,Access log records the wrong frontend name,contributor/waiting-for-feedback kind/bug/possible priority/P2,"### Do you want to request a *feature* or report a *bug*?
+Dependency Hierarchy:
+ - :x: **jquery-1.11.2.min.js** (Vulnerable Library)
+
+
+jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.
-Bug
+
+For more information on CVSS3 Scores, click here.
+
+
+
+ Suggested Fix
+
-1. Using the consul config provider, create several frontends (with different Host rules) and point them to the same backend.
-2. Turn on the `accessLog` feature.
-3. Make a HTTP request to one of the frontend domains.
+
-### What did you expect to see?
+
+
+
-The log message includes the name of the frontend matching the domain of the HTTP request.
+",0,cve medium detected in jquery min js cve medium severity vulnerability vulnerable library jquery min js javascript library for dom operations library home page a href path to vulnerable library app src main webapp resources js jquery min js dependency hierarchy x jquery min js vulnerable library found in head commit a href found in base branch main vulnerability details jquery before as used in drupal backdrop cms and other products mishandles jquery extend true because of object prototype pollution if an unsanitized source object contained an enumerable proto property it could extend the native object prototype publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution isopenpronvulnerability true ispackagebased true isdefaultbranch true packages istransitivedependency false dependencytree jquery isminimumfixversionavailable true minimumfixversion basebranches vulnerabilityidentifier cve vulnerabilitydetails jquery before as used in drupal backdrop cms and other products mishandles jquery extend true because of object prototype pollution if an unsanitized source object contained an enumerable proto property it could extend the native object prototype vulnerabilityurl ,0
+200289,22750029949.0,IssuesEvent,2022-07-07 12:26:24,mixcore/mix.core,https://api.github.com/repos/mixcore/mix.core,closed,(CS-A1008) Audit required: Insecurely generated random number,security vulnerability,"## Description
+`Random` is a pseudo-random number generator, which is an algorithm that produces a sequence of numbers that meet certain statistical requirements for randomness. Because the number generated is not random enough for sensitive operations, consider using `RandomNumberGenerator` from `System.Security.Cryptography` namespace instead.
+
+## Occurrences
+There are 4 occurrences of this issue in the repository.
+
+See all occurrences on DeepSource → [deepsource.io/gh/mixcore/mix.core/issue/CS-A1008/occurrences/](https://deepsource.io/gh/mixcore/mix.core/issue/CS-A1008/occurrences/)
+",True,"(CS-A1008) Audit required: Insecurely generated random number - ## Description
+`Random` is a pseudo-random number generator, which is an algorithm that produces a sequence of numbers that meet certain statistical requirements for randomness. Because the number generated is not random enough for sensitive operations, consider using `RandomNumberGenerator` from `System.Security.Cryptography` namespace instead.
+
+## Occurrences
+There are 4 occurrences of this issue in the repository.
+
+See all occurrences on DeepSource → [deepsource.io/gh/mixcore/mix.core/issue/CS-A1008/occurrences/](https://deepsource.io/gh/mixcore/mix.core/issue/CS-A1008/occurrences/)
+",0, cs audit required insecurely generated random number description random is a pseudo random number generator which is an algorithm that produces a sequence of numbers that meet certain statistical requirements for randomness because the number generated is not random enough for sensitive operations consider using randomnumbergenerator from system security cryptography namespace instead occurrences there are occurrences of this issue in the repository see all occurrences on deepsource rarr ,0
+75395,7470580859.0,IssuesEvent,2018-04-03 05:55:43,zalando/zalenium,https://api.github.com/repos/zalando/zalenium,closed,Can't choose chrome's language ,waiting-retest,"**Please make sure that you provide enough information for us to help you with this issue. Thank you!**
+
+
+
+Zalenium Image Version(s):
+""dosel/zalenium:latest""
+If using docker-compose, version:
+
+OS:
+
+Docker Command to start Zalenium:
+
+version: '2'
+
+services:
+
+ zalenium:
+ image: ""dosel/zalenium:latest""
+ container_name: zalenium
+ hostname: zalenium
+ tty: true
+ volumes:
+ - /tmp/videos:/home/seluser/videos
+ - /var/run/docker.sock:/var/run/docker.sock
+ - /usr/bin/docker:/usr/bin/docker
+ ports:
+ - 4444:4444
+ extra_hosts:
+ - ""myapp.mydomain.fr:172.25.0.10""
+ command: >
+ start --desiredContainers 2
+ --maxDockerSeleniumContainers 8
+ --screenWidth 1680 --screenHeight 1050
+ --timeZone ""Europe/Paris""
+ --videoRecordingEnabled true
+ --sauceLabsEnabled false
+ --browserStackEnabled false
+ --testingBotEnabled false
+ --startTunnel false
+ environment:
+ - HOST_UID
+ - HOST_GID
+ - SAUCE_USERNAME
+ - SAUCE_ACCESS_KEY
+ - BROWSER_STACK_USER
+ - BROWSER_STACK_KEY
+ - TESTINGBOT_KEY
+ - TESTINGBOT_SECRET
+ - LANG=fr_FR.UTF-8
+ - LANGUAGE=fr_FR.UTF-8
+ - LC_ALL=fr_FR.UTF-8
+ networks:
+ mynet:
+ ipv4_address: 172.25.0.15
+
+
+I set :
+chromeOptions.addArguments(""lang=fr_FR"");
+capability.setCapability(ChromeOptions.CAPABILITY, chromeOptions);
+before invoke webdrvier :
+new RemoteWebDriver(new URL(this.hubUrl), capability);
+
+My browser is always in english and not take arguement ""lang=fr""
+
+Thank's for you help and sorry for by bad english :) ",1.0,"Can't choose chrome's language - **Please make sure that you provide enough information for us to help you with this issue. Thank you!**
+
+
+
+Zalenium Image Version(s):
+""dosel/zalenium:latest""
+If using docker-compose, version:
+
+OS:
+
+Docker Command to start Zalenium:
+
+version: '2'
+
+services:
+
+ zalenium:
+ image: ""dosel/zalenium:latest""
+ container_name: zalenium
+ hostname: zalenium
+ tty: true
+ volumes:
+ - /tmp/videos:/home/seluser/videos
+ - /var/run/docker.sock:/var/run/docker.sock
+ - /usr/bin/docker:/usr/bin/docker
+ ports:
+ - 4444:4444
+ extra_hosts:
+ - ""myapp.mydomain.fr:172.25.0.10""
+ command: >
+ start --desiredContainers 2
+ --maxDockerSeleniumContainers 8
+ --screenWidth 1680 --screenHeight 1050
+ --timeZone ""Europe/Paris""
+ --videoRecordingEnabled true
+ --sauceLabsEnabled false
+ --browserStackEnabled false
+ --testingBotEnabled false
+ --startTunnel false
+ environment:
+ - HOST_UID
+ - HOST_GID
+ - SAUCE_USERNAME
+ - SAUCE_ACCESS_KEY
+ - BROWSER_STACK_USER
+ - BROWSER_STACK_KEY
+ - TESTINGBOT_KEY
+ - TESTINGBOT_SECRET
+ - LANG=fr_FR.UTF-8
+ - LANGUAGE=fr_FR.UTF-8
+ - LC_ALL=fr_FR.UTF-8
+ networks:
+ mynet:
+ ipv4_address: 172.25.0.15
+
+
+I set :
+chromeOptions.addArguments(""lang=fr_FR"");
+capability.setCapability(ChromeOptions.CAPABILITY, chromeOptions);
+before invoke webdrvier :
+new RemoteWebDriver(new URL(this.hubUrl), capability);
+
+My browser is always in english and not take arguement ""lang=fr""
+
+Thank's for you help and sorry for by bad english :) ",0,can t choose chrome s language please make sure that you provide enough information for us to help you with this issue thank you zalenium image version s dosel zalenium latest if using docker compose version os docker command to start zalenium version services zalenium image dosel zalenium latest container name zalenium hostname zalenium tty true volumes tmp videos home seluser videos var run docker sock var run docker sock usr bin docker usr bin docker ports extra hosts myapp mydomain fr command start desiredcontainers maxdockerseleniumcontainers screenwidth screenheight timezone europe paris videorecordingenabled true saucelabsenabled false browserstackenabled false testingbotenabled false starttunnel false environment host uid host gid sauce username sauce access key browser stack user browser stack key testingbot key testingbot secret lang fr fr utf language fr fr utf lc all fr fr utf networks mynet address i set chromeoptions addarguments lang fr fr capability setcapability chromeoptions capability chromeoptions before invoke webdrvier new remotewebdriver new url this huburl capability my browser is always in english and not take arguement lang fr thank s for you help and sorry for by bad english ,0
+12228,14442108234.0,IssuesEvent,2020-12-07 17:41:07,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,parser: STRAIGHT_JOIN and SQL_SMALL_RESULT cannot be used at the same time,component/parser severity/moderate type/bug type/compatibility type/duplicate,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+```
+create table t;
+insert into t values(1);
+```
+2. What did you expect to see?
+Results from Mysql:
+```
+mysql> select STRAIGHT_JOIN SQL_SMALL_RESULT count(*) from t;
++----------+
+| count(*) |
++----------+
+| 1 |
++----------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+Results: from TiDB:
+```
+select STRAIGHT_JOIN SQL_SMALL_RESULT count(*) from t;
+ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your TiDB version for the right syntax to use line 1 column 37 near ""SQL_SMALL_RESULT count(*) from t""
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+[tidb@VM2 bin]$ ./tidb-server -V
+2019-11-26 18:27:18.059136 I | maxprocs: Leaving GOMAXPROCS=8: CPU quota undefined
+Release Version:
+Git Commit Hash:
+Git Branch:
+UTC Build Time: 2019-11-22 02:54:53
+GoVersion: go version go1.13.3 linux/amd64
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+",True,"parser: STRAIGHT_JOIN and SQL_SMALL_RESULT cannot be used at the same time - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+```
+create table t;
+insert into t values(1);
+```
+2. What did you expect to see?
+Results from Mysql:
+```
+mysql> select STRAIGHT_JOIN SQL_SMALL_RESULT count(*) from t;
++----------+
+| count(*) |
++----------+
+| 1 |
++----------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+Results: from TiDB:
+```
+select STRAIGHT_JOIN SQL_SMALL_RESULT count(*) from t;
+ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your TiDB version for the right syntax to use line 1 column 37 near ""SQL_SMALL_RESULT count(*) from t""
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+[tidb@VM2 bin]$ ./tidb-server -V
+2019-11-26 18:27:18.059136 I | maxprocs: Leaving GOMAXPROCS=8: CPU quota undefined
+Release Version:
+Git Commit Hash:
+Git Branch:
+UTC Build Time: 2019-11-22 02:54:53
+GoVersion: go version go1.13.3 linux/amd64
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+",1,parser straight join and sql small result cannot be used at the same time bug report please answer these questions before submitting your issue thanks what did you do create table t insert into t values what did you expect to see results from mysql mysql select straight join sql small result count from t count row in set sec what did you see instead results from tidb select straight join sql small result count from t error you have an error in your sql syntax check the manual that corresponds to your tidb version for the right syntax to use line column near sql small result count from t what version of tidb are you using tidb server v or run select tidb version on tidb tidb server v i maxprocs leaving gomaxprocs cpu quota undefined release version git commit hash git branch utc build time goversion go version linux race enabled false tikv min version check table before drop false ,1
+136962,20023377990.0,IssuesEvent,2022-02-01 18:32:44,psf/black,https://api.github.com/repos/psf/black,reopened,Line splitting on conditional operators should take precendence over splitting on function parameters,R: duplicate T: design F: linebreak,"Black should split conditionals at conditional operators (i.e. `and`, `or`, etc.) when possible, instead of splitting function parameters over multiple lines.
+
+Currently, this is how black formats a long conditional:
+```
+if str(
+ self.user.id
+) != self.target_user_id and not CheckUserManagementViewPermission.user_has_permission(
+ self.user
+):
+ pass
+```
+
+Ideally, it should be formatted like this:
+```
+if (
+ str(self.user.id) != self.target_user_id
+ and not CheckUserManagementViewPermission.user_has_permission(
+ self.user
+ )
+):
+ pass
+```
+
+This appears to be a general issue with splitting conditionals and it looks like it's related to these issues: https://github.com/psf/black/issues/815 https://github.com/psf/black/issues/1050",1.0,"Line splitting on conditional operators should take precendence over splitting on function parameters - Black should split conditionals at conditional operators (i.e. `and`, `or`, etc.) when possible, instead of splitting function parameters over multiple lines.
+
+Currently, this is how black formats a long conditional:
+```
+if str(
+ self.user.id
+) != self.target_user_id and not CheckUserManagementViewPermission.user_has_permission(
+ self.user
+):
+ pass
+```
+
+Ideally, it should be formatted like this:
+```
+if (
+ str(self.user.id) != self.target_user_id
+ and not CheckUserManagementViewPermission.user_has_permission(
+ self.user
+ )
+):
+ pass
+```
+
+This appears to be a general issue with splitting conditionals and it looks like it's related to these issues: https://github.com/psf/black/issues/815 https://github.com/psf/black/issues/1050",0,line splitting on conditional operators should take precendence over splitting on function parameters black should split conditionals at conditional operators i e and or etc when possible instead of splitting function parameters over multiple lines currently this is how black formats a long conditional if str self user id self target user id and not checkusermanagementviewpermission user has permission self user pass ideally it should be formatted like this if str self user id self target user id and not checkusermanagementviewpermission user has permission self user pass this appears to be a general issue with splitting conditionals and it looks like it s related to these issues ,0
+5611,5092861751.0,IssuesEvent,2017-01-03 00:20:01,tfussell/xlnt,https://api.github.com/repos/tfussell/xlnt,closed,Create some performance benchmarks,performance,"- Speed in terms of cells written/read per second.
+- Memory usage per cell/row/column/sheet.
+- Time needed to make an identical copy of a large XLSX file.
+- Are there standard benchmarks that other libraries are using?
+",True,"Create some performance benchmarks - - Speed in terms of cells written/read per second.
+- Memory usage per cell/row/column/sheet.
+- Time needed to make an identical copy of a large XLSX file.
+- Are there standard benchmarks that other libraries are using?
+",0,create some performance benchmarks speed in terms of cells written read per second memory usage per cell row column sheet time needed to make an identical copy of a large xlsx file are there standard benchmarks that other libraries are using ,0
+130282,12425976728.0,IssuesEvent,2020-05-24 18:53:58,P3rf3ctXZer0/mc-1.15.2-Pokecube-Evolved,https://api.github.com/repos/P3rf3ctXZer0/mc-1.15.2-Pokecube-Evolved,closed,Twitch Launcher Keeps Glitching Updating PamsTrees2,documentation,Make sure before exporting packs you check to see if pams trees 2 is in the mods,1.0,Twitch Launcher Keeps Glitching Updating PamsTrees2 - Make sure before exporting packs you check to see if pams trees 2 is in the mods,0,twitch launcher keeps glitching updating make sure before exporting packs you check to see if pams trees is in the mods,0
+39917,5256532271.0,IssuesEvent,2017-02-02 18:10:56,cul-2016/quiz,https://api.github.com/repos/cul-2016/quiz,closed,Previewed quiz set to 'already run',bug please-test priority-1,"To replicate:
+
+1. Add a new quiz with at least one question
+2. Preview quiz all the way through, returning to module overview page
+3. Do something else: E.g., go to edit quiz page, or do manual refresh of module overview page, then return to module overview page
+
+The previewed quiz is now shown as having been run, and cannot be run again.",1.0,"Previewed quiz set to 'already run' - To replicate:
+
+1. Add a new quiz with at least one question
+2. Preview quiz all the way through, returning to module overview page
+3. Do something else: E.g., go to edit quiz page, or do manual refresh of module overview page, then return to module overview page
+
+The previewed quiz is now shown as having been run, and cannot be run again.",0,previewed quiz set to already run to replicate add a new quiz with at least one question preview quiz all the way through returning to module overview page do something else e g go to edit quiz page or do manual refresh of module overview page then return to module overview page the previewed quiz is now shown as having been run and cannot be run again ,0
+11861,13995564192.0,IssuesEvent,2020-10-28 03:36:04,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Support multiple table rename (swap table use case),challenge-program difficulty/medium high-performance picked sig/DDL type/compatibility type/enhancement,"## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+I know that multiple DDL changes are currently on the roadmap. My feature request is to support a much smaller subset, which is an atomic rename of two tables.
+
+This supports the use case of swapping tables, something that occurs frequently in the replication stream due to its usage by tools such as `pt-online-schema-change`.
+
+**Describe the feature you'd like:**
+
+```
+mysql> CREATE TABLE t1 (a int);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> CREATE TABLE t2 (a int, b int);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> RENAME TABLE t1 to t1_old, t2 to t1; <--- should work
+ERROR 1105 (HY000): can't run multi schema change
+```
+
+**Describe alternatives you've considered:**
+
+The alternative is to do this non-atomically (breaks apps) or under a global lock (not yet supported by TiDB). So there is not really a good alternative.
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+
+MySQL compatible behavior.
+
+## Score
+1500
+
+## SIG Slack Channel
+You can join [#sig-ddl ](https://app.slack.com/client/TH91JCS4W/CMAKWBNJU)on slack in your spare time to discuss and get help with mentors or others.
+
+## Mentor(s)
+* @zimulala
+
+## Recommended Skills
+* DDL
+* Golang
+
+## Learning Materials
+MySQL's [document](https://dev.mysql.com/doc/refman/8.0/en/invisible-indexes.html) for syntax reference.
+[TiDB DDL architecture](https://github.com/pingcap/tidb/blob/master/docs/design/2018-10-08-online-DDL.md)",True,"Support multiple table rename (swap table use case) - ## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+I know that multiple DDL changes are currently on the roadmap. My feature request is to support a much smaller subset, which is an atomic rename of two tables.
+
+This supports the use case of swapping tables, something that occurs frequently in the replication stream due to its usage by tools such as `pt-online-schema-change`.
+
+**Describe the feature you'd like:**
+
+```
+mysql> CREATE TABLE t1 (a int);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> CREATE TABLE t2 (a int, b int);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> RENAME TABLE t1 to t1_old, t2 to t1; <--- should work
+ERROR 1105 (HY000): can't run multi schema change
+```
+
+**Describe alternatives you've considered:**
+
+The alternative is to do this non-atomically (breaks apps) or under a global lock (not yet supported by TiDB). So there is not really a good alternative.
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+
+MySQL compatible behavior.
+
+## Score
+1500
+
+## SIG Slack Channel
+You can join [#sig-ddl ](https://app.slack.com/client/TH91JCS4W/CMAKWBNJU)on slack in your spare time to discuss and get help with mentors or others.
+
+## Mentor(s)
+* @zimulala
+
+## Recommended Skills
+* DDL
+* Golang
+
+## Learning Materials
+MySQL's [document](https://dev.mysql.com/doc/refman/8.0/en/invisible-indexes.html) for syntax reference.
+[TiDB DDL architecture](https://github.com/pingcap/tidb/blob/master/docs/design/2018-10-08-online-DDL.md)",1,support multiple table rename swap table use case feature request is your feature request related to a problem please describe i know that multiple ddl changes are currently on the roadmap my feature request is to support a much smaller subset which is an atomic rename of two tables this supports the use case of swapping tables something that occurs frequently in the replication stream due to its usage by tools such as pt online schema change describe the feature you d like mysql create table a int query ok rows affected sec mysql create table a int b int query ok rows affected sec mysql rename table to old to should work error can t run multi schema change describe alternatives you ve considered the alternative is to do this non atomically breaks apps or under a global lock not yet supported by tidb so there is not really a good alternative teachability documentation adoption migration strategy mysql compatible behavior score sig slack channel you can join slack in your spare time to discuss and get help with mentors or others mentor s zimulala recommended skills ddl golang learning materials mysql s for syntax reference ,1
+7372,9621030170.0,IssuesEvent,2019-05-14 09:40:55,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Function `period_diff ` is not compatible with MySQL 8.0,component/expression help wanted type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+Function `period_diff` is not compatible with MySQL 8.0
+
+2. What did you expect to see?
+MySQL 8.0:
+```
+mysql> SELECT PERIOD_diff(-00013,1);
+ERROR 1210 (HY000): Incorrect arguments to period_diff
+```
+
+
+3. What did you see instead?
+TiDB
+```
+mysql> SELECT PERIOD_diff(-00013,1);
++-----------------------+
+| PERIOD_diff(-00013,1) |
++-----------------------+
+| 2213609288845122194 |
++-----------------------+
+1 row in set (0.00 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+mysql> select tidb_version();
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta.1-218-g2f7241138-dirty
+Git Commit Hash: 2f7241138adfc434f4b199ecae68fb83ad33b36b
+Git Branch: myfeature-perioddiff
+UTC Build Time: 2019-05-07 03:36:21
+GoVersion: go version go1.11.4 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+",True,"Function `period_diff ` is not compatible with MySQL 8.0 - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+Function `period_diff` is not compatible with MySQL 8.0
+
+2. What did you expect to see?
+MySQL 8.0:
+```
+mysql> SELECT PERIOD_diff(-00013,1);
+ERROR 1210 (HY000): Incorrect arguments to period_diff
+```
+
+
+3. What did you see instead?
+TiDB
+```
+mysql> SELECT PERIOD_diff(-00013,1);
++-----------------------+
+| PERIOD_diff(-00013,1) |
++-----------------------+
+| 2213609288845122194 |
++-----------------------+
+1 row in set (0.00 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+mysql> select tidb_version();
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta.1-218-g2f7241138-dirty
+Git Commit Hash: 2f7241138adfc434f4b199ecae68fb83ad33b36b
+Git Branch: myfeature-perioddiff
+UTC Build Time: 2019-05-07 03:36:21
+GoVersion: go version go1.11.4 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+",1,function period diff is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error function period diff is not compatible with mysql what did you expect to see mysql mysql select period diff error incorrect arguments to period diff what did you see instead tidb mysql select period diff period diff row in set sec what version of tidb are you using tidb server v or run select tidb version on tidb mysql select tidb version tidb version release version beta dirty git commit hash git branch myfeature perioddiff utc build time goversion go version darwin race enabled false tikv min version alpha check table before drop false row in set sec ,1
+301115,9216196333.0,IssuesEvent,2019-03-11 07:11:51,etternagame/etterna,https://api.github.com/repos/etternagame/etterna,closed,Misc Bugs here and there.,Priority: Low,"I made a theme that uses etterna's fallback theme. I went though trying to debug a few things here and there. I found a few issues.
+
+(Missing Metrics)
+
+ScreenSelectPlayMode::ChoiceNonstop=""""
+ScreenSelectPlayMode::ChoiceOni=""""
+ScreenSelectPlayMode::ChoiceEndless=""""
+OptionExplanations::FullTapExplosions="""" (I could not actually get this one to work. Must be broken.)
+
+(Menu Options)
+
+Jukebox does not work. Should be removed.
+Edit Step/Chart does not work. Should be removed.
+
+(Crash)
+
+Couples Mode crashes the game. Needs to be removed.
+
+(Concerns)
+
+Verses and Doubles work but should be removed. (Since player 2 was removed, likely, this will not work in doubles/verses.)
+Nonstop, Oni, and Endless should be removed. (If done, you can ignore the metrics then.)
+
+-----------------------------------------------------------------------------------------------------------
+
+More bugs found. The following seemed to have been removed from the game:
+
+(However, I did a search in the repo and some things still remain noting these, Please be sure to remove them if this is the intended case.)
+
+SONGMAN:GetNumCourses();
+
+Themes/Til Death/BGAnimations/ScreenSelectMusic decorations/other.lua
+src/SongManager.cpp
+Docs/Luadoc/Lua.xml
+Docs/Luadoc/LuaDocumentation.xml
+
+SONGMAN:GetNumAdditionalCourses();
+
+Docs/Luadoc/LuaDocumentation.xml
+
+SONGMAN:GetNumLockedSongs();
+
+Docs/Changelog_sm5.txt
+Docs/Luadoc/LuaDocumentation.xml
+
+Update: SONGMAN:GetNumCourses(); seems to work. Although, it should be removed anyway.
+
+Themes/Til Death/BGAnimations/ScreenSelectMusic decorations/other.lua
+src/SongManager.cpp
+Docs/Luadoc/Lua.xml
+Docs/Luadoc/LuaDocumentation.xml
+
+Update: Hmm... Seems GAMESTATE:GetCurrentStage(); was removed as well? Oh well.
+
+Docs/Changelog_sm5.txt
+Docs/Luadoc/LuaDocumentation.xml
+
+Update: I am unsure but, I think this is removed. PREFSMAN:GetPreference(""PercentageScoring""); Although, a few references to it.
+
+Themes/_fallback/Languages/zh.ini
+Themes/_fallback/Languages/es.ini
+Themes/_fallback/Languages/fr.ini
+Themes/_fallback/Languages/ja.ini
+Themes/_fallback/Languages/nl.ini
+Themes/_fallback/Languages/pl.ini
+Themes/_fallback/Languages/de.ini
+Themes/_fallback/Languages/en.ini
+Docs/old_changelog.txt
+Docs/Changelog_sm-ssc.txt
+Themes/_fallback/metrics.ini
+
+Update: Unsure of this but likely my theme. Check into metric ComboContinuesBetweenSongs.
+
+Update: Two others found. Unsure still. DancePointsForOni and MenuTimer.",1.0,"Misc Bugs here and there. - I made a theme that uses etterna's fallback theme. I went though trying to debug a few things here and there. I found a few issues.
+
+(Missing Metrics)
+
+ScreenSelectPlayMode::ChoiceNonstop=""""
+ScreenSelectPlayMode::ChoiceOni=""""
+ScreenSelectPlayMode::ChoiceEndless=""""
+OptionExplanations::FullTapExplosions="""" (I could not actually get this one to work. Must be broken.)
+
+(Menu Options)
+
+Jukebox does not work. Should be removed.
+Edit Step/Chart does not work. Should be removed.
+
+(Crash)
+
+Couples Mode crashes the game. Needs to be removed.
+
+(Concerns)
+
+Verses and Doubles work but should be removed. (Since player 2 was removed, likely, this will not work in doubles/verses.)
+Nonstop, Oni, and Endless should be removed. (If done, you can ignore the metrics then.)
+
+-----------------------------------------------------------------------------------------------------------
+
+More bugs found. The following seemed to have been removed from the game:
+
+(However, I did a search in the repo and some things still remain noting these, Please be sure to remove them if this is the intended case.)
+
+SONGMAN:GetNumCourses();
+
+Themes/Til Death/BGAnimations/ScreenSelectMusic decorations/other.lua
+src/SongManager.cpp
+Docs/Luadoc/Lua.xml
+Docs/Luadoc/LuaDocumentation.xml
+
+SONGMAN:GetNumAdditionalCourses();
+
+Docs/Luadoc/LuaDocumentation.xml
+
+SONGMAN:GetNumLockedSongs();
+
+Docs/Changelog_sm5.txt
+Docs/Luadoc/LuaDocumentation.xml
+
+Update: SONGMAN:GetNumCourses(); seems to work. Although, it should be removed anyway.
+
+Themes/Til Death/BGAnimations/ScreenSelectMusic decorations/other.lua
+src/SongManager.cpp
+Docs/Luadoc/Lua.xml
+Docs/Luadoc/LuaDocumentation.xml
+
+Update: Hmm... Seems GAMESTATE:GetCurrentStage(); was removed as well? Oh well.
+
+Docs/Changelog_sm5.txt
+Docs/Luadoc/LuaDocumentation.xml
+
+Update: I am unsure but, I think this is removed. PREFSMAN:GetPreference(""PercentageScoring""); Although, a few references to it.
+
+Themes/_fallback/Languages/zh.ini
+Themes/_fallback/Languages/es.ini
+Themes/_fallback/Languages/fr.ini
+Themes/_fallback/Languages/ja.ini
+Themes/_fallback/Languages/nl.ini
+Themes/_fallback/Languages/pl.ini
+Themes/_fallback/Languages/de.ini
+Themes/_fallback/Languages/en.ini
+Docs/old_changelog.txt
+Docs/Changelog_sm-ssc.txt
+Themes/_fallback/metrics.ini
+
+Update: Unsure of this but likely my theme. Check into metric ComboContinuesBetweenSongs.
+
+Update: Two others found. Unsure still. DancePointsForOni and MenuTimer.",0,misc bugs here and there i made a theme that uses etterna s fallback theme i went though trying to debug a few things here and there i found a few issues missing metrics screenselectplaymode choicenonstop screenselectplaymode choiceoni screenselectplaymode choiceendless optionexplanations fulltapexplosions i could not actually get this one to work must be broken menu options jukebox does not work should be removed edit step chart does not work should be removed crash couples mode crashes the game needs to be removed concerns verses and doubles work but should be removed since player was removed likely this will not work in doubles verses nonstop oni and endless should be removed if done you can ignore the metrics then more bugs found the following seemed to have been removed from the game however i did a search in the repo and some things still remain noting these please be sure to remove them if this is the intended case songman getnumcourses themes til death bganimations screenselectmusic decorations other lua src songmanager cpp docs luadoc lua xml docs luadoc luadocumentation xml songman getnumadditionalcourses docs luadoc luadocumentation xml songman getnumlockedsongs docs changelog txt docs luadoc luadocumentation xml update songman getnumcourses seems to work although it should be removed anyway themes til death bganimations screenselectmusic decorations other lua src songmanager cpp docs luadoc lua xml docs luadoc luadocumentation xml update hmm seems gamestate getcurrentstage was removed as well oh well docs changelog txt docs luadoc luadocumentation xml update i am unsure but i think this is removed prefsman getpreference percentagescoring although a few references to it themes fallback languages zh ini themes fallback languages es ini themes fallback languages fr ini themes fallback languages ja ini themes fallback languages nl ini themes fallback languages pl ini themes fallback languages de ini themes fallback languages en ini docs old changelog txt docs changelog sm ssc txt themes fallback metrics ini update unsure of this but likely my theme check into metric combocontinuesbetweensongs update two others found unsure still dancepointsforoni and menutimer ,0
+352416,32065039261.0,IssuesEvent,2023-09-25 01:45:32,unifyai/ivy,https://api.github.com/repos/unifyai/ivy,reopened,Fix jax_lax_operators.test_jax_nextafter,JAX Frontend Sub Task Failing Test,"| | |
+|---|---|
+|numpy|
+|jax|
+|tensorflow|
+|torch|
+|paddle|
+",1.0,"Fix jax_lax_operators.test_jax_nextafter - | | |
+|---|---|
+|numpy|
+|jax|
+|tensorflow|
+|torch|
+|paddle|
+",0,fix jax lax operators test jax nextafter numpy a href src jax a href src tensorflow a href src torch a href src paddle a href src ,0
+11164,13182146458.0,IssuesEvent,2020-08-12 15:20:08,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,join on int primary key and text is not the same with MySQL,type/compatibility type/wontfix,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```
+CREATE TABLE t1 (id int(11) NOT NULL AUTO_INCREMENT, PRIMARY KEY (`id`));
+INSERT INTO t1(`id`) VALUES(3);
+CREATE TABLE t2 (title text);
+INSERT INTO t2(`title`) VALUES(""3.0.1"");
+SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
+```
+
+2. What did you expect to see?
+
+* MySQL 8.0
+
+```
+mysql> CREATE TABLE t1 (id int(11) NOT NULL AUTO_INCREMENT, PRIMARY KEY (`id`));
+Query OK, 0 rows affected, 1 warning (0.01 sec)
+
+mysql> INSERT INTO t1(`id`) VALUES(3);
+Query OK, 1 row affected (0.00 sec)
+
+mysql> CREATE TABLE t2 (title text);
+Query OK, 0 rows affected (0.00 sec)
+
+mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
+Query OK, 1 row affected (0.00 sec)
+
+mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
+Empty set (0.00 sec)
+
+mysql> SELECT version();
++-----------+
+| version() |
++-----------+
+| 8.0.18 |
++-----------+
+1 row in set (0.00 sec)
+
+mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
++----+-------------+-------+------------+--------+---------------+---------+---------+----------------+------+----------+--------------------------+
+| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
++----+-------------+-------+------------+--------+---------------+---------+---------+----------------+------+----------+--------------------------+
+| 1 | SIMPLE | t2 | NULL | ALL | NULL | NULL | NULL | NULL | 1 | 100.00 | Using where |
+| 1 | SIMPLE | t1 | NULL | eq_ref | PRIMARY | PRIMARY | 4 | repro.t2.title | 1 | 100.00 | Using where; Using index |
++----+-------------+-------+------------+--------+---------------+---------+---------+----------------+------+----------+--------------------------+
+2 rows in set, 1 warning (0.00 sec)
+```
+
+3. What did you see instead?
+
+* TiDB
+
+```
+mysql> CREATE TABLE t1 (id int(11) NOT NULL AUTO_INCREMENT, PRIMARY KEY (`id`));
+Query OK, 0 rows affected (0.08 sec)
+
+mysql> INSERT INTO t1(`id`) VALUES(3);
+Query OK, 1 row affected (0.01 sec)
+
+mysql> CREATE TABLE t2 (title text);
+Query OK, 0 rows affected (0.08 sec)
+
+mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
+Query OK, 1 row affected (0.01 sec)
+
+mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
++----+-------+
+| id | title |
++----+-------+
+| 3 | 3.0.1 |
++----+-------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
++----------------------------+-------+-----------+-----------------------------------------------------------------+
+| id | count | task | operator info |
++----------------------------+-------+-----------+-----------------------------------------------------------------+
+| Projection_8 | 1.00 | root | Column#1, Column#2 |
+| └─HashLeftJoin_9 | 1.00 | root | inner join, inner:Projection_14, equal:[eq(Column#6, Column#7)] |
+| ├─Projection_11 | 1.00 | root | Column#1, cast(Column#1) |
+| │ └─TableReader_13 | 1.00 | root | data:TableScan_12 |
+| │ └─TableScan_12 | 1.00 | cop[tikv] | table:t1, range:[-inf,+inf], keep order:false, stats:pseudo |
+| └─Projection_14 | 1.00 | root | Column#2, cast(Column#2) |
+| └─TableReader_16 | 1.00 | root | data:TableScan_15 |
+| └─TableScan_15 | 1.00 | cop[tikv] | table:t2, range:[-inf,+inf], keep order:false, stats:pseudo |
++----------------------------+-------+-----------+-----------------------------------------------------------------+
+8 rows in set (0.00 sec)
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+Release Version: v4.0.0-alpha-842-g3ca8661b5
+Git Commit Hash: 3ca8661b5b3b12ecdfd664a5dd090f2af859a55c
+Git Branch: master
+UTC Build Time: 2019-11-12 01:03:14
+GoVersion: go version go1.13 linux/amd64
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+```
+
+5. More information
+
+BTW, this incorrect behavior only happens in primary key, the following SQLs are executed same in both side.
+
+```
+CREATE TABLE t1 (id int);
+INSERT INTO t1(`id`) VALUES(3);
+CREATE TABLE t2 (title text);
+INSERT INTO t2(`title`) VALUES(""3.0.1"");
+SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
+```
+
+* In MySQL 8.0
+
+```
+mysql> CREATE TABLE t1 (id int);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> INSERT INTO t1(`id`) VALUES(3);
+Query OK, 1 row affected (0.00 sec)
+
+mysql> CREATE TABLE t2 (title text);
+Query OK, 0 rows affected (0.00 sec)
+
+mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
+Query OK, 1 row affected (0.00 sec)
+
+mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
++------+-------+
+| id | title |
++------+-------+
+| 3 | 3.0.1 |
++------+-------+
+1 row in set (0.01 sec)
+
+mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
++----+-------------+-------+------------+------+---------------+------+---------+------+------+----------+----------------------------------------------------+
+| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
++----+-------------+-------+------------+------+---------------+------+---------+------+------+----------+----------------------------------------------------+
+| 1 | SIMPLE | t1 | NULL | ALL | NULL | NULL | NULL | NULL | 1 | 100.00 | NULL |
+| 1 | SIMPLE | t2 | NULL | ALL | NULL | NULL | NULL | NULL | 1 | 100.00 | Using where; Using join buffer (Block Nested Loop) |
++----+-------------+-------+------------+------+---------------+------+---------+------+------+----------+----------------------------------------------------+
+2 rows in set, 1 warning (0.00 sec)
+```
+
+* In TiDB
+
+```
+mysql> CREATE TABLE t1 (id int);
+Query OK, 0 rows affected (0.08 sec)
+
+mysql> INSERT INTO t1(`id`) VALUES(3);
+Query OK, 1 row affected (0.01 sec)
+
+mysql> CREATE TABLE t2 (title text);
+Query OK, 0 rows affected (0.08 sec)
+
+mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
+Query OK, 1 row affected (0.02 sec)
+
+mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
++------+-------+
+| id | title |
++------+-------+
+| 3 | 3.0.1 |
++------+-------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
++----------------------------+----------+-----------+-----------------------------------------------------------------+
+| id | count | task | operator info |
++----------------------------+----------+-----------+-----------------------------------------------------------------+
+| Projection_8 | 12500.00 | root | Column#1, Column#3 |
+| └─HashLeftJoin_9 | 12500.00 | root | inner join, inner:Projection_14, equal:[eq(Column#7, Column#8)] |
+| ├─Projection_11 | 10000.00 | root | Column#1, cast(Column#1) |
+| │ └─TableReader_13 | 10000.00 | root | data:TableScan_12 |
+| │ └─TableScan_12 | 10000.00 | cop[tikv] | table:t1, range:[-inf,+inf], keep order:false, stats:pseudo |
+| └─Projection_14 | 10000.00 | root | Column#3, cast(Column#3) |
+| └─TableReader_16 | 10000.00 | root | data:TableScan_15 |
+| └─TableScan_15 | 10000.00 | cop[tikv] | table:t2, range:[-inf,+inf], keep order:false, stats:pseudo |
++----------------------------+----------+-----------+-----------------------------------------------------------------+
+8 rows in set (0.00 sec)
+```",True,"join on int primary key and text is not the same with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```
+CREATE TABLE t1 (id int(11) NOT NULL AUTO_INCREMENT, PRIMARY KEY (`id`));
+INSERT INTO t1(`id`) VALUES(3);
+CREATE TABLE t2 (title text);
+INSERT INTO t2(`title`) VALUES(""3.0.1"");
+SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
+```
+
+2. What did you expect to see?
+
+* MySQL 8.0
+
+```
+mysql> CREATE TABLE t1 (id int(11) NOT NULL AUTO_INCREMENT, PRIMARY KEY (`id`));
+Query OK, 0 rows affected, 1 warning (0.01 sec)
+
+mysql> INSERT INTO t1(`id`) VALUES(3);
+Query OK, 1 row affected (0.00 sec)
+
+mysql> CREATE TABLE t2 (title text);
+Query OK, 0 rows affected (0.00 sec)
+
+mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
+Query OK, 1 row affected (0.00 sec)
+
+mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
+Empty set (0.00 sec)
+
+mysql> SELECT version();
++-----------+
+| version() |
++-----------+
+| 8.0.18 |
++-----------+
+1 row in set (0.00 sec)
+
+mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
++----+-------------+-------+------------+--------+---------------+---------+---------+----------------+------+----------+--------------------------+
+| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
++----+-------------+-------+------------+--------+---------------+---------+---------+----------------+------+----------+--------------------------+
+| 1 | SIMPLE | t2 | NULL | ALL | NULL | NULL | NULL | NULL | 1 | 100.00 | Using where |
+| 1 | SIMPLE | t1 | NULL | eq_ref | PRIMARY | PRIMARY | 4 | repro.t2.title | 1 | 100.00 | Using where; Using index |
++----+-------------+-------+------------+--------+---------------+---------+---------+----------------+------+----------+--------------------------+
+2 rows in set, 1 warning (0.00 sec)
+```
+
+3. What did you see instead?
+
+* TiDB
+
+```
+mysql> CREATE TABLE t1 (id int(11) NOT NULL AUTO_INCREMENT, PRIMARY KEY (`id`));
+Query OK, 0 rows affected (0.08 sec)
+
+mysql> INSERT INTO t1(`id`) VALUES(3);
+Query OK, 1 row affected (0.01 sec)
+
+mysql> CREATE TABLE t2 (title text);
+Query OK, 0 rows affected (0.08 sec)
+
+mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
+Query OK, 1 row affected (0.01 sec)
+
+mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
++----+-------+
+| id | title |
++----+-------+
+| 3 | 3.0.1 |
++----+-------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
++----------------------------+-------+-----------+-----------------------------------------------------------------+
+| id | count | task | operator info |
++----------------------------+-------+-----------+-----------------------------------------------------------------+
+| Projection_8 | 1.00 | root | Column#1, Column#2 |
+| └─HashLeftJoin_9 | 1.00 | root | inner join, inner:Projection_14, equal:[eq(Column#6, Column#7)] |
+| ├─Projection_11 | 1.00 | root | Column#1, cast(Column#1) |
+| │ └─TableReader_13 | 1.00 | root | data:TableScan_12 |
+| │ └��TableScan_12 | 1.00 | cop[tikv] | table:t1, range:[-inf,+inf], keep order:false, stats:pseudo |
+| └─Projection_14 | 1.00 | root | Column#2, cast(Column#2) |
+| └─TableReader_16 | 1.00 | root | data:TableScan_15 |
+| └─TableScan_15 | 1.00 | cop[tikv] | table:t2, range:[-inf,+inf], keep order:false, stats:pseudo |
++----------------------------+-------+-----------+-----------------------------------------------------------------+
+8 rows in set (0.00 sec)
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+Release Version: v4.0.0-alpha-842-g3ca8661b5
+Git Commit Hash: 3ca8661b5b3b12ecdfd664a5dd090f2af859a55c
+Git Branch: master
+UTC Build Time: 2019-11-12 01:03:14
+GoVersion: go version go1.13 linux/amd64
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+```
+
+5. More information
+
+BTW, this incorrect behavior only happens in primary key, the following SQLs are executed same in both side.
+
+```
+CREATE TABLE t1 (id int);
+INSERT INTO t1(`id`) VALUES(3);
+CREATE TABLE t2 (title text);
+INSERT INTO t2(`title`) VALUES(""3.0.1"");
+SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
+```
+
+* In MySQL 8.0
+
+```
+mysql> CREATE TABLE t1 (id int);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> INSERT INTO t1(`id`) VALUES(3);
+Query OK, 1 row affected (0.00 sec)
+
+mysql> CREATE TABLE t2 (title text);
+Query OK, 0 rows affected (0.00 sec)
+
+mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
+Query OK, 1 row affected (0.00 sec)
+
+mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
++------+-------+
+| id | title |
++------+-------+
+| 3 | 3.0.1 |
++------+-------+
+1 row in set (0.01 sec)
+
+mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
++----+-------------+-------+------------+------+---------------+------+---------+------+------+----------+----------------------------------------------------+
+| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
++----+-------------+-------+------------+------+---------------+------+---------+------+------+----------+----------------------------------------------------+
+| 1 | SIMPLE | t1 | NULL | ALL | NULL | NULL | NULL | NULL | 1 | 100.00 | NULL |
+| 1 | SIMPLE | t2 | NULL | ALL | NULL | NULL | NULL | NULL | 1 | 100.00 | Using where; Using join buffer (Block Nested Loop) |
++----+-------------+-------+------------+------+---------------+------+---------+------+------+----------+----------------------------------------------------+
+2 rows in set, 1 warning (0.00 sec)
+```
+
+* In TiDB
+
+```
+mysql> CREATE TABLE t1 (id int);
+Query OK, 0 rows affected (0.08 sec)
+
+mysql> INSERT INTO t1(`id`) VALUES(3);
+Query OK, 1 row affected (0.01 sec)
+
+mysql> CREATE TABLE t2 (title text);
+Query OK, 0 rows affected (0.08 sec)
+
+mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
+Query OK, 1 row affected (0.02 sec)
+
+mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
++------+-------+
+| id | title |
++------+-------+
+| 3 | 3.0.1 |
++------+-------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
++----------------------------+----------+-----------+-----------------------------------------------------------------+
+| id | count | task | operator info |
++----------------------------+----------+-----------+-----------------------------------------------------------------+
+| Projection_8 | 12500.00 | root | Column#1, Column#3 |
+| └─HashLeftJoin_9 | 12500.00 | root | inner join, inner:Projection_14, equal:[eq(Column#7, Column#8)] |
+| ├─Projection_11 | 10000.00 | root | Column#1, cast(Column#1) |
+| │ └─TableReader_13 | 10000.00 | root | data:TableScan_12 |
+| │ └─TableScan_12 | 10000.00 | cop[tikv] | table:t1, range:[-inf,+inf], keep order:false, stats:pseudo |
+| └─Projection_14 | 10000.00 | root | Column#3, cast(Column#3) |
+| └─TableReader_16 | 10000.00 | root | data:TableScan_15 |
+| └─TableScan_15 | 10000.00 | cop[tikv] | table:t2, range:[-inf,+inf], keep order:false, stats:pseudo |
++----------------------------+----------+-----------+-----------------------------------------------------------------+
+8 rows in set (0.00 sec)
+```",1,join on int primary key and text is not the same with mysql bug report please answer these questions before submitting your issue thanks what did you do create table id int not null auto increment primary key id insert into id values create table title text insert into title values select from join on id title what did you expect to see mysql mysql create table id int not null auto increment primary key id query ok rows affected warning sec mysql insert into id values query ok row affected sec mysql create table title text query ok rows affected sec mysql insert into title values query ok row affected sec mysql select from join on id title empty set sec mysql select version version row in set sec mysql explain select from join on id title id select type table partitions type possible keys key key len ref rows filtered extra simple null all null null null null using where simple null eq ref primary primary repro title using where using index rows in set warning sec what did you see instead tidb mysql create table id int not null auto increment primary key id query ok rows affected sec mysql insert into id values query ok row affected sec mysql create table title text query ok rows affected sec mysql insert into title values query ok row affected sec mysql select from join on id title id title row in set warning sec mysql explain select from join on id title id count task operator info projection root column column └─hashleftjoin root inner join inner projection equal ├─projection root column cast column │ └─tablereader root data tablescan │ └─tablescan cop table range keep order false stats pseudo └─projection root column cast column └─tablereader root data tablescan └─tablescan cop table range keep order false stats pseudo rows in set sec what version of tidb are you using tidb server v or run select tidb version on tidb release version alpha git commit hash git branch master utc build time goversion go version linux race enabled false tikv min version check table before drop false more information btw this incorrect behavior only happens in primary key the following sqls are executed same in both side create table id int insert into id values create table title text insert into title values select from join on id title in mysql mysql create table id int query ok rows affected sec mysql insert into id values query ok row affected sec mysql create table title text query ok rows affected sec mysql insert into title values query ok row affected sec mysql select from join on id title id title row in set sec mysql explain select from join on id title id select type table partitions type possible keys key key len ref rows filtered extra simple null all null null null null null simple null all null null null null using where using join buffer block nested loop rows in set warning sec in tidb mysql create table id int query ok rows affected sec mysql insert into id values query ok row affected sec mysql create table title text query ok rows affected sec mysql insert into title values query ok row affected sec mysql select from join on id title id title row in set warning sec mysql explain select from join on id title id count task operator info projection root column column └─hashleftjoin root inner join inner projection equal ├─projection root column cast column │ └─tablereader root data tablescan │ └─tablescan cop table range keep order false stats pseudo └─projection root column cast column └─tablereader root data tablescan └─tablescan cop table range keep order false stats pseudo rows in set sec ,1
+69787,22669454850.0,IssuesEvent,2022-07-03 11:47:05,cython/cython,https://api.github.com/repos/cython/cython,closed,[BUG] Includes: declaration for newfunc is wrong,defect Library,"
+
+Hello up there. object.pxd currently declares `newfunc` as follows:
+
+```pyx
+ctypedef object (*newfunc)(cpython.type.type, object, object) # (type, args, kwargs)
+```
+
+which implies that `args` and `kwargs` are always live objects and cannot be NULL.
+
+However Python can, and does, call tp_new with either args=NULL, or kwargs=NULL or both. And in such cases this leads to segfault in automatically-generated __Pyx_INCREF for args or kw.
+
+The fix is to change `object` to `PyObject*` for both args and kwargs.
+
+Please see below for details:
+
+```cython
+# cython: language_level=3
+from cpython cimport newfunc, type as cpytype, Py_TYPE
+
+cdef class X:
+ cdef int i
+ def __init__(self, i):
+ self.i = i
+ def __repr__(self):
+ return 'X(%d)' % self.i
+
+cdef newfunc _orig_tp_new = Py_TYPE(X(0)).tp_new
+
+cdef object _trace_tp_new(cpytype cls, object args, object kw):
+ print('_trace_tp_new', cls, args, kw)
+ return _orig_tp_new(cls, args, kw)
+
+Py_TYPE(X(0)).tp_new = _trace_tp_new
+
+
+x = X(123)
+print(x)
+```
+
+```console
+(neo) (py3.venv) (g.env) kirr@deca:~/src/tools/go/pygolang$ cythonize -i x.pyx
+Compiling /home/kirr/src/tools/go/pygolang/x.pyx because it changed.
+[1/1] Cythonizing /home/kirr/src/tools/go/pygolang/x.pyx
+running build_ext
+building 'x' extension
+...
+x86_64-linux-gnu-gcc -pthread -Wno-unused-result -Wsign-compare -DNDEBUG -g -fwrapv -O2 -Wall -g -ffile-prefix-map=/build/python3.9-RNBry6/python3.9-3.9.2=. -fstack-protector-strong -Wformat -Werror=format-security -g -fwrapv -O2 -g -ffile-prefix-map=/build/python3.9-RNBry6/python3.9-3.9.2=. -fstack-protector-strong -Wformat -Werror=format-security -Wdate-time -D_FORTIFY_SOURCE=2 -fPIC -I/home/kirr/src/wendelin/venv/py3.venv/include -I/usr/include/python3.9 -c /home/kirr/src/tools/go/pygolang/x.c -o /home/kirr/src/tools/go/pygolang/tmpqkz1r96s/home/kirr/src/tools/go/pygolang/x.o
+x86_64-linux-gnu-gcc -pthread -shared -Wl,-O1 -Wl,-Bsymbolic-functions -Wl,-z,relro -g -fwrapv -O2 -Wl,-z,relro -g -fwrapv -O2 -g -ffile-prefix-map=/build/python3.9-RNBry6/python3.9-3.9.2=. -fstack-protector-strong -Wformat -Werror=format-security -Wdate-time -D_FORTIFY_SOURCE=2 /home/kirr/src/tools/go/pygolang/tmpqkz1r96s/home/kirr/src/tools/go/pygolang/x.o -o /home/kirr/src/tools/go/pygolang/x.cpython-39-x86_64-linux-gnu.so
+```
+
+```console
+(neo) (py3.venv) (g.env) kirr@deca:~/src/tools/go/pygolang$ python -c 'import x'
+Ошибка сегментирования (стек памяти сброшен на диск)
+```
+
+```console
+(neo) (py3.venv) (g.env) kirr@deca:~/src/tools/go/pygolang$ gdb python core
+...
+Reading symbols from python...
+Reading symbols from /usr/lib/debug/.build-id/f9/02f8a561c3abdb9c8d8c859d4243bd8c3f928f.debug...
+[New LWP 218557]
+[Thread debugging using libthread_db enabled]
+Using host libthread_db library ""/lib/x86_64-linux-gnu/libthread_db.so.1"".
+Core was generated by `python -c import x'.
+Program terminated with signal SIGSEGV, Segmentation fault.
+#0 _Py_INCREF (op=0x0) at /usr/include/python3.9/object.h:408
+408 op->ob_refcnt++;
+
+(gdb) bt 5
+#0 _Py_INCREF (op=0x0) at /usr/include/python3.9/object.h:408
+#1 __pyx_f_1x__trace_tp_new (__pyx_v_cls=0x7f5ce75e6880 <__pyx_type_1x_X>, __pyx_v_args=(123,), __pyx_v_kw=0x0) at /home/kirr/src/tools/go/pygolang/x.c:1986
+#2 0x000000000051dd7e in type_call (type=type@entry=0x7f5ce75e6880 <__pyx_type_1x_X>, args=args@entry=(123,), kwds=kwds@entry=0x0)
+ at ../Objects/typeobject.c:1014
+#3 0x00007f5ce75df8d4 in __Pyx_PyObject_Call (func=, arg=(123,), kw=0x0) at /home/kirr/src/tools/go/pygolang/x.c:3414
+#4 0x00007f5ce75df276 in __pyx_pymod_exec_x (__pyx_pyinit_module=) at /home/kirr/src/tools/go/pygolang/x.c:3017
+(More stack frames follow...)
+
+(gdb) f 1
+#1 __pyx_f_1x__trace_tp_new (__pyx_v_cls=0x7f5ce75e6880 <__pyx_type_1x_X>, __pyx_v_args=(123,), __pyx_v_kw=0x0) at /home/kirr/src/tools/go/pygolang/x.c:1986
+1986 __Pyx_INCREF(__pyx_v_kw);
+```
+
+
+**Expected behavior**
+No segfault in autogenerated coce if `_trace_tp_new` matches `newfunc` signature.
+
+**Environment (please complete the following information):**
+ - OS: Linux
+ - Python version: 3.9.2
+ - Cython version: 0.29.30
+
+
+Thanks beforehand,
+Kirill",1.0,"[BUG] Includes: declaration for newfunc is wrong -
+
+Hello up there. object.pxd currently declares `newfunc` as follows:
+
+```pyx
+ctypedef object (*newfunc)(cpython.type.type, object, object) # (type, args, kwargs)
+```
+
+which implies that `args` and `kwargs` are always live objects and cannot be NULL.
+
+However Python can, and does, call tp_new with either args=NULL, or kwargs=NULL or both. And in such cases this leads to segfault in automatically-generated __Pyx_INCREF for args or kw.
+
+The fix is to change `object` to `PyObject*` for both args and kwargs.
+
+Please see below for details:
+
+```cython
+# cython: language_level=3
+from cpython cimport newfunc, type as cpytype, Py_TYPE
+
+cdef class X:
+ cdef int i
+ def __init__(self, i):
+ self.i = i
+ def __repr__(self):
+ return 'X(%d)' % self.i
+
+cdef newfunc _orig_tp_new = Py_TYPE(X(0)).tp_new
+
+cdef object _trace_tp_new(cpytype cls, object args, object kw):
+ print('_trace_tp_new', cls, args, kw)
+ return _orig_tp_new(cls, args, kw)
+
+Py_TYPE(X(0)).tp_new = _trace_tp_new
+
+
+x = X(123)
+print(x)
+```
+
+```console
+(neo) (py3.venv) (g.env) kirr@deca:~/src/tools/go/pygolang$ cythonize -i x.pyx
+Compiling /home/kirr/src/tools/go/pygolang/x.pyx because it changed.
+[1/1] Cythonizing /home/kirr/src/tools/go/pygolang/x.pyx
+running build_ext
+building 'x' extension
+...
+x86_64-linux-gnu-gcc -pthread -Wno-unused-result -Wsign-compare -DNDEBUG -g -fwrapv -O2 -Wall -g -ffile-prefix-map=/build/python3.9-RNBry6/python3.9-3.9.2=. -fstack-protector-strong -Wformat -Werror=format-security -g -fwrapv -O2 -g -ffile-prefix-map=/build/python3.9-RNBry6/python3.9-3.9.2=. -fstack-protector-strong -Wformat -Werror=format-security -Wdate-time -D_FORTIFY_SOURCE=2 -fPIC -I/home/kirr/src/wendelin/venv/py3.venv/include -I/usr/include/python3.9 -c /home/kirr/src/tools/go/pygolang/x.c -o /home/kirr/src/tools/go/pygolang/tmpqkz1r96s/home/kirr/src/tools/go/pygolang/x.o
+x86_64-linux-gnu-gcc -pthread -shared -Wl,-O1 -Wl,-Bsymbolic-functions -Wl,-z,relro -g -fwrapv -O2 -Wl,-z,relro -g -fwrapv -O2 -g -ffile-prefix-map=/build/python3.9-RNBry6/python3.9-3.9.2=. -fstack-protector-strong -Wformat -Werror=format-security -Wdate-time -D_FORTIFY_SOURCE=2 /home/kirr/src/tools/go/pygolang/tmpqkz1r96s/home/kirr/src/tools/go/pygolang/x.o -o /home/kirr/src/tools/go/pygolang/x.cpython-39-x86_64-linux-gnu.so
+```
+
+```console
+(neo) (py3.venv) (g.env) kirr@deca:~/src/tools/go/pygolang$ python -c 'import x'
+Ошибка сегментирования (стек памяти сброшен на диск)
+```
+
+```console
+(neo) (py3.venv) (g.env) kirr@deca:~/src/tools/go/pygolang$ gdb python core
+...
+Reading symbols from python...
+Reading symbols from /usr/lib/debug/.build-id/f9/02f8a561c3abdb9c8d8c859d4243bd8c3f928f.debug...
+[New LWP 218557]
+[Thread debugging using libthread_db enabled]
+Using host libthread_db library ""/lib/x86_64-linux-gnu/libthread_db.so.1"".
+Core was generated by `python -c import x'.
+Program terminated with signal SIGSEGV, Segmentation fault.
+#0 _Py_INCREF (op=0x0) at /usr/include/python3.9/object.h:408
+408 op->ob_refcnt++;
+
+(gdb) bt 5
+#0 _Py_INCREF (op=0x0) at /usr/include/python3.9/object.h:408
+#1 __pyx_f_1x__trace_tp_new (__pyx_v_cls=0x7f5ce75e6880 <__pyx_type_1x_X>, __pyx_v_args=(123,), __pyx_v_kw=0x0) at /home/kirr/src/tools/go/pygolang/x.c:1986
+#2 0x000000000051dd7e in type_call (type=type@entry=0x7f5ce75e6880 <__pyx_type_1x_X>, args=args@entry=(123,), kwds=kwds@entry=0x0)
+ at ../Objects/typeobject.c:1014
+#3 0x00007f5ce75df8d4 in __Pyx_PyObject_Call (func=, arg=(123,), kw=0x0) at /home/kirr/src/tools/go/pygolang/x.c:3414
+#4 0x00007f5ce75df276 in __pyx_pymod_exec_x (__pyx_pyinit_module=) at /home/kirr/src/tools/go/pygolang/x.c:3017
+(More stack frames follow...)
+
+(gdb) f 1
+#1 __pyx_f_1x__trace_tp_new (__pyx_v_cls=0x7f5ce75e6880 <__pyx_type_1x_X>, __pyx_v_args=(123,), __pyx_v_kw=0x0) at /home/kirr/src/tools/go/pygolang/x.c:1986
+1986 __Pyx_INCREF(__pyx_v_kw);
+```
+
+
+**Expected behavior**
+No segfault in autogenerated coce if `_trace_tp_new` matches `newfunc` signature.
+
+**Environment (please complete the following information):**
+ - OS: Linux
+ - Python version: 3.9.2
+ - Cython version: 0.29.30
+
+
+Thanks beforehand,
+Kirill",0, includes declaration for newfunc is wrong please read this first do not use the bug and feature tracker for general questions and support requests use the cython users mailing list instead it has a wider audience so you get more and better answers did you search for similar issues already please do it helps to save us precious time that we otherwise could not invest into development did you try the latest master branch or pre release it might already have what you want to report also see the regarding recent changes hello up there object pxd currently declares newfunc as follows pyx ctypedef object newfunc cpython type type object object type args kwargs which implies that args and kwargs are always live objects and cannot be null however python can and does call tp new with either args null or kwargs null or both and in such cases this leads to segfault in automatically generated pyx incref for args or kw the fix is to change object to pyobject for both args and kwargs please see below for details cython cython language level from cpython cimport newfunc type as cpytype py type cdef class x cdef int i def init self i self i i def repr self return x d self i cdef newfunc orig tp new py type x tp new cdef object trace tp new cpytype cls object args object kw print trace tp new cls args kw return orig tp new cls args kw py type x tp new trace tp new x x print x console neo venv g env kirr deca src tools go pygolang cythonize i x pyx compiling home kirr src tools go pygolang x pyx because it changed cythonizing home kirr src tools go pygolang x pyx running build ext building x extension linux gnu gcc pthread wno unused result wsign compare dndebug g fwrapv wall g ffile prefix map build fstack protector strong wformat werror format security g fwrapv g ffile prefix map build fstack protector strong wformat werror format security wdate time d fortify source fpic i home kirr src wendelin venv venv include i usr include c home kirr src tools go pygolang x c o home kirr src tools go pygolang home kirr src tools go pygolang x o linux gnu gcc pthread shared wl wl bsymbolic functions wl z relro g fwrapv wl z relro g fwrapv g ffile prefix map build fstack protector strong wformat werror format security wdate time d fortify source home kirr src tools go pygolang home kirr src tools go pygolang x o o home kirr src tools go pygolang x cpython linux gnu so console neo venv g env kirr deca src tools go pygolang python c import x ошибка сегментирования стек памяти сброшен на диск console neo venv g env kirr deca src tools go pygolang gdb python core reading symbols from python reading symbols from usr lib debug build id debug using host libthread db library lib linux gnu libthread db so core was generated by python c import x program terminated with signal sigsegv segmentation fault py incref op at usr include object h op ob refcnt gdb bt py incref op at usr include object h pyx f trace tp new pyx v cls pyx v args pyx v kw at home kirr src tools go pygolang x c in type call type type entry args args entry kwds kwds entry at objects typeobject c in pyx pyobject call func arg kw at home kirr src tools go pygolang x c in pyx pymod exec x pyx pyinit module at home kirr src tools go pygolang x c more stack frames follow gdb f pyx f trace tp new pyx v cls pyx v args pyx v kw at home kirr src tools go pygolang x c pyx incref pyx v kw expected behavior no segfault in autogenerated coce if trace tp new matches newfunc signature environment please complete the following information os linux python version cython version thanks beforehand kirill,0
+14844,18344170075.0,IssuesEvent,2021-10-08 02:27:25,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,SET PASSWORD FOR CURRENT_USER() fails,type/bug type/compatibility sig/execution severity/moderate,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```sql
+select current_user();
+SET PASSWORD FOR CURRENT_USER() = ""admin""; # fails
+SET PASSWORD for ""root""@""%"" = ""admin""; # works
+```
+
+### 2. What did you expect to see? (Required)
+
+The statements should both work.
+
+### 3. What did you see instead (Required)
+
+```sql
+mysql> select current_user();
++----------------+
+| current_user() |
++----------------+
+| root@% |
++----------------+
+1 row in set (0.00 sec)
+
+mysql> SET PASSWORD FOR CURRENT_USER() = ""admin""; # fails
+ERROR 1133 (42000): Can't find any matching row in the user table
+mysql> SET PASSWORD for ""root""@""%"" = ""admin""; # works
+Query OK, 0 rows affected (0.00 sec)
+```
+### 4. What is your TiDB version? (Required)
+
+```sql
+mysql> SELECT tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v5.3.0-alpha-256-gb0b559f23
+Edition: Community
+Git Commit Hash: b0b559f2389de5e27d0d2e12d2bfae049186b54b
+Git Branch: master
+UTC Build Time: 2021-10-01 14:52:33
+GoVersion: go1.16.7
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+1 row in set (0.00 sec)
+```
+",True,"SET PASSWORD FOR CURRENT_USER() fails - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```sql
+select current_user();
+SET PASSWORD FOR CURRENT_USER() = ""admin""; # fails
+SET PASSWORD for ""root""@""%"" = ""admin""; # works
+```
+
+### 2. What did you expect to see? (Required)
+
+The statements should both work.
+
+### 3. What did you see instead (Required)
+
+```sql
+mysql> select current_user();
++----------------+
+| current_user() |
++----------------+
+| root@% |
++----------------+
+1 row in set (0.00 sec)
+
+mysql> SET PASSWORD FOR CURRENT_USER() = ""admin""; # fails
+ERROR 1133 (42000): Can't find any matching row in the user table
+mysql> SET PASSWORD for ""root""@""%"" = ""admin""; # works
+Query OK, 0 rows affected (0.00 sec)
+```
+### 4. What is your TiDB version? (Required)
+
+```sql
+mysql> SELECT tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v5.3.0-alpha-256-gb0b559f23
+Edition: Community
+Git Commit Hash: b0b559f2389de5e27d0d2e12d2bfae049186b54b
+Git Branch: master
+UTC Build Time: 2021-10-01 14:52:33
+GoVersion: go1.16.7
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+1 row in set (0.00 sec)
+```
+",1,set password for current user fails bug report please answer these questions before submitting your issue thanks minimal reproduce step required sql select current user set password for current user admin fails set password for root admin works what did you expect to see required the statements should both work what did you see instead required sql mysql select current user current user root row in set sec mysql set password for current user admin fails error can t find any matching row in the user table mysql set password for root admin works query ok rows affected sec what is your tidb version required sql mysql select tidb version g row tidb version release version alpha edition community git commit hash git branch master utc build time goversion race enabled false tikv min version check table before drop false row in set sec ,1
+260766,8214534148.0,IssuesEvent,2018-09-04 23:56:05,kassy916/Test,https://api.github.com/repos/kassy916/Test,closed,芸人のフォロー/フォロー解除機能,priority:middle ruby,"## WHAT - 何を作るのか?
+ユーザーが芸人をフォロー/フォロー解除する機能
+フォロー数は1000までを予定
+
+### フォローボタンの仕様
+フォローしてないときは「フォロー」を表示
+フォローしてるとき→「フォロー中」を表示、マウスオーバーで「フォロー解除」に文字を変更
+
+## WHY - 何故作るのか?
+「自分の好きな芸人さんの情報がほしい」というお客さん(ユーザー)のニーズに答えるため
+
+## HOW - どうやって作るのか?
+
+
+
+## 参考URL
+- [すごく参考になるページ](https://www.google.com)
+- [ちょっと参考になるページ](https://www.yahoo.com)
+
+
+## 参考資料
+添付ファイルを参照(ある場合は)
+",1.0,"芸人のフォロー/フォロー解除機能 - ## WHAT - 何を作るのか?
+ユーザーが芸人をフォロー/フォロー解除する機能
+フォロー数は1000までを予定
+
+### フォローボタンの仕様
+フォローしてないときは「フォロー」を表示
+フォローしてるとき→「フォロー中」を表示、マウスオーバーで「フォロー解除」に文字を変更
+
+## WHY - 何故作るのか?
+「自分の好きな芸人さんの情報がほしい」というお客さん(ユーザー)のニーズに答えるため
+
+## HOW - どうやって作るのか?
+
+
+
+## 参考URL
+- [すごく参考になるページ](https://www.google.com)
+- [ちょっと参考になるページ](https://www.yahoo.com)
+
+
+## 参考資料
+添付ファイルを参照(ある場合は)
+",0,芸人のフォロー/フォロー解除機能 what 何を作るのか? ユーザーが芸人をフォロー/フォロー解除する機能 フォローボタンの仕様 フォローしてないときは「フォロー」を表示 フォローしてるとき→「フォロー中」を表示、マウスオーバーで「フォロー解除」に文字を変更 why 何故作るのか? 「自分の好きな芸人さんの情報がほしい」というお客さん(ユーザー)のニーズに答えるため how どうやって作るのか? 参考url 参考資料 添付ファイルを参照(ある場合は) ,0
+147979,19526236751.0,IssuesEvent,2021-12-30 08:22:24,panasalap/linux-4.1.15,https://api.github.com/repos/panasalap/linux-4.1.15,opened,CVE-2021-28660 (High) detected in linux-stable-rtv4.1.33,security vulnerability,"## CVE-2021-28660 - High Severity Vulnerability
+ Vulnerable Library - linux-stable-rtv4.1.33
+
-The log message always seems to show the first frontend (alphabetically) from consul.
+
Found in base branch: master
+
+
+ Vulnerable Source Files (2)
+
+
-### Output of `traefik version`: (_What version of Traefik are you using?_)
+ /drivers/staging/rtl8188eu/os_dep/ioctl_linux.c
+ /drivers/staging/rtl8188eu/os_dep/ioctl_linux.c
+
+
+
+
+
+
+ Vulnerability Details
+
+
+rtw_wx_set_scan in drivers/staging/rtl8188eu/os_dep/ioctl_linux.c in the Linux kernel through 5.11.6 allows writing beyond the end of the ->ssid[] array. NOTE: from the perspective of kernel.org releases, CVE IDs are not normally used for drivers/staging/* (unfinished work); however, system integrators may have situations in which a drivers/staging issue is relevant to their own customer base.
-1.6.4
-",1.0,"Access log records the wrong frontend name - ### Do you want to request a *feature* or report a *bug*?
+
-1. Using the consul config provider, create several frontends (with different Host rules) and point them to the same backend.
-2. Turn on the `accessLog` feature.
-3. Make a HTTP request to one of the frontend domains.
+
+
+
-### What did you expect to see?
+***
+Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",True,"CVE-2021-28660 (High) detected in linux-stable-rtv4.1.33 - ## CVE-2021-28660 - High Severity Vulnerability
+ Vulnerable Library - linux-stable-rtv4.1.33
+
-The log message includes the name of the frontend matching the domain of the HTTP request.
+
-The log message always seems to show the first frontend (alphabetically) from consul.
+ /drivers/staging/rtl8188eu/os_dep/ioctl_linux.c
+ /drivers/staging/rtl8188eu/os_dep/ioctl_linux.c
+
+
+
+
+
+
+ Vulnerability Details
+
+
+rtw_wx_set_scan in drivers/staging/rtl8188eu/os_dep/ioctl_linux.c in the Linux kernel through 5.11.6 allows writing beyond the end of the ->ssid[] array. NOTE: from the perspective of kernel.org releases, CVE IDs are not normally used for drivers/staging/* (unfinished work); however, system integrators may have situations in which a drivers/staging issue is relevant to their own customer base.
-### Output of `traefik version`: (_What version of Traefik are you using?_)
+
-1.6.4
-",0,access log records the wrong frontend name do you want to request a feature or report a bug bug what did you do using the consul config provider create several frontends with different host rules and point them to the same backend turn on the accesslog feature make a http request to one of the frontend domains what did you expect to see the log message includes the name of the frontend matching the domain of the http request what did you see instead the log message always seems to show the first frontend alphabetically from consul output of traefik version what version of traefik are you using ,0
-7034,9307518771.0,IssuesEvent,2019-03-25 12:30:39,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,`SELECT 9223372036854775807 + 1;` is not compatible with MySQL,type/compatibility,"## Bug Report
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Local
+ - Attack Complexity: Low
+ - Privileges Required: Low
+ - User Interaction: None
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: High
+ - Integrity Impact: High
+ - Availability Impact: High
+
+For more information on CVSS3 Scores, click here.
+
+
+
+ Suggested Fix
+
-Please answer these questions before submitting your issue. Thanks!
+
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-`SELECT 9223372036854775807 + 1;`
-
-2. What did you expect to see?
-In Mysql 8.0.15
-```
-mysql> SELECT 9223372036854775807+1;
-ERROR 1690 (22003): BIGINT value is out of range in '(9223372036854775807 + 1)'
-```
-See also https://dev.mysql.com/doc/refman/8.0/en/out-of-range-and-overflow.html
-
-3. What did you see instead?
-```
-mysql> SELECT 9223372036854775807+1;
-+-----------------------+
-| 9223372036854775807+1 |
-+-----------------------+
-| 9223372036854775808 |
-+-----------------------+
-1 row in set (0.00 sec)
-```
+
+
+
+***
+Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",0,cve high detected in linux stable cve high severity vulnerability vulnerable library linux stable julia cartwright s fork of linux stable rt git library home page a href found in head commit a href found in base branch master vulnerable source files drivers staging os dep ioctl linux c drivers staging os dep ioctl linux c vulnerability details rtw wx set scan in drivers staging os dep ioctl linux c in the linux kernel through allows writing beyond the end of the ssid array note from the perspective of kernel org releases cve ids are not normally used for drivers staging unfinished work however system integrators may have situations in which a drivers staging issue is relevant to their own customer base publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required low user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource ,0
+115502,14789798427.0,IssuesEvent,2021-01-12 11:04:36,mutwo-org/mutwo,https://api.github.com/repos/mutwo-org/mutwo,opened,set doc string standard,design documentation enhancement,"@timpauli if we want to use [spinx](https://www.sphinx-doc.org) for building the documentation, it may be a good idea to use their standard for doc string formation (to have access to their automatic markdown) as it is described [here](https://sphinx-rtd-tutorial.readthedocs.io/en/latest/docstrings.html). What do you think?",1.0,"set doc string standard - @timpauli if we want to use [spinx](https://www.sphinx-doc.org) for building the documentation, it may be a good idea to use their standard for doc string formation (to have access to their automatic markdown) as it is described [here](https://sphinx-rtd-tutorial.readthedocs.io/en/latest/docstrings.html). What do you think?",0,set doc string standard timpauli if we want to use for building the documentation it may be a good idea to use their standard for doc string formation to have access to their automatic markdown as it is described what do you think ,0
+7003,9292889746.0,IssuesEvent,2019-03-22 05:37:25,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,TiDB doesn't handle `signed + unsigned` properly ,type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+`select cast(1 as signed) + cast(9223372036854775807 as unsigned);`
+
+2. What did you expect to see?
+```
+mysql> select cast(1 as signed) + cast(9223372036854775807 as unsigned);
++-----------------------------------------------------------+
+| cast(1 as signed) + cast(9223372036854775807 as unsigned) |
++-----------------------------------------------------------+
+| 9223372036854775808 |
++-----------------------------------------------------------+
+```
+
+
+
+
+3. What did you see instead?
+```
+mysql> select cast(1 as signed) + cast(9223372036854775807 as unsigned);
+ERROR 1690 (22003): BIGINT UNSIGNED value is out of range in '(1 + 9223372036854775807)'
+```
+
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+mysql> select tidb_version();
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-231-g20463d6-dirty
+Git Commit Hash: 20463d6da90fdf12c0d9d18c15dc33a78334882d
+Git Branch: master
+UTC Build Time: 2019-03-20 03:32:11
+GoVersion: go version go1.12 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+",True,"TiDB doesn't handle `signed + unsigned` properly - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+`select cast(1 as signed) + cast(9223372036854775807 as unsigned);`
+
+2. What did you expect to see?
+```
+mysql> select cast(1 as signed) + cast(9223372036854775807 as unsigned);
++-----------------------------------------------------------+
+| cast(1 as signed) + cast(9223372036854775807 as unsigned) |
++-----------------------------------------------------------+
+| 9223372036854775808 |
++-----------------------------------------------------------+
+```
+
+
+
+
+3. What did you see instead?
+```
+mysql> select cast(1 as signed) + cast(9223372036854775807 as unsigned);
+ERROR 1690 (22003): BIGINT UNSIGNED value is out of range in '(1 + 9223372036854775807)'
+```
+
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+mysql> select tidb_version();
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-231-g20463d6-dirty
+Git Commit Hash: 20463d6da90fdf12c0d9d18c15dc33a78334882d
+Git Branch: master
+UTC Build Time: 2019-03-20 03:32:11
+GoVersion: go version go1.12 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+",1,tidb doesn t handle signed unsigned properly bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error select cast as signed cast as unsigned what did you expect to see mysql select cast as signed cast as unsigned cast as signed cast as unsigned what did you see instead mysql select cast as signed cast as unsigned error bigint unsigned value is out of range in what version of tidb are you using tidb server v or run select tidb version on tidb mysql select tidb version tidb version release version beta dirty git commit hash git branch master utc build time goversion go version linux race enabled false tikv min version alpha check table before drop false row in set sec ,1
+313656,26945078478.0,IssuesEvent,2023-02-08 07:17:42,cockroachdb/cockroach,https://api.github.com/repos/cockroachdb/cockroach,opened,pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test: TestLogic_cluster_settings failed,C-test-failure O-robot branch-master,"pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test.TestLogic_cluster_settings [failed](https://teamcity.cockroachdb.com/buildConfiguration/Cockroach_Nightlies_SqlLogicTestHighVModuleNightlyBazel/8626728?buildTab=log) with [artifacts](https://teamcity.cockroachdb.com/buildConfiguration/Cockroach_Nightlies_SqlLogicTestHighVModuleNightlyBazel/8626728?buildTab=artifacts#/) on master @ [ff67a4ba86d710db090ce700f229020365851183](https://github.com/cockroachdb/cockroach/commits/ff67a4ba86d710db090ce700f229020365851183):
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
```
-mysql> select tidb_version();
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v3.0.0-beta-231-g20463d6-dirty
-Git Commit Hash: 20463d6da90fdf12c0d9d18c15dc33a78334882d
-Git Branch: master
-UTC Build Time: 2019-03-20 02:03:04
-GoVersion: go version go1.12 linux/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false |
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-1 row in set (0.01 sec)
+[06:30:09] ALTER TENANT ALL RESET CLUSTER SETTING server.mem_profile.total_dump_size_limit;
+ logictestbase.go:512: statement/query skipped with reason: unsupported configuration fakedist-disk, statement/query only supports 3node-tenant-default-configs (no issue given)
+[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [0];
+[06:30:09] -- XFAIL;
+[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [1];
+[06:30:09] -- XFAIL;
+[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [1111];
+[06:30:09] -- XFAIL;
+[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [10];
+[06:30:09] -- OK;
+[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT ""tenant-10"";
+[06:30:09] -- OK;
+ logictestbase.go:512: statement/query skipped with reason: unsupported configuration fakedist-disk, statement/query only supports 3snode-tenant-default-config (no issue given)
+[06:30:09] SHOW CLUSTER SETTINGS FOR TENANT [0];
+[06:30:09] -- XFAIL;
+[06:30:09] SHOW CLUSTER SETTINGS FOR TENANT [1];
+[06:30:10] -- XFAIL;
+[06:30:10] SHOW CLUSTER SETTINGS FOR TENANT [1111];
+[06:30:10] -- XFAIL;
+[06:30:10] SELECT variable, type, origin FROM [SHOW CLUSTER SETTINGS FOR TENANT [10]]
+WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
+[06:30:10] -- OK;
+[06:30:10] SELECT variable, type, origin FROM [SHOW CLUSTER SETTINGS FOR TENANT ""tenant-10""]
+WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
+[06:30:10] -- OK;
+[06:30:10] SELECT variable, type, public, origin FROM [SHOW ALL CLUSTER SETTINGS FOR TENANT [10]]
+WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
+[06:30:10] -- OK;
+[06:30:10] SELECT variable, type, public, origin FROM [SHOW ALL CLUSTER SETTINGS FOR TENANT ""tenant-10""]
+WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
+[06:30:10] -- OK;
+[06:30:10] SHOW CLUSTER SETTING sql.defaults.distsql;;
+[06:30:10] -- FAIL
+ logic.go:2892:
+
+ /home/roach/.cache/bazel/_bazel_roach/c5a4e7d36696d9cd970af2045211a7df/sandbox/processwrapper-sandbox/3738/execroot/com_github_cockroachdb_cockroach/bazel-out/k8-fastbuild/bin/pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test_/fakedist-disk_test.runfiles/com_github_cockroachdb_cockroach/pkg/sql/logictest/testdata/logic_test/cluster_settings:331: SHOW CLUSTER SETTING sql.defaults.distsql;
+ expected:
+ NOTICE: using global default sql.defaults.distsql is not recommended
+ HINT: use the ``ALTER ROLE ... SET`` syntax to control session variable defaults at a finer-grained level. See: https://www.cockroachlabs.com/docs/v23.1/alter-role.html#set-default-session-variable-values-for-a-role
+
+ but found (query options: ""noticetrace"") :
+ NOTICE: using global default sql.defaults.distsql is not recommended
+ HINT: use the ``ALTER ROLE ... SET`` syntax to control session variable defaults at a finer-grained level. See: https://www.cockroachlabs.com/docs/dev/alter-role.html#set-default-session-variable-values-for-a-role
+[06:30:10] -- FAIL
+ logic.go:2151:
+ /home/roach/.cache/bazel/_bazel_roach/c5a4e7d36696d9cd970af2045211a7df/sandbox/processwrapper-sandbox/3738/execroot/com_github_cockroachdb_cockroach/bazel-out/k8-fastbuild/bin/pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test_/fakedist-disk_test.runfiles/com_github_cockroachdb_cockroach/pkg/sql/logictest/testdata/logic_test/cluster_settings:337: too many errors encountered, skipping the rest of the input
+[06:30:10] --- done: /home/roach/.cache/bazel/_bazel_roach/c5a4e7d36696d9cd970af2045211a7df/sandbox/processwrapper-sandbox/3738/execroot/com_github_cockroachdb_cockroach/bazel-out/k8-fastbuild/bin/pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test_/fakedist-disk_test.runfiles/com_github_cockroachdb_cockroach/pkg/sql/logictest/testdata/logic_test/cluster_settings with config fakedist-disk: 71 tests, 2 failures
+[06:30:10] --- total progress: 71 statements
+--- total: 71 tests, 2 failures
+ --- FAIL: TestLogic_cluster_settings/tenant-cluster-settings (0.55s)
```
+Help
+
-",True,"`SELECT 9223372036854775807 + 1;` is not compatible with MySQL - ## Bug Report
-
-Please answer these questions before submitting your issue. Thanks!
+See also: [How To Investigate a Go Test Failure \(internal\)](https://cockroachlabs.atlassian.net/l/c/HgfXfJgM)
+
+
+/cc @cockroachdb/sql-queries
+
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-`SELECT 9223372036854775807 + 1;`
+[This test on roachdash](https://roachdash.crdb.dev/?filter=status:open%20t:.*TestLogic_cluster_settings.*&sort=title+created&display=lastcommented+project) | [Improve this report!](https://github.com/cockroachdb/cockroach/tree/master/pkg/cmd/internal/issues)
+
+",1.0,"pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test: TestLogic_cluster_settings failed - pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test.TestLogic_cluster_settings [failed](https://teamcity.cockroachdb.com/buildConfiguration/Cockroach_Nightlies_SqlLogicTestHighVModuleNightlyBazel/8626728?buildTab=log) with [artifacts](https://teamcity.cockroachdb.com/buildConfiguration/Cockroach_Nightlies_SqlLogicTestHighVModuleNightlyBazel/8626728?buildTab=artifacts#/) on master @ [ff67a4ba86d710db090ce700f229020365851183](https://github.com/cockroachdb/cockroach/commits/ff67a4ba86d710db090ce700f229020365851183):
-2. What did you expect to see?
-In Mysql 8.0.15
-```
-mysql> SELECT 9223372036854775807+1;
-ERROR 1690 (22003): BIGINT value is out of range in '(9223372036854775807 + 1)'
-```
-See also https://dev.mysql.com/doc/refman/8.0/en/out-of-range-and-overflow.html
-3. What did you see instead?
```
-mysql> SELECT 9223372036854775807+1;
-+-----------------------+
-| 9223372036854775807+1 |
-+-----------------------+
-| 9223372036854775808 |
-+-----------------------+
-1 row in set (0.00 sec)
+[06:30:09] ALTER TENANT ALL RESET CLUSTER SETTING server.mem_profile.total_dump_size_limit;
+ logictestbase.go:512: statement/query skipped with reason: unsupported configuration fakedist-disk, statement/query only supports 3node-tenant-default-configs (no issue given)
+[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [0];
+[06:30:09] -- XFAIL;
+[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [1];
+[06:30:09] -- XFAIL;
+[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [1111];
+[06:30:09] -- XFAIL;
+[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [10];
+[06:30:09] -- OK;
+[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT ""tenant-10"";
+[06:30:09] -- OK;
+ logictestbase.go:512: statement/query skipped with reason: unsupported configuration fakedist-disk, statement/query only supports 3snode-tenant-default-config (no issue given)
+[06:30:09] SHOW CLUSTER SETTINGS FOR TENANT [0];
+[06:30:09] -- XFAIL;
+[06:30:09] SHOW CLUSTER SETTINGS FOR TENANT [1];
+[06:30:10] -- XFAIL;
+[06:30:10] SHOW CLUSTER SETTINGS FOR TENANT [1111];
+[06:30:10] -- XFAIL;
+[06:30:10] SELECT variable, type, origin FROM [SHOW CLUSTER SETTINGS FOR TENANT [10]]
+WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
+[06:30:10] -- OK;
+[06:30:10] SELECT variable, type, origin FROM [SHOW CLUSTER SETTINGS FOR TENANT ""tenant-10""]
+WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
+[06:30:10] -- OK;
+[06:30:10] SELECT variable, type, public, origin FROM [SHOW ALL CLUSTER SETTINGS FOR TENANT [10]]
+WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
+[06:30:10] -- OK;
+[06:30:10] SELECT variable, type, public, origin FROM [SHOW ALL CLUSTER SETTINGS FOR TENANT ""tenant-10""]
+WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
+[06:30:10] -- OK;
+[06:30:10] SHOW CLUSTER SETTING sql.defaults.distsql;;
+[06:30:10] -- FAIL
+ logic.go:2892:
+
+ /home/roach/.cache/bazel/_bazel_roach/c5a4e7d36696d9cd970af2045211a7df/sandbox/processwrapper-sandbox/3738/execroot/com_github_cockroachdb_cockroach/bazel-out/k8-fastbuild/bin/pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test_/fakedist-disk_test.runfiles/com_github_cockroachdb_cockroach/pkg/sql/logictest/testdata/logic_test/cluster_settings:331: SHOW CLUSTER SETTING sql.defaults.distsql;
+ expected:
+ NOTICE: using global default sql.defaults.distsql is not recommended
+ HINT: use the ``ALTER ROLE ... SET`` syntax to control session variable defaults at a finer-grained level. See: https://www.cockroachlabs.com/docs/v23.1/alter-role.html#set-default-session-variable-values-for-a-role
+
+ but found (query options: ""noticetrace"") :
+ NOTICE: using global default sql.defaults.distsql is not recommended
+ HINT: use the ``ALTER ROLE ... SET`` syntax to control session variable defaults at a finer-grained level. See: https://www.cockroachlabs.com/docs/dev/alter-role.html#set-default-session-variable-values-for-a-role
+[06:30:10] -- FAIL
+ logic.go:2151:
+ /home/roach/.cache/bazel/_bazel_roach/c5a4e7d36696d9cd970af2045211a7df/sandbox/processwrapper-sandbox/3738/execroot/com_github_cockroachdb_cockroach/bazel-out/k8-fastbuild/bin/pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test_/fakedist-disk_test.runfiles/com_github_cockroachdb_cockroach/pkg/sql/logictest/testdata/logic_test/cluster_settings:337: too many errors encountered, skipping the rest of the input
+[06:30:10] --- done: /home/roach/.cache/bazel/_bazel_roach/c5a4e7d36696d9cd970af2045211a7df/sandbox/processwrapper-sandbox/3738/execroot/com_github_cockroachdb_cockroach/bazel-out/k8-fastbuild/bin/pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test_/fakedist-disk_test.runfiles/com_github_cockroachdb_cockroach/pkg/sql/logictest/testdata/logic_test/cluster_settings with config fakedist-disk: 71 tests, 2 failures
+[06:30:10] --- total progress: 71 statements
+--- total: 71 tests, 2 failures
+ --- FAIL: TestLogic_cluster_settings/tenant-cluster-settings (0.55s)
```
+Help
+
+See also: [How To Investigate a Go Test Failure \(internal\)](https://cockroachlabs.atlassian.net/l/c/HgfXfJgM)
+
+
+/cc @cockroachdb/sql-queries
+
+[This test on roachdash](https://roachdash.crdb.dev/?filter=status:open%20t:.*TestLogic_cluster_settings.*&sort=title+created&display=lastcommented+project) | [Improve this report!](https://github.com/cockroachdb/cockroach/tree/master/pkg/cmd/internal/issues)
+
+",0,pkg sql logictest tests fakedist disk fakedist disk test testlogic cluster settings failed pkg sql logictest tests fakedist disk fakedist disk test testlogic cluster settings with on master alter tenant all reset cluster setting server mem profile total dump size limit logictestbase go statement query skipped with reason unsupported configuration fakedist disk statement query only supports tenant default configs no issue given show cluster setting server mem profile total dump size limit for tenant xfail show cluster setting server mem profile total dump size limit for tenant xfail show cluster setting server mem profile total dump size limit for tenant xfail show cluster setting server mem profile total dump size limit for tenant ok show cluster setting server mem profile total dump size limit for tenant tenant ok logictestbase go statement query skipped with reason unsupported configuration fakedist disk statement query only supports tenant default config no issue given show cluster settings for tenant xfail show cluster settings for tenant xfail show cluster settings for tenant xfail select variable type origin from where variable in jobs scheduler enabled jobs retention time order by ok select variable type origin from where variable in jobs scheduler enabled jobs retention time order by ok select variable type public origin from where variable in jobs scheduler enabled jobs retention time order by ok select variable type public origin from where variable in jobs scheduler enabled jobs retention time order by ok show cluster setting sql defaults distsql fail logic go home roach cache bazel bazel roach sandbox processwrapper sandbox execroot com github cockroachdb cockroach bazel out fastbuild bin pkg sql logictest tests fakedist disk fakedist disk test fakedist disk test runfiles com github cockroachdb cockroach pkg sql logictest testdata logic test cluster settings show cluster setting sql defaults distsql expected notice using global default sql defaults distsql is not recommended hint use the alter role set syntax to control session variable defaults at a finer grained level see but found query options noticetrace notice using global default sql defaults distsql is not recommended hint use the alter role set syntax to control session variable defaults at a finer grained level see fail logic go home roach cache bazel bazel roach sandbox processwrapper sandbox execroot com github cockroachdb cockroach bazel out fastbuild bin pkg sql logictest tests fakedist disk fakedist disk test fakedist disk test runfiles com github cockroachdb cockroach pkg sql logictest testdata logic test cluster settings too many errors encountered skipping the rest of the input done home roach cache bazel bazel roach sandbox processwrapper sandbox execroot com github cockroachdb cockroach bazel out fastbuild bin pkg sql logictest tests fakedist disk fakedist disk test fakedist disk test runfiles com github cockroachdb cockroach pkg sql logictest testdata logic test cluster settings with config fakedist disk tests failures total progress statements total tests failures fail testlogic cluster settings tenant cluster settings help see also cc cockroachdb sql queries ,0
+94370,8486379988.0,IssuesEvent,2018-10-26 10:41:02,devdaydresden/devday_website,https://api.github.com/repos/devdaydresden/devday_website,opened,Improve test dada,django tests,"**Describe the solution you'd like**
+We need additional test data entries:
+- site.domain should use the appropriate value for the environment (localhost:8000, devday-test.mms-at-work.de:8080) instead of devday.de
+- the sponsoring page should link to the sponsoring app
+- a basic set of sponsoring packages should be added for the current event
+- die Seite sponsoring sollte auf die Sponsoring-App verlinken
+- es sollte ein Grunddatenbestand für Sponsoringpakete für das aktuelle Event da sein, damit man den nicht manuell pflegen muss
+",1.0,"Improve test dada - **Describe the solution you'd like**
+We need additional test data entries:
+- site.domain should use the appropriate value for the environment (localhost:8000, devday-test.mms-at-work.de:8080) instead of devday.de
+- the sponsoring page should link to the sponsoring app
+- a basic set of sponsoring packages should be added for the current event
+- die Seite sponsoring sollte auf die Sponsoring-App verlinken
+- es sollte ein Grunddatenbestand für Sponsoringpakete für das aktuelle Event da sein, damit man den nicht manuell pflegen muss
+",0,improve test dada describe the solution you d like we need additional test data entries site domain should use the appropriate value for the environment localhost devday test mms at work de instead of devday de the sponsoring page should link to the sponsoring app a basic set of sponsoring packages should be added for the current event die seite sponsoring sollte auf die sponsoring app verlinken es sollte ein grunddatenbestand für sponsoringpakete für das aktuelle event da sein damit man den nicht manuell pflegen muss ,0
+245472,26549233562.0,IssuesEvent,2023-01-20 05:24:00,nidhi7598/linux-3.0.35_CVE-2022-45934,https://api.github.com/repos/nidhi7598/linux-3.0.35_CVE-2022-45934,opened,CVE-2014-2672 (Medium) detected in linux-stable-rtv3.8.6,security vulnerability,"## CVE-2014-2672 - Medium Severity Vulnerability
+ Vulnerable Library - linux-stable-rtv3.8.6
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-```
-mysql> select tidb_version();
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v3.0.0-beta-231-g20463d6-dirty
-Git Commit Hash: 20463d6da90fdf12c0d9d18c15dc33a78334882d
-Git Branch: master
-UTC Build Time: 2019-03-20 02:03:04
-GoVersion: go version go1.12 linux/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false |
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-1 row in set (0.01 sec)
-```
+
-",1, select is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error select what did you expect to see in mysql mysql select error bigint value is out of range in see also what did you see instead mysql select row in set sec what version of tidb are you using tidb server v or run select tidb version on tidb mysql select tidb version tidb version release version beta dirty git commit hash git branch master utc build time goversion go version linux race enabled false tikv min version alpha check table before drop false row in set sec ,1
-6587,8854545270.0,IssuesEvent,2019-01-09 01:51:28,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,tidb-server options -socket and -host are incompatible,type/compatibility,"## Bug Report
+
Found in base branch: master
+
+
+ Vulnerable Source Files (1)
+
+
-Please answer these questions before submitting your issue. Thanks!
+ /drivers/net/wireless/ath/ath9k/xmit.c
+
+
+
+
+
+
+ Vulnerability Details
+
+
+Race condition in the ath_tx_aggr_sleep function in drivers/net/wireless/ath/ath9k/xmit.c in the Linux kernel before 3.13.7 allows remote attackers to cause a denial of service (system crash) via a large amount of network traffic that triggers certain list deletions.
-1. What did you do?
+
-I would expect it to listen on both. This is important because of MySQL's special handling of localhost:
-- For the libmysql derived clients it will switch to using unix socket.
-- For other drivers like JDBC it will only ever use tcp.
+
+
+
-So it is useful to be able to have the server listen on both for a fully local install.
+***
+Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",True,"CVE-2014-2672 (Medium) detected in linux-stable-rtv3.8.6 - ## CVE-2014-2672 - Medium Severity Vulnerability
+ Vulnerable Library - linux-stable-rtv3.8.6
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+ /drivers/net/wireless/ath/ath9k/xmit.c
+
+
+
+
+
+
+ Vulnerability Details
+
+
+Race condition in the ath_tx_aggr_sleep function in drivers/net/wireless/ath/ath9k/xmit.c in the Linux kernel before 3.13.7 allows remote attackers to cause a denial of service (system crash) via a large amount of network traffic that triggers certain list deletions.
-```
-mysql> select tidb_version()\G
-*************************** 1. row ***************************
-tidb_version(): Release Version: v2.1.0-beta-644-g89cd59d21
-Git Commit Hash: 89cd59d217637f5e79fdc81681c98531c668e688
-Git Branch: newmaster
-UTC Build Time: 2018-11-26 04:47:59
-GoVersion: go version go1.11 linux/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false
-1 row in set (0.00 sec)
-```",True,"tidb-server options -socket and -host are incompatible - ## Bug Report
-
-Please answer these questions before submitting your issue. Thanks!
-
-1. What did you do?
+
-I would expect it to listen on both. This is important because of MySQL's special handling of localhost:
-- For the libmysql derived clients it will switch to using unix socket.
-- For other drivers like JDBC it will only ever use tcp.
-
-So it is useful to be able to have the server listen on both for a fully local install.
+
+
+
-3. What did you see instead?
+***
+Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",0,cve medium detected in linux stable cve medium severity vulnerability vulnerable library linux stable julia cartwright s fork of linux stable rt git library home page a href found in head commit a href found in base branch master vulnerable source files drivers net wireless ath xmit c vulnerability details race condition in the ath tx aggr sleep function in drivers net wireless ath xmit c in the linux kernel before allows remote attackers to cause a denial of service system crash via a large amount of network traffic that triggers certain list deletions publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with mend ,0
+298070,9195554656.0,IssuesEvent,2019-03-07 02:55:34,kubeflow/katib,https://api.github.com/repos/kubeflow/katib,closed,StudyJob controller shouldn't crash if PyTorch (or other job operators not installed),area/katib kind/bug priority/p1,"See: kubeflow/kubeflow#2212
+
+User reports that the StudyJob controller crashes if pytorch operator isn't installed on the cluster.
+
+Logs for StudyJobController
+
+```
+$ kubectl logs -n kubeflow studyjob-controller-7d77f959-pjfzf
+2019/01/06 22:43:34 Registering Components.
+2019/01/06 22:43:34 controller.AddToManager(mgr)
+2019/01/06 22:43:34 no matches for kind ""PyTorchJob"" in version ""kubeflow.org/v1beta1""
+```
+
+This seems like a bug. If a particular job controller isn't installed I would still expect katib and StudyJobs to work with other types of job controllers.",1.0,"StudyJob controller shouldn't crash if PyTorch (or other job operators not installed) - See: kubeflow/kubeflow#2212
+
+User reports that the StudyJob controller crashes if pytorch operator isn't installed on the cluster.
+
+Logs for StudyJobController
+
+```
+$ kubectl logs -n kubeflow studyjob-controller-7d77f959-pjfzf
+2019/01/06 22:43:34 Registering Components.
+2019/01/06 22:43:34 controller.AddToManager(mgr)
+2019/01/06 22:43:34 no matches for kind ""PyTorchJob"" in version ""kubeflow.org/v1beta1""
+```
+
+This seems like a bug. If a particular job controller isn't installed I would still expect katib and StudyJobs to work with other types of job controllers.",0,studyjob controller shouldn t crash if pytorch or other job operators not installed see kubeflow kubeflow user reports that the studyjob controller crashes if pytorch operator isn t installed on the cluster logs for studyjobcontroller kubectl logs n kubeflow studyjob controller pjfzf registering components controller addtomanager mgr no matches for kind pytorchjob in version kubeflow org this seems like a bug if a particular job controller isn t installed i would still expect katib and studyjobs to work with other types of job controllers ,0
+6614,8881908724.0,IssuesEvent,2019-01-14 11:34:23,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,sql_mode ALLOW_INVALID_DATES is not supported,type/compatibility,"## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+Relates to #2738 - currently `ALLOW_INVALID_DATES` is not supported. It is not commonly used, but could be useful for compatibility.
+
+**Describe the feature you'd like:**
+```
+# testcase
+CREATE TABLE d1 (d DATE);
+SET sql_mode='STRICT_TRANS_TABLES,ALLOW_INVALID_DATES';
+INSERT INTO d1 VALUES ('2010-00-01');
+```
+Passes in MySQL, produces this in TiDB:
+```
+MySQL [test]> SET sql_mode='STRICT_TRANS_TABLES,ALLOW_INVALID_DATES';
+ERROR 1105 (HY000): ERROR 1231 (42000): Variable 'sql_mode' can't be set to the value of 'ALLOW_INVALID_DATES'
+MySQL [test]> INSERT INTO d1 VALUES ('2010-00-01');
+ERROR 1292 (22007): Incorrect datetime value: '2010-00-01'
+```
+
+**Describe alternatives you've considered:**
+Possible to document as unsupported.
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+Improves compatibility with MySQL.",True,"sql_mode ALLOW_INVALID_DATES is not supported - ## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+Relates to #2738 - currently `ALLOW_INVALID_DATES` is not supported. It is not commonly used, but could be useful for compatibility.
+
+**Describe the feature you'd like:**
+```
+# testcase
+CREATE TABLE d1 (d DATE);
+SET sql_mode='STRICT_TRANS_TABLES,ALLOW_INVALID_DATES';
+INSERT INTO d1 VALUES ('2010-00-01');
+```
+Passes in MySQL, produces this in TiDB:
+```
+MySQL [test]> SET sql_mode='STRICT_TRANS_TABLES,ALLOW_INVALID_DATES';
+ERROR 1105 (HY000): ERROR 1231 (42000): Variable 'sql_mode' can't be set to the value of 'ALLOW_INVALID_DATES'
+MySQL [test]> INSERT INTO d1 VALUES ('2010-00-01');
+ERROR 1292 (22007): Incorrect datetime value: '2010-00-01'
+```
+
+**Describe alternatives you've considered:**
+Possible to document as unsupported.
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+Improves compatibility with MySQL.",1,sql mode allow invalid dates is not supported feature request is your feature request related to a problem please describe relates to currently allow invalid dates is not supported it is not commonly used but could be useful for compatibility describe the feature you d like testcase create table d date set sql mode strict trans tables allow invalid dates insert into values passes in mysql produces this in tidb mysql set sql mode strict trans tables allow invalid dates error error variable sql mode can t be set to the value of allow invalid dates mysql insert into values error incorrect datetime value describe alternatives you ve considered possible to document as unsupported teachability documentation adoption migration strategy improves compatibility with mysql ,1
+20584,30582031316.0,IssuesEvent,2023-07-21 10:24:46,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,"Default value for TEXT, BLOB or JSON columns",type/bug type/compatibility sig/sql-infra compatibility-mysql8,"## Bug Report
+
+TiDB doesn't allow a default value for TEXT, BLOB or JSON columns.
+
+### 1. Minimal reproduce step (Required)
+
+```sql
+CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT 'foo');
+CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT ('foo'));
+SHOW CREATE TABLE t1\G
+INSERT INTO t1(id) VALUES(1);
+TABLE t1;
+```
+
+### 2. What did you expect to see? (Required)
+
+With MySQL 8.1.0:
+```
+sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT 'foo');
+ERROR: 1101 (42000): BLOB, TEXT, GEOMETRY or JSON column 'c1' can't have a default value
+
+sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT ('foo'));
+Query OK, 0 rows affected (0.0586 sec)
+
+sql> SHOW CREATE TABLE t1\G
+*************************** 1. row ***************************
+ Table: t1
+Create Table: CREATE TABLE `t1` (
+ `id` int NOT NULL,
+ `c1` text COLLATE utf8mb4_general_ci DEFAULT (_utf8mb4'foo'),
+ PRIMARY KEY (`id`)
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_general_ci
+1 row in set (0.0184 sec)
+
+sql> INSERT INTO t1(id) VALUES(1);
+Query OK, 1 row affected (0.0076 sec)
+
+sql> TABLE t1;
++----+-----+
+| id | c1 |
++----+-----+
+| 1 | foo |
++----+-----+
+1 row in set (0.0009 sec)
+```
+### 3. What did you see instead (Required)
+
+```
+sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT 'foo');
+ERROR: 1101 (42000): BLOB/TEXT/JSON column 'c1' can't have a default value
+
+sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT ('foo'));
+ERROR: 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your TiDB version for the right syntax to use line 1 column 59 near ""'foo'))""
+
+...
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+
+```
+Release Version: v7.2.0
+Edition: Community
+Git Commit Hash: 9fd5f4a8e4f273a60fbe7d3848f85a1be8f0600b
+Git Branch: heads/refs/tags/v7.2.0
+UTC Build Time: 2023-06-27 15:04:42
+GoVersion: go1.20.5
+Race Enabled: false
+Check Table Before Drop: false
+Store: tikv
+```",True,"Default value for TEXT, BLOB or JSON columns - ## Bug Report
+
+TiDB doesn't allow a default value for TEXT, BLOB or JSON columns.
+
+### 1. Minimal reproduce step (Required)
+
+```sql
+CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT 'foo');
+CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT ('foo'));
+SHOW CREATE TABLE t1\G
+INSERT INTO t1(id) VALUES(1);
+TABLE t1;
+```
+
+### 2. What did you expect to see? (Required)
+
+With MySQL 8.1.0:
+```
+sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT 'foo');
+ERROR: 1101 (42000): BLOB, TEXT, GEOMETRY or JSON column 'c1' can't have a default value
+
+sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT ('foo'));
+Query OK, 0 rows affected (0.0586 sec)
+
+sql> SHOW CREATE TABLE t1\G
+*************************** 1. row ***************************
+ Table: t1
+Create Table: CREATE TABLE `t1` (
+ `id` int NOT NULL,
+ `c1` text COLLATE utf8mb4_general_ci DEFAULT (_utf8mb4'foo'),
+ PRIMARY KEY (`id`)
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_general_ci
+1 row in set (0.0184 sec)
+
+sql> INSERT INTO t1(id) VALUES(1);
+Query OK, 1 row affected (0.0076 sec)
+
+sql> TABLE t1;
++----+-----+
+| id | c1 |
++----+-----+
+| 1 | foo |
++----+-----+
+1 row in set (0.0009 sec)
+```
+### 3. What did you see instead (Required)
+
+```
+sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT 'foo');
+ERROR: 1101 (42000): BLOB/TEXT/JSON column 'c1' can't have a default value
+
+sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT ('foo'));
+ERROR: 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your TiDB version for the right syntax to use line 1 column 59 near ""'foo'))""
+
+...
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+
+```
+Release Version: v7.2.0
+Edition: Community
+Git Commit Hash: 9fd5f4a8e4f273a60fbe7d3848f85a1be8f0600b
+Git Branch: heads/refs/tags/v7.2.0
+UTC Build Time: 2023-06-27 15:04:42
+GoVersion: go1.20.5
+Race Enabled: false
+Check Table Before Drop: false
+Store: tikv
+```",1,default value for text blob or json columns bug report tidb doesn t allow a default value for text blob or json columns minimal reproduce step required sql create table id int primary key text default foo create table id int primary key text default foo show create table g insert into id values table what did you expect to see required with mysql sql create table id int primary key text default foo error blob text geometry or json column can t have a default value sql create table id int primary key text default foo query ok rows affected sec sql show create table g row table create table create table id int not null text collate general ci default foo primary key id engine innodb default charset collate general ci row in set sec sql insert into id values query ok row affected sec sql table id foo row in set sec what did you see instead required sql create table id int primary key text default foo error blob text json column can t have a default value sql create table id int primary key text default foo error you have an error in your sql syntax check the manual that corresponds to your tidb version for the right syntax to use line column near foo what is your tidb version required release version edition community git commit hash git branch heads refs tags utc build time goversion race enabled false check table before drop false store tikv ,1
+8816,10764654481.0,IssuesEvent,2019-11-01 08:56:17,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Support use `on duplicate key update b=default` in generated columns,type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+mysql> create table t1 (a int unique,
+ -> b int generated always as (-a) virtual,
+ -> c int generated always as (-a) stored);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> insert into t1 values (1,default,default);
+Query OK, 1 row affected (0.01 sec)
+
+mysql> insert into t1 values (1,default,default)
+ -> on duplicate key update a=2, b=default;
+
+```
+2. What did you expect to see?
+
+```
+ERROR 3105 (HY000): The value specified for generated column 'b' in table 't1' is not allowed.
+```
+
+3. What did you see instead?
+
+```
+Query OK, 1 row affected (0.01 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+Release Version: v4.0.0-alpha-693-gada724a2a
+```
+",True,"Support use `on duplicate key update b=default` in generated columns - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+mysql> create table t1 (a int unique,
+ -> b int generated always as (-a) virtual,
+ -> c int generated always as (-a) stored);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> insert into t1 values (1,default,default);
+Query OK, 1 row affected (0.01 sec)
+
+mysql> insert into t1 values (1,default,default)
+ -> on duplicate key update a=2, b=default;
+
+```
+2. What did you expect to see?
+
+```
+ERROR 3105 (HY000): The value specified for generated column 'b' in table 't1' is not allowed.
+```
+
+3. What did you see instead?
+
+```
+Query OK, 1 row affected (0.01 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+Release Version: v4.0.0-alpha-693-gada724a2a
+```
+",1,support use on duplicate key update b default in generated columns bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error mysql create table a int unique b int generated always as a virtual c int generated always as a stored query ok rows affected sec mysql insert into values default default query ok row affected sec mysql insert into values default default on duplicate key update a b default what did you expect to see error the value specified for generated column b in table is not allowed what did you see instead query ok row affected sec what version of tidb are you using tidb server v or run select tidb version on tidb release version alpha ,1
+18564,25821598639.0,IssuesEvent,2022-12-12 09:58:53,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,force index behaviour not same as mysql,type/compatibility good first issue sig/planner compatibility-mysql8,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+# ----- step 1: create table
+CREATE TABLE `projects_send` (
+ `entry` bigint(20) unsigned NOT NULL AUTO_INCREMENT COMMENT 'id',
+ `projectid` int(8) NOT NULL COMMENT 'ID',
+ `status` tinyint(1) unsigned NOT NULL DEFAULT '0' COMMENT '状态(0:not send;1:sent;2:back)',
+ `sendtime` datetime NOT NULL COMMENT 'senttime',
+ PRIMARY KEY (`entry`) USING BTREE,
+ KEY `idx_sendtime_status_projectid` (`sendtime`,`status`,`projectid`) USING BTREE,
+ KEY `idx_sendtime_status` (`sendtime`,`status`) USING BTREE
+) ENGINE=InnoDB AUTO_INCREMENT=1 DEFAULT CHARSET=utf8;
+
+# ----- step 2: EXPLAIN on tidb & mysql
+
+#1. tidb & mysql same
+mysql>
+EXPLAIN select * from projects_send force index(idx_sendtime) where sendtime > ""2020-01-01"";
+Key 'idx_sendtime' doesnt exist in table 'projects_send'
+
+#2. tidb & mysql same
+mysql>
+EXPLAIN select * from projects_send force index(idx_sendtime_status) where sendtime > ""2020-01-01"";
++----+-------------+---------------+-------+---------------------+---------------------+---------+------+------+--------------------------+
+| id | select_type | table | type | possible_keys | key | key_len | ref | rows | Extra |
++----+-------------+---------------+-------+---------------------+---------------------+---------+------+------+--------------------------+
+| 1 | SIMPLE | projects_send | index | idx_sendtime_status | idx_sendtime_status | 10 | NULL | 1 | Using where; Using index |
++----+-------------+---------------+-------+---------------------+---------------------+---------+------+------+--------------------------+
+
+#3. tidb & mysql not same: tidb show index not exist
+mysql>
+EXPLAIN select * from projects_send force index(idx_sendtime_status_pro) where sendtime > ""2020-01-01"";
++----+-------------+---------------+-------+-------------------------------+-------------------------------+---------+------+------+--------------------------+
+| id | select_type | table | type | possible_keys | key | key_len | ref | rows | Extra |
++----+-------------+---------------+-------+-------------------------------+-------------------------------+---------+------+------+--------------------------+
+| 1 | SIMPLE | projects_send | index | idx_sendtime_status_projectid | idx_sendtime_status_projectid | 10 | NULL | 1 | Using where; Using index |
++----+-------------+---------------+-------+-------------------------------+-------------------------------+---------+------+------+--------------------------+
+1 row in set (0.14 sec)
+
+#on mysql the only one same prefix index idx_sendtime_status_pro can be used, but on tidb only the same name index can be use
+```
+2. What did you expect to see?
+
+
+
+3. What did you see instead?
+
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+Release Version: v3.0.8
+Git Commit Hash: 8f13cf1449bd8903ff465a4f12ed89ecbac858a4
+Git Branch: HEAD
+UTC Build Time: 2019-12-31 11:14:59
+GoVersion: go version go1.13 linux/amd64
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+",True,"force index behaviour not same as mysql - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+# ----- step 1: create table
+CREATE TABLE `projects_send` (
+ `entry` bigint(20) unsigned NOT NULL AUTO_INCREMENT COMMENT 'id',
+ `projectid` int(8) NOT NULL COMMENT 'ID',
+ `status` tinyint(1) unsigned NOT NULL DEFAULT '0' COMMENT '状态(0:not send;1:sent;2:back)',
+ `sendtime` datetime NOT NULL COMMENT 'senttime',
+ PRIMARY KEY (`entry`) USING BTREE,
+ KEY `idx_sendtime_status_projectid` (`sendtime`,`status`,`projectid`) USING BTREE,
+ KEY `idx_sendtime_status` (`sendtime`,`status`) USING BTREE
+) ENGINE=InnoDB AUTO_INCREMENT=1 DEFAULT CHARSET=utf8;
+
+# ----- step 2: EXPLAIN on tidb & mysql
+
+#1. tidb & mysql same
+mysql>
+EXPLAIN select * from projects_send force index(idx_sendtime) where sendtime > ""2020-01-01"";
+Key 'idx_sendtime' doesnt exist in table 'projects_send'
+
+#2. tidb & mysql same
+mysql>
+EXPLAIN select * from projects_send force index(idx_sendtime_status) where sendtime > ""2020-01-01"";
++----+-------------+---------------+-------+---------------------+---------------------+---------+------+------+--------------------------+
+| id | select_type | table | type | possible_keys | key | key_len | ref | rows | Extra |
++----+-------------+---------------+-------+---------------------+---------------------+---------+------+------+--------------------------+
+| 1 | SIMPLE | projects_send | index | idx_sendtime_status | idx_sendtime_status | 10 | NULL | 1 | Using where; Using index |
++----+-------------+---------------+-------+---------------------+---------------------+---------+------+------+--------------------------+
+
+#3. tidb & mysql not same: tidb show index not exist
+mysql>
+EXPLAIN select * from projects_send force index(idx_sendtime_status_pro) where sendtime > ""2020-01-01"";
++----+-------------+---------------+-------+-------------------------------+-------------------------------+---------+------+------+--------------------------+
+| id | select_type | table | type | possible_keys | key | key_len | ref | rows | Extra |
++----+-------------+---------------+-------+-------------------------------+-------------------------------+---------+------+------+--------------------------+
+| 1 | SIMPLE | projects_send | index | idx_sendtime_status_projectid | idx_sendtime_status_projectid | 10 | NULL | 1 | Using where; Using index |
++----+-------------+---------------+-------+-------------------------------+-------------------------------+---------+------+------+--------------------------+
+1 row in set (0.14 sec)
+
+#on mysql the only one same prefix index idx_sendtime_status_pro can be used, but on tidb only the same name index can be use
+```
+2. What did you expect to see?
+
+
+
+3. What did you see instead?
+
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+Release Version: v3.0.8
+Git Commit Hash: 8f13cf1449bd8903ff465a4f12ed89ecbac858a4
+Git Branch: HEAD
+UTC Build Time: 2019-12-31 11:14:59
+GoVersion: go version go1.13 linux/amd64
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+",1,force index behaviour not same as mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error step create table create table projects send entry bigint unsigned not null auto increment comment id projectid int not null comment id status tinyint unsigned not null default comment 状态 not send sent back sendtime datetime not null comment senttime primary key entry using btree key idx sendtime status projectid sendtime status projectid using btree key idx sendtime status sendtime status using btree engine innodb auto increment default charset step explain on tidb mysql tidb mysql same mysql explain select from projects send force index idx sendtime where sendtime key idx sendtime doesnt exist in table projects send tidb mysql same mysql explain select from projects send force index idx sendtime status where sendtime id select type table type possible keys key key len ref rows extra simple projects send index idx sendtime status idx sendtime status null using where using index tidb mysql not same tidb show index not exist mysql explain select from projects send force index idx sendtime status pro where sendtime id select type table type possible keys key key len ref rows extra simple projects send index idx sendtime status projectid idx sendtime status projectid null using where using index row in set sec on mysql the only one same prefix index idx sendtime status pro can be used but on tidb only the same name index can be use what did you expect to see what did you see instead what version of tidb are you using tidb server v or run select tidb version on tidb release version git commit hash git branch head utc build time goversion go version linux race enabled false tikv min version check table before drop false ,1
+11624,13671944268.0,IssuesEvent,2020-09-29 07:48:08,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,_utf8 not supported,component/parser type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+select left(_utf8 0xD0B0D0B1D0B2,1)
+```
+
+2. What did you expect to see?
+
+```
+mysql> select left(_utf8 0xD0B0D0B1D0B2,1);
++------------------------------+
+| left(_utf8 0xD0B0D0B1D0B2,1) |
++------------------------------+
+| а |
++------------------------------+
+1 row in set (0.01 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> select left(_utf8 0xD0B0D0B1D0B2,1);
+ERROR 1105 (HY000): line 0 column 32 near "",1)"" (total length 35)
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"_utf8 not supported - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+select left(_utf8 0xD0B0D0B1D0B2,1)
+```
+
+2. What did you expect to see?
+
+```
+mysql> select left(_utf8 0xD0B0D0B1D0B2,1);
++------------------------------+
+| left(_utf8 0xD0B0D0B1D0B2,1) |
++------------------------------+
+| а |
++------------------------------+
+1 row in set (0.01 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> select left(_utf8 0xD0B0D0B1D0B2,1);
+ERROR 1105 (HY000): line 0 column 32 near "",1)"" (total length 35)
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1, not supported please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql select left what did you expect to see mysql select left left а row in set sec what did you see instead mysql select left error line column near total length what version of tidb are you using tidb server v ,1
+13155,15496099739.0,IssuesEvent,2021-03-11 02:03:37,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,reopened,Test compatibility using DataGrip,status/help-wanted type/compatibility,"DataGrip is a Database management systems that support many databases, including MySQL. See https://www.jetbrains.com/datagrip/
+",True,"Test compatibility using DataGrip - DataGrip is a Database management systems that support many databases, including MySQL. See https://www.jetbrains.com/datagrip/
+",1,test compatibility using datagrip datagrip is a database management systems that support many databases including mysql see ,1
+5495,7937199932.0,IssuesEvent,2018-07-09 12:06:28,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,"Intellij IDEA database plugin return an error ""Unknown column 'generation_expression' in 'field list'""",help wanted type/compatibility,"Error encountered when performing Introspect schema xlqy: Unknown column 'generation_expression' in 'field list'.
+Unknown column 'generation_expression' in 'field list'",True,"Intellij IDEA database plugin return an error ""Unknown column 'generation_expression' in 'field list'"" - Error encountered when performing Introspect schema xlqy: Unknown column 'generation_expression' in 'field list'.
+Unknown column 'generation_expression' in 'field list'",1,intellij idea database plugin return an error unknown column generation expression in field list error encountered when performing introspect schema xlqy unknown column generation expression in field list unknown column generation expression in field list ,1
+12085,14247181455.0,IssuesEvent,2020-11-19 11:04:55,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Comparison result is incorrect between year column and int constant,challenge-program component/executor picked severity/critical sig/execution type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+
+
+``` mysql
+create table t2 (a year(4));
+insert into t2 values(69);
+select * from t2 where a <= 69;
+```
+
+### 2. What did you expect to see? (Required)
+
+In mysql 8.0
+
+``` mysql
+mysql> select * from t2 where a <= 69;
++------+
+| a |
++------+
+| 2069 |
++------+
+1 row in set (0.00 sec)
+```
+
+### 3. What did you see instead (Required)
+
+``` mysql
+mysql> select * from t2 where a <= 69;
+Empty set (0.00 sec)
+
+mysql> explain select * from t2 where a <= 69;
++-------------------------+---------+-----------+---------------+--------------------------------+
+| id | estRows | task | access object | operator info |
++-------------------------+---------+-----------+---------------+--------------------------------+
+| TableReader_7 | 1.00 | root | | data:Selection_6 |
+| └─Selection_6 | 1.00 | cop[tikv] | | le(test.t2.a, 69) |
+| └─TableFullScan_5 | 3.00 | cop[tikv] | table:t2 | keep order:false, stats:pseudo |
++-------------------------+---------+-----------+---------------+--------------------------------+
+3 rows in set (0.00 sec)
+```
+
+`69` should be adjusted to `2069`.
+
+### 4. What is your TiDB version? (Required)
+
+
+
+``` mysql
+mysql> select tidb_version();
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: None
+Edition: Community
+Git Commit Hash: None
+Git Branch: None
+UTC Build Time: None
+GoVersion: go1.15
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false |
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+## Score
+
+- 600
+
+## Mentor
+
+* @lzmhhh123 ",True,"Comparison result is incorrect between year column and int constant - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+
+
+``` mysql
+create table t2 (a year(4));
+insert into t2 values(69);
+select * from t2 where a <= 69;
+```
+
+### 2. What did you expect to see? (Required)
+
+In mysql 8.0
+
+``` mysql
+mysql> select * from t2 where a <= 69;
++------+
+| a |
++------+
+| 2069 |
++------+
+1 row in set (0.00 sec)
+```
+
+### 3. What did you see instead (Required)
+
+``` mysql
+mysql> select * from t2 where a <= 69;
+Empty set (0.00 sec)
+
+mysql> explain select * from t2 where a <= 69;
++-------------------------+---------+-----------+---------------+--------------------------------+
+| id | estRows | task | access object | operator info |
++-------------------------+---------+-----------+---------------+--------------------------------+
+| TableReader_7 | 1.00 | root | | data:Selection_6 |
+| └─Selection_6 | 1.00 | cop[tikv] | | le(test.t2.a, 69) |
+| └─TableFullScan_5 | 3.00 | cop[tikv] | table:t2 | keep order:false, stats:pseudo |
++-------------------------+---------+-----------+---------------+--------------------------------+
+3 rows in set (0.00 sec)
+```
+
+`69` should be adjusted to `2069`.
+
+### 4. What is your TiDB version? (Required)
+
+
+
+``` mysql
+mysql> select tidb_version();
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: None
+Edition: Community
+Git Commit Hash: None
+Git Branch: None
+UTC Build Time: None
+GoVersion: go1.15
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false |
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+## Score
+
+- 600
+
+## Mentor
+
+* @lzmhhh123 ",1,comparison result is incorrect between year column and int constant bug report please answer these questions before submitting your issue thanks minimal reproduce step required mysql create table a year insert into values select from where a what did you expect to see required in mysql mysql mysql select from where a a row in set sec what did you see instead required mysql mysql select from where a empty set sec mysql explain select from where a id estrows task access object operator info tablereader root data selection └─selection cop le test a └─tablefullscan cop table keep order false stats pseudo rows in set sec should be adjusted to what is your tidb version required mysql mysql select tidb version tidb version release version none edition community git commit hash none git branch none utc build time none goversion race enabled false tikv min version check table before drop false row in set sec score mentor ,1
+5800,8247240513.0,IssuesEvent,2018-09-11 15:02:16,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,"""div"" scientific notation values out of range",help wanted type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+select (1.175494351E-37 div 1.7976931348623157E+308);
+```
+
+2. What did you expect to see?
+
+```
++-----------------------------------------------+
+| (1.175494351E-37 div 1.7976931348623157E+308) |
++-----------------------------------------------+
+| 0 |
++-----------------------------------------------+
+```
+
+3. What did you see instead?
+
+```
+ERROR 1690 (22003): %s value is out of range in '%s'
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"""div"" scientific notation values out of range - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+select (1.175494351E-37 div 1.7976931348623157E+308);
+```
+
+2. What did you expect to see?
+
+```
++-----------------------------------------------+
+| (1.175494351E-37 div 1.7976931348623157E+308) |
++-----------------------------------------------+
+| 0 |
++-----------------------------------------------+
+```
+
+3. What did you see instead?
+
+```
+ERROR 1690 (22003): %s value is out of range in '%s'
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1, div scientific notation values out of range please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql select div what did you expect to see div what did you see instead error s value is out of range in s what version of tidb are you using tidb server v ,1
+451606,13039229324.0,IssuesEvent,2020-07-28 16:24:07,googleapis/release-please,https://api.github.com/repos/googleapis/release-please,closed,Cannot read property 'sha' of undefined (Java),priority: p2 type: bug,"We're seeing a bunch of these in the `repo-automation-bots` logs:
+
+```
+TypeError: Cannot read property 'sha' of undefined
+at JavaYoshi._run (/workspace/node_modules/release-please/build/src/releasers/java-yoshi.js:84)
+```
+
+It looks like it's possible for the number of commits in this situation to be 0:
+
+```js
+if (this.snapshot) {
+ const latestCommit = (
+ await this.commits(latestTag ? latestTag.sha : undefined, 1, true)
+ )[0];
+ prSHA = latestCommit.sha;
+ }
+```
+
+In this case, the size of the value returned from `this.commits` is 0. ",1.0,"Cannot read property 'sha' of undefined (Java) - We're seeing a bunch of these in the `repo-automation-bots` logs:
+
+```
+TypeError: Cannot read property 'sha' of undefined
+at JavaYoshi._run (/workspace/node_modules/release-please/build/src/releasers/java-yoshi.js:84)
+```
+
+It looks like it's possible for the number of commits in this situation to be 0:
+
+```js
+if (this.snapshot) {
+ const latestCommit = (
+ await this.commits(latestTag ? latestTag.sha : undefined, 1, true)
+ )[0];
+ prSHA = latestCommit.sha;
+ }
+```
+
+In this case, the size of the value returned from `this.commits` is 0. ",0,cannot read property sha of undefined java we re seeing a bunch of these in the repo automation bots logs typeerror cannot read property sha of undefined at javayoshi run workspace node modules release please build src releasers java yoshi js it looks like it s possible for the number of commits in this situation to be js if this snapshot const latestcommit await this commits latesttag latesttag sha undefined true prsha latestcommit sha in this case the size of the value returned from this commits is ,0
+11111,13131607739.0,IssuesEvent,2020-08-06 17:19:47,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,error message is not compatible with MySQL,good-first-issue status/help-wanted type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+``` sql
+create table t(a int);
+select a as b from t group by values(b);
+```
+
+2. What did you expect to see?
+``` sql
+mysql> SELECT a AS b FROM t GROUP BY VALUES(b);
+ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column 'test.t.a' which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by
+```
+
+
+3. What did you see instead?
+Column name is lost.
+``` sql
+tidb> SELECT a AS b FROM t GROUP BY VALUES(b);
+ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column '' which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+select tidb_version();
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v2.1.0-rc.3-1-geb617c5f9
+Git Commit Hash: eb617c5f9f75c38d75fa848b6732c6071e66ab3e
+Git Branch: master
+UTC Build Time: 2018-09-30 03:35:34
+GoVersion: go version go1.10.3 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+",True,"error message is not compatible with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+``` sql
+create table t(a int);
+select a as b from t group by values(b);
+```
+
+2. What did you expect to see?
+``` sql
+mysql> SELECT a AS b FROM t GROUP BY VALUES(b);
+ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column 'test.t.a' which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by
+```
+
+
+3. What did you see instead?
+Column name is lost.
+``` sql
+tidb> SELECT a AS b FROM t GROUP BY VALUES(b);
+ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column '' which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+select tidb_version();
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v2.1.0-rc.3-1-geb617c5f9
+Git Commit Hash: eb617c5f9f75c38d75fa848b6732c6071e66ab3e
+Git Branch: master
+UTC Build Time: 2018-09-30 03:35:34
+GoVersion: go version go1.10.3 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+",1,error message is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do sql create table t a int select a as b from t group by values b what did you expect to see sql mysql select a as b from t group by values b error expression of select list is not in group by clause and contains nonaggregated column test t a which is not functionally dependent on columns in group by clause this is incompatible with sql mode only full group by what did you see instead column name is lost sql tidb select a as b from t group by values b error expression of select list is not in group by clause and contains nonaggregated column which is not functionally dependent on columns in group by clause this is incompatible with sql mode only full group by what version of tidb are you using tidb server v or run select tidb version on tidb select tidb version tidb version release version rc git commit hash git branch master utc build time goversion go version darwin race enabled false tikv min version alpha check table before drop false row in set sec ,1
+239038,26201190674.0,IssuesEvent,2023-01-03 17:37:19,samq-ghdemo/monorepo-dotnet,https://api.github.com/repos/samq-ghdemo/monorepo-dotnet,closed,dotnetcore-sample-1.0.0: 7 vulnerabilities (highest severity is: 8.8) - autoclosed,security vulnerability," Vulnerable Library - dotnetcore-sample-1.0.0
- It will only listen on one (the socket!)
+
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/system.security.cryptography.xml/4.4.0/system.security.cryptography.xml.4.4.0.nupkg
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-```
-mysql> select tidb_version()\G
-*************************** 1. row ***************************
-tidb_version(): Release Version: v2.1.0-beta-644-g89cd59d21
-Git Commit Hash: 89cd59d217637f5e79fdc81681c98531c668e688
-Git Branch: newmaster
-UTC Build Time: 2018-11-26 04:47:59
-GoVersion: go version go1.11 linux/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false
-1 row in set (0.00 sec)
-```",1,tidb server options socket and host are incompatible bug report please answer these questions before submitting your issue thanks what did you do bin tidb server socket tmp mysql sock host p what did you expect to see i would expect it to listen on both this is important because of mysql s special handling of localhost for the libmysql derived clients it will switch to using unix socket for other drivers like jdbc it will only ever use tcp so it is useful to be able to have the server listen on both for a fully local install what did you see instead it will only listen on one the socket what version of tidb are you using tidb server v or run select tidb version on tidb mysql select tidb version g row tidb version release version beta git commit hash git branch newmaster utc build time goversion go version linux race enabled false tikv min version alpha check table before drop false row in set sec ,1
-51196,10595774186.0,IssuesEvent,2019-10-09 19:44:25,fdorg/flashdevelop,https://api.github.com/repos/fdorg/flashdevelop,opened,[Haxe][CodeGenerator] Add the generator `Generate constructor with initializer` for `abstract`,coderefactor enhancement haxe,"```haxe
-abstract AType(Int) {
- $(EntryPoint)
-}
-```
-expected result:
-```haxe
-abstract AType(Int) {
- public function new(value:Int) this = value;
-}
-```",1.0,"[Haxe][CodeGenerator] Add the generator `Generate constructor with initializer` for `abstract` - ```haxe
-abstract AType(Int) {
- $(EntryPoint)
-}
-```
-expected result:
-```haxe
-abstract AType(Int) {
- public function new(value:Int) this = value;
-}
-```",0, add the generator generate constructor with initializer for abstract haxe abstract atype int entrypoint expected result haxe abstract atype int public function new value int this value ,0
-31279,2732890259.0,IssuesEvent,2015-04-17 10:01:15,tiku01/oryx-editor,https://api.github.com/repos/tiku01/oryx-editor,closed,"Repository view: ""writer"" vs. ""contributor""",auto-migrated Priority-Medium Type-Enhancement,"```
-In the repository: On the left at ""access-filter"" it shows ""Me as writer"".
-On the right (with selected model) you can add ""contributors"". For some
-people this could be misleading. I prefer ""contributor"".
-```
+
-Original issue reported on code.google.com by `MaKoL...@gmail.com` on 17 Jun 2009 at 6:10",1.0,"Repository view: ""writer"" vs. ""contributor"" - ```
-In the repository: On the left at ""access-filter"" it shows ""Me as writer"".
-On the right (with selected model) you can add ""contributors"". For some
-people this could be misleading. I prefer ""contributor"".
-```
+## Vulnerabilities
-Original issue reported on code.google.com by `MaKoL...@gmail.com` on 17 Jun 2009 at 6:10",0,repository view writer vs contributor in the repository on the left at access filter it shows me as writer on the right with selected model you can add contributors for some people this could be misleading i prefer contributor original issue reported on code google com by makol gmail com on jun at ,0
-7851,10062884541.0,IssuesEvent,2019-07-23 03:11:05,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Incompatible with MySQL 8.0 about CAST string to unsigned,type/bug type/compatibility,"## Bug Report
+| CVE | Severity | CVSS | Dependency | Type | Fixed in (dotnetcore-sample version) | Remediation Available |
+| ------------- | ------------- | ----- | ----- | ----- | ------------- | --- |
+| [CVE-2018-0787](https://www.mend.io/vulnerability-database/CVE-2018-0787) | High | 8.8 | detected in multiple dependencies | Transitive | N/A* | ❌ |
+| [WS-2018-0608](https://github.com/aspnet/Announcements/issues/300) | High | 7.5 | detected in multiple dependencies | Transitive | N/A* | ❌ |
+| [CVE-2018-0808](https://www.mend.io/vulnerability-database/CVE-2018-0808) | High | 7.5 | detected in multiple dependencies | Transitive | N/A* | ❌ |
+| [WS-2018-0607](https://github.com/aspnet/Announcements/issues/311) | High | 7.5 | microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg | Transitive | N/A* | ❌ |
+| [CVE-2020-1045](https://www.mend.io/vulnerability-database/CVE-2020-1045) | High | 7.5 | microsoft.aspnetcore.http.2.0.0.nupkg | Transitive | N/A* | ❌ |
+| [CVE-2021-1723](https://www.mend.io/vulnerability-database/CVE-2021-1723) | High | 7.5 | microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg | Transitive | N/A* | ❌ |
+| [CVE-2022-34716](https://www.mend.io/vulnerability-database/CVE-2022-34716) | Medium | 5.9 | system.security.cryptography.xml.4.4.0.nupkg | Transitive | N/A* | ❌ |
+
*For some transitive vulnerabilities, there is no version of direct dependency with a fix. Check the section ""Details"" below to see if there is a version of transitive dependency where vulnerability is fixed.
-Please answer these questions before submitting your issue. Thanks!
+## Details
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+
-```
-MySQL(127.0.0.1:3306)> select cast('-1111.911' as unsigned)
-+-------------------------------+
-| cast('-1111.911' as unsigned) |
-+-------------------------------+
-| 18446744073709550505 |
-+-------------------------------+
-1 row in set (0.002 sec)
-
-TiDB(127.0.0.1:4000)> select cast('-1111.911' as unsigned)
-+-------------------------------+
-| cast('-1111.911' as unsigned) |
-+-------------------------------+
-| 18446744073709550504 |
-+-------------------------------+
-1 row in set (0.003 sec)
-```
+ CVE-2018-0787
-2. What did you expect to see?
-Expected: `18446744073709550505`
+### Vulnerable Libraries - microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg, microsoft.aspnetcore.httpoverrides.2.0.0.nupkg
+
-3. What did you see instead?
-Got: `18446744073709550504`
+### microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
Core components of ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
+
-```
-+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v2.1.8-24-g7b36cdfb6-dirty
-Git Commit Hash: 7b36cdfb6e8a4c279fc360ed79cf1c499b553688
-Git Branch: failpoint-2.1
-UTC Build Time: 2019-04-30 08:26:17
-GoVersion: go version go1.12 darwin/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false |
-+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-```
-",True,"Incompatible with MySQL 8.0 about CAST string to unsigned - ## Bug Report
+Dependency Hierarchy:
+ - dotnetcore-sample-1.0.0 (Root Library)
+ - microsoft.aspnetcore.2.0.0.nupkg
+ - microsoft.aspnetcore.server.kestrel.2.0.0.nupkg
+ - :x: **microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg** (Vulnerable Library)
-Please answer these questions before submitting your issue. Thanks!
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+### microsoft.aspnetcore.httpoverrides.2.0.0.nupkg
-```
-MySQL(127.0.0.1:3306)> select cast('-1111.911' as unsigned)
-+-------------------------------+
-| cast('-1111.911' as unsigned) |
-+-------------------------------+
-| 18446744073709550505 |
-+-------------------------------+
-1 row in set (0.002 sec)
-
-TiDB(127.0.0.1:4000)> select cast('-1111.911' as unsigned)
-+-------------------------------+
-| cast('-1111.911' as unsigned) |
-+-------------------------------+
-| 18446744073709550504 |
-+-------------------------------+
-1 row in set (0.003 sec)
-```
+
ASP.NET Core basic middleware for supporting HTTP method overrides. Includes:
+* X-Forwarded-* header...
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.httpoverrides/2.0.0/microsoft.aspnetcore.httpoverrides.2.0.0.nupkg
+
-2. What did you expect to see?
+Dependency Hierarchy:
+ - dotnetcore-sample-1.0.0 (Root Library)
+ - microsoft.aspnetcore.2.0.0.nupkg
+ - microsoft.aspnetcore.server.iisintegration.2.0.0.nupkg
+ - :x: **microsoft.aspnetcore.httpoverrides.2.0.0.nupkg** (Vulnerable Library)
-Expected: `18446744073709550505`
-3. What did you see instead?
+
+
-Got: `18446744073709550504`
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+### Vulnerability Details
+
+
+ASP.NET Core 1.0. 1.1, and 2.0 allow an elevation of privilege vulnerability due to how web applications that are created from templates validate web requests, aka ""ASP.NET Core Elevation Of Privilege Vulnerability"".
-```
-+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v2.1.8-24-g7b36cdfb6-dirty
-Git Commit Hash: 7b36cdfb6e8a4c279fc360ed79cf1c499b553688
-Git Branch: failpoint-2.1
-UTC Build Time: 2019-04-30 08:26:17
-GoVersion: go version go1.12 darwin/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false |
-+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-```
-",1,incompatible with mysql about cast string to unsigned bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error mysql select cast as unsigned cast as unsigned row in set sec tidb select cast as unsigned cast as unsigned row in set sec what did you expect to see expected what did you see instead got what version of tidb are you using tidb server v or run select tidb version on tidb tidb version release version dirty git commit hash git branch failpoint utc build time goversion go version darwin race enabled false tikv min version alpha check table before drop false ,1
-16384,22092463572.0,IssuesEvent,2022-06-01 07:20:29,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,release savepoint behavior is inconsistent with mysql,type/bug severity/minor compatibility-mysql8,"## Bug Report
-
-Please answer these questions before submitting your issue. Thanks!
-
-### 1. Minimal reproduce step (Required)
-
-```sql
-/* test */ select version();
-/* test */ drop table if exists t;
-/* test */ create table t (k int primary key, v varchar(20));
-/* test */ begin;
-/* test */ insert into t values (1, 'a');
-/* test */ savepoint p1;
-/* test */ insert into t values (2, 'b');
-/* test */ savepoint p2;
-/* test */ select * from t;
-/* test */ release savepoint p1;
-/* test */ select * from t;
-/* test */ rollback to p2; -- tidb: OK; mysql: SAVEPOINT p2 does not exist;
-/* test */ select * from t;
-/* test */ rollback;
-```
+
-### 2. What did you expect to see? (Required)
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Network
+ - Attack Complexity: Low
+ - Privileges Required: None
+ - User Interaction: Required
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: High
+ - Integrity Impact: High
+ - Availability Impact: High
+
+For more information on CVSS3 Scores, click here.
+
-### 3. What did you see instead (Required)
+
-### 4. What is your TiDB version? (Required)
+### Suggested Fix
+
-master: 2c3f717af66c6925f46776da867790ca150ecfcc
+
-",True,"release savepoint behavior is inconsistent with mysql - ## Bug Report
+
-Please answer these questions before submitting your issue. Thanks!
+
-### 1. Minimal reproduce step (Required)
+ WS-2018-0608
-```sql
-/* test */ select version();
-/* test */ drop table if exists t;
-/* test */ create table t (k int primary key, v varchar(20));
-/* test */ begin;
-/* test */ insert into t values (1, 'a');
-/* test */ savepoint p1;
-/* test */ insert into t values (2, 'b');
-/* test */ savepoint p2;
-/* test */ select * from t;
-/* test */ release savepoint p1;
-/* test */ select * from t;
-/* test */ rollback to p2; -- tidb: OK; mysql: SAVEPOINT p2 does not exist;
-/* test */ select * from t;
-/* test */ rollback;
-```
+### Vulnerable Libraries - microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg, microsoft.aspnetcore.server.kestrel.transport.abstractions.2.0.0.nupkg, microsoft.aspnetcore.server.kestrel.transport.libuv.2.0.0.nupkg
+
-
-### 2. What did you expect to see? (Required)
+### microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
-### 3. What did you see instead (Required)
+
Core components of ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
-",1,release savepoint behavior is inconsistent with mysql bug report please answer these questions before submitting your issue thanks minimal reproduce step required sql test select version test drop table if exists t test create table t k int primary key v varchar test begin test insert into t values a test savepoint test insert into t values b test savepoint test select from t test release savepoint test select from t test rollback to tidb ok mysql savepoint does not exist test select from t test rollback what did you expect to see required what did you see instead required what is your tidb version required master ,1
-22492,6254129005.0,IssuesEvent,2017-07-14 00:41:22,diaspora/diaspora,https://api.github.com/repos/diaspora/diaspora,closed,"Message has redundant ""conversation_guid"" in it XML representation",code refactor federation,"In its federated XML representation Message model have property [conversation_guid](https://github.com/diaspora/diaspora/blob/develop/app/models/message.rb#L10) and property [parent_guid](https://github.com/diaspora/diaspora/blob/develop/lib/diaspora/relayable.rb#L12) from the Relayable inclusion. Looks like these properties duplicate each other. I think the former could be removed in favour to the latter. However it could ruin signature verifications, so it's not possible, before the new method of signature computation is adopted for the whole federation.
-##
+
Transport abstractions for the ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.transport.abstractions/2.0.0/microsoft.aspnetcore.server.kestrel.transport.abstractions.2.0.0.nupkg
+
-Want to back this issue? **[Post a bounty on it!](https://www.bountysource.com/issues/29123253-message-has-redundant-conversation_guid-in-it-xml-representation?utm_campaign=plugin&utm_content=tracker%2F522&utm_medium=issues&utm_source=github)** We accept bounties via [Bountysource](https://www.bountysource.com/?utm_campaign=plugin&utm_content=tracker%2F522&utm_medium=issues&utm_source=github).
-
-",1.0,"Message has redundant ""conversation_guid"" in it XML representation - In its federated XML representation Message model have property [conversation_guid](https://github.com/diaspora/diaspora/blob/develop/app/models/message.rb#L10) and property [parent_guid](https://github.com/diaspora/diaspora/blob/develop/lib/diaspora/relayable.rb#L12) from the Relayable inclusion. Looks like these properties duplicate each other. I think the former could be removed in favour to the latter. However it could ruin signature verifications, so it's not possible, before the new method of signature computation is adopted for the whole federation.
-##
+Dependency Hierarchy:
+ - dotnetcore-sample-1.0.0 (Root Library)
+ - microsoft.aspnetcore.2.0.0.nupkg
+ - microsoft.aspnetcore.server.kestrel.2.0.0.nupkg
+ - microsoft.aspnetcore.server.kestrel.transport.libuv.2.0.0.nupkg
+ - :x: **microsoft.aspnetcore.server.kestrel.transport.abstractions.2.0.0.nupkg** (Vulnerable Library)
-Want to back this issue? **[Post a bounty on it!](https://www.bountysource.com/issues/29123253-message-has-redundant-conversation_guid-in-it-xml-representation?utm_campaign=plugin&utm_content=tracker%2F522&utm_medium=issues&utm_source=github)** We accept bounties via [Bountysource](https://www.bountysource.com/?utm_campaign=plugin&utm_content=tracker%2F522&utm_medium=issues&utm_source=github).
-
-",0,message has redundant conversation guid in it xml representation in its federated xml representation message model have property and property from the relayable inclusion looks like these properties duplicate each other i think the former could be removed in favour to the latter however it could ruin signature verifications so it s not possible before the new method of signature computation is adopted for the whole federation want to back this issue we accept bounties via ,0
-8046,10185915799.0,IssuesEvent,2019-08-10 08:22:46,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,window function: should check fuction's arguments firstly.,help wanted type/bug type/compatibility,"## Bug Report
-Please answer these questions before submitting your issue. Thanks!
+### microsoft.aspnetcore.server.kestrel.transport.libuv.2.0.0.nupkg
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+
Libuv transport for the ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.transport.libuv/2.0.0/microsoft.aspnetcore.server.kestrel.transport.libuv.2.0.0.nupkg
+
-```mysql
-SELECT NTH_VALUE(fieldA, -1) OVER (w1 PARTITION BY fieldB ORDER BY fieldB , fieldA ) AS 'ntile', fieldA, fieldB FROM ( SELECT `pk` AS fieldA, `col_date_key` AS fieldB FROM `table70_int_autoinc` ) as t WINDOW w1 AS ( ORDER BY fieldB ASC, fieldA DESC );
-```
+Dependency Hierarchy:
+ - dotnetcore-sample-1.0.0 (Root Library)
+ - microsoft.aspnetcore.2.0.0.nupkg
+ - microsoft.aspnetcore.server.kestrel.2.0.0.nupkg
+ - :x: **microsoft.aspnetcore.server.kestrel.transport.libuv.2.0.0.nupkg** (Vulnerable Library)
-2. What did you expect to see?
-```mysql
-ERROR 1210 (HY000): Incorrect arguments to nth_value
-```
+
+
-3. What did you see instead?
+
-```mysql
-ERROR 3581 (HY000): A window which depends on another cannot define partitioning.
-```
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+### Vulnerability Details
+
+
+A vulnerability was discovered in versions 2.x of ASP.NET Core where a specially crafted request can cause excess resource consumption in Kestrel.
-",True,"window function: should check fuction's arguments firstly. - ## Bug Report
+
+
-Please answer these questions before submitting your issue. Thanks!
+
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+### CVSS 3 Score Details (7.5)
+
-```mysql
-SELECT NTH_VALUE(fieldA, -1) OVER (w1 PARTITION BY fieldB ORDER BY fieldB , fieldA ) AS 'ntile', fieldA, fieldB FROM ( SELECT `pk` AS fieldA, `col_date_key` AS fieldB FROM `table70_int_autoinc` ) as t WINDOW w1 AS ( ORDER BY fieldB ASC, fieldA DESC );
-```
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Network
+ - Attack Complexity: Low
+ - Privileges Required: None
+ - User Interaction: None
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: None
+ - Integrity Impact: None
+ - Availability Impact: High
+
+For more information on CVSS3 Scores, click here.
+
-2. What did you expect to see?
+
-```mysql
-ERROR 1210 (HY000): Incorrect arguments to nth_value
-```
+### Suggested Fix
+
-```mysql
-ERROR 3581 (HY000): A window which depends on another cannot define partitioning.
-```
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
-",1,window function should check fuction s arguments firstly bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error mysql select nth value fielda over partition by fieldb order by fieldb fielda as ntile fielda fieldb from select pk as fielda col date key as fieldb from int autoinc as t window as order by fieldb asc fielda desc what did you expect to see mysql error incorrect arguments to nth value what did you see instead mysql error a window which depends on another cannot define partitioning what version of tidb are you using tidb server v or run select tidb version on tidb ,1
-309329,23291607790.0,IssuesEvent,2022-08-06 00:30:36,TavaresDylan/ICG,https://api.github.com/repos/TavaresDylan/ICG,closed,fix(doc): mkdocs error page no css,bug scope/documentation stale,"**Bug description**
-404 page of mkdocs is show without css
+
-**Steps to reproduce**
-- [ ] Just go on non existant page in documentation
+
-**Expected behavior**
-404 page showing up in site template
-",1.0,"fix(doc): mkdocs error page no css - **Bug description**
-404 page of mkdocs is show without css
+ CVE-2018-0808
-**Steps to reproduce**
-- [ ] Just go on non existant page in documentation
-**Expected behavior**
-404 page showing up in site template
-",0,fix doc mkdocs error page no css bug description page of mkdocs is show without css steps to reproduce just go on non existant page in documentation expected behavior page showing up in site template ,0
-15728,20366116739.0,IssuesEvent,2022-02-21 05:57:42,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Built-in function CHARSET not supported,help wanted type/compatibility component/expression,"Please answer these questions before submitting your issue. Thanks!
+### Vulnerable Libraries - microsoft.aspnetcore.server.iisintegration.2.0.0.nupkg, microsoft.aspnetcore.hosting.2.0.0.nupkg
+
-1. What did you do?
-```sql
-SELECT CHARSET('a');
-```
+### microsoft.aspnetcore.server.iisintegration.2.0.0.nupkg
-2. What did you expect to see?
+
ASP.NET Core components for working with the IIS AspNetCoreModule.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.iisintegration/2.0.0/microsoft.aspnetcore.server.iisintegration.2.0.0.nupkg
+
-```
-+--------------+
-| CHARSET('a') |
-+--------------+
-| utf8 |
-+--------------+
-1 row in set (0.00 sec)
-```
+Dependency Hierarchy:
+ - dotnetcore-sample-1.0.0 (Root Library)
+ - microsoft.aspnetcore.2.0.0.nupkg
+ - :x: **microsoft.aspnetcore.server.iisintegration.2.0.0.nupkg** (Vulnerable Library)
-3. What did you see instead?
-```
-ERROR 1305 (42000): FUNCTION CHARSET does not exist
-```
+### microsoft.aspnetcore.hosting.2.0.0.nupkg
-4. What version of TiDB are you using (`tidb-server -V`)?
+
ASP.NET Core hosting infrastructure and startup logic for web applications.
+
-2. What did you expect to see?
+
-```
-+--------------+
-| CHARSET('a') |
-+--------------+
-| utf8 |
-+--------------+
-1 row in set (0.00 sec)
-```
-
-3. What did you see instead?
-
-```
-ERROR 1305 (42000): FUNCTION CHARSET does not exist
-```
-
-4. What version of TiDB are you using (`tidb-server -V`)?
-
-",1,built in function charset not supported please answer these questions before submitting your issue thanks what did you do sql select charset a what did you expect to see charset a row in set sec what did you see instead error function charset does not exist what version of tidb are you using tidb server v ,1
-25651,12701403801.0,IssuesEvent,2020-06-22 18:06:11,bbc/simorgh,https://api.github.com/repos/bbc/simorgh,opened,Serve images in next-gen formats,Refinement Needed performance ws-stories,"**Is your feature request related to a problem? Please describe.**
-Parent issue: https://github.com/bbc/simorgh-infrastructure/issues/1088
-
-We serve images in JPG format, but formats like JPEG 200, JPEG XR and WebP often provide better compression, which means faster downloads and less data consumption.
-
-**Describe the solution you'd like**
-Serve images in next-gen formats.
+### Vulnerability Details
+
+
+ASP.NET Core 1.0. 1.1, and 2.0 allow an elevation of privilege vulnerability due to how ASP.NET web applications handle web requests, aka ""ASP.NET Core Elevation Of Privilege Vulnerability"". This CVE is unique from CVE-2018-0784.
-More information: https://web.dev/uses-webp-images/
+
+
-**Describe alternatives you've considered**
-A clear and concise description of any alternative solutions or features you've considered.
+
-**Testing notes**
-[Tester to complete]
+### CVSS 3 Score Details (7.5)
+
-Dev insight: Will Cypress tests be required or are unit tests sufficient? Will there be any potential regression? etc
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Network
+ - Attack Complexity: Low
+ - Privileges Required: None
+ - User Interaction: None
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: None
+ - Integrity Impact: None
+ - Availability Impact: High
+
+For more information on CVSS3 Scores, click here.
+
-- [ ] This feature is expected to need manual testing.
+
-**Additional context**
-Add any other context or screenshots about the feature request here.
-",True,"Serve images in next-gen formats - **Is your feature request related to a problem? Please describe.**
-Parent issue: https://github.com/bbc/simorgh-infrastructure/issues/1088
+### Suggested Fix
+
-We serve images in JPG format, but formats like JPEG 200, JPEG XR and WebP often provide better compression, which means faster downloads and less data consumption.
+
-**Describe the solution you'd like**
-Serve images in next-gen formats.
+
-More information: https://web.dev/uses-webp-images/
+
-**Describe alternatives you've considered**
-A clear and concise description of any alternative solutions or features you've considered.
+
-**Testing notes**
-[Tester to complete]
+ WS-2018-0607
-Dev insight: Will Cypress tests be required or are unit tests sufficient? Will there be any potential regression? etc
-- [ ] This feature is expected to need manual testing.
+### Vulnerable Library - microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
-**Additional context**
-Add any other context or screenshots about the feature request here.
-",0,serve images in next gen formats is your feature request related to a problem please describe parent issue we serve images in jpg format but formats like jpeg jpeg xr and webp often provide better compression which means faster downloads and less data consumption describe the solution you d like serve images in next gen formats more information describe alternatives you ve considered a clear and concise description of any alternative solutions or features you ve considered testing notes dev insight will cypress tests be required or are unit tests sufficient will there be any potential regression etc this feature is expected to need manual testing additional context add any other context or screenshots about the feature request here ,0
-6409,8709680723.0,IssuesEvent,2018-12-06 14:36:51,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,builtin uncompress function ignored the four bytes length,help wanted type/compatibility,"## Bug Report
+
Core components of ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
+
-Please answer these questions before submitting your issue. Thanks!
+Dependency Hierarchy:
+ - dotnetcore-sample-1.0.0 (Root Library)
+ - microsoft.aspnetcore.2.0.0.nupkg
+ - microsoft.aspnetcore.server.kestrel.2.0.0.nupkg
+ - :x: **microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg** (Vulnerable Library)
+
+
-1. What did you do?
+
-```
-mysql> select uncompress(unhex('02000000789CCB48CDC9C95728CF2FCA4901001A0B045D'));
-```
+### Vulnerability Details
+
+
+Denial of service vulnerability in ASP.NET Core when a malformed request is terminated.
-2. What did you expect to see?
-
-```
-mysql> select uncompress(unhex('02000000789CCB48CDC9C95728CF2FCA4901001A0B045D'));
-+---------------------------------------------------------------------+
-| uncompress(unhex('02000000789CCB48CDC9C95728CF2FCA4901001A0B045D')) |
-+---------------------------------------------------------------------+
-| NULL |
-+---------------------------------------------------------------------+
-1 row in set, 1 warning (0.00 sec)
-
-mysql> show warnings;
-+---------+------+--------------------------------------------------------------------------------------------------+
-| Level | Code | Message |
-+---------+------+--------------------------------------------------------------------------------------------------+
-| Warning | 1258 | ZLIB: Not enough room in the output buffer (probably, length of uncompressed data was corrupted) |
-+---------+------+--------------------------------------------------------------------------------------------------+
-1 row in set (0.00 sec)
-```
+
+
-3. What did you see instead?
-```
-+---------------------------------------------------------------------+
-| uncompress(unhex('02000000789CCB48CDC9C95728CF2FCA4901001A0B045D')) |
-+---------------------------------------------------------------------+
-| hello world |
-+---------------------------------------------------------------------+
-1 row in set (0.01 sec)
-```
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+### CVSS 3 Score Details (7.5)
+
+For more information on CVSS3 Scores, click here.
+
-5. more info
-This is found when I try to implement builtin compress and uncompress function in TiKV (https://github.com/tikv/tikv/pull/3856)
-the first four bytes stored the length of the uncompress string, if it's less than the corrected length (maybe corrupted), MySQL return Null, TiDB just ignore it.",True,"builtin uncompress function ignored the four bytes length - ## Bug Report
+
-Please answer these questions before submitting your issue. Thanks!
+### Suggested Fix
+
-```
-mysql> select uncompress(unhex('02000000789CCB48CDC9C95728CF2FCA4901001A0B045D'));
-```
+
-2. What did you expect to see?
-
-```
-mysql> select uncompress(unhex('02000000789CCB48CDC9C95728CF2FCA4901001A0B045D'));
-+---------------------------------------------------------------------+
-| uncompress(unhex('02000000789CCB48CDC9C95728CF2FCA4901001A0B045D')) |
-+---------------------------------------------------------------------+
-| NULL |
-+---------------------------------------------------------------------+
-1 row in set, 1 warning (0.00 sec)
-
-mysql> show warnings;
-+---------+------+--------------------------------------------------------------------------------------------------+
-| Level | Code | Message |
-+---------+------+--------------------------------------------------------------------------------------------------+
-| Warning | 1258 | ZLIB: Not enough room in the output buffer (probably, length of uncompressed data was corrupted) |
-+---------+------+--------------------------------------------------------------------------------------------------+
-1 row in set (0.00 sec)
-```
+
-3. What did you see instead?
-```
-+---------------------------------------------------------------------+
-| uncompress(unhex('02000000789CCB48CDC9C95728CF2FCA4901001A0B045D')) |
-+---------------------------------------------------------------------+
-| hello world |
-+---------------------------------------------------------------------+
-1 row in set (0.01 sec)
-```
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+ CVE-2020-1045
-```
-tidb_version(): Release Version: v2.1.0-rc.2-10-gb30dbd0
-Git Commit Hash: b30dbd06acaab088a1e8fa004e189c651ca08bf1
-Git Branch: master
-UTC Build Time: 2018-09-17 01:20:48
-GoVersion: go version go1.11 linux/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false
-```
-5. more info
-This is found when I try to implement builtin compress and uncompress function in TiKV (https://github.com/tikv/tikv/pull/3856)
-the first four bytes stored the length of the uncompress string, if it's less than the corrected length (maybe corrupted), MySQL return Null, TiDB just ignore it.",1,builtin uncompress function ignored the four bytes length bug report please answer these questions before submitting your issue thanks what did you do mysql select uncompress unhex what did you expect to see mysql select uncompress unhex uncompress unhex null row in set warning sec mysql show warnings level code message warning zlib not enough room in the output buffer probably length of uncompressed data was corrupted row in set sec what did you see instead uncompress unhex hello world row in set sec what version of tidb are you using tidb server v or run select tidb version on tidb tidb version release version rc git commit hash git branch master utc build time goversion go version linux race enabled false tikv min version alpha check table before drop false more info this is found when i try to implement builtin compress and uncompress function in tikv the first four bytes stored the length of the uncompress string if it s less than the corrected length maybe corrupted mysql return null, tidb just ignore it ,1
-11635,13684960343.0,IssuesEvent,2020-09-30 06:14:21,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Support VALUES and TABLE statements syntax,challenge-program difficulty/easy high-performance picked sig/DDL status/help-wanted type/compatibility,"## Description
+### Vulnerable Library - microsoft.aspnetcore.http.2.0.0.nupkg
-Related parser issue: https://github.com/pingcap/parser/issues/869
+
ASP.NET Core default HTTP feature implementations.
+
-The [`TABLE`](https://dev.mysql.com/doc/refman/8.0/en/table.html) and [`VALUES`](https://dev.mysql.com/doc/refman/8.0/en/values.html) statements are two query specification statements introduced in [MySQL 8.0.19](https://dev.mysql.com/doc/relnotes/mysql/8.0/en/news-8-0-19.html#mysqld-8-0-19-sql-syntax).
+
-```sql
-TABLE tbl_name [ORDER BY col_name] [LIMIT limit [OFFSET offset]];
+### Vulnerability Details
+
+
+A security feature bypass vulnerability exists in the way Microsoft ASP.NET Core parses encoded cookie names.The ASP.NET Core cookie parser decodes entire cookie strings which could allow a malicious attacker to set a second cookie with the name being percent encoded.The security update addresses the vulnerability by fixing the way the ASP.NET Core cookie parser handles encoded names., aka 'Microsoft ASP.NET Core Security Feature Bypass Vulnerability'.
-VALUES ROW(val1, val2, …), … [ORDER BY column_N [LIMIT limit [OFFSET offset]]];
-```
+
+For more information on CVSS3 Scores, click here.
+
+
-### Solution
-For a reference, please see https://github.com/pingcap/parser/pull/680 and learn how to support a new syntax in the parser.
+### Suggested Fix
+
-* 300
+
-## SIG Slack Channel
+
-You can join [#sig-ddl](https://app.slack.com/client/TH91JCS4W/CMAKWBNJU) on slack in your spare time to discuss and get help with mentors or others.
+
-## Mentor(s)
+ CVE-2021-1723
-* @tangenta
-Contact the mentors: **#tidb-challenge-program** channel in [TiDB Community](https://join.slack.com/t/tidbcommunity/shared_invite/enQtNzc0MzI4ODExMDc4LWYwYmIzMjZkYzJiNDUxMmZlN2FiMGJkZjAyMzQ5NGU0NGY0NzI3NTYwMjAyNGQ1N2I2ZjAxNzc1OGUwYWM0NzE) Slack Workspace
+### Vulnerable Library - microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
-## Recommended Skills
+
Core components of ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
+
-### Example
+
-The [`TABLE`](https://dev.mysql.com/doc/refman/8.0/en/table.html) and [`VALUES`](https://dev.mysql.com/doc/refman/8.0/en/values.html) statements are two query specification statements introduced in [MySQL 8.0.19](https://dev.mysql.com/doc/relnotes/mysql/8.0/en/news-8-0-19.html#mysqld-8-0-19-sql-syntax).
+### CVSS 3 Score Details (7.5)
+
-* UNION
-* JOIN
-* subqueries
-* SELECT INTO OUTFILE
-* INSERT INTO SELECT
-* CREATE TABLE SELECT
+
+
-### Solution
-For a reference, please see https://github.com/pingcap/parser/pull/680 and learn how to support a new syntax in the parser.
+
-## Score
+ CVE-2022-34716
-* 300
-## SIG Slack Channel
+### Vulnerable Library - system.security.cryptography.xml.4.4.0.nupkg
-You can join [#sig-ddl](https://app.slack.com/client/TH91JCS4W/CMAKWBNJU) on slack in your spare time to discuss and get help with mentors or others.
+
Provides classes to support the creation and validation of XML digital signatures. The classes in th...
+
-* @tangenta
+
-Contact the mentors: **#tidb-challenge-program** channel in [TiDB Community](https://join.slack.com/t/tidbcommunity/shared_invite/enQtNzc0MzI4ODExMDc4LWYwYmIzMjZkYzJiNDUxMmZlN2FiMGJkZjAyMzQ5NGU0NGY0NzI3NTYwMjAyNGQ1N2I2ZjAxNzc1OGUwYWM0NzE) Slack Workspace
+### Vulnerability Details
+
+
+Microsoft is releasing this security advisory to provide information about a vulnerability in .NET Core 3.1 and .NET 6.0. An information disclosure vulnerability exists in .NET Core 3.1 and .NET 6.0 that could lead to unauthorized access of privileged information.
-## Recommended Skills
+## Affected software
-* Parser
-* Golang
+* Any .NET 6.0 application running on .NET 6.0.7 or earlier.
+* Any .NET Core 3.1 applicaiton running on .NET Core 3.1.27 or earlier.
-## Learning Materials
+## Patches
-* [Parser Quickstart](https://github.com/pingcap/parser/blob/master/docs/quickstart.md)
-* [Parser implementation(CN)](https://pingcap.com/blog-cn/tidb-source-code-reading-5/)
-",1,support values and table statements syntax description related parser issue example the and statements are two query specification statements introduced in sql table tbl name values row … … explaination these can be used in place everywhere a select statement was expected including union join subqueries select into outfile insert into select create table select solution for a reference please see and learn how to support a new syntax in the parser score sig slack channel you can join on slack in your spare time to discuss and get help with mentors or others mentor s tangenta contact the mentors tidb challenge program channel in slack workspace recommended skills parser golang learning materials ,1
-27185,7922117851.0,IssuesEvent,2018-07-05 09:44:48,ShaikASK/Testing,https://api.github.com/repos/ShaikASK/Testing,closed,Safari(11) : New Hires : New Hire /Re Hire Header & Save /cancel buttons are missing due to missing of vertical scroll bar ,Defect HR Admin Module New Hire P1 Release #3 Build 8,"Steps to Replicate :
+* If you're using .NET 6.0, you should download and install Runtime 6.0.8 or SDK 6.0.108 (for Visual Studio 2022 v17.1) from https://dotnet.microsoft.com/download/dotnet-core/6.0.
+* If you're using .NET Core 3.1, you should download and install Runtime 3.1.28 (for Visual Studio 2019 v16.9) from https://dotnet.microsoft.com/download/dotnet-core/3.1.
-1. Launch the URL
-2. Sign in as HR Admin user
-3. Create a New Hire by entering full length of text
+
+
-Experienced Behaviour : Observed that New Hire /Re Hire Header & Save /cancel buttons are missing upon entering full length text in Notes field Safari (11)
-Expected Behaviour : Ensure that New Hire /Re Hire Header & Save /cancel buttons buttons should be displayed upon entering full length of text ",1.0,"Safari(11) : New Hires : New Hire /Re Hire Header & Save /cancel buttons are missing due to missing of vertical scroll bar - Steps to Replicate :
+
-1. Launch the URL
-2. Sign in as HR Admin user
-3. Create a New Hire by entering full length of text
+### CVSS 3 Score Details (5.9)
+
-Experienced Behaviour : Observed that New Hire /Re Hire Header & Save /cancel buttons are missing upon entering full length text in Notes field Safari (11)
-Expected Behaviour : Ensure that New Hire /Re Hire Header & Save /cancel buttons buttons should be displayed upon entering full length of text ",0,safari new hires new hire re hire header save cancel buttons are missing due to missing of vertical scroll bar steps to replicate launch the url sign in as hr admin user create a new hire by entering full length of text experienced behaviour observed that new hire re hire header save cancel buttons are missing upon entering full length text in notes field safari expected behaviour ensure that new hire re hire header save cancel buttons buttons should be displayed upon entering full length of text ,0
-176171,28039053342.0,IssuesEvent,2023-03-28 17:03:48,pulumi/pulumi-docker,https://api.github.com/repos/pulumi/pulumi-docker,closed,docker:index:Image could not open dockerfile at relative path Dockerfile,kind/bug resolution/by-design,"### What happened?
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Network
+ - Attack Complexity: High
+ - Privileges Required: None
+ - User Interaction: None
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: High
+ - Integrity Impact: None
+ - Availability Impact: None
+
+For more information on CVSS3 Scores, click here.
+
-Upgraded from `pulumi-docker` `4.0.0` to `4.1.0`.
-`pulumi up` unexpectedly errors:
+
-```
-Diagnostics:
- docker:index:Image (my-app:latest):
- error: could not open dockerfile at relative path Dockerfile. Try setting `dockerfile` to ""/Users/shed/Repos/my-repo/projects/my-app/Dockerfile""
-```
+### Suggested Fix
+
-There is a file `/Users/shed/Repos/my-repo/projects/my-app/Dockerfile`.
-`context` is set to the directory and `dockerfile` is explicitly set to `Dockerfile`.
+
+
-### Output of `pulumi about`
+",True,"dotnetcore-sample-1.0.0: 7 vulnerabilities (highest severity is: 8.8) - autoclosed - Vulnerable Library - dotnetcore-sample-1.0.0
-I don't want to copy/paste this from a work project. I'll try to provide specific info as requested if relevant.
+
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/system.security.cryptography.xml/4.4.0/system.security.cryptography.xml.4.4.0.nupkg
-### Contributing
+## Vulnerabilities
-Vote on this issue by adding a 👍 reaction.
-To contribute a fix for this issue, leave a comment (and link to your pull request, if you've opened one already).
-",1.0,"docker:index:Image could not open dockerfile at relative path Dockerfile - ### What happened?
+| CVE | Severity | CVSS | Dependency | Type | Fixed in (dotnetcore-sample version) | Remediation Available |
+| ------------- | ------------- | ----- | ----- | ----- | ------------- | --- |
+| [CVE-2018-0787](https://www.mend.io/vulnerability-database/CVE-2018-0787) | High | 8.8 | detected in multiple dependencies | Transitive | N/A* | ❌ |
+| [WS-2018-0608](https://github.com/aspnet/Announcements/issues/300) | High | 7.5 | detected in multiple dependencies | Transitive | N/A* | ❌ |
+| [CVE-2018-0808](https://www.mend.io/vulnerability-database/CVE-2018-0808) | High | 7.5 | detected in multiple dependencies | Transitive | N/A* | ❌ |
+| [WS-2018-0607](https://github.com/aspnet/Announcements/issues/311) | High | 7.5 | microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg | Transitive | N/A* | ❌ |
+| [CVE-2020-1045](https://www.mend.io/vulnerability-database/CVE-2020-1045) | High | 7.5 | microsoft.aspnetcore.http.2.0.0.nupkg | Transitive | N/A* | ❌ |
+| [CVE-2021-1723](https://www.mend.io/vulnerability-database/CVE-2021-1723) | High | 7.5 | microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg | Transitive | N/A* | ❌ |
+| [CVE-2022-34716](https://www.mend.io/vulnerability-database/CVE-2022-34716) | Medium | 5.9 | system.security.cryptography.xml.4.4.0.nupkg | Transitive | N/A* | ❌ |
+
*For some transitive vulnerabilities, there is no version of direct dependency with a fix. Check the section ""Details"" below to see if there is a version of transitive dependency where vulnerability is fixed.
-Upgraded from `pulumi-docker` `4.0.0` to `4.1.0`.
-`pulumi up` unexpectedly errors:
+## Details
-```
-Diagnostics:
- docker:index:Image (my-app:latest):
- error: could not open dockerfile at relative path Dockerfile. Try setting `dockerfile` to ""/Users/shed/Repos/my-repo/projects/my-app/Dockerfile""
-```
+
-### Expected Behavior
-
-`pulumi up` to locate `Dockerfile` relative to my project directory.
-
-### Steps to reproduce
-
-My pulumi resource looks something like:
-
-```python
-image = docker.Image(
- ""my_app:latest"",
- build=docker.DockerBuildArgs(
- context=""/Users/shed/Repos/my-repo/projects/my-app/"",
- dockerfile=""Dockerfile"",
- args={""BUILDKIT_INLINE_CACHE"": ""1""}, # may not be necessary?
- cache_from=docker.CacheFromArgs(
- images=[
- pulumi.Output.concat(repo.repository_url, "":"", ""latest"")
- ]
- ),
- platform=""linux/amd64"",
- ),
- registry=registry,
- image_name=pulumi.Output.concat(self.repo.repository_url, "":"", ""latest""),
- )
-```
+ CVE-2018-0787
-There is a file `/Users/shed/Repos/my-repo/projects/my-app/Dockerfile`.
-`context` is set to the directory and `dockerfile` is explicitly set to `Dockerfile`.
+### Vulnerable Libraries - microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg, microsoft.aspnetcore.httpoverrides.2.0.0.nupkg
+
-### Output of `pulumi about`
-I don't want to copy/paste this from a work project. I'll try to provide specific info as requested if relevant.
+### microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
-### Additional context
+
Core components of ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
+
-Split from #566
+Dependency Hierarchy:
+ - dotnetcore-sample-1.0.0 (Root Library)
+ - microsoft.aspnetcore.2.0.0.nupkg
+ - microsoft.aspnetcore.server.kestrel.2.0.0.nupkg
+ - :x: **microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg** (Vulnerable Library)
-### Contributing
-Vote on this issue by adding a 👍 reaction.
-To contribute a fix for this issue, leave a comment (and link to your pull request, if you've opened one already).
-",0,docker index image could not open dockerfile at relative path dockerfile what happened upgraded from pulumi docker to pulumi up unexpectedly errors diagnostics docker index image my app latest error could not open dockerfile at relative path dockerfile try setting dockerfile to users shed repos my repo projects my app dockerfile expected behavior pulumi up to locate dockerfile relative to my project directory steps to reproduce my pulumi resource looks something like python image docker image my app latest build docker dockerbuildargs context users shed repos my repo projects my app dockerfile dockerfile args buildkit inline cache may not be necessary cache from docker cachefromargs images pulumi output concat repo repository url latest platform linux registry registry image name pulumi output concat self repo repository url latest there is a file users shed repos my repo projects my app dockerfile context is set to the directory and dockerfile is explicitly set to dockerfile output of pulumi about i don t want to copy paste this from a work project i ll try to provide specific info as requested if relevant additional context split from contributing vote on this issue by adding a 👍 reaction to contribute a fix for this issue leave a comment and link to your pull request if you ve opened one already ,0
-17959,10169183491.0,IssuesEvent,2019-08-07 23:19:28,dotnet/corefx,https://api.github.com/repos/dotnet/corefx,closed,ASN.1 Deserialize fails with SequenceOf strings,area-System.Security,"Let me preface this with the statement that I fully understand this is an internal-only API (for now at least). Nevertheless, this is a fairly important test case.
+### microsoft.aspnetcore.httpoverrides.2.0.0.nupkg
-Suppose an ASN.1 of
+
ASP.NET Core basic middleware for supporting HTTP method overrides. Includes:
+* X-Forwarded-* header...
+
-There are two issues here.
+
-1. GeneralString is not actually supported. You cannot futz your way through by decorating the struct field to think it's an IA5String. I had to add a new attribute and modified the deserializer to treat it the same as IA5String.
-2. SequenceOf GeneralString/IA5String cannot parse correctly *when there are multiple values in the sequence*.
+### Vulnerability Details
+
+
+ASP.NET Core 1.0. 1.1, and 2.0 allow an elevation of privilege vulnerability due to how web applications that are created from templates validate web requests, aka ""ASP.NET Core Elevation Of Privilege Vulnerability"".
-It decodes the array as a struct and throws because there's extra data. There's no way it can move on to the next element in the sequence. Conversely, you can't coerce the deserializer to operate against string[] because it can't be a SequenceOf and GeneralizedString/IA5String at the same time.
+
+For more information on CVSS3 Scores, click here.
+
-This will throw when it finishes reading the first string of `sname`. It'll complete the pass over the struct fields, but there's more data in the sequence.
+
-I think it would be helpful if you could decorate a `SequenceOf` as a specialized type, e.g. `GeneralizedString`.
+### Suggested Fix
+
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
+
- [ExpectedTag(1)]
- public KerberosString[] nameString;
+Dependency Hierarchy:
+ - dotnetcore-sample-1.0.0 (Root Library)
+ - microsoft.aspnetcore.2.0.0.nupkg
+ - microsoft.aspnetcore.server.kestrel.2.0.0.nupkg
+ - :x: **microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg** (Vulnerable Library)
- // this does not work either
- // [ExpectedTag(1), GeneralizedString]
- // public string[] nameString;
-}
-[StructLayout(LayoutKind.Sequential)]
-public struct KerberosString
-{
- [GeneralizedString]
- public string name;
-}
+### microsoft.aspnetcore.server.kestrel.transport.abstractions.2.0.0.nupkg
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.transport.abstractions/2.0.0/microsoft.aspnetcore.server.kestrel.transport.abstractions.2.0.0.nupkg
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.transport.libuv/2.0.0/microsoft.aspnetcore.server.kestrel.transport.libuv.2.0.0.nupkg
- [ExpectedTag(1, ExplicitTag = true), OctetString]
- public ReadOnlyMemory adData;
-}
+
-[StructLayout(LayoutKind.Sequential)]
-public struct Ticket { }
-```",True,"ASN.1 Deserialize fails with SequenceOf strings - Let me preface this with the statement that I fully understand this is an internal-only API (for now at least). Nevertheless, this is a fairly important test case.
+### Vulnerability Details
+
+
+A vulnerability was discovered in versions 2.x of ASP.NET Core where a specially crafted request can cause excess resource consumption in Kestrel.
-Suppose an ASN.1 of
+
+For more information on CVSS3 Scores, click here.
+
-There are two issues here.
+
-1. GeneralString is not actually supported. You cannot futz your way through by decorating the struct field to think it's an IA5String. I had to add a new attribute and modified the deserializer to treat it the same as IA5String.
-2. SequenceOf GeneralString/IA5String cannot parse correctly *when there are multiple values in the sequence*.
+### Suggested Fix
+
-It decodes the array as a struct and throws because there's extra data. There's no way it can move on to the next element in the sequence. Conversely, you can't coerce the deserializer to operate against string[] because it can't be a SequenceOf and GeneralizedString/IA5String at the same time.
+
+
+
-### Sample
+
-This will throw when it finishes reading the first string of `sname`. It'll complete the pass over the struct fields, but there's more data in the sequence.
+ CVE-2018-0808
-I think it would be helpful if you could decorate a `SequenceOf` as a specialized type, e.g. `GeneralizedString`.
-```c#
-var asReq = ""3081d3a103020105a20302010aa31530133011a10402020080a20904073005a0030101ffa481af30""
-+ ""81aca00703050040810010a1153013a003020101a10c300a1b087374737966756873a2091b07524""
-+ ""5444d4f4e44a31c301aa003020102a11330111b066b72627467741b075245444d4f4e44a511180f3""
-+ ""2303337303931333032343830355aa611180f32303337303931333032343830355aa70502036875""
-+ ""0da81530130201120201110201170201180202ff79020103a91d301b3019a003020114a11204104""
-+ ""d494e494e542d364a49454842472020"";
+### Vulnerable Libraries - microsoft.aspnetcore.server.iisintegration.2.0.0.nupkg, microsoft.aspnetcore.hosting.2.0.0.nupkg
+
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.iisintegration/2.0.0/microsoft.aspnetcore.server.iisintegration.2.0.0.nupkg
+
- // this does not work either
- // [ExpectedTag(1), GeneralizedString]
- // public string[] nameString;
-}
+
-[StructLayout(LayoutKind.Sequential)]
-public struct KerberosString
-{
- [GeneralizedString]
- public string name;
-}
+### Vulnerability Details
+
+
+ASP.NET Core 1.0. 1.1, and 2.0 allow an elevation of privilege vulnerability due to how ASP.NET web applications handle web requests, aka ""ASP.NET Core Elevation Of Privilege Vulnerability"". This CVE is unique from CVE-2018-0784.
-[StructLayout(LayoutKind.Sequential)]
-public struct HostAddress
-{
- // addr-type[0] Int32,
- // address[1] OCTET STRING
+
+For more information on CVSS3 Scores, click here.
+
- [ExpectedTag(0, ExplicitTag = true)]
- public int etype;
+
- [ExpectedTag(1, ExplicitTag = true), OptionalValue]
- public int kvno;
+### Suggested Fix
+
-[StructLayout(LayoutKind.Sequential)]
-public struct AuthorizationData
-{
- [ExpectedTag(0, ExplicitTag = true)]
- public int adType;
+
- [ExpectedTag(1, ExplicitTag = true), OctetString]
- public ReadOnlyMemory adData;
-}
+
-[StructLayout(LayoutKind.Sequential)]
-public struct Ticket { }
-```",0,asn deserialize fails with sequenceof strings let me preface this with the statement that i fully understand this is an internal only api for now at least nevertheless this is a fairly important test case suppose an asn of kdc req sequence sname principalname optional principalname sequence name type name string sequence of kerberosstring kerberosstring generalstring there are two issues here generalstring is not actually supported you cannot futz your way through by decorating the struct field to think it s an i had to add a new attribute and modified the deserializer to treat it the same as sequenceof generalstring cannot parse correctly when there are multiple values in the sequence it decodes the array as a struct and throws because there s extra data there s no way it can move on to the next element in the sequence conversely you can t coerce the deserializer to operate against string because it can t be a sequenceof and generalizedstring at the same time sample this will throw when it finishes reading the first string of sname it ll complete the pass over the struct fields but there s more data in the sequence i think it would be helpful if you could decorate a sequenceof as a specialized type e g generalizedstring c var asreq var req asnserializer deserialize stringtobytearray asreq asnencodingrules der public struct kdcreq as req kdc req tgs req kdc req kdc req sequence note first tag is not pvno integer msg type integer as tgs padata sequence of pa data optional note not empty req body kdc req body public int pvno public int msgtype public padata padata public kdcreqbody reqbody public struct padata padata type padata value octet string might be encoded ap req public int padatatype public readonlymemory padatavalue public struct kdcreqbody kdc options kdcoptions cname principalname optional used only in as req realm realm server s realm also client s in as req sname principalname optional from kerberostime optional till kerberostime rtime kerberostime optional nonce etype sequence of encryptiontype in preference order addresses hostaddresses optional enc authorization data encrypteddata optional authorizationdata additional tickets sequence of ticket optional note not empty public readonlymemory kdcoptions public principalname cname public kerberosstring realm public principalname sname public datetimeoffset from public datetimeoffset till public datetimeoffset rtime public uint nonce public int etype public hostaddress addresses public encrypteddata encauthorizationdata public ticket additionaltickets public struct principalname name type name string sequence of kerberosstring public int nametype public kerberosstring namestring this does not work either public string namestring public struct kerberosstring public string name public struct hostaddress addr type address octet string public int addrtype public readonlymemory address public struct encrypteddata encrypteddata sequence etype encryptiontype kvno optional cipher octet string ciphertext public int etype public int kvno public readonlymemory cipher public struct authorizationdata public int adtype public readonlymemory addata public struct ticket ,0
-134101,18421805849.0,IssuesEvent,2021-10-13 16:56:27,daniel-brown-ws-test/verademo,https://api.github.com/repos/daniel-brown-ws-test/verademo,opened,CVE-2019-11358 (Medium) detected in jquery-1.11.2.min.js,security vulnerability,"## CVE-2019-11358 - Medium Severity Vulnerability
- Vulnerable Library - jquery-1.11.2.min.js
+
-
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
-jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.
+Denial of service vulnerability in ASP.NET Core when a malformed request is terminated.
-
-jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.
+A security feature bypass vulnerability exists in the way Microsoft ASP.NET Core parses encoded cookie names.The ASP.NET Core cookie parser decodes entire cookie strings which could allow a malicious attacker to set a second cookie with the name being percent encoded.The security update addresses the vulnerability by fixing the way the ASP.NET Core cookie parser handles encoded names., aka 'Microsoft ASP.NET Core Security Feature Bypass Vulnerability'.
-
-
+
-",0,cve medium detected in jquery min js cve medium severity vulnerability vulnerable library jquery min js javascript library for dom operations library home page a href path to vulnerable library app src main webapp resources js jquery min js dependency hierarchy x jquery min js vulnerable library found in head commit a href found in base branch main vulnerability details jquery before as used in drupal backdrop cms and other products mishandles jquery extend true because of object prototype pollution if an unsanitized source object contained an enumerable proto property it could extend the native object prototype publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution isopenpronvulnerability true ispackagebased true isdefaultbranch true packages istransitivedependency false dependencytree jquery isminimumfixversionavailable true minimumfixversion basebranches vulnerabilityidentifier cve vulnerabilitydetails jquery before as used in drupal backdrop cms and other products mishandles jquery extend true because of object prototype pollution if an unsanitized source object contained an enumerable proto property it could extend the native object prototype vulnerabilityurl ,0
-200289,22750029949.0,IssuesEvent,2022-07-07 12:26:24,mixcore/mix.core,https://api.github.com/repos/mixcore/mix.core,closed,(CS-A1008) Audit required: Insecurely generated random number,security vulnerability,"## Description
-`Random` is a pseudo-random number generator, which is an algorithm that produces a sequence of numbers that meet certain statistical requirements for randomness. Because the number generated is not random enough for sensitive operations, consider using `RandomNumberGenerator` from `System.Security.Cryptography` namespace instead.
+
-## Occurrences
-There are 4 occurrences of this issue in the repository.
+ CVE-2021-1723
-See all occurrences on DeepSource → [deepsource.io/gh/mixcore/mix.core/issue/CS-A1008/occurrences/](https://deepsource.io/gh/mixcore/mix.core/issue/CS-A1008/occurrences/)
-",True,"(CS-A1008) Audit required: Insecurely generated random number - ## Description
-`Random` is a pseudo-random number generator, which is an algorithm that produces a sequence of numbers that meet certain statistical requirements for randomness. Because the number generated is not random enough for sensitive operations, consider using `RandomNumberGenerator` from `System.Security.Cryptography` namespace instead.
-## Occurrences
-There are 4 occurrences of this issue in the repository.
+### Vulnerable Library - microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
-See all occurrences on DeepSource → [deepsource.io/gh/mixcore/mix.core/issue/CS-A1008/occurrences/](https://deepsource.io/gh/mixcore/mix.core/issue/CS-A1008/occurrences/)
-",0, cs audit required insecurely generated random number description random is a pseudo random number generator which is an algorithm that produces a sequence of numbers that meet certain statistical requirements for randomness because the number generated is not random enough for sensitive operations consider using randomnumbergenerator from system security cryptography namespace instead occurrences there are occurrences of this issue in the repository see all occurrences on deepsource rarr ,0
-75395,7470580859.0,IssuesEvent,2018-04-03 05:55:43,zalando/zalenium,https://api.github.com/repos/zalando/zalenium,closed,Can't choose chrome's language ,waiting-retest,"**Please make sure that you provide enough information for us to help you with this issue. Thank you!**
+
Core components of ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
+
-Zalenium Image Version(s):
-""dosel/zalenium:latest""
-If using docker-compose, version:
-
-OS:
-
-Docker Command to start Zalenium:
-
-version: '2'
+
-services:
-
- zalenium:
- image: ""dosel/zalenium:latest""
- container_name: zalenium
- hostname: zalenium
- tty: true
- volumes:
- - /tmp/videos:/home/seluser/videos
- - /var/run/docker.sock:/var/run/docker.sock
- - /usr/bin/docker:/usr/bin/docker
- ports:
- - 4444:4444
- extra_hosts:
- - ""myapp.mydomain.fr:172.25.0.10""
- command: >
- start --desiredContainers 2
- --maxDockerSeleniumContainers 8
- --screenWidth 1680 --screenHeight 1050
- --timeZone ""Europe/Paris""
- --videoRecordingEnabled true
- --sauceLabsEnabled false
- --browserStackEnabled false
- --testingBotEnabled false
- --startTunnel false
- environment:
- - HOST_UID
- - HOST_GID
- - SAUCE_USERNAME
- - SAUCE_ACCESS_KEY
- - BROWSER_STACK_USER
- - BROWSER_STACK_KEY
- - TESTINGBOT_KEY
- - TESTINGBOT_SECRET
- - LANG=fr_FR.UTF-8
- - LANGUAGE=fr_FR.UTF-8
- - LC_ALL=fr_FR.UTF-8
- networks:
- mynet:
- ipv4_address: 172.25.0.15
-
-
-I set :
-chromeOptions.addArguments(""lang=fr_FR"");
-capability.setCapability(ChromeOptions.CAPABILITY, chromeOptions);
-before invoke webdrvier :
-new RemoteWebDriver(new URL(this.hubUrl), capability);
-
-My browser is always in english and not take arguement ""lang=fr""
-
-Thank's for you help and sorry for by bad english :) ",1.0,"Can't choose chrome's language - **Please make sure that you provide enough information for us to help you with this issue. Thank you!**
-
-
-
-Zalenium Image Version(s):
-""dosel/zalenium:latest""
-If using docker-compose, version:
-
-OS:
-
-Docker Command to start Zalenium:
-
-version: '2'
-
-services:
+### Vulnerability Details
+
- zalenium:
- image: ""dosel/zalenium:latest""
- container_name: zalenium
- hostname: zalenium
- tty: true
- volumes:
- - /tmp/videos:/home/seluser/videos
- - /var/run/docker.sock:/var/run/docker.sock
- - /usr/bin/docker:/usr/bin/docker
- ports:
- - 4444:4444
- extra_hosts:
- - ""myapp.mydomain.fr:172.25.0.10""
- command: >
- start --desiredContainers 2
- --maxDockerSeleniumContainers 8
- --screenWidth 1680 --screenHeight 1050
- --timeZone ""Europe/Paris""
- --videoRecordingEnabled true
- --sauceLabsEnabled false
- --browserStackEnabled false
- --testingBotEnabled false
- --startTunnel false
- environment:
- - HOST_UID
- - HOST_GID
- - SAUCE_USERNAME
- - SAUCE_ACCESS_KEY
- - BROWSER_STACK_USER
- - BROWSER_STACK_KEY
- - TESTINGBOT_KEY
- - TESTINGBOT_SECRET
- - LANG=fr_FR.UTF-8
- - LANGUAGE=fr_FR.UTF-8
- - LC_ALL=fr_FR.UTF-8
- networks:
- mynet:
- ipv4_address: 172.25.0.15
-
-
-I set :
-chromeOptions.addArguments(""lang=fr_FR"");
-capability.setCapability(ChromeOptions.CAPABILITY, chromeOptions);
-before invoke webdrvier :
-new RemoteWebDriver(new URL(this.hubUrl), capability);
-
-My browser is always in english and not take arguement ""lang=fr""
-
-Thank's for you help and sorry for by bad english :) ",0,can t choose chrome s language please make sure that you provide enough information for us to help you with this issue thank you zalenium image version s dosel zalenium latest if using docker compose version os docker command to start zalenium version services zalenium image dosel zalenium latest container name zalenium hostname zalenium tty true volumes tmp videos home seluser videos var run docker sock var run docker sock usr bin docker usr bin docker ports extra hosts myapp mydomain fr command start desiredcontainers maxdockerseleniumcontainers screenwidth screenheight timezone europe paris videorecordingenabled true saucelabsenabled false browserstackenabled false testingbotenabled false starttunnel false environment host uid host gid sauce username sauce access key browser stack user browser stack key testingbot key testingbot secret lang fr fr utf language fr fr utf lc all fr fr utf networks mynet address i set chromeoptions addarguments lang fr fr capability setcapability chromeoptions capability chromeoptions before invoke webdrvier new remotewebdriver new url this huburl capability my browser is always in english and not take arguement lang fr thank s for you help and sorry for by bad english ,0
-12228,14442108234.0,IssuesEvent,2020-12-07 17:41:07,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,parser: STRAIGHT_JOIN and SQL_SMALL_RESULT cannot be used at the same time,component/parser severity/moderate type/bug type/compatibility type/duplicate,"## Bug Report
+ASP.NET Core and Visual Studio Denial of Service Vulnerability
-Please answer these questions before submitting your issue. Thanks!
+
+
-1. What did you do?
-```
-create table t;
-insert into t values(1);
-```
-2. What did you expect to see?
-Results from Mysql:
-```
-mysql> select STRAIGHT_JOIN SQL_SMALL_RESULT count(*) from t;
-+----------+
-| count(*) |
-+----------+
-| 1 |
-+----------+
-1 row in set (0.00 sec)
-```
+
-3. What did you see instead?
-Results: from TiDB:
-```
-select STRAIGHT_JOIN SQL_SMALL_RESULT count(*) from t;
-ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your TiDB version for the right syntax to use line 1 column 37 near ""SQL_SMALL_RESULT count(*) from t""
-```
+### CVSS 3 Score Details (7.5)
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-[tidb@VM2 bin]$ ./tidb-server -V
-2019-11-26 18:27:18.059136 I | maxprocs: Leaving GOMAXPROCS=8: CPU quota undefined
-Release Version:
-Git Commit Hash:
-Git Branch:
-UTC Build Time: 2019-11-22 02:54:53
-GoVersion: go version go1.13.3 linux/amd64
-Race Enabled: false
-TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
-Check Table Before Drop: false
-",True,"parser: STRAIGHT_JOIN and SQL_SMALL_RESULT cannot be used at the same time - ## Bug Report
-
-Please answer these questions before submitting your issue. Thanks!
-
-1. What did you do?
-```
-create table t;
-insert into t values(1);
-```
-2. What did you expect to see?
-Results from Mysql:
-```
-mysql> select STRAIGHT_JOIN SQL_SMALL_RESULT count(*) from t;
-+----------+
-| count(*) |
-+----------+
-| 1 |
-+----------+
-1 row in set (0.00 sec)
-```
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Network
+ - Attack Complexity: Low
+ - Privileges Required: None
+ - User Interaction: None
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: None
+ - Integrity Impact: None
+ - Availability Impact: High
+
+For more information on CVSS3 Scores, click here.
+
-3. What did you see instead?
-Results: from TiDB:
-```
-select STRAIGHT_JOIN SQL_SMALL_RESULT count(*) from t;
-ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your TiDB version for the right syntax to use line 1 column 37 near ""SQL_SMALL_RESULT count(*) from t""
-```
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-[tidb@VM2 bin]$ ./tidb-server -V
-2019-11-26 18:27:18.059136 I | maxprocs: Leaving GOMAXPROCS=8: CPU quota undefined
-Release Version:
-Git Commit Hash:
-Git Branch:
-UTC Build Time: 2019-11-22 02:54:53
-GoVersion: go version go1.13.3 linux/amd64
-Race Enabled: false
-TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
-Check Table Before Drop: false
-",1,parser straight join and sql small result cannot be used at the same time bug report please answer these questions before submitting your issue thanks what did you do create table t insert into t values what did you expect to see results from mysql mysql select straight join sql small result count from t count row in set sec what did you see instead results from tidb select straight join sql small result count from t error you have an error in your sql syntax check the manual that corresponds to your tidb version for the right syntax to use line column near sql small result count from t what version of tidb are you using tidb server v or run select tidb version on tidb tidb server v i maxprocs leaving gomaxprocs cpu quota undefined release version git commit hash git branch utc build time goversion go version linux race enabled false tikv min version check table before drop false ,1
-136962,20023377990.0,IssuesEvent,2022-02-01 18:32:44,psf/black,https://api.github.com/repos/psf/black,reopened,Line splitting on conditional operators should take precendence over splitting on function parameters,R: duplicate T: design F: linebreak,"Black should split conditionals at conditional operators (i.e. `and`, `or`, etc.) when possible, instead of splitting function parameters over multiple lines.
+### Suggested Fix
+
-Currently, this is how black formats a long conditional:
-```
-if str(
- self.user.id
-) != self.target_user_id and not CheckUserManagementViewPermission.user_has_permission(
- self.user
-):
- pass
-```
+
-Ideally, it should be formatted like this:
-```
-if (
- str(self.user.id) != self.target_user_id
- and not CheckUserManagementViewPermission.user_has_permission(
- self.user
- )
-):
- pass
-```
+
-This appears to be a general issue with splitting conditionals and it looks like it's related to these issues: https://github.com/psf/black/issues/815 https://github.com/psf/black/issues/1050",1.0,"Line splitting on conditional operators should take precendence over splitting on function parameters - Black should split conditionals at conditional operators (i.e. `and`, `or`, etc.) when possible, instead of splitting function parameters over multiple lines.
+
-Currently, this is how black formats a long conditional:
-```
-if str(
- self.user.id
-) != self.target_user_id and not CheckUserManagementViewPermission.user_has_permission(
- self.user
-):
- pass
-```
+
-Ideally, it should be formatted like this:
-```
-if (
- str(self.user.id) != self.target_user_id
- and not CheckUserManagementViewPermission.user_has_permission(
- self.user
- )
-):
- pass
-```
+ CVE-2022-34716
-This appears to be a general issue with splitting conditionals and it looks like it's related to these issues: https://github.com/psf/black/issues/815 https://github.com/psf/black/issues/1050",0,line splitting on conditional operators should take precendence over splitting on function parameters black should split conditionals at conditional operators i e and or etc when possible instead of splitting function parameters over multiple lines currently this is how black formats a long conditional if str self user id self target user id and not checkusermanagementviewpermission user has permission self user pass ideally it should be formatted like this if str self user id self target user id and not checkusermanagementviewpermission user has permission self user pass this appears to be a general issue with splitting conditionals and it looks like it s related to these issues ,0
-5611,5092861751.0,IssuesEvent,2017-01-03 00:20:01,tfussell/xlnt,https://api.github.com/repos/tfussell/xlnt,closed,Create some performance benchmarks,performance,"- Speed in terms of cells written/read per second.
-- Memory usage per cell/row/column/sheet.
-- Time needed to make an identical copy of a large XLSX file.
-- Are there standard benchmarks that other libraries are using?
-",True,"Create some performance benchmarks - - Speed in terms of cells written/read per second.
-- Memory usage per cell/row/column/sheet.
-- Time needed to make an identical copy of a large XLSX file.
-- Are there standard benchmarks that other libraries are using?
-",0,create some performance benchmarks speed in terms of cells written read per second memory usage per cell row column sheet time needed to make an identical copy of a large xlsx file are there standard benchmarks that other libraries are using ,0
-130282,12425976728.0,IssuesEvent,2020-05-24 18:53:58,P3rf3ctXZer0/mc-1.15.2-Pokecube-Evolved,https://api.github.com/repos/P3rf3ctXZer0/mc-1.15.2-Pokecube-Evolved,closed,Twitch Launcher Keeps Glitching Updating PamsTrees2,documentation,Make sure before exporting packs you check to see if pams trees 2 is in the mods,1.0,Twitch Launcher Keeps Glitching Updating PamsTrees2 - Make sure before exporting packs you check to see if pams trees 2 is in the mods,0,twitch launcher keeps glitching updating make sure before exporting packs you check to see if pams trees is in the mods,0
-39917,5256532271.0,IssuesEvent,2017-02-02 18:10:56,cul-2016/quiz,https://api.github.com/repos/cul-2016/quiz,closed,Previewed quiz set to 'already run',bug please-test priority-1,"To replicate:
-1. Add a new quiz with at least one question
-2. Preview quiz all the way through, returning to module overview page
-3. Do something else: E.g., go to edit quiz page, or do manual refresh of module overview page, then return to module overview page
+### Vulnerable Library - system.security.cryptography.xml.4.4.0.nupkg
-The previewed quiz is now shown as having been run, and cannot be run again.",1.0,"Previewed quiz set to 'already run' - To replicate:
+
Provides classes to support the creation and validation of XML digital signatures. The classes in th...
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
+
Path to vulnerable library: /home/wss-scanner/.nuget/packages/system.security.cryptography.xml/4.4.0/system.security.cryptography.xml.4.4.0.nupkg
+
-1. Add a new quiz with at least one question
-2. Preview quiz all the way through, returning to module overview page
-3. Do something else: E.g., go to edit quiz page, or do manual refresh of module overview page, then return to module overview page
+Dependency Hierarchy:
+ - dotnetcore-sample-1.0.0 (Root Library)
+ - microsoft.aspnetcore.mvc.2.0.0.nupkg
+ - microsoft.aspnetcore.mvc.viewfeatures.2.0.0.nupkg
+ - microsoft.aspnetcore.antiforgery.2.0.0.nupkg
+ - microsoft.aspnetcore.dataprotection.2.0.0.nupkg
+ - :x: **system.security.cryptography.xml.4.4.0.nupkg** (Vulnerable Library)
+
+
-The previewed quiz is now shown as having been run, and cannot be run again.",0,previewed quiz set to already run to replicate add a new quiz with at least one question preview quiz all the way through returning to module overview page do something else e g go to edit quiz page or do manual refresh of module overview page then return to module overview page the previewed quiz is now shown as having been run and cannot be run again ,0
-11861,13995564192.0,IssuesEvent,2020-10-28 03:36:04,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Support multiple table rename (swap table use case),challenge-program difficulty/medium high-performance picked sig/DDL type/compatibility type/enhancement,"## Feature Request
+
-**Is your feature request related to a problem? Please describe:**
+### Vulnerability Details
+
+
+Microsoft is releasing this security advisory to provide information about a vulnerability in .NET Core 3.1 and .NET 6.0. An information disclosure vulnerability exists in .NET Core 3.1 and .NET 6.0 that could lead to unauthorized access of privileged information.
-I know that multiple DDL changes are currently on the roadmap. My feature request is to support a much smaller subset, which is an atomic rename of two tables.
+## Affected software
-This supports the use case of swapping tables, something that occurs frequently in the replication stream due to its usage by tools such as `pt-online-schema-change`.
+* Any .NET 6.0 application running on .NET 6.0.7 or earlier.
+* Any .NET Core 3.1 applicaiton running on .NET Core 3.1.27 or earlier.
-**Describe the feature you'd like:**
+## Patches
-```
-mysql> CREATE TABLE t1 (a int);
-Query OK, 0 rows affected (0.01 sec)
+* If you're using .NET 6.0, you should download and install Runtime 6.0.8 or SDK 6.0.108 (for Visual Studio 2022 v17.1) from https://dotnet.microsoft.com/download/dotnet-core/6.0.
+* If you're using .NET Core 3.1, you should download and install Runtime 3.1.28 (for Visual Studio 2019 v16.9) from https://dotnet.microsoft.com/download/dotnet-core/3.1.
-mysql> CREATE TABLE t2 (a int, b int);
-Query OK, 0 rows affected (0.01 sec)
+
+
-mysql> RENAME TABLE t1 to t1_old, t2 to t1; <--- should work
-ERROR 1105 (HY000): can't run multi schema change
-```
+
-**Describe alternatives you've considered:**
+### CVSS 3 Score Details (5.9)
+
-The alternative is to do this non-atomically (breaks apps) or under a global lock (not yet supported by TiDB). So there is not really a good alternative.
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Network
+ - Attack Complexity: High
+ - Privileges Required: None
+ - User Interaction: None
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: High
+ - Integrity Impact: None
+ - Availability Impact: None
+
+For more information on CVSS3 Scores, click here.
+
-**Teachability, Documentation, Adoption, Migration Strategy:**
+
-MySQL compatible behavior.
+### Suggested Fix
+
-## SIG Slack Channel
-You can join [#sig-ddl ](https://app.slack.com/client/TH91JCS4W/CMAKWBNJU)on slack in your spare time to discuss and get help with mentors or others.
+
-## Mentor(s)
-* @zimulala
+
-## Recommended Skills
-* DDL
-* Golang
+",0,dotnetcore sample vulnerabilities highest severity is autoclosed vulnerable library dotnetcore sample path to vulnerable library home wss scanner nuget packages system security cryptography xml system security cryptography xml nupkg found in head commit a href vulnerabilities cve severity cvss dependency type fixed in dotnetcore sample version remediation available high detected in multiple dependencies transitive n a high detected in multiple dependencies transitive n a high detected in multiple dependencies transitive n a high microsoft aspnetcore server kestrel core nupkg transitive n a high microsoft aspnetcore http nupkg transitive n a high microsoft aspnetcore server kestrel core nupkg transitive n a medium system security cryptography xml nupkg transitive n a for some transitive vulnerabilities there is no version of direct dependency with a fix check the section details below to see if there is a version of transitive dependency where vulnerability is fixed details cve vulnerable libraries microsoft aspnetcore server kestrel core nupkg microsoft aspnetcore httpoverrides nupkg microsoft aspnetcore server kestrel core nupkg core components of asp net core kestrel cross platform web server library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore server kestrel core microsoft aspnetcore server kestrel core nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg x microsoft aspnetcore server kestrel core nupkg vulnerable library microsoft aspnetcore httpoverrides nupkg asp net core basic middleware for supporting http method overrides includes x forwarded header library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore httpoverrides microsoft aspnetcore httpoverrides nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server iisintegration nupkg x microsoft aspnetcore httpoverrides nupkg vulnerable library found in head commit a href found in base branch main vulnerability details asp net core and allow an elevation of privilege vulnerability due to how web applications that are created from templates validate web requests aka asp net core elevation of privilege vulnerability publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution microsoft aspnetcore httpoverrides microsoft aspnetcore server kestrel core ws vulnerable libraries microsoft aspnetcore server kestrel core nupkg microsoft aspnetcore server kestrel transport abstractions nupkg microsoft aspnetcore server kestrel transport libuv nupkg microsoft aspnetcore server kestrel core nupkg core components of asp net core kestrel cross platform web server library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore server kestrel core microsoft aspnetcore server kestrel core nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg x microsoft aspnetcore server kestrel core nupkg vulnerable library microsoft aspnetcore server kestrel transport abstractions nupkg transport abstractions for the asp net core kestrel cross platform web server library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore server kestrel transport abstractions microsoft aspnetcore server kestrel transport abstractions nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg microsoft aspnetcore server kestrel transport libuv nupkg x microsoft aspnetcore server kestrel transport abstractions nupkg vulnerable library microsoft aspnetcore server kestrel transport libuv nupkg libuv transport for the asp net core kestrel cross platform web server library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore server kestrel transport libuv microsoft aspnetcore server kestrel transport libuv nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg x microsoft aspnetcore server kestrel transport libuv nupkg vulnerable library found in head commit a href found in base branch main vulnerability details a vulnerability was discovered in versions x of asp net core where a specially crafted request can cause excess resource consumption in kestrel publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution microsoft aspnetcore server kestrel core microsoft aspnetcore server kestrel transport abstractions microsoft aspnetcore server kestrel transport libuv microsoft aspnetcore all cve vulnerable libraries microsoft aspnetcore server iisintegration nupkg microsoft aspnetcore hosting nupkg microsoft aspnetcore server iisintegration nupkg asp net core components for working with the iis aspnetcoremodule library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore server iisintegration microsoft aspnetcore server iisintegration nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg x microsoft aspnetcore server iisintegration nupkg vulnerable library microsoft aspnetcore hosting nupkg asp net core hosting infrastructure and startup logic for web applications library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore hosting microsoft aspnetcore hosting nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg x microsoft aspnetcore hosting nupkg vulnerable library found in head commit a href found in base branch main vulnerability details asp net core and allow an elevation of privilege vulnerability due to how asp net web applications handle web requests aka asp net core elevation of privilege vulnerability this cve is unique from cve publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution microsoft aspnetcore server iisintegration microsoft aspnetcore hosting ws vulnerable library microsoft aspnetcore server kestrel core nupkg core components of asp net core kestrel cross platform web server library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore server kestrel core microsoft aspnetcore server kestrel core nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg x microsoft aspnetcore server kestrel core nupkg vulnerable library found in head commit a href found in base branch main vulnerability details denial of service vulnerability in asp net core when a malformed request is terminated publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution microsoft aspnetcore server kestrel core cve vulnerable library microsoft aspnetcore http nupkg asp net core default http feature implementations library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore http microsoft aspnetcore http nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg microsoft aspnetcore hosting nupkg x microsoft aspnetcore http nupkg vulnerable library found in head commit a href found in base branch main vulnerability details a security feature bypass vulnerability exists in the way microsoft asp net core parses encoded cookie names the asp net core cookie parser decodes entire cookie strings which could allow a malicious attacker to set a second cookie with the name being percent encoded the security update addresses the vulnerability by fixing the way the asp net core cookie parser handles encoded names aka microsoft asp net core security feature bypass vulnerability publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact high availability impact none for more information on scores click a href suggested fix type upgrade version release date fix resolution microsoft aspnetcore app microsoft aspnetcore all microsoft netcore app microsoft aspnetcore http cve vulnerable library microsoft aspnetcore server kestrel core nupkg core components of asp net core kestrel cross platform web server library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore server kestrel core microsoft aspnetcore server kestrel core nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg x microsoft aspnetcore server kestrel core nupkg vulnerable library found in head commit a href found in base branch main vulnerability details asp net core and visual studio denial of service vulnerability publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution microsoft aspnetcore app runtime win livereloadserver plugga core maple branch module microsoft aspnetcore components webassembly server rc aspnetcoreruntime aspnetcoreruntime microsoft aspnetcore app runtime osx grazedocs microsoft aspnetcore app runtime linux musl arm microsoft aspnetcore app runtime linux musl yhwins template microsoft aspnetcore app runtime linux musl microsoft aspnetcore app runtime linux microsoft aspnetcore app ref rc microsoft aspnetcore blazor devserver microsoft aspnetcore app runtime linux arm microsoft aspnetcore app runtime linux stankins console toolbelt blazor devserver withcsslivereloader rc dragonfire server alpha poextractor orchardcore microsoft aspnetcore app runtime win arm microsoft aspnetcore app runtime win microsoft aspnetcore app runtime win hulu template api aspnetcoreruntime aspnetcoreruntime microsoft aspnetcore components webassembly devserver rc microsoft aspnetcore app runtime win lingman webapi cve vulnerable library system security cryptography xml nupkg provides classes to support the creation and validation of xml digital signatures the classes in th library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages system security cryptography xml system security cryptography xml nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore mvc nupkg microsoft aspnetcore mvc viewfeatures nupkg microsoft aspnetcore antiforgery nupkg microsoft aspnetcore dataprotection nupkg x system security cryptography xml nupkg vulnerable library found in head commit a href found in base branch main vulnerability details microsoft is releasing this security advisory to provide information about a vulnerability in net core and net an information disclosure vulnerability exists in net core and net that could lead to unauthorized access of privileged information affected software any net application running on net or earlier any net core applicaiton running on net core or earlier patches if you re using net you should download and install runtime or sdk for visual studio from if you re using net core you should download and install runtime for visual studio from publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact none availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution microsoft aspnetcore app runtime linux arm microsoft aspnetcore app runtime linux microsoft aspnetcore app runtime linux musl arm microsoft aspnetcore app runtime linux musl microsoft aspnetcore app runtime linux musl microsoft aspnetcore app runtime linux microsoft aspnetcore app runtime osx microsoft aspnetcore app runtime win arm microsoft aspnetcore app runtime win microsoft aspnetcore app runtime win microsoft aspnetcore app runtime win system security cryptography xml ,0
+19269,26766613367.0,IssuesEvent,2023-01-31 11:05:57,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Column names incorrect when using a non default delimiter,type/compatibility sig/sql-infra type/feature-request severity/minor compatibility-mysql8 affects-6.4 affects-6.5,"## Bug Report
+
+This is with MySQL Shell 8.0 as client. I would expect that this also happens with MySQL Client.
+
+```
+sql> delimiter $$
+
+sql> SELECT 1; SELECT 2; $$
++--------------+
+| 1; SELECT 2; |
++--------------+
+| 1 |
++--------------+
+1 row in set (0.0004 sec)
+
++----+
+| 2; |
++----+
+| 2 |
++----+
+1 row in set (0.0004 sec)
+
+sql> SELECT 1 AS 'a'; SELECT 2 AS 'b'; $$
++---+
+| a |
++---+
+| 1 |
++---+
+1 row in set (0.0004 sec)
+
++---+
+| b |
++---+
+| 2 |
++---+
+1 row in set (0.0004 sec)
+
+sql> delimiter ;
+
+sql> SELECT tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v6.4.0
+Edition: Community
+Git Commit Hash: cf36a9ce2fe1039db3cf3444d51930b887df18a1
+Git Branch: heads/refs/tags/v6.4.0
+UTC Build Time: 2022-11-13 05:25:30
+GoVersion: go1.19.2
+Race Enabled: false
+TiKV Min Version: 6.2.0-alpha
+Check Table Before Drop: false
+Store: tikv
+1 row in set (0.0003 sec)
+```
+
+I expected this to have the same column names as when the default delimiter is used:
+```
+sql> SELECT 1; SELECT 2;
++---+
+| 1 |
++---+
+| 1 |
++---+
+1 row in set (0.0006 sec)
++---+
+| 2 |
++---+
+| 2 |
++---+
+1 row in set (0.0002 sec)
+```",True,"Column names incorrect when using a non default delimiter - ## Bug Report
+
+This is with MySQL Shell 8.0 as client. I would expect that this also happens with MySQL Client.
+
+```
+sql> delimiter $$
+
+sql> SELECT 1; SELECT 2; $$
++--------------+
+| 1; SELECT 2; |
++--------------+
+| 1 |
++--------------+
+1 row in set (0.0004 sec)
+
++----+
+| 2; |
++----+
+| 2 |
++----+
+1 row in set (0.0004 sec)
+
+sql> SELECT 1 AS 'a'; SELECT 2 AS 'b'; $$
++---+
+| a |
++---+
+| 1 |
++---+
+1 row in set (0.0004 sec)
+
++---+
+| b |
++---+
+| 2 |
++---+
+1 row in set (0.0004 sec)
+
+sql> delimiter ;
+
+sql> SELECT tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v6.4.0
+Edition: Community
+Git Commit Hash: cf36a9ce2fe1039db3cf3444d51930b887df18a1
+Git Branch: heads/refs/tags/v6.4.0
+UTC Build Time: 2022-11-13 05:25:30
+GoVersion: go1.19.2
+Race Enabled: false
+TiKV Min Version: 6.2.0-alpha
+Check Table Before Drop: false
+Store: tikv
+1 row in set (0.0003 sec)
+```
+
+I expected this to have the same column names as when the default delimiter is used:
+```
+sql> SELECT 1; SELECT 2;
++---+
+| 1 |
++---+
+| 1 |
++---+
+1 row in set (0.0006 sec)
++---+
+| 2 |
++---+
+| 2 |
++---+
+1 row in set (0.0002 sec)
+```",1,column names incorrect when using a non default delimiter bug report this is with mysql shell as client i would expect that this also happens with mysql client sql delimiter sql select select select row in set sec row in set sec sql select as a select as b a row in set sec b row in set sec sql delimiter sql select tidb version g row tidb version release version edition community git commit hash git branch heads refs tags utc build time goversion race enabled false tikv min version alpha check table before drop false store tikv row in set sec i expected this to have the same column names as when the default delimiter is used sql select select row in set sec row in set sec ,1
+38730,5002728904.0,IssuesEvent,2016-12-11 15:08:59,HeitzmanCo/ChristChurchRaleigh-Theme,https://api.github.com/repos/HeitzmanCo/ChristChurchRaleigh-Theme,closed,Put the blue bar back.,design,I like it. Can I see the one with the circle in the middle (where the chicken goes?),1.0,Put the blue bar back. - I like it. Can I see the one with the circle in the middle (where the chicken goes?),0,put the blue bar back i like it can i see the one with the circle in the middle where the chicken goes ,0
+170429,14260029849.0,IssuesEvent,2020-11-20 09:13:49,jfm1006/GESPRO_PracticaGestionTareas_2021,https://api.github.com/repos/jfm1006/GESPRO_PracticaGestionTareas_2021,closed,Pasar anexos a latex,documentation," **Anexos**
+- [x] Plan del proyecto software
+- [x] Especificación de Requisitos
+- [x] Especificación de diseño
+- [x] Manual del programador
+- [x] Manual de usuario
+
+Expresión regular para corregir las referencias:
+
+- Buscar: (\{\[\})([\w:\\]+)(\{\]\}\\\_)
+- Reemplazar por: \\citep{\2}
+
+Ej: {[}art:campbell2005{]}\_ -> \citep{art:campbell2005}
+
+Expresión regular para corregir las imágenes:
+
+- Buscar: (\\includegraphics{..\/..\/img\/)(\w*)(.\w*\})
+- Reemplazar por: \\imagen{\2}{descripción...}
+
+Ej: \includegraphics{../../img/s2.png} -> \imagen{s2}{descripción...}}",1.0,"Pasar anexos a latex - **Anexos**
+- [x] Plan del proyecto software
+- [x] Especificación de Requisitos
+- [x] Especificación de diseño
+- [x] Manual del programador
+- [x] Manual de usuario
+
+Expresión regular para corregir las referencias:
+
+- Buscar: (\{\[\})([\w:\\]+)(\{\]\}\\\_)
+- Reemplazar por: \\citep{\2}
+
+Ej: {[}art:campbell2005{]}\_ -> \citep{art:campbell2005}
+
+Expresión regular para corregir las imágenes:
+
+- Buscar: (\\includegraphics{..\/..\/img\/)(\w*)(.\w*\})
+- Reemplazar por: \\imagen{\2}{descripción...}
+
+Ej: \includegraphics{../../img/s2.png} -> \imagen{s2}{descripción...}}",0,pasar anexos a latex anexos plan del proyecto software especificación de requisitos especificación de diseño manual del programador manual de usuario expresión regular para corregir las referencias buscar reemplazar por citep ej citep art expresión regular para corregir las imágenes buscar includegraphics img w w reemplazar por imagen descripción ej includegraphics img png imagen descripción ,0
+16349,22037681061.0,IssuesEvent,2022-05-28 21:22:50,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,no warning info for config deleted and change to system variable,type/bug type/compatibility component/config sig/sql-infra severity/moderate may-affects-4.0 may-affects-5.1 may-affects-5.2 may-affects-5.3 may-affects-5.4 may-affects-5.0 may-affects-6.0 affects-6.1,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+1. install v6.0.0 include following config:
+server_configs:
+ tidb:
+ enable-batch-dml: true
+ experimental.enable-global-kill: false
+ log.query-log-max-len: 4000
+ mem-quota-query: 0
+ oom-action: log
+ performance.committer-concurrency: 120
+ performance.run-auto-analyze: true
+ performance.txn-entry-size-limit: 6000000
+ performance.txn-total-size-limit: 6000000
+ prepared-plan-cache.capacity: 2000
+ prepared-plan-cache.enabled: true
+ security.require-secure-transport: false
+2. upgrade to v6.1.0 nightly
+
+### 2. What did you expect to see? (Required)
+according to the discussion with PM, when the old cluster includes the above configs, during upgrade, the tidb node should report
+a warning to tell the user that these configs have been deleted and converted to system variables.
+
+### 3. What did you see instead (Required)
+no waring found
++ [ Serial ] - InitConfig: cluster=local, user=tidb, host=172.16.5.101, path=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache/tidb-4000.service, deploy_dir=/home/tidb/deploy/tidb-4000, data_dir=[], log_dir=/home/tidb/deploy/tidb-4000/log, cache_dir=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache
++ [ Serial ] - InitConfig: cluster=local, user=tidb, host=172.16.5.101, path=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache/tidb-14000.service, deploy_dir=/home/tidb/deploy/tidb-14000, data_dir=[], log_dir=/home/tidb/deploy/tidb-14000/log, cache_dir=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache
+
+
+### 4. What is your TiDB version? (Required)
+
+Git Commit Hash: 388b3c79cc3a313aee59334ebe6fc7dc451769c3
+Git Branch: heads/refs/tags/v6.1.0-alpha
+UTC Build Time: 2022-05-22 15:03:09
+
+",True,"no warning info for config deleted and change to system variable - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+1. install v6.0.0 include following config:
+server_configs:
+ tidb:
+ enable-batch-dml: true
+ experimental.enable-global-kill: false
+ log.query-log-max-len: 4000
+ mem-quota-query: 0
+ oom-action: log
+ performance.committer-concurrency: 120
+ performance.run-auto-analyze: true
+ performance.txn-entry-size-limit: 6000000
+ performance.txn-total-size-limit: 6000000
+ prepared-plan-cache.capacity: 2000
+ prepared-plan-cache.enabled: true
+ security.require-secure-transport: false
+2. upgrade to v6.1.0 nightly
+
+### 2. What did you expect to see? (Required)
+according to the discussion with PM, when the old cluster includes the above configs, during upgrade, the tidb node should report
+a warning to tell the user that these configs have been deleted and converted to system variables.
+
+### 3. What did you see instead (Required)
+no waring found
++ [ Serial ] - InitConfig: cluster=local, user=tidb, host=172.16.5.101, path=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache/tidb-4000.service, deploy_dir=/home/tidb/deploy/tidb-4000, data_dir=[], log_dir=/home/tidb/deploy/tidb-4000/log, cache_dir=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache
++ [ Serial ] - InitConfig: cluster=local, user=tidb, host=172.16.5.101, path=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache/tidb-14000.service, deploy_dir=/home/tidb/deploy/tidb-14000, data_dir=[], log_dir=/home/tidb/deploy/tidb-14000/log, cache_dir=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache
+
+
+### 4. What is your TiDB version? (Required)
+
+Git Commit Hash: 388b3c79cc3a313aee59334ebe6fc7dc451769c3
+Git Branch: heads/refs/tags/v6.1.0-alpha
+UTC Build Time: 2022-05-22 15:03:09
+
+",1,no warning info for config deleted and change to system variable bug report please answer these questions before submitting your issue thanks minimal reproduce step required install include following config server configs tidb enable batch dml true experimental enable global kill false log query log max len mem quota query oom action log performance committer concurrency performance run auto analyze true performance txn entry size limit performance txn total size limit prepared plan cache capacity prepared plan cache enabled true security require secure transport false upgrade to nightly what did you expect to see required according to the discussion with pm when the old cluster includes the above configs during upgrade the tidb node should report a warning to tell the user that these configs have been deleted and converted to system variables what did you see instead required no waring found initconfig cluster local user tidb host path home tidb tiup storage cluster clusters local config cache tidb service deploy dir home tidb deploy tidb data dir log dir home tidb deploy tidb log cache dir home tidb tiup storage cluster clusters local config cache initconfig cluster local user tidb host path home tidb tiup storage cluster clusters local config cache tidb service deploy dir home tidb deploy tidb data dir log dir home tidb deploy tidb log cache dir home tidb tiup storage cluster clusters local config cache what is your tidb version required git commit hash git branch heads refs tags alpha utc build time ,1
+473821,13648131595.0,IssuesEvent,2020-09-26 07:29:38,TerryCavanagh/diceydungeonsbeta,https://api.github.com/repos/TerryCavanagh/diceydungeonsbeta,closed,"Downgraded Bronze Cauldron's description just says ""(reuseable)""",High Priority release candidate v0.1,"
+Will update with a screenshot if it happens again, but I think it's because the equipment.csv description is incomplete",1.0,"Downgraded Bronze Cauldron's description just says ""(reuseable)"" - 
+Will update with a screenshot if it happens again, but I think it's because the equipment.csv description is incomplete",0,downgraded bronze cauldron s description just says reuseable will update with a screenshot if it happens again but i think it s because the equipment csv description is incomplete,0
+389593,11504288053.0,IssuesEvent,2020-02-12 22:56:01,cuappdev/pollo-ios,https://api.github.com/repos/cuappdev/pollo-ios,opened,Deleting question on professor side records incorrect index,Priority: High Type: Bug,"If I have 3 polls and I delete the 2nd poll (currently at 2/3), the current behavior is to slide the next poll into my current position (so I would expect to be at 2/2). However, the indexing leaves me at (1/2). This is bad because let's say I delete the 2nd poll (2/3) and try to delete the live poll (2/2), the app thinks I'm at 1/2 and will delete the first poll I didn't mean to delete.",1.0,"Deleting question on professor side records incorrect index - If I have 3 polls and I delete the 2nd poll (currently at 2/3), the current behavior is to slide the next poll into my current position (so I would expect to be at 2/2). However, the indexing leaves me at (1/2). This is bad because let's say I delete the 2nd poll (2/3) and try to delete the live poll (2/2), the app thinks I'm at 1/2 and will delete the first poll I didn't mean to delete.",0,deleting question on professor side records incorrect index if i have polls and i delete the poll currently at the current behavior is to slide the next poll into my current position so i would expect to be at however the indexing leaves me at this is bad because let s say i delete the poll and try to delete the live poll the app thinks i m at and will delete the first poll i didn t mean to delete ,0
+4323,7045264199.0,IssuesEvent,2018-01-01 17:08:42,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,invalid time cast bug.,compatibility help wanted,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+`select cast('239010' as time);`
+
+
+2. What did you expect to see?
+
+```
+mysql> select cast('239010' as time);
++------------------------+
+| cast('239010' as time) |
++------------------------+
+| NULL |
++------------------------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> show warnings;
++---------+------+------------------------------------------+
+| Level | Code | Message |
++---------+------+------------------------------------------+
+| Warning | 1292 | Truncated incorrect time value: '239010' |
++---------+------+------------------------------------------+
+1 row in set (0.04 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> select cast('239010' as time);
++------------------------+
+| cast('239010' as time) |
++------------------------+
+| 24:30:10 |
++------------------------+
+1 row in set (0.00 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+```
+Release Version: 0.8.0
+Git Commit Hash: ae512b3e3e66eb2464be71d42cc61cbd2302b302
+Git Branch: master
+UTC Build Time: 2017-08-20 09:27:45
+```",True,"invalid time cast bug. - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+`select cast('239010' as time);`
+
+
+2. What did you expect to see?
+
+```
+mysql> select cast('239010' as time);
++------------------------+
+| cast('239010' as time) |
++------------------------+
+| NULL |
++------------------------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> show warnings;
++---------+------+------------------------------------------+
+| Level | Code | Message |
++---------+------+------------------------------------------+
+| Warning | 1292 | Truncated incorrect time value: '239010' |
++---------+------+------------------------------------------+
+1 row in set (0.04 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> select cast('239010' as time);
++------------------------+
+| cast('239010' as time) |
++------------------------+
+| 24:30:10 |
++------------------------+
+1 row in set (0.00 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+```
+Release Version: 0.8.0
+Git Commit Hash: ae512b3e3e66eb2464be71d42cc61cbd2302b302
+Git Branch: master
+UTC Build Time: 2017-08-20 09:27:45
+```",1,invalid time cast bug please answer these questions before submitting your issue thanks what did you do select cast as time what did you expect to see mysql select cast as time cast as time null row in set warning sec mysql show warnings level code message warning truncated incorrect time value row in set sec what did you see instead mysql select cast as time cast as time row in set sec what version of tidb are you using tidb server v release version git commit hash git branch master utc build time ,1
+20759,27492774604.0,IssuesEvent,2023-03-04 20:38:42,Azure/azure-sdk-tools,https://api.github.com/repos/Azure/azure-sdk-tools,closed,"Define role, responsibilities, and more for Service buddy",Engagement Experience WS: Process Tools & Automation,"The purpose of this Epic is to focus on defining the roles and responsibilities, tools for people to do their job, and mechanisms to build in accountability for the service buddy for Cadl ",1.0,"Define role, responsibilities, and more for Service buddy - The purpose of this Epic is to focus on defining the roles and responsibilities, tools for people to do their job, and mechanisms to build in accountability for the service buddy for Cadl ",0,define role responsibilities and more for service buddy the purpose of this epic is to focus on defining the roles and responsibilities tools for people to do their job and mechanisms to build in accountability for the service buddy for cadl ,0
+6415,8713685984.0,IssuesEvent,2018-12-07 03:55:51,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Character set name is case sensitive in TiDB,type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+I use mydumper from version 1. 0 dumper to version 2. 0. 8.for example, character sets are case-sensitive.
+
+
+2. What did you expect to see?
+I can loader to 2.0.8
+
+3. What did you see instead?
+dumper sql:
+create table test
+(id int)
+ENGINE=InnoDB DEFAULT CHARSET=UTF8 COLLATE=UTF8_BIN;
+
+Can't recognize UTF8, if I change to utf8, it can be created
+
+Is there a parameter that can be controlled case-sensitive
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+1.0.8 to 2.0.8
+",True,"Character set name is case sensitive in TiDB - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+I use mydumper from version 1. 0 dumper to version 2. 0. 8.for example, character sets are case-sensitive.
+
+
+2. What did you expect to see?
+I can loader to 2.0.8
+
+3. What did you see instead?
+dumper sql:
+create table test
+(id int)
+ENGINE=InnoDB DEFAULT CHARSET=UTF8 COLLATE=UTF8_BIN;
+
+Can't recognize UTF8, if I change to utf8, it can be created
+
+Is there a parameter that can be controlled case-sensitive
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+1.0.8 to 2.0.8
+",1,character set name is case sensitive in tidb bug report please answer these questions before submitting your issue thanks what did you do i use mydumper from version dumper to version for example character sets are case sensitive what did you expect to see i can loader to what did you see instead dumper sql create table test id int engine innodb default charset collate bin can t recognize if i change to it can be created is there a parameter that can be controlled case sensitive what version of tidb are you using tidb server v or run select tidb version on tidb to ,1
+226852,18044983162.0,IssuesEvent,2021-09-18 18:40:03,skyjake/lagrange,https://api.github.com/repos/skyjake/lagrange,closed,Broken text rendering,bug needs testing,"Lagrange sometimes fails at rendering text (missing characters and lines out of place; see images) in the main text display, side interfaces, and context menus.
+This is somehow dependent on text scaling: text rendering frequently breaks down or fixes itself when zoom-level is changed.
+
+Things I have tried that don't fix it:
+* changing the font
+* enabling ""monospace body""
+* changing line width
+* disabling ""wrap plain text""
+
+This happens on Lagrange 1.5.2, installed on Windows 7 from `lagrange_v1.5.2_windows-x64_setup.exe`.
+
+
+
+",1.0,"Broken text rendering - Lagrange sometimes fails at rendering text (missing characters and lines out of place; see images) in the main text display, side interfaces, and context menus.
+This is somehow dependent on text scaling: text rendering frequently breaks down or fixes itself when zoom-level is changed.
+
+Things I have tried that don't fix it:
+* changing the font
+* enabling ""monospace body""
+* changing line width
+* disabling ""wrap plain text""
+
+This happens on Lagrange 1.5.2, installed on Windows 7 from `lagrange_v1.5.2_windows-x64_setup.exe`.
+
+
+
+",0,broken text rendering lagrange sometimes fails at rendering text missing characters and lines out of place see images in the main text display side interfaces and context menus this is somehow dependent on text scaling text rendering frequently breaks down or fixes itself when zoom level is changed things i have tried that don t fix it changing the font enabling monospace body changing line width disabling wrap plain text this happens on lagrange installed on windows from lagrange windows setup exe ,0
+5647,8126480512.0,IssuesEvent,2018-08-17 02:29:36,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,"When the field list of the select statement contains the Enum type, the client will report an error",component/expression for new contributors help wanted status/TODO type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+When I use Server Prepared Statements, that is set `useServerPrepStmts=true`, if the select statement's field list contains the `Enum` type, the client will report an error.
+
+```
+CREATE TABLE shirts (
+ name VARCHAR(40),
+ size ENUM('small', 'medium', 'large')
+);
+
+INSERT INTO shirts (name, size) VALUES ('dress shirt','large'), ('t-shirt','medium'),('polo shirt','small');
+
+mysql> desc shirts;
++-------+--------------------------------+------+------+---------+-------+
+| Field | Type | Null | Key | Default | Extra |
++-------+--------------------------------+------+------+---------+-------+
+| name | varchar(40) | YES | | NULL | |
+| size | enum('small','medium','large') | YES | | NULL | |
++-------+--------------------------------+------+------+---------+-------+
+```
+Java Code snippet:
+
+```
+ String DB_URL = ""jdbc:mysql://xxx.xxx.xxxx.xxx:4000/test"";
+ Properties info = new Properties();
+ info.setProperty(""user"", ""root"");
+ info.setProperty(""password"", """");
+ info.setProperty(""useServerPrepStmts"", ""true"");
+ Connection conn = DriverManager.getConnection(DB_URL, info);
+
+ String sql = ""SELECT name, size FROM shirts WHERE name = ?"";
+
+ PreparedStatement preparedStatement = conn.prepareStatement(sql);
+ preparedStatement.setString(1, ""t-shirt"");
+ ResultSet resultSet = preparedStatement.executeQuery();
+
+ while (resultSet.next()) {
+ String name = resultSet.getString(""name"");
+ String size = resultSet.getString(""size"");
+ System.out.println(name + "", "" + size );
+ }
+```
+MySQL Connector/J version:
+
+```
+
+ mysql
+ mysql-connector-java
+ 6.0.6
+
+```
+
+2. What did you expect to see?
+
+I expect the TiDB to return the correct query result.
+
+3. What did you see instead?
+
+The client reported the following error message:
+
+```
+Exception in thread ""main"" java.sql.SQLException: Unknown type '247' in column '1' of '2' in binary-encoded result set.
+ at com.mysql.cj.jdbc.exceptions.SQLError.createSQLException(SQLError.java:545)
+ at com.mysql.cj.jdbc.exceptions.SQLError.createSQLException(SQLError.java:513)
+ at com.mysql.cj.jdbc.exceptions.SQLExceptionsMapping.translateException(SQLExceptionsMapping.java:115)
+ at com.mysql.cj.jdbc.ServerPreparedStatement.serverExecute(ServerPreparedStatement.java:1299)
+ at com.mysql.cj.jdbc.ServerPreparedStatement.executeInternal(ServerPreparedStatement.java:701)
+ at com.mysql.cj.jdbc.PreparedStatement.executeQuery(PreparedStatement.java:1923)
+ at com.apusic.test.CursorExample.main(CursorExample.java:27)
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+----------------------------------------------------------------------------------------------------------------+
+| Release Version: v2.1.0-alpha-75-g41f8ac195
+Git Commit Hash: 41f8ac19523386d0eb6ca871397f49f834958169
+Git Branch: master
+UTC Build Time: 2018-06-26 07:08:04
+GoVersion: go version go1.10.1 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e |
++------------------------------------------------------------------------------------",True,"When the field list of the select statement contains the Enum type, the client will report an error - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+When I use Server Prepared Statements, that is set `useServerPrepStmts=true`, if the select statement's field list contains the `Enum` type, the client will report an error.
+
+```
+CREATE TABLE shirts (
+ name VARCHAR(40),
+ size ENUM('small', 'medium', 'large')
+);
+
+INSERT INTO shirts (name, size) VALUES ('dress shirt','large'), ('t-shirt','medium'),('polo shirt','small');
+
+mysql> desc shirts;
++-------+--------------------------------+------+------+---------+-------+
+| Field | Type | Null | Key | Default | Extra |
++-------+--------------------------------+------+------+---------+-------+
+| name | varchar(40) | YES | | NULL | |
+| size | enum('small','medium','large') | YES | | NULL | |
++-------+--------------------------------+------+------+---------+-------+
+```
+Java Code snippet:
+
+```
+ String DB_URL = ""jdbc:mysql://xxx.xxx.xxxx.xxx:4000/test"";
+ Properties info = new Properties();
+ info.setProperty(""user"", ""root"");
+ info.setProperty(""password"", """");
+ info.setProperty(""useServerPrepStmts"", ""true"");
+ Connection conn = DriverManager.getConnection(DB_URL, info);
+
+ String sql = ""SELECT name, size FROM shirts WHERE name = ?"";
+
+ PreparedStatement preparedStatement = conn.prepareStatement(sql);
+ preparedStatement.setString(1, ""t-shirt"");
+ ResultSet resultSet = preparedStatement.executeQuery();
+
+ while (resultSet.next()) {
+ String name = resultSet.getString(""name"");
+ String size = resultSet.getString(""size"");
+ System.out.println(name + "", "" + size );
+ }
+```
+MySQL Connector/J version:
+
+```
+
+ mysql
+ mysql-connector-java
+ 6.0.6
+
+```
+
+2. What did you expect to see?
+
+I expect the TiDB to return the correct query result.
+
+3. What did you see instead?
+
+The client reported the following error message:
+
+```
+Exception in thread ""main"" java.sql.SQLException: Unknown type '247' in column '1' of '2' in binary-encoded result set.
+ at com.mysql.cj.jdbc.exceptions.SQLError.createSQLException(SQLError.java:545)
+ at com.mysql.cj.jdbc.exceptions.SQLError.createSQLException(SQLError.java:513)
+ at com.mysql.cj.jdbc.exceptions.SQLExceptionsMapping.translateException(SQLExceptionsMapping.java:115)
+ at com.mysql.cj.jdbc.ServerPreparedStatement.serverExecute(ServerPreparedStatement.java:1299)
+ at com.mysql.cj.jdbc.ServerPreparedStatement.executeInternal(ServerPreparedStatement.java:701)
+ at com.mysql.cj.jdbc.PreparedStatement.executeQuery(PreparedStatement.java:1923)
+ at com.apusic.test.CursorExample.main(CursorExample.java:27)
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+----------------------------------------------------------------------------------------------------------------+
+| Release Version: v2.1.0-alpha-75-g41f8ac195
+Git Commit Hash: 41f8ac19523386d0eb6ca871397f49f834958169
+Git Branch: master
+UTC Build Time: 2018-06-26 07:08:04
+GoVersion: go version go1.10.1 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e |
++------------------------------------------------------------------------------------",1,when the field list of the select statement contains the enum type the client will report an error please answer these questions before submitting your issue thanks what did you do when i use server prepared statements that is set useserverprepstmts true if the select statement s field list contains the enum type the client will report an error create table shirts name varchar size enum small medium large insert into shirts name size values dress shirt large t shirt medium polo shirt small mysql desc shirts field type null key default extra name varchar yes null size enum small medium large yes null java code snippet: string db url jdbc mysql xxx xxx xxxx xxx test properties info new properties info setproperty user root info setproperty password info setproperty useserverprepstmts true connection conn drivermanager getconnection db url info string sql select name size from shirts where name preparedstatement preparedstatement conn preparestatement sql preparedstatement setstring t shirt resultset resultset preparedstatement executequery while resultset next string name resultset getstring name string size resultset getstring size system out println name size mysql connector j version: mysql mysql connector java what did you expect to see i expect the tidb to return the correct query result what did you see instead the client reported the following error message exception in thread main java sql sqlexception unknown type in column of in binary encoded result set at com mysql cj jdbc exceptions sqlerror createsqlexception sqlerror java at com mysql cj jdbc exceptions sqlerror createsqlexception sqlerror java at com mysql cj jdbc exceptions sqlexceptionsmapping translateexception sqlexceptionsmapping java at com mysql cj jdbc serverpreparedstatement serverexecute serverpreparedstatement java at com mysql cj jdbc serverpreparedstatement executeinternal serverpreparedstatement java at com mysql cj jdbc preparedstatement executequery preparedstatement java at com apusic test cursorexample main cursorexample java what version of tidb are you using tidb server v or run select tidb version on tidb release version alpha git commit hash git branch master utc build time goversion go version darwin race enabled false tikv min version alpha ,1
+110995,13996339299.0,IssuesEvent,2020-10-28 05:39:51,ajency/Dhanda-App,https://api.github.com/repos/ajency/Dhanda-App,closed,"No categories for DAILY,WORK BASIS,WEEKLY,WORKBASIS",Assigned to QA Design Issue bug,"There are no categories for DAILY,WORK BASIS,WEEKLY,WORKBASIS
+
+Description-As the staff must be segregated into such category like in case of monthly and hourly staff but the Daily ,weekly and work basis dont have category and are put under one category of monthly
+
+",1.0,"No categories for DAILY,WORK BASIS,WEEKLY,WORKBASIS - There are no categories for DAILY,WORK BASIS,WEEKLY,WORKBASIS
+
+Description-As the staff must be segregated into such category like in case of monthly and hourly staff but the Daily ,weekly and work basis dont have category and are put under one category of monthly
+
+",0,no categories for daily work basis weekly workbasis there are no categories for daily work basis weekly workbasis description as the staff must be segregated into such category like in case of monthly and hourly staff but the daily weekly and work basis dont have category and are put under one category of monthly ,0
+3210,9213817246.0,IssuesEvent,2019-03-10 15:09:07,jimkyndemeyer/js-graphql-intellij-plugin,https://api.github.com/repos/jimkyndemeyer/js-graphql-intellij-plugin,closed,Support for multiple schemas (on multiple endpoints),enhancement v2-alpha v2-architecture,"I need to access two different graphql endpoints from a project, where each endpoint has a different schema.
+
+I'm currently keeping two different copies of graphql.config.json that I swap between as needed.
+
+Is there a better way to handle this? If not, consider this an enhancement request.",1.0,"Support for multiple schemas (on multiple endpoints) - I need to access two different graphql endpoints from a project, where each endpoint has a different schema.
+
+I'm currently keeping two different copies of graphql.config.json that I swap between as needed.
+
+Is there a better way to handle this? If not, consider this an enhancement request.",0,support for multiple schemas on multiple endpoints i need to access two different graphql endpoints from a project where each endpoint has a different schema i m currently keeping two different copies of graphql config json that i swap between as needed is there a better way to handle this if not consider this an enhancement request ,0
+411812,12032337110.0,IssuesEvent,2020-04-13 11:53:54,mir-dataset-loaders/mirdata,https://api.github.com/repos/mir-dataset-loaders/mirdata,closed,"`module.load_*` should raise `IOError`, not return `None`",priority question,"raised by @rabitt in a meeting today
+
+Many of the module-specific loaders, e.g. `orchset.load_melody`, return `None` if the argument does not exist. This can be confusing in the sense that it may suggest that the file exists but that there is no annotation for this file, or that the annotation is not applicable (non-melodic music, following my example above).
+
+She now recommends raising an `IOError`.
+
+This is a breaking change so i wouldn't recommend it for v0.2
+But we can deprecate it in v0.2 and change the behavior in v0.3
+
+@rabitt what should we do for people providing new loaders? Should we tell them to work with the old or the new convention?
+This affects `new_loader.md` (excerpt below):
+
+```
+# -- Write any necessary loader functions for loading the dataset's data
+def load_annotation(annotation_path):
+ if not os.path.exists(annotation_path):
+ return None
+```",1.0,"`module.load_*` should raise `IOError`, not return `None` - raised by @rabitt in a meeting today
+
+Many of the module-specific loaders, e.g. `orchset.load_melody`, return `None` if the argument does not exist. This can be confusing in the sense that it may suggest that the file exists but that there is no annotation for this file, or that the annotation is not applicable (non-melodic music, following my example above).
+
+She now recommends raising an `IOError`.
+
+This is a breaking change so i wouldn't recommend it for v0.2
+But we can deprecate it in v0.2 and change the behavior in v0.3
+
+@rabitt what should we do for people providing new loaders? Should we tell them to work with the old or the new convention?
+This affects `new_loader.md` (excerpt below):
+
+```
+# -- Write any necessary loader functions for loading the dataset's data
+def load_annotation(annotation_path):
+ if not os.path.exists(annotation_path):
+ return None
+```",0, module load should raise ioerror not return none raised by rabitt in a meeting today many of the module specific loaders e g orchset load melody return none if the argument does not exist this can be confusing in the sense that it may suggest that the file exists but that there is no annotation for this file or that the annotation is not applicable non melodic music following my example above she now recommends raising an ioerror this is a breaking change so i wouldn t recommend it for but we can deprecate it in and change the behavior in rabitt what should we do for people providing new loaders should we tell them to work with the old or the new convention this affects new loader md excerpt below write any necessary loader functions for loading the dataset s data def load annotation annotation path if not os path exists annotation path return none ,0
+5570,8049273217.0,IssuesEvent,2018-08-01 09:35:12,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Check how MySQL sort privilege cache items exactly,help wanted type/compatibility,"https://github.com/pingcap/tidb/pull/7211 try to sort the user records according to the document https://dev.mysql.com/doc/refman/5.5/en/connection-access.html
+
+The document missing many details, so maybe we should check the MySQL source code to see how to do it.",True,"Check how MySQL sort privilege cache items exactly - https://github.com/pingcap/tidb/pull/7211 try to sort the user records according to the document https://dev.mysql.com/doc/refman/5.5/en/connection-access.html
+
+The document missing many details, so maybe we should check the MySQL source code to see how to do it.",1,check how mysql sort privilege cache items exactly try to sort the user records according to the document the document missing many details so maybe we should check the mysql source code to see how to do it ,1
+192560,14620553142.0,IssuesEvent,2020-12-22 19:56:36,github-vet/rangeloop-pointer-findings,https://api.github.com/repos/github-vet/rangeloop-pointer-findings,closed,pbolla0818/oci_terraform: oci/budget_budget_test.go; 14 LoC,fresh small test,"
+Found a possible issue in [pbolla0818/oci_terraform](https://www.github.com/pbolla0818/oci_terraform) at [oci/budget_budget_test.go](https://github.com/pbolla0818/oci_terraform/blob/c233d54c5fe32f12c234d6dceefba0a9b4ab3022/oci/budget_budget_test.go#L477-L490)
-## Learning Materials
-MySQL's [document](https://dev.mysql.com/doc/refman/8.0/en/invisible-indexes.html) for syntax reference.
-[TiDB DDL architecture](https://github.com/pingcap/tidb/blob/master/docs/design/2018-10-08-online-DDL.md)",True,"Support multiple table rename (swap table use case) - ## Feature Request
+Below is the message reported by the analyzer for this snippet of code. Beware that the analyzer only reports the first
+issue it finds, so please do not limit your consideration to the contents of the below message.
-**Is your feature request related to a problem? Please describe:**
+> reference to budgetId is reassigned at line 481
-I know that multiple DDL changes are currently on the roadmap. My feature request is to support a much smaller subset, which is an atomic rename of two tables.
+[Click here to see the code in its original context.](https://github.com/pbolla0818/oci_terraform/blob/c233d54c5fe32f12c234d6dceefba0a9b4ab3022/oci/budget_budget_test.go#L477-L490)
-This supports the use case of swapping tables, something that occurs frequently in the replication stream due to its usage by tools such as `pt-online-schema-change`.
+
+Click here to show the 14 line(s) of Go which triggered the analyzer.
-**Describe the feature you'd like:**
+```go
+ for _, budgetId := range budgetIds {
+ if ok := SweeperDefaultResourceId[budgetId]; !ok {
+ deleteBudgetRequest := oci_budget.DeleteBudgetRequest{}
-```
-mysql> CREATE TABLE t1 (a int);
-Query OK, 0 rows affected (0.01 sec)
+ deleteBudgetRequest.BudgetId = &budgetId
-mysql> CREATE TABLE t2 (a int, b int);
-Query OK, 0 rows affected (0.01 sec)
+ deleteBudgetRequest.RequestMetadata.RetryPolicy = getRetryPolicy(true, ""budget"")
+ _, error := budgetClient.DeleteBudget(context.Background(), deleteBudgetRequest)
+ if error != nil {
+ fmt.Printf(""Error deleting Budget %s %s, It is possible that the resource is already deleted. Please verify manually \n"", budgetId, error)
+ continue
+ }
+ }
+ }
-mysql> RENAME TABLE t1 to t1_old, t2 to t1; <--- should work
-ERROR 1105 (HY000): can't run multi schema change
```
+
-**Describe alternatives you've considered:**
-
-The alternative is to do this non-atomically (breaks apps) or under a global lock (not yet supported by TiDB). So there is not really a good alternative.
-
-**Teachability, Documentation, Adoption, Migration Strategy:**
-
-MySQL compatible behavior.
-
-## Score
-1500
+Leave a reaction on this issue to contribute to the project by classifying this instance as a **Bug** :-1:, **Mitigated** :+1:, or **Desirable Behavior** :rocket:
+See the descriptions of the classifications [here](https://github.com/github-vet/rangeclosure-findings#how-can-i-help) for more information.
-## SIG Slack Channel
-You can join [#sig-ddl ](https://app.slack.com/client/TH91JCS4W/CMAKWBNJU)on slack in your spare time to discuss and get help with mentors or others.
+commit ID: c233d54c5fe32f12c234d6dceefba0a9b4ab3022
+",1.0,"pbolla0818/oci_terraform: oci/budget_budget_test.go; 14 LoC -
+Found a possible issue in [pbolla0818/oci_terraform](https://www.github.com/pbolla0818/oci_terraform) at [oci/budget_budget_test.go](https://github.com/pbolla0818/oci_terraform/blob/c233d54c5fe32f12c234d6dceefba0a9b4ab3022/oci/budget_budget_test.go#L477-L490)
-## Mentor(s)
-* @zimulala
+Below is the message reported by the analyzer for this snippet of code. Beware that the analyzer only reports the first
+issue it finds, so please do not limit your consideration to the contents of the below message.
-## Recommended Skills
-* DDL
-* Golang
+> reference to budgetId is reassigned at line 481
-## Learning Materials
-MySQL's [document](https://dev.mysql.com/doc/refman/8.0/en/invisible-indexes.html) for syntax reference.
-[TiDB DDL architecture](https://github.com/pingcap/tidb/blob/master/docs/design/2018-10-08-online-DDL.md)",1,support multiple table rename swap table use case feature request is your feature request related to a problem please describe i know that multiple ddl changes are currently on the roadmap my feature request is to support a much smaller subset which is an atomic rename of two tables this supports the use case of swapping tables something that occurs frequently in the replication stream due to its usage by tools such as pt online schema change describe the feature you d like mysql create table a int query ok rows affected sec mysql create table a int b int query ok rows affected sec mysql rename table to old to should work error can t run multi schema change describe alternatives you ve considered the alternative is to do this non atomically breaks apps or under a global lock not yet supported by tidb so there is not really a good alternative teachability documentation adoption migration strategy mysql compatible behavior score sig slack channel you can join slack in your spare time to discuss and get help with mentors or others mentor s zimulala recommended skills ddl golang learning materials mysql s for syntax reference ,1
-7372,9621030170.0,IssuesEvent,2019-05-14 09:40:55,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Function `period_diff ` is not compatible with MySQL 8.0,component/expression help wanted type/bug type/compatibility,"## Bug Report
+[Click here to see the code in its original context.](https://github.com/pbolla0818/oci_terraform/blob/c233d54c5fe32f12c234d6dceefba0a9b4ab3022/oci/budget_budget_test.go#L477-L490)
-Please answer these questions before submitting your issue. Thanks!
+
+Click here to show the 14 line(s) of Go which triggered the analyzer.
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-Function `period_diff` is not compatible with MySQL 8.0
+```go
+ for _, budgetId := range budgetIds {
+ if ok := SweeperDefaultResourceId[budgetId]; !ok {
+ deleteBudgetRequest := oci_budget.DeleteBudgetRequest{}
-2. What did you expect to see?
-MySQL 8.0:
-```
-mysql> SELECT PERIOD_diff(-00013,1);
-ERROR 1210 (HY000): Incorrect arguments to period_diff
-```
+ deleteBudgetRequest.BudgetId = &budgetId
+ deleteBudgetRequest.RequestMetadata.RetryPolicy = getRetryPolicy(true, ""budget"")
+ _, error := budgetClient.DeleteBudget(context.Background(), deleteBudgetRequest)
+ if error != nil {
+ fmt.Printf(""Error deleting Budget %s %s, It is possible that the resource is already deleted. Please verify manually \n"", budgetId, error)
+ continue
+ }
+ }
+ }
-3. What did you see instead?
-TiDB
-```
-mysql> SELECT PERIOD_diff(-00013,1);
-+-----------------------+
-| PERIOD_diff(-00013,1) |
-+-----------------------+
-| 2213609288845122194 |
-+-----------------------+
-1 row in set (0.00 sec)
```
+
+Leave a reaction on this issue to contribute to the project by classifying this instance as a **Bug** :-1:, **Mitigated** :+1:, or **Desirable Behavior** :rocket:
+See the descriptions of the classifications [here](https://github.com/github-vet/rangeclosure-findings#how-can-i-help) for more information.
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-```
-mysql> select tidb_version();
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v3.0.0-beta.1-218-g2f7241138-dirty
-Git Commit Hash: 2f7241138adfc434f4b199ecae68fb83ad33b36b
-Git Branch: myfeature-perioddiff
-UTC Build Time: 2019-05-07 03:36:21
-GoVersion: go version go1.11.4 darwin/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false |
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-1 row in set (0.00 sec)
-```
-",True,"Function `period_diff ` is not compatible with MySQL 8.0 - ## Bug Report
-
-Please answer these questions before submitting your issue. Thanks!
+commit ID: c233d54c5fe32f12c234d6dceefba0a9b4ab3022
+",0, oci terraform oci budget budget test go loc found a possible issue in at below is the message reported by the analyzer for this snippet of code beware that the analyzer only reports the first issue it finds so please do not limit your consideration to the contents of the below message reference to budgetid is reassigned at line click here to show the line s of go which triggered the analyzer go for budgetid range budgetids if ok sweeperdefaultresourceid ok deletebudgetrequest oci budget deletebudgetrequest deletebudgetrequest budgetid budgetid deletebudgetrequest requestmetadata retrypolicy getretrypolicy true budget error budgetclient deletebudget context background deletebudgetrequest if error nil fmt printf error deleting budget s s it is possible that the resource is already deleted please verify manually n budgetid error continue leave a reaction on this issue to contribute to the project by classifying this instance as a bug mitigated or desirable behavior rocket see the descriptions of the classifications for more information commit id ,0
+144718,11627883384.0,IssuesEvent,2020-02-27 17:16:30,dhowe/spectre,https://api.github.com/repos/dhowe/spectre,closed,Insight: sliders don’t activate the next button on touch screen,CRITICAL needs-verification test-on-touchscreen,"This works correctly in touch-screen simulation (see below). @billposters Are you saying that when you drag the slider, the 'next' button does not become active (and turn blue)?
+
+
+
+",1.0,"Insight: sliders don’t activate the next button on touch screen - This works correctly in touch-screen simulation (see below). @billposters Are you saying that when you drag the slider, the 'next' button does not become active (and turn blue)?
+
+
+
+",0,insight sliders don’t activate the next button on touch screen this works correctly in touch screen simulation see below billposters are you saying that when you drag the slider the next button does not become active and turn blue ,0
+16544,22497246529.0,IssuesEvent,2022-06-23 08:40:39,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Bad error message for numeric conversion,type/compatibility severity/moderate component/executor compatibility-mysql8,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+```sql
+DROP TABLE IF EXISTS t0;
+CREATE TABLE t0 (c0 DECIMAL);
+INSERT INTO t0 VALUES (1);
+SELECT * FROM t0 WHERE t0.c0 > 'a';
+SHOW WARNINGS;
+```
+
+
+### 2. What did you expect to see? (Required)
+A specific type of error for external applications like MySQL.
+```sql
++---------+------+----------------------------------------+
+| Level | Code | Message |
++---------+------+----------------------------------------+
+| Warning | 1292 | Truncated incorrect DECIMAL value: 'a' |
++---------+------+----------------------------------------+
+1 row in set (0.00 sec)
+```
+### 3. What did you see instead (Required)
+```sql
++---------+------+------------+
+| Level | Code | Message |
++---------+------+------------+
+| Warning | 8029 | Bad Number |
++---------+------+------------+
+1 row in set (0.00 sec)
+```
+### 4. What is your TiDB version? (Required)
+```sql
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version()
+
+ |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v5.4.0
+Edition: Community
+Git Commit Hash: 55f3b24c1c9f506bd652ef1d162283541e428872
+Git Branch: heads/refs/tags/v5.4.0
+UTC Build Time: 2022-01-25 08:39:26
+GoVersion: go1.16.4
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+",True,"Bad error message for numeric conversion - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+```sql
+DROP TABLE IF EXISTS t0;
+CREATE TABLE t0 (c0 DECIMAL);
+INSERT INTO t0 VALUES (1);
+SELECT * FROM t0 WHERE t0.c0 > 'a';
+SHOW WARNINGS;
+```
+
+
+### 2. What did you expect to see? (Required)
+A specific type of error for external applications like MySQL.
+```sql
++---------+------+----------------------------------------+
+| Level | Code | Message |
++---------+------+----------------------------------------+
+| Warning | 1292 | Truncated incorrect DECIMAL value: 'a' |
++---------+------+----------------------------------------+
+1 row in set (0.00 sec)
+```
+### 3. What did you see instead (Required)
+```sql
++---------+------+------------+
+| Level | Code | Message |
++---------+------+------------+
+| Warning | 8029 | Bad Number |
++---------+------+------------+
+1 row in set (0.00 sec)
+```
+### 4. What is your TiDB version? (Required)
+```sql
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version()
+
+ |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v5.4.0
+Edition: Community
+Git Commit Hash: 55f3b24c1c9f506bd652ef1d162283541e428872
+Git Branch: heads/refs/tags/v5.4.0
+UTC Build Time: 2022-01-25 08:39:26
+GoVersion: go1.16.4
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+",1,bad error message for numeric conversion bug report please answer these questions before submitting your issue thanks minimal reproduce step required sql drop table if exists create table decimal insert into values select from where a show warnings what did you expect to see required a specific type of error for external applications like mysql sql level code message warning truncated incorrect decimal value a row in set sec what did you see instead required sql level code message warning bad number row in set sec what is your tidb version required sql tidb version release version edition community git commit hash git branch heads refs tags utc build time goversion race enabled false tikv min version check table before drop false row in set sec ,1
+15229,19325304162.0,IssuesEvent,2021-12-14 10:38:36,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,JSON_EXTRACT function does not get the expected result,type/bug type/compatibility severity/moderate component/executor,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```sql
+SELECT JSON_EXTRACT('{""properties"": {""$type"": ""TiDB""}}','$.properties.$type')
+```
+
+### 2. What did you expect to see? (Required)
+
+""TiDB""
+
+### 3. What did you see instead (Required)
+
+{""$type"": ""TiDB""}
+
+### 4. What is your TiDB version? (Required)
+
+5.7.25-TiDB-v5.1.0",True,"JSON_EXTRACT function does not get the expected result - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```sql
+SELECT JSON_EXTRACT('{""properties"": {""$type"": ""TiDB""}}','$.properties.$type')
+```
+
+### 2. What did you expect to see? (Required)
+
+""TiDB""
+
+### 3. What did you see instead (Required)
+
+{""$type"": ""TiDB""}
+
+### 4. What is your TiDB version? (Required)
+
+5.7.25-TiDB-v5.1.0",1,json extract function does not get the expected result bug report please answer these questions before submitting your issue thanks minimal reproduce step required sql select json extract properties type tidb properties type what did you expect to see required tidb what did you see instead required type tidb what is your tidb version required tidb ,1
+7434,9674066855.0,IssuesEvent,2019-05-22 09:03:30,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,`LOAD DATA LOCAL INFILE` with IGNORE will report an error,for new contributors help wanted type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+run `load data` with `ignore` will occur an error
+
+`
+mysql -h {host} -P {port} -u root --local-infile=1 -p{password} -D SCALIFIED -e LOAD DATA LOCAL INFILE 'SCALIFIED.T_STU' IGNORE INTO TABLE SCALIFIED.T_STU FIELDS TERMINATED BY '\t' LINES TERMINATED BY '\n';
+`
+
+the command run against mysql successfully.
+
+
+
+2. What did you expect to see?
+
+load data into tidb successfully.
+
+3. What did you see instead?
+
+error occurs.
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+v2.1.4",True,"`LOAD DATA LOCAL INFILE` with IGNORE will report an error - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+run `load data` with `ignore` will occur an error
+
+`
+mysql -h {host} -P {port} -u root --local-infile=1 -p{password} -D SCALIFIED -e LOAD DATA LOCAL INFILE 'SCALIFIED.T_STU' IGNORE INTO TABLE SCALIFIED.T_STU FIELDS TERMINATED BY '\t' LINES TERMINATED BY '\n';
+`
+
+the command run against mysql successfully.
+
+
+
+2. What did you expect to see?
+
+load data into tidb successfully.
+
+3. What did you see instead?
+
+error occurs.
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+v2.1.4",1, load data local infile with ignore will report an error bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error run load data with ignore will occur an error mysql h host p port u root local infile p password d scalified e load data local infile scalified t stu ignore into table scalified t stu fields terminated by t lines terminated by n the command run against mysql successfully what did you expect to see load data into tidb successfully what did you see instead error occurs what version of tidb are you using tidb server v or run select tidb version on tidb ,1
+143373,11551049555.0,IssuesEvent,2020-02-19 00:12:44,Team1559/2020-InfiniteRecharge,https://api.github.com/repos/Team1559/2020-InfiniteRecharge,closed,Chassis tuning at full robot weight,Test Tuning,Re-tune velocity mode once the robot is assembled. Adjust PIDF coefficients as well as ramp rates and current limits.,1.0,Chassis tuning at full robot weight - Re-tune velocity mode once the robot is assembled. Adjust PIDF coefficients as well as ramp rates and current limits.,0,chassis tuning at full robot weight re tune velocity mode once the robot is assembled adjust pidf coefficients as well as ramp rates and current limits ,0
+3419,6392908898.0,IssuesEvent,2017-08-04 05:09:30,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Function `encrypt` not supported,compatibility rc3.1,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+select length(encrypt('foo', 'ff')) <> 0;
+```
+
+2. What did you expect to see?
+
+```
+length(encrypt('foo', 'ff')) <> 0
+1
+```
+
+3. What did you see instead?
+
+```
+ERROR 1305 (42000) at line 1: FUNCTION ENCRYPT does not exist
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"Function `encrypt` not supported - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+select length(encrypt('foo', 'ff')) <> 0;
+```
+
+2. What did you expect to see?
+
+```
+length(encrypt('foo', 'ff')) <> 0
+1
+```
+
+3. What did you see instead?
+
+```
+ERROR 1305 (42000) at line 1: FUNCTION ENCRYPT does not exist
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,function encrypt not supported please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql select length encrypt foo ff what did you expect to see length encrypt foo ff what did you see instead error at line function encrypt does not exist what version of tidb are you using tidb server v ,1
+7609,9859060291.0,IssuesEvent,2019-06-20 08:44:51,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Window function panicked when range bound is time type,component/executor type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+CREATE TABLE `t_time` (
+ `t` time DEFAULT NULL,
+ `ts` timestamp NULL DEFAULT NULL
+)
+INSERT INTO t_time VALUES ('12:30', '2016-07-05 08:30:42');
+SELECT t, FIRST_VALUE(t) OVER (ORDER BY t RANGE BETWEEN INTERVAL 2 HOUR PRECEDING AND INTERVAL 2 HOUR_MINUTE PRECEDING) FROM t_time;
+```
+
+2. What did you expect to see?
+
+Execute successfully.
+
+3. What did you see instead?
+
+Panicked.
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+",True,"Window function panicked when range bound is time type - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+CREATE TABLE `t_time` (
+ `t` time DEFAULT NULL,
+ `ts` timestamp NULL DEFAULT NULL
+)
+INSERT INTO t_time VALUES ('12:30', '2016-07-05 08:30:42');
+SELECT t, FIRST_VALUE(t) OVER (ORDER BY t RANGE BETWEEN INTERVAL 2 HOUR PRECEDING AND INTERVAL 2 HOUR_MINUTE PRECEDING) FROM t_time;
+```
+
+2. What did you expect to see?
+
+Execute successfully.
+
+3. What did you see instead?
+
+Panicked.
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+",1,window function panicked when range bound is time type bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error create table t time t time default null ts timestamp null default null insert into t time values select t first value t over order by t range between interval hour preceding and interval hour minute preceding from t time what did you expect to see execute successfully what did you see instead panicked what version of tidb are you using tidb server v or run select tidb version on tidb ,1
+19384,26903946824.0,IssuesEvent,2023-02-06 17:32:02,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Column defaults in ComFieldList response violate protocol,type/bug type/compatibility component/mysql-protocol severity/minor compatibility-mysql8,"## Bug Report
+
+The `mysql.ComFieldList` returns default values for columns. However this isn't fully implemented in TiDB, so it won't send the actual defaults and it also seems to violate the protocol.
+
+### 1. Minimal reproduce step (Required)
+
+Send a field list query, e.g. by connecting without database and running `use test` in the MySQL Client.
+Dump and inspect traffic with Wireshark
+
+### 2. What did you expect to see? (Required)
+
+Proper column defaults
+
+### 3. What did you see instead (Required)
+
+Too many zeros being written.
+
+### 4. What is your TiDB version? (Required)
+
+```
+$ ./bin/tidb-server -V
+Release Version: v6.6.0-alpha-274-g1e0956d5b
+Edition: Community
+Git Commit Hash: 1e0956d5ba41182e603295e02ae8f767d62979e4
+Git Branch: master
+UTC Build Time: 2023-01-22 23:13:24
+GoVersion: go1.19.5
+Race Enabled: false
+TiKV Min Version: 6.2.0-alpha
+Check Table Before Drop: false
+Store: unistore
+```",True,"Column defaults in ComFieldList response violate protocol - ## Bug Report
+
+The `mysql.ComFieldList` returns default values for columns. However this isn't fully implemented in TiDB, so it won't send the actual defaults and it also seems to violate the protocol.
+
+### 1. Minimal reproduce step (Required)
+
+Send a field list query, e.g. by connecting without database and running `use test` in the MySQL Client.
+Dump and inspect traffic with Wireshark
+
+### 2. What did you expect to see? (Required)
+
+Proper column defaults
+
+### 3. What did you see instead (Required)
+
+Too many zeros being written.
+
+### 4. What is your TiDB version? (Required)
+
+```
+$ ./bin/tidb-server -V
+Release Version: v6.6.0-alpha-274-g1e0956d5b
+Edition: Community
+Git Commit Hash: 1e0956d5ba41182e603295e02ae8f767d62979e4
+Git Branch: master
+UTC Build Time: 2023-01-22 23:13:24
+GoVersion: go1.19.5
+Race Enabled: false
+TiKV Min Version: 6.2.0-alpha
+Check Table Before Drop: false
+Store: unistore
+```",1,column defaults in comfieldlist response violate protocol bug report the mysql comfieldlist returns default values for columns however this isn t fully implemented in tidb so it won t send the actual defaults and it also seems to violate the protocol minimal reproduce step required send a field list query e g by connecting without database and running use test in the mysql client dump and inspect traffic with wireshark what did you expect to see required proper column defaults what did you see instead required too many zeros being written what is your tidb version required bin tidb server v release version alpha edition community git commit hash git branch master utc build time goversion race enabled false tikv min version alpha check table before drop false store unistore ,1
+8679,10605931139.0,IssuesEvent,2019-10-10 21:40:12,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Navicat fails to connect (due to missing mysql.proc_priv table),help wanted type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+ SELECT * FROM mysql.procs_priv;
+
+2. What did you expect to see?
+
+Host Db User Routine_name Routine_type Grantor Proc_priv Timestamp
+
+3. What did you see instead?
+[Err] 1146 - Table 'mysql.procs_priv' doesn't exist
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+1.1.0-dev.2
+
+TiDB don't have t mysql.proc_priv table. Navicat have failed to login in TiDB with non-root user because it got an error by sending such sql query.",True,"Navicat fails to connect (due to missing mysql.proc_priv table) - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+ SELECT * FROM mysql.procs_priv;
+
+2. What did you expect to see?
+
+Host Db User Routine_name Routine_type Grantor Proc_priv Timestamp
+
+3. What did you see instead?
+[Err] 1146 - Table 'mysql.procs_priv' doesn't exist
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+1.1.0-dev.2
+
+TiDB don't have t mysql.proc_priv table. Navicat have failed to login in TiDB with non-root user because it got an error by sending such sql query.",1,navicat fails to connect due to missing mysql proc priv table please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error select from mysql procs priv what did you expect to see host db user routine name routine type grantor proc priv timestamp what did you see instead table mysql procs priv doesn t exist what version of tidb are you using tidb server v or run select tidb version on tidb dev tidb don t have t mysql proc priv table navicat have failed to login in tidb with non root user because it got an error by sending such sql query ,1
+193019,14635237919.0,IssuesEvent,2020-12-24 07:42:00,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,executor_test.go:testSuiteP2.TestPointUpdatePreparedPlan failed,component/test,"executor_test.go:testSuiteP2.TestPointUpdatePreparedPlan
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-Function `period_diff` is not compatible with MySQL 8.0
+Latest failed builds:
+https://internal.pingcap.net/idc-jenkins/job/tidb_ghpr_unit_test/31968/display/redirect
+https://internal.pingcap.net/idc-jenkins/job/tidb_ghpr_unit_test/31876/display/redirect
+https://internal.pingcap.net/idc-jenkins/job/tidb_ghpr_unit_test/31961/display/redirect
+",1.0,"executor_test.go:testSuiteP2.TestPointUpdatePreparedPlan failed - executor_test.go:testSuiteP2.TestPointUpdatePreparedPlan
-2. What did you expect to see?
-MySQL 8.0:
-```
-mysql> SELECT PERIOD_diff(-00013,1);
-ERROR 1210 (HY000): Incorrect arguments to period_diff
-```
+Latest failed builds:
+https://internal.pingcap.net/idc-jenkins/job/tidb_ghpr_unit_test/31968/display/redirect
+https://internal.pingcap.net/idc-jenkins/job/tidb_ghpr_unit_test/31876/display/redirect
+https://internal.pingcap.net/idc-jenkins/job/tidb_ghpr_unit_test/31961/display/redirect
+",0,executor test go testpointupdatepreparedplan failed executor test go testpointupdatepreparedplan latest failed builds ,0
+3476,6460255882.0,IssuesEvent,2017-08-16 03:12:06,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Built-in function TIME_FORMAT not supported,compatibility rc3.1,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+select TIME_FORMAT(""24:00:00"", '%r');
+```
+
+2. What did you expect to see?
+
+```
++-------------------------------+
+| TIME_FORMAT(""24:00:00"", '%r') |
++-------------------------------+
+| 12:00:00 AM |
++-------------------------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+ERROR 1305 (42000): FUNCTION TIME_FORMAT does not exist
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"Built-in function TIME_FORMAT not supported - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+select TIME_FORMAT(""24:00:00"", '%r');
+```
+
+2. What did you expect to see?
+
+```
++-------------------------------+
+| TIME_FORMAT(""24:00:00"", '%r') |
++-------------------------------+
+| 12:00:00 AM |
++-------------------------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+ERROR 1305 (42000): FUNCTION TIME_FORMAT does not exist
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,built in function time format not supported please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql select time format r what did you expect to see time format r am row in set sec what did you see instead error function time format does not exist what version of tidb are you using tidb server v ,1
+3500,6485730661.0,IssuesEvent,2017-08-19 13:18:43,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,type inference of `@@GLOBAL.sql_mode` and `@@SESSION.sql_mode` is incorrect,compatibility easy,"## 1. What did you do?
+
+result type's `Collation` and `Type` of `@@GLOBAL.sql_mode` and `@@SESSION.sql_mode` is incorrect
+
+## 2. What did you expect to see?
+
+```sql
+MySQL > SELECT @@GLOBAL.sql_mode;
+Field 1: `@@GLOBAL.sql_mode`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: VAR_STRING
+Collation: utf8_general_ci (33)
+Length: 411
+Max_length: 137
+Decimals: 31
+Flags:
+
+
++-------------------------------------------------------------------------------------------------------------------------------------------+
+| @@GLOBAL.sql_mode |
++-------------------------------------------------------------------------------------------------------------------------------------------+
+| ONLY_FULL_GROUP_BY,STRICT_TRANS_TABLES,NO_ZERO_IN_DATE,NO_ZERO_DATE,ERROR_FOR_DIVISION_BY_ZERO,NO_AUTO_CREATE_USER,NO_ENGINE_SUBSTITUTION |
++-------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+```sql
+MySQL > SELECT @@SESSION.sql_mode;
+Field 1: `@@SESSION.sql_mode`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: VAR_STRING
+Collation: utf8_general_ci (33)
+Length: 411
+Max_length: 137
+Decimals: 31
+Flags:
+
+
++-------------------------------------------------------------------------------------------------------------------------------------------+
+| @@SESSION.sql_mode |
++-------------------------------------------------------------------------------------------------------------------------------------------+
+| ONLY_FULL_GROUP_BY,STRICT_TRANS_TABLES,NO_ZERO_IN_DATE,NO_ZERO_DATE,ERROR_FOR_DIVISION_BY_ZERO,NO_AUTO_CREATE_USER,NO_ENGINE_SUBSTITUTION |
++-------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+## 3. What did you see instead?
+
+```sql
+TiDB > SELECT @@GLOBAL.sql_mode;
+Field 1: `@@GLOBAL.sql_mode`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: STRING
+Collation: ? (0)
+Length: 0
+Max_length: 42
+Decimals: 31
+Flags:
+
+
++--------------------------------------------+
+| @@GLOBAL.sql_mode |
++--------------------------------------------+
+| STRICT_TRANS_TABLES,NO_ENGINE_SUBSTITUTION |
++--------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+```sql
+TiDB > SELECT @@SESSION.sql_mode;
+Field 1: `@@SESSION.sql_mode`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: STRING
+Collation: ? (0)
+Length: 0
+Max_length: 42
+Decimals: 31
+Flags:
+
+
++--------------------------------------------+
+| @@SESSION.sql_mode |
++--------------------------------------------+
+| STRICT_TRANS_TABLES,NO_ENGINE_SUBSTITUTION |
++--------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+## 4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"type inference of `@@GLOBAL.sql_mode` and `@@SESSION.sql_mode` is incorrect - ## 1. What did you do?
+
+result type's `Collation` and `Type` of `@@GLOBAL.sql_mode` and `@@SESSION.sql_mode` is incorrect
+
+## 2. What did you expect to see?
+
+```sql
+MySQL > SELECT @@GLOBAL.sql_mode;
+Field 1: `@@GLOBAL.sql_mode`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: VAR_STRING
+Collation: utf8_general_ci (33)
+Length: 411
+Max_length: 137
+Decimals: 31
+Flags:
+
+
++-------------------------------------------------------------------------------------------------------------------------------------------+
+| @@GLOBAL.sql_mode |
++-------------------------------------------------------------------------------------------------------------------------------------------+
+| ONLY_FULL_GROUP_BY,STRICT_TRANS_TABLES,NO_ZERO_IN_DATE,NO_ZERO_DATE,ERROR_FOR_DIVISION_BY_ZERO,NO_AUTO_CREATE_USER,NO_ENGINE_SUBSTITUTION |
++-------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+```sql
+MySQL > SELECT @@SESSION.sql_mode;
+Field 1: `@@SESSION.sql_mode`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: VAR_STRING
+Collation: utf8_general_ci (33)
+Length: 411
+Max_length: 137
+Decimals: 31
+Flags:
+
+
++-------------------------------------------------------------------------------------------------------------------------------------------+
+| @@SESSION.sql_mode |
++-------------------------------------------------------------------------------------------------------------------------------------------+
+| ONLY_FULL_GROUP_BY,STRICT_TRANS_TABLES,NO_ZERO_IN_DATE,NO_ZERO_DATE,ERROR_FOR_DIVISION_BY_ZERO,NO_AUTO_CREATE_USER,NO_ENGINE_SUBSTITUTION |
++-------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+## 3. What did you see instead?
+
+```sql
+TiDB > SELECT @@GLOBAL.sql_mode;
+Field 1: `@@GLOBAL.sql_mode`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: STRING
+Collation: ? (0)
+Length: 0
+Max_length: 42
+Decimals: 31
+Flags:
+
+
++--------------------------------------------+
+| @@GLOBAL.sql_mode |
++--------------------------------------------+
+| STRICT_TRANS_TABLES,NO_ENGINE_SUBSTITUTION |
++--------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+```sql
+TiDB > SELECT @@SESSION.sql_mode;
+Field 1: `@@SESSION.sql_mode`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: STRING
+Collation: ? (0)
+Length: 0
+Max_length: 42
+Decimals: 31
+Flags:
+
+
++--------------------------------------------+
+| @@SESSION.sql_mode |
++--------------------------------------------+
+| STRICT_TRANS_TABLES,NO_ENGINE_SUBSTITUTION |
++--------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+## 4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,type inference of global sql mode and session sql mode is incorrect what did you do result type s collation and type of global sql mode and session sql mode is incorrect what did you expect to see sql mysql select global sql mode field global sql mode catalog def database table org table type var string collation general ci length max length decimals flags global sql mode only full group by strict trans tables no zero in date no zero date error for division by zero no auto create user no engine substitution row in set sec sql mysql select session sql mode field session sql mode catalog def database table org table type var string collation general ci length max length decimals flags session sql mode only full group by strict trans tables no zero in date no zero date error for division by zero no auto create user no engine substitution row in set sec what did you see instead sql tidb select global sql mode field global sql mode catalog def database table org table type string collation length max length decimals flags global sql mode strict trans tables no engine substitution row in set sec sql tidb select session sql mode field session sql mode catalog def database table org table type string collation length max length decimals flags session sql mode strict trans tables no engine substitution row in set sec what version of tidb are you using tidb server v ,1
+4994,7600556755.0,IssuesEvent,2018-04-28 03:29:55,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,"Support ""ALTER TABLE ti1 AUTO_INCREMENT 3""",DDL compatibility help wanted,"```
+CREATE TABLE ti1(a INT NOT NULL, b INT, c INT) engine=InnoDB;
+ALTER TABLE ti1 AUTO_INCREMENT 3;
+```
+
+report `line 1 column 32 near "";"" (total length 33)`",True,"Support ""ALTER TABLE ti1 AUTO_INCREMENT 3"" - ```
+CREATE TABLE ti1(a INT NOT NULL, b INT, c INT) engine=InnoDB;
+ALTER TABLE ti1 AUTO_INCREMENT 3;
+```
+
+report `line 1 column 32 near "";"" (total length 33)`",1,support alter table auto increment create table a int not null b int c int engine innodb alter table auto increment report line column near total length ,1
+11625,13672437994.0,IssuesEvent,2020-09-29 08:30:18,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,_utf8mb4 not supported,type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+select left(_utf8mb4 0xD0B0D0B1D0B2, 1);
+select right(_utf8mb4 0xD0B0D0B2D0B2, 1);
+```
+
+2. What did you expect to see?
+
+```
++----------------------------------+
+| left(_utf8mb4 0xD0B0D0B1D0B2, 1) |
++----------------------------------+
+| а |
++----------------------------------+
+1 row in set (0.00 sec)
+
++-----------------------------------+
+| right(_utf8mb4 0xD0B0D0B2D0B2, 1) |
++-----------------------------------+
+| в |
++-----------------------------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+ERROR 1105 (HY000): line 0 column 35 near "", 1)"" (total length 39)
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"_utf8mb4 not supported - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+select left(_utf8mb4 0xD0B0D0B1D0B2, 1);
+select right(_utf8mb4 0xD0B0D0B2D0B2, 1);
+```
+
+2. What did you expect to see?
+
+```
++----------------------------------+
+| left(_utf8mb4 0xD0B0D0B1D0B2, 1) |
++----------------------------------+
+| а |
++----------------------------------+
+1 row in set (0.00 sec)
+
++-----------------------------------+
+| right(_utf8mb4 0xD0B0D0B2D0B2, 1) |
++-----------------------------------+
+| в |
++-----------------------------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+ERROR 1105 (HY000): line 0 column 35 near "", 1)"" (total length 39)
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1, not supported please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql select left select right what did you expect to see left а row in set sec right в row in set sec what did you see instead error line column near total length what version of tidb are you using tidb server v ,1
+42246,17090646116.0,IssuesEvent,2021-07-08 16:58:20,microsoft/BotFramework-Composer,https://api.github.com/repos/microsoft/BotFramework-Composer,reopened,"BUG ""Luis build failed: Cannot read property 'utterances' of undefined"" after training on LUIS.ai",Bot Services Support Type: Bug customer-replied-to customer-reported,"## Describe the bug
+
+Hello! I'm sorry to open another ticket despite having another one opened for another issue, but this one seems like a bigger problem.
+
+When I create any bot (both C# and Node.js) on Composer, if I create the apps on luis.ai through composer (by creating dialogs and entities) as shown on the picture below:
+
+
+
+After I train and publish the AI through LUIS.ai, the bot on Composer becomes unresponsible, I can't even start the bot because of the following error message:
+
+
+
+I saw some topics on the error and they ended on the agreement that the ""solution"" is to delete the conversation apps on Luis.ai and recreate them again through Composer (by restarting the bot). This made the trick for me, the bot works now but I lost all my work on LUIS.ai. What is the point of training an AI through LUIS if I can't use it on Composer after that? Am I missing something?
+
+Is there another solution to this bug?
+
+## Version
+2.0
+## Browser
+
+
+
+- [ ] Electron distribution
+- [ ] Chrome
+- [ ] Safari
+- [ ] Firefox
+- [ X] Edge
+
+## OS
+
+
+
+- [ ] macOS
+- [X ] Windows
+- [ ] Ubuntu
+
+## To Reproduce
+
+Steps to reproduce the behavior:
+
+1. Create an empty bot on composer
+2. Create some dialogs and entities
+3. Connect to luis.ai through the bot settings -> development resources button
+4. Train the AI on luis.ai and publish a new version of the AI
+5. Try to restart the bot
+
+## Expected behavior
+
+Bot restarts with new AI from luis.ai
+
+## Screenshots
+
+
+
+## Additional context
+
+I love the application, Composer and the fast replies Microsoft gives on Github. I truly hope these bugs get fixed because Composer is a great platform for chatbot development",1.0,"BUG ""Luis build failed: Cannot read property 'utterances' of undefined"" after training on LUIS.ai - ## Describe the bug
+
+Hello! I'm sorry to open another ticket despite having another one opened for another issue, but this one seems like a bigger problem.
+
+When I create any bot (both C# and Node.js) on Composer, if I create the apps on luis.ai through composer (by creating dialogs and entities) as shown on the picture below:
+
+
+
+After I train and publish the AI through LUIS.ai, the bot on Composer becomes unresponsible, I can't even start the bot because of the following error message:
+
+
+
+I saw some topics on the error and they ended on the agreement that the ""solution"" is to delete the conversation apps on Luis.ai and recreate them again through Composer (by restarting the bot). This made the trick for me, the bot works now but I lost all my work on LUIS.ai. What is the point of training an AI through LUIS if I can't use it on Composer after that? Am I missing something?
+
+Is there another solution to this bug?
+
+## Version
+2.0
+## Browser
+
+
+
+- [ ] Electron distribution
+- [ ] Chrome
+- [ ] Safari
+- [ ] Firefox
+- [ X] Edge
+
+## OS
+
+
+
+- [ ] macOS
+- [X ] Windows
+- [ ] Ubuntu
+
+## To Reproduce
+
+Steps to reproduce the behavior:
+
+1. Create an empty bot on composer
+2. Create some dialogs and entities
+3. Connect to luis.ai through the bot settings -> development resources button
+4. Train the AI on luis.ai and publish a new version of the AI
+5. Try to restart the bot
+
+## Expected behavior
+
+Bot restarts with new AI from luis.ai
+
+## Screenshots
+
+
+
+## Additional context
+
+I love the application, Composer and the fast replies Microsoft gives on Github. I truly hope these bugs get fixed because Composer is a great platform for chatbot development",0,bug luis build failed cannot read property utterances of undefined after training on luis ai describe the bug hello i m sorry to open another ticket despite having another one opened for another issue but this one seems like a bigger problem when i create any bot both c and node js on composer if i create the apps on luis ai through composer by creating dialogs and entities as shown on the picture below after i train and publish the ai through luis ai the bot on composer becomes unresponsible i can t even start the bot because of the following error message i saw some topics on the error and they ended on the agreement that the solution is to delete the conversation apps on luis ai and recreate them again through composer by restarting the bot this made the trick for me the bot works now but i lost all my work on luis ai what is the point of training an ai through luis if i can t use it on composer after that am i missing something is there another solution to this bug version browser electron distribution chrome safari firefox edge os macos windows ubuntu to reproduce steps to reproduce the behavior create an empty bot on composer create some dialogs and entities connect to luis ai through the bot settings development resources button train the ai on luis ai and publish a new version of the ai try to restart the bot expected behavior bot restarts with new ai from luis ai screenshots additional context i love the application composer and the fast replies microsoft gives on github i truly hope these bugs get fixed because composer is a great platform for chatbot development,0
+6991,9284638287.0,IssuesEvent,2019-03-21 02:41:43,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Need to check and fix more types in `shou (full) columns`,type/compatibility,"## General Question
+
+
+As https://github.com/pingcap/tidb/pull/9810 discussed, we should check more types in `show columns` and ` show full columns`, and fix it!",True,"Need to check and fix more types in `shou (full) columns` - ## General Question
+
+
+As https://github.com/pingcap/tidb/pull/9810 discussed, we should check more types in `show columns` and ` show full columns`, and fix it!",1,need to check and fix more types in shou full columns general question as discussed we should check more types in show columns and show full columns and fix it ,1
+13939,3788390898.0,IssuesEvent,2016-03-21 14:37:02,tarbell-project/tarbell,https://api.github.com/repos/tarbell-project/tarbell,closed,Context variables only work in HTML files,in progress tag: documentation,"Should probably cut [this whole section](http://tarbell.readthedocs.org/en/1.0.5/build.html#where-can-context-variables-be-used) from the docs, or slim it way down, since javascript and CSS files are no longer rendered as templates (until we make that configurable).",1.0,"Context variables only work in HTML files - Should probably cut [this whole section](http://tarbell.readthedocs.org/en/1.0.5/build.html#where-can-context-variables-be-used) from the docs, or slim it way down, since javascript and CSS files are no longer rendered as templates (until we make that configurable).",0,context variables only work in html files should probably cut from the docs or slim it way down since javascript and css files are no longer rendered as templates until we make that configurable ,0
+3790,6653174894.0,IssuesEvent,2017-09-29 07:09:11,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,No length limitation for comment of index,compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+CREATE TABLE t1 (id INT);
+CREATE INDEX id_index ON t1 (id) COMMENT 'MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD';
+```
+
+2. What did you expect to see?
+
+ERROR 1688 (HY000) at line 1: Comment for index 'id_index' is too long (max = 1024)
+
+3. What did you see instead?
+
+Query OK, 0 rows affected (0.05 sec)
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"No length limitation for comment of index - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+CREATE TABLE t1 (id INT);
+CREATE INDEX id_index ON t1 (id) COMMENT 'MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD';
+```
+
+2. What did you expect to see?
+
+ERROR 1688 (HY000) at line 1: Comment for index 'id_index' is too long (max = 1024)
+
+3. What did you see instead?
+
+Query OK, 0 rows affected (0.05 sec)
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,no length limitation for comment of index please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql create table id int create index id index on id comment merge threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold what did you expect to see error at line comment for index id index is too long max what did you see instead query ok rows affected sec what version of tidb are you using tidb server v ,1
+6231,8633471784.0,IssuesEvent,2018-11-22 13:58:19,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,support show hash partition table.,help wanted type/compatibility,"## Bug Report
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```sql
+set @@session.tidb_enable_table_partition = 'on';
+create table th (
+ a int,
+ b int
+) partition by hash(a) partitions 4;
+```
+
+2. What did you expect to see?
+mysql:
+```sql
+mysql root@127.0.0.1:test> show create table th;
++-------+----------------------------------------+
+| Table | Create Table |
++-------+----------------------------------------+
+| th | CREATE TABLE `th` ( |
+| | `a` int(11) DEFAULT NULL, |
+| | `b` int(11) DEFAULT NULL |
+| | ) ENGINE=InnoDB DEFAULT CHARSET=latin1 |
+| | /*!50100 PARTITION BY HASH (a) |
+| | PARTITIONS 4 */ |
++-------+----------------------------------------+
+```
+
+or
+```sql
+mysql root@127.0.0.1:test> show create table th;
++-------+----------------------------------------+
+| Table | Create Table |
++-------+----------------------------------------+
+| th | CREATE TABLE `th` ( |
+| | `a` int(11) DEFAULT NULL, |
+| | `b` int(11) DEFAULT NULL |
+| | ) ENGINE=InnoDB DEFAULT CHARSET=latin1 |
+| | PARTITION BY HASH (a) |
+| | PARTITIONS 4 |
++-------+----------------------------------------+
+```
+
+3. What did you see instead?
+```sql
++-------+-------------------------------------------------------------+
+| Table | Create Table |
++-------+-------------------------------------------------------------+
+| th | CREATE TABLE `th` ( |
+| | `a` int(11) DEFAULT NULL, |
+| | `b` int(11) DEFAULT NULL |
+| | ) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_bin |
+| | PARTITION BY HASH ( `a` ) ( |
+| | PARTITION VALUES LESS THAN (), |
+| | PARTITION VALUES LESS THAN (), |
+| | PARTITION VALUES LESS THAN (), |
+| | PARTITION VALUES LESS THAN () |
+| | ) |
++-------+-------------------------------------------------------------+
+```
+
+
+Related issue:
+https://github.com/pingcap/tidb/issues/7907
+
+",True,"support show hash partition table. - ## Bug Report
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```sql
+set @@session.tidb_enable_table_partition = 'on';
+create table th (
+ a int,
+ b int
+) partition by hash(a) partitions 4;
+```
+
+2. What did you expect to see?
+mysql:
+```sql
+mysql root@127.0.0.1:test> show create table th;
++-------+----------------------------------------+
+| Table | Create Table |
++-------+----------------------------------------+
+| th | CREATE TABLE `th` ( |
+| | `a` int(11) DEFAULT NULL, |
+| | `b` int(11) DEFAULT NULL |
+| | ) ENGINE=InnoDB DEFAULT CHARSET=latin1 |
+| | /*!50100 PARTITION BY HASH (a) |
+| | PARTITIONS 4 */ |
++-------+----------------------------------------+
+```
+
+or
+```sql
+mysql root@127.0.0.1:test> show create table th;
++-------+----------------------------------------+
+| Table | Create Table |
++-------+----------------------------------------+
+| th | CREATE TABLE `th` ( |
+| | `a` int(11) DEFAULT NULL, |
+| | `b` int(11) DEFAULT NULL |
+| | ) ENGINE=InnoDB DEFAULT CHARSET=latin1 |
+| | PARTITION BY HASH (a) |
+| | PARTITIONS 4 |
++-------+----------------------------------------+
+```
+
+3. What did you see instead?
+```sql
++-------+-------------------------------------------------------------+
+| Table | Create Table |
++-------+-------------------------------------------------------------+
+| th | CREATE TABLE `th` ( |
+| | `a` int(11) DEFAULT NULL, |
+| | `b` int(11) DEFAULT NULL |
+| | ) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_bin |
+| | PARTITION BY HASH ( `a` ) ( |
+| | PARTITION VALUES LESS THAN (), |
+| | PARTITION VALUES LESS THAN (), |
+| | PARTITION VALUES LESS THAN (), |
+| | PARTITION VALUES LESS THAN () |
+| | ) |
++-------+-------------------------------------------------------------+
+```
+
+
+Related issue:
+https://github.com/pingcap/tidb/issues/7907
+
+",1,support show hash partition table bug report what did you do if possible provide a recipe for reproducing the error sql set session tidb enable table partition on create table th a int b int partition by hash a partitions what did you expect to see mysql sql mysql root test show create table th table create table th create table th a int default null b int default null engine innodb default charset partition by hash a partitions or sql mysql root test show create table th table create table th create table th a int default null b int default null engine innodb default charset partition by hash a partitions what did you see instead sql table create table th create table th a int default null b int default null engine innodb default charset collate bin partition by hash a partition values less than partition values less than partition values less than partition values less than related issue ,1
+301266,9218166044.0,IssuesEvent,2019-03-11 12:44:15,rism-ch/muscat,https://api.github.com/repos/rism-ch/muscat,opened,Prevent source.id == source.source_id,Bug First priority Source,"if you add a 773 with the same id as the source, it will become the parent of itself.
+We need:
+
+ - [ ] Prevent it in the backend
+ - [ ] Add it to the validation",1.0,"Prevent source.id == source.source_id - if you add a 773 with the same id as the source, it will become the parent of itself.
+We need:
+
+ - [ ] Prevent it in the backend
+ - [ ] Add it to the validation",0,prevent source id source source id if you add a with the same id as the source it will become the parent of itself we need prevent it in the backend add it to the validation,0
+8680,10606147953.0,IssuesEvent,2019-10-10 22:19:36,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,tidb gives error while mysql gives warning when time is invalid,help wanted type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+CREATE TABLE t1 (
+ a INT,
+ ts TIMESTAMP DEFAULT NOW(),
+ PRIMARY KEY (ts)
+ );
+SELECT * FROM t1 WHERE ts = '2008-12-31 23:59:60';
+```
+
+2. What did you expect to see?
+
+mysql:
+
+```
+mysql> SELECT * FROM t1 WHERE ts = '2008-12-31 23:59:60';
+Empty set, 2 warnings (0.00 sec)
+
+mysql> show warnings;
++---------+------+--------------------------------------------------------------------------+
+| Level | Code | Message |
++---------+------+--------------------------------------------------------------------------+
+| Warning | 1292 | Incorrect datetime value: '2008-12-31 23:59:60' for column 'ts' at row 1 |
+| Warning | 1292 | Incorrect datetime value: '2008-12-31 23:59:60' for column 'ts' at row 1 |
++---------+------+--------------------------------------------------------------------------+
+2 rows in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+tidb:
+
+```
+mysql> SELECT * FROM t1 WHERE ts = '2008-12-31 23:59:60';
+ERROR 1292 (22007): invalid time format: '60'
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+Release Version: v2.0.3
+Git Commit Hash: e4878329f0c69d7b810b8b40fb3b8071c69b5e02
+Git Commit Branch: HEAD
+UTC Build Time: 2018-06-29 11:43:51
+GoVersion: go version go1.10.3 darwin/amd64
+TiKV Min Version: 2.0.0-rc.4.1
+```",True,"tidb gives error while mysql gives warning when time is invalid - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+CREATE TABLE t1 (
+ a INT,
+ ts TIMESTAMP DEFAULT NOW(),
+ PRIMARY KEY (ts)
+ );
+SELECT * FROM t1 WHERE ts = '2008-12-31 23:59:60';
+```
+
+2. What did you expect to see?
+
+mysql:
+
+```
+mysql> SELECT * FROM t1 WHERE ts = '2008-12-31 23:59:60';
+Empty set, 2 warnings (0.00 sec)
+
+mysql> show warnings;
++---------+------+--------------------------------------------------------------------------+
+| Level | Code | Message |
++---------+------+--------------------------------------------------------------------------+
+| Warning | 1292 | Incorrect datetime value: '2008-12-31 23:59:60' for column 'ts' at row 1 |
+| Warning | 1292 | Incorrect datetime value: '2008-12-31 23:59:60' for column 'ts' at row 1 |
++---------+------+--------------------------------------------------------------------------+
+2 rows in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+tidb:
+
+```
+mysql> SELECT * FROM t1 WHERE ts = '2008-12-31 23:59:60';
+ERROR 1292 (22007): invalid time format: '60'
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+Release Version: v2.0.3
+Git Commit Hash: e4878329f0c69d7b810b8b40fb3b8071c69b5e02
+Git Commit Branch: HEAD
+UTC Build Time: 2018-06-29 11:43:51
+GoVersion: go version go1.10.3 darwin/amd64
+TiKV Min Version: 2.0.0-rc.4.1
+```",1,tidb gives error while mysql gives warning when time is invalid please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql create table a int ts timestamp default now primary key ts select from where ts what did you expect to see mysql mysql select from where ts empty set warnings sec mysql show warnings level code message warning incorrect datetime value for column ts at row warning incorrect datetime value for column ts at row rows in set sec what did you see instead tidb mysql select from where ts error invalid time format what version of tidb are you using tidb server v or run select tidb version on tidb release version git commit hash git commit branch head utc build time goversion go version darwin tikv min version rc ,1
+5094,7702926353.0,IssuesEvent,2018-05-21 05:59:49,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,inconsistent create table behavior when set timestamp col default value to 0,compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+``` go
+create table t(a timestamp not null default 0);
+```
+
+2. What did you expect to see?
+``` go
+mysql(127.0.0.1)> create table t(a timestamp null default 0);
+ERROR 1067 (42000): Invalid default value for 'a'
+```
+
+
+3. What did you see instead?
+```go
+tidb(127.0.0.1)> create table t (a timestamp null default 0);
+Query OK, 0 rows affected (0.13 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```go
+tidb(127.0.0.1)> select tidb_version();
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v2.0.0-rc.3-12-gb6b708aa4
+Git Commit Hash: b6b708aa4369f89147a3f9a31a9daff38c489999
+Git Branch: master
+UTC Build Time: 2018-04-03 08:14:49
+GoVersion: go version go1.9.5 linux/amd64
+TiKV Min Version: 1.1.0-dev.2 |
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+```
+",True,"inconsistent create table behavior when set timestamp col default value to 0 - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+``` go
+create table t(a timestamp not null default 0);
+```
+
+2. What did you expect to see?
+``` go
+mysql(127.0.0.1)> create table t(a timestamp null default 0);
+ERROR 1067 (42000): Invalid default value for 'a'
+```
+
+
+3. What did you see instead?
+```go
+tidb(127.0.0.1)> create table t (a timestamp null default 0);
+Query OK, 0 rows affected (0.13 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```go
+tidb(127.0.0.1)> select tidb_version();
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v2.0.0-rc.3-12-gb6b708aa4
+Git Commit Hash: b6b708aa4369f89147a3f9a31a9daff38c489999
+Git Branch: master
+UTC Build Time: 2018-04-03 08:14:49
+GoVersion: go version go1.9.5 linux/amd64
+TiKV Min Version: 1.1.0-dev.2 |
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+```
+",1,inconsistent create table behavior when set timestamp col default value to please answer these questions before submitting your issue thanks what did you do go create table t a timestamp not null default what did you expect to see go mysql create table t a timestamp null default error invalid default value for a what did you see instead go tidb create table t a timestamp null default query ok rows affected sec what version of tidb are you using tidb server v or run select tidb version on tidb go tidb select tidb version tidb version release version rc git commit hash git branch master utc build time goversion go version linux tikv min version dev ,1
+69114,14970070454.0,IssuesEvent,2021-01-27 19:04:02,jgeraigery/experian-java,https://api.github.com/repos/jgeraigery/experian-java,closed,CVE-2019-14893 (High) detected in jackson-databind-2.9.2.jar - autoclosed,security vulnerability,"## CVE-2019-14893 - High Severity Vulnerability
+ Vulnerable Library - jackson-databind-2.9.2.jar
+
General data-binding functionality for Jackson: works on core streaming API
+
+A flaw was discovered in FasterXML jackson-databind in all versions before 2.9.10 and 2.10.0, where it would permit polymorphic deserialization of malicious objects using the xalan JNDI gadget when used in conjunction with polymorphic type handling methods such as `enableDefaultTyping()` or when @JsonTypeInfo is using `Id.CLASS` or `Id.MINIMAL_CLASS` or in any other way which ObjectMapper.readValue might instantiate objects from unsafe sources. An attacker could use this flaw to execute arbitrary code.
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-```
-mysql> select tidb_version();
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v3.0.0-beta.1-218-g2f7241138-dirty
-Git Commit Hash: 2f7241138adfc434f4b199ecae68fb83ad33b36b
-Git Branch: myfeature-perioddiff
-UTC Build Time: 2019-05-07 03:36:21
-GoVersion: go version go1.11.4 darwin/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false |
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-1 row in set (0.00 sec)
-```
-",1,function period diff is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error function period diff is not compatible with mysql what did you expect to see mysql mysql select period diff error incorrect arguments to period diff what did you see instead tidb mysql select period diff period diff row in set sec what version of tidb are you using tidb server v or run select tidb version on tidb mysql select tidb version tidb version release version beta dirty git commit hash git branch myfeature perioddiff utc build time goversion go version darwin race enabled false tikv min version alpha check table before drop false row in set sec ,1
-301115,9216196333.0,IssuesEvent,2019-03-11 07:11:51,etternagame/etterna,https://api.github.com/repos/etternagame/etterna,closed,Misc Bugs here and there.,Priority: Low,"I made a theme that uses etterna's fallback theme. I went though trying to debug a few things here and there. I found a few issues.
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Network
+ - Attack Complexity: Low
+ - Privileges Required: None
+ - User Interaction: None
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: High
+ - Integrity Impact: High
+ - Availability Impact: High
+
+For more information on CVSS3 Scores, click here.
+
+
+
+ Suggested Fix
+
-ScreenSelectPlayMode::ChoiceNonstop=""""
-ScreenSelectPlayMode::ChoiceOni=""""
-ScreenSelectPlayMode::ChoiceEndless=""""
-OptionExplanations::FullTapExplosions="""" (I could not actually get this one to work. Must be broken.)
+
+
+
-(Menu Options)
+***
+:rescue_worker_helmet: Automatic Remediation is available for this issue
+",True,"CVE-2019-14893 (High) detected in jackson-databind-2.9.2.jar - autoclosed - ## CVE-2019-14893 - High Severity Vulnerability
+ Vulnerable Library - jackson-databind-2.9.2.jar
-Jukebox does not work. Should be removed.
-Edit Step/Chart does not work. Should be removed.
+
General data-binding functionality for Jackson: works on core streaming API
+
+A flaw was discovered in FasterXML jackson-databind in all versions before 2.9.10 and 2.10.0, where it would permit polymorphic deserialization of malicious objects using the xalan JNDI gadget when used in conjunction with polymorphic type handling methods such as `enableDefaultTyping()` or when @JsonTypeInfo is using `Id.CLASS` or `Id.MINIMAL_CLASS` or in any other way which ObjectMapper.readValue might instantiate objects from unsafe sources. An attacker could use this flaw to execute arbitrary code.
-Couples Mode crashes the game. Needs to be removed.
+
+For more information on CVSS3 Scores, click here.
+
+
+
+ Suggested Fix
+
-Verses and Doubles work but should be removed. (Since player 2 was removed, likely, this will not work in doubles/verses.)
-Nonstop, Oni, and Endless should be removed. (If done, you can ignore the metrics then.)
-
------------------------------------------------------------------------------------------------------------
+
-More bugs found. The following seemed to have been removed from the game:
+
+
+
-(However, I did a search in the repo and some things still remain noting these, Please be sure to remove them if this is the intended case.)
+***
+:rescue_worker_helmet: Automatic Remediation is available for this issue
+",0,cve high detected in jackson databind jar autoclosed cve high severity vulnerability vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file experian java mavenworkspace bis services lib bis services base pom xml path to vulnerable library canner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a flaw was discovered in fasterxml jackson databind in all versions before and where it would permit polymorphic deserialization of malicious objects using the xalan jndi gadget when used in conjunction with polymorphic type handling methods such as enabledefaulttyping or when jsontypeinfo is using id class or id minimal class or in any other way which objectmapper readvalue might instantiate objects from unsafe sources an attacker could use this flaw to execute arbitrary code publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind rescue worker helmet automatic remediation is available for this issue isopenpronvulnerability true ispackagebased true isdefaultbranch true packages vulnerabilityidentifier cve vulnerabilitydetails a flaw was discovered in fasterxml jackson databind in all versions before and where it would permit polymorphic deserialization of malicious objects using the xalan jndi gadget when used in conjunction with polymorphic type handling methods such as enabledefaulttyping or when jsontypeinfo is using id class or id minimal class or in any other way which objectmapper readvalue might instantiate objects from unsafe sources an attacker could use this flaw to execute arbitrary code vulnerabilityurl ,0
+7028,9305281659.0,IssuesEvent,2019-03-25 05:47:18,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,`TIME_FORMAT` is not compatible with MySQL,for new contributors help wanted type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+SELECT TIME_FORMAT(""24:00:00"", '%r');
+SELECT TIME_FORMAT(""25:00:00"", '%r');
+SELECT TIME_FORMAT(""24:00:00"", '%l %p');
+```
+
+2. What did you expect to see?
+In Mysql
+```
+mysql> SELECT TIME_FORMAT(""24:00:00"", '%r');
++-------------------------------+
+| TIME_FORMAT(""24:00:00"", '%r') |
++-------------------------------+
+| 12:00:00 AM |
++-------------------------------+
+1 row in set (0.00 sec)
+
+mysql> SELECT TIME_FORMAT(""25:00:00"", '%r');
++-------------------------------+
+| TIME_FORMAT(""25:00:00"", '%r') |
++-------------------------------+
+| 01:00:00 AM |
++-------------------------------+
+1 row in set (0.00 sec)
+
+mysql> SELECT TIME_FORMAT(""24:00:00"", '%l %p');
++----------------------------------+
+| TIME_FORMAT(""24:00:00"", '%l %p') |
++----------------------------------+
+| 12 AM |
++----------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+In TiDB
+```
+mysql> SELECT TIME_FORMAT(""24:00:00"", '%r');
++-------------------------------+
+| TIME_FORMAT(""24:00:00"", '%r') |
++-------------------------------+
+| 12:00:00 PM |
++-------------------------------+
+1 row in set (0.00 sec)
+
+mysql> SELECT TIME_FORMAT(""25:00:00"", '%r');
++-------------------------------+
+| TIME_FORMAT(""25:00:00"", '%r') |
++-------------------------------+
+| 13:00:00 PM |
++-------------------------------+
+1 row in set (0.00 sec)
+
+mysql> SELECT TIME_FORMAT(""24:00:00"", '%l %p');
++----------------------------------+
+| TIME_FORMAT(""24:00:00"", '%l %p') |
++----------------------------------+
+| 0 AM |
++----------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-227-g06183393e-dirty
+Git Commit Hash: 06183393ed536aa248248b72d4bf9f5010947f66
+Git Branch: master
+UTC Build Time: 2019-03-15 08:22:53
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+```
+
+",True,"`TIME_FORMAT` is not compatible with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+SELECT TIME_FORMAT(""24:00:00"", '%r');
+SELECT TIME_FORMAT(""25:00:00"", '%r');
+SELECT TIME_FORMAT(""24:00:00"", '%l %p');
+```
+
+2. What did you expect to see?
+In Mysql
+```
+mysql> SELECT TIME_FORMAT(""24:00:00"", '%r');
++-------------------------------+
+| TIME_FORMAT(""24:00:00"", '%r') |
++-------------------------------+
+| 12:00:00 AM |
++-------------------------------+
+1 row in set (0.00 sec)
+
+mysql> SELECT TIME_FORMAT(""25:00:00"", '%r');
++-------------------------------+
+| TIME_FORMAT(""25:00:00"", '%r') |
++-------------------------------+
+| 01:00:00 AM |
++-------------------------------+
+1 row in set (0.00 sec)
+
+mysql> SELECT TIME_FORMAT(""24:00:00"", '%l %p');
++----------------------------------+
+| TIME_FORMAT(""24:00:00"", '%l %p') |
++----------------------------------+
+| 12 AM |
++----------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+In TiDB
+```
+mysql> SELECT TIME_FORMAT(""24:00:00"", '%r');
++-------------------------------+
+| TIME_FORMAT(""24:00:00"", '%r') |
++-------------------------------+
+| 12:00:00 PM |
++-------------------------------+
+1 row in set (0.00 sec)
+
+mysql> SELECT TIME_FORMAT(""25:00:00"", '%r');
++-------------------------------+
+| TIME_FORMAT(""25:00:00"", '%r') |
++-------------------------------+
+| 13:00:00 PM |
++-------------------------------+
+1 row in set (0.00 sec)
+
+mysql> SELECT TIME_FORMAT(""24:00:00"", '%l %p');
++----------------------------------+
+| TIME_FORMAT(""24:00:00"", '%l %p') |
++----------------------------------+
+| 0 AM |
++----------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-227-g06183393e-dirty
+Git Commit Hash: 06183393ed536aa248248b72d4bf9f5010947f66
+Git Branch: master
+UTC Build Time: 2019-03-15 08:22:53
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+```
+
+",1, time format is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error select time format r select time format r select time format l p what did you expect to see in mysql mysql select time format r time format r am row in set sec mysql select time format r time format r am row in set sec mysql select time format l p time format l p am row in set sec what did you see instead in tidb mysql select time format r time format r pm row in set sec mysql select time format r time format r pm row in set sec mysql select time format l p time format l p am row in set sec what version of tidb are you using tidb server v or run select tidb version on tidb tidb version release version beta dirty git commit hash git branch master utc build time goversion go version darwin race enabled false tikv min version alpha check table before drop false ,1
+563355,16681158968.0,IssuesEvent,2021-06-08 00:02:47,ThePyrotechnic/rocketleague-spotify,https://api.github.com/repos/ThePyrotechnic/rocketleague-spotify,closed,Authenticate with the user's Steam account,high priority,"In order to release publicly, the API must implement the [Steam OpenID flow](https://partner.steamgames.com/doc/features/auth#website) in order to authenticate all API calls and prevent users from altering each other's settings.",1.0,"Authenticate with the user's Steam account - In order to release publicly, the API must implement the [Steam OpenID flow](https://partner.steamgames.com/doc/features/auth#website) in order to authenticate all API calls and prevent users from altering each other's settings.",0,authenticate with the user s steam account in order to release publicly the api must implement the in order to authenticate all api calls and prevent users from altering each other s settings ,0
+183023,31141929913.0,IssuesEvent,2023-08-16 01:14:41,MetaMask/metamask-extension,https://api.github.com/repos/MetaMask/metamask-extension,opened,Replace deprecated Callout component with BannerAlert from the component-library,good first issue team-design-system,"
+### Description
+
+Currently, the extension is using an outdated `Callout` component, which needs to be replaced with the new `BannerAlert` component.
+
+This is a massive undertaking by itself and creating a single PR would be too large. Smaller PRs can be submitted against this issue to ensure easier review and gradual improvements.
+
+### Technical Details
+
+- Replace instances of `Callout` component (`ui/components/ui/callout/callout.js`) with `BannerAlert` component (`ui/components/component-library/banner-alert/banner-alert.js`)
+- Component APIs are slightly different so ensure all props have been migrated appropriately
+
+### Acceptance Criteria
+
+- Instances of `Callout` component are completely replaced with the new `BannerAlert` component
+- The component APIs are updated to reflect the changes in the new `Callout`` component and there is no functional changes or visual regression
+- Each Pull Request (PR) should include **no more than 3 files**
+- The code changes should pass Jest tests, linting, and Storybook without any errors.
+- The PR must include before and after screenshots of the UI to ensure there are no visual regressions.
+
+If the acceptance criteria is not met, PRs may be closed.
+
+### Difficulty: Intermediate
+
+Good first issue for: External contributors who are familiar with running the extension locally, have knowledge of React, component props, Jest tests, linting, and Storybook, and want to contribute to improving the cohesiveness of UI in the extension
+",1.0,"Replace deprecated Callout component with BannerAlert from the component-library -
+### Description
+
+Currently, the extension is using an outdated `Callout` component, which needs to be replaced with the new `BannerAlert` component.
+
+This is a massive undertaking by itself and creating a single PR would be too large. Smaller PRs can be submitted against this issue to ensure easier review and gradual improvements.
+
+### Technical Details
+
+- Replace instances of `Callout` component (`ui/components/ui/callout/callout.js`) with `BannerAlert` component (`ui/components/component-library/banner-alert/banner-alert.js`)
+- Component APIs are slightly different so ensure all props have been migrated appropriately
+
+### Acceptance Criteria
+
+- Instances of `Callout` component are completely replaced with the new `BannerAlert` component
+- The component APIs are updated to reflect the changes in the new `Callout`` component and there is no functional changes or visual regression
+- Each Pull Request (PR) should include **no more than 3 files**
+- The code changes should pass Jest tests, linting, and Storybook without any errors.
+- The PR must include before and after screenshots of the UI to ensure there are no visual regressions.
+
+If the acceptance criteria is not met, PRs may be closed.
+
+### Difficulty: Intermediate
+
+Good first issue for: External contributors who are familiar with running the extension locally, have knowledge of React, component props, Jest tests, linting, and Storybook, and want to contribute to improving the cohesiveness of UI in the extension
+",0,replace deprecated callout component with banneralert from the component library description currently the extension is using an outdated callout component which needs to be replaced with the new banneralert component this is a massive undertaking by itself and creating a single pr would be too large smaller prs can be submitted against this issue to ensure easier review and gradual improvements technical details replace instances of callout component ui components ui callout callout js with banneralert component ui components component library banner alert banner alert js component apis are slightly different so ensure all props have been migrated appropriately acceptance criteria instances of callout component are completely replaced with the new banneralert component the component apis are updated to reflect the changes in the new callout component and there is no functional changes or visual regression each pull request pr should include no more than files the code changes should pass jest tests linting and storybook without any errors the pr must include before and after screenshots of the ui to ensure there are no visual regressions if the acceptance criteria is not met prs may be closed difficulty intermediate good first issue for external contributors who are familiar with running the extension locally have knowledge of react component props jest tests linting and storybook and want to contribute to improving the cohesiveness of ui in the extension ,0
+5630,8114859545.0,IssuesEvent,2018-08-15 03:05:44,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,LOAD DATA does not support to set character set,type/compatibility,"Part of MySQL syntax looks like below:
+```
+LOAD DATA [LOW_PRIORITY | CONCURRENT] [LOCAL] INFILE 'file_name'
+ [REPLACE | IGNORE]
+ INTO TABLE tbl_name
+ [PARTITION (partition_name [, partition_name] ...)]
+ [CHARACTER SET charset_name]
+```
+It has a character set option in it, but TiDB not.
+TiDB version: 0d18ac2c18c31d7d2fcf85ab7828359df0408c7f
+
+",True,"LOAD DATA does not support to set character set - Part of MySQL syntax looks like below:
+```
+LOAD DATA [LOW_PRIORITY | CONCURRENT] [LOCAL] INFILE 'file_name'
+ [REPLACE | IGNORE]
+ INTO TABLE tbl_name
+ [PARTITION (partition_name [, partition_name] ...)]
+ [CHARACTER SET charset_name]
+```
+It has a character set option in it, but TiDB not.
+TiDB version: 0d18ac2c18c31d7d2fcf85ab7828359df0408c7f
+
+",1,load data does not support to set character set part of mysql syntax looks like below load data infile file name into table tbl name it has a character set option in it but tidb not tidb version ,1
+390033,26844603212.0,IssuesEvent,2023-02-03 05:23:50,NASA-AMMOS/aerie,https://api.github.com/repos/NASA-AMMOS/aerie,closed,Add search feature to help documentation,documentation,"As far as I can tell there's no ability to search the aerie documentation website. There's a lot of information in there and as a newcomer it's hard to know where to find things.
+
+https://nasa-ammos.github.io/aerie/stable/",1.0,"Add search feature to help documentation - As far as I can tell there's no ability to search the aerie documentation website. There's a lot of information in there and as a newcomer it's hard to know where to find things.
+
+https://nasa-ammos.github.io/aerie/stable/",0,add search feature to help documentation as far as i can tell there s no ability to search the aerie documentation website there s a lot of information in there and as a newcomer it s hard to know where to find things ,0
+7376,9629016732.0,IssuesEvent,2019-05-15 08:39:40,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Casting string to real is not compatible with MySQL,component/expression help wanted type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+create table t (a varchar(30));
+insert into t values (2), ("""");
+select * from t where a=2;
+show warnings;
+delete from t where a=2;
+```
+
+2. What did you expect to see?
+```
+mysql> create table t (a varchar(30));
+Query OK, 0 rows affected (0.05 sec)
+
+mysql> insert into t values (2), ("""");
+Query OK, 2 rows affected (0.01 sec)
+Records: 2 Duplicates: 0 Warnings: 0
+
+mysql> select * from t where a=2;
++------+
+| a |
++------+
+| 2 |
++------+
+1 row in set (0.00 sec)
+
+mysql> show warnings;
+Empty set (0.00 sec)
+
+mysql> delete from t where a=2;
+Query OK, 1 row affected (0.05 sec)
+```
+
+
+3. What did you see instead?
+```
+mysql> create table t (a varchar(30));
+Query OK, 0 rows affected (0.00 sec)
+
+mysql> insert into t values (2), ("""");
+Query OK, 2 rows affected (0.01 sec)
+Records: 2 Duplicates: 0 Warnings: 0
+
+mysql> select * from t where a=2;
++------+
+| a |
++------+
+| 2 |
++------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> show warnings;
++---------+------+----------------+
+| Level | Code | Message |
++---------+------+----------------+
+| Warning | 1265 | Data Truncated |
++---------+------+----------------+
+1 row in set (0.00 sec)
+
+mysql> delete from t where a=2;
+ERROR 1265 (01000): Data Truncated
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+mysql> select tidb_version();
++--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-rc.1-58-gfc2768c02
+Git Commit Hash: fc2768c0297be90925cea1b83b3bb0b7997ec00b
+Git Branch: fix-10181
+UTC Build Time: 2019-05-15 08:31:51
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+",True,"Casting string to real is not compatible with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+create table t (a varchar(30));
+insert into t values (2), ("""");
+select * from t where a=2;
+show warnings;
+delete from t where a=2;
+```
+
+2. What did you expect to see?
+```
+mysql> create table t (a varchar(30));
+Query OK, 0 rows affected (0.05 sec)
+
+mysql> insert into t values (2), ("""");
+Query OK, 2 rows affected (0.01 sec)
+Records: 2 Duplicates: 0 Warnings: 0
+
+mysql> select * from t where a=2;
++------+
+| a |
++------+
+| 2 |
++------+
+1 row in set (0.00 sec)
+
+mysql> show warnings;
+Empty set (0.00 sec)
+
+mysql> delete from t where a=2;
+Query OK, 1 row affected (0.05 sec)
+```
+
+
+3. What did you see instead?
+```
+mysql> create table t (a varchar(30));
+Query OK, 0 rows affected (0.00 sec)
+
+mysql> insert into t values (2), ("""");
+Query OK, 2 rows affected (0.01 sec)
+Records: 2 Duplicates: 0 Warnings: 0
+
+mysql> select * from t where a=2;
++------+
+| a |
++------+
+| 2 |
++------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> show warnings;
++---------+------+----------------+
+| Level | Code | Message |
++---------+------+----------------+
+| Warning | 1265 | Data Truncated |
++---------+------+----------------+
+1 row in set (0.00 sec)
+
+mysql> delete from t where a=2;
+ERROR 1265 (01000): Data Truncated
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+mysql> select tidb_version();
++--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-rc.1-58-gfc2768c02
+Git Commit Hash: fc2768c0297be90925cea1b83b3bb0b7997ec00b
+Git Branch: fix-10181
+UTC Build Time: 2019-05-15 08:31:51
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+",1,casting string to real is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error create table t a varchar insert into t values select from t where a show warnings delete from t where a what did you expect to see mysql create table t a varchar query ok rows affected sec mysql insert into t values query ok rows affected sec records duplicates warnings mysql select from t where a a row in set sec mysql show warnings empty set sec mysql delete from t where a query ok row affected sec what did you see instead mysql create table t a varchar query ok rows affected sec mysql insert into t values query ok rows affected sec records duplicates warnings mysql select from t where a a row in set warning sec mysql show warnings level code message warning data truncated row in set sec mysql delete from t where a error data truncated what version of tidb are you using tidb server v or run select tidb version on tidb mysql select tidb version tidb version release version rc git commit hash git branch fix utc build time goversion go version darwin race enabled false tikv min version alpha check table before drop false row in set sec ,1
+8677,10605717161.0,IssuesEvent,2019-10-10 21:08:22,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,GUI client can't not show the rows of the table ,type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+The navicat client always shows rows and data length of 100, which cannot display these two values correctly. So are tools like heidisql.
+
+
+2. What did you expect to see?
+The GUI client displays the rows and data length values in the table correctly.
+
+3. What did you see instead?
+The GUI client displays the rows and data length values in the table correctly.
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+Git Commit Hash: 6921161fde5c74c66d022f98ff9c793a0d37f148
+UTC Build Time: 2017-08-01 03:35:43
+navicat v12.0.x(MAC)
+",True,"GUI client can't not show the rows of the table - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+The navicat client always shows rows and data length of 100, which cannot display these two values correctly. So are tools like heidisql.
+
+
+2. What did you expect to see?
+The GUI client displays the rows and data length values in the table correctly.
+
+3. What did you see instead?
+The GUI client displays the rows and data length values in the table correctly.
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+Git Commit Hash: 6921161fde5c74c66d022f98ff9c793a0d37f148
+UTC Build Time: 2017-08-01 03:35:43
+navicat v12.0.x(MAC)
+",1,gui client can t not show the rows of the table please answer these questions before submitting your issue thanks what did you do the navicat client always shows rows and data length of which cannot display these two values correctly so are tools like heidisql what did you expect to see the gui client displays the rows and data length values in the table correctly what did you see instead the gui client displays the rows and data length values in the table correctly what version of tidb are you using tidb server v git commit hash utc build time navicat x mac ,1
+6922,9213835266.0,IssuesEvent,2019-03-10 15:17:05,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Error message about `select ... inner join` is not same with MYSQL.,help wanted type/compatibility,"# Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+## 1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+### Scene 1
+Execute `select person.id from person inner join person on person.id = person.id;` with no table;
+
+### Scene 2
+Execute `select person.id from person inner join person on person.id = person.id;` with table exist;
+## 2. What did you expect to see?
+
+### Scene 1
+**In MYSQL**
+```SQL
+mysql> select person.id from person inner join person on person.id = person.id;
+ERROR 1066 (42000): Not unique table/alias: 'person'
+mysql>
+mysql> select version();
++-------------------------+
+| version() |
++-------------------------+
+| 5.7.25-0ubuntu0.18.04.2 |
++-------------------------+
+1 row in set (0.00 sec)
+mysql>
+```
+
+### Scene 2
+**In MYSQL**
+```SQL
+mysql> select version();
++-------------------------+
+| version() |
++-------------------------+
+| 5.7.25-0ubuntu0.18.04.2 |
++-------------------------+
+1 row in set (0.00 sec)
+
+mysql> create table person(id int(4));
+Query OK, 0 rows affected (0.02 sec)
+mysql> select person.id from person inner join person on person.id = person.id;
+ERROR 1066 (42000): Not unique table/alias: 'person'
+```
+
+
+3. What did you see instead?
+
+### Scene 1
+**In TiDB**
+```SQL
+TiDB> select person.id from person inner join person on person.id = person.id;
+ERROR 1146 (42S02): Table 'test.person' doesn't exist
+```
+
+### Scene 2
+**In TiDB**
+```SQL
+TiDB> create table person(id int(4));
+Query OK, 0 rows affected (0.01 sec)
+TiDB> select person.id from person inner join person on person.id = person.id;
+ERROR 1052 (23000): Column 'id' in field list is ambiguous
+```
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```SQL
+TiDB> select tidb_version()\G;
+*************************** 1. row ***************************
+tidb_version(): Release Version: v3.0.0-beta-155-g4ccc4c1bc-dirty
+Git Commit Hash: 4ccc4c1bcb41e4dd958c7ae5eb23e905957e7433
+Git Branch: master
+UTC Build Time: 2019-03-06 07:11:01
+GoVersion: go version go1.12 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false
+1 row in set (0.00 sec)
+```",True,"Error message about `select ... inner join` is not same with MYSQL. - # Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+## 1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+### Scene 1
+Execute `select person.id from person inner join person on person.id = person.id;` with no table;
+
+### Scene 2
+Execute `select person.id from person inner join person on person.id = person.id;` with table exist;
+## 2. What did you expect to see?
+
+### Scene 1
+**In MYSQL**
+```SQL
+mysql> select person.id from person inner join person on person.id = person.id;
+ERROR 1066 (42000): Not unique table/alias: 'person'
+mysql>
+mysql> select version();
++-------------------------+
+| version() |
++-------------------------+
+| 5.7.25-0ubuntu0.18.04.2 |
++-------------------------+
+1 row in set (0.00 sec)
+mysql>
+```
+
+### Scene 2
+**In MYSQL**
+```SQL
+mysql> select version();
++-------------------------+
+| version() |
++-------------------------+
+| 5.7.25-0ubuntu0.18.04.2 |
++-------------------------+
+1 row in set (0.00 sec)
+
+mysql> create table person(id int(4));
+Query OK, 0 rows affected (0.02 sec)
+mysql> select person.id from person inner join person on person.id = person.id;
+ERROR 1066 (42000): Not unique table/alias: 'person'
+```
+
+
+3. What did you see instead?
+
+### Scene 1
+**In TiDB**
+```SQL
+TiDB> select person.id from person inner join person on person.id = person.id;
+ERROR 1146 (42S02): Table 'test.person' doesn't exist
+```
+
+### Scene 2
+**In TiDB**
+```SQL
+TiDB> create table person(id int(4));
+Query OK, 0 rows affected (0.01 sec)
+TiDB> select person.id from person inner join person on person.id = person.id;
+ERROR 1052 (23000): Column 'id' in field list is ambiguous
+```
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```SQL
+TiDB> select tidb_version()\G;
+*************************** 1. row ***************************
+tidb_version(): Release Version: v3.0.0-beta-155-g4ccc4c1bc-dirty
+Git Commit Hash: 4ccc4c1bcb41e4dd958c7ae5eb23e905957e7433
+Git Branch: master
+UTC Build Time: 2019-03-06 07:11:01
+GoVersion: go version go1.12 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false
+1 row in set (0.00 sec)
+```",1,error message about select inner join is not same with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error scene execute select person id from person inner join person on person id person id with no table scene execute select person id from person inner join person on person id person id with table exist what did you expect to see scene in mysql sql mysql select person id from person inner join person on person id person id error not unique table alias person mysql mysql select version version row in set sec mysql scene in mysql sql mysql select version version row in set sec mysql create table person id int query ok rows affected sec mysql select person id from person inner join person on person id person id error not unique table alias person what did you see instead scene in tidb sql tidb select person id from person inner join person on person id person id error table test person doesn t exist scene in tidb sql tidb create table person id int query ok rows affected sec tidb select person id from person inner join person on person id person id error column id in field list is ambiguous what version of tidb are you using tidb server v or run select tidb version on tidb sql tidb select tidb version g row tidb version release version beta dirty git commit hash git branch master utc build time goversion go version linux race enabled false tikv min version alpha check table before drop false row in set sec ,1
+7119,9414947765.0,IssuesEvent,2019-04-10 11:26:01,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,`create table` error message is not same with MySQL,help wanted type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+Exec
+```sql
+CREATE TABLE t1 (id INT NOT NULL,
+ c1 VARCHAR(20) AS ('foo') VIRTUAL KEY NULL, PRIMARY KEY (id));
+CREATE TABLE t1 (id INT NOT NULL,
+ c1 VARCHAR(20) AS ('foo') VIRTUAL KEY NOT NULL, PRIMARY KEY (id));
+```
+
+2. What did you expect to see?
+
+```sql
+mysql> CREATE TABLE t1 (id INT NOT NULL,
+ -> c1 VARCHAR(20) AS ('foo') VIRTUAL KEY NULL, PRIMARY KEY (id));
+ERROR 3106 (HY000): 'Defining a virtual generated column as primary key' is not supported for generated columns.
+mysql> CREATE TABLE t1 (id INT NOT NULL,
+ -> c1 VARCHAR(20) AS ('foo') VIRTUAL KEY NOT NULL, PRIMARY KEY (id));
+ERROR 3106 (HY000): 'Defining a virtual generated column as primary key' is not supported for generated columns.
+mysql> select version();
++-------------------------+
+| version() |
++-------------------------+
+| 5.7.25-0ubuntu0.18.04.2 |
++-------------------------+
+1 row in set (0.00 sec)
+
+mysql>
+
+```
+
+3. What did you see instead?
+
+```sql
+mysql> CREATE TABLE t1 (id INT NOT NULL,
+ -> c1 VARCHAR(20) AS ('foo') VIRTUAL KEY NULL, PRIMARY KEY (id));
+ERROR 1068 (42000): Multiple primary key defined
+mysql> CREATE TABLE t1 (id INT NOT NULL,
+ -> c1 VARCHAR(20) AS ('foo') VIRTUAL KEY NOT NULL, PRIMARY KEY (id));
+ERROR 1068 (42000): Multiple primary key defined
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```sql
+mysql> select TiDB_version();
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| TiDB_version() |
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-117-gc48ac8af1-dirty
+Git Commit Hash: c48ac8af1817bd92847c15d98b9d8eaf3d389130
+Git Branch: master
+UTC Build Time: 2019-02-26 02:07:00
+GoVersion: go version go1.11.5 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+
+```",True,"`create table` error message is not same with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+Exec
+```sql
+CREATE TABLE t1 (id INT NOT NULL,
+ c1 VARCHAR(20) AS ('foo') VIRTUAL KEY NULL, PRIMARY KEY (id));
+CREATE TABLE t1 (id INT NOT NULL,
+ c1 VARCHAR(20) AS ('foo') VIRTUAL KEY NOT NULL, PRIMARY KEY (id));
+```
+
+2. What did you expect to see?
+
+```sql
+mysql> CREATE TABLE t1 (id INT NOT NULL,
+ -> c1 VARCHAR(20) AS ('foo') VIRTUAL KEY NULL, PRIMARY KEY (id));
+ERROR 3106 (HY000): 'Defining a virtual generated column as primary key' is not supported for generated columns.
+mysql> CREATE TABLE t1 (id INT NOT NULL,
+ -> c1 VARCHAR(20) AS ('foo') VIRTUAL KEY NOT NULL, PRIMARY KEY (id));
+ERROR 3106 (HY000): 'Defining a virtual generated column as primary key' is not supported for generated columns.
+mysql> select version();
++-------------------------+
+| version() |
++-------------------------+
+| 5.7.25-0ubuntu0.18.04.2 |
++-------------------------+
+1 row in set (0.00 sec)
+
+mysql>
+
+```
+
+3. What did you see instead?
+
+```sql
+mysql> CREATE TABLE t1 (id INT NOT NULL,
+ -> c1 VARCHAR(20) AS ('foo') VIRTUAL KEY NULL, PRIMARY KEY (id));
+ERROR 1068 (42000): Multiple primary key defined
+mysql> CREATE TABLE t1 (id INT NOT NULL,
+ -> c1 VARCHAR(20) AS ('foo') VIRTUAL KEY NOT NULL, PRIMARY KEY (id));
+ERROR 1068 (42000): Multiple primary key defined
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```sql
+mysql> select TiDB_version();
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| TiDB_version() |
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-117-gc48ac8af1-dirty
+Git Commit Hash: c48ac8af1817bd92847c15d98b9d8eaf3d389130
+Git Branch: master
+UTC Build Time: 2019-02-26 02:07:00
+GoVersion: go version go1.11.5 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+
+```",1, create table error message is not same with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error exec sql create table id int not null varchar as foo virtual key null primary key id create table id int not null varchar as foo virtual key not null primary key id what did you expect to see sql mysql create table id int not null varchar as foo virtual key null primary key id error defining a virtual generated column as primary key is not supported for generated columns mysql create table id int not null varchar as foo virtual key not null primary key id error defining a virtual generated column as primary key is not supported for generated columns mysql select version version row in set sec mysql what did you see instead sql mysql create table id int not null varchar as foo virtual key null primary key id error multiple primary key defined mysql create table id int not null varchar as foo virtual key not null primary key id error multiple primary key defined what version of tidb are you using tidb server v or run select tidb version on tidb sql mysql select tidb version tidb version release version beta dirty git commit hash git branch master utc build time goversion go version linux race enabled false tikv min version alpha check table before drop false row in set sec ,1
+15511,2858504634.0,IssuesEvent,2015-06-03 03:10:25,cakephp/cakephp,https://api.github.com/repos/cakephp/cakephp,closed,Problem with Inflector,Defect On hold utility,"Since 2.6.5 I have problems con multi-word irregular nouns (with 3 or more words). In 2.6.4 this works fine.
+
+Example:
+
+I define (in spanish) with the Inflector::rules the plural ""categorias_preguntas_frecuentes"" for the singular ""categoria_pregunta_frecuente""... But in the model the application looks for the table ""faq_categoria_preguntas_frecuentes"" instead the correct table ""faq_categorias_preguntas_frecuentes"". My model is into a plugin named Faq (tables start with ""faq_"").
+
+I have obseved that now I need to prepend the name of the plugin into the expressions like ""faq_categorias_preguntas_frecuentes"" for the plural and ""faq_categoria_pregunta_frecuente"" for the singular in order to keep the application working... In previous versions this was not required. ¿Is this behaviour correct or is an error...?
+
+Thank you so much for your attention.",1.0,"Problem with Inflector - Since 2.6.5 I have problems con multi-word irregular nouns (with 3 or more words). In 2.6.4 this works fine.
+
+Example:
+
+I define (in spanish) with the Inflector::rules the plural ""categorias_preguntas_frecuentes"" for the singular ""categoria_pregunta_frecuente""... But in the model the application looks for the table ""faq_categoria_preguntas_frecuentes"" instead the correct table ""faq_categorias_preguntas_frecuentes"". My model is into a plugin named Faq (tables start with ""faq_"").
+
+I have obseved that now I need to prepend the name of the plugin into the expressions like ""faq_categorias_preguntas_frecuentes"" for the plural and ""faq_categoria_pregunta_frecuente"" for the singular in order to keep the application working... In previous versions this was not required. ¿Is this behaviour correct or is an error...?
+
+Thank you so much for your attention.",0,problem with inflector since i have problems con multi word irregular nouns with or more words in this works fine example i define in spanish with the inflector rules the plural categorias preguntas frecuentes for the singular categoria pregunta frecuente but in the model the application looks for the table faq categoria preguntas frecuentes instead the correct table faq categorias preguntas frecuentes my model is into a plugin named faq tables start with faq i have obseved that now i need to prepend the name of the plugin into the expressions like faq categorias preguntas frecuentes for the plural and faq categoria pregunta frecuente for the singular in order to keep the application working in previous versions this was not required ¿is this behaviour correct or is an error thank you so much for your attention ,0
+7675,9931705449.0,IssuesEvent,2019-07-02 08:09:19,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Incompatible issues about window function,type/bug type/compatibility,"We have some incompatible issues about window function, and need help from contributors, most of them are simple to fix.
+
+- [ ] #10996
+- [ ] #11001
+- [ ] #11002
+- [ ] #11007
+- [ ] #11008
+- [ ] #11009
+- [ ] #11010
+- [ ] #11011 ",True,"Incompatible issues about window function - We have some incompatible issues about window function, and need help from contributors, most of them are simple to fix.
+
+- [ ] #10996
+- [ ] #11001
+- [ ] #11002
+- [ ] #11007
+- [ ] #11008
+- [ ] #11009
+- [ ] #11010
+- [ ] #11011 ",1,incompatible issues about window function we have some incompatible issues about window function and need help from contributors most of them are simple to fix ,1
+59497,3113936772.0,IssuesEvent,2015-09-03 04:11:13,AutomationSolutionz/Framework_0.1,https://api.github.com/repos/AutomationSolutionz/Framework_0.1,closed,Common tab is not considering all the other status that were added later.,bug Priority 2 (High) Release Gating Shetu,"Common tab is not considering all the other status that we added new.
+
+Please make sure all status are grouped together and user can view full detail.",1.0,"Common tab is not considering all the other status that were added later. - Common tab is not considering all the other status that we added new.
+
+Please make sure all status are grouped together and user can view full detail.",0,common tab is not considering all the other status that were added later common tab is not considering all the other status that we added new please make sure all status are grouped together and user can view full detail ,0
+13662,16343631397.0,IssuesEvent,2021-05-13 03:15:40,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Inconsistent error with MySQL for GRANT CREATE USER ON .*,good-first-issue severity/moderate sig/sql-infra status/help-wanted type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+create user testuser@localhost;
+grant create user on test.* to testuser@localhost;
+
+### 2. What did you expect to see? (Required)
+
+mysql> create user testuser@localhost;
+Query OK, 0 rows affected (0.04 sec)
+
+mysql> grant create user on test.* to testuser@localhost;
+ERROR 1221 (HY000): Incorrect usage of DB GRANT and GLOBAL PRIVILEGES
+
+### 3. What did you see instead (Required)
+
+tidb> create user testuser@localhost;
+Query OK, 0 rows affected (0.01 sec)
+
+tidb> grant create user on test.* to testuser@localhost;
+ERROR 1054 (42S22): Unknown column 'Create_user_priv' in 'field list'
+
+### 4. What is your TiDB version? (Required)
+
+tidb_version(): Release Version: v4.0.0-beta.2-2806-ga6ec081b8
+Edition: Community
+Git Commit Hash: a6ec081b82a5357a9688a98d4d3cca35c87eab75
+Git Branch: HEAD
+UTC Build Time: 2021-05-06 14:56:18
+GoVersion: go1.13.8
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+
+",True,"Inconsistent error with MySQL for GRANT CREATE USER ON .* - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+create user testuser@localhost;
+grant create user on test.* to testuser@localhost;
+
+### 2. What did you expect to see? (Required)
+
+mysql> create user testuser@localhost;
+Query OK, 0 rows affected (0.04 sec)
+
+mysql> grant create user on test.* to testuser@localhost;
+ERROR 1221 (HY000): Incorrect usage of DB GRANT and GLOBAL PRIVILEGES
+
+### 3. What did you see instead (Required)
+
+tidb> create user testuser@localhost;
+Query OK, 0 rows affected (0.01 sec)
+
+tidb> grant create user on test.* to testuser@localhost;
+ERROR 1054 (42S22): Unknown column 'Create_user_priv' in 'field list'
+
+### 4. What is your TiDB version? (Required)
+
+tidb_version(): Release Version: v4.0.0-beta.2-2806-ga6ec081b8
+Edition: Community
+Git Commit Hash: a6ec081b82a5357a9688a98d4d3cca35c87eab75
+Git Branch: HEAD
+UTC Build Time: 2021-05-06 14:56:18
+GoVersion: go1.13.8
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+
+",1,inconsistent error with mysql for grant create user on bug report please answer these questions before submitting your issue thanks minimal reproduce step required create user testuser localhost grant create user on test to testuser localhost what did you expect to see required mysql create user testuser localhost query ok rows affected sec mysql grant create user on test to testuser localhost error incorrect usage of db grant and global privileges what did you see instead required tidb create user testuser localhost query ok rows affected sec tidb grant create user on test to testuser localhost error unknown column create user priv in field list what is your tidb version required tidb version release version beta edition community git commit hash git branch head utc build time goversion race enabled false tikv min version check table before drop false ,1
+8998,11034837643.0,IssuesEvent,2019-12-07 09:01:45,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Datetime compare incompatible with MySQL,type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```
+CREATE TABLE t(d datetime);
+INSERT INTO t(d) VALUES('2019-08-10 11:45:14');
+SELECT d, d > 1 FROM t;
+SELECT COUNT(1) FROM t WHERE d > 1;
+```
+
+
+2. What did you expect to see?
+
+* MySQL 8.0
+
+```
+mysql> CREATE TABLE t(d datetime);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> INSERT INTO t(d) VALUES('2019-08-10 11:45:14');
+Query OK, 1 row affected (0.00 sec)
+
+mysql> SELECT d, d > 1 FROM t;
++---------------------+-------+
+| d | d > 1 |
++---------------------+-------+
+| 2019-08-10 11:45:14 | 1 |
++---------------------+-------+
+1 row in set, 1 warning (0.02 sec)
+
+mysql> SELECT COUNT(1) FROM t WHERE d > 1;
++----------+
+| COUNT(1) |
++----------+
+| 1 |
++----------+
+1 row in set, 1 warning (0.04 sec)
+
+mysql> SELECT version();
++-----------+
+| version() |
++-----------+
+| 8.0.18 |
++-----------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+
+* TiDB 3.0.7
+
+```
+mysql> CREATE TABLE t(d datetime);
+Query OK, 0 rows affected (1.01 sec)
+
+mysql> INSERT INTO t(d) VALUES('2019-08-10 11:45:14');
+Query OK, 1 row affected (0.01 sec)
+
+mysql> SELECT d, d > 1 FROM t;
++---------------------+-------+
+| d | d > 1 |
++---------------------+-------+
+| 2019-08-10 11:45:14 | NULL |
++---------------------+-------+
+1 row in set, 1 warning (0.01 sec)
+
+mysql> SELECT COUNT(1) FROM t WHERE d > 1;
++----------+
+| COUNT(1) |
++----------+
+| 0 |
++----------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> SELECT version();
++--------------------+
+| version() |
++--------------------+
+| 5.7.25-TiDB-v3.0.7 |
++--------------------+
+1 row in set (0.00 sec)
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+Release Version: v3.0.7
+Git Commit Hash: 84e4386c7a77d4b8df5db7f2303fb7fd3370eb9a
+Git Branch: HEAD
+UTC Build Time: 2019-12-04 10:08:24
+GoVersion: go version go1.13 linux/amd64
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+```
+",True,"Datetime compare incompatible with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```
+CREATE TABLE t(d datetime);
+INSERT INTO t(d) VALUES('2019-08-10 11:45:14');
+SELECT d, d > 1 FROM t;
+SELECT COUNT(1) FROM t WHERE d > 1;
+```
+
+
+2. What did you expect to see?
+
+* MySQL 8.0
+
+```
+mysql> CREATE TABLE t(d datetime);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> INSERT INTO t(d) VALUES('2019-08-10 11:45:14');
+Query OK, 1 row affected (0.00 sec)
+
+mysql> SELECT d, d > 1 FROM t;
++---------------------+-------+
+| d | d > 1 |
++---------------------+-------+
+| 2019-08-10 11:45:14 | 1 |
++---------------------+-------+
+1 row in set, 1 warning (0.02 sec)
+
+mysql> SELECT COUNT(1) FROM t WHERE d > 1;
++----------+
+| COUNT(1) |
++----------+
+| 1 |
++----------+
+1 row in set, 1 warning (0.04 sec)
+
+mysql> SELECT version();
++-----------+
+| version() |
++-----------+
+| 8.0.18 |
++-----------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+
+* TiDB 3.0.7
+
+```
+mysql> CREATE TABLE t(d datetime);
+Query OK, 0 rows affected (1.01 sec)
+
+mysql> INSERT INTO t(d) VALUES('2019-08-10 11:45:14');
+Query OK, 1 row affected (0.01 sec)
+
+mysql> SELECT d, d > 1 FROM t;
++---------------------+-------+
+| d | d > 1 |
++---------------------+-------+
+| 2019-08-10 11:45:14 | NULL |
++---------------------+-------+
+1 row in set, 1 warning (0.01 sec)
+
+mysql> SELECT COUNT(1) FROM t WHERE d > 1;
++----------+
+| COUNT(1) |
++----------+
+| 0 |
++----------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> SELECT version();
++--------------------+
+| version() |
++--------------------+
+| 5.7.25-TiDB-v3.0.7 |
++--------------------+
+1 row in set (0.00 sec)
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+Release Version: v3.0.7
+Git Commit Hash: 84e4386c7a77d4b8df5db7f2303fb7fd3370eb9a
+Git Branch: HEAD
+UTC Build Time: 2019-12-04 10:08:24
+GoVersion: go version go1.13 linux/amd64
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+```
+",1,datetime compare incompatible with mysql bug report please answer these questions before submitting your issue thanks what did you do create table t d datetime insert into t d values select d d from t select count from t where d what did you expect to see mysql mysql create table t d datetime query ok rows affected sec mysql insert into t d values query ok row affected sec mysql select d d from t d d row in set warning sec mysql select count from t where d count row in set warning sec mysql select version version row in set sec what did you see instead tidb mysql create table t d datetime query ok rows affected sec mysql insert into t d values query ok row affected sec mysql select d d from t d d null row in set warning sec mysql select count from t where d count row in set warning sec mysql select version version tidb row in set sec what version of tidb are you using tidb server v or run select tidb version on tidb release version git commit hash git branch head utc build time goversion go version linux race enabled false tikv min version check table before drop false ,1
+20413,30191146881.0,IssuesEvent,2023-07-04 15:29:16,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,TiDB should support query argument with type `MYSQL_TIMESTAMP_DATETIME_TZ`,type/bug component/mysql-protocol severity/minor compatibility-mysql8,"## Enhancement
+
+Now TiDB can only handle three different kinds of date arguments:
+
+```go
+case mysql.TypeDate, mysql.TypeTimestamp, mysql.TypeDatetime:
+ if len(paramValues) < (pos + 1) {
+ err = mysql.ErrMalformPacket
+ return
+ }
+ // See https://dev.mysql.com/doc/internals/en/binary-protocol-value.html
+ // for more details.
+ length := paramValues[pos]
+ pos++
+ switch length {
+ case 0:
+ tmp = types.ZeroDatetimeStr
+ case 4:
+ pos, tmp = binaryDate(pos, paramValues)
+ case 7:
+ pos, tmp = binaryDateTime(pos, paramValues)
+ case 11:
+ pos, tmp = binaryTimestamp(pos, paramValues)
+ default:
+ err = mysql.ErrMalformPacket
+ return
+ }
+ args[i] = types.NewDatum(tmp) // FIXME: After check works!!!!!!
+ continue
+```
+
+It's fine according to the MySQL [document](https://dev.mysql.com/doc/dev/mysql-server/latest/page_protocol_binary_resultset.html#sect_protocol_binary_resultset_row_value_date), but the mysql c connector can pass an argument with TZ information, whose length is 13.
+
+See the `test_time_zone` in the mysql client test:
+
+```
+ MYSQL_TIME mt{2011,
+ 02,
+ 03,
+ 04,
+ 05,
+ 06,
+ 123456,
+ false,
+ MYSQL_TIMESTAMP_DATETIME_TZ,
+ 12 * SECS_PER_HOUR + 34 * SECS_PER_MIN};
+```",True,"TiDB should support query argument with type `MYSQL_TIMESTAMP_DATETIME_TZ` - ## Enhancement
+
+Now TiDB can only handle three different kinds of date arguments:
+
+```go
+case mysql.TypeDate, mysql.TypeTimestamp, mysql.TypeDatetime:
+ if len(paramValues) < (pos + 1) {
+ err = mysql.ErrMalformPacket
+ return
+ }
+ // See https://dev.mysql.com/doc/internals/en/binary-protocol-value.html
+ // for more details.
+ length := paramValues[pos]
+ pos++
+ switch length {
+ case 0:
+ tmp = types.ZeroDatetimeStr
+ case 4:
+ pos, tmp = binaryDate(pos, paramValues)
+ case 7:
+ pos, tmp = binaryDateTime(pos, paramValues)
+ case 11:
+ pos, tmp = binaryTimestamp(pos, paramValues)
+ default:
+ err = mysql.ErrMalformPacket
+ return
+ }
+ args[i] = types.NewDatum(tmp) // FIXME: After check works!!!!!!
+ continue
+```
+
+It's fine according to the MySQL [document](https://dev.mysql.com/doc/dev/mysql-server/latest/page_protocol_binary_resultset.html#sect_protocol_binary_resultset_row_value_date), but the mysql c connector can pass an argument with TZ information, whose length is 13.
+
+See the `test_time_zone` in the mysql client test:
+
+```
+ MYSQL_TIME mt{2011,
+ 02,
+ 03,
+ 04,
+ 05,
+ 06,
+ 123456,
+ false,
+ MYSQL_TIMESTAMP_DATETIME_TZ,
+ 12 * SECS_PER_HOUR + 34 * SECS_PER_MIN};
+```",1,tidb should support query argument with type mysql timestamp datetime tz enhancement now tidb can only handle three different kinds of date arguments go case mysql typedate mysql typetimestamp mysql typedatetime if len paramvalues pos err mysql errmalformpacket return see for more details length paramvalues pos switch length case tmp types zerodatetimestr case pos tmp binarydate pos paramvalues case pos tmp binarydatetime pos paramvalues case pos tmp binarytimestamp pos paramvalues default err mysql errmalformpacket return args types newdatum tmp fixme after check works continue it s fine according to the mysql but the mysql c connector can pass an argument with tz information whose length is see the test time zone in the mysql client test mysql time mt false mysql timestamp datetime tz secs per hour secs per min ,1
+7854,10062990055.0,IssuesEvent,2019-07-23 03:40:19,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Function `period_add ` is not compatible with MySQL 8.0,type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+The `period_add` behavior is not compatible with MySQL 8.0
+
+2. What did you expect to see?
+
+MySQL 8.0:
+
+```
+mysql> select period_add(128081,887);
+ERROR 1210 (HY000): Incorrect arguments to period_add
+mysql> select period_add(128011,887);
++------------------------+
+| period_add(128011,887) |
++------------------------+
+| 135410 |
++------------------------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+
+```
+mysql> select period_add(128081,887);
++------------------------+
+| period_add(128081,887) |
++------------------------+
+| 136008 |
++------------------------+
+1 row in set (0.00 sec)
+
+mysql> select period_add(128011,887);
++------------------------+
+| period_add(128011,887) |
++------------------------+
+| 135410 |
++------------------------+
+1 row in set (0.00 sec)
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+mysql> select tidb_version();
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta.1-187-g5876abd70
+Git Commit Hash: 5876abd70ccc054704ab0e8cbf02ed129c6efc76
+Git Branch: refine-point-get-failpoint
+UTC Build Time: 2019-04-30 03:35:49
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.01 sec)
+```
+",True,"Function `period_add ` is not compatible with MySQL 8.0 - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+The `period_add` behavior is not compatible with MySQL 8.0
+
+2. What did you expect to see?
+
+MySQL 8.0:
+
+```
+mysql> select period_add(128081,887);
+ERROR 1210 (HY000): Incorrect arguments to period_add
+mysql> select period_add(128011,887);
++------------------------+
+| period_add(128011,887) |
++------------------------+
+| 135410 |
++------------------------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+
+```
+mysql> select period_add(128081,887);
++------------------------+
+| period_add(128081,887) |
++------------------------+
+| 136008 |
++------------------------+
+1 row in set (0.00 sec)
+
+mysql> select period_add(128011,887);
++------------------------+
+| period_add(128011,887) |
++------------------------+
+| 135410 |
++------------------------+
+1 row in set (0.00 sec)
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+mysql> select tidb_version();
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta.1-187-g5876abd70
+Git Commit Hash: 5876abd70ccc054704ab0e8cbf02ed129c6efc76
+Git Branch: refine-point-get-failpoint
+UTC Build Time: 2019-04-30 03:35:49
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.01 sec)
+```
+",1,function period add is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error the period add behavior is not compatible with mysql what did you expect to see mysql mysql select period add error incorrect arguments to period add mysql select period add period add row in set sec what did you see instead mysql select period add period add row in set sec mysql select period add period add row in set sec what version of tidb are you using tidb server v or run select tidb version on tidb mysql select tidb version tidb version release version beta git commit hash git branch refine point get failpoint utc build time goversion go version darwin race enabled false tikv min version alpha check table before drop false row in set sec ,1
+3895,6741642683.0,IssuesEvent,2017-10-20 02:18:34,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Field type year should have unsigned flag,compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+drop table if exists t;
+create table t (
+ c_year year
+);
+
+insert into t values (
+ 11
+);
+
+select * from t;
+```
+
+2. What did you expect to see?
+
+```
+Field 1: `c_year`
+Catalog: `def`
+Database: `mysql`
+Table: `t`
+Org_table: `t`
+Type: YEAR
+Collation: binary (63)
+Length: 4
+Max_length: 4
+Decimals: 0
+Flags: UNSIGNED ZEROFILL NUM
+
+
++--------+
+| c_year |
++--------+
+| 2011 |
++--------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+Field 1: `c_year`
+Catalog: `def`
+Database: `test`
+Table: `t`
+Org_table: `t`
+Type: YEAR
+Collation: binary (63)
+Length: 16
+Max_length: 4
+Decimals: 0
+Flags: BINARY NUM
+
+
++--------+
+| c_year |
++--------+
+| 2011 |
++--------+
+1 row in set (0.00 sec)
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"Field type year should have unsigned flag - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+drop table if exists t;
+create table t (
+ c_year year
+);
+
+insert into t values (
+ 11
+);
+
+select * from t;
+```
+
+2. What did you expect to see?
+
+```
+Field 1: `c_year`
+Catalog: `def`
+Database: `mysql`
+Table: `t`
+Org_table: `t`
+Type: YEAR
+Collation: binary (63)
+Length: 4
+Max_length: 4
+Decimals: 0
+Flags: UNSIGNED ZEROFILL NUM
+
+
++--------+
+| c_year |
++--------+
+| 2011 |
++--------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+Field 1: `c_year`
+Catalog: `def`
+Database: `test`
+Table: `t`
+Org_table: `t`
+Type: YEAR
+Collation: binary (63)
+Length: 16
+Max_length: 4
+Decimals: 0
+Flags: BINARY NUM
+
+
++--------+
+| c_year |
++--------+
+| 2011 |
++--------+
+1 row in set (0.00 sec)
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,field type year should have unsigned flag please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql drop table if exists t create table t c year year insert into t values select from t what did you expect to see field c year catalog def database mysql table t org table t type year collation binary length max length decimals flags unsigned zerofill num c year row in set sec what did you see instead field c year catalog def database test table t org table t type year collation binary length max length decimals flags binary num c year row in set sec what version of tidb are you using tidb server v ,1
+7065,9345171494.0,IssuesEvent,2019-03-30 04:47:47,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,`set time_zone` is not compatible with MySQL,for new contributors help wanted type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+set time_zone= '-20:00';
+set time_zone= '+20:00';
+```
+
+2. What did you expect to see?
+In Mysql
+```
+mysql> set time_zone= '-20:00';
+ERROR 1298 (HY000): Unknown or incorrect time zone: '-20:00'
+mysql> set time_zone= '+20:00';
+ERROR 1298 (HY000): Unknown or incorrect time zone: '+20:00'
+```
+
+
+3. What did you see instead?
+In TiDB
+```
+mysql> set time_zone= '-20:00';
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> set time_zone= '+20:00';
+Query OK, 0 rows affected (0.00 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-227-g06183393e-dirty
+Git Commit Hash: 06183393ed536aa248248b72d4bf9f5010947f66
+Git Branch: master
+UTC Build Time: 2019-03-15 08:22:53
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+```
+",True,"`set time_zone` is not compatible with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+set time_zone= '-20:00';
+set time_zone= '+20:00';
+```
+
+2. What did you expect to see?
+In Mysql
+```
+mysql> set time_zone= '-20:00';
+ERROR 1298 (HY000): Unknown or incorrect time zone: '-20:00'
+mysql> set time_zone= '+20:00';
+ERROR 1298 (HY000): Unknown or incorrect time zone: '+20:00'
+```
+
+
+3. What did you see instead?
+In TiDB
+```
+mysql> set time_zone= '-20:00';
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> set time_zone= '+20:00';
+Query OK, 0 rows affected (0.00 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-227-g06183393e-dirty
+Git Commit Hash: 06183393ed536aa248248b72d4bf9f5010947f66
+Git Branch: master
+UTC Build Time: 2019-03-15 08:22:53
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+```
+",1, set time zone is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error set time zone set time zone what did you expect to see in mysql mysql set time zone error unknown or incorrect time zone mysql set time zone error unknown or incorrect time zone what did you see instead in tidb mysql set time zone query ok rows affected sec mysql set time zone query ok rows affected sec what version of tidb are you using tidb server v or run select tidb version on tidb tidb version release version beta dirty git commit hash git branch master utc build time goversion go version darwin race enabled false tikv min version alpha check table before drop false ,1
+413441,12067366437.0,IssuesEvent,2020-04-16 13:17:26,Avanade/Liquid-Application-Framework,https://api.github.com/repos/Avanade/Liquid-Application-Framework,closed,Retire LightApi,complexity:high enhancement priority size:large,"LightApi is reinventing the wheel - libraries like RestSharp already exists and does what it does in a much better way - but, worse, LightApi is full of design and implementation issues. In the sake of conciseness, this issue tracks all of it's defects.
+
+Before we get into that, my official recommendations is to excise LightApi from the framework and adopt RestSharp. We should be doing that on milestone 2.0.0. Nonetheless, there are many people already using LightApi and, for _their sake_, I'll try to fix as many bugs as possible. Design issues, however, won't be addressed unless completely necessary.
+
+Before dealing with any of the issues related here, one should do the unit tests (#148).
+
+*Note:* everything mentioned here also applies to its base class, `AbstractAPIWrapper`.
+
+### The class makes a lot of misuses of async/await, Task, etc.
+
+On many places, the code forces synchronicity:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L127
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L216
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L247
+
+And so on and so forth.
+
+To make matters worse, the class presents async methods that wraps this forced synchronous code in a task, effectively wasting at least two threads and creating numerous performance issues:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/AbstractAPIWrapper.cs#L103
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/AbstractAPIWrapper.cs#L118
+
+Etc.
+
+### Duplicated code
+
+Hard to read/debug critical code is duplicated:
+
+1.
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/AbstractAPIWrapper.cs#L78
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/AbstractAPIWrapper.cs#L50
+
+2.
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L433
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L466
+
+### It won't correctly set headers for requests
+
+See #66.
+
+ ### AbstractApiWrapper is coupled to HttpClient.
+
+Although AAW is supposed to use it's concrete implementations to perform the requests (`AbstractApiWrapper.Get`, `AbstractApiWrapper.Post`, etc), for some reason `AbstractApiWrapper.ResilientRequest` directly uses a HttpClient, simply removing the benefit of it being a base abstract class.
+
+### It isn't thread-safe
+
+HttpClient is supposed to be _thread-safe_ because, since it opens up a socket, you get better performance if you reuse it. However, the implementation of LightApi isn't, as the code change _default_ properties that are shared among all calls.
+
+Docs: https://docs.microsoft.com/en-us/dotnet/api/system.net.http.httpclient?view=netframework-4.8#remarks
+
+Non-thread-safe manipulation:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L275
+
+### It doesn't consistently uses `WorkBenchServiceHttp`
+
+Out of blue the code decides to pass verbs as strings:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L492
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L516
+
+### It ignore status codes on generic calls
+
+LightApi has a *very* non standard behavior - if you use any of it's generic interfaces, but inform the desired type to be `HttpResponseMessage`, then it will not convert the response from the underling `HttpClient`.
+
+You can also not inform a generic parameter, in which case LightApi usually returns a JToken, or inform anything else than HttpResponseMessage.
+
+In both of the later cases, what happens is this: LightApi *ignores the status code* returned by the call (which means, you could be getting even a 500) and converts its result into `DomainResult`, for instance:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L457
+
+And then it returns you the resulting object. In many exceptional cases you'll get a obscure parsing error wrapped around a generic LightException, so it's even uncacheable. *This renders LightApi uneffective on the smashing majority of use cases,* unless you can magically guarantee that your calls always returns successfully.
+
+Again, you can effectively use it by passing a `HttpResponseMessage `as the return type... the only big question here is what does it actually do for you once you follow that path. As you can see by the code, once you do this, LightApi short-circuits a lot of functionality, so what you get is a strange API that is very limited.
+
+### It calls Convert unnecessarily
+
+The (code)[https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L522] is
+
+```csharp
+var httpResponse = base.ResilientRequest(this.MakeUri(serviceRoute), httpClient, httpMethod, body.ConvertToByteArrayContent()).Result;
+
+if (typeof(T).Equals(typeof(HttpResponseMessage)))
+{
+ return (T)Convert.ChangeType(httpResponse, typeof(T));
+}
+```
+
+It checks if T is `HttpResponseMessage `and then it uses `Convert.ChangeType` to change the variable httpResponse to `HttpResponseMessage`. Thing is, `httpResponse `already is a instance of HttpResponseMessage.
+
+### DELETE is inconsistent in in the way that it handles a response body
+
+Get, Post and Put parses the body as a instance of `DomainResult` by calling `HandleResult`:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L457
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L590
+
+etc.
+
+However, DELETE does not calls `HandleResult`:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L247
+
+(please note the comment right above it)
+
+This means that the full body is stuck inside PayLoad, so the returning body conforms to the idiom and returns a serialized `DomainResult`, then we will have a `DomainResult` structure inside a `DomainResult` structure.
+
+### Delete ignores all errors
+
+Yep:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L253-L256",1.0,"Retire LightApi - LightApi is reinventing the wheel - libraries like RestSharp already exists and does what it does in a much better way - but, worse, LightApi is full of design and implementation issues. In the sake of conciseness, this issue tracks all of it's defects.
+
+Before we get into that, my official recommendations is to excise LightApi from the framework and adopt RestSharp. We should be doing that on milestone 2.0.0. Nonetheless, there are many people already using LightApi and, for _their sake_, I'll try to fix as many bugs as possible. Design issues, however, won't be addressed unless completely necessary.
+
+Before dealing with any of the issues related here, one should do the unit tests (#148).
+
+*Note:* everything mentioned here also applies to its base class, `AbstractAPIWrapper`.
+
+### The class makes a lot of misuses of async/await, Task, etc.
+
+On many places, the code forces synchronicity:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L127
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L216
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L247
+
+And so on and so forth.
+
+To make matters worse, the class presents async methods that wraps this forced synchronous code in a task, effectively wasting at least two threads and creating numerous performance issues:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/AbstractAPIWrapper.cs#L103
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/AbstractAPIWrapper.cs#L118
+
+Etc.
+
+### Duplicated code
+
+Hard to read/debug critical code is duplicated:
+
+1.
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/AbstractAPIWrapper.cs#L78
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/AbstractAPIWrapper.cs#L50
+
+2.
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L433
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L466
+
+### It won't correctly set headers for requests
+
+See #66.
+
+ ### AbstractApiWrapper is coupled to HttpClient.
+
+Although AAW is supposed to use it's concrete implementations to perform the requests (`AbstractApiWrapper.Get`, `AbstractApiWrapper.Post`, etc), for some reason `AbstractApiWrapper.ResilientRequest` directly uses a HttpClient, simply removing the benefit of it being a base abstract class.
+
+### It isn't thread-safe
+
+HttpClient is supposed to be _thread-safe_ because, since it opens up a socket, you get better performance if you reuse it. However, the implementation of LightApi isn't, as the code change _default_ properties that are shared among all calls.
+
+Docs: https://docs.microsoft.com/en-us/dotnet/api/system.net.http.httpclient?view=netframework-4.8#remarks
+
+Non-thread-safe manipulation:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L275
+
+### It doesn't consistently uses `WorkBenchServiceHttp`
+
+Out of blue the code decides to pass verbs as strings:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L492
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L516
+
+### It ignore status codes on generic calls
+
+LightApi has a *very* non standard behavior - if you use any of it's generic interfaces, but inform the desired type to be `HttpResponseMessage`, then it will not convert the response from the underling `HttpClient`.
+
+You can also not inform a generic parameter, in which case LightApi usually returns a JToken, or inform anything else than HttpResponseMessage.
+
+In both of the later cases, what happens is this: LightApi *ignores the status code* returned by the call (which means, you could be getting even a 500) and converts its result into `DomainResult`, for instance:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L457
+
+And then it returns you the resulting object. In many exceptional cases you'll get a obscure parsing error wrapped around a generic LightException, so it's even uncacheable. *This renders LightApi uneffective on the smashing majority of use cases,* unless you can magically guarantee that your calls always returns successfully.
+
+Again, you can effectively use it by passing a `HttpResponseMessage `as the return type... the only big question here is what does it actually do for you once you follow that path. As you can see by the code, once you do this, LightApi short-circuits a lot of functionality, so what you get is a strange API that is very limited.
+
+### It calls Convert unnecessarily
+
+The (code)[https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L522] is
+
+```csharp
+var httpResponse = base.ResilientRequest(this.MakeUri(serviceRoute), httpClient, httpMethod, body.ConvertToByteArrayContent()).Result;
+
+if (typeof(T).Equals(typeof(HttpResponseMessage)))
+{
+ return (T)Convert.ChangeType(httpResponse, typeof(T));
+}
+```
+
+It checks if T is `HttpResponseMessage `and then it uses `Convert.ChangeType` to change the variable httpResponse to `HttpResponseMessage`. Thing is, `httpResponse `already is a instance of HttpResponseMessage.
+
+### DELETE is inconsistent in in the way that it handles a response body
+
+Get, Post and Put parses the body as a instance of `DomainResult` by calling `HandleResult`:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L457
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L590
+
+etc.
+
+However, DELETE does not calls `HandleResult`:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L247
+
+(please note the comment right above it)
+
+This means that the full body is stuck inside PayLoad, so the returning body conforms to the idiom and returns a serialized `DomainResult`, then we will have a `DomainResult` structure inside a `DomainResult` structure.
+
+### Delete ignores all errors
+
+Yep:
+
+https://github.com/Avanade/Liquid-Application-Framework/blob/8f03b94252db859c61992662bc7c84fced8fee64/src/Liquid.Domain/API/LightAPI.cs#L253-L256",0,retire lightapi lightapi is reinventing the wheel libraries like restsharp already exists and does what it does in a much better way but worse lightapi is full of design and implementation issues in the sake of conciseness this issue tracks all of it s defects before we get into that my official recommendations is to excise lightapi from the framework and adopt restsharp we should be doing that on milestone nonetheless there are many people already using lightapi and for their sake i ll try to fix as many bugs as possible design issues however won t be addressed unless completely necessary before dealing with any of the issues related here one should do the unit tests note everything mentioned here also applies to its base class abstractapiwrapper the class makes a lot of misuses of async await task etc on many places the code forces synchronicity and so on and so forth to make matters worse the class presents async methods that wraps this forced synchronous code in a task effectively wasting at least two threads and creating numerous performance issues etc duplicated code hard to read debug critical code is duplicated it won t correctly set headers for requests see abstractapiwrapper is coupled to httpclient although aaw is supposed to use it s concrete implementations to perform the requests abstractapiwrapper get abstractapiwrapper post etc for some reason abstractapiwrapper resilientrequest directly uses a httpclient simply removing the benefit of it being a base abstract class it isn t thread safe httpclient is supposed to be thread safe because since it opens up a socket you get better performance if you reuse it however the implementation of lightapi isn t as the code change default properties that are shared among all calls docs non thread safe manipulation it doesn t consistently uses workbenchservicehttp out of blue the code decides to pass verbs as strings it ignore status codes on generic calls lightapi has a very non standard behavior if you use any of it s generic interfaces but inform the desired type to be httpresponsemessage then it will not convert the response from the underling httpclient you can also not inform a generic parameter in which case lightapi usually returns a jtoken or inform anything else than httpresponsemessage in both of the later cases what happens is this lightapi ignores the status code returned by the call which means you could be getting even a and converts its result into domainresult for instance and then it returns you the resulting object in many exceptional cases you ll get a obscure parsing error wrapped around a generic lightexception so it s even uncacheable this renders lightapi uneffective on the smashing majority of use cases unless you can magically guarantee that your calls always returns successfully again you can effectively use it by passing a httpresponsemessage as the return type the only big question here is what does it actually do for you once you follow that path as you can see by the code once you do this lightapi short circuits a lot of functionality so what you get is a strange api that is very limited it calls convert unnecessarily the code is csharp var httpresponse base resilientrequest this makeuri serviceroute httpclient httpmethod body converttobytearraycontent result if typeof t equals typeof httpresponsemessage return t convert changetype httpresponse typeof t it checks if t is httpresponsemessage and then it uses convert changetype to change the variable httpresponse to httpresponsemessage thing is httpresponse already is a instance of httpresponsemessage delete is inconsistent in in the way that it handles a response body get post and put parses the body as a instance of domainresult by calling handleresult etc however delete does not calls handleresult please note the comment right above it this means that the full body is stuck inside payload so the returning body conforms to the idiom and returns a serialized domainresult then we will have a domainresult structure inside a domainresult structure delete ignores all errors yep ,0
+11103,13129825155.0,IssuesEvent,2020-08-06 14:28:13,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,"SELECT 'a'='a ' , 'a'='A' , 'a'='A ' not same to MySQL in TiDB",type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sh
+mysql> select 'a'='a ' , 'a'='A' , 'a'='A ';
+```
+
+2. What did you expect to see?
+
+```sh
+mysql> select 'a'='a ' , 'a'='A' , 'a'='A ';
+'a'='a ' 'a'='A' 'a'='A '
+1 1 1
+```
+
+3. What did you see instead?
+
+```sh
+mysql> select 'a'='a ' , 'a'='A' , 'a'='A ';
+'a'='a ' 'a'='A' 'a'='A '
+0 0 0
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+tidb-server(e1ba30914)
+
+more details: https://asktug.com/t/mysqlslap-tidb-varbinary-varchar-select-bug/1434",True,"SELECT 'a'='a ' , 'a'='A' , 'a'='A ' not same to MySQL in TiDB - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sh
+mysql> select 'a'='a ' , 'a'='A' , 'a'='A ';
+```
+
+2. What did you expect to see?
+
+```sh
+mysql> select 'a'='a ' , 'a'='A' , 'a'='A ';
+'a'='a ' 'a'='A' 'a'='A '
+1 1 1
+```
+
+3. What did you see instead?
+
+```sh
+mysql> select 'a'='a ' , 'a'='A' , 'a'='A ';
+'a'='a ' 'a'='A' 'a'='A '
+0 0 0
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+tidb-server(e1ba30914)
+
+more details: https://asktug.com/t/mysqlslap-tidb-varbinary-varchar-select-bug/1434",1,select a a a a a a not same to mysql in tidb bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sh mysql select a a a a a a what did you expect to see sh mysql select a a a a a a a a a a a a what did you see instead sh mysql select a a a a a a a a a a a a what version of tidb are you using tidb server v or run select tidb version on tidb tidb server more details ,1
+5724,8183087581.0,IssuesEvent,2018-08-29 07:58:00,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,SHOW GRANTS FOR CURRENT_USER() does not work,type/compatibility,"Hi.
+I'm execute command(by mysql cli)
+`SHOW GRANTS FOR CURRENT_USER();`
+
+get the error
+`
+ERROR 1105 (HY000): line 1 column 28 near ""()"" (total length 30)
+`
+
+tidb version:
+`5.7.1-TiDB-v1.1.0-alpha-459-ga2a48b3`
+
+
+BTW .
+tidb support MySQL Protocol , but not very compatible with MySQL's existing client tools ( `Navicat`, `MySQL-Front`,`mysql workbench` and so on ) . Less convenient for developers to use it.
+",True,"SHOW GRANTS FOR CURRENT_USER() does not work - Hi.
+I'm execute command(by mysql cli)
+`SHOW GRANTS FOR CURRENT_USER();`
+
+get the error
+`
+ERROR 1105 (HY000): line 1 column 28 near ""()"" (total length 30)
+`
+
+tidb version:
+`5.7.1-TiDB-v1.1.0-alpha-459-ga2a48b3`
+
+
+BTW .
+tidb support MySQL Protocol , but not very compatible with MySQL's existing client tools ( `Navicat`, `MySQL-Front`,`mysql workbench` and so on ) . Less convenient for developers to use it.
+",1,show grants for current user does not work hi i m execute command(by mysql cli) show grants for current user get the error error line column near total length tidb version tidb alpha btw tidb support mysql protocol but not very compatible with mysql s existing client tools navicat , mysql front , mysql workbench and so on less convenient for developers to use it ,1
+72828,9612230169.0,IssuesEvent,2019-05-13 08:25:43,kyma-project/kyma,https://api.github.com/repos/kyma-project/kyma,closed,Document command to check Kyma version before update,area/documentation area/installation enhancement,"**Description**
+Before updating Kyma to a newer version some users might want to check their current version. It would be helpful if the instructions at https://kyma-project.io/docs/root/kyma/#installation-update-kyma include a command to check the current version. I propose using this one but there might be shorter/better ways as well:
+
+`kubectl -n kyma-installer get deploy kyma-installer -o jsonpath='{.spec.template.spec.containers[].image}' `
+
+The output looks like this:
+
+`'eu.gcr.io/kyma-project/kyma-installer:0.8.1'`
+
+**Reasons**
+Especially when updating Kyma it might be helpful to have a command in the documentation to quickly check the version. Otherwise, every user has to find an own way to check the Kyma version.",1.0,"Document command to check Kyma version before update - **Description**
+Before updating Kyma to a newer version some users might want to check their current version. It would be helpful if the instructions at https://kyma-project.io/docs/root/kyma/#installation-update-kyma include a command to check the current version. I propose using this one but there might be shorter/better ways as well:
+
+`kubectl -n kyma-installer get deploy kyma-installer -o jsonpath='{.spec.template.spec.containers[].image}' `
+
+The output looks like this:
+
+`'eu.gcr.io/kyma-project/kyma-installer:0.8.1'`
+
+**Reasons**
+Especially when updating Kyma it might be helpful to have a command in the documentation to quickly check the version. Otherwise, every user has to find an own way to check the Kyma version.",0,document command to check kyma version before update description before updating kyma to a newer version some users might want to check their current version it would be helpful if the instructions at include a command to check the current version i propose using this one but there might be shorter better ways as well kubectl n kyma installer get deploy kyma installer o jsonpath spec template spec containers image the output looks like this eu gcr io kyma project kyma installer reasons especially when updating kyma it might be helpful to have a command in the documentation to quickly check the version otherwise every user has to find an own way to check the kyma version ,0
+18987,26403693018.0,IssuesEvent,2023-01-13 05:14:42,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Unexpected Error by CAST and CHAR functions,sig/execution severity/moderate compatibility-mysql8 fuzz/sqlancer,"## Bug Report
+
+### 1. Minimal reproduce step (Required)
+```sql
+SELECT CAST(CHAR(21474647) AS CHAR); --Cannot convert string 'G\xADW' from binary to utf8
+```
+### 2. What did you expect to see? (Required)
+No error
+As a reference, there is no error for MySQL: https://www.db-fiddle.com/f/gtq3wBBEJezuCxHy1cgWtL/0
+
+### 3. What did you see instead (Required)
+Cannot convert string 'G\xADW' from binary to utf8
+
+### 4. What is your TiDB version? (Required)
+
+| Release Version: v6.2.0-alpha-159-ge0527ba27
+Edition: Community
+Git Commit Hash: e0527ba27c72b0a533b126fedfa025d47a209ca9
+Git Branch: master
+UTC Build Time: 2022-06-21 11:55:54
+GoVersion: go1.18.3
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+Store: unistore |
+
+
+",True,"Unexpected Error by CAST and CHAR functions - ## Bug Report
+
+### 1. Minimal reproduce step (Required)
+```sql
+SELECT CAST(CHAR(21474647) AS CHAR); --Cannot convert string 'G\xADW' from binary to utf8
+```
+### 2. What did you expect to see? (Required)
+No error
+As a reference, there is no error for MySQL: https://www.db-fiddle.com/f/gtq3wBBEJezuCxHy1cgWtL/0
+
+### 3. What did you see instead (Required)
+Cannot convert string 'G\xADW' from binary to utf8
+
+### 4. What is your TiDB version? (Required)
+
+| Release Version: v6.2.0-alpha-159-ge0527ba27
+Edition: Community
+Git Commit Hash: e0527ba27c72b0a533b126fedfa025d47a209ca9
+Git Branch: master
+UTC Build Time: 2022-06-21 11:55:54
+GoVersion: go1.18.3
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+Store: unistore |
+
+
+",1,unexpected error by cast and char functions bug report minimal reproduce step required sql select cast char as char cannot convert string g xadw from binary to what did you expect to see required no error as a reference there is no error for mysql what did you see instead required cannot convert string g xadw from binary to what is your tidb version required release version alpha edition community git commit hash git branch master utc build time goversion race enabled false tikv min version check table before drop false store unistore ,1
+16876,23232540105.0,IssuesEvent,2022-08-03 08:54:37,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,The default value of timestamp inconsistent with MySQL,compatibility-mysql8,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```
+create table t(a timestamp default '2010-09-12 12:23:00');
+select COLUMN_DEFAULT, COLUMN_TYPE from information_schema.columns where table_name='t' and column_name='a';
+```
+
+### 2. What did you expect to see? (Required)
+
+```
+mysql> select COLUMN_DEFAULT, COLUMN_TYPE from information_schema.columns where table_name='t' and column_name='a';
++---------------------+-------------+
+| COLUMN_DEFAULT | COLUMN_TYPE |
++---------------------+-------------+
+| 2010-09-12 12:23:00 | timestamp |
++---------------------+-------------+
+1 row in set (0.00 sec)
+```
+
+### 3. What did you see instead (Required)
+
+```
+mysql> select COLUMN_DEFAULT, COLUMN_TYPE from information_schema.columns where table_name='t' and column_name='a';
++---------------------+-------------+
+| COLUMN_DEFAULT | COLUMN_TYPE |
++---------------------+-------------+
+| 2010-09-12 04:23:00 | timestamp |
++---------------------+-------------+
+1 row in set (0.00 sec)
+```
+
+### 4. What is your TiDB version? (Required)
+```
+mysql> select tidb_version();
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v6.2.0-alpha-73-ga523d767f
+Edition: Community
+Git Commit Hash: a523d767f88e3fbcff1c3f138c8461dc0af5cd5e
+Git Branch: master
+UTC Build Time: 2022-06-07 09:24:17
+GoVersion: go1.18
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+Store: unistore |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+",True,"The default value of timestamp inconsistent with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```
+create table t(a timestamp default '2010-09-12 12:23:00');
+select COLUMN_DEFAULT, COLUMN_TYPE from information_schema.columns where table_name='t' and column_name='a';
+```
+
+### 2. What did you expect to see? (Required)
+
+```
+mysql> select COLUMN_DEFAULT, COLUMN_TYPE from information_schema.columns where table_name='t' and column_name='a';
++---------------------+-------------+
+| COLUMN_DEFAULT | COLUMN_TYPE |
++---------------------+-------------+
+| 2010-09-12 12:23:00 | timestamp |
++---------------------+-------------+
+1 row in set (0.00 sec)
+```
+
+### 3. What did you see instead (Required)
+
+```
+mysql> select COLUMN_DEFAULT, COLUMN_TYPE from information_schema.columns where table_name='t' and column_name='a';
++---------------------+-------------+
+| COLUMN_DEFAULT | COLUMN_TYPE |
++---------------------+-------------+
+| 2010-09-12 04:23:00 | timestamp |
++---------------------+-------------+
+1 row in set (0.00 sec)
+```
+
+### 4. What is your TiDB version? (Required)
+```
+mysql> select tidb_version();
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v6.2.0-alpha-73-ga523d767f
+Edition: Community
+Git Commit Hash: a523d767f88e3fbcff1c3f138c8461dc0af5cd5e
+Git Branch: master
+UTC Build Time: 2022-06-07 09:24:17
+GoVersion: go1.18
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+Store: unistore |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+",1,the default value of timestamp inconsistent with mysql bug report please answer these questions before submitting your issue thanks minimal reproduce step required create table t a timestamp default select column default column type from information schema columns where table name t and column name a what did you expect to see required mysql select column default column type from information schema columns where table name t and column name a column default column type timestamp row in set sec what did you see instead required mysql select column default column type from information schema columns where table name t and column name a column default column type timestamp row in set sec what is your tidb version required mysql select tidb version tidb version release version alpha edition community git commit hash git branch master utc build time goversion race enabled false tikv min version check table before drop false store unistore row in set sec ,1
+3301,6261686382.0,IssuesEvent,2017-07-15 02:16:25,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,create user without quotes failed,compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+exec sql `create user user1@localhost;`
+
+2. What did you expect to see?
+
+```
+mysql> create user user1@localhost;
+Query OK, 0 rows affected (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> create user uesr1@localhost;
+ERROR 1105 (HY000): line 0 column 17 near ""@localhost"" (total length 27)
+```
+
+but add quotes will succeed:
+
+```
+create user 'uesr1'@'localhost';
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+```
+Git Commit Hash: d1328e1b7282c026e579a413db3ad386c15fdabf
+UTC Build Time: 2017-06-22 03:37:28
+```
+",True,"create user without quotes failed - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+exec sql `create user user1@localhost;`
+
+2. What did you expect to see?
+
+```
+mysql> create user user1@localhost;
+Query OK, 0 rows affected (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> create user uesr1@localhost;
+ERROR 1105 (HY000): line 0 column 17 near ""@localhost"" (total length 27)
+```
+
+but add quotes will succeed:
+
+```
+create user 'uesr1'@'localhost';
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+```
+Git Commit Hash: d1328e1b7282c026e579a413db3ad386c15fdabf
+UTC Build Time: 2017-06-22 03:37:28
+```
+",1,create user without quotes failed please answer these questions before submitting your issue thanks what did you do exec sql create user localhost what did you expect to see mysql create user localhost query ok rows affected sec what did you see instead mysql create user localhost error line column near localhost total length but add quotes will succeed create user localhost what version of tidb are you using tidb server v git commit hash utc build time ,1
+3673,6545287682.0,IssuesEvent,2017-09-04 03:22:49,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,support `INSERT IGNORE` and `UPDATE IGNORE`,compatibility help wanted,"## 1. What did you do?
+
+Strict mode controls how TiDB and MySQL handles invalid or missing values in data-change statements such as `INSERT` or `UPDATE`.
+
+If strict mode is not in effect, TiDB and MySQL inserts adjusted values for invalid or missing values and produces warnings. In strict mode, users can produce this behavior by using `INSERT IGNORE` or `UPDATE IGNORE`
+
+TiDB doesn't support `INSERT IGNORE` or `UPDATE IGNORE` currently.
+
+## 2. What did you expect to see?
+
+```sql
+drop table if exists t;
+create table t(a bigint);
+```
+
+```sql
+MySQL > insert ignore into t select ""1a"";
+Query OK, 1 row affected, 1 warning (0.01 sec)
+Records: 1 Duplicates: 0 Warnings: 1
+```
+
+## 3. What did you see instead?
+
+```sql
+TiDB > insert ignore into t select ""1a"";
+ERROR 1265 (01000): Data Truncated
+```
+
+
+## 4. What version of TiDB are you using?
+```sh
+$./bin/tidb-server -V
+Release Version: 0.8.0
+Git Commit Hash: 97e9dfe92ce8acb6fa42834097a504379c711567
+Git Commit Branch: master
+UTC Build Time: 2017-08-21 08:53:16
+```
+",True,"support `INSERT IGNORE` and `UPDATE IGNORE` - ## 1. What did you do?
+
+Strict mode controls how TiDB and MySQL handles invalid or missing values in data-change statements such as `INSERT` or `UPDATE`.
+
+If strict mode is not in effect, TiDB and MySQL inserts adjusted values for invalid or missing values and produces warnings. In strict mode, users can produce this behavior by using `INSERT IGNORE` or `UPDATE IGNORE`
+
+TiDB doesn't support `INSERT IGNORE` or `UPDATE IGNORE` currently.
+
+## 2. What did you expect to see?
+
+```sql
+drop table if exists t;
+create table t(a bigint);
+```
+
+```sql
+MySQL > insert ignore into t select ""1a"";
+Query OK, 1 row affected, 1 warning (0.01 sec)
+Records: 1 Duplicates: 0 Warnings: 1
+```
+
+## 3. What did you see instead?
+
+```sql
+TiDB > insert ignore into t select ""1a"";
+ERROR 1265 (01000): Data Truncated
+```
+
+
+## 4. What version of TiDB are you using?
+```sh
+$./bin/tidb-server -V
+Release Version: 0.8.0
+Git Commit Hash: 97e9dfe92ce8acb6fa42834097a504379c711567
+Git Commit Branch: master
+UTC Build Time: 2017-08-21 08:53:16
+```
+",1,support insert ignore and update ignore what did you do strict mode controls how tidb and mysql handles invalid or missing values in data change statements such as insert or update if strict mode is not in effect tidb and mysql inserts adjusted values for invalid or missing values and produces warnings in strict mode users can produce this behavior by using insert ignore or update ignore tidb doesn t support insert ignore or update ignore currently what did you expect to see sql drop table if exists t create table t a bigint sql mysql insert ignore into t select query ok row affected warning sec records duplicates warnings what did you see instead sql tidb insert ignore into t select error data truncated what version of tidb are you using sh bin tidb server v release version git commit hash git commit branch master utc build time ,1
+12183,14367004351.0,IssuesEvent,2020-12-01 05:46:37,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,the range of bootstrapVer of different release should not overlapped,severity/critical sig/DDL type/bug type/compatibility,"The range of bootstrapVer of branch release-4.0 and branch master is overlapped for now.
+* branch release-4.0
+
+
+* branch master
+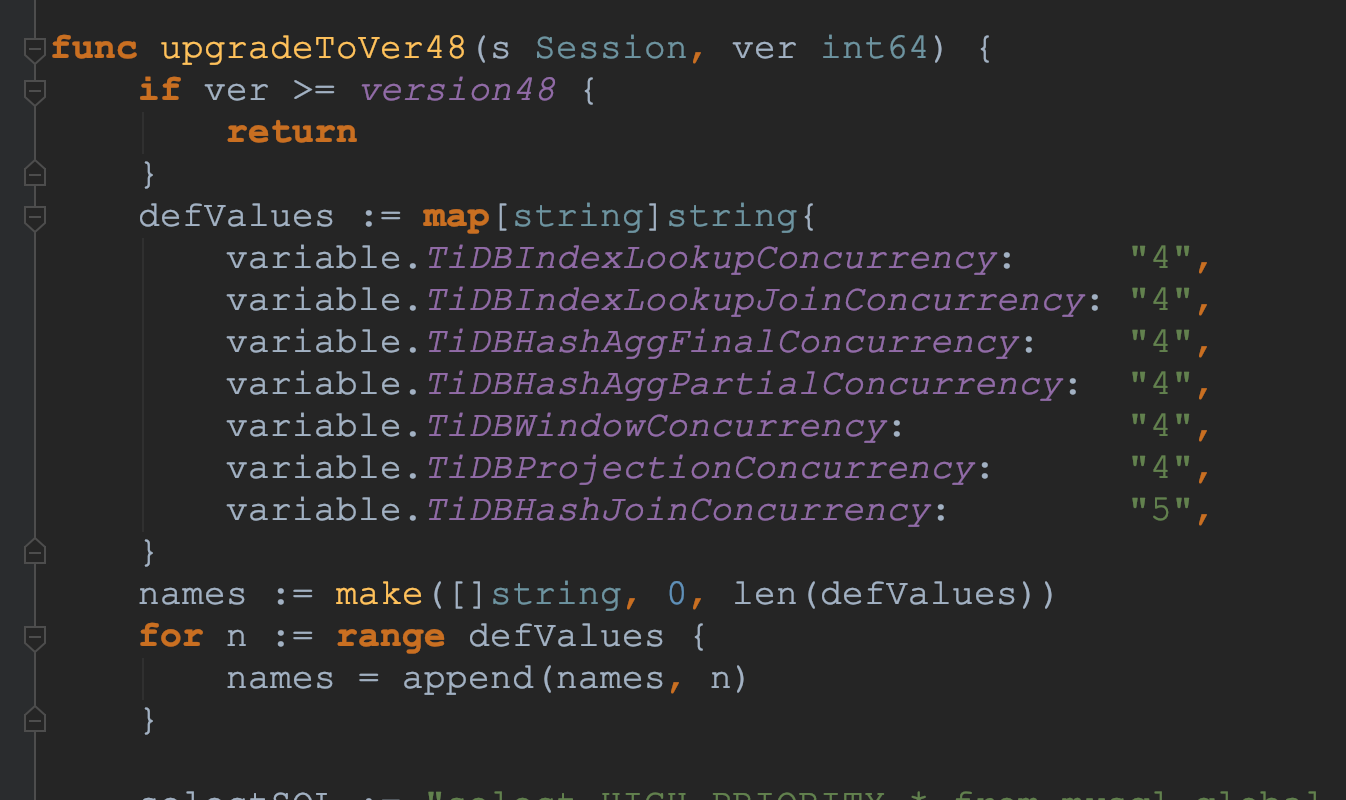
+
+
+It'll cause unexpected results when upgrading from V4.0 to V5.0.
+The following things need to be done to solve this problem.
+- [ ] Define unoverlapped ranges of bootstrapVer numbers for the different release versions.
+- [ ] Add version range check for the bootstrapVer.
+- [ ] Make sure all the upgrade operations are reentrant.",True,"the range of bootstrapVer of different release should not overlapped - The range of bootstrapVer of branch release-4.0 and branch master is overlapped for now.
+* branch release-4.0
+
+
+* branch master
+
+
+
+It'll cause unexpected results when upgrading from V4.0 to V5.0.
+The following things need to be done to solve this problem.
+- [ ] Define unoverlapped ranges of bootstrapVer numbers for the different release versions.
+- [ ] Add version range check for the bootstrapVer.
+- [ ] Make sure all the upgrade operations are reentrant.",1,the range of bootstrapver of different release should not overlapped the range of bootstrapver of branch release and branch master is overlapped for now branch release branch master it ll cause unexpected results when upgrading from to the following things need to be done to solve this problem define unoverlapped ranges of bootstrapver numbers for the different release versions add version range check for the bootstrapver make sure all the upgrade operations are reentrant ,1
+17245,23786746380.0,IssuesEvent,2022-09-02 10:50:27,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,create json value from string with binary charset should report error,type/enhancement type/compatibility component/json,"## Enhancement
+
+In MySQL 5.7, creating a json key from the blob value will give an error:
+
+```
+create table t (s varchar(255), b blob);
+insert into t values (""a string"", X'ABCD');
+insert into t values (""b string"", X'DCBA');
+
+select json_objectagg(b,s) from t;
+```
+
+Will give an error: `ERROR 3144 (22032): Cannot create a JSON value from a string with CHARACTER SET 'binary'.`.
+
+In TiDB, it will give: `{""\ufffd\ufffd"": ""a string"", ""ܺ"": ""b string""} `",True,"create json value from string with binary charset should report error - ## Enhancement
+
+In MySQL 5.7, creating a json key from the blob value will give an error:
+
+```
+create table t (s varchar(255), b blob);
+insert into t values (""a string"", X'ABCD');
+insert into t values (""b string"", X'DCBA');
+
+select json_objectagg(b,s) from t;
+```
+
+Will give an error: `ERROR 3144 (22032): Cannot create a JSON value from a string with CHARACTER SET 'binary'.`.
+
+In TiDB, it will give: `{""\ufffd\ufffd"": ""a string"", ""ܺ"": ""b string""} `",1,create json value from string with binary charset should report error enhancement in mysql creating a json key from the blob value will give an error create table t s varchar b blob insert into t values a string x abcd insert into t values b string x dcba select json objectagg b s from t will give an error error cannot create a json value from a string with character set binary in tidb it will give ufffd ufffd a string ܺ b string ,1
+3238,6193698498.0,IssuesEvent,2017-07-05 08:00:12,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Parsing `SET SESSION TRANSACTION ISOLATION LEVEL READ UNCOMMITTED` failed,compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+Dealing with statements invoked by sonarqube.
+
+2. What did you expect to see?
+Parse ok.
+
+3. What did you see instead?
+`[parser:1]syntax error`
+
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+`git rev-parse origin/master`
+`b780d6afefcbfca2b4f2b037cce5fb10ef0875f1`
+",True,"Parsing `SET SESSION TRANSACTION ISOLATION LEVEL READ UNCOMMITTED` failed - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+Dealing with statements invoked by sonarqube.
+
+2. What did you expect to see?
+Parse ok.
+
+3. What did you see instead?
+`[parser:1]syntax error`
+
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+`git rev-parse origin/master`
+`b780d6afefcbfca2b4f2b037cce5fb10ef0875f1`
+",1,parsing set session transaction isolation level read uncommitted failed please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error dealing with statements invoked by sonarqube what did you expect to see parse ok what did you see instead syntax error what version of tidb are you using tidb server v git rev parse origin master ,1
+3402,6368254226.0,IssuesEvent,2017-08-01 08:47:40,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,"Builtin function ""CAST"" compatibilities",compatibility rc3.1,"select cast(cast(1-2 as unsigned) as signed integer);
+
+MySQL:
+mysql> select cast(cast(1-2 as unsigned) as signed integer);
++-----------------------------------------------+
+| cast(cast(1-2 as unsigned) as signed integer) |
++-----------------------------------------------+
+| -1 |
++-----------------------------------------------+
+1 row in set (0.00 sec)
+
+TiDB:
+mysql> select cast(cast(1-2 as unsigned) as signed integer);
+ERROR 1690 (22003): constant 18446744073709551615 overflows bigint
+",True,"Builtin function ""CAST"" compatibilities - select cast(cast(1-2 as unsigned) as signed integer);
+
+MySQL:
+mysql> select cast(cast(1-2 as unsigned) as signed integer);
++-----------------------------------------------+
+| cast(cast(1-2 as unsigned) as signed integer) |
++-----------------------------------------------+
+| -1 |
++-----------------------------------------------+
+1 row in set (0.00 sec)
+
+TiDB:
+mysql> select cast(cast(1-2 as unsigned) as signed integer);
+ERROR 1690 (22003): constant 18446744073709551615 overflows bigint
+",1,builtin function cast compatibilities select cast cast as unsigned as signed integer mysql mysql select cast cast as unsigned as signed integer cast cast as unsigned as signed integer row in set sec tidb mysql select cast cast as unsigned as signed integer error constant overflows bigint ,1
+215913,7299277561.0,IssuesEvent,2018-02-26 19:36:29,GSA/code-gov-api,https://api.github.com/repos/GSA/code-gov-api,closed,Can't filter by multiple usage types,[priority] medium,"## Expected Behavior
+
+
+Should be able to get all repos for an agency that are open source or government wide reuse
+
+## Current Behavior
+
+
+Internal Server Error when try to filter by both at the same time. The repos endpoint works when try to filter by only one.
+
+## Possible Solution
+
+
+Not sure. Can I assume that all the repos returned from the repos endpoint are either governmentWideReuse or openSource and never exempt?
+
+## Steps to Reproduce (for bugs)
+
+
+1. https://code-api-staging.app.cloud.gov/api/0.1/repos?agency.acronym=GSA&size=1000&permissions.usageType=openSource&permissions.usageType=governmentWideReuse
+
+
+## Context
+
+
+Need this in order to show repos for an agency on code.gov while not showing exempt repos.
+",1.0,"Can't filter by multiple usage types - ## Expected Behavior
+
+
+Should be able to get all repos for an agency that are open source or government wide reuse
+
+## Current Behavior
+
+
+Internal Server Error when try to filter by both at the same time. The repos endpoint works when try to filter by only one.
+
+## Possible Solution
+
+
+Not sure. Can I assume that all the repos returned from the repos endpoint are either governmentWideReuse or openSource and never exempt?
+
+## Steps to Reproduce (for bugs)
+
+
+1. https://code-api-staging.app.cloud.gov/api/0.1/repos?agency.acronym=GSA&size=1000&permissions.usageType=openSource&permissions.usageType=governmentWideReuse
+
+
+## Context
+
+
+Need this in order to show repos for an agency on code.gov while not showing exempt repos.
+",0,can t filter by multiple usage types expected behavior should be able to get all repos for an agency that are open source or government wide reuse current behavior internal server error when try to filter by both at the same time the repos endpoint works when try to filter by only one possible solution not sure can i assume that all the repos returned from the repos endpoint are either governmentwidereuse or opensource and never exempt steps to reproduce for bugs context need this in order to show repos for an agency on code gov while not showing exempt repos ,0
+117058,4710472655.0,IssuesEvent,2016-10-14 10:15:40,default1406/PhyLab,https://api.github.com/repos/default1406/PhyLab,opened,整理录入数据处理方式,priority 1 size 2,"- 对象:杨子琛(2.5h)、程富瑞(0.5h)
+- 预计时长:3h
+- 详情:与程富瑞合作,预估需要修复的以及未来将使用的数据处理脚本信息,对其进行收集整理,形成较为详细的信息文档,以供未来脚本编写使用。",1.0,"整理录入数据处理方式 - - 对象:杨子琛(2.5h)、程富瑞(0.5h)
+- 预计时长:3h
+- 详情:与程富瑞合作,预估需要修复的以及未来将使用的数据处理脚本信息,对其进行收集整理,形成较为详细的信息文档,以供未来脚本编写使用。",0,整理录入数据处理方式 对象:杨子琛( )、程富瑞( ) 预计时长: 详情:与程富瑞合作,预估需要修复的以及未来将使用的数据处理脚本信息,对其进行收集整理,形成较为详细的信息文档,以供未来脚本编写使用。,0
+275103,23893295977.0,IssuesEvent,2022-09-08 13:08:06,iotaledger/explorer,https://api.github.com/repos/iotaledger/explorer,closed,[Task]: Revise and update the info modals for Stardust,network:testnet network:shimmer,"### Task description
-SONGMAN:GetNumCourses();
+- Info modals for Address, Block etc should be revised and updated for stardust
-Themes/Til Death/BGAnimations/ScreenSelectMusic decorations/other.lua
-src/SongManager.cpp
-Docs/Luadoc/Lua.xml
-Docs/Luadoc/LuaDocumentation.xml
+
-SONGMAN:GetNumAdditionalCourses();
+https://www.notion.so/Explorer-Broken-and-Requested-Links-dfa9afcf271048e99633863757497dae
-Docs/Luadoc/LuaDocumentation.xml
+### Requirements
-SONGMAN:GetNumLockedSongs();
+N/A
-Docs/Changelog_sm5.txt
-Docs/Luadoc/LuaDocumentation.xml
+### Acceptance criteria
-Update: SONGMAN:GetNumCourses(); seems to work. Although, it should be removed anyway.
+N/A
-Themes/Til Death/BGAnimations/ScreenSelectMusic decorations/other.lua
-src/SongManager.cpp
-Docs/Luadoc/Lua.xml
-Docs/Luadoc/LuaDocumentation.xml
+### Creation checklist
-Update: Hmm... Seems GAMESTATE:GetCurrentStage(); was removed as well? Oh well.
+- [X] I have assigned this task to the correct people
+- [X] I have added the most appropriate labels
+- [X] I have linked the correct milestone and/or project",1.0,"[Task]: Revise and update the info modals for Stardust - ### Task description
-Docs/Changelog_sm5.txt
-Docs/Luadoc/LuaDocumentation.xml
+- Info modals for Address, Block etc should be revised and updated for stardust
-Update: I am unsure but, I think this is removed. PREFSMAN:GetPreference(""PercentageScoring""); Although, a few references to it.
+
-Themes/_fallback/Languages/zh.ini
-Themes/_fallback/Languages/es.ini
-Themes/_fallback/Languages/fr.ini
-Themes/_fallback/Languages/ja.ini
-Themes/_fallback/Languages/nl.ini
-Themes/_fallback/Languages/pl.ini
-Themes/_fallback/Languages/de.ini
-Themes/_fallback/Languages/en.ini
-Docs/old_changelog.txt
-Docs/Changelog_sm-ssc.txt
-Themes/_fallback/metrics.ini
+https://www.notion.so/Explorer-Broken-and-Requested-Links-dfa9afcf271048e99633863757497dae
-Update: Unsure of this but likely my theme. Check into metric ComboContinuesBetweenSongs.
+### Requirements
-Update: Two others found. Unsure still. DancePointsForOni and MenuTimer.",1.0,"Misc Bugs here and there. - I made a theme that uses etterna's fallback theme. I went though trying to debug a few things here and there. I found a few issues.
+N/A
-(Missing Metrics)
+### Acceptance criteria
-ScreenSelectPlayMode::ChoiceNonstop=""""
-ScreenSelectPlayMode::ChoiceOni=""""
-ScreenSelectPlayMode::ChoiceEndless=""""
-OptionExplanations::FullTapExplosions="""" (I could not actually get this one to work. Must be broken.)
+N/A
-(Menu Options)
+### Creation checklist
-Jukebox does not work. Should be removed.
-Edit Step/Chart does not work. Should be removed.
+- [X] I have assigned this task to the correct people
+- [X] I have added the most appropriate labels
+- [X] I have linked the correct milestone and/or project",0, revise and update the info modals for stardust task description info modals for address block etc should be revised and updated for stardust requirements n a acceptance criteria n a creation checklist i have assigned this task to the correct people i have added the most appropriate labels i have linked the correct milestone and or project,0
+7074,9359291082.0,IssuesEvent,2019-04-02 06:21:25,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,reopened,"compatibility: “show full columns” prints wrong Collation for date, datatime, timestamp columns",type/compatibility,"```
+create table t1 (a date,b datetime,c timestamp);
+show full columns from t1;
+```
+TiDB shows a different collation value (""binary"") than mysql(null), this is not a big deal in most cases. It's reported that a CDC software called ""Attunity"" check the ""collation"" output of ""show full columns"" of the tables that managed by itself.
+the tool can't pass the db usability check ,pls take a look.
+
+MySQL 5.7.20
+
+> +-------+-----------+-----------+------+-----+---------+-------+---------------------------------+---------+
+> | Field | Type | Collation | Null | Key | Default | Extra | Privileges | Comment |
+> +-------+-----------+-----------+------+-----+---------+-------+---------------------------------+---------+
+> | a | date | NULL | YES | | NULL | | select,insert,update,references | |
+> | b | datetime | NULL | YES | | NULL | | select,insert,update,references | |
+> | c | timestamp | NULL | YES | | NULL | | select,insert,update,references | |
+> +-------+-----------+-----------+------+-----+---------+-------+---------------------------------+---------+
+> 3 rows in set (0.00 sec)
+
+TiDB 2.1.6:
+
+> +-------+-----------+-----------+------+------+---------+-------+---------------------------------+---------+
+> | Field | Type | Collation | Null | Key | Default | Extra | Privileges | Comment |
+> +-------+-----------+-----------+------+------+---------+-------+---------------------------------+---------+
+> | a | date | binary | YES | | NULL | | select,insert,update,references | |
+> | b | datetime | binary | YES | | NULL | | select,insert,update,references | |
+> | c | timestamp | binary | YES | | NULL | | select,insert,update,references | |
+> +-------+-----------+-----------+------+------+---------+-------+---------------------------------+---------+
+> 3 rows in set (0.01 sec)
+
+> Release Version: v2.1.6
+> Git Commit Hash: 66e639e8e127f71662f37287eb984dd84d169cba
+> Git Branch: HEAD
+> UTC Build Time: 2019-03-15 09:09:07
+> GoVersion: go version go1.11.2 linux/amd64
+> Race Enabled: false
+> TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+> Check Table Before Drop: false",True,"compatibility: “show full columns” prints wrong Collation for date, datatime, timestamp columns - ```
+create table t1 (a date,b datetime,c timestamp);
+show full columns from t1;
+```
+TiDB shows a different collation value (""binary"") than mysql(null), this is not a big deal in most cases. It's reported that a CDC software called ""Attunity"" check the ""collation"" output of ""show full columns"" of the tables that managed by itself.
+the tool can't pass the db usability check ,pls take a look.
+
+MySQL 5.7.20
+
+> +-------+-----------+-----------+------+-----+---------+-------+---------------------------------+---------+
+> | Field | Type | Collation | Null | Key | Default | Extra | Privileges | Comment |
+> +-------+-----------+-----------+------+-----+---------+-------+---------------------------------+---------+
+> | a | date | NULL | YES | | NULL | | select,insert,update,references | |
+> | b | datetime | NULL | YES | | NULL | | select,insert,update,references | |
+> | c | timestamp | NULL | YES | | NULL | | select,insert,update,references | |
+> +-------+-----------+-----------+------+-----+---------+-------+---------------------------------+---------+
+> 3 rows in set (0.00 sec)
+
+TiDB 2.1.6:
+
+> +-------+-----------+-----------+------+------+---------+-------+---------------------------------+---------+
+> | Field | Type | Collation | Null | Key | Default | Extra | Privileges | Comment |
+> +-------+-----------+-----------+------+------+---------+-------+---------------------------------+---------+
+> | a | date | binary | YES | | NULL | | select,insert,update,references | |
+> | b | datetime | binary | YES | | NULL | | select,insert,update,references | |
+> | c | timestamp | binary | YES | | NULL | | select,insert,update,references | |
+> +-------+-----------+-----------+------+------+---------+-------+---------------------------------+---------+
+> 3 rows in set (0.01 sec)
+
+> Release Version: v2.1.6
+> Git Commit Hash: 66e639e8e127f71662f37287eb984dd84d169cba
+> Git Branch: HEAD
+> UTC Build Time: 2019-03-15 09:09:07
+> GoVersion: go version go1.11.2 linux/amd64
+> Race Enabled: false
+> TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+> Check Table Before Drop: false",1,compatibility “show full columns” prints wrong collation for date datatime timestamp columns create table a date b datetime c timestamp show full columns from tidb shows a different collation value binary than mysql null this is not a big deal in most cases it s reported that a cdc software called attunity check the collation output of show full columns of the tables that managed by itself the tool can t pass the db usability check pls take a look mysql field type collation null key default extra privileges comment a date null yes null select insert update references b datetime null yes null select insert update references c timestamp null yes null select insert update references rows in set sec tidb field type collation null key default extra privileges comment a date binary yes null select insert update references b datetime binary yes null select insert update references c timestamp binary yes null select insert update references rows in set sec release version git commit hash git branch head utc build time goversion go version linux race enabled false tikv min version alpha check table before drop false,1
+6295,7551772720.0,IssuesEvent,2018-04-18 21:14:27,hyperledger/composer,https://api.github.com/repos/hyperledger/composer,closed,"debug trace can log large amounts of data, for example on method entry and exit",P3 debugging enhancement hlfv1 serviceability,"Looking at the chaincode logs from 0.16.x and the master branch there are times when a lot of data is output which serves no value but causes the logs to be massive making it difficult to navigate. An Example of this is outputting the base64 representation of the bna, if that bna is large. Another example is the constant output of the system transaction implementations.
+We should start by looking to cap the output of large strings by default to reduce this.",1.0,"debug trace can log large amounts of data, for example on method entry and exit - Looking at the chaincode logs from 0.16.x and the master branch there are times when a lot of data is output which serves no value but causes the logs to be massive making it difficult to navigate. An Example of this is outputting the base64 representation of the bna, if that bna is large. Another example is the constant output of the system transaction implementations.
+We should start by looking to cap the output of large strings by default to reduce this.",0,debug trace can log large amounts of data for example on method entry and exit looking at the chaincode logs from x and the master branch there are times when a lot of data is output which serves no value but causes the logs to be massive making it difficult to navigate an example of this is outputting the representation of the bna if that bna is large another example is the constant output of the system transaction implementations we should start by looking to cap the output of large strings by default to reduce this ,0
+14785,18170221258.0,IssuesEvent,2021-09-27 19:04:32,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Sysvar `identity` returns wrong value,type/bug help wanted type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+Manual code inspection. See: https://dev.mysql.com/doc/refman/8.0/en/server-system-variables.html#sysvar_identity -- the identity sysvar is an alias for `last_insert_id`
+
+### 2. What did you expect to see? (Required)
+
+There should be a `GetSession()` func for Identity that does the same thing. Instead it is a noop and does nothing:
+
+https://github.com/pingcap/tidb/blob/74b329402dac67da23a142e04f013d3355e4b6f3/sessionctx/variable/noop.go#L488
+
+See: https://github.com/pingcap/tidb/pull/28072 for where this was implemented for `last_insert_id`.
+
+### 3. What did you see instead (Required)
+
+Noop
+
+### 4. What is your TiDB version? (Required)
+
+master
+",True,"Sysvar `identity` returns wrong value - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+Manual code inspection. See: https://dev.mysql.com/doc/refman/8.0/en/server-system-variables.html#sysvar_identity -- the identity sysvar is an alias for `last_insert_id`
+
+### 2. What did you expect to see? (Required)
+
+There should be a `GetSession()` func for Identity that does the same thing. Instead it is a noop and does nothing:
+
+https://github.com/pingcap/tidb/blob/74b329402dac67da23a142e04f013d3355e4b6f3/sessionctx/variable/noop.go#L488
+
+See: https://github.com/pingcap/tidb/pull/28072 for where this was implemented for `last_insert_id`.
+
+### 3. What did you see instead (Required)
+
+Noop
+
+### 4. What is your TiDB version? (Required)
+
+master
+",1,sysvar identity returns wrong value bug report please answer these questions before submitting your issue thanks minimal reproduce step required manual code inspection see the identity sysvar is an alias for last insert id what did you expect to see required there should be a getsession func for identity that does the same thing instead it is a noop and does nothing see for where this was implemented for last insert id what did you see instead required noop what is your tidb version required master ,1
+158679,20028876621.0,IssuesEvent,2022-02-02 01:24:58,turkdevops/brackets,https://api.github.com/repos/turkdevops/brackets,closed,WS-2017-0247 (High) detected in ms-0.7.1.tgz - autoclosed,security vulnerability,"## WS-2017-0247 - High Severity Vulnerability
+ Vulnerable Library - ms-0.7.1.tgz
-(Crash)
+
-Verses and Doubles work but should be removed. (Since player 2 was removed, likely, this will not work in doubles/verses.)
-Nonstop, Oni, and Endless should be removed. (If done, you can ignore the metrics then.)
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Network
+ - Attack Complexity: Low
+ - Privileges Required: None
+ - User Interaction: None
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: None
+ - Integrity Impact: None
+ - Availability Impact: High
+
+For more information on CVSS3 Scores, click here.
+
+
+
+ Suggested Fix
+
-More bugs found. The following seemed to have been removed from the game:
+
+
+
-(However, I did a search in the repo and some things still remain noting these, Please be sure to remove them if this is the intended case.)
+***
+Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",True,"WS-2017-0247 (High) detected in ms-0.7.1.tgz - autoclosed - ## WS-2017-0247 - High Severity Vulnerability
+ Vulnerable Library - ms-0.7.1.tgz
-SONGMAN:GetNumCourses();
+
-Docs/Changelog_sm5.txt
-Docs/Luadoc/LuaDocumentation.xml
+
+
+
-Update: SONGMAN:GetNumCourses(); seems to work. Although, it should be removed anyway.
+***
+Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",0,ws high detected in ms tgz autoclosed ws high severity vulnerability vulnerable library ms tgz tiny ms conversion utility library home page a href path to dependency file brackets package json path to vulnerable library brackets node modules tiny lr node modules ms package json brackets node modules body parser node modules ms package json dependency hierarchy grunt contrib watch tgz root library tiny lr tgz debug tgz x ms tgz vulnerable library found in head commit a href found in base branch checktravis vulnerability details affected versions of this package are vulnerable to regular expression denial of service redos publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource ,0
+5168,7747785887.0,IssuesEvent,2018-05-30 05:37:52,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,"""in"" clause should not return error if type overflow",compatibility help wanted,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+create table t1 (some_id smallint(5) unsigned,key (some_id) );
+insert into t1 values (1),(2);
+select some_id from t1 where some_id not in(2,-1);
+```
+
+2. What did you expect to see?
+
+```
++---------+
+| some_id |
++---------+
+| 1 |
++---------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+ERROR 1690 (22003): constant -1 overflows smallint
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"""in"" clause should not return error if type overflow - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+create table t1 (some_id smallint(5) unsigned,key (some_id) );
+insert into t1 values (1),(2);
+select some_id from t1 where some_id not in(2,-1);
+```
+
+2. What did you expect to see?
+
+```
++---------+
+| some_id |
++---------+
+| 1 |
++---------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+ERROR 1690 (22003): constant -1 overflows smallint
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1, in clause should not return error if type overflow please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql create table some id smallint unsigned key some id insert into values select some id from where some id not in what did you expect to see some id row in set sec what did you see instead error constant overflows smallint what version of tidb are you using tidb server v ,1
+169055,26740743190.0,IssuesEvent,2023-01-30 12:48:35,codestates-seb/seb41_main_028,https://api.github.com/repos/codestates-seb/seb41_main_028,closed,[FE] Feat: certificationModal 데이터 바인딩 작업,FE Feat Design,"## To do List
+
+- [x] certification 모달창의 데이터를 받아와서 뿌려주기
+
+
+## Deadline
+
+230129 / 23:59
+
+## Issue Checklist
+아래 체크리스트를 확인해주세요.
+- [x] Issue Title을 다음 예시와 같이 작성했습니다. (e.g. [FE] Feat: 회원가입 기능 구현 )
+- [x] 우측의 Assignees, Labels, Projects, Milestone을 적절하게 선택했습니다.
+",1.0,"[FE] Feat: certificationModal 데이터 바인딩 작업 - ## To do List
+
+- [x] certification 모달창의 데이터를 받아와서 뿌려주기
+
+
+## Deadline
+
+230129 / 23:59
+
+## Issue Checklist
+아래 체크리스트를 확인해주세��.
+- [x] Issue Title을 다음 예시와 같이 작성했습니다. (e.g. [FE] Feat: 회원가입 기능 구현 )
+- [x] 우측의 Assignees, Labels, Projects, Milestone을 적절하게 선택했습니다.
+",0, feat certificationmodal 데이터 바인딩 작업 to do list certification 모달창의 데이터를 받아와서 뿌려주기 deadline issue checklist 아래 체크리스트를 확인해주세요 issue title을 다음 예시와 같이 작성했습니다 e g feat 회원가입 기능 구현 우측의 assignees labels projects milestone을 적절하게 선택했습니다 ,0
+5816,8269218042.0,IssuesEvent,2018-09-15 02:52:23,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,[bug] Inconsistent behavior of grant command between MySQL and TiDB,question type/compatibility,"
+1. What did you do?
+when trying to create different user and different databases, I encountered a inconsistent behavior of grant command between MySQL and TiDB.
+
+To reproduce this, follow the steps below
+
+1. `create database db123;`
+2. `grant select,insert,delete on db123.* to '123' identified by 'test';`
+3. login with `123:test`
+4. `show databases;` there are two databases `information_schema`, `db123`
+5. `use information_schema;` `select * from tables;`
+
+tables that not belongs to user `123` appears in the result of last command;
+
+while MySQL behaves normal, user `123` cannot see anything belongs to others.
+
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+Git Commit Hash: 37d8ea3e38209d0f49a0f46c649220f8877b9fd8
+UTC Build Time: 2017-07-19 02:19:35
+",True,"[bug] Inconsistent behavior of grant command between MySQL and TiDB -
+1. What did you do?
+when trying to create different user and different databases, I encountered a inconsistent behavior of grant command between MySQL and TiDB.
+
+To reproduce this, follow the steps below
+
+1. `create database db123;`
+2. `grant select,insert,delete on db123.* to '123' identified by 'test';`
+3. login with `123:test`
+4. `show databases;` there are two databases `information_schema`, `db123`
+5. `use information_schema;` `select * from tables;`
+
+tables that not belongs to user `123` appears in the result of last command;
+
+while MySQL behaves normal, user `123` cannot see anything belongs to others.
+
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+Git Commit Hash: 37d8ea3e38209d0f49a0f46c649220f8877b9fd8
+UTC Build Time: 2017-07-19 02:19:35
+",1, inconsistent behavior of grant command between mysql and tidb what did you do when trying to create different user and different databases i encountered a inconsistent behavior of grant command between mysql and tidb to reproduce this follow the steps below create database grant select insert delete on to identified by test login with test show databases there are two databases information schema use information schema select from tables tables that not belongs to user appears in the result of last command; while mysql behaves normal user cannot see anything belongs to others what version of tidb are you using tidb server v git commit hash utc build time ,1
+256772,27561720404.0,IssuesEvent,2023-03-07 22:42:08,samqws-marketing/box_box-ui-elements,https://api.github.com/repos/samqws-marketing/box_box-ui-elements,closed,CVE-2022-25912 (High) detected in simple-git-1.131.0.tgz - autoclosed,security vulnerability,"## CVE-2022-25912 - High Severity Vulnerability
+ Vulnerable Library - simple-git-1.131.0.tgz
-Themes/Til Death/BGAnimations/ScreenSelectMusic decorations/other.lua
-src/SongManager.cpp
-Docs/Luadoc/Lua.xml
-Docs/Luadoc/LuaDocumentation.xml
+
+
+The package simple-git before 3.15.0 are vulnerable to Remote Code Execution (RCE) when enabling the ext transport protocol, which makes it exploitable via clone() method. This vulnerability exists due to an incomplete fix of [CVE-2022-24066](https://security.snyk.io/vuln/SNYK-JS-SIMPLEGIT-2434306).
-Docs/Changelog_sm5.txt
-Docs/Luadoc/LuaDocumentation.xml
+
-Update: Unsure of this but likely my theme. Check into metric ComboContinuesBetweenSongs.
+
+
+
-Update: Two others found. Unsure still. DancePointsForOni and MenuTimer.",0,misc bugs here and there i made a theme that uses etterna s fallback theme i went though trying to debug a few things here and there i found a few issues missing metrics screenselectplaymode choicenonstop screenselectplaymode choiceoni screenselectplaymode choiceendless optionexplanations fulltapexplosions i could not actually get this one to work must be broken menu options jukebox does not work should be removed edit step chart does not work should be removed crash couples mode crashes the game needs to be removed concerns verses and doubles work but should be removed since player was removed likely this will not work in doubles verses nonstop oni and endless should be removed if done you can ignore the metrics then more bugs found the following seemed to have been removed from the game however i did a search in the repo and some things still remain noting these please be sure to remove them if this is the intended case songman getnumcourses themes til death bganimations screenselectmusic decorations other lua src songmanager cpp docs luadoc lua xml docs luadoc luadocumentation xml songman getnumadditionalcourses docs luadoc luadocumentation xml songman getnumlockedsongs docs changelog txt docs luadoc luadocumentation xml update songman getnumcourses seems to work although it should be removed anyway themes til death bganimations screenselectmusic decorations other lua src songmanager cpp docs luadoc lua xml docs luadoc luadocumentation xml update hmm seems gamestate getcurrentstage was removed as well oh well docs changelog txt docs luadoc luadocumentation xml update i am unsure but i think this is removed prefsman getpreference percentagescoring although a few references to it themes fallback languages zh ini themes fallback languages es ini themes fallback languages fr ini themes fallback languages ja ini themes fallback languages nl ini themes fallback languages pl ini themes fallback languages de ini themes fallback languages en ini docs old changelog txt docs changelog sm ssc txt themes fallback metrics ini update unsure of this but likely my theme check into metric combocontinuesbetweensongs update two others found unsure still dancepointsforoni and menutimer ,0
-352416,32065039261.0,IssuesEvent,2023-09-25 01:45:32,unifyai/ivy,https://api.github.com/repos/unifyai/ivy,reopened,Fix jax_lax_operators.test_jax_nextafter,JAX Frontend Sub Task Failing Test,"| | |
-|---|---|
-|numpy|
-|jax|
-|tensorflow|
-|torch|
-|paddle|
-",1.0,"Fix jax_lax_operators.test_jax_nextafter - | | |
-|---|---|
-|numpy|
-|jax|
-|tensorflow|
-|torch|
-|paddle|
-",0,fix jax lax operators test jax nextafter numpy a href src jax a href src tensorflow a href src torch a href src paddle a href src ,0
-11164,13182146458.0,IssuesEvent,2020-08-12 15:20:08,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,join on int primary key and text is not the same with MySQL,type/compatibility type/wontfix,"## Bug Report
+***
+
+- [ ] Check this box to open an automated fix PR
+
+",True,"CVE-2022-25912 (High) detected in simple-git-1.131.0.tgz - autoclosed - ## CVE-2022-25912 - High Severity Vulnerability
+ Vulnerable Library - simple-git-1.131.0.tgz
-Please answer these questions before submitting your issue. Thanks!
+
+
+The package simple-git before 3.15.0 are vulnerable to Remote Code Execution (RCE) when enabling the ext transport protocol, which makes it exploitable via clone() method. This vulnerability exists due to an incomplete fix of [CVE-2022-24066](https://security.snyk.io/vuln/SNYK-JS-SIMPLEGIT-2434306).
-```
-CREATE TABLE t1 (id int(11) NOT NULL AUTO_INCREMENT, PRIMARY KEY (`id`));
-INSERT INTO t1(`id`) VALUES(3);
-CREATE TABLE t2 (title text);
-INSERT INTO t2(`title`) VALUES(""3.0.1"");
-SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-```
-
-2. What did you expect to see?
+
-mysql> INSERT INTO t1(`id`) VALUES(3);
-Query OK, 1 row affected (0.00 sec)
+
+
+
-mysql> CREATE TABLE t2 (title text);
-Query OK, 0 rows affected (0.00 sec)
+***
+
+- [ ] Check this box to open an automated fix PR
+
+",0,cve high detected in simple git tgz autoclosed cve high severity vulnerability vulnerable library simple git tgz simple git interface for node js library home page a href path to dependency file package json path to vulnerable library node modules simple git package json dependency hierarchy x simple git tgz vulnerable library found in head commit a href found in base branch master vulnerability details the package simple git before are vulnerable to remote code execution rce when enabling the ext transport protocol which makes it exploitable via clone method this vulnerability exists due to an incomplete fix of publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution check this box to open an automated fix pr ,0
+8204,10287748012.0,IssuesEvent,2019-08-27 09:35:37,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Function arguments in error message should represent as a column name if possible.,component/expression help wanted type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```mysql
+SELECT EXP(col_float_unsigned) FROM table40_int_autoinc;
+SELECT EXP(17324);
+```
+
+2. What did you expect to see?
+
+```mysql
+mysql> SELECT EXP(col_float_unsigned) FROM table40_int_autoinc;
+ERROR 1690 (22003): DOUBLE value is out of range in 'exp(`randgen_test`.`table40_int_autoinc`.`col_float_unsigned`)'
+mysql> SELECT EXP(17324);
+ERROR 1690 (22003): DOUBLE value is out of range in 'exp(17324)'
+```
+
+3. What did you see instead?
+
+```mysql
+mysql> SELECT EXP(col_float_unsigned) FROM table40_int_autoinc;
+ERROR 1690 (22003): DOUBLE value is out of range in 'exp(17324)'
+mysql> SELECT EXP(17324);
+ERROR 1690 (22003): DOUBLE value is out of range in 'exp(17324)'
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+8c20289c7",True,"Function arguments in error message should represent as a column name if possible. - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```mysql
+SELECT EXP(col_float_unsigned) FROM table40_int_autoinc;
+SELECT EXP(17324);
+```
+
+2. What did you expect to see?
+
+```mysql
+mysql> SELECT EXP(col_float_unsigned) FROM table40_int_autoinc;
+ERROR 1690 (22003): DOUBLE value is out of range in 'exp(`randgen_test`.`table40_int_autoinc`.`col_float_unsigned`)'
+mysql> SELECT EXP(17324);
+ERROR 1690 (22003): DOUBLE value is out of range in 'exp(17324)'
+```
+
+3. What did you see instead?
+
+```mysql
+mysql> SELECT EXP(col_float_unsigned) FROM table40_int_autoinc;
+ERROR 1690 (22003): DOUBLE value is out of range in 'exp(17324)'
+mysql> SELECT EXP(17324);
+ERROR 1690 (22003): DOUBLE value is out of range in 'exp(17324)'
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+8c20289c7",1,function arguments in error message should represent as a column name if possible bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error mysql select exp col float unsigned from int autoinc select exp what did you expect to see mysql mysql select exp col float unsigned from int autoinc error double value is out of range in exp randgen test int autoinc col float unsigned mysql select exp error double value is out of range in exp what did you see instead mysql mysql select exp col float unsigned from int autoinc error double value is out of range in exp mysql select exp error double value is out of range in exp what version of tidb are you using tidb server v or run select tidb version on tidb ,1
+548041,16055850029.0,IssuesEvent,2021-04-23 04:51:17,npm/statusboard,https://api.github.com/repos/npm/statusboard,closed,fix: running `npm` commands in `npm exec`,Bug Priority 1 Release 7.x workspaces-custom,"### Current Behavior
+* `npm exec -ws -c 'npm whoami'` fails because `workspaces` is passed into the subprocess as an environment var
+* `npm exec -w foo -c 'npm whoami'` fails because `workspace` is passed into the subprocess as an environment var
+
+### Expected Behavior
+* `npm exec` should not pass on `workspace` or `workspaces` config into the env
+
+### Exit Criteria
+* [ ] bug should be fixed
+* [ ] documentation should exist for `npm exec` that explicitly outlines the absence of those envs from the subprocess
+* [ ] documentation should be updated to use `--ws` wherever `-ws` currently is marked (ex. examples)",1.0,"fix: running `npm` commands in `npm exec` - ### Current Behavior
+* `npm exec -ws -c 'npm whoami'` fails because `workspaces` is passed into the subprocess as an environment var
+* `npm exec -w foo -c 'npm whoami'` fails because `workspace` is passed into the subprocess as an environment var
+
+### Expected Behavior
+* `npm exec` should not pass on `workspace` or `workspaces` config into the env
+
+### Exit Criteria
+* [ ] bug should be fixed
+* [ ] documentation should exist for `npm exec` that explicitly outlines the absence of those envs from the subprocess
+* [ ] documentation should be updated to use `--ws` wherever `-ws` currently is marked (ex. examples)",0,fix running npm commands in npm exec current behavior npm exec ws c npm whoami fails because workspaces is passed into the subprocess as an environment var npm exec w foo c npm whoami fails because workspace is passed into the subprocess as an environment var expected behavior npm exec should not pass on workspace or workspaces config into the env exit criteria bug should be fixed documentation should exist for npm exec that explicitly outlines the absence of those envs from the subprocess documentation should be updated to use ws wherever ws currently is marked ex examples ,0
+3472,6447689761.0,IssuesEvent,2017-08-14 08:37:37,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Cannot authenticate users which username contains '@',compatibility,"MySQL:
+
+```
+mysql> create user 'test@example.com'@'localhost' identified by '';
+Query OK, 0 rows affected (0.03 sec)
+```
+
+```
+$ mysql -u 'test@example.com' --host 127.0.0.1
+Welcome to the MySQL monitor. Commands end with ; or \g.
+....
+```
+
+TiDB:
+
+```
+mysql> create user 'test@example.com'@'localhost' identified by '';
+Query OK, 1 row affected (0.00 sec)
+```
+
+```
+$ mysql -u 'test@example.com' --host 127.0.0.1 --port 4000
+ERROR 1045 (28000): Access denied for user 'test@example.com'@'127.0.0.1' (using password: YES)
+```",True,"Cannot authenticate users which username contains '@' - MySQL:
+
+```
+mysql> create user 'test@example.com'@'localhost' identified by '';
+Query OK, 0 rows affected (0.03 sec)
+```
+
+```
+$ mysql -u 'test@example.com' --host 127.0.0.1
+Welcome to the MySQL monitor. Commands end with ; or \g.
+....
+```
+
+TiDB:
+
+```
+mysql> create user 'test@example.com'@'localhost' identified by '';
+Query OK, 1 row affected (0.00 sec)
+```
+
+```
+$ mysql -u 'test@example.com' --host 127.0.0.1 --port 4000
+ERROR 1045 (28000): Access denied for user 'test@example.com'@'127.0.0.1' (using password: YES)
+```",1,cannot authenticate users which username contains mysql mysql create user test example com localhost identified by query ok rows affected sec mysql u test example com host welcome to the mysql monitor commands end with or g tidb mysql create user test example com localhost identified by query ok row affected sec mysql u test example com host port error access denied for user test example com using password yes ,1
+11610,13652838854.0,IssuesEvent,2020-09-27 09:37:38,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Different error message from MySQL when `group by` a window function or agg function with a `as`,severity/moderate sig/planner type/bug type/compatibility,"## Bug Report
+
+### 1. What did you do?
+
+In a select stmt, `group by` a number, and this number refers to a window function or aggregation function with a `as`.
+
+### 2. What did you expect to see?
+In 8.0.19 MySQL Community:
+```
+MySQL [test]> select row_number() over () as x from t group by 1;
+ERROR 1056 (42000): Can't group on 'x'
+MySQL [test]> select sum(a) as x from t group by 1;
+ERROR 1056 (42000): Can't group on 'x'
+```
+### 3. What did you see instead?
+In TiDB:
+```
+MySQL [test]> select row_number() over () as x from t group by 1;
+ERROR 1056 (42000): Can't group on ''
+MySQL [test]> select sum(a) as x from t group by 1;
+ERROR 1056 (42000): Can't group on ''
+```
+### 4. What version of TiDB are you using? (`tidb-server -V` or run `select tidb_version();` on TiDB)
+Release Version: v4.0.0-beta-710-gac8785a97",True,"Different error message from MySQL when `group by` a window function or agg function with a `as` - ## Bug Report
+
+### 1. What did you do?
+
+In a select stmt, `group by` a number, and this number refers to a window function or aggregation function with a `as`.
+
+### 2. What did you expect to see?
+In 8.0.19 MySQL Community:
+```
+MySQL [test]> select row_number() over () as x from t group by 1;
+ERROR 1056 (42000): Can't group on 'x'
+MySQL [test]> select sum(a) as x from t group by 1;
+ERROR 1056 (42000): Can't group on 'x'
+```
+### 3. What did you see instead?
+In TiDB:
+```
+MySQL [test]> select row_number() over () as x from t group by 1;
+ERROR 1056 (42000): Can't group on ''
+MySQL [test]> select sum(a) as x from t group by 1;
+ERROR 1056 (42000): Can't group on ''
+```
+### 4. What version of TiDB are you using? (`tidb-server -V` or run `select tidb_version();` on TiDB)
+Release Version: v4.0.0-beta-710-gac8785a97",1,different error message from mysql when group by a window function or agg function with a as bug report what did you do in a select stmt group by a number and this number refers to a window function or aggregation function with a as what did you expect to see in mysql community mysql select row number over as x from t group by error can t group on x mysql select sum a as x from t group by error can t group on x what did you see instead in tidb mysql select row number over as x from t group by error can t group on mysql select sum a as x from t group by error can t group on what version of tidb are you using tidb server v or run select tidb version on tidb release version beta ,1
+24802,5104332780.0,IssuesEvent,2017-01-05 00:45:28,Azure/azure-mobile-apps-net-client,https://api.github.com/repos/Azure/azure-mobile-apps-net-client,closed,Improve doccoments: add class summary and exception list,Category-Documentation Feature Request,"There is very little documentation for the SDK - _in xml doc comments in particular_.
-mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
-Query OK, 1 row affected (0.00 sec)
-
-mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-Empty set (0.00 sec)
-
-mysql> SELECT version();
-+-----------+
-| version() |
-+-----------+
-| 8.0.18 |
-+-----------+
-1 row in set (0.00 sec)
-
-mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-+----+-------------+-------+------------+--------+---------------+---------+---------+----------------+------+----------+--------------------------+
-| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
-+----+-------------+-------+------------+--------+---------------+---------+---------+----------------+------+----------+--------------------------+
-| 1 | SIMPLE | t2 | NULL | ALL | NULL | NULL | NULL | NULL | 1 | 100.00 | Using where |
-| 1 | SIMPLE | t1 | NULL | eq_ref | PRIMARY | PRIMARY | 4 | repro.t2.title | 1 | 100.00 | Using where; Using index |
-+----+-------------+-------+------------+--------+---------------+---------+---------+----------------+------+----------+--------------------------+
-2 rows in set, 1 warning (0.00 sec)
-```
+If this is not a priority item right now, then at least provide the basics:
+1. Describe each class and interface, in the topmost `/// `. So at least we know what a `SomethingOrOtherService` actually does. This would also give us Intellisense.
+2. Important, even moreso than (1): specify WHICH EXCEPTIONS ARE THROWN by the various methods, i.e. `/// Thrown when blah.`. We're tired of our code blowing up because of unseen problems. :sob:
-3. What did you see instead?
+The lack of (2) is a giving us endless problems. And resorting to a failsafe catch of `Exception` everywhere is the sure sign of bad API design. It means we don't really know what is going on, and the design contract between API supplier (you) and consumer (us) is tenuous at best.
-* TiDB
+The SDK is rock solid, no doubt, and performs as promised, when you are doing the right things. But without at least the above it is incomplete. **Tutorials, articles, blogs and sample code projects - though appreciated, do not qualify as documentation, they are supplementary.**
-```
-mysql> CREATE TABLE t1 (id int(11) NOT NULL AUTO_INCREMENT, PRIMARY KEY (`id`));
-Query OK, 0 rows affected (0.08 sec)
-
-mysql> INSERT INTO t1(`id`) VALUES(3);
-Query OK, 1 row affected (0.01 sec)
-
-mysql> CREATE TABLE t2 (title text);
-Query OK, 0 rows affected (0.08 sec)
-
-mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
-Query OK, 1 row affected (0.01 sec)
-
-mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-+----+-------+
-| id | title |
-+----+-------+
-| 3 | 3.0.1 |
-+----+-------+
-1 row in set, 1 warning (0.00 sec)
-
-mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-+----------------------------+-------+-----------+-----------------------------------------------------------------+
-| id | count | task | operator info |
-+----------------------------+-------+-----------+-----------------------------------------------------------------+
-| Projection_8 | 1.00 | root | Column#1, Column#2 |
-| └─HashLeftJoin_9 | 1.00 | root | inner join, inner:Projection_14, equal:[eq(Column#6, Column#7)] |
-| ├─Projection_11 | 1.00 | root | Column#1, cast(Column#1) |
-| │ └─TableReader_13 | 1.00 | root | data:TableScan_12 |
-| │ └─TableScan_12 | 1.00 | cop[tikv] | table:t1, range:[-inf,+inf], keep order:false, stats:pseudo |
-| └─Projection_14 | 1.00 | root | Column#2, cast(Column#2) |
-| └─TableReader_16 | 1.00 | root | data:TableScan_15 |
-| └─TableScan_15 | 1.00 | cop[tikv] | table:t2, range:[-inf,+inf], keep order:false, stats:pseudo |
-+----------------------------+-------+-----------+-----------------------------------------------------------------+
-8 rows in set (0.00 sec)
-```
+Sorry for the rant, because we love where Azure is headed, but if this SDK is intended as a way for us to buy into a professional paid-for service, then the reference documentation must be improved.
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+**EDIT:** PS, before getting upset with me, please know that this is a very widely reported problem on StackOverflow, for Azure in particular. Which is unfortunate as the underlying .NET platform is _very_ well documented. Amazon AWS don't release new services without extensive docs.
+",1.0,"Improve doccoments: add class summary and exception list - There is very little documentation for the SDK - _in xml doc comments in particular_.
-```
-Release Version: v4.0.0-alpha-842-g3ca8661b5
-Git Commit Hash: 3ca8661b5b3b12ecdfd664a5dd090f2af859a55c
-Git Branch: master
-UTC Build Time: 2019-11-12 01:03:14
-GoVersion: go version go1.13 linux/amd64
-Race Enabled: false
-TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
-Check Table Before Drop: false
-```
+If this is not a priority item right now, then at least provide the basics:
+1. Describe each class and interface, in the topmost `/// `. So at least we know what a `SomethingOrOtherService` actually does. This would also give us Intellisense.
+2. Important, even moreso than (1): specify WHICH EXCEPTIONS ARE THROWN by the various methods, i.e. `/// Thrown when blah.`. We're tired of our code blowing up because of unseen problems. :sob:
-5. More information
+The lack of (2) is a giving us endless problems. And resorting to a failsafe catch of `Exception` everywhere is the sure sign of bad API design. It means we don't really know what is going on, and the design contract between API supplier (you) and consumer (us) is tenuous at best.
-BTW, this incorrect behavior only happens in primary key, the following SQLs are executed same in both side.
+The SDK is rock solid, no doubt, and performs as promised, when you are doing the right things. But without at least the above it is incomplete. **Tutorials, articles, blogs and sample code projects - though appreciated, do not qualify as documentation, they are supplementary.**
-```
-CREATE TABLE t1 (id int);
-INSERT INTO t1(`id`) VALUES(3);
-CREATE TABLE t2 (title text);
-INSERT INTO t2(`title`) VALUES(""3.0.1"");
-SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-```
+Sorry for the rant, because we love where Azure is headed, but if this SDK is intended as a way for us to buy into a professional paid-for service, then the reference documentation must be improved.
-* In MySQL 8.0
+**EDIT:** PS, before getting upset with me, please know that this is a very widely reported problem on StackOverflow, for Azure in particular. Which is unfortunate as the underlying .NET platform is _very_ well documented. Amazon AWS don't release new services without extensive docs.
+",0,improve doccoments add class summary and exception list there is very little documentation for the sdk in xml doc comments in particular if this is not a priority item right now then at least provide the basics describe each class and interface in the topmost so at least we know what a somethingorotherservice actually does this would also give us intellisense important even moreso than specify which exceptions are thrown by the various methods i e thrown when blah we re tired of our code blowing up because of unseen problems sob the lack of is a giving us endless problems and resorting to a failsafe catch of exception everywhere is the sure sign of bad api design it means we don t really know what is going on and the design contract between api supplier you and consumer us is tenuous at best the sdk is rock solid no doubt and performs as promised when you are doing the right things but without at least the above it is incomplete tutorials articles blogs and sample code projects though appreciated do not qualify as documentation they are supplementary sorry for the rant because we love where azure is headed but if this sdk is intended as a way for us to buy into a professional paid for service then the reference documentation must be improved edit ps before getting upset with me please know that this is a very widely reported problem on stackoverflow for azure in particular which is unfortunate as the underlying net platform is very well documented amazon aws don t release new services without extensive docs ,0
+11149,13164855839.0,IssuesEvent,2020-08-11 05:02:19,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,TiDB does not support COM_RESET_CONNECTION,component/mysql-protocol type/compatibility," var conn = new MySql.Data.MySqlClient.MySqlConnection();
+ using (conn)
+ {
+ conn.Open();
+ }
+ conn = new MySql.Data.MySqlClient.MySqlConnection();
+ using (conn)
+ {
+ conn.Open(); // Crash here!!!
+ }
+
+when close connection then use another one, crash on open method with the exception:
+MySql.Data.MySqlClient.MySqlException:“ERROR 1105 (HY000): command 17 not supported now”",True,"TiDB does not support COM_RESET_CONNECTION - var conn = new MySql.Data.MySqlClient.MySqlConnection();
+ using (conn)
+ {
+ conn.Open();
+ }
+ conn = new MySql.Data.MySqlClient.MySqlConnection();
+ using (conn)
+ {
+ conn.Open(); // Crash here!!!
+ }
+
+when close connection then use another one, crash on open method with the exception:
+MySql.Data.MySqlClient.MySqlException:“ERROR 1105 (HY000): command 17 not supported now”",1,tidb does not support com reset connection var conn new mysql data mysqlclient mysqlconnection using conn conn open conn new mysql data mysqlclient mysqlconnection using conn conn open crash here when close connection then use another one crash on open method with the exception mysql data mysqlclient mysqlexception “error command not supported now”,1
+148932,5703563518.0,IssuesEvent,2017-04-18 00:23:49,nesh170/asap-inventory-system,https://api.github.com/repos/nesh170/asap-inventory-system,closed,Edit crontab on production server when we are allowed to ,HIGH PRIORITY,Set cron job to make sure loan reminder emails will be generated,1.0,Edit crontab on production server when we are allowed to - Set cron job to make sure loan reminder emails will be generated,0,edit crontab on production server when we are allowed to set cron job to make sure loan reminder emails will be generated,0
+141367,18976979155.0,IssuesEvent,2021-11-20 06:12:44,go-gitea/gitea,https://api.github.com/repos/go-gitea/gitea,closed,Configurable SSL cipher suite,kind/proposal kind/security,"- Gitea version: 1.10.2
+- Git version: 2.24.0
+- Operating system: Linux
+- Database:
+ - [X] MySQL
+- Can you reproduce the bug at https://try.gitea.io:
+ - [X] Not tested / may run behind a reverse proxy so the results could vary
+
+## Description
+
+```
+'Vulnerable' cipher suites accepted by this service via the TLSv1.0 protocol:
+
+TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
+TLS_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
+
+'Vulnerable' cipher suites accepted by this service via the TLSv1.1 protocol:
+
+TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
+TLS_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
+
+'Vulnerable' cipher suites accepted by this service via the TLSv1.2 protocol:
+
+TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
+TLS_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
+```
+
+https://github.com/go-gitea/gitea/pull/913 added configurable SSH cipher suite, it would be nice to have the same to configure the SSL cipher suite since currently TLSv1.0 and TLSv1.1 are still accepted which shouldn't be used in 2020 anymore: https://blog.qualys.com/ssllabs/2018/11/19/grade-change-for-tls-1-0-and-tls-1-1-protocols
+and it would also be nice to configure excludes for TLSv1.2 to get rid of the weak ones there as well / provide a way to configure them in general.
+",True,"Configurable SSL cipher suite - - Gitea version: 1.10.2
+- Git version: 2.24.0
+- Operating system: Linux
+- Database:
+ - [X] MySQL
+- Can you reproduce the bug at https://try.gitea.io:
+ - [X] Not tested / may run behind a reverse proxy so the results could vary
+
+## Description
+
+```
+'Vulnerable' cipher suites accepted by this service via the TLSv1.0 protocol:
+
+TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
+TLS_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
+
+'Vulnerable' cipher suites accepted by this service via the TLSv1.1 protocol:
+
+TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
+TLS_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
+
+'Vulnerable' cipher suites accepted by this service via the TLSv1.2 protocol:
+
+TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
+TLS_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
+```
+
+https://github.com/go-gitea/gitea/pull/913 added configurable SSH cipher suite, it would be nice to have the same to configure the SSL cipher suite since currently TLSv1.0 and TLSv1.1 are still accepted which shouldn't be used in 2020 anymore: https://blog.qualys.com/ssllabs/2018/11/19/grade-change-for-tls-1-0-and-tls-1-1-protocols
+and it would also be nice to configure excludes for TLSv1.2 to get rid of the weak ones there as well / provide a way to configure them in general.
+",0,configurable ssl cipher suite gitea version git version operating system linux database mysql can you reproduce the bug at not tested may run behind a reverse proxy so the results could vary description vulnerable cipher suites accepted by this service via the protocol tls ecdhe rsa with ede cbc sha tls rsa with ede cbc sha vulnerable cipher suites accepted by this service via the protocol tls ecdhe rsa with ede cbc sha tls rsa with ede cbc sha vulnerable cipher suites accepted by this service via the protocol tls ecdhe rsa with ede cbc sha tls rsa with ede cbc sha added configurable ssh cipher suite it would be nice to have the same to configure the ssl cipher suite since currently and are still accepted which shouldn t be used in anymore and it would also be nice to configure excludes for to get rid of the weak ones there as well provide a way to configure them in general ,0
+19548,27140998374.0,IssuesEvent,2023-02-16 16:20:06,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Wrong error message for unknown column in INSERT...SET,type/bug type/compatibility sig/sql-infra severity/minor compatibility-mysql8,"## Bug Report
+
+### 1. Minimal reproduce step (Required)
+
+```sql
+CREATE TABLE t1(id INT PRIMARY KEY);
+INSERT INTO t1 SET c2=123;
+```
+
+### 2. What did you expect to see? (Required)
+
+MySQL 8.0.32 returns this:
+```
+sql> CREATE TABLE t1(id INT PRIMARY KEY);
+Query OK, 0 rows affected (0.0527 sec)
+
+sql> INSERT INTO t1 SET c2=123;
+ERROR: 1054 (42S22): Unknown column 'c2' in 'field list'
+```
+### 3. What did you see instead (Required)
+
+TiDB returns
+```
+sql> CREATE TABLE t1(id INT PRIMARY KEY);
+Query OK, 0 rows affected (0.0111 sec)
+
+sql> INSERT INTO t1 SET c2=123;
+ERROR: 1105 (HY000): Can't find column c2
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+
+```
+sql> SELECT tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v6.7.0-alpha-23-g08f57c7ea-dirty
+Edition: Community
+Git Commit Hash: 08f57c7ead9fb6c45e00b670feb2b1a738676b38
+Git Branch: load_data_colname_mismatch
+UTC Build Time: 2023-02-15 19:47:12
+GoVersion: go1.19.5
+Race Enabled: false
+TiKV Min Version: 6.2.0-alpha
+Check Table Before Drop: false
+Store: unistore
+1 row in set (0.0005 sec)
+```",True,"Wrong error message for unknown column in INSERT...SET - ## Bug Report
+
+### 1. Minimal reproduce step (Required)
+
+```sql
+CREATE TABLE t1(id INT PRIMARY KEY);
+INSERT INTO t1 SET c2=123;
+```
+
+### 2. What did you expect to see? (Required)
+
+MySQL 8.0.32 returns this:
+```
+sql> CREATE TABLE t1(id INT PRIMARY KEY);
+Query OK, 0 rows affected (0.0527 sec)
+
+sql> INSERT INTO t1 SET c2=123;
+ERROR: 1054 (42S22): Unknown column 'c2' in 'field list'
+```
+### 3. What did you see instead (Required)
+
+TiDB returns
+```
+sql> CREATE TABLE t1(id INT PRIMARY KEY);
+Query OK, 0 rows affected (0.0111 sec)
+
+sql> INSERT INTO t1 SET c2=123;
+ERROR: 1105 (HY000): Can't find column c2
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+
+```
+sql> SELECT tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v6.7.0-alpha-23-g08f57c7ea-dirty
+Edition: Community
+Git Commit Hash: 08f57c7ead9fb6c45e00b670feb2b1a738676b38
+Git Branch: load_data_colname_mismatch
+UTC Build Time: 2023-02-15 19:47:12
+GoVersion: go1.19.5
+Race Enabled: false
+TiKV Min Version: 6.2.0-alpha
+Check Table Before Drop: false
+Store: unistore
+1 row in set (0.0005 sec)
+```",1,wrong error message for unknown column in insert set bug report minimal reproduce step required sql create table id int primary key insert into set what did you expect to see required mysql returns this sql create table id int primary key query ok rows affected sec sql insert into set error unknown column in field list what did you see instead required tidb returns sql create table id int primary key query ok rows affected sec sql insert into set error can t find column what is your tidb version required sql select tidb version g row tidb version release version alpha dirty edition community git commit hash git branch load data colname mismatch utc build time goversion race enabled false tikv min version alpha check table before drop false store unistore row in set sec ,1
+3775,6647147343.0,IssuesEvent,2017-09-28 02:01:56,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed," `show variables` statement don't support ""Combination SQL Modes""",compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+1). `show variables` statement don't support ""Combination SQL Modes"".
+2). `show variables` statement don't remove duplicates.
+
+my PR is on the way.
+
+2. What did you expect to see?
+```
+mysql> set sql_mode='ANSI';
+Query OK, 0 rows affected (0.00 sec)
+
+mysql> show variables like 'SQL_MODE';
++---------------+-------------------------------------------------------------+
+| Variable_name | Value |
++---------------+-------------------------------------------------------------+
+| sql_mode | REAL_AS_FLOAT,PIPES_AS_CONCAT,ANSI_QUOTES,IGNORE_SPACE,ANSI |
++---------------+-------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+```
+tidb>set sql_mode='ANSI';
+Query OK, 0 rows affected (3 min 54.46 sec)
+
+tidb>show variables like 'SQL_MODE';
++---------------+-------+
+| Variable_name | Value |
++---------------+-------+
+| sql_mode | ANSI |
++---------------+-------+
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+```
+Release Version: 0.9.0
+Git Commit Hash: 376a7ddbddd0de91153ee36f6b6a434f22578363
+Git Commit Branch: master
+UTC Build Time: 2017-09-21 09:53:01
+```",True," `show variables` statement don't support ""Combination SQL Modes"" - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+1). `show variables` statement don't support ""Combination SQL Modes"".
+2). `show variables` statement don't remove duplicates.
+
+my PR is on the way.
+
+2. What did you expect to see?
+```
+mysql> set sql_mode='ANSI';
+Query OK, 0 rows affected (0.00 sec)
+
+mysql> show variables like 'SQL_MODE';
++---------------+-------------------------------------------------------------+
+| Variable_name | Value |
++---------------+-------------------------------------------------------------+
+| sql_mode | REAL_AS_FLOAT,PIPES_AS_CONCAT,ANSI_QUOTES,IGNORE_SPACE,ANSI |
++---------------+-------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+```
+tidb>set sql_mode='ANSI';
+Query OK, 0 rows affected (3 min 54.46 sec)
+
+tidb>show variables like 'SQL_MODE';
++---------------+-------+
+| Variable_name | Value |
++---------------+-------+
+| sql_mode | ANSI |
++---------------+-------+
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+```
+Release Version: 0.9.0
+Git Commit Hash: 376a7ddbddd0de91153ee36f6b6a434f22578363
+Git Commit Branch: master
+UTC Build Time: 2017-09-21 09:53:01
+```",1, show variables statement don t support combination sql modes please answer these questions before submitting your issue thanks what did you do show variables statement don t support combination sql modes show variables statement don t remove duplicates my pr is on the way what did you expect to see mysql set sql mode ansi query ok rows affected sec mysql show variables like sql mode variable name value sql mode real as float pipes as concat ansi quotes ignore space ansi row in set sec what did you see instead tidb set sql mode ansi query ok rows affected min sec tidb show variables like sql mode variable name value sql mode ansi what version of tidb are you using tidb server v release version git commit hash git commit branch master utc build time ,1
+6169,8571704484.0,IssuesEvent,2018-11-12 05:45:39,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Support NO_AUTO_CREATE_USER sql_mode,component/privilege for new contributors status/TODO type/compatibility,"## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+Currently the sql-mode `NO_AUTO_CREATE_USER` is parsed but ignored. This mode is important, since the MySQL permission model is otherwise vulnerable to spelling errors causing unathenticated users to have admin privileges. Consider the following hypothetical case:
+
+```
+-- A new user joins an organization, and is given read only access
+CREATE USER 'morgantocker' IDENTIFIED BY 'sekret';
+GRANT SELECT ON *.* TO 'morgantocker';
+
+-- Time elapses.
+-- The user is then given admin privileges by the organization:
+GRANT ALL ON *.* TO 'morgantucker';
+
+-- But there was a common spelling error, 'morgantucker' instead of 'morgantocker' !
+-- This leads to a really bad situation, a new user is created with `ALL` and no password!
+```
+
+**Describe the feature you'd like:**
+
+The sql_mode `NO_AUTO_CREATE_USER`, to be enabled by default (next GA) as it is in MySQL.
+
+**Describe alternatives you've considered:**
+
+N/A
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+
+N/A",True,"Support NO_AUTO_CREATE_USER sql_mode - ## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+Currently the sql-mode `NO_AUTO_CREATE_USER` is parsed but ignored. This mode is important, since the MySQL permission model is otherwise vulnerable to spelling errors causing unathenticated users to have admin privileges. Consider the following hypothetical case:
+
+```
+-- A new user joins an organization, and is given read only access
+CREATE USER 'morgantocker' IDENTIFIED BY 'sekret';
+GRANT SELECT ON *.* TO 'morgantocker';
+
+-- Time elapses.
+-- The user is then given admin privileges by the organization:
+GRANT ALL ON *.* TO 'morgantucker';
+
+-- But there was a common spelling error, 'morgantucker' instead of 'morgantocker' !
+-- This leads to a really bad situation, a new user is created with `ALL` and no password!
+```
+
+**Describe the feature you'd like:**
+
+The sql_mode `NO_AUTO_CREATE_USER`, to be enabled by default (next GA) as it is in MySQL.
+
+**Describe alternatives you've considered:**
+
+N/A
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+
+N/A",1,support no auto create user sql mode feature request is your feature request related to a problem please describe currently the sql mode no auto create user is parsed but ignored this mode is important since the mysql permission model is otherwise vulnerable to spelling errors causing unathenticated users to have admin privileges consider the following hypothetical case a new user joins an organization and is given read only access create user morgantocker identified by sekret grant select on to morgantocker time elapses the user is then given admin privileges by the organization grant all on to morgantucker but there was a common spelling error morgantucker instead of morgantocker this leads to a really bad situation a new user is created with all and no password describe the feature you d like the sql mode no auto create user to be enabled by default next ga as it is in mysql describe alternatives you ve considered n a teachability documentation adoption migration strategy n a,1
+6995,9292267154.0,IssuesEvent,2019-03-22 02:17:36,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,ERROR 1105 (HY000): privilege check fail (with GRANT OPTION set),component/privilege type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+user `root`:
+```
+MySQL [test]> CREATE USER test_test_u1@localhost;
+Query OK, 1 row affected (0.009 sec)
+
+MySQL [test]> CREATE DATABASE test_test_db1;
+Query OK, 0 rows affected (0.014 sec)
+
+MySQL [test]> CREATE DATABASE test_test_db2;
+Query OK, 0 rows affected (0.014 sec)
+
+MySQL [test]> GRANT ALL ON test_test_db1.* TO test_test_u1@localhost WITH GRANT OPTION;
+Query OK, 0 rows affected (0.010 sec)
+
+MySQL [test]> CREATE USER test_test_u2@localhost;
+Query OK, 1 row affected (0.007 sec)
+
+MySQL [test]> use mysql;
+Reading table information for completion of table and column names
+You can turn off this feature to get a quicker startup with -A
+
+Database changed
+MySQL [mysql]> select db;
+ERROR 1054 (42S22): Unknown column 'db' in 'field list'
+MySQL [mysql]> select * from db;
++-----------+---------------+--------------+-------------+-------------+-------------+-------------+-------------+-----------+------------+-----------------+------------+------------+-----------------------+------------------+------------------+----------------+---------------------+--------------------+--------------+------------+--------------+
+| Host | DB | User | Select_priv | Insert_priv | Update_priv | Delete_priv | Create_priv | Drop_priv | Grant_priv | References_priv | Index_priv | Alter_priv | Create_tmp_table_priv | Lock_tables_priv | Create_view_priv | Show_view_priv | Create_routine_priv | Alter_routine_priv | Execute_priv | Event_priv | Trigger_priv |
++-----------+---------------+--------------+-------------+-------------+-------------+-------------+-------------+-----------+------------+-----------------+------------+------------+-----------------------+------------------+------------------+----------------+---------------------+--------------------+--------------+------------+--------------+
+| localhost | test_test_db1 | test_test_u1 | Y | Y | Y | Y | Y | Y | Y | N | Y | Y | N | N | Y | Y | N | N | Y | N | N |
++-----------+---------------+--------------+-------------+-------------+-------------+-------------+-------------+-----------+------------+-----------------+------------+------------+-----------------------+------------------+------------------+----------------+---------------------+--------------------+--------------+------------+--------------+
+2 rows in set (0.002 sec)
+
+MySQL [mysql]>
+```
+
+user `test_test_u1`
+
+```
+MySQL [(none)]> use test_test_db1
+Database changed
+MySQL [test_test_db1]> GRANT SELECT ON v1 TO test_test_u2@localhost;
+ERROR 1105 (HY000): privilege check fail
+MySQL [test_test_db1]> GRANT SELECT ON t2 TO test_test_u2@localhost;
+ERROR 1105 (HY000): privilege check fail
+MySQL [test_test_db1]>
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+`Server version: 5.7.25-TiDB-v3.0.0-beta-231-g20463d6da-dirty`",True,"ERROR 1105 (HY000): privilege check fail (with GRANT OPTION set) - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+user `root`:
+```
+MySQL [test]> CREATE USER test_test_u1@localhost;
+Query OK, 1 row affected (0.009 sec)
+
+MySQL [test]> CREATE DATABASE test_test_db1;
+Query OK, 0 rows affected (0.014 sec)
+
+MySQL [test]> CREATE DATABASE test_test_db2;
+Query OK, 0 rows affected (0.014 sec)
+
+MySQL [test]> GRANT ALL ON test_test_db1.* TO test_test_u1@localhost WITH GRANT OPTION;
+Query OK, 0 rows affected (0.010 sec)
+
+MySQL [test]> CREATE USER test_test_u2@localhost;
+Query OK, 1 row affected (0.007 sec)
+
+MySQL [test]> use mysql;
+Reading table information for completion of table and column names
+You can turn off this feature to get a quicker startup with -A
+
+Database changed
+MySQL [mysql]> select db;
+ERROR 1054 (42S22): Unknown column 'db' in 'field list'
+MySQL [mysql]> select * from db;
++-----------+---------------+--------------+-------------+-------------+-------------+-------------+-------------+-----------+------------+-----------------+------------+------------+-----------------------+------------------+------------------+----------------+---------------------+--------------------+--------------+------------+--------------+
+| Host | DB | User | Select_priv | Insert_priv | Update_priv | Delete_priv | Create_priv | Drop_priv | Grant_priv | References_priv | Index_priv | Alter_priv | Create_tmp_table_priv | Lock_tables_priv | Create_view_priv | Show_view_priv | Create_routine_priv | Alter_routine_priv | Execute_priv | Event_priv | Trigger_priv |
++-----------+---------------+--------------+-------------+-------------+-------------+-------------+-------------+-----------+------------+-----------------+------------+------------+-----------------------+------------------+------------------+----------------+---------------------+--------------------+--------------+------------+--------------+
+| localhost | test_test_db1 | test_test_u1 | Y | Y | Y | Y | Y | Y | Y | N | Y | Y | N | N | Y | Y | N | N | Y | N | N |
++-----------+---------------+--------------+-------------+-------------+-------------+-------------+-------------+-----------+------------+-----------------+------------+------------+-----------------------+------------------+------------------+----------------+---------------------+--------------------+--------------+------------+--------------+
+2 rows in set (0.002 sec)
+
+MySQL [mysql]>
+```
+
+user `test_test_u1`
+
+```
+MySQL [(none)]> use test_test_db1
+Database changed
+MySQL [test_test_db1]> GRANT SELECT ON v1 TO test_test_u2@localhost;
+ERROR 1105 (HY000): privilege check fail
+MySQL [test_test_db1]> GRANT SELECT ON t2 TO test_test_u2@localhost;
+ERROR 1105 (HY000): privilege check fail
+MySQL [test_test_db1]>
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+`Server version: 5.7.25-TiDB-v3.0.0-beta-231-g20463d6da-dirty`",1,error privilege check fail with grant option set bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error user root mysql create user test test localhost query ok row affected sec mysql create database test test query ok rows affected sec mysql create database test test query ok rows affected sec mysql grant all on test test to test test localhost with grant option query ok rows affected sec mysql create user test test localhost query ok row affected sec mysql use mysql reading table information for completion of table and column names you can turn off this feature to get a quicker startup with a database changed mysql select db error unknown column db in field list mysql select from db host db user select priv insert priv update priv delete priv create priv drop priv grant priv references priv index priv alter priv create tmp table priv lock tables priv create view priv show view priv create routine priv alter routine priv execute priv event priv trigger priv localhost test test test test y y y y y y y n y y n n y y n n y n n rows in set sec mysql user test test mysql use test test database changed mysql grant select on to test test localhost error privilege check fail mysql grant select on to test test localhost error privilege check fail mysql what version of tidb are you using tidb server v or run select tidb version on tidb server version tidb beta dirty ,1
+132746,5192219237.0,IssuesEvent,2017-01-22 05:49:57,cs-club-appdev/ac-apiserver,https://api.github.com/repos/cs-club-appdev/ac-apiserver,closed,"Create User, Router, and Controller",priority:high type:feature,"# User
+
+## Model
+| Attribute | Type |
+|-----------|-------|
+| organization | ObjectId Reference |
+| email | string |
+| password | string |
+| role | enum (user or admin) |
+| token | string |
+
+Do not forget to add the StatPlugin to the schema.
+
+## Router and Controller
+Create a generic ResourceController and resource route for Users.",1.0,"Create User, Router, and Controller - # User
+
+## Model
+| Attribute | Type |
+|-----------|-------|
+| organization | ObjectId Reference |
+| email | string |
+| password | string |
+| role | enum (user or admin) |
+| token | string |
+
+Do not forget to add the StatPlugin to the schema.
+
+## Router and Controller
+Create a generic ResourceController and resource route for Users.",0,create user router and controller user model attribute type organization objectid reference email string password string role enum user or admin token string do not forget to add the statplugin to the schema router and controller create a generic resourcecontroller and resource route for users ,0
+6463,8755267787.0,IssuesEvent,2018-12-14 14:23:57,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,wait_timeout used instead of interactive_timeout,help wanted type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+Currently `wait_timeout` is also applicable for interactive sessions (i.e. mysql cli tool). The MySQL compatible behavior is as follows:
+
+2. What did you expect to see?
+```
+session1> set global wait_timeout = 5;
+session1> set global interactive_timeout = 100;
+..
+session1> show global variables like 'wait_timeout';
++---------------+-------+
+| Variable_name | Value |
++---------------+-------+
+| wait_timeout | 5 |
++---------------+-------+
+1 row in set (0.00 sec)
+
+session1> show global variables like 'interactive_timeout';
++---------------------+-------+
+| Variable_name | Value |
++---------------------+-------+
+| interactive_timeout | 100 |
++---------------------+-------+
+1 row in set (0.01 sec)
+```
+Then control +c and start a new session:
+```
+session2> show variables like 'wait_timeout';
++---------------+-------+
+| Variable_name | Value |
++---------------+-------+
+| wait_timeout | 100 |
++---------------+-------+
+1 row in set (0.00 sec)
+
+session2> show variables like 'interactive_timeout';
++---------------------+-------+
+| Variable_name | Value |
++---------------------+-------+
+| interactive_timeout | 100 |
++---------------------+-------+
+1 row in set (0.01 sec)
+```
+Because the session sets the interactive bit, the `interactive_timeout` is actually copied over the `wait_timeout`. The global `wait_timeout` is still 5:
+```
+session2> show global variables like 'wait_timeout';
++---------------+-------+
+| Variable_name | Value |
++---------------+-------+
+| wait_timeout | 5 |
++---------------+-------+
+1 row in set (0.00 sec)
+```
+3. What did you see instead?
+
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+",True,"wait_timeout used instead of interactive_timeout - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+Currently `wait_timeout` is also applicable for interactive sessions (i.e. mysql cli tool). The MySQL compatible behavior is as follows:
+
+2. What did you expect to see?
+```
+session1> set global wait_timeout = 5;
+session1> set global interactive_timeout = 100;
+..
+session1> show global variables like 'wait_timeout';
++---------------+-------+
+| Variable_name | Value |
++---------------+-------+
+| wait_timeout | 5 |
++---------------+-------+
+1 row in set (0.00 sec)
+
+session1> show global variables like 'interactive_timeout';
++---------------------+-------+
+| Variable_name | Value |
++---------------------+-------+
+| interactive_timeout | 100 |
++---------------------+-------+
+1 row in set (0.01 sec)
+```
+Then control +c and start a new session:
+```
+session2> show variables like 'wait_timeout';
++---------------+-------+
+| Variable_name | Value |
++---------------+-------+
+| wait_timeout | 100 |
++---------------+-------+
+1 row in set (0.00 sec)
+
+session2> show variables like 'interactive_timeout';
++---------------------+-------+
+| Variable_name | Value |
++---------------------+-------+
+| interactive_timeout | 100 |
++---------------------+-------+
+1 row in set (0.01 sec)
+```
+Because the session sets the interactive bit, the `interactive_timeout` is actually copied over the `wait_timeout`. The global `wait_timeout` is still 5:
+```
+session2> show global variables like 'wait_timeout';
++---------------+-------+
+| Variable_name | Value |
++---------------+-------+
+| wait_timeout | 5 |
++---------------+-------+
+1 row in set (0.00 sec)
+```
+3. What did you see instead?
+
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+",1,wait timeout used instead of interactive timeout bug report please answer these questions before submitting your issue thanks what did you do currently wait timeout is also applicable for interactive sessions i e mysql cli tool the mysql compatible behavior is as follows what did you expect to see set global wait timeout set global interactive timeout show global variables like wait timeout variable name value wait timeout row in set sec show global variables like interactive timeout variable name value interactive timeout row in set sec then control c and start a new session show variables like wait timeout variable name value wait timeout row in set sec show variables like interactive timeout variable name value interactive timeout row in set sec because the session sets the interactive bit the interactive timeout is actually copied over the wait timeout the global wait timeout is still show global variables like wait timeout variable name value wait timeout row in set sec what did you see instead what version of tidb are you using tidb server v or run select tidb version on tidb ,1
+18246,25237672188.0,IssuesEvent,2022-11-15 03:13:58,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,"`bit`, `char` type column metadata is not compatible with mysql.",type/bug type/compatibility sig/sql-infra severity/moderate,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```
+CREATE TABLE `PK_MULTI_COL_527_tmp` (
+ `COL1` char(10) COLLATE utf8_general_ci NOT NULL,
+ `COL3` bit(1) NOT NULL,
+ PRIMARY KEY (`COL1`(5),`COL3`) /*T![clustered_index] NONCLUSTERED */
+) ENGINE=InnoDB DEFAULT CHARSET=utf8 COLLATE=utf8_general_ci;
+
+select table_catalog table_catalog,table_name table_name,column_name column_name,ordinal_position ordinal_position,column_default column_default,is_nullable is_nullable,data_type data_type,character_maximum_length character_maximum_length,character_octet_length character_octet_length,numeric_precision numeric_precision,numeric_scale numeric_scale,datetime_precision datetime_precision,character_set_name character_set_name,collation_name collation_name,column_type column_type,column_key column_key,extra extra,privileges privileges,column_comment column_comment,generation_expression generation_expression from information_schema.columns where table_schema=(select database()) and table_name=""PK_MULTI_COL_527_tmp"" order by ordinal_position;
+
+
+```
+### 2. What did you expect to see? (Required)
+
+```
++---------------+----------------------+-------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-----------------+------------+-------+---------------------------------+----------------+-----------------------+
+| table_catalog | table_name | column_name | ordinal_position | column_default | is_nullable | data_type | character_maximum_length | character_octet_length | numeric_precision | numeric_scale | datetime_precision | character_set_name | collation_name | column_type | column_key | extra | privileges | column_comment | generation_expression |
++---------------+----------------------+-------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-----------------+------------+-------+---------------------------------+----------------+-----------------------+
+| def | PK_MULTI_COL_527_tmp | COL1 | 1 | NULL | NO | char | 10 | 30 | NULL | NULL | NULL | utf8 | utf8_general_ci | char(10) | PRI | | select,insert,update,references | | |
+| def | PK_MULTI_COL_527_tmp | COL3 | 2 | NULL | NO | bit | NULL | NULL | 1 | NULL | NULL | NULL | NULL | bit(1) | PRI | | select,insert,update,references | | |
++---------------+----------------------+-------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-----------------+------------+-------+---------------------------------+----------------+-----------------------+
+```
+
+### 3. What did you see instead (Required)
+
+```
++---------------+----------------------+-------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-----------------+------------+-------+---------------------------------+----------------+-----------------------+
+| table_catalog | table_name | column_name | ordinal_position | column_default | is_nullable | data_type | character_maximum_length | character_octet_length | numeric_precision | numeric_scale | datetime_precision | character_set_name | collation_name | column_type | column_key | extra | privileges | column_comment | generation_expression |
++---------------+----------------------+-------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-----------------+------------+-------+---------------------------------+----------------+-----------------------+
+| def | PK_MULTI_COL_527_tmp | COL1 | 1 | NULL | NO | char | 10 | 10 | NULL | NULL | NULL | utf8 | utf8_general_ci | char(10) | PRI | | select,insert,update,references | | |
+| def | PK_MULTI_COL_527_tmp | COL3 | 2 | NULL | NO | bit | NULL | NULL | 1 | 0 | NULL | NULL | NULL | bit(1) unsigned | PRI | | select,insert,update,references | | |
++---------------+----------------------+-------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-----------------+------------+-------+---------------------------------+----------------+-----------------------+
+```
+### 4. What is your TiDB version? (Required)
+
+```
+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v5.1.0-20210611
+Edition: Community
+Git Commit Hash: 29bfbb28437609d0a524b7b84e6920dc765978c7
+Git Branch: heads/refs/tags/v5.1.0-20210611
+UTC Build Time: 2021-06-11 07:52:09
+GoVersion: go1.16.4
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+
+```
+",True,"`bit`, `char` type column metadata is not compatible with mysql. - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```
+CREATE TABLE `PK_MULTI_COL_527_tmp` (
+ `COL1` char(10) COLLATE utf8_general_ci NOT NULL,
+ `COL3` bit(1) NOT NULL,
+ PRIMARY KEY (`COL1`(5),`COL3`) /*T![clustered_index] NONCLUSTERED */
+) ENGINE=InnoDB DEFAULT CHARSET=utf8 COLLATE=utf8_general_ci;
+
+select table_catalog table_catalog,table_name table_name,column_name column_name,ordinal_position ordinal_position,column_default column_default,is_nullable is_nullable,data_type data_type,character_maximum_length character_maximum_length,character_octet_length character_octet_length,numeric_precision numeric_precision,numeric_scale numeric_scale,datetime_precision datetime_precision,character_set_name character_set_name,collation_name collation_name,column_type column_type,column_key column_key,extra extra,privileges privileges,column_comment column_comment,generation_expression generation_expression from information_schema.columns where table_schema=(select database()) and table_name=""PK_MULTI_COL_527_tmp"" order by ordinal_position;
+
+
+```
+### 2. What did you expect to see? (Required)
+
+```
++---------------+----------------------+-------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-----------------+------------+-------+---------------------------------+----------------+-----------------------+
+| table_catalog | table_name | column_name | ordinal_position | column_default | is_nullable | data_type | character_maximum_length | character_octet_length | numeric_precision | numeric_scale | datetime_precision | character_set_name | collation_name | column_type | column_key | extra | privileges | column_comment | generation_expression |
++---------------+----------------------+-------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-----------------+------------+-------+---------------------------------+----------------+-----------------------+
+| def | PK_MULTI_COL_527_tmp | COL1 | 1 | NULL | NO | char | 10 | 30 | NULL | NULL | NULL | utf8 | utf8_general_ci | char(10) | PRI | | select,insert,update,references | | |
+| def | PK_MULTI_COL_527_tmp | COL3 | 2 | NULL | NO | bit | NULL | NULL | 1 | NULL | NULL | NULL | NULL | bit(1) | PRI | | select,insert,update,references | | |
++---------------+----------------------+-------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-----------------+------------+-------+---------------------------------+----------------+-----------------------+
+```
+
+### 3. What did you see instead (Required)
+
+```
++---------------+----------------------+-------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-----------------+------------+-------+---------------------------------+----------------+-----------------------+
+| table_catalog | table_name | column_name | ordinal_position | column_default | is_nullable | data_type | character_maximum_length | character_octet_length | numeric_precision | numeric_scale | datetime_precision | character_set_name | collation_name | column_type | column_key | extra | privileges | column_comment | generation_expression |
++---------------+----------------------+-------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-----------------+------------+-------+---------------------------------+----------------+-----------------------+
+| def | PK_MULTI_COL_527_tmp | COL1 | 1 | NULL | NO | char | 10 | 10 | NULL | NULL | NULL | utf8 | utf8_general_ci | char(10) | PRI | | select,insert,update,references | | |
+| def | PK_MULTI_COL_527_tmp | COL3 | 2 | NULL | NO | bit | NULL | NULL | 1 | 0 | NULL | NULL | NULL | bit(1) unsigned | PRI | | select,insert,update,references | | |
++---------------+----------------------+-------------+------------------+----------------+-------------+-----------+--------------------------+------------------------+-------------------+---------------+--------------------+--------------------+-----------------+-----------------+------------+-------+---------------------------------+----------------+-----------------------+
+```
+### 4. What is your TiDB version? (Required)
+
+```
+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v5.1.0-20210611
+Edition: Community
+Git Commit Hash: 29bfbb28437609d0a524b7b84e6920dc765978c7
+Git Branch: heads/refs/tags/v5.1.0-20210611
+UTC Build Time: 2021-06-11 07:52:09
+GoVersion: go1.16.4
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+
+```
+",1, bit char type column metadata is not compatible with mysql bug report please answer these questions before submitting your issue thanks minimal reproduce step required create table pk multi col tmp char collate general ci not null bit not null primary key t nonclustered engine innodb default charset collate general ci select table catalog table catalog table name table name column name column name ordinal position ordinal position column default column default is nullable is nullable data type data type character maximum length character maximum length character octet length character octet length numeric precision numeric precision numeric scale numeric scale datetime precision datetime precision character set name character set name collation name collation name column type column type column key column key extra extra privileges privileges column comment column comment generation expression generation expression from information schema columns where table schema select database and table name pk multi col tmp order by ordinal position what did you expect to see required table catalog table name column name ordinal position column default is nullable data type character maximum length character octet length numeric precision numeric scale datetime precision character set name collation name column type column key extra privileges column comment generation expression def pk multi col tmp null no char null null null general ci char pri select insert update references def pk multi col tmp null no bit null null null null null null bit pri select insert update references what did you see instead required table catalog table name column name ordinal position column default is nullable data type character maximum length character octet length numeric precision numeric scale datetime precision character set name collation name column type column key extra privileges column comment generation expression def pk multi col tmp null no char null null null general ci char pri select insert update references def pk multi col tmp null no bit null null null null null bit unsigned pri select insert update references what is your tidb version required tidb version release version edition community git commit hash git branch heads refs tags utc build time goversion race enabled false tikv min version check table before drop false ,1
+192746,6876423169.0,IssuesEvent,2017-11-20 00:23:20,OpenNebula/one,https://api.github.com/repos/OpenNebula/one,opened,Add paravirtualized End-of-Interrupt indication to KVM,Category: Drivers - VM Priority: High Status: Assigned Tracker: Backlog,"---
-```
-mysql> CREATE TABLE t1 (id int);
-Query OK, 0 rows affected (0.01 sec)
-mysql> INSERT INTO t1(`id`) VALUES(3);
-Query OK, 1 row affected (0.00 sec)
+Author Name: **Javi Fontan** (Javi Fontan)
+Original Redmine Issue: 2717, https://dev.opennebula.org/issues/2717
+Original Date: 2014-02-07
-mysql> CREATE TABLE t2 (title text);
-Query OK, 0 rows affected (0.00 sec)
-mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
-Query OK, 1 row affected (0.00 sec)
+---
-mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-+------+-------+
-| id | title |
-+------+-------+
-| 3 | 3.0.1 |
-+------+-------+
-1 row in set (0.01 sec)
+From an e-mail by Shankhadeep Shome (http://lists.opennebula.org/pipermail/users-opennebula.org/2014-February/026514.html):
+
+> Please consider exposing the para-virtualized end of interrupts flag to the vm configuration markup
+>
+> Expose the KVM end of Interrupt feature to improve KVM vm performance
+>
+> Instead of the standard enable for newer linux kernels like Fedora 18/RHEL 6.4+/Ubuntu 13.04 and up on KVM
+>
+> Here is some more info regarding this feature..
+>
+> https://access.redhat.com/site/documentation/en-US/Red_Hat_Enterprise_Linux/6/html/6.4_Release_Notes/virtualization.html
-mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-+----+-------------+-------+------------+------+---------------+------+---------+------+------+----------+----------------------------------------------------+
-| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
-+----+-------------+-------+------------+------+---------------+------+---------+------+------+----------+----------------------------------------------------+
-| 1 | SIMPLE | t1 | NULL | ALL | NULL | NULL | NULL | NULL | 1 | 100.00 | NULL |
-| 1 | SIMPLE | t2 | NULL | ALL | NULL | NULL | NULL | NULL | 1 | 100.00 | Using where; Using join buffer (Block Nested Loop) |
-+----+-------------+-------+------------+------+---------------+------+---------+------+------+----------+----------------------------------------------------+
-2 rows in set, 1 warning (0.00 sec)
-```
-* In TiDB
+",1.0,"Add paravirtualized End-of-Interrupt indication to KVM - ---
-```
-mysql> CREATE TABLE t1 (id int);
-Query OK, 0 rows affected (0.08 sec)
-
-mysql> INSERT INTO t1(`id`) VALUES(3);
-Query OK, 1 row affected (0.01 sec)
-
-mysql> CREATE TABLE t2 (title text);
-Query OK, 0 rows affected (0.08 sec)
-
-mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
-Query OK, 1 row affected (0.02 sec)
-
-mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-+------+-------+
-| id | title |
-+------+-------+
-| 3 | 3.0.1 |
-+------+-------+
-1 row in set, 1 warning (0.00 sec)
-
-mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-+----------------------------+----------+-----------+-----------------------------------------------------------------+
-| id | count | task | operator info |
-+----------------------------+----------+-----------+-----------------------------------------------------------------+
-| Projection_8 | 12500.00 | root | Column#1, Column#3 |
-| └─HashLeftJoin_9 | 12500.00 | root | inner join, inner:Projection_14, equal:[eq(Column#7, Column#8)] |
-| ├─Projection_11 | 10000.00 | root | Column#1, cast(Column#1) |
-| │ └─TableReader_13 | 10000.00 | root | data:TableScan_12 |
-| │ └─TableScan_12 | 10000.00 | cop[tikv] | table:t1, range:[-inf,+inf], keep order:false, stats:pseudo |
-| └─Projection_14 | 10000.00 | root | Column#3, cast(Column#3) |
-| └─TableReader_16 | 10000.00 | root | data:TableScan_15 |
-| └─TableScan_15 | 10000.00 | cop[tikv] | table:t2, range:[-inf,+inf], keep order:false, stats:pseudo |
-+----------------------------+----------+-----------+-----------------------------------------------------------------+
-8 rows in set (0.00 sec)
-```",True,"join on int primary key and text is not the same with MySQL - ## Bug Report
-
-Please answer these questions before submitting your issue. Thanks!
-
-1. What did you do?
-```
-CREATE TABLE t1 (id int(11) NOT NULL AUTO_INCREMENT, PRIMARY KEY (`id`));
-INSERT INTO t1(`id`) VALUES(3);
-CREATE TABLE t2 (title text);
-INSERT INTO t2(`title`) VALUES(""3.0.1"");
-SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-```
+Author Name: **Javi Fontan** (Javi Fontan)
+Original Redmine Issue: 2717, https://dev.opennebula.org/issues/2717
+Original Date: 2014-02-07
-2. What did you expect to see?
-* MySQL 8.0
+---
-```
-mysql> CREATE TABLE t1 (id int(11) NOT NULL AUTO_INCREMENT, PRIMARY KEY (`id`));
-Query OK, 0 rows affected, 1 warning (0.01 sec)
+From an e-mail by Shankhadeep Shome (http://lists.opennebula.org/pipermail/users-opennebula.org/2014-February/026514.html):
+
+> Please consider exposing the para-virtualized end of interrupts flag to the vm configuration markup
+>
+> Expose the KVM end of Interrupt feature to improve KVM vm performance
+>
+> Instead of the standard enable for newer linux kernels like Fedora 18/RHEL 6.4+/Ubuntu 13.04 and up on KVM
+>
+> Here is some more info regarding this feature..
+>
+> https://access.redhat.com/site/documentation/en-US/Red_Hat_Enterprise_Linux/6/html/6.4_Release_Notes/virtualization.html
-mysql> INSERT INTO t1(`id`) VALUES(3);
-Query OK, 1 row affected (0.00 sec)
-mysql> CREATE TABLE t2 (title text);
-Query OK, 0 rows affected (0.00 sec)
+",0,add paravirtualized end of interrupt indication to kvm author name javi fontan javi fontan original redmine issue original date from an e mail by shankhadeep shome please consider exposing the para virtualized end of interrupts flag to the vm configuration markup expose the kvm end of interrupt feature to improve kvm vm performance instead of the standard enable for newer linux kernels like fedora rhel ubuntu and up on kvm here is some more info regarding this feature ,0
+5543,8015047121.0,IssuesEvent,2018-07-25 08:47:24,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,"need to handle ""ER_WARN_ALLOWED_PACKET_OVERFLOWED"" for some string functions",component/expression help wanted type/compatibility,"Take this as an example:
+```sql
+select rpad('hello', 18446744073709551617, '1');
+```
+
+In MySQL, the result is NULL and a warning about **""Result of rpad() was larger than max_allowed_packet""** is returned:
+```sql
+MySQL(localhost:3306) > select rpad('hello', 18446744073709551617, '1');
++------------------------------------------+
+| rpad('hello', 18446744073709551617, '1') |
++------------------------------------------+
+| NULL |
++------------------------------------------+
+1 row in set, 3 warnings (0.01 sec)
+
+MySQL(localhost:3306) > show warnings;
++---------+------+---------------------------------------------------------------------------+
+| Level | Code | Message |
++---------+------+---------------------------------------------------------------------------+
+| Warning | 1292 | Truncated incorrect DECIMAL value: '18446744073709551617' |
+| Warning | 1292 | Truncated incorrect DECIMAL value: '18446744073709551617' |
+| Warning | 1301 | Result of rpad() was larger than max_allowed_packet (4194304) - truncated |
++---------+------+---------------------------------------------------------------------------+
+3 rows in set (0.00 sec)
+
+MySQL(localhost:3306) > select version();
++-----------+
+| version() |
++-----------+
+| 5.7.22 |
++-----------+
+1 row in set (0.00 sec)
+```
+
+In TiDB, this query results in a ""lost connection"" and the panic is **""runtime error: makeslice: len out of range""**, and the panic stack is:
+```
+2018/07/25 16:33:10.027 conn.go:427: [error] lastCmd select rpad('hello', 18446744073709551617, '1'), runtime error: makeslice: len out of range, goroutine 743 [running]:
+github.com/pingcap/tidb/server.(*clientConn).Run.func1(0xc43bbea000, 0xc4203bddff)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/server/conn.go:425 +0x10e
+panic(0x1d54500, 0x2024180)
+ /Users/jianzhang.zj/opt/goroot/src/runtime/panic.go:505 +0x229
+strings.Repeat(0xc43c64253d, 0x1, 0x7ffffffffffffffb, 0xc4203bca18, 0x1)
+ /Users/jianzhang.zj/opt/goroot/src/strings/strings.go:543 +0x83
+github.com/pingcap/tidb/expression.(*builtinRpadSig).evalString(0xc422664f40, 0x0, 0x0, 0x0, 0x17f2c44, 0xc422664f40, 0x205eb00, 0xc43e274000)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/expression/builtin_string.go:1959 +0x38c
+github.com/pingcap/tidb/expression.(*ScalarFunction).EvalString(0xc43d1e0aa0, 0x205eb00, 0xc43e274000, 0x0, 0x0, 0x0, 0x0, 0x0, 0xc4203bcca8, 0x1741c17)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/expression/scalar_function.go:216 +0x4c
+github.com/pingcap/tidb/expression.(*ScalarFunction).Eval(0xc43d1e0aa0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, ...)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/expression/scalar_function.go:188 +0x481
+github.com/pingcap/tidb/expression.foldConstant(0x205df00, 0xc43d1e0aa0, 0x1e18b60, 0xc43c642501, 0xc43d1e0aa0)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/expression/constant_fold.go:102 +0x5e2
+github.com/pingcap/tidb/expression.FoldConstant(0x205df00, 0xc43d1e0aa0, 0xc43c642518, 0x4)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/expression/constant_fold.go:33 +0x35
+github.com/pingcap/tidb/expression.NewFunction(0x205eb00, 0xc43e274000, 0xc43c642518, 0x4, 0xc43c6406c0, 0xc422664ec0, 0x3, 0x4, 0x1e18aa0, 0xc422664ec0, ...)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/expression/scalar_function.go:98 +0x341
+github.com/pingcap/tidb/plan.(*expressionRewriter).funcCallToExpression(0xc421a80d00, 0xc43c8e87e0)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/expression_rewriter.go:1198 +0x174
+github.com/pingcap/tidb/plan.(*expressionRewriter).Leave(0xc421a80d00, 0x20313e0, 0xc43c8e87e0, 0x2048e40, 0xc438357e40, 0x1aa0b01)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/expression_rewriter.go:746 +0x86a
+github.com/pingcap/tidb/ast.(*FuncCallExpr).Accept(0xc43c8e87e0, 0x202cae0, 0xc421a80d00, 0x1a2fd5c, 0x205e800, 0xc421a80c80)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/ast/functions.go:363 +0x1bf
+github.com/pingcap/tidb/plan.(*planBuilder).rewriteExprNode(0xc43b7e3e00, 0xc421a80d00, 0x2048740, 0xc43c8e87e0, 0xc4203bd301, 0x1010559, 0xc422664e40, 0x40, 0x38, 0x1dedf60, ...)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/expression_rewriter.go:132 +0x54
+github.com/pingcap/tidb/plan.(*planBuilder).rewriteWithPreprocess(0xc43b7e3e00, 0x2048740, 0xc43c8e87e0, 0x205e800, 0xc421a80c80, 0x0, 0x1eba401, 0x0, 0x0, 0x0, ...)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/expression_rewriter.go:104 +0x12b
+github.com/pingcap/tidb/plan.(*planBuilder).rewrite(0xc43b7e3e00, 0x2048740, 0xc43c8e87e0, 0x205e800, 0xc421a80c80, 0x0, 0x1, 0x0, 0x0, 0x0, ...)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/expression_rewriter.go:80 +0x96
+github.com/pingcap/tidb/plan.(*planBuilder).buildProjection(0xc43b7e3e00, 0x205e800, 0xc421a80c80, 0xc42402e6e0, 0x1, 0x1, 0x0, 0x1, 0x1, 0x1e17360)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/logical_plan_builder.go:572 +0x220
+github.com/pingcap/tidb/plan.(*planBuilder).buildSelect(0xc43b7e3e00, 0xc4210bb4a0, 0x0, 0x0)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/logical_plan_builder.go:1664 +0x309
+github.com/pingcap/tidb/plan.(*planBuilder).build(0xc43b7e3e00, 0x2031ca0, 0xc4210bb4a0, 0xc421a293b0, 0x205eb00)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/planbuilder.go:155 +0x603
+github.com/pingcap/tidb/plan.Optimize(0x205eb00, 0xc43e274000, 0x2031ca0, 0xc4210bb4a0, 0x2048fc0, 0xc421a293b0, 0x2a7bd00, 0x0, 0x0, 0x2f)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/optimize
+2018/07/25 16:33:10.027 server.go:316: [info] con:1 close connection
+```
+
+What we need to do is **not** allocate a buffer larger than **""max_allowed_packet""** for these string functions:
+- [ ] to_base64
+- [ ] from_base64
+- [ ] concat
+- [ ] concat_ws
+- [ ] replace
+- [ ] insert
+- [ ] repeat
+- [ ] space
+- [ ] rpad
+- [ ] lpad
+- [ ] cast
+- [ ] export_set
+- [ ] quote
+
+All the above functions implemented in MySQL are located in the **""sql/item_strfunc.cc""** file, you can grep the function name to see specific implementations.
+
+All the above functions can be found in TiDB from the source file **""expression/builtin.go""**.",True,"need to handle ""ER_WARN_ALLOWED_PACKET_OVERFLOWED"" for some string functions - Take this as an example:
+```sql
+select rpad('hello', 18446744073709551617, '1');
+```
+
+In MySQL, the result is NULL and a warning about **""Result of rpad() was larger than max_allowed_packet""** is returned:
+```sql
+MySQL(localhost:3306) > select rpad('hello', 18446744073709551617, '1');
++------------------------------------------+
+| rpad('hello', 18446744073709551617, '1') |
++------------------------------------------+
+| NULL |
++------------------------------------------+
+1 row in set, 3 warnings (0.01 sec)
+
+MySQL(localhost:3306) > show warnings;
++---------+------+---------------------------------------------------------------------------+
+| Level | Code | Message |
++---------+------+---------------------------------------------------------------------------+
+| Warning | 1292 | Truncated incorrect DECIMAL value: '18446744073709551617' |
+| Warning | 1292 | Truncated incorrect DECIMAL value: '18446744073709551617' |
+| Warning | 1301 | Result of rpad() was larger than max_allowed_packet (4194304) - truncated |
++---------+------+---------------------------------------------------------------------------+
+3 rows in set (0.00 sec)
+
+MySQL(localhost:3306) > select version();
++-----------+
+| version() |
++-----------+
+| 5.7.22 |
++-----------+
+1 row in set (0.00 sec)
+```
+
+In TiDB, this query results in a ""lost connection"" and the panic is **""runtime error: makeslice: len out of range""**, and the panic stack is:
+```
+2018/07/25 16:33:10.027 conn.go:427: [error] lastCmd select rpad('hello', 18446744073709551617, '1'), runtime error: makeslice: len out of range, goroutine 743 [running]:
+github.com/pingcap/tidb/server.(*clientConn).Run.func1(0xc43bbea000, 0xc4203bddff)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/server/conn.go:425 +0x10e
+panic(0x1d54500, 0x2024180)
+ /Users/jianzhang.zj/opt/goroot/src/runtime/panic.go:505 +0x229
+strings.Repeat(0xc43c64253d, 0x1, 0x7ffffffffffffffb, 0xc4203bca18, 0x1)
+ /Users/jianzhang.zj/opt/goroot/src/strings/strings.go:543 +0x83
+github.com/pingcap/tidb/expression.(*builtinRpadSig).evalString(0xc422664f40, 0x0, 0x0, 0x0, 0x17f2c44, 0xc422664f40, 0x205eb00, 0xc43e274000)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/expression/builtin_string.go:1959 +0x38c
+github.com/pingcap/tidb/expression.(*ScalarFunction).EvalString(0xc43d1e0aa0, 0x205eb00, 0xc43e274000, 0x0, 0x0, 0x0, 0x0, 0x0, 0xc4203bcca8, 0x1741c17)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/expression/scalar_function.go:216 +0x4c
+github.com/pingcap/tidb/expression.(*ScalarFunction).Eval(0xc43d1e0aa0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, ...)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/expression/scalar_function.go:188 +0x481
+github.com/pingcap/tidb/expression.foldConstant(0x205df00, 0xc43d1e0aa0, 0x1e18b60, 0xc43c642501, 0xc43d1e0aa0)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/expression/constant_fold.go:102 +0x5e2
+github.com/pingcap/tidb/expression.FoldConstant(0x205df00, 0xc43d1e0aa0, 0xc43c642518, 0x4)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/expression/constant_fold.go:33 +0x35
+github.com/pingcap/tidb/expression.NewFunction(0x205eb00, 0xc43e274000, 0xc43c642518, 0x4, 0xc43c6406c0, 0xc422664ec0, 0x3, 0x4, 0x1e18aa0, 0xc422664ec0, ...)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/expression/scalar_function.go:98 +0x341
+github.com/pingcap/tidb/plan.(*expressionRewriter).funcCallToExpression(0xc421a80d00, 0xc43c8e87e0)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/expression_rewriter.go:1198 +0x174
+github.com/pingcap/tidb/plan.(*expressionRewriter).Leave(0xc421a80d00, 0x20313e0, 0xc43c8e87e0, 0x2048e40, 0xc438357e40, 0x1aa0b01)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/expression_rewriter.go:746 +0x86a
+github.com/pingcap/tidb/ast.(*FuncCallExpr).Accept(0xc43c8e87e0, 0x202cae0, 0xc421a80d00, 0x1a2fd5c, 0x205e800, 0xc421a80c80)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/ast/functions.go:363 +0x1bf
+github.com/pingcap/tidb/plan.(*planBuilder).rewriteExprNode(0xc43b7e3e00, 0xc421a80d00, 0x2048740, 0xc43c8e87e0, 0xc4203bd301, 0x1010559, 0xc422664e40, 0x40, 0x38, 0x1dedf60, ...)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/expression_rewriter.go:132 +0x54
+github.com/pingcap/tidb/plan.(*planBuilder).rewriteWithPreprocess(0xc43b7e3e00, 0x2048740, 0xc43c8e87e0, 0x205e800, 0xc421a80c80, 0x0, 0x1eba401, 0x0, 0x0, 0x0, ...)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/expression_rewriter.go:104 +0x12b
+github.com/pingcap/tidb/plan.(*planBuilder).rewrite(0xc43b7e3e00, 0x2048740, 0xc43c8e87e0, 0x205e800, 0xc421a80c80, 0x0, 0x1, 0x0, 0x0, 0x0, ...)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/expression_rewriter.go:80 +0x96
+github.com/pingcap/tidb/plan.(*planBuilder).buildProjection(0xc43b7e3e00, 0x205e800, 0xc421a80c80, 0xc42402e6e0, 0x1, 0x1, 0x0, 0x1, 0x1, 0x1e17360)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/logical_plan_builder.go:572 +0x220
+github.com/pingcap/tidb/plan.(*planBuilder).buildSelect(0xc43b7e3e00, 0xc4210bb4a0, 0x0, 0x0)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/logical_plan_builder.go:1664 +0x309
+github.com/pingcap/tidb/plan.(*planBuilder).build(0xc43b7e3e00, 0x2031ca0, 0xc4210bb4a0, 0xc421a293b0, 0x205eb00)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/planbuilder.go:155 +0x603
+github.com/pingcap/tidb/plan.Optimize(0x205eb00, 0xc43e274000, 0x2031ca0, 0xc4210bb4a0, 0x2048fc0, 0xc421a293b0, 0x2a7bd00, 0x0, 0x0, 0x2f)
+ /Users/jianzhang.zj/opt/gopath/src/github.com/pingcap/tidb/plan/optimize
+2018/07/25 16:33:10.027 server.go:316: [info] con:1 close connection
+```
+
+What we need to do is **not** allocate a buffer larger than **""max_allowed_packet""** for these string functions:
+- [ ] to_base64
+- [ ] from_base64
+- [ ] concat
+- [ ] concat_ws
+- [ ] replace
+- [ ] insert
+- [ ] repeat
+- [ ] space
+- [ ] rpad
+- [ ] lpad
+- [ ] cast
+- [ ] export_set
+- [ ] quote
+
+All the above functions implemented in MySQL are located in the **""sql/item_strfunc.cc""** file, you can grep the function name to see specific implementations.
+
+All the above functions can be found in TiDB from the source file **""expression/builtin.go""**.",1,need to handle er warn allowed packet overflowed for some string functions take this as an example sql select rpad hello in mysql the result is null and a warning about result of rpad was larger than max allowed packet is returned sql mysql localhost select rpad hello rpad hello null row in set warnings sec mysql localhost show warnings level code message warning truncated incorrect decimal value warning truncated incorrect decimal value warning result of rpad was larger than max allowed packet truncated rows in set sec mysql localhost select version version row in set sec in tidb this query results in a lost connection and the panic is runtime error makeslice len out of range and the panic stack is conn go lastcmd select rpad hello runtime error makeslice len out of range goroutine github com pingcap tidb server clientconn run users jianzhang zj opt gopath src github com pingcap tidb server conn go panic users jianzhang zj opt goroot src runtime panic go strings repeat users jianzhang zj opt goroot src strings strings go github com pingcap tidb expression builtinrpadsig evalstring users jianzhang zj opt gopath src github com pingcap tidb expression builtin string go github com pingcap tidb expression scalarfunction evalstring users jianzhang zj opt gopath src github com pingcap tidb expression scalar function go github com pingcap tidb expression scalarfunction eval users jianzhang zj opt gopath src github com pingcap tidb expression scalar function go github com pingcap tidb expression foldconstant users jianzhang zj opt gopath src github com pingcap tidb expression constant fold go github com pingcap tidb expression foldconstant users jianzhang zj opt gopath src github com pingcap tidb expression constant fold go github com pingcap tidb expression newfunction users jianzhang zj opt gopath src github com pingcap tidb expression scalar function go github com pingcap tidb plan expressionrewriter funccalltoexpression users jianzhang zj opt gopath src github com pingcap tidb plan expression rewriter go github com pingcap tidb plan expressionrewriter leave users jianzhang zj opt gopath src github com pingcap tidb plan expression rewriter go github com pingcap tidb ast funccallexpr accept users jianzhang zj opt gopath src github com pingcap tidb ast functions go github com pingcap tidb plan planbuilder rewriteexprnode users jianzhang zj opt gopath src github com pingcap tidb plan expression rewriter go github com pingcap tidb plan planbuilder rewritewithpreprocess users jianzhang zj opt gopath src github com pingcap tidb plan expression rewriter go github com pingcap tidb plan planbuilder rewrite users jianzhang zj opt gopath src github com pingcap tidb plan expression rewriter go github com pingcap tidb plan planbuilder buildprojection users jianzhang zj opt gopath src github com pingcap tidb plan logical plan builder go github com pingcap tidb plan planbuilder buildselect users jianzhang zj opt gopath src github com pingcap tidb plan logical plan builder go github com pingcap tidb plan planbuilder build users jianzhang zj opt gopath src github com pingcap tidb plan planbuilder go github com pingcap tidb plan optimize users jianzhang zj opt gopath src github com pingcap tidb plan optimize server go con close connection what we need to do is not allocate a buffer larger than max allowed packet for these string functions to from concat concat ws replace insert repeat space rpad lpad cast export set quote all the above functions implemented in mysql are located in the sql item strfunc cc file you can grep the function name to see specific implementations all the above functions can be found in tidb from the source file expression builtin go ,1
+16626,22764866505.0,IssuesEvent,2022-07-08 02:33:04,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,dbForge Can't connect to TiDB,type/bug severity/minor compatibility-mysql8,"
+
+error : Table 'performance_schema.session_variables' doesn't exist",True,"dbForge Can't connect to TiDB - 
+
+error : Table 'performance_schema.session_variables' doesn't exist",1,dbforge can t connect to tidb error table performance schema session variables doesn t exist,1
+21643,17382983119.0,IssuesEvent,2021-08-01 04:19:11,danmoran-pro/manga_shop,https://api.github.com/repos/danmoran-pro/manga_shop,opened,"User Story 17, Merchant Item Index Link",Usability,"As a visitor
+When I visit a merchant show page ('/merchants/:id')
+Then I see a link to take me to that merchant's items page ('/merchants/:id/items')",True,"User Story 17, Merchant Item Index Link - As a visitor
+When I visit a merchant show page ('/merchants/:id')
+Then I see a link to take me to that merchant's items page ('/merchants/:id/items')",0,user story merchant item index link as a visitor when i visit a merchant show page merchants id then i see a link to take me to that merchant s items page merchants id items ,0
+188940,14480081882.0,IssuesEvent,2020-12-10 10:40:28,kalexmills/github-vet-tests-dec2020,https://api.github.com/repos/kalexmills/github-vet-tests-dec2020,closed,TimeIncUK/ape-dev-rt: vendor/github.com/gophercloud/gophercloud/acceptance/openstack/sharedfilesystems/v2/securityservices_test.go; 3 LoC,fresh test tiny vendored,"
+Found a possible issue in [TimeIncUK/ape-dev-rt](https://www.github.com/TimeIncUK/ape-dev-rt) at [vendor/github.com/gophercloud/gophercloud/acceptance/openstack/sharedfilesystems/v2/securityservices_test.go](https://github.com/TimeIncUK/ape-dev-rt/blob/e78f833cd49bf6aee580dd4cf9224b3e040ee02f/vendor/github.com/gophercloud/gophercloud/acceptance/openstack/sharedfilesystems/v2/securityservices_test.go#L51-L53)
-mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
-Query OK, 1 row affected (0.00 sec)
-
-mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-Empty set (0.00 sec)
-
-mysql> SELECT version();
-+-----------+
-| version() |
-+-----------+
-| 8.0.18 |
-+-----------+
-1 row in set (0.00 sec)
-
-mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-+----+-------------+-------+------------+--------+---------------+---------+---------+----------------+------+----------+--------------------------+
-| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
-+----+-------------+-------+------------+--------+---------------+---------+---------+----------------+------+----------+--------------------------+
-| 1 | SIMPLE | t2 | NULL | ALL | NULL | NULL | NULL | NULL | 1 | 100.00 | Using where |
-| 1 | SIMPLE | t1 | NULL | eq_ref | PRIMARY | PRIMARY | 4 | repro.t2.title | 1 | 100.00 | Using where; Using index |
-+----+-------------+-------+------------+--------+---------------+---------+---------+----------------+------+----------+--------------------------+
-2 rows in set, 1 warning (0.00 sec)
-```
+Below is the message reported by the analyzer for this snippet of code. Beware that the analyzer only reports the first
+issue it finds, so please do not limit your consideration to the contents of the below message.
-3. What did you see instead?
+> function call which takes a reference to securityService at line 52 may start a goroutine
-* TiDB
+[Click here to see the code in its original context.](https://github.com/TimeIncUK/ape-dev-rt/blob/e78f833cd49bf6aee580dd4cf9224b3e040ee02f/vendor/github.com/gophercloud/gophercloud/acceptance/openstack/sharedfilesystems/v2/securityservices_test.go#L51-L53)
-```
-mysql> CREATE TABLE t1 (id int(11) NOT NULL AUTO_INCREMENT, PRIMARY KEY (`id`));
-Query OK, 0 rows affected (0.08 sec)
-
-mysql> INSERT INTO t1(`id`) VALUES(3);
-Query OK, 1 row affected (0.01 sec)
-
-mysql> CREATE TABLE t2 (title text);
-Query OK, 0 rows affected (0.08 sec)
-
-mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
-Query OK, 1 row affected (0.01 sec)
-
-mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-+----+-------+
-| id | title |
-+----+-------+
-| 3 | 3.0.1 |
-+----+-------+
-1 row in set, 1 warning (0.00 sec)
-
-mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-+----------------------------+-------+-----------+-----------------------------------------------------------------+
-| id | count | task | operator info |
-+----------------------------+-------+-----------+-----------------------------------------------------------------+
-| Projection_8 | 1.00 | root | Column#1, Column#2 |
-| └─HashLeftJoin_9 | 1.00 | root | inner join, inner:Projection_14, equal:[eq(Column#6, Column#7)] |
-| ├─Projection_11 | 1.00 | root | Column#1, cast(Column#1) |
-| │ └─TableReader_13 | 1.00 | root | data:TableScan_12 |
-| │ └─TableScan_12 | 1.00 | cop[tikv] | table:t1, range:[-inf,+inf], keep order:false, stats:pseudo |
-| └─Projection_14 | 1.00 | root | Column#2, cast(Column#2) |
-| └─TableReader_16 | 1.00 | root | data:TableScan_15 |
-| └─TableScan_15 | 1.00 | cop[tikv] | table:t2, range:[-inf,+inf], keep order:false, stats:pseudo |
-+----------------------------+-------+-----------+-----------------------------------------------------------------+
-8 rows in set (0.00 sec)
-```
+
+Click here to show the 3 line(s) of Go which triggered the analyzer.
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```go
+ for _, securityService := range allSecurityServices {
+ PrintSecurityService(t, &securityService)
+ }
```
-Release Version: v4.0.0-alpha-842-g3ca8661b5
-Git Commit Hash: 3ca8661b5b3b12ecdfd664a5dd090f2af859a55c
-Git Branch: master
-UTC Build Time: 2019-11-12 01:03:14
-GoVersion: go version go1.13 linux/amd64
-Race Enabled: false
-TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
-Check Table Before Drop: false
-```
-
-5. More information
-
-BTW, this incorrect behavior only happens in primary key, the following SQLs are executed same in both side.
+
-```
-CREATE TABLE t1 (id int);
-INSERT INTO t1(`id`) VALUES(3);
-CREATE TABLE t2 (title text);
-INSERT INTO t2(`title`) VALUES(""3.0.1"");
-SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-```
+Leave a reaction on this issue to contribute to the project by classifying this instance as a **Bug** :-1:, **Mitigated** :+1:, or **Desirable Behavior** :rocket:
+See the descriptions of the classifications [here](https://github.com/github-vet/rangeclosure-findings#how-can-i-help) for more information.
-* In MySQL 8.0
+commit ID: e78f833cd49bf6aee580dd4cf9224b3e040ee02f
+",1.0,"TimeIncUK/ape-dev-rt: vendor/github.com/gophercloud/gophercloud/acceptance/openstack/sharedfilesystems/v2/securityservices_test.go; 3 LoC -
+Found a possible issue in [TimeIncUK/ape-dev-rt](https://www.github.com/TimeIncUK/ape-dev-rt) at [vendor/github.com/gophercloud/gophercloud/acceptance/openstack/sharedfilesystems/v2/securityservices_test.go](https://github.com/TimeIncUK/ape-dev-rt/blob/e78f833cd49bf6aee580dd4cf9224b3e040ee02f/vendor/github.com/gophercloud/gophercloud/acceptance/openstack/sharedfilesystems/v2/securityservices_test.go#L51-L53)
-```
-mysql> CREATE TABLE t1 (id int);
-Query OK, 0 rows affected (0.01 sec)
+Below is the message reported by the analyzer for this snippet of code. Beware that the analyzer only reports the first
+issue it finds, so please do not limit your consideration to the contents of the below message.
-mysql> INSERT INTO t1(`id`) VALUES(3);
-Query OK, 1 row affected (0.00 sec)
+> function call which takes a reference to securityService at line 52 may start a goroutine
-mysql> CREATE TABLE t2 (title text);
-Query OK, 0 rows affected (0.00 sec)
+[Click here to see the code in its original context.](https://github.com/TimeIncUK/ape-dev-rt/blob/e78f833cd49bf6aee580dd4cf9224b3e040ee02f/vendor/github.com/gophercloud/gophercloud/acceptance/openstack/sharedfilesystems/v2/securityservices_test.go#L51-L53)
-mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
-Query OK, 1 row affected (0.00 sec)
+
+Click here to show the 3 line(s) of Go which triggered the analyzer.
-mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-+------+-------+
-| id | title |
-+------+-------+
-| 3 | 3.0.1 |
-+------+-------+
-1 row in set (0.01 sec)
+```go
+ for _, securityService := range allSecurityServices {
+ PrintSecurityService(t, &securityService)
+ }
-mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-+----+-------------+-------+------------+------+---------------+------+---------+------+------+----------+----------------------------------------------------+
-| id | select_type | table | partitions | type | possible_keys | key | key_len | ref | rows | filtered | Extra |
-+----+-------------+-------+------------+------+---------------+------+---------+------+------+----------+----------------------------------------------------+
-| 1 | SIMPLE | t1 | NULL | ALL | NULL | NULL | NULL | NULL | 1 | 100.00 | NULL |
-| 1 | SIMPLE | t2 | NULL | ALL | NULL | NULL | NULL | NULL | 1 | 100.00 | Using where; Using join buffer (Block Nested Loop) |
-+----+-------------+-------+------------+------+---------------+------+---------+------+------+----------+----------------------------------------------------+
-2 rows in set, 1 warning (0.00 sec)
```
+
-* In TiDB
-
-```
-mysql> CREATE TABLE t1 (id int);
-Query OK, 0 rows affected (0.08 sec)
-
-mysql> INSERT INTO t1(`id`) VALUES(3);
-Query OK, 1 row affected (0.01 sec)
-
-mysql> CREATE TABLE t2 (title text);
-Query OK, 0 rows affected (0.08 sec)
-
-mysql> INSERT INTO t2(`title`) VALUES(""3.0.1"");
-Query OK, 1 row affected (0.02 sec)
-
-mysql> SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-+------+-------+
-| id | title |
-+------+-------+
-| 3 | 3.0.1 |
-+------+-------+
-1 row in set, 1 warning (0.00 sec)
-
-mysql> EXPLAIN SELECT * FROM t1 JOIN t2 ON t1.id=t2.title;
-+----------------------------+----------+-----------+-----------------------------------------------------------------+
-| id | count | task | operator info |
-+----------------------------+----------+-----------+-----------------------------------------------------------------+
-| Projection_8 | 12500.00 | root | Column#1, Column#3 |
-| └─HashLeftJoin_9 | 12500.00 | root | inner join, inner:Projection_14, equal:[eq(Column#7, Column#8)] |
-| ├─Projection_11 | 10000.00 | root | Column#1, cast(Column#1) |
-| │ └─TableReader_13 | 10000.00 | root | data:TableScan_12 |
-| │ └─TableScan_12 | 10000.00 | cop[tikv] | table:t1, range:[-inf,+inf], keep order:false, stats:pseudo |
-| └─Projection_14 | 10000.00 | root | Column#3, cast(Column#3) |
-| └─TableReader_16 | 10000.00 | root | data:TableScan_15 |
-| └─TableScan_15 | 10000.00 | cop[tikv] | table:t2, range:[-inf,+inf], keep order:false, stats:pseudo |
-+----------------------------+----------+-----------+-----------------------------------------------------------------+
-8 rows in set (0.00 sec)
-```",1,join on int primary key and text is not the same with mysql bug report please answer these questions before submitting your issue thanks what did you do create table id int not null auto increment primary key id insert into id values create table title text insert into title values select from join on id title what did you expect to see mysql mysql create table id int not null auto increment primary key id query ok rows affected warning sec mysql insert into id values query ok row affected sec mysql create table title text query ok rows affected sec mysql insert into title values query ok row affected sec mysql select from join on id title empty set sec mysql select version version row in set sec mysql explain select from join on id title id select type table partitions type possible keys key key len ref rows filtered extra simple null all null null null null using where simple null eq ref primary primary repro title using where using index rows in set warning sec what did you see instead tidb mysql create table id int not null auto increment primary key id query ok rows affected sec mysql insert into id values query ok row affected sec mysql create table title text query ok rows affected sec mysql insert into title values query ok row affected sec mysql select from join on id title id title row in set warning sec mysql explain select from join on id title id count task operator info projection root column column └─hashleftjoin root inner join inner projection equal ├─projection root column cast column │ └─tablereader root data tablescan │ └─tablescan cop table range keep order false stats pseudo └─projection root column cast column └─tablereader root data tablescan └─tablescan cop table range keep order false stats pseudo rows in set sec what version of tidb are you using tidb server v or run select tidb version on tidb release version alpha git commit hash git branch master utc build time goversion go version linux race enabled false tikv min version check table before drop false more information btw this incorrect behavior only happens in primary key the following sqls are executed same in both side create table id int insert into id values create table title text insert into title values select from join on id title in mysql mysql create table id int query ok rows affected sec mysql insert into id values query ok row affected sec mysql create table title text query ok rows affected sec mysql insert into title values query ok row affected sec mysql select from join on id title id title row in set sec mysql explain select from join on id title id select type table partitions type possible keys key key len ref rows filtered extra simple null all null null null null null simple null all null null null null using where using join buffer block nested loop rows in set warning sec in tidb mysql create table id int query ok rows affected sec mysql insert into id values query ok row affected sec mysql create table title text query ok rows affected sec mysql insert into title values query ok row affected sec mysql select from join on id title id title row in set warning sec mysql explain select from join on id title id count task operator info projection root column column └─hashleftjoin root inner join inner projection equal ├─projection root column cast column │ └─tablereader root data tablescan │ └─tablescan cop table range keep order false stats pseudo └─projection root column cast column └─tablereader root data tablescan └─tablescan cop table range keep order false stats pseudo rows in set sec ,1
-69787,22669454850.0,IssuesEvent,2022-07-03 11:47:05,cython/cython,https://api.github.com/repos/cython/cython,closed,[BUG] Includes: declaration for newfunc is wrong,defect Library,"
-
-Hello up there. object.pxd currently declares `newfunc` as follows:
-
-```pyx
-ctypedef object (*newfunc)(cpython.type.type, object, object) # (type, args, kwargs)
-```
+Leave a reaction on this issue to contribute to the project by classifying this instance as a **Bug** :-1:, **Mitigated** :+1:, or **Desirable Behavior** :rocket:
+See the descriptions of the classifications [here](https://github.com/github-vet/rangeclosure-findings#how-can-i-help) for more information.
-which implies that `args` and `kwargs` are always live objects and cannot be NULL.
+commit ID: e78f833cd49bf6aee580dd4cf9224b3e040ee02f
+",0,timeincuk ape dev rt vendor github com gophercloud gophercloud acceptance openstack sharedfilesystems securityservices test go loc found a possible issue in at below is the message reported by the analyzer for this snippet of code beware that the analyzer only reports the first issue it finds so please do not limit your consideration to the contents of the below message function call which takes a reference to securityservice at line may start a goroutine click here to show the line s of go which triggered the analyzer go for securityservice range allsecurityservices printsecurityservice t securityservice leave a reaction on this issue to contribute to the project by classifying this instance as a bug mitigated or desirable behavior rocket see the descriptions of the classifications for more information commit id ,0
+191285,15283693530.0,IssuesEvent,2021-02-23 11:11:40,ethersphere/bee,https://api.github.com/repos/ethersphere/bee,closed,Pin listing options are missing from autogenerated API docs,bug documentation issue,"#### Summary
+The [listing of pinned chunks](https://docs.ethswarm.org/api/#tag/Chunk-pinning/paths/~1pin~1chunks/get) endpoint API documentation is missing the `offset` and `limit` optional query parameters. However, without specifying the `limit` parameter the endpoint only returns 100 items whereas there may be more items than that.
+",1.0,"Pin listing options are missing from autogenerated API docs - #### Summary
+The [listing of pinned chunks](https://docs.ethswarm.org/api/#tag/Chunk-pinning/paths/~1pin~1chunks/get) endpoint API documentation is missing the `offset` and `limit` optional query parameters. However, without specifying the `limit` parameter the endpoint only returns 100 items whereas there may be more items than that.
+",0,pin listing options are missing from autogenerated api docs summary the endpoint api documentation is missing the offset and limit optional query parameters however without specifying the limit parameter the endpoint only returns items whereas there may be more items than that ,0
+725072,24950636755.0,IssuesEvent,2022-11-01 06:49:44,Hyperobjekt/seeing-solitary,https://api.github.com/repos/Hyperobjekt/seeing-solitary,closed,Handle 0 values on Barchart,high priority,"- [x] Make manual 0% along x-axis
+- [x] Add transparent bar to trigger tooltip hover state
+- [x] Confirm that not reported values should not be included in charts (ex: state-and-federal totals) @james-minton ?",1.0,"Handle 0 values on Barchart - - [x] Make manual 0% along x-axis
+- [x] Add transparent bar to trigger tooltip hover state
+- [x] Confirm that not reported values should not be included in charts (ex: state-and-federal totals) @james-minton ?",0,handle values on barchart make manual along x axis add transparent bar to trigger tooltip hover state confirm that not reported values should not be included in charts ex state and federal totals james minton ,0
+92280,3869353401.0,IssuesEvent,2016-04-10 15:13:06,cs2103jan2016-w13-2j/todolist,https://api.github.com/repos/cs2103jan2016-w13-2j/todolist,closed,[UI/Parser/Logic] enhancement: refine Natty controls and notifications / feedback,priority.high status.ongoing type.enhancement type.epic type.task,"- Set standard references and alias (e.g. today)
+- Refine case logic flow
+- Refine notifications through exception handling",1.0,"[UI/Parser/Logic] enhancement: refine Natty controls and notifications / feedback - - Set standard references and alias (e.g. today)
+- Refine case logic flow
+- Refine notifications through exception handling",0, enhancement refine natty controls and notifications feedback set standard references and alias e g today refine case logic flow refine notifications through exception handling,0
+12983,15254600337.0,IssuesEvent,2021-02-20 12:41:54,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,prefixed column clustered index's duplicate error message differ to mysql,status/help-wanted type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```
+set @@tidb_enable_clustered_index=1;
+create table t(name varchar(255), b int, c int, primary key(name(2)), index idx(b));
+insert into t(name, b) values(""cha"", 3);
+insert into t(name, b) values(""chb"", 3);
+```
+
+
+
+### 2. What did you expect to see? (Required)
+
+```
+ERROR 1062 (23000): Duplicate entry 'ch' for key 'PRIMARY'
+```
+
+### 3. What did you see instead (Required)
+
+```
+ERROR 1062 (23000): Duplicate entry 'chb' for key 'PRIMARY'
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+
+```
+Release Version: None
+Edition: Community
+Git Commit Hash: None
+Git Branch: None
+UTC Build Time: None
+GoVersion: go1.15
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+```
+
+",True,"prefixed column clustered index's duplicate error message differ to mysql - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```
+set @@tidb_enable_clustered_index=1;
+create table t(name varchar(255), b int, c int, primary key(name(2)), index idx(b));
+insert into t(name, b) values(""cha"", 3);
+insert into t(name, b) values(""chb"", 3);
+```
+
+
+
+### 2. What did you expect to see? (Required)
+
+```
+ERROR 1062 (23000): Duplicate entry 'ch' for key 'PRIMARY'
+```
+
+### 3. What did you see instead (Required)
+
+```
+ERROR 1062 (23000): Duplicate entry 'chb' for key 'PRIMARY'
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+
+```
+Release Version: None
+Edition: Community
+Git Commit Hash: None
+Git Branch: None
+UTC Build Time: None
+GoVersion: go1.15
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+```
+
+",1,prefixed column clustered index s duplicate error message differ to mysql bug report please answer these questions before submitting your issue thanks minimal reproduce step required set tidb enable clustered index create table t name varchar b int c int primary key name index idx b insert into t name b values cha insert into t name b values chb what did you expect to see required error duplicate entry ch for key primary what did you see instead required error duplicate entry chb for key primary what is your tidb version required release version none edition community git commit hash none git branch none utc build time none goversion race enabled false tikv min version check table before drop false ,1
+222711,24711258543.0,IssuesEvent,2022-10-20 01:07:57,wagner-deoliveira/proofy-react-app,https://api.github.com/repos/wagner-deoliveira/proofy-react-app,opened,CVE-2022-3517 (High) detected in minimatch-3.0.4.tgz,security vulnerability,"## CVE-2022-3517 - High Severity Vulnerability
+ Vulnerable Library - minimatch-3.0.4.tgz
-However Python can, and does, call tp_new with either args=NULL, or kwargs=NULL or both. And in such cases this leads to segfault in automatically-generated __Pyx_INCREF for args or kw.
+
Path to vulnerable library: /node_modules/recursive-readdir/node_modules/minimatch/package.json
+
-The fix is to change `object` to `PyObject*` for both args and kwargs.
+Dependency Hierarchy:
+ - react-scripts-5.0.1.tgz (Root Library)
+ - react-dev-utils-12.0.1.tgz
+ - recursive-readdir-2.2.2.tgz
+ - :x: **minimatch-3.0.4.tgz** (Vulnerable Library)
+
Found in base branch: master
+
+
+
+ Vulnerability Details
+
+
+A vulnerability was found in the minimatch package. This flaw allows a Regular Expression Denial of Service (ReDoS) when calling the braceExpand function with specific arguments, resulting in a Denial of Service.
-Please see below for details:
+
+
+A vulnerability was found in the minimatch package. This flaw allows a Regular Expression Denial of Service (ReDoS) when calling the braceExpand function with specific arguments, resulting in a Denial of Service.
-x = X(123)
-print(x)
-```
+
+For more information on CVSS3 Scores, click here.
+
+
+
+ Suggested Fix
+
-```console
-(neo) (py3.venv) (g.env) kirr@deca:~/src/tools/go/pygolang$ python -c 'import x'
-Ошибка сегментирования (стек памяти сброшен на диск)
-```
-
-```console
-(neo) (py3.venv) (g.env) kirr@deca:~/src/tools/go/pygolang$ gdb python core
-...
-Reading symbols from python...
-Reading symbols from /usr/lib/debug/.build-id/f9/02f8a561c3abdb9c8d8c859d4243bd8c3f928f.debug...
-[New LWP 218557]
-[Thread debugging using libthread_db enabled]
-Using host libthread_db library ""/lib/x86_64-linux-gnu/libthread_db.so.1"".
-Core was generated by `python -c import x'.
-Program terminated with signal SIGSEGV, Segmentation fault.
-#0 _Py_INCREF (op=0x0) at /usr/include/python3.9/object.h:408
-408 op->ob_refcnt++;
-
-(gdb) bt 5
-#0 _Py_INCREF (op=0x0) at /usr/include/python3.9/object.h:408
-#1 __pyx_f_1x__trace_tp_new (__pyx_v_cls=0x7f5ce75e6880 <__pyx_type_1x_X>, __pyx_v_args=(123,), __pyx_v_kw=0x0) at /home/kirr/src/tools/go/pygolang/x.c:1986
-#2 0x000000000051dd7e in type_call (type=type@entry=0x7f5ce75e6880 <__pyx_type_1x_X>, args=args@entry=(123,), kwds=kwds@entry=0x0)
- at ../Objects/typeobject.c:1014
-#3 0x00007f5ce75df8d4 in __Pyx_PyObject_Call (func=, arg=(123,), kw=0x0) at /home/kirr/src/tools/go/pygolang/x.c:3414
-#4 0x00007f5ce75df276 in __pyx_pymod_exec_x (__pyx_pyinit_module=) at /home/kirr/src/tools/go/pygolang/x.c:3017
-(More stack frames follow...)
-
-(gdb) f 1
-#1 __pyx_f_1x__trace_tp_new (__pyx_v_cls=0x7f5ce75e6880 <__pyx_type_1x_X>, __pyx_v_args=(123,), __pyx_v_kw=0x0) at /home/kirr/src/tools/go/pygolang/x.c:1986
-1986 __Pyx_INCREF(__pyx_v_kw);
-```
-
-
-**Expected behavior**
-No segfault in autogenerated coce if `_trace_tp_new` matches `newfunc` signature.
+
Type: Upgrade version
+
Release Date: 2022-10-17
+
Fix Resolution: minimatch - 3.0.5
-**Environment (please complete the following information):**
- - OS: Linux
- - Python version: 3.9.2
- - Cython version: 0.29.30
+
+
+
+***
+Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",0,cve high detected in minimatch tgz cve high severity vulnerability vulnerable library minimatch tgz a glob matcher in javascript library home page a href path to dependency file package json path to vulnerable library node modules recursive readdir node modules minimatch package json dependency hierarchy react scripts tgz root library react dev utils tgz recursive readdir tgz x minimatch tgz vulnerable library found in base branch master vulnerability details a vulnerability was found in the minimatch package this flaw allows a regular expression denial of service redos when calling the braceexpand function with specific arguments resulting in a denial of service publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution minimatch step up your open source security game with mend ,0
+107781,11571057289.0,IssuesEvent,2020-02-20 20:44:34,nucypher/nucypher,https://api.github.com/repos/nucypher/nucypher,closed,Update documentation to reflect new local fleet scripts filepaths ,Bug 🐞 Documentation Good Intro Issue,"Local fleet scripts moved from `examples` to `scripts/local_fleet` in commit `6df4dfd5060d09e570f444e249f01085a9da26f8`, but the documentation was not changed with the new file paths.",1.0,"Update documentation to reflect new local fleet scripts filepaths - Local fleet scripts moved from `examples` to `scripts/local_fleet` in commit `6df4dfd5060d09e570f444e249f01085a9da26f8`, but the documentation was not changed with the new file paths.",0,update documentation to reflect new local fleet scripts filepaths local fleet scripts moved from examples to scripts local fleet in commit but the documentation was not changed with the new file paths ,0
+5991,8414371281.0,IssuesEvent,2018-10-13 01:38:48,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,should we display foreign key information in `show create table`,type/compatibility,"## Question
+Currently, TiDB only support `foreign key` grammar, not support `foreign key constrain`.
+If create table with foreign key, Should we display the foreign key information when `show create table`?
+sql:
+```sql
+create table t1 (a int, index(a));
+create table t2 (b int, foreign key (b) references t1(a));
+show create table t2;
+```
+**TiDB** return
+```sql
++-------+-------------------------------------------------------+
+| Table | Create Table |
++-------+-------------------------------------------------------+
+| t2 | CREATE TABLE `t2` ( |
+| | `b` int(11) DEFAULT NULL |
+| | ) ENGINE=InnoDB DEFAULT CHARSET=utf8 COLLATE=utf8_bin |
++-------+-------------------------------------------------------+
+```
+
+**MySQL** return
+```sql
++-------+------------------------------------------------------------------+
+| Table | Create Table |
++-------+------------------------------------------------------------------+
+| t2 | CREATE TABLE `t2` ( |
+| | `b` int(11) DEFAULT NULL, |
+| | KEY `b` (`b`), |
+| | CONSTRAINT `t2_ibfk_1` FOREIGN KEY (`b`) REFERENCES `t1` (`a`) |
+| | ) ENGINE=InnoDB DEFAULT CHARSET=latin1 |
++-------+------------------------------------------------------------------+
+```",True,"should we display foreign key information in `show create table` - ## Question
+Currently, TiDB only support `foreign key` grammar, not support `foreign key constrain`.
+If create table with foreign key, Should we display the foreign key information when `show create table`?
+sql:
+```sql
+create table t1 (a int, index(a));
+create table t2 (b int, foreign key (b) references t1(a));
+show create table t2;
+```
+**TiDB** return
+```sql
++-------+-------------------------------------------------------+
+| Table | Create Table |
++-------+-------------------------------------------------------+
+| t2 | CREATE TABLE `t2` ( |
+| | `b` int(11) DEFAULT NULL |
+| | ) ENGINE=InnoDB DEFAULT CHARSET=utf8 COLLATE=utf8_bin |
++-------+-------------------------------------------------------+
+```
+
+**MySQL** return
+```sql
++-------+------------------------------------------------------------------+
+| Table | Create Table |
++-------+------------------------------------------------------------------+
+| t2 | CREATE TABLE `t2` ( |
+| | `b` int(11) DEFAULT NULL, |
+| | KEY `b` (`b`), |
+| | CONSTRAINT `t2_ibfk_1` FOREIGN KEY (`b`) REFERENCES `t1` (`a`) |
+| | ) ENGINE=InnoDB DEFAULT CHARSET=latin1 |
++-------+------------------------------------------------------------------+
+```",1,should we display foreign key information in show create table question currently tidb only support foreign key grammar not support foreign key constrain if create table with foreign key should we display the foreign key information when show create table sql sql create table a int index a create table b int foreign key b references a show create table tidb return sql table create table create table b int default null engine innodb default charset collate bin mysql return sql table create table create table b int default null key b b constraint ibfk foreign key b references a engine innodb default charset ,1
+12247,14478089401.0,IssuesEvent,2020-12-10 07:48:04,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Can not swap values by a multi-tables update,severity/major sig/execution type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+
+```sql
+drop table if exists t1, t2;
+create table t1 (c_str varchar(40));
+create table t2 (c_str varchar(40));
+insert into t1 values ('Alice');
+insert into t2 values ('Bob');
+select t1.c_str, t2.c_str from t1, t2 where t1.c_str <= t2.c_str;
+update t1, t2 set t1.c_str = t2.c_str, t2.c_str = t1.c_str where t1.c_str <= t2.c_str;
+select t1.c_str, t2.c_str from t1, t2 where t1.c_str <= t2.c_str;
+```
+
+### 2. What did you expect to see? (Required)
+
+The values of `t1.c_str` and `t2.c_str` should be swapped in the above case, that is, the last selection should return an empty set.
+
+### 3. What did you see instead (Required)
+
+```
+mysql> select t1.c_str, t2.c_str from t1, t2 where t1.c_str <= t2.c_str;
++-------+-------+
+| c_str | c_str |
++-------+-------+
+| Alice | Bob |
++-------+-------+
+1 row in set (0.06 sec)
+
+mysql> update t1, t2 set t1.c_str = t2.c_str, t2.c_str = t1.c_str where t1.c_str <= t2.c_str;
+Query OK, 1 row affected (0.06 sec)
+Rows matched: 2 Changed: 1 Warnings: 0
+
+mysql> select t1.c_str, t2.c_str from t1, t2 where t1.c_str <= t2.c_str;
++-------+-------+
+| c_str | c_str |
++-------+-------+
+| Bob | Bob |
++-------+-------+
+1 row in set (0.05 sec)
+
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+master @ 8978773f5e3d43a100550e6babea9904a99e5938
+release-4.0 @ 3948c7ba7b5d4a081abf2162b791ab67fe650882
+",True,"Can not swap values by a multi-tables update - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+
+```sql
+drop table if exists t1, t2;
+create table t1 (c_str varchar(40));
+create table t2 (c_str varchar(40));
+insert into t1 values ('Alice');
+insert into t2 values ('Bob');
+select t1.c_str, t2.c_str from t1, t2 where t1.c_str <= t2.c_str;
+update t1, t2 set t1.c_str = t2.c_str, t2.c_str = t1.c_str where t1.c_str <= t2.c_str;
+select t1.c_str, t2.c_str from t1, t2 where t1.c_str <= t2.c_str;
+```
+
+### 2. What did you expect to see? (Required)
+
+The values of `t1.c_str` and `t2.c_str` should be swapped in the above case, that is, the last selection should return an empty set.
+
+### 3. What did you see instead (Required)
+
+```
+mysql> select t1.c_str, t2.c_str from t1, t2 where t1.c_str <= t2.c_str;
++-------+-------+
+| c_str | c_str |
++-------+-------+
+| Alice | Bob |
++-------+-------+
+1 row in set (0.06 sec)
+
+mysql> update t1, t2 set t1.c_str = t2.c_str, t2.c_str = t1.c_str where t1.c_str <= t2.c_str;
+Query OK, 1 row affected (0.06 sec)
+Rows matched: 2 Changed: 1 Warnings: 0
+
+mysql> select t1.c_str, t2.c_str from t1, t2 where t1.c_str <= t2.c_str;
++-------+-------+
+| c_str | c_str |
++-------+-------+
+| Bob | Bob |
++-------+-------+
+1 row in set (0.05 sec)
+
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+master @ 8978773f5e3d43a100550e6babea9904a99e5938
+release-4.0 @ 3948c7ba7b5d4a081abf2162b791ab67fe650882
+",1,can not swap values by a multi tables update bug report please answer these questions before submitting your issue thanks minimal reproduce step required sql drop table if exists create table c str varchar create table c str varchar insert into values alice insert into values bob select c str c str from where c str c str update set c str c str c str c str where c str c str select c str c str from where c str c str what did you expect to see required the values of c str and c str should be swapped in the above case that is the last selection should return an empty set what did you see instead required mysql select c str c str from where c str c str c str c str alice bob row in set sec mysql update set c str c str c str c str where c str c str query ok row affected sec rows matched changed warnings mysql select c str c str from where c str c str c str c str bob bob row in set sec what is your tidb version required master release ,1
+12178,14354611704.0,IssuesEvent,2020-11-30 08:55:52,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Support LIST COLUMNS partitioning,feature/accepted status/help-wanted type/compatibility type/feature-request,"## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+
+MySQL support [LIST COLUMNS](https://dev.mysql.com/doc/refman/8.0/en/partitioning-columns-list.html) partition but TiDB didn't support it now.
+
+support it will help mysql user migrate to TiDB
+
+**Describe the feature you'd like:**
+
+
+Compatible with MySQL's [LIST COLUMNS](https://dev.mysql.com/doc/refman/8.0/en/partitioning-columns-list.html) partition
+
+**Describe alternatives you've considered:**
+
+
+n/a
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+
+",True,"Support LIST COLUMNS partitioning - ## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+
+MySQL support [LIST COLUMNS](https://dev.mysql.com/doc/refman/8.0/en/partitioning-columns-list.html) partition but TiDB didn't support it now.
+
+support it will help mysql user migrate to TiDB
+
+**Describe the feature you'd like:**
+
+
+Compatible with MySQL's [LIST COLUMNS](https://dev.mysql.com/doc/refman/8.0/en/partitioning-columns-list.html) partition
+
+**Describe alternatives you've considered:**
+
+
+n/a
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+
+",1,support list columns partitioning feature request is your feature request related to a problem please describe mysql support partition but tidb didn t support it now support it will help mysql user migrate to tidb describe the feature you d like compatible with mysql s partition describe alternatives you ve considered n a teachability documentation adoption migration strategy ,1
+3839,6690511347.0,IssuesEvent,2017-10-09 09:24:38,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,default unsigned integer column length is not consistent with MySQL.,compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+```
+mysql> create table `t1` (`c1` tinyint unsigned default null, `c2` smallint unsigned default null, `c3` mediumint unsigned default null, `c4` int unsigned default null, `c5` bigint unsigned default null);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> show create table t1;
++-------+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| t1 | CREATE TABLE `t1` (
+ `c1` tinyint(3) unsigned DEFAULT NULL,
+ `c2` smallint(5) unsigned DEFAULT NULL,
+ `c3` mediumint(8) unsigned DEFAULT NULL,
+ `c4` int(10) unsigned DEFAULT NULL,
+ `c5` bigint(20) unsigned DEFAULT NULL
+) ENGINE=InnoDB DEFAULT CHARSET=latin1 |
++-------+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+TiDB:
+
+```
+mysql> create table `t1` (`c1` tinyint unsigned default null, `c2` smallint unsigned default null, `c3` mediumint unsigned default null, `c4` int unsigned default null, `c5` bigint unsigned default null);
+Query OK, 0 rows affected (0.09 sec)
+
+mysql> show create table t1;
++-------+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Table | Create Table
+ |
++-------+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| t1 | CREATE TABLE `t1` (
+ `c1` tinyint(4) UNSIGNED DEFAULT NULL,
+ `c2` smallint(6) UNSIGNED DEFAULT NULL,
+ `c3` mediumint(9) UNSIGNED DEFAULT NULL,
+ `c4` int(11) UNSIGNED DEFAULT NULL,
+ `c5` bigint(20) UNSIGNED DEFAULT NULL
+) ENGINE=InnoDB DEFAULT CHARSET=utf8 COLLATE=utf8_bin |
++-------+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+version:
+
+```
+mysql> select tidb_version();
++-----------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++-----------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: 0.9.0
+Git Commit Hash: e599ceec2b32b450a1e42ef49cdf5be7ea5853da
+Git Branch: master
+UTC Build Time: 2017-09-26 07:32:19 |
++-----------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+",True,"default unsigned integer column length is not consistent with MySQL. - Please answer these questions before submitting your issue. Thanks!
+
+```
+mysql> create table `t1` (`c1` tinyint unsigned default null, `c2` smallint unsigned default null, `c3` mediumint unsigned default null, `c4` int unsigned default null, `c5` bigint unsigned default null);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> show create table t1;
++-------+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| t1 | CREATE TABLE `t1` (
+ `c1` tinyint(3) unsigned DEFAULT NULL,
+ `c2` smallint(5) unsigned DEFAULT NULL,
+ `c3` mediumint(8) unsigned DEFAULT NULL,
+ `c4` int(10) unsigned DEFAULT NULL,
+ `c5` bigint(20) unsigned DEFAULT NULL
+) ENGINE=InnoDB DEFAULT CHARSET=latin1 |
++-------+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+TiDB:
+
+```
+mysql> create table `t1` (`c1` tinyint unsigned default null, `c2` smallint unsigned default null, `c3` mediumint unsigned default null, `c4` int unsigned default null, `c5` bigint unsigned default null);
+Query OK, 0 rows affected (0.09 sec)
+
+mysql> show create table t1;
++-------+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Table | Create Table
+ |
++-------+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| t1 | CREATE TABLE `t1` (
+ `c1` tinyint(4) UNSIGNED DEFAULT NULL,
+ `c2` smallint(6) UNSIGNED DEFAULT NULL,
+ `c3` mediumint(9) UNSIGNED DEFAULT NULL,
+ `c4` int(11) UNSIGNED DEFAULT NULL,
+ `c5` bigint(20) UNSIGNED DEFAULT NULL
+) ENGINE=InnoDB DEFAULT CHARSET=utf8 COLLATE=utf8_bin |
++-------+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+version:
+
+```
+mysql> select tidb_version();
++-----------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++-----------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: 0.9.0
+Git Commit Hash: e599ceec2b32b450a1e42ef49cdf5be7ea5853da
+Git Branch: master
+UTC Build Time: 2017-09-26 07:32:19 |
++-----------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+",1,default unsigned integer column length is not consistent with mysql please answer these questions before submitting your issue thanks mysql create table tinyint unsigned default null smallint unsigned default null mediumint unsigned default null int unsigned default null bigint unsigned default null query ok rows affected sec mysql show create table table create table create table tinyint unsigned default null smallint unsigned default null mediumint unsigned default null int unsigned default null bigint unsigned default null engine innodb default charset row in set sec tidb mysql create table tinyint unsigned default null smallint unsigned default null mediumint unsigned default null int unsigned default null bigint unsigned default null query ok rows affected sec mysql show create table table create table create table tinyint unsigned default null smallint unsigned default null mediumint unsigned default null int unsigned default null bigint unsigned default null engine innodb default charset collate bin row in set sec version mysql select tidb version tidb version release version git commit hash git branch master utc build time row in set sec ,1
+8188,10270345398.0,IssuesEvent,2019-08-23 11:21:45,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,"After executing ""modify column"", its flag has changed",type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+CREATE TABLE `t` (
+ `a` varchar(123) DEFAULT NULL,
+ `d` datetime DEFAULT NULL
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_bin;
+
+tidb> select d from t;
+Field 1: `d`
+Catalog: `def`
+Database: `test`
+Table: `t`
+Org_table: `t`
+Type: DATETIME
+Collation: binary (63)
+Length: 19
+Max_length: 0
+Decimals: 0
+Flags: NOT_NULL BINARY
+```
+
+alter table t modify column d datetime
+select d from t;
+```
+
+2. What did you expect to see?
+I hope that after executing ""modify column"", its flag is the same as before.
+
+3. What did you see instead?
+```
+tidb> alter table t modify column d datetime;
+Query OK, 0 rows affected (0.01 sec)
+tidb> select d from t;
+Field 1: `d`
+Catalog: `def`
+Database: `test`
+Table: `t`
+Org_table: `t`
+Type: DATETIME
+Collation: binary (63)
+Length: 19
+Max_length: 0
+Decimals: 0
+Flags:
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+[""Release Version""=v4.0.0-alpha-119-g0ff5b50c1-dirty]
+[""Git Commit Hash""=0ff5b50c1509bed279a2c2ba7acdb38519b38c9c]
+
+",True,"After executing ""modify column"", its flag has changed - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+CREATE TABLE `t` (
+ `a` varchar(123) DEFAULT NULL,
+ `d` datetime DEFAULT NULL
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_bin;
+
+tidb> select d from t;
+Field 1: `d`
+Catalog: `def`
+Database: `test`
+Table: `t`
+Org_table: `t`
+Type: DATETIME
+Collation: binary (63)
+Length: 19
+Max_length: 0
+Decimals: 0
+Flags: NOT_NULL BINARY
+```
+
+alter table t modify column d datetime
+select d from t;
+```
+
+2. What did you expect to see?
+I hope that after executing ""modify column"", its flag is the same as before.
+
+3. What did you see instead?
+```
+tidb> alter table t modify column d datetime;
+Query OK, 0 rows affected (0.01 sec)
+tidb> select d from t;
+Field 1: `d`
+Catalog: `def`
+Database: `test`
+Table: `t`
+Org_table: `t`
+Type: DATETIME
+Collation: binary (63)
+Length: 19
+Max_length: 0
+Decimals: 0
+Flags:
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+[""Release Version""=v4.0.0-alpha-119-g0ff5b50c1-dirty]
+[""Git Commit Hash""=0ff5b50c1509bed279a2c2ba7acdb38519b38c9c]
+
+",1,after executing modify column its flag has changed bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error create table t a varchar default null d datetime default null engine innodb default charset collate bin tidb select d from t field d catalog def database test table t org table t type datetime collation binary length max length decimals flags not null binary alter table t modify column d datetime select d from t what did you expect to see i hope that after executing modify column its flag is the same as before what did you see instead tidb alter table t modify column d datetime query ok rows affected sec tidb select d from t field d catalog def database test table t org table t type datetime collation binary length max length decimals flags what version of tidb are you using tidb server v or run select tidb version on tidb ,1
+79275,28081685536.0,IssuesEvent,2023-03-30 06:56:50,SeleniumHQ/selenium,https://api.github.com/repos/SeleniumHQ/selenium,closed,[🐛 Bug]: Gradual reduction in performance when same action is repeated,I-defect I-issue-template,"### What happened?
-Thanks beforehand,
-Kirill",1.0,"[BUG] Includes: declaration for newfunc is wrong -
+I am testing an application where there are multiple links (more than 5). I am running a loop and in each loop does below
+1. Verify link details (few texts)
+2. Click on the link (which open up a side panel)
+3. Verify details in side panel
+4. Close side panel
+
+Its observed that on doing so, the webdriver commands response slows down with time heavily
+For instance
+Loop 1
+`[0-0] 2023-03-23T06:30:04.067Z INFO webdriver: COMMAND findElementFromElement(""9623c3f1-dd20-4be3-8f51-96219f951266"", ""xpath"", "".//*[@class='rule-name']//*[text()]"")
+[0-0] 2023-03-23T06:30:04.067Z INFO webdriver: [POST] http://localhost:4444/wd/hub/session/cfb74892c7201126ddcba3bd6eb536a8/element/9623c3f1-dd20-4be3-8f51-96219f951266/element
+[0-0] 2023-03-23T06:30:04.067Z INFO webdriver: DATA { using: 'xpath', value: "".//*[@class='rule-name']//*[text()]"" }
+[0-0] 2023-03-23T06:30:04.144Z INFO webdriver: RESULT {
+[0-0] 'element-6066-11e4-a52e-4f735466cecf': 'e650ee14-fadf-4e4b-8976-5b0f22e51d63'
+[0-0] }
+[0-0] 2023-03-23T06:30:04.149Z INFO webdriver: COMMAND getElementText(""e650ee14-fadf-4e4b-8976-5b0f22e51d63"")
+[0-0] 2023-03-23T06:30:04.149Z INFO webdriver: [GET] http://localhost:4444/wd/hub/session/cfb74892c7201126ddcba3bd6eb536a8/element/e650ee14-fadf-4e4b-8976-5b0f22e51d63/text
+[0-0] 2023-03-23T06:30:04.173Z INFO webdriver: RESULT Global Bypass Lists`
+
+LOOP 4
+`[0-0] value: "".//app-rule-view[child::div[starts-with(@class,'rule')][descendant::*[normalize-space(text())='Domains Bypass']]]""
+[0-0] }
+[0-0] 2023-03-23T06:30:53.114Z INFO webdriver: RESULT {
+[0-0] 'element-6066-11e4-a52e-4f735466cecf': '89d8aced-27a1-454d-ab89-9df2c2b437f5'
+[0-0] }
+[0-0] 2023-03-23T06:30:53.116Z INFO webdriver: COMMAND findElementFromElement(""89d8aced-27a1-454d-ab89-9df2c2b437f5"", ""xpath"", "".//app-pill//*[text()]"")
+[0-0] 2023-03-23T06:30:53.117Z INFO webdriver: [POST] http://localhost:4444/wd/hub/session/cfb74892c7201126ddcba3bd6eb536a8/element/89d8aced-27a1-454d-ab89-9df2c2b437f5/element
+[0-0] 2023-03-23T06:30:53.117Z INFO webdriver: DATA { using: 'xpath', value: './/app-pill//*[text()]' }
+[0-0] 2023-03-23T06:30:54.740Z INFO webdriver: RESULT {
+[0-0] 'element-6066-11e4-a52e-4f735466cecf': 'aa216411-f2f4-407d-915e-f8cce7214337'
+[0-0] }
+[0-0] 2023-03-23T06:30:54.744Z INFO webdriver: COMMAND getElementText(""aa216411-f2f4-407d-915e-f8cce7214337"")
+[0-0] 2023-03-23T06:30:54.744Z INFO webdriver: [GET] http://localhost:4444/wd/hub/session/cfb74892c7201126ddcba3bd6eb536a8/element/aa216411-f2f4-407d-915e-f8cce7214337/text
+[0-0] 2023-03-23T06:30:58.089Z INFO webdriver: RESULT Bypass`
+
+
+The same command to fetch text of the link took 4 seconds in the 4th loop as opposed to fraction of a second
-Hello up there. object.pxd currently declares `newfunc` as follows:
+### How can we reproduce the issue?
-```pyx
-ctypedef object (*newfunc)(cpython.type.type, object, object) # (type, args, kwargs)
+```shell
+Unfortunately I could not share the links to reproduce the code but i hope the attached data above helps. If not let me know how i can help
```
-which implies that `args` and `kwargs` are always live objects and cannot be NULL.
-
-However Python can, and does, call tp_new with either args=NULL, or kwargs=NULL or both. And in such cases this leads to segfault in automatically-generated __Pyx_INCREF for args or kw.
-
-The fix is to change `object` to `PyObject*` for both args and kwargs.
-
-Please see below for details:
-
-```cython
-# cython: language_level=3
-from cpython cimport newfunc, type as cpytype, Py_TYPE
-
-cdef class X:
- cdef int i
- def __init__(self, i):
- self.i = i
- def __repr__(self):
- return 'X(%d)' % self.i
-
-cdef newfunc _orig_tp_new = Py_TYPE(X(0)).tp_new
-
-cdef object _trace_tp_new(cpytype cls, object args, object kw):
- print('_trace_tp_new', cls, args, kw)
- return _orig_tp_new(cls, args, kw)
-
-Py_TYPE(X(0)).tp_new = _trace_tp_new
-
-x = X(123)
-print(x)
-```
-
-```console
-(neo) (py3.venv) (g.env) kirr@deca:~/src/tools/go/pygolang$ cythonize -i x.pyx
-Compiling /home/kirr/src/tools/go/pygolang/x.pyx because it changed.
-[1/1] Cythonizing /home/kirr/src/tools/go/pygolang/x.pyx
-running build_ext
-building 'x' extension
-...
-x86_64-linux-gnu-gcc -pthread -Wno-unused-result -Wsign-compare -DNDEBUG -g -fwrapv -O2 -Wall -g -ffile-prefix-map=/build/python3.9-RNBry6/python3.9-3.9.2=. -fstack-protector-strong -Wformat -Werror=format-security -g -fwrapv -O2 -g -ffile-prefix-map=/build/python3.9-RNBry6/python3.9-3.9.2=. -fstack-protector-strong -Wformat -Werror=format-security -Wdate-time -D_FORTIFY_SOURCE=2 -fPIC -I/home/kirr/src/wendelin/venv/py3.venv/include -I/usr/include/python3.9 -c /home/kirr/src/tools/go/pygolang/x.c -o /home/kirr/src/tools/go/pygolang/tmpqkz1r96s/home/kirr/src/tools/go/pygolang/x.o
-x86_64-linux-gnu-gcc -pthread -shared -Wl,-O1 -Wl,-Bsymbolic-functions -Wl,-z,relro -g -fwrapv -O2 -Wl,-z,relro -g -fwrapv -O2 -g -ffile-prefix-map=/build/python3.9-RNBry6/python3.9-3.9.2=. -fstack-protector-strong -Wformat -Werror=format-security -Wdate-time -D_FORTIFY_SOURCE=2 /home/kirr/src/tools/go/pygolang/tmpqkz1r96s/home/kirr/src/tools/go/pygolang/x.o -o /home/kirr/src/tools/go/pygolang/x.cpython-39-x86_64-linux-gnu.so
-```
+### Relevant log output
-```console
-(neo) (py3.venv) (g.env) kirr@deca:~/src/tools/go/pygolang$ python -c 'import x'
-Ошибка сегментирования (стек памяти сброшен на диск)
+```shell
+[0-0] value: "".//app-rule-view[child::div[starts-with(@class,'rule')][descendant::*[normalize-space(text())='Domains Bypass']]]""
+[0-0] }
+[0-0] 2023-03-23T06:30:53.114Z INFO webdriver: RESULT {
+[0-0] 'element-6066-11e4-a52e-4f735466cecf': '89d8aced-27a1-454d-ab89-9df2c2b437f5'
+[0-0] }
+[0-0] 2023-03-23T06:30:53.116Z INFO webdriver: COMMAND findElementFromElement(""89d8aced-27a1-454d-ab89-9df2c2b437f5"", ""xpath"", "".//app-pill//*[text()]"")
+[0-0] 2023-03-23T06:30:53.117Z INFO webdriver: [POST] http://localhost:4444/wd/hub/session/cfb74892c7201126ddcba3bd6eb536a8/element/89d8aced-27a1-454d-ab89-9df2c2b437f5/element
+[0-0] 2023-03-23T06:30:53.117Z INFO webdriver: DATA { using: 'xpath', value: './/app-pill//*[text()]' }
+[0-0] 2023-03-23T06:30:54.740Z INFO webdriver: RESULT {
+[0-0] 'element-6066-11e4-a52e-4f735466cecf': 'aa216411-f2f4-407d-915e-f8cce7214337'
+[0-0] }
+[0-0] 2023-03-23T06:30:54.744Z INFO webdriver: COMMAND getElementText(""aa216411-f2f4-407d-915e-f8cce7214337"")
+[0-0] 2023-03-23T06:30:54.744Z INFO webdriver: [GET] http://localhost:4444/wd/hub/session/cfb74892c7201126ddcba3bd6eb536a8/element/aa216411-f2f4-407d-915e-f8cce7214337/text
+[0-0] 2023-03-23T06:30:58.089Z INFO webdriver: RESULT Bypass
```
-```console
-(neo) (py3.venv) (g.env) kirr@deca:~/src/tools/go/pygolang$ gdb python core
-...
-Reading symbols from python...
-Reading symbols from /usr/lib/debug/.build-id/f9/02f8a561c3abdb9c8d8c859d4243bd8c3f928f.debug...
-[New LWP 218557]
-[Thread debugging using libthread_db enabled]
-Using host libthread_db library ""/lib/x86_64-linux-gnu/libthread_db.so.1"".
-Core was generated by `python -c import x'.
-Program terminated with signal SIGSEGV, Segmentation fault.
-#0 _Py_INCREF (op=0x0) at /usr/include/python3.9/object.h:408
-408 op->ob_refcnt++;
-
-(gdb) bt 5
-#0 _Py_INCREF (op=0x0) at /usr/include/python3.9/object.h:408
-#1 __pyx_f_1x__trace_tp_new (__pyx_v_cls=0x7f5ce75e6880 <__pyx_type_1x_X>, __pyx_v_args=(123,), __pyx_v_kw=0x0) at /home/kirr/src/tools/go/pygolang/x.c:1986
-#2 0x000000000051dd7e in type_call (type=type@entry=0x7f5ce75e6880 <__pyx_type_1x_X>, args=args@entry=(123,), kwds=kwds@entry=0x0)
- at ../Objects/typeobject.c:1014
-#3 0x00007f5ce75df8d4 in __Pyx_PyObject_Call (func=, arg=(123,), kw=0x0) at /home/kirr/src/tools/go/pygolang/x.c:3414
-#4 0x00007f5ce75df276 in __pyx_pymod_exec_x (__pyx_pyinit_module=) at /home/kirr/src/tools/go/pygolang/x.c:3017
-(More stack frames follow...)
-
-(gdb) f 1
-#1 __pyx_f_1x__trace_tp_new (__pyx_v_cls=0x7f5ce75e6880 <__pyx_type_1x_X>, __pyx_v_args=(123,), __pyx_v_kw=0x0) at /home/kirr/src/tools/go/pygolang/x.c:1986
-1986 __Pyx_INCREF(__pyx_v_kw);
-```
+### Operating System
-**Expected behavior**
-No segfault in autogenerated coce if `_trace_tp_new` matches `newfunc` signature.
+Windows 10
-**Environment (please complete the following information):**
- - OS: Linux
- - Python version: 3.9.2
- - Cython version: 0.29.30
+### Selenium version
+Javascript (WebdriverIO 7.25.2) with Selenium Webdrive 4.8.1
-Thanks beforehand,
-Kirill",0, includes declaration for newfunc is wrong please read this first do not use the bug and feature tracker for general questions and support requests use the cython users mailing list instead it has a wider audience so you get more and better answers did you search for similar issues already please do it helps to save us precious time that we otherwise could not invest into development did you try the latest master branch or pre release it might already have what you want to report also see the regarding recent changes hello up there object pxd currently declares newfunc as follows pyx ctypedef object newfunc cpython type type object object type args kwargs which implies that args and kwargs are always live objects and cannot be null however python can and does call tp new with either args null or kwargs null or both and in such cases this leads to segfault in automatically generated pyx incref for args or kw the fix is to change object to pyobject for both args and kwargs please see below for details cython cython language level from cpython cimport newfunc type as cpytype py type cdef class x cdef int i def init self i self i i def repr self return x d self i cdef newfunc orig tp new py type x tp new cdef object trace tp new cpytype cls object args object kw print trace tp new cls args kw return orig tp new cls args kw py type x tp new trace tp new x x print x console neo venv g env kirr deca src tools go pygolang cythonize i x pyx compiling home kirr src tools go pygolang x pyx because it changed cythonizing home kirr src tools go pygolang x pyx running build ext building x extension linux gnu gcc pthread wno unused result wsign compare dndebug g fwrapv wall g ffile prefix map build fstack protector strong wformat werror format security g fwrapv g ffile prefix map build fstack protector strong wformat werror format security wdate time d fortify source fpic i home kirr src wendelin venv venv include i usr include c home kirr src tools go pygolang x c o home kirr src tools go pygolang home kirr src tools go pygolang x o linux gnu gcc pthread shared wl wl bsymbolic functions wl z relro g fwrapv wl z relro g fwrapv g ffile prefix map build fstack protector strong wformat werror format security wdate time d fortify source home kirr src tools go pygolang home kirr src tools go pygolang x o o home kirr src tools go pygolang x cpython linux gnu so console neo venv g env kirr deca src tools go pygolang python c import x ошибка сегментирования стек памяти сброшен на диск console neo venv g env kirr deca src tools go pygolang gdb python core reading symbols from python reading symbols from usr lib debug build id debug using host libthread db library lib linux gnu libthread db so core was generated by python c import x program terminated with signal sigsegv segmentation fault py incref op at usr include object h op ob refcnt gdb bt py incref op at usr include object h pyx f trace tp new pyx v cls pyx v args pyx v kw at home kirr src tools go pygolang x c in type call type type entry args args entry kwds kwds entry at objects typeobject c in pyx pyobject call func arg kw at home kirr src tools go pygolang x c in pyx pymod exec x pyx pyinit module at home kirr src tools go pygolang x c more stack frames follow gdb f pyx f trace tp new pyx v cls pyx v args pyx v kw at home kirr src tools go pygolang x c pyx incref pyx v kw expected behavior no segfault in autogenerated coce if trace tp new matches newfunc signature environment please complete the following information os linux python version cython version thanks beforehand kirill,0
-14844,18344170075.0,IssuesEvent,2021-10-08 02:27:25,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,SET PASSWORD FOR CURRENT_USER() fails,type/bug type/compatibility sig/execution severity/moderate,"## Bug Report
+### What are the browser(s) and version(s) where you see this issue?
-Please answer these questions before submitting your issue. Thanks!
+Chrome 111.0.5563.65
-### 1. Minimal reproduce step (Required)
+### What are the browser driver(s) and version(s) where you see this issue?
-```sql
-select current_user();
-SET PASSWORD FOR CURRENT_USER() = ""admin""; # fails
-SET PASSWORD for ""root""@""%"" = ""admin""; # works
-```
+Chromedriver 111.0.5563.64
-### 2. What did you expect to see? (Required)
+### Are you using Selenium Grid?
-The statements should both work.
+4.8.1",1.0,"[🐛 Bug]: Gradual reduction in performance when same action is repeated - ### What happened?
-### 3. What did you see instead (Required)
+I am testing an application where there are multiple links (more than 5). I am running a loop and in each loop does below
+1. Verify link details (few texts)
+2. Click on the link (which open up a side panel)
+3. Verify details in side panel
+4. Close side panel
+
+Its observed that on doing so, the webdriver commands response slows down with time heavily
+For instance
+Loop 1
+`[0-0] 2023-03-23T06:30:04.067Z INFO webdriver: COMMAND findElementFromElement(""9623c3f1-dd20-4be3-8f51-96219f951266"", ""xpath"", "".//*[@class='rule-name']//*[text()]"")
+[0-0] 2023-03-23T06:30:04.067Z INFO webdriver: [POST] http://localhost:4444/wd/hub/session/cfb74892c7201126ddcba3bd6eb536a8/element/9623c3f1-dd20-4be3-8f51-96219f951266/element
+[0-0] 2023-03-23T06:30:04.067Z INFO webdriver: DATA { using: 'xpath', value: "".//*[@class='rule-name']//*[text()]"" }
+[0-0] 2023-03-23T06:30:04.144Z INFO webdriver: RESULT {
+[0-0] 'element-6066-11e4-a52e-4f735466cecf': 'e650ee14-fadf-4e4b-8976-5b0f22e51d63'
+[0-0] }
+[0-0] 2023-03-23T06:30:04.149Z INFO webdriver: COMMAND getElementText(""e650ee14-fadf-4e4b-8976-5b0f22e51d63"")
+[0-0] 2023-03-23T06:30:04.149Z INFO webdriver: [GET] http://localhost:4444/wd/hub/session/cfb74892c7201126ddcba3bd6eb536a8/element/e650ee14-fadf-4e4b-8976-5b0f22e51d63/text
+[0-0] 2023-03-23T06:30:04.173Z INFO webdriver: RESULT Global Bypass Lists`
+
+LOOP 4
+`[0-0] value: "".//app-rule-view[child::div[starts-with(@class,'rule')][descendant::*[normalize-space(text())='Domains Bypass']]]""
+[0-0] }
+[0-0] 2023-03-23T06:30:53.114Z INFO webdriver: RESULT {
+[0-0] 'element-6066-11e4-a52e-4f735466cecf': '89d8aced-27a1-454d-ab89-9df2c2b437f5'
+[0-0] }
+[0-0] 2023-03-23T06:30:53.116Z INFO webdriver: COMMAND findElementFromElement(""89d8aced-27a1-454d-ab89-9df2c2b437f5"", ""xpath"", "".//app-pill//*[text()]"")
+[0-0] 2023-03-23T06:30:53.117Z INFO webdriver: [POST] http://localhost:4444/wd/hub/session/cfb74892c7201126ddcba3bd6eb536a8/element/89d8aced-27a1-454d-ab89-9df2c2b437f5/element
+[0-0] 2023-03-23T06:30:53.117Z INFO webdriver: DATA { using: 'xpath', value: './/app-pill//*[text()]' }
+[0-0] 2023-03-23T06:30:54.740Z INFO webdriver: RESULT {
+[0-0] 'element-6066-11e4-a52e-4f735466cecf': 'aa216411-f2f4-407d-915e-f8cce7214337'
+[0-0] }
+[0-0] 2023-03-23T06:30:54.744Z INFO webdriver: COMMAND getElementText(""aa216411-f2f4-407d-915e-f8cce7214337"")
+[0-0] 2023-03-23T06:30:54.744Z INFO webdriver: [GET] http://localhost:4444/wd/hub/session/cfb74892c7201126ddcba3bd6eb536a8/element/aa216411-f2f4-407d-915e-f8cce7214337/text
+[0-0] 2023-03-23T06:30:58.089Z INFO webdriver: RESULT Bypass`
+
+
+The same command to fetch text of the link took 4 seconds in the 4th loop as opposed to fraction of a second
-```sql
-mysql> select current_user();
-+----------------+
-| current_user() |
-+----------------+
-| root@% |
-+----------------+
-1 row in set (0.00 sec)
+### How can we reproduce the issue?
-mysql> SET PASSWORD FOR CURRENT_USER() = ""admin""; # fails
-ERROR 1133 (42000): Can't find any matching row in the user table
-mysql> SET PASSWORD for ""root""@""%"" = ""admin""; # works
-Query OK, 0 rows affected (0.00 sec)
-```
-### 4. What is your TiDB version? (Required)
-
-```sql
-mysql> SELECT tidb_version()\G
-*************************** 1. row ***************************
-tidb_version(): Release Version: v5.3.0-alpha-256-gb0b559f23
-Edition: Community
-Git Commit Hash: b0b559f2389de5e27d0d2e12d2bfae049186b54b
-Git Branch: master
-UTC Build Time: 2021-10-01 14:52:33
-GoVersion: go1.16.7
-Race Enabled: false
-TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
-Check Table Before Drop: false
-1 row in set (0.00 sec)
+```shell
+Unfortunately I could not share the links to reproduce the code but i hope the attached data above helps. If not let me know how i can help
```
-",True,"SET PASSWORD FOR CURRENT_USER() fails - ## Bug Report
-Please answer these questions before submitting your issue. Thanks!
-### 1. Minimal reproduce step (Required)
+### Relevant log output
-```sql
-select current_user();
-SET PASSWORD FOR CURRENT_USER() = ""admin""; # fails
-SET PASSWORD for ""root""@""%"" = ""admin""; # works
+```shell
+[0-0] value: "".//app-rule-view[child::div[starts-with(@class,'rule')][descendant::*[normalize-space(text())='Domains Bypass']]]""
+[0-0] }
+[0-0] 2023-03-23T06:30:53.114Z INFO webdriver: RESULT {
+[0-0] 'element-6066-11e4-a52e-4f735466cecf': '89d8aced-27a1-454d-ab89-9df2c2b437f5'
+[0-0] }
+[0-0] 2023-03-23T06:30:53.116Z INFO webdriver: COMMAND findElementFromElement(""89d8aced-27a1-454d-ab89-9df2c2b437f5"", ""xpath"", "".//app-pill//*[text()]"")
+[0-0] 2023-03-23T06:30:53.117Z INFO webdriver: [POST] http://localhost:4444/wd/hub/session/cfb74892c7201126ddcba3bd6eb536a8/element/89d8aced-27a1-454d-ab89-9df2c2b437f5/element
+[0-0] 2023-03-23T06:30:53.117Z INFO webdriver: DATA { using: 'xpath', value: './/app-pill//*[text()]' }
+[0-0] 2023-03-23T06:30:54.740Z INFO webdriver: RESULT {
+[0-0] 'element-6066-11e4-a52e-4f735466cecf': 'aa216411-f2f4-407d-915e-f8cce7214337'
+[0-0] }
+[0-0] 2023-03-23T06:30:54.744Z INFO webdriver: COMMAND getElementText(""aa216411-f2f4-407d-915e-f8cce7214337"")
+[0-0] 2023-03-23T06:30:54.744Z INFO webdriver: [GET] http://localhost:4444/wd/hub/session/cfb74892c7201126ddcba3bd6eb536a8/element/aa216411-f2f4-407d-915e-f8cce7214337/text
+[0-0] 2023-03-23T06:30:58.089Z INFO webdriver: RESULT Bypass
```
-### 2. What did you expect to see? (Required)
-The statements should both work.
+### Operating System
-### 3. What did you see instead (Required)
+Windows 10
-```sql
-mysql> select current_user();
-+----------------+
-| current_user() |
-+----------------+
-| root@% |
-+----------------+
-1 row in set (0.00 sec)
+### Selenium version
-mysql> SET PASSWORD FOR CURRENT_USER() = ""admin""; # fails
-ERROR 1133 (42000): Can't find any matching row in the user table
-mysql> SET PASSWORD for ""root""@""%"" = ""admin""; # works
-Query OK, 0 rows affected (0.00 sec)
-```
-### 4. What is your TiDB version? (Required)
-
-```sql
-mysql> SELECT tidb_version()\G
-*************************** 1. row ***************************
-tidb_version(): Release Version: v5.3.0-alpha-256-gb0b559f23
-Edition: Community
-Git Commit Hash: b0b559f2389de5e27d0d2e12d2bfae049186b54b
-Git Branch: master
-UTC Build Time: 2021-10-01 14:52:33
-GoVersion: go1.16.7
-Race Enabled: false
-TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
-Check Table Before Drop: false
-1 row in set (0.00 sec)
-```
-",1,set password for current user fails bug report please answer these questions before submitting your issue thanks minimal reproduce step required sql select current user set password for current user admin fails set password for root admin works what did you expect to see required the statements should both work what did you see instead required sql mysql select current user current user root row in set sec mysql set password for current user admin fails error can t find any matching row in the user table mysql set password for root admin works query ok rows affected sec what is your tidb version required sql mysql select tidb version g row tidb version release version alpha edition community git commit hash git branch master utc build time goversion race enabled false tikv min version check table before drop false row in set sec ,1
-260766,8214534148.0,IssuesEvent,2018-09-04 23:56:05,kassy916/Test,https://api.github.com/repos/kassy916/Test,closed,芸人のフォロー/フォロー解除機能,priority:middle ruby,"## WHAT - 何を作るのか?
-ユーザーが芸人をフォロー/フォロー解除する機能
-フォロー数は1000までを予定
+Javascript (WebdriverIO 7.25.2) with Selenium Webdrive 4.8.1
-### フォローボタンの仕様
-フォローしてないときは「フォロー」を表示
-フォローしてるとき→「フォロー中」を表示、マウスオーバーで「フォロー解除」に文字を変更
+### What are the browser(s) and version(s) where you see this issue?
-## WHY - 何故作るのか?
-「自分の好きな芸人さんの情報がほしい」というお客さん(ユーザー)のニーズに答えるため
+Chrome 111.0.5563.65
-## HOW - どうやって作るのか?
+### What are the browser driver(s) and version(s) where you see this issue?
+Chromedriver 111.0.5563.64
+### Are you using Selenium Grid?
-## 参考URL
-- [すごく参考になるページ](https://www.google.com)
-- [ちょっと参考になるページ](https://www.yahoo.com)
+4.8.1",0, gradual reduction in performance when same action is repeated what happened i am testing an application where there are multiple links more than i am running a loop and in each loop does below verify link details few texts click on the link which open up a side panel verify details in side panel close side panel its observed that on doing so the webdriver commands response slows down with time heavily for instance loop info webdriver command findelementfromelement xpath info webdriver info webdriver data using xpath value info webdriver result element fadf info webdriver command getelementtext fadf info webdriver info webdriver result global bypass lists loop value app rule view info webdriver result element info webdriver command findelementfromelement xpath app pill info webdriver info webdriver data using xpath value app pill info webdriver result element info webdriver command getelementtext info webdriver info webdriver result bypass the same command to fetch text of the link took seconds in the loop as opposed to fraction of a second how can we reproduce the issue shell unfortunately i could not share the links to reproduce the code but i hope the attached data above helps if not let me know how i can help relevant log output shell value app rule view info webdriver result element info webdriver command findelementfromelement xpath app pill info webdriver info webdriver data using xpath value app pill info webdriver result element info webdriver command getelementtext info webdriver info webdriver result bypass operating system windows selenium version javascript webdriverio with selenium webdrive what are the browser s and version s where you see this issue chrome what are the browser driver s and version s where you see this issue chromedriver are you using selenium grid ,0
+340964,10280767901.0,IssuesEvent,2019-08-26 06:39:41,UniversityOfHelsinkiCS/fuksilaiterekisteri,https://api.github.com/repos/UniversityOfHelsinkiCS/fuksilaiterekisteri,closed,send email to student after ready for device,enhancement high priority,"When an eligible student has completed their tasks (digiskills and registration), they'll receive an email with instructions to pick up the device",1.0,"send email to student after ready for device - When an eligible student has completed their tasks (digiskills and registration), they'll receive an email with instructions to pick up the device",0,send email to student after ready for device when an eligible student has completed their tasks digiskills and registration they ll receive an email with instructions to pick up the device,0
+7433,9673989573.0,IssuesEvent,2019-05-22 08:53:22,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,DROP USER IF EXISTS behavior difference,type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+This is a similar problem to https://github.com/pingcap/tidb/issues/7867 :
+
+```
+DROP USER IF EXISTS idontexist;
+```
+
+2. What did you expect to see?
+
+MySQL:
+```
+mysql80> DROP USER IF EXISTS idontexist;
+Query OK, 0 rows affected, 1 warning (0.00 sec)
+
+mysql80> SHOW WARNINGS;
++-------+------+---------------------------------------------------+
+| Level | Code | Message |
++-------+------+---------------------------------------------------+
+| Note | 3162 | Authorization ID 'idontexist'@'%' does not exist. |
++-------+------+---------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> DROP USER IF EXISTS idontexist;
+Query OK, 0 rows affected (0.01 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+mysql> select tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v3.0.0-beta.1-109-g7666f688b
+Git Commit Hash: 7666f688b3d91ea84fa6b0a20c2e784fff3c8945
+Git Branch: master
+UTC Build Time: 2019-04-17 05:09:28
+GoVersion: go version go1.12.1 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false
+1 row in set (0.00 sec)
+```",True,"DROP USER IF EXISTS behavior difference - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+This is a similar problem to https://github.com/pingcap/tidb/issues/7867 :
+
+```
+DROP USER IF EXISTS idontexist;
+```
+
+2. What did you expect to see?
+
+MySQL:
+```
+mysql80> DROP USER IF EXISTS idontexist;
+Query OK, 0 rows affected, 1 warning (0.00 sec)
+
+mysql80> SHOW WARNINGS;
++-------+------+---------------------------------------------------+
+| Level | Code | Message |
++-------+------+---------------------------------------------------+
+| Note | 3162 | Authorization ID 'idontexist'@'%' does not exist. |
++-------+------+---------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> DROP USER IF EXISTS idontexist;
+Query OK, 0 rows affected (0.01 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+mysql> select tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v3.0.0-beta.1-109-g7666f688b
+Git Commit Hash: 7666f688b3d91ea84fa6b0a20c2e784fff3c8945
+Git Branch: master
+UTC Build Time: 2019-04-17 05:09:28
+GoVersion: go version go1.12.1 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false
+1 row in set (0.00 sec)
+```",1,drop user if exists behavior difference bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error this is a similar problem to drop user if exists idontexist what did you expect to see mysql drop user if exists idontexist query ok rows affected warning sec show warnings level code message note authorization id idontexist does not exist row in set sec what did you see instead mysql drop user if exists idontexist query ok rows affected sec what version of tidb are you using tidb server v or run select tidb version on tidb mysql select tidb version g row tidb version release version beta git commit hash git branch master utc build time goversion go version linux race enabled false tikv min version alpha check table before drop false row in set sec ,1
+12188,14381020870.0,IssuesEvent,2020-12-02 04:18:50,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,P1-[4.0 bug hunting]-[SQL Plan Management]-NATURAL LEFT JOIN results in incorrect result for <=> operator,component/expression severity/major sig/execution type/bug type/compatibility,"Bug Hunter issue tidb-challenge-program/bug-hunting-issue#5
+---
-## 参考資料
-添付ファイルを参照(ある場合は)
-",1.0,"芸人のフォロー/フォロー解除機能 - ## WHAT - 何を作るのか?
-ユーザーが芸人をフォロー/フォロー解除する機能
-フォロー数は1000までを予定
+Consider the following statements:
+
+```sql
+CREATE TABLE t0(c0 INT);
+CREATE TABLE t1(c0 INT);
+INSERT INTO t0 VALUES (0);
+INSERT INTO t1 VALUES (0);
+SELECT * FROM t1 NATURAL LEFT JOIN t0 WHERE NOT(t0.c0<=>t1.c0); -- expected: {}, actual: {0}
+```
+Unexpectedly, the `SELECT` fetches a row:
+```
+Welcome to the MySQL monitor. Commands end with ; or \g.
+Your MySQL connection id is 1452
+Server version: 5.7.25-TiDB-v4.0.0-beta.2-231-gc66320c46 TiDB Server (Apache License 2.0), MySQL 5.7 compatible
+
+Copyright (c) 2000, 2020, Oracle and/or its affiliates. All rights reserved.
+
+Oracle is a registered trademark of Oracle Corporation and/or its
+affiliates. Other names may be trademarks of their respective
+owners.
+
+Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
+
+mysql> CREATE TABLE t0(c0 INT);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> CREATE TABLE t1(c0 INT);
+Query OK, 0 rows affected (0.00 sec)
+
+mysql> INSERT INTO t0 VALUES (0);
+Query OK, 1 row affected (0.00 sec)
+
+mysql> INSERT INTO t1 VALUES (0);
+Query OK, 1 row affected (0.00 sec)
+
+mysql> SELECT * FROM t1 NATURAL LEFT JOIN t0 WHERE NOT(t0.c0<=>t1.c0); -- expected: {}, actual: {0}
++------+
+| c0 |
++------+
+| 0 |
++------+
+1 row in set (0.00 sec)
+```
+
+ Interestingly, the following query with the negated predicate also fetches a row, which is expected:
+```sql
+SELECT t1.c0 FROM t1 NATURAL LEFT JOIN t0 WHERE t0.c0<=>t1.c0 -- {0}
+```
+I double-checked with MySQL 8.0.19, which does not fetch a row for the first query, as expected:
+```
+Welcome to the MySQL monitor. Commands end with ; or \g.
+Your MySQL connection id is 14
+Server version: 8.0.19 MySQL Community Server - GPL
+
+Copyright (c) 2000, 2020, Oracle and/or its affiliates. All rights reserved.
+
+Oracle is a registered trademark of Oracle Corporation and/or its
+affiliates. Other names may be trademarks of their respective
+owners.
+
+Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
+
+mysql> CREATE TABLE t0(c0 INT);
+Query OK, 0 rows affected (0.04 sec)
+
+mysql> CREATE TABLE t1(c0 INT);
+Query OK, 0 rows affected (0.04 sec)
+
+mysql> INSERT INTO t0 VALUES (0);
+Query OK, 1 row affected (0.01 sec)
+
+mysql> INSERT INTO t1 VALUES (0);
+Query OK, 1 row affected (0.01 sec)
+
+mysql> SELECT * FROM t1 NATURAL LEFT JOIN t0 WHERE NOT(t0.c0<=>t1.c0); -- expected: {}, actual: {0}
+Empty set (0.00 sec)
+```
+Environment:
+```
+| Release Version: v4.0.0-beta.2-231-gc66320c46
+Git Commit Hash: c66320c46456c0d5b23b3b0403be6b9f8227d6d8
+Git Branch: master
+UTC Build Time: 2020-04-14 11:12:29
+GoVersion: go1.13.4
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false |
+```
+I propose P0 as a bug level, since it matches the following description: `wrong results returned by the query, and inconsistent results returned by the SQL output`.",True,"P1-[4.0 bug hunting]-[SQL Plan Management]-NATURAL LEFT JOIN results in incorrect result for <=> operator - Bug Hunter issue tidb-challenge-program/bug-hunting-issue#5
-### フォローボタンの仕様
-フォローしてないときは「フォロー」を表示
-フォローしてるとき→「フォロー中」を表示、マウスオーバーで「フォロー解除」に文字を変更
+---
-## WHY - 何故作るのか?
-「自分の好きな芸人さんの情報がほしい」というお客さん(ユーザー)のニーズに答えるため
+Consider the following statements:
+
+```sql
+CREATE TABLE t0(c0 INT);
+CREATE TABLE t1(c0 INT);
+INSERT INTO t0 VALUES (0);
+INSERT INTO t1 VALUES (0);
+SELECT * FROM t1 NATURAL LEFT JOIN t0 WHERE NOT(t0.c0<=>t1.c0); -- expected: {}, actual: {0}
+```
+Unexpectedly, the `SELECT` fetches a row:
+```
+Welcome to the MySQL monitor. Commands end with ; or \g.
+Your MySQL connection id is 1452
+Server version: 5.7.25-TiDB-v4.0.0-beta.2-231-gc66320c46 TiDB Server (Apache License 2.0), MySQL 5.7 compatible
+
+Copyright (c) 2000, 2020, Oracle and/or its affiliates. All rights reserved.
+
+Oracle is a registered trademark of Oracle Corporation and/or its
+affiliates. Other names may be trademarks of their respective
+owners.
+
+Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
+
+mysql> CREATE TABLE t0(c0 INT);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> CREATE TABLE t1(c0 INT);
+Query OK, 0 rows affected (0.00 sec)
+
+mysql> INSERT INTO t0 VALUES (0);
+Query OK, 1 row affected (0.00 sec)
+
+mysql> INSERT INTO t1 VALUES (0);
+Query OK, 1 row affected (0.00 sec)
+
+mysql> SELECT * FROM t1 NATURAL LEFT JOIN t0 WHERE NOT(t0.c0<=>t1.c0); -- expected: {}, actual: {0}
++------+
+| c0 |
++------+
+| 0 |
++------+
+1 row in set (0.00 sec)
+```
+
+ Interestingly, the following query with the negated predicate also fetches a row, which is expected:
+```sql
+SELECT t1.c0 FROM t1 NATURAL LEFT JOIN t0 WHERE t0.c0<=>t1.c0 -- {0}
+```
+I double-checked with MySQL 8.0.19, which does not fetch a row for the first query, as expected:
+```
+Welcome to the MySQL monitor. Commands end with ; or \g.
+Your MySQL connection id is 14
+Server version: 8.0.19 MySQL Community Server - GPL
+
+Copyright (c) 2000, 2020, Oracle and/or its affiliates. All rights reserved.
+
+Oracle is a registered trademark of Oracle Corporation and/or its
+affiliates. Other names may be trademarks of their respective
+owners.
+
+Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
+
+mysql> CREATE TABLE t0(c0 INT);
+Query OK, 0 rows affected (0.04 sec)
+
+mysql> CREATE TABLE t1(c0 INT);
+Query OK, 0 rows affected (0.04 sec)
+
+mysql> INSERT INTO t0 VALUES (0);
+Query OK, 1 row affected (0.01 sec)
+
+mysql> INSERT INTO t1 VALUES (0);
+Query OK, 1 row affected (0.01 sec)
+
+mysql> SELECT * FROM t1 NATURAL LEFT JOIN t0 WHERE NOT(t0.c0<=>t1.c0); -- expected: {}, actual: {0}
+Empty set (0.00 sec)
+```
+Environment:
+```
+| Release Version: v4.0.0-beta.2-231-gc66320c46
+Git Commit Hash: c66320c46456c0d5b23b3b0403be6b9f8227d6d8
+Git Branch: master
+UTC Build Time: 2020-04-14 11:12:29
+GoVersion: go1.13.4
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false |
+```
+I propose P0 as a bug level, since it matches the following description: `wrong results returned by the query, and inconsistent results returned by the SQL output`.",1, natural left join results in incorrect result for operator bug hunter issue tidb challenge program bug hunting issue consider the following statements sql create table int create table int insert into values insert into values select from natural left join where not expected actual unexpectedly the select fetches a row welcome to the mysql monitor commands end with or g your mysql connection id is server version tidb beta tidb server apache license mysql compatible copyright c oracle and or its affiliates all rights reserved oracle is a registered trademark of oracle corporation and or its affiliates other names may be trademarks of their respective owners type help or h for help type c to clear the current input statement mysql create table int query ok rows affected sec mysql create table int query ok rows affected sec mysql insert into values query ok row affected sec mysql insert into values query ok row affected sec mysql select from natural left join where not expected actual row in set sec interestingly the following query with the negated predicate also fetches a row which is expected sql select from natural left join where i double checked with mysql which does not fetch a row for the first query as expected welcome to the mysql monitor commands end with or g your mysql connection id is server version mysql community server gpl copyright c oracle and or its affiliates all rights reserved oracle is a registered trademark of oracle corporation and or its affiliates other names may be trademarks of their respective owners type help or h for help type c to clear the current input statement mysql create table int query ok rows affected sec mysql create table int query ok rows affected sec mysql insert into values query ok row affected sec mysql insert into values query ok row affected sec mysql select from natural left join where not expected actual empty set sec environment release version beta git commit hash git branch master utc build time goversion race enabled false tikv min version check table before drop false i propose as a bug level since it matches the following description wrong results returned by the query and inconsistent results returned by the sql output ,1
+80806,15586079657.0,IssuesEvent,2021-03-18 01:07:33,Lerer/veracode-async,https://api.github.com/repos/Lerer/veracode-async,opened,Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS),Severity: Medium Veracode,"### Description:
+
+
+This call to javax.servlet.jsp.JspWriter.print() contains a cross-site scripting (XSS) flaw. The application populates the HTTP response with untrusted input, allowing an attacker to embed malicious content, such as Javascript code, which will be executed in the context of the victim's browser. XSS vulnerabilities are commonly exploited to steal or manipulate cookies, modify presentation of content, and compromise confidential information, with new attack vectors being discovered on a regular basis. The first argument to print() contains tainted data from the variable blab_name. The tainted data originated from an earlier call to java.sql.PreparedStatement.executeQuery. The tainted data is directed into an output stream returned by javax.servlet.jsp.JspWriter.
+
+Use contextual escaping on all untrusted data before using it to construct any portion of an HTTP response. The escaping method should be chosen based on the specific use case of the untrusted data, otherwise it may not protect fully against the attack. For example, if the data is being written to the body of an HTML page, use HTML entity escaping; if the data is being written to an attribute, use attribute escaping; etc. Both the OWASP Java Encoder library and the Microsoft AntiXSS library provide contextual escaping methods. For more details on contextual escaping, see https://github.com/OWASP/CheatSheetSeries/blob/master/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.md. In addition, as a best practice, always validate untrusted input to ensure that it conforms to the expected format, using centralized data validation routines when possible.
+
+
+- Veracode issue ID: 296
+- Severity: Medium
+- Location: [/WEB-INF/views/blab.jsp:57](https://github.com/Lerer/veracode-async/search?q=filename:blab.jsp)
+- Issue found on build: 11256520
+- Issue first found at: Tue, 05 Jan 2021 04:12:30 GMT
+- Scanner: Veracode Static Application Security Testing
+
+### Identifiers:
+- [CWE](https://cwe.mitre.org/data/definitions/79.html)
+- [OWASP](https://www.owasp.org/index.php/XSS)
+- [WASC](https://webappsec.pbworks.com/Cross-Site-Scripting)
+- [Supported Cleansers](https://help.veracode.com/reader/4EKhlLSMHm5jC8P8j3XccQ/IiF_rOE79ANbwnZwreSPGA)
-## HOW - どうやって作るのか?
+",1.0,"Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) - ### Description:
+
+
+This call to javax.servlet.jsp.JspWriter.print() contains a cross-site scripting (XSS) flaw. The application populates the HTTP response with untrusted input, allowing an attacker to embed malicious content, such as Javascript code, which will be executed in the context of the victim's browser. XSS vulnerabilities are commonly exploited to steal or manipulate cookies, modify presentation of content, and compromise confidential information, with new attack vectors being discovered on a regular basis. The first argument to print() contains tainted data from the variable blab_name. The tainted data originated from an earlier call to java.sql.PreparedStatement.executeQuery. The tainted data is directed into an output stream returned by javax.servlet.jsp.JspWriter.
+
+Use contextual escaping on all untrusted data before using it to construct any portion of an HTTP response. The escaping method should be chosen based on the specific use case of the untrusted data, otherwise it may not protect fully against the attack. For example, if the data is being written to the body of an HTML page, use HTML entity escaping; if the data is being written to an attribute, use attribute escaping; etc. Both the OWASP Java Encoder library and the Microsoft AntiXSS library provide contextual escaping methods. For more details on contextual escaping, see https://github.com/OWASP/CheatSheetSeries/blob/master/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.md. In addition, as a best practice, always validate untrusted input to ensure that it conforms to the expected format, using centralized data validation routines when possible.
+
+
+- Veracode issue ID: 296
+- Severity: Medium
+- Location: [/WEB-INF/views/blab.jsp:57](https://github.com/Lerer/veracode-async/search?q=filename:blab.jsp)
+- Issue found on build: 11256520
+- Issue first found at: Tue, 05 Jan 2021 04:12:30 GMT
+- Scanner: Veracode Static Application Security Testing
+
+### Identifiers:
+- [CWE](https://cwe.mitre.org/data/definitions/79.html)
+- [OWASP](https://www.owasp.org/index.php/XSS)
+- [WASC](https://webappsec.pbworks.com/Cross-Site-Scripting)
+- [Supported Cleansers](https://help.veracode.com/reader/4EKhlLSMHm5jC8P8j3XccQ/IiF_rOE79ANbwnZwreSPGA)
-## 参考URL
-- [すごく参考になるページ](https://www.google.com)
-- [ちょっと参考になるページ](https://www.yahoo.com)
+",0,improper neutralization of script related html tags in a web page basic xss description this call to javax servlet jsp jspwriter print contains a cross site scripting xss flaw the application populates the http response with untrusted input allowing an attacker to embed malicious content such as javascript code which will be executed in the context of the victim s browser xss vulnerabilities are commonly exploited to steal or manipulate cookies modify presentation of content and compromise confidential information with new attack vectors being discovered on a regular basis the first argument to print contains tainted data from the variable blab name the tainted data originated from an earlier call to java sql preparedstatement executequery the tainted data is directed into an output stream returned by javax servlet jsp jspwriter use contextual escaping on all untrusted data before using it to construct any portion of an http response the escaping method should be chosen based on the specific use case of the untrusted data otherwise it may not protect fully against the attack for example if the data is being written to the body of an html page use html entity escaping if the data is being written to an attribute use attribute escaping etc both the owasp java encoder library and the microsoft antixss library provide contextual escaping methods for more details on contextual escaping see in addition as a best practice always validate untrusted input to ensure that it conforms to the expected format using centralized data validation routines when possible veracode issue id severity medium location issue found on build issue first found at tue jan gmt scanner veracode static application security testing identifiers ,0
+133512,18298919863.0,IssuesEvent,2021-10-05 23:46:04,bsbtd/Teste,https://api.github.com/repos/bsbtd/Teste,opened,"CVE-2019-17531 (High) detected in jackson-databind-2.9.5.jar, jackson-databind-2.6.7.3.jar",security vulnerability,"## CVE-2019-17531 - High Severity Vulnerability
+ Vulnerable Libraries - jackson-databind-2.9.5.jar, jackson-databind-2.6.7.3.jar
+
+jackson-databind-2.9.5.jar
-## 参考資料
-添付ファイルを参照(ある場合は)
-",0,芸人のフォロー/フォロー解除機能 what 何を作るのか? ユーザーが芸人をフォロー/フォロー解除する機能 フォローボタンの仕様 フォローしてないときは「フォロー」を表示 フォローしてるとき→「フォロー中」を表示、マウスオーバーで「フォロー解除」に文字を変更 why 何故作るのか? 「自分の好きな芸人さんの情報がほしい」というお客さん(ユーザー)のニーズに答えるため how どうやって作るのか? 参考url 参考資料 添付ファイルを参照(ある場合は) ,0
-147979,19526236751.0,IssuesEvent,2021-12-30 08:22:24,panasalap/linux-4.1.15,https://api.github.com/repos/panasalap/linux-4.1.15,opened,CVE-2021-28660 (High) detected in linux-stable-rtv4.1.33,security vulnerability,"## CVE-2021-28660 - High Severity Vulnerability
- Vulnerable Library - linux-stable-rtv4.1.33
+
General data-binding functionality for Jackson: works on core streaming API
Path to dependency file: Teste/liferay-portal/modules/etl/talend/talend-runtime/pom.xml
+
Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.5/jackson-databind-2.9.5.jar,/home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.5/jackson-databind-2.9.5.jar,/home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.5/jackson-databind-2.9.5.jar
Path to dependency file: Teste/opentelemetry-java/sdk_contrib/aws_v1_support/build.gradle
+
Path to vulnerable library: /home/wss-scanner/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.6.7.3/c8bad9f57a5d298280f8bc0efcb7bf8393a41534/jackson-databind-2.6.7.3.jar
-rtw_wx_set_scan in drivers/staging/rtl8188eu/os_dep/ioctl_linux.c in the Linux kernel through 5.11.6 allows writing beyond the end of the ->ssid[] array. NOTE: from the perspective of kernel.org releases, CVE IDs are not normally used for drivers/staging/* (unfinished work); however, system integrators may have situations in which a drivers/staging issue is relevant to their own customer base.
+A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the apache-log4j-extra (version 1.2.x) jar in the classpath, and an attacker can provide a JNDI service to access, it is possible to make the service execute a malicious payload.
-
***
-Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",True,"CVE-2021-28660 (High) detected in linux-stable-rtv4.1.33 - ## CVE-2021-28660 - High Severity Vulnerability
- Vulnerable Library - linux-stable-rtv4.1.33
+Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",True,"CVE-2019-17531 (High) detected in jackson-databind-2.9.5.jar, jackson-databind-2.6.7.3.jar - ## CVE-2019-17531 - High Severity Vulnerability
+ Vulnerable Libraries - jackson-databind-2.9.5.jar, jackson-databind-2.6.7.3.jar
Path to dependency file: Teste/liferay-portal/modules/etl/talend/talend-runtime/pom.xml
+
Path to vulnerable library: /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.5/jackson-databind-2.9.5.jar,/home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.5/jackson-databind-2.9.5.jar,/home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.5/jackson-databind-2.9.5.jar
Path to dependency file: Teste/opentelemetry-java/sdk_contrib/aws_v1_support/build.gradle
+
Path to vulnerable library: /home/wss-scanner/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.6.7.3/c8bad9f57a5d298280f8bc0efcb7bf8393a41534/jackson-databind-2.6.7.3.jar
-rtw_wx_set_scan in drivers/staging/rtl8188eu/os_dep/ioctl_linux.c in the Linux kernel through 5.11.6 allows writing beyond the end of the ->ssid[] array. NOTE: from the perspective of kernel.org releases, CVE IDs are not normally used for drivers/staging/* (unfinished work); however, system integrators may have situations in which a drivers/staging issue is relevant to their own customer base.
+A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the apache-log4j-extra (version 1.2.x) jar in the classpath, and an attacker can provide a JNDI service to access, it is possible to make the service execute a malicious payload.
-
***
-Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",0,cve high detected in linux stable cve high severity vulnerability vulnerable library linux stable julia cartwright s fork of linux stable rt git library home page a href found in head commit a href found in base branch master vulnerable source files drivers staging os dep ioctl linux c drivers staging os dep ioctl linux c vulnerability details rtw wx set scan in drivers staging os dep ioctl linux c in the linux kernel through allows writing beyond the end of the ssid array note from the perspective of kernel org releases cve ids are not normally used for drivers staging unfinished work however system integrators may have situations in which a drivers staging issue is relevant to their own customer base publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required low user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource ,0
-115502,14789798427.0,IssuesEvent,2021-01-12 11:04:36,mutwo-org/mutwo,https://api.github.com/repos/mutwo-org/mutwo,opened,set doc string standard,design documentation enhancement,"@timpauli if we want to use [spinx](https://www.sphinx-doc.org) for building the documentation, it may be a good idea to use their standard for doc string formation (to have access to their automatic markdown) as it is described [here](https://sphinx-rtd-tutorial.readthedocs.io/en/latest/docstrings.html). What do you think?",1.0,"set doc string standard - @timpauli if we want to use [spinx](https://www.sphinx-doc.org) for building the documentation, it may be a good idea to use their standard for doc string formation (to have access to their automatic markdown) as it is described [here](https://sphinx-rtd-tutorial.readthedocs.io/en/latest/docstrings.html). What do you think?",0,set doc string standard timpauli if we want to use for building the documentation it may be a good idea to use their standard for doc string formation to have access to their automatic markdown as it is described what do you think ,0
-7003,9292889746.0,IssuesEvent,2019-03-22 05:37:25,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,TiDB doesn't handle `signed + unsigned` properly ,type/compatibility,"## Bug Report
-
-Please answer these questions before submitting your issue. Thanks!
-
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-`select cast(1 as signed) + cast(9223372036854775807 as unsigned);`
-
-2. What did you expect to see?
-```
-mysql> select cast(1 as signed) + cast(9223372036854775807 as unsigned);
-+-----------------------------------------------------------+
-| cast(1 as signed) + cast(9223372036854775807 as unsigned) |
-+-----------------------------------------------------------+
-| 9223372036854775808 |
-+-----------------------------------------------------------+
-```
-
-
-
-
-3. What did you see instead?
-```
-mysql> select cast(1 as signed) + cast(9223372036854775807 as unsigned);
-ERROR 1690 (22003): BIGINT UNSIGNED value is out of range in '(1 + 9223372036854775807)'
-```
-
-
+Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",0,cve high detected in jackson databind jar jackson databind jar cve high severity vulnerability vulnerable libraries jackson databind jar jackson databind jar jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file teste liferay portal modules etl talend talend runtime pom xml path to vulnerable library home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy components api jar root library daikon jar x jackson databind jar vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file teste opentelemetry java sdk contrib aws support build gradle path to vulnerable library home wss scanner gradle caches modules files com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy aws java sdk jar root library jmespath java jar x jackson databind jar vulnerable library found in head commit a href vulnerability details a polymorphic typing issue was discovered in fasterxml jackson databind through when default typing is enabled either globally or for a specific property for an externally exposed json endpoint and the service has the apache extra version x jar in the classpath and an attacker can provide a jndi service to access it is possible to make the service execute a malicious payload publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource ,0
+6689,8967144933.0,IssuesEvent,2019-01-29 01:59:17,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Float'precision is different from MySQL,type/compatibility,"## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+```
+CREATE TABLE test_float (
+ uuid char(32) NOT NULL,
+ average float DEFAULT '0',
+ PRIMARY KEY (uuid)
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
+
+insert into test_float value('0a6f9d012f98467f8e671e9870044528', 208.867);
+
+SELECT
+ CONCAT_WS( ',', average)
+FROM
+ test_float
+WHERE
+ uuid = '0a6f9d012f98467f8e671e9870044528';
+```
++ MySQL OUTPUT:
+```
++----------------------------+
+| CONCAT_WS( ',', `average`) |
++----------------------------+
+| 208.867 |
++----------------------------+
+```
+
++ TiDB OUTPUT:
+```
++----------------------------+
+| CONCAT_WS( ',', `average`) |
++----------------------------+
+| 208.86700439 |
++----------------------------+
+```
+ + [Related Issues](https://github.com/pingcap/tidb/issues/6882)",True,"Float'precision is different from MySQL - ## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+```
+CREATE TABLE test_float (
+ uuid char(32) NOT NULL,
+ average float DEFAULT '0',
+ PRIMARY KEY (uuid)
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
+
+insert into test_float value('0a6f9d012f98467f8e671e9870044528', 208.867);
+
+SELECT
+ CONCAT_WS( ',', average)
+FROM
+ test_float
+WHERE
+ uuid = '0a6f9d012f98467f8e671e9870044528';
+```
++ MySQL OUTPUT:
+```
++----------------------------+
+| CONCAT_WS( ',', `average`) |
++----------------------------+
+| 208.867 |
++----------------------------+
+```
+
++ TiDB OUTPUT:
+```
++----------------------------+
+| CONCAT_WS( ',', `average`) |
++----------------------------+
+| 208.86700439 |
++----------------------------+
+```
+ + [Related Issues](https://github.com/pingcap/tidb/issues/6882)",1,float precision is different from mysql feature request is your feature request related to a problem please describe create table test float uuid char not null average float default primary key uuid engine innodb default charset insert into test float value select concat ws average from test float where uuid mysql output concat ws average tidb output concat ws average ,1
+202874,15305191154.0,IssuesEvent,2021-02-24 17:48:29,cockroachdb/cockroach,https://api.github.com/repos/cockroachdb/cockroach,closed,roachtest: tpccbench/nodes=9/cpu=4/chaos/partition failed,C-test-failure O-roachtest O-robot branch-release-20.2 release-blocker,"[(roachtest).tpccbench/nodes=9/cpu=4/chaos/partition failed](https://teamcity.cockroachdb.com/viewLog.html?buildId=2657161&tab=buildLog) on [release-20.2@8c79e2bc4b35d36c8527f4c40c974f03d9034f46](https://github.com/cockroachdb/cockroach/commits/8c79e2bc4b35d36c8527f4c40c974f03d9034f46):
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-```
-mysql> select tidb_version();
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v3.0.0-beta-231-g20463d6-dirty
-Git Commit Hash: 20463d6da90fdf12c0d9d18c15dc33a78334882d
-Git Branch: master
-UTC Build Time: 2019-03-20 03:32:11
-GoVersion: go version go1.12 linux/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false |
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-1 row in set (0.00 sec)
```
+The test failed on branch=release-20.2, cloud=gce:
+test artifacts and logs in: /home/agent/work/.go/src/github.com/cockroachdb/cockroach/artifacts/tpccbench/nodes=9/cpu=4/chaos/partition/run_1
+ cluster.go:2654,tpcc.go:735,tpcc.go:576,test_runner.go:755: monitor failure: monitor task failed: failed with output ""./workload: /lib/x86_64-linux-gnu/libm.so.6: version `GLIBC_2.29' not found (required by ./workload)\nError: COMMAND_PROBLEM: exit status 1\n(1) COMMAND_PROBLEM\nWraps: (2) Node 10. Command with error:\n | ```\n | ./workload run tpcc --warehouses=2000 --workers=2000 --max-rate=1000 --wait=false --duration=16m0s --scatter --tolerate-errors {pgurl:1-9}\n | ```\nWraps: (3) exit status 1\nError types: (1) errors.Cmd (2) *hintdetail.withDetail (3) *exec.ExitError\n"": /home/agent/work/.go/src/github.com/cockroachdb/cockroach/bin/roachprod run teamcity-2657161-1612856692-131-n10cpu4:10 -- ./workload run tpcc --warehouses=2000 --workers=2000 --max-rate=1000 --wait=false --duration=16m0s --scatter --tolerate-errors {pgurl:1-9}: exit status 20
+ (1) attached stack trace
+ -- stack trace:
+ | main.(*monitor).WaitE
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/cluster.go:2642
+ | main.(*monitor).Wait
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/cluster.go:2650
+ | main.runTPCCBench
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/tpcc.go:735
+ | main.registerTPCCBenchSpec.func1
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/tpcc.go:576
+ | main.(*testRunner).runTest.func2
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/test_runner.go:755
+ Wraps: (2) monitor failure
+ Wraps: (3) attached stack trace
+ -- stack trace:
+ | main.(*monitor).wait.func2
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/cluster.go:2698
+ Wraps: (4) monitor task failed
+ Wraps: (5) attached stack trace
+ -- stack trace:
+ | main.loadTPCCBench
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/tpcc.go:663
+ | [...repeated from below...]
+ Wraps: (6) failed with output ""./workload: /lib/x86_64-linux-gnu/libm.so.6: version `GLIBC_2.29' not found (required by ./workload)\nError: COMMAND_PROBLEM: exit status 1\n(1) COMMAND_PROBLEM\nWraps: (2) Node 10. Command with error:\n | ```\n | ./workload run tpcc --warehouses=2000 --workers=2000 --max-rate=1000 --wait=false --duration=16m0s --scatter --tolerate-errors {pgurl:1-9}\n | ```\nWraps: (3) exit status 1\nError types: (1) errors.Cmd (2) *hintdetail.withDetail (3) *exec.ExitError\n""
+ Wraps: (7) attached stack trace
+ -- stack trace:
+ | main.execCmdWithBuffer
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/cluster.go:564
+ | main.(*cluster).RunWithBuffer
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/cluster.go:2311
+ | main.loadTPCCBench
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/tpcc.go:662
+ | main.runTPCCBench.func1
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/tpcc.go:733
+ | main.(*monitor).Go.func1
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/cluster.go:2632
+ | golang.org/x/sync/errgroup.(*Group).Go.func1
+ | /home/agent/work/.go/pkg/mod/golang.org/x/sync@v0.0.0-20190911185100-cd5d95a43a6e/errgroup/errgroup.go:57
+ | runtime.goexit
+ | /usr/local/go/src/runtime/asm_amd64.s:1374
+ Wraps: (8) /home/agent/work/.go/src/github.com/cockroachdb/cockroach/bin/roachprod run teamcity-2657161-1612856692-131-n10cpu4:10 -- ./workload run tpcc --warehouses=2000 --workers=2000 --max-rate=1000 --wait=false --duration=16m0s --scatter --tolerate-errors {pgurl:1-9}
+ Wraps: (9) exit status 20
+ Error types: (1) *withstack.withStack (2) *errutil.withPrefix (3) *withstack.withStack (4) *errutil.withPrefix (5) *withstack.withStack (6) *errutil.withPrefix (7) *withstack.withStack (8) *errutil.withPrefix (9) *exec.ExitError
-",True,"TiDB doesn't handle `signed + unsigned` properly - ## Bug Report
-
-Please answer these questions before submitting your issue. Thanks!
-
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-`select cast(1 as signed) + cast(9223372036854775807 as unsigned);`
-
-2. What did you expect to see?
-```
-mysql> select cast(1 as signed) + cast(9223372036854775807 as unsigned);
-+-----------------------------------------------------------+
-| cast(1 as signed) + cast(9223372036854775807 as unsigned) |
-+-----------------------------------------------------------+
-| 9223372036854775808 |
-+-----------------------------------------------------------+
```
+More
+
+Artifacts: [/tpccbench/nodes=9/cpu=4/chaos/partition](https://teamcity.cockroachdb.com/viewLog.html?buildId=2657161&tab=artifacts#/tpccbench/nodes=9/cpu=4/chaos/partition)
+[See this test on roachdash](https://roachdash.crdb.dev/?filter=status%3Aopen+t%3A.%2Atpccbench%2Fnodes%3D9%2Fcpu%3D4%2Fchaos%2Fpartition.%2A&sort=title&restgroup=false&display=lastcommented+project)
+powered by [pkg/cmd/internal/issues](https://github.com/cockroachdb/cockroach/tree/master/pkg/cmd/internal/issues)
+",2.0,"roachtest: tpccbench/nodes=9/cpu=4/chaos/partition failed - [(roachtest).tpccbench/nodes=9/cpu=4/chaos/partition failed](https://teamcity.cockroachdb.com/viewLog.html?buildId=2657161&tab=buildLog) on [release-20.2@8c79e2bc4b35d36c8527f4c40c974f03d9034f46](https://github.com/cockroachdb/cockroach/commits/8c79e2bc4b35d36c8527f4c40c974f03d9034f46):
-3. What did you see instead?
```
-mysql> select cast(1 as signed) + cast(9223372036854775807 as unsigned);
-ERROR 1690 (22003): BIGINT UNSIGNED value is out of range in '(1 + 9223372036854775807)'
+The test failed on branch=release-20.2, cloud=gce:
+test artifacts and logs in: /home/agent/work/.go/src/github.com/cockroachdb/cockroach/artifacts/tpccbench/nodes=9/cpu=4/chaos/partition/run_1
+ cluster.go:2654,tpcc.go:735,tpcc.go:576,test_runner.go:755: monitor failure: monitor task failed: failed with output ""./workload: /lib/x86_64-linux-gnu/libm.so.6: version `GLIBC_2.29' not found (required by ./workload)\nError: COMMAND_PROBLEM: exit status 1\n(1) COMMAND_PROBLEM\nWraps: (2) Node 10. Command with error:\n | ```\n | ./workload run tpcc --warehouses=2000 --workers=2000 --max-rate=1000 --wait=false --duration=16m0s --scatter --tolerate-errors {pgurl:1-9}\n | ```\nWraps: (3) exit status 1\nError types: (1) errors.Cmd (2) *hintdetail.withDetail (3) *exec.ExitError\n"": /home/agent/work/.go/src/github.com/cockroachdb/cockroach/bin/roachprod run teamcity-2657161-1612856692-131-n10cpu4:10 -- ./workload run tpcc --warehouses=2000 --workers=2000 --max-rate=1000 --wait=false --duration=16m0s --scatter --tolerate-errors {pgurl:1-9}: exit status 20
+ (1) attached stack trace
+ -- stack trace:
+ | main.(*monitor).WaitE
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/cluster.go:2642
+ | main.(*monitor).Wait
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/cluster.go:2650
+ | main.runTPCCBench
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/tpcc.go:735
+ | main.registerTPCCBenchSpec.func1
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/tpcc.go:576
+ | main.(*testRunner).runTest.func2
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/test_runner.go:755
+ Wraps: (2) monitor failure
+ Wraps: (3) attached stack trace
+ -- stack trace:
+ | main.(*monitor).wait.func2
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/cluster.go:2698
+ Wraps: (4) monitor task failed
+ Wraps: (5) attached stack trace
+ -- stack trace:
+ | main.loadTPCCBench
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/tpcc.go:663
+ | [...repeated from below...]
+ Wraps: (6) failed with output ""./workload: /lib/x86_64-linux-gnu/libm.so.6: version `GLIBC_2.29' not found (required by ./workload)\nError: COMMAND_PROBLEM: exit status 1\n(1) COMMAND_PROBLEM\nWraps: (2) Node 10. Command with error:\n | ```\n | ./workload run tpcc --warehouses=2000 --workers=2000 --max-rate=1000 --wait=false --duration=16m0s --scatter --tolerate-errors {pgurl:1-9}\n | ```\nWraps: (3) exit status 1\nError types: (1) errors.Cmd (2) *hintdetail.withDetail (3) *exec.ExitError\n""
+ Wraps: (7) attached stack trace
+ -- stack trace:
+ | main.execCmdWithBuffer
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/cluster.go:564
+ | main.(*cluster).RunWithBuffer
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/cluster.go:2311
+ | main.loadTPCCBench
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/tpcc.go:662
+ | main.runTPCCBench.func1
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/tpcc.go:733
+ | main.(*monitor).Go.func1
+ | /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachtest/cluster.go:2632
+ | golang.org/x/sync/errgroup.(*Group).Go.func1
+ | /home/agent/work/.go/pkg/mod/golang.org/x/sync@v0.0.0-20190911185100-cd5d95a43a6e/errgroup/errgroup.go:57
+ | runtime.goexit
+ | /usr/local/go/src/runtime/asm_amd64.s:1374
+ Wraps: (8) /home/agent/work/.go/src/github.com/cockroachdb/cockroach/bin/roachprod run teamcity-2657161-1612856692-131-n10cpu4:10 -- ./workload run tpcc --warehouses=2000 --workers=2000 --max-rate=1000 --wait=false --duration=16m0s --scatter --tolerate-errors {pgurl:1-9}
+ Wraps: (9) exit status 20
+ Error types: (1) *withstack.withStack (2) *errutil.withPrefix (3) *withstack.withStack (4) *errutil.withPrefix (5) *withstack.withStack (6) *errutil.withPrefix (7) *withstack.withStack (8) *errutil.withPrefix (9) *exec.ExitError
+
```
+More
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-```
-mysql> select tidb_version();
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v3.0.0-beta-231-g20463d6-dirty
-Git Commit Hash: 20463d6da90fdf12c0d9d18c15dc33a78334882d
-Git Branch: master
-UTC Build Time: 2019-03-20 03:32:11
-GoVersion: go version go1.12 linux/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false |
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-1 row in set (0.00 sec)
+Artifacts: [/tpccbench/nodes=9/cpu=4/chaos/partition](https://teamcity.cockroachdb.com/viewLog.html?buildId=2657161&tab=artifacts#/tpccbench/nodes=9/cpu=4/chaos/partition)
+
+[See this test on roachdash](https://roachdash.crdb.dev/?filter=status%3Aopen+t%3A.%2Atpccbench%2Fnodes%3D9%2Fcpu%3D4%2Fchaos%2Fpartition.%2A&sort=title&restgroup=false&display=lastcommented+project)
+powered by [pkg/cmd/internal/issues](https://github.com/cockroachdb/cockroach/tree/master/pkg/cmd/internal/issues)
+",0,roachtest tpccbench nodes cpu chaos partition failed on the test failed on branch release cloud gce test artifacts and logs in home agent work go src github com cockroachdb cockroach artifacts tpccbench nodes cpu chaos partition run cluster go tpcc go tpcc go test runner go monitor failure monitor task failed failed with output workload lib linux gnu libm so version glibc not found required by workload nerror command problem exit status n command problem nwraps node command with error n n workload run tpcc warehouses workers max rate wait false duration scatter tolerate errors pgurl n nwraps exit status nerror types errors cmd hintdetail withdetail exec exiterror n home agent work go src github com cockroachdb cockroach bin roachprod run teamcity workload run tpcc warehouses workers max rate wait false duration scatter tolerate errors pgurl exit status attached stack trace stack trace main monitor waite home agent work go src github com cockroachdb cockroach pkg cmd roachtest cluster go main monitor wait home agent work go src github com cockroachdb cockroach pkg cmd roachtest cluster go main runtpccbench home agent work go src github com cockroachdb cockroach pkg cmd roachtest tpcc go main registertpccbenchspec home agent work go src github com cockroachdb cockroach pkg cmd roachtest tpcc go main testrunner runtest home agent work go src github com cockroachdb cockroach pkg cmd roachtest test runner go wraps monitor failure wraps attached stack trace stack trace main monitor wait home agent work go src github com cockroachdb cockroach pkg cmd roachtest cluster go wraps monitor task failed wraps attached stack trace stack trace main loadtpccbench home agent work go src github com cockroachdb cockroach pkg cmd roachtest tpcc go wraps failed with output workload lib linux gnu libm so version glibc not found required by workload nerror command problem exit status n command problem nwraps node command with error n n workload run tpcc warehouses workers max rate wait false duration scatter tolerate errors pgurl n nwraps exit status nerror types errors cmd hintdetail withdetail exec exiterror n wraps attached stack trace stack trace main execcmdwithbuffer home agent work go src github com cockroachdb cockroach pkg cmd roachtest cluster go main cluster runwithbuffer home agent work go src github com cockroachdb cockroach pkg cmd roachtest cluster go main loadtpccbench home agent work go src github com cockroachdb cockroach pkg cmd roachtest tpcc go main runtpccbench home agent work go src github com cockroachdb cockroach pkg cmd roachtest tpcc go main monitor go home agent work go src github com cockroachdb cockroach pkg cmd roachtest cluster go golang org x sync errgroup group go home agent work go pkg mod golang org x sync errgroup errgroup go runtime goexit usr local go src runtime asm s wraps home agent work go src github com cockroachdb cockroach bin roachprod run teamcity workload run tpcc warehouses workers max rate wait false duration scatter tolerate errors pgurl wraps exit status error types withstack withstack errutil withprefix withstack withstack errutil withprefix withstack withstack errutil withprefix withstack withstack errutil withprefix exec exiterror more artifacts powered by ,0
+140898,11382515442.0,IssuesEvent,2020-01-29 02:05:36,OpenAPITools/openapi-generator,https://api.github.com/repos/OpenAPITools/openapi-generator,closed,[build] Move setup-related scripting to external scripts in the repo,Enhancement: CI/Test,"##### Description
+
+.travis.yml, appveyor.yml, circle.yml, and shippable.yml have some shared logic which would be more easily maintained if they referenced local shell scripts for preparation/installation work.
+
+This is a minor improvement which could also help reduce errors. For example, in multi-line `if` statements inlined in yaml files, it's easy to miss trailing semicolons.",1.0,"[build] Move setup-related scripting to external scripts in the repo - ##### Description
+
+.travis.yml, appveyor.yml, circle.yml, and shippable.yml have some shared logic which would be more easily maintained if they referenced local shell scripts for preparation/installation work.
+
+This is a minor improvement which could also help reduce errors. For example, in multi-line `if` statements inlined in yaml files, it's easy to miss trailing semicolons.",0, move setup related scripting to external scripts in the repo description travis yml appveyor yml circle yml and shippable yml have some shared logic which would be more easily maintained if they referenced local shell scripts for preparation installation work this is a minor improvement which could also help reduce errors for example in multi line if statements inlined in yaml files it s easy to miss trailing semicolons ,0
+295839,9101415017.0,IssuesEvent,2019-02-20 11:02:01,ipfs/ipfs-cluster,https://api.github.com/repos/ipfs/ipfs-cluster,closed,"Support PinPath, UnpinPath (resolve before pinning)",difficulty:easy enhancement/feature in progress priority:medium ready,"
+
+#### Basic information
+
+* [x] Type (mark as appropiate):
+ * [ ] Bug
+ * [x] Feature request
+ * [ ] Enhancement
+
+#### Description
+
+Currently, Cluster operates on CIDs. `Pin()`, `Unpin()` work given a CID, but not given a path like `/ipfs//something/else`, or `/ipns/something`.
+
+The main component should provide `PinPath` and `UnpinPath` at least, and resolution to obtain the CID should happen via the IPFS daemon (ipfs connector component).
+
+Thus, we'd have `func PinPath(path string, p api.Pin) error` and `func UnpinPath(path string`)`.
+
+The only thing these functions would do is to resolve the path to a *cid.Cid and call the original functions. Resolving requires modifying the IPFSConnector interface and implementation with a new method.
+
+---
+The second part of this PR is to support path-pinning and unpinning in the `api/rest` component, the `api/rest/client` and have `ipfs-cluster-ctl pin add` and `pin rm` take paths just as they take Cids.
+
+The `POST /pins/{hash}` endpoint is used to Pin a Cid. Perhaps it is worth to implement path-pinning by supporting `POST /pins/ipfs/` and `POST /pins/ipns/path`. Same for Unpin (`DELETE`).
+
+The `api/rest` route handler should realize and call `Pin` (as now) or `PinPath` (a new rpc method), as needed.
+
+Note that https://godoc.org/github.com/ipfs/go-ipfs-path#ParsePath is here to help, and that we should use `IsJustAKey()` to shortcut paths like `/ipfs/` to a *cid.Cid directly, without needing to resolve those.
+
+
+
+https://godoc.org/github.com/ipfs/ipfs-cluster/api#Pin
+
+",1.0,"Support PinPath, UnpinPath (resolve before pinning) -
+
+#### Basic information
+
+* [x] Type (mark as appropiate):
+ * [ ] Bug
+ * [x] Feature request
+ * [ ] Enhancement
+
+#### Description
+
+Currently, Cluster operates on CIDs. `Pin()`, `Unpin()` work given a CID, but not given a path like `/ipfs//something/else`, or `/ipns/something`.
+
+The main component should provide `PinPath` and `UnpinPath` at least, and resolution to obtain the CID should happen via the IPFS daemon (ipfs connector component).
+
+Thus, we'd have `func PinPath(path string, p api.Pin) error` and `func UnpinPath(path string`)`.
+
+The only thing these functions would do is to resolve the path to a *cid.Cid and call the original functions. Resolving requires modifying the IPFSConnector interface and implementation with a new method.
+
+---
+The second part of this PR is to support path-pinning and unpinning in the `api/rest` component, the `api/rest/client` and have `ipfs-cluster-ctl pin add` and `pin rm` take paths just as they take Cids.
+
+The `POST /pins/{hash}` endpoint is used to Pin a Cid. Perhaps it is worth to implement path-pinning by supporting `POST /pins/ipfs/` and `POST /pins/ipns/path`. Same for Unpin (`DELETE`).
+
+The `api/rest` route handler should realize and call `Pin` (as now) or `PinPath` (a new rpc method), as needed.
+
+Note that https://godoc.org/github.com/ipfs/go-ipfs-path#ParsePath is here to help, and that we should use `IsJustAKey()` to shortcut paths like `/ipfs/` to a *cid.Cid directly, without needing to resolve those.
+
+
+
+https://godoc.org/github.com/ipfs/ipfs-cluster/api#Pin
+
+",0,support pinpath unpinpath resolve before pinning hello you are about to create an issue in ipfs cluster we ask you to please read and complete the following template note it might be easier to just click on these check boxes right after creating the issue basic information type mark as appropiate bug feature request enhancement description currently cluster operates on cids pin unpin work given a cid but not given a path like ipfs something else or ipns something the main component should provide pinpath and unpinpath at least and resolution to obtain the cid should happen via the ipfs daemon ipfs connector component thus we d have func pinpath path string p api pin error and func unpinpath path string the only thing these functions would do is to resolve the path to a cid cid and call the original functions resolving requires modifying the ipfsconnector interface and implementation with a new method the second part of this pr is to support path pinning and unpinning in the api rest component the api rest client and have ipfs cluster ctl pin add and pin rm take paths just as they take cids the post pins hash endpoint is used to pin a cid perhaps it is worth to implement path pinning by supporting post pins ipfs and post pins ipns path same for unpin delete the api rest route handler should realize and call pin as now or pinpath a new rpc method as needed note that is here to help and that we should use isjustakey to shortcut paths like ipfs to a cid cid directly without needing to resolve those include a description of the problem or the feature when reporting a bug please try to include what you were doing when you experienced the bug any relevant log messages and the peers they belong to if you have logs for several peers when possible steps to reproduce the bug ,0
+25704,7741478064.0,IssuesEvent,2018-05-29 05:59:54,curl/curl,https://api.github.com/repos/curl/curl,closed,Hint when compiling with another openssl library,SSL/TLS build documentation,"I would like to provide an information which could be published in the installation manual in order to help others.
+
+When curl is compiled with another openssl version than the system default it is often not possible to set the library path from the new openssl version in `/etc/ld.so.conf` because this may break the system.
+
+In this case the `configure` script fails running `conftest` when it is using the openssl libraries with `./conftest: error while loading shared libraries: libssl.so.1.1: cannot open shared object file: No such file or directory`.
+
+The only way in this case is to use the `rpath` linker option.
+
+**_Solution:_**
+Before running `./configure` execute `export LDFLAGS=""-Wl,--rpath=/""`",1.0,"Hint when compiling with another openssl library - I would like to provide an information which could be published in the installation manual in order to help others.
+
+When curl is compiled with another openssl version than the system default it is often not possible to set the library path from the new openssl version in `/etc/ld.so.conf` because this may break the system.
+
+In this case the `configure` script fails running `conftest` when it is using the openssl libraries with `./conftest: error while loading shared libraries: libssl.so.1.1: cannot open shared object file: No such file or directory`.
+
+The only way in this case is to use the `rpath` linker option.
+
+**_Solution:_**
+Before running `./configure` execute `export LDFLAGS=""-Wl,--rpath=/""`",0,hint when compiling with another openssl library i would like to provide an information which could be published in the installation manual in order to help others when curl is compiled with another openssl version than the system default it is often not possible to set the library path from the new openssl version in etc ld so conf because this may break the system in this case the configure script fails running conftest when it is using the openssl libraries with conftest error while loading shared libraries libssl so cannot open shared object file no such file or directory the only way in this case is to use the rpath linker option solution before running configure execute export ldflags wl rpath ,0
+104446,8972527879.0,IssuesEvent,2019-01-29 18:32:04,SunwellWoW/Sunwell-TBC-Bugtracker,https://api.github.com/repos/SunwellWoW/Sunwell-TBC-Bugtracker,closed,[Quest] Who Are They?,Quest/RP Resolved - retest required,"Description:
+If you lose the disguise, you can't get new one from quest giver Private Weeks
+
+How it works:
+If you lost the disguise, you can't get new one from quest giver Private Weeks. All you can do is to abandon quest and get it again.
+
+How it should work:
+He should give you new disguise buff in case you lost it.
+
+Source (you should point out proofs of your report, please give us some source):
+https://www.wowhead.com/quest=10040/who-are-they#comments",1.0,"[Quest] Who Are They? - Description:
+If you lose the disguise, you can't get new one from quest giver Private Weeks
+
+How it works:
+If you lost the disguise, you can't get new one from quest giver Private Weeks. All you can do is to abandon quest and get it again.
+
+How it should work:
+He should give you new disguise buff in case you lost it.
+
+Source (you should point out proofs of your report, please give us some source):
+https://www.wowhead.com/quest=10040/who-are-they#comments",0, who are they description if you lose the disguise you can t get new one from quest giver private weeks how it works if you lost the disguise you can t get new one from quest giver private weeks all you can do is to abandon quest and get it again how it should work he should give you new disguise buff in case you lost it source you should point out proofs of your report please give us some source ,0
+213503,16525362714.0,IssuesEvent,2021-05-26 19:20:42,puppetlabs/pdkgo,https://api.github.com/repos/puppetlabs/pdkgo,opened,Template authoring tips,documentation,"Add to initial doc a set of authoring tips:
+
+- use pct new puppet-content-template to get started
+- install go-template vscode extension for syntax highlighting",1.0,"Template authoring tips - Add to initial doc a set of authoring tips:
+
+- use pct new puppet-content-template to get started
+- install go-template vscode extension for syntax highlighting",0,template authoring tips add to initial doc a set of authoring tips use pct new puppet content template to get started install go template vscode extension for syntax highlighting,0
+251938,18982368582.0,IssuesEvent,2021-11-21 05:04:53,kopia/kopia,https://api.github.com/repos/kopia/kopia,closed,Kopia documentation missing?,documentation,"https://kopia.io/docs/reference/command-line/common/
+This page has no sub-pages about ""kopia snapshot..."", but there are pages if you search, like ""snapshot create"", ""snapshot list"", etc.
+Seems the documentation lists only the first X sub-pages, the rest are not indexed and visible?
+I can't find any info on snapshot commands on the documentation or site either.",1.0,"Kopia documentation missing? - https://kopia.io/docs/reference/command-line/common/
+This page has no sub-pages about ""kopia snapshot..."", but there are pages if you search, like ""snapshot create"", ""snapshot list"", etc.
+Seems the documentation lists only the first X sub-pages, the rest are not indexed and visible?
+I can't find any info on snapshot commands on the documentation or site either.",0,kopia documentation missing this page has no sub pages about kopia snapshot but there are pages if you search like snapshot create snapshot list etc seems the documentation lists only the first x sub pages the rest are not indexed and visible i can t find any info on snapshot commands on the documentation or site either ,0
+765366,26843159314.0,IssuesEvent,2023-02-03 03:24:16,microsoft/STL,https://api.github.com/repos/microsoft/STL,opened,Errors when linking x64 OBJ files into ARM64EC programs,bug high priority ARM64,"When linking x64 OBJ files into ARM64EC programs, users are encountering errors like:
+
+```
+error LNK2001: unresolved external symbol __std_reverse_trivially_swappable_8 (EC Symbol)
+```
+
+Related to #2635 and #2740.
+
+It appears that for this scenario, we need to provide separately compiled functions in the import lib (the ARM64 import lib?) that x64 object files could be expecting. These functions can perform plain vanilla swaps/reverses/etc., they don't need to be fancy initially. I am not exactly sure what their mangled names should look like, or what the entire fix will look like as a whole. We should be sure to actually validate the fix end-to-end manually (we now have the ability to create ARM64 VMs for internal testing).
+
+Originally reported as DevCom-10219146 and Microsoft-internal VSO-1707080 / AB#1707080 .",1.0,"Errors when linking x64 OBJ files into ARM64EC programs - When linking x64 OBJ files into ARM64EC programs, users are encountering errors like:
+
+```
+error LNK2001: unresolved external symbol __std_reverse_trivially_swappable_8 (EC Symbol)
+```
+
+Related to #2635 and #2740.
+
+It appears that for this scenario, we need to provide separately compiled functions in the import lib (the ARM64 import lib?) that x64 object files could be expecting. These functions can perform plain vanilla swaps/reverses/etc., they don't need to be fancy initially. I am not exactly sure what their mangled names should look like, or what the entire fix will look like as a whole. We should be sure to actually validate the fix end-to-end manually (we now have the ability to create ARM64 VMs for internal testing).
+
+Originally reported as DevCom-10219146 and Microsoft-internal VSO-1707080 / AB#1707080 .",0,errors when linking obj files into programs when linking obj files into programs users are encountering errors like error unresolved external symbol std reverse trivially swappable ec symbol related to and it appears that for this scenario we need to provide separately compiled functions in the import lib the import lib that object files could be expecting these functions can perform plain vanilla swaps reverses etc they don t need to be fancy initially i am not exactly sure what their mangled names should look like or what the entire fix will look like as a whole we should be sure to actually validate the fix end to end manually we now have the ability to create vms for internal testing originally reported as devcom and microsoft internal vso ab ,0
+179315,13865497694.0,IssuesEvent,2020-10-16 04:30:32,nyu-mll/jiant,https://api.github.com/repos/nyu-mll/jiant,closed,Increase test coverage over training code,jiant-v1-legacy tests needed,Changes like #980 would be safer and faster with improved test coverage. This issue requests more test coverage over the core training classes. ,1.0,Increase test coverage over training code - Changes like #980 would be safer and faster with improved test coverage. This issue requests more test coverage over the core training classes. ,0,increase test coverage over training code changes like would be safer and faster with improved test coverage this issue requests more test coverage over the core training classes ,0
+4251,2610090235.0,IssuesEvent,2015-02-26 18:27:19,chrsmith/dsdsdaadf,https://api.github.com/repos/chrsmith/dsdsdaadf,opened,深圳痘痘怎么样祛,auto-migrated Priority-Medium Type-Defect,"```
+深圳痘痘怎么样祛【深圳韩方科颜全国热线400-869-1818,24小时
+QQ4008691818】深圳韩方科颜专业祛痘连锁机构,机构以韩国秘��
+�——韩方科颜这一国妆准字号治疗型权威,祛痘佳品,韩方�
+��颜专业祛痘连锁机构,采用韩国秘方配合专业“不反弹”健
+康祛痘技术并结合先进“先进豪华彩光”仪,开创国内专业��
+�疗粉刺、痤疮签约包治先河,成功消除了许多顾客脸上的痘�
+��。
```
-",1,tidb doesn t handle signed unsigned properly bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error select cast as signed cast as unsigned what did you expect to see mysql select cast as signed cast as unsigned cast as signed cast as unsigned what did you see instead mysql select cast as signed cast as unsigned error bigint unsigned value is out of range in what version of tidb are you using tidb server v or run select tidb version on tidb mysql select tidb version tidb version release version beta dirty git commit hash git branch master utc build time goversion go version linux race enabled false tikv min version alpha check table before drop false row in set sec ,1
-313656,26945078478.0,IssuesEvent,2023-02-08 07:17:42,cockroachdb/cockroach,https://api.github.com/repos/cockroachdb/cockroach,opened,pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test: TestLogic_cluster_settings failed,C-test-failure O-robot branch-master,"pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test.TestLogic_cluster_settings [failed](https://teamcity.cockroachdb.com/buildConfiguration/Cockroach_Nightlies_SqlLogicTestHighVModuleNightlyBazel/8626728?buildTab=log) with [artifacts](https://teamcity.cockroachdb.com/buildConfiguration/Cockroach_Nightlies_SqlLogicTestHighVModuleNightlyBazel/8626728?buildTab=artifacts#/) on master @ [ff67a4ba86d710db090ce700f229020365851183](https://github.com/cockroachdb/cockroach/commits/ff67a4ba86d710db090ce700f229020365851183):
+-----
+Original issue reported on code.google.com by `szft...@163.com` on 14 May 2014 at 7:40",1.0,"深圳痘痘怎么样祛 - ```
+深圳痘痘怎么样祛【深圳韩方科颜全国热线400-869-1818,24小时
+QQ4008691818】深圳韩方科颜专业祛痘连锁机构,机构以韩国秘��
+�——韩方科颜这一国妆准字号治疗型权威,祛痘佳品,韩方�
+��颜专业祛痘连锁机构,采用韩国秘方配合专业“不反弹”健
+康祛痘技术并结合先进“先进豪华彩光”仪,开创国内专业��
+�疗粉刺、痤疮签约包治先河,成功消除了许多顾客脸上的痘�
+��。
+```
+-----
+Original issue reported on code.google.com by `szft...@163.com` on 14 May 2014 at 7:40",0,深圳痘痘怎么样祛 深圳痘痘怎么样祛【 , 】深圳韩方科颜专业祛痘连锁机构,机构以韩国秘�� �——韩方科颜这一国妆准字号治疗型权威,祛痘佳品,韩方� ��颜专业祛痘���锁机构,采用韩国秘方配合专业“不反弹”健 康祛痘技术并结合先进“先进豪华彩光”仪,开创国内专业�� �疗粉刺、痤疮签约包治先河,成功消除了许多顾客脸上的痘� ��。 original issue reported on code google com by szft com on may at ,0
+13330,15721839980.0,IssuesEvent,2021-03-29 04:14:23,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,executor: sum(time) differs from mysql,component/executor sig/execution type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```
+mysql> select col_time_not_null_key from cc;
++-----------------------+
+| col_time_not_null_key |
++-----------------------+
+| 00:20:03 |
+| 12:20:27 |
+| 00:46:14 |
+| 00:20:02 |
+| 07:41:25 |
+| 20:15:56 |
+| 10:00:31 |
+| 21:32:46 |
+| 07:26:48 |
+| 00:20:02 |
+| 00:20:09 |
+| 17:18:55 |
+| 18:22:56 |
+| 10:54:06 |
+| 00:00:00 |
+| 09:23:25 |
+| 00:41:20 |
+| 17:04:45 |
+| 10:14:20 |
+| 16:44:10 |
+| 22:36:40 |
+| 00:00:00 |
+| 00:42:04 |
+| 06:25:39 |
+| 14:27:59 |
+| 11:37:03 |
+| 22:58:43 |
+| 00:20:02 |
+| 10:31:24 |
+| 06:02:13 |
+| 02:30:43 |
+| 09:04:12 |
+| 00:20:00 |
+| 07:54:44 |
+| 00:20:08 |
+| 13:41:03 |
+| 00:20:02 |
+| 00:00:00 |
+| 21:35:31 |
+| 19:43:41 |
+| 15:29:59 |
+| 00:00:00 |
+| 00:20:03 |
+| 21:28:05 |
+| 20:35:26 |
+| 00:10:46 |
+| 02:09:06 |
+| 04:30:35 |
+| 00:00:00 |
+| 15:41:21 |
++-----------------------+
+50 rows in set (0.05 sec)
+
+```
+
+
+
+### 2. What did you expect to see? (Required)
+```
+from mysql
+mysql> select sum(col_time_not_null_key) from CC;
++----------------------------+
+| sum(col_time_not_null_key) |
++----------------------------+
+| 4263835 |
++----------------------------+
+1 row in set (0.00 sec)
+```
+### 3. What did you see instead (Required)
+```
+mysql> select sum(col_time_not_null_key) from cc;
++----------------------------+
+| sum(col_time_not_null_key) |
++----------------------------+
+| 4253812 |
++----------------------------+
+1 row in set (0.04 sec)
+
+mysql>
+```
+### 4. What is your TiDB version? (Required)
+master
+
+
+",True,"executor: sum(time) differs from mysql - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```
+mysql> select col_time_not_null_key from cc;
++-----------------------+
+| col_time_not_null_key |
++-----------------------+
+| 00:20:03 |
+| 12:20:27 |
+| 00:46:14 |
+| 00:20:02 |
+| 07:41:25 |
+| 20:15:56 |
+| 10:00:31 |
+| 21:32:46 |
+| 07:26:48 |
+| 00:20:02 |
+| 00:20:09 |
+| 17:18:55 |
+| 18:22:56 |
+| 10:54:06 |
+| 00:00:00 |
+| 09:23:25 |
+| 00:41:20 |
+| 17:04:45 |
+| 10:14:20 |
+| 16:44:10 |
+| 22:36:40 |
+| 00:00:00 |
+| 00:42:04 |
+| 06:25:39 |
+| 14:27:59 |
+| 11:37:03 |
+| 22:58:43 |
+| 00:20:02 |
+| 10:31:24 |
+| 06:02:13 |
+| 02:30:43 |
+| 09:04:12 |
+| 00:20:00 |
+| 07:54:44 |
+| 00:20:08 |
+| 13:41:03 |
+| 00:20:02 |
+| 00:00:00 |
+| 21:35:31 |
+| 19:43:41 |
+| 15:29:59 |
+| 00:00:00 |
+| 00:20:03 |
+| 21:28:05 |
+| 20:35:26 |
+| 00:10:46 |
+| 02:09:06 |
+| 04:30:35 |
+| 00:00:00 |
+| 15:41:21 |
++-----------------------+
+50 rows in set (0.05 sec)
+
+```
+
+
+
+### 2. What did you expect to see? (Required)
+```
+from mysql
+mysql> select sum(col_time_not_null_key) from CC;
++----------------------------+
+| sum(col_time_not_null_key) |
++----------------------------+
+| 4263835 |
++----------------------------+
+1 row in set (0.00 sec)
+```
+### 3. What did you see instead (Required)
+```
+mysql> select sum(col_time_not_null_key) from cc;
++----------------------------+
+| sum(col_time_not_null_key) |
++----------------------------+
+| 4253812 |
++----------------------------+
+1 row in set (0.04 sec)
+
+mysql>
+```
+### 4. What is your TiDB version? (Required)
+master
+
+
+",1,executor sum time differs from mysql bug report please answer these questions before submitting your issue thanks minimal reproduce step required mysql select col time not null key from cc col time not null key rows in set sec what did you expect to see required from mysql mysql select sum col time not null key from cc sum col time not null key row in set sec what did you see instead required mysql select sum col time not null key from cc sum col time not null key row in set sec mysql what is your tidb version required master ,1
+12111,3576296149.0,IssuesEvent,2016-01-27 19:00:30,GarageGames/Torque2D,https://api.github.com/repos/GarageGames/Torque2D,closed,List the todos publicly to finish them quickly,Documentation,"We should have Torque2D on Todofy, I tried it on my fork and there are about 169 todos in the master branch. Here's the link: https://todofy.org/r/fybot/Torque2D
+
+This will give clear visibility on what all need to be finished, and platform has various feature to assist the process.",1.0,"List the todos publicly to finish them quickly - We should have Torque2D on Todofy, I tried it on my fork and there are about 169 todos in the master branch. Here's the link: https://todofy.org/r/fybot/Torque2D
+
+This will give clear visibility on what all need to be finished, and platform has various feature to assist the process.",0,list the todos publicly to finish them quickly we should have on todofy i tried it on my fork and there are about todos in the master branch here s the link this will give clear visibility on what all need to be finished and platform has various feature to assist the process ,0
+4895,7498308285.0,IssuesEvent,2018-04-09 03:40:25,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,`unix_timestamp`'s return type is not compatible,compatibility for-new-contributors help wanted,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+mysql> select unix_timestamp('2016-01-01');
++------------------------------+
+| unix_timestamp('2016-01-01') |
++------------------------------+
+| 1451577600.000000 |
++------------------------------+
+1 row in set (0.00 sec)
+
+2. What did you expect to see?
+
+mysql> select unix_timestamp('2016-01-01');
++------------------------------+
+| unix_timestamp('2016-01-01') |
++------------------------------+
+| 1451577600 |
++------------------------------+
+1 row in set (0.00 sec)
+
+3. What did you see instead?
+
+Should be the same, but it's different.
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+57afbe2680dbc6b23e604b5c0d5ab322a494e772",True,"`unix_timestamp`'s return type is not compatible - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+mysql> select unix_timestamp('2016-01-01');
++------------------------------+
+| unix_timestamp('2016-01-01') |
++------------------------------+
+| 1451577600.000000 |
++------------------------------+
+1 row in set (0.00 sec)
+
+2. What did you expect to see?
+
+mysql> select unix_timestamp('2016-01-01');
++------------------------------+
+| unix_timestamp('2016-01-01') |
++------------------------------+
+| 1451577600 |
++------------------------------+
+1 row in set (0.00 sec)
+
+3. What did you see instead?
+
+Should be the same, but it's different.
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+57afbe2680dbc6b23e604b5c0d5ab322a494e772",1, unix timestamp s return type is not compatible please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error mysql select unix timestamp unix timestamp row in set sec what did you expect to see mysql select unix timestamp unix timestamp row in set sec what did you see instead should be the same but it s different what version of tidb are you using tidb server v or run select tidb version on tidb ,1
+23230,11881887819.0,IssuesEvent,2020-03-27 13:31:06,Altinn/altinn-studio,https://api.github.com/repos/Altinn/altinn-studio,closed,Analyse the findings and opportunities on performance in Lighthouse,area/ui-editor kind/analysis ops/performance status/ready-for-specification,"## Description
+The performance analysis done by Lighthouse (chrome extension under ""audit"") shows that Altinn studio has bad performance. Especially the UI-editor. We should look at the pains and the opportunities listed by Lighthouse to determine what actions we can do to improve the performance.
+
+
+
+## In scope
+What are the quick wins we can do for MVP2?
+What are the actions we should take to improve performance?
+
+## Out of scope
+Solve everything related to performance.
+Some pains seems to be caused by blocking API-calls because we're waiting on data. This type of larger rewriting tasks should be limited to drafts for this analysis.
+
+## Analysis
+
+
+
+## Conclusion
+> Short summary of the proposed solution.
+
+## Tasks
+- [ ] Analyse the pains and opportunities
+- [ ] Create new tasks under the epic; Performance issue MVP2 #1371
+- [ ] Create tasks/drafts for actions that should be done after MVP2
+- [ ] QA has been done
+",True,"Analyse the findings and opportunities on performance in Lighthouse - ## Description
+The performance analysis done by Lighthouse (chrome extension under ""audit"") shows that Altinn studio has bad performance. Especially the UI-editor. We should look at the pains and the opportunities listed by Lighthouse to determine what actions we can do to improve the performance.
+
+
+
+## In scope
+What are the quick wins we can do for MVP2?
+What are the actions we should take to improve performance?
+
+## Out of scope
+Solve everything related to performance.
+Some pains seems to be caused by blocking API-calls because we're waiting on data. This type of larger rewriting tasks should be limited to drafts for this analysis.
+
+## Analysis
+
+
+
+## Conclusion
+> Short summary of the proposed solution.
+
+## Tasks
+- [ ] Analyse the pains and opportunities
+- [ ] Create new tasks under the epic; Performance issue MVP2 #1371
+- [ ] Create tasks/drafts for actions that should be done after MVP2
+- [ ] QA has been done
+",0,analyse the findings and opportunities on performance in lighthouse description the performance analysis done by lighthouse chrome extension under audit shows that altinn studio has bad performance especially the ui editor we should look at the pains and the opportunities listed by lighthouse to determine what actions we can do to improve the performance in scope what are the quick wins we can do for what are the actions we should take to improve performance out of scope solve everything related to performance some pains seems to be caused by blocking api calls because we re waiting on data this type of larger rewriting tasks should be limited to drafts for this analysis analysis conclusion short summary of the proposed solution tasks analyse the pains and opportunities create new tasks under the epic performance issue create tasks drafts for actions that should be done after qa has been done ,0
+152336,12102224071.0,IssuesEvent,2020-04-20 16:21:24,cockroachdb/cockroach,https://api.github.com/repos/cockroachdb/cockroach,closed,roachtest: transfer-leases/quit failed,C-test-failure O-roachtest O-robot branch-provisional_202004061746_v19.2.6 release-blocker,"[(roachtest).transfer-leases/quit failed](https://teamcity.cockroachdb.com/viewLog.html?buildId=1864738&tab=buildLog) on [provisional_202004061746_v19.2.6@ee759892738f7f203ff95ec7627b90d7c47b4350](https://github.com/cockroachdb/cockroach/commits/ee759892738f7f203ff95ec7627b90d7c47b4350):
```
-[06:30:09] ALTER TENANT ALL RESET CLUSTER SETTING server.mem_profile.total_dump_size_limit;
- logictestbase.go:512: statement/query skipped with reason: unsupported configuration fakedist-disk, statement/query only supports 3node-tenant-default-configs (no issue given)
-[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [0];
-[06:30:09] -- XFAIL;
-[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [1];
-[06:30:09] -- XFAIL;
-[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [1111];
-[06:30:09] -- XFAIL;
-[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [10];
-[06:30:09] -- OK;
-[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT ""tenant-10"";
-[06:30:09] -- OK;
- logictestbase.go:512: statement/query skipped with reason: unsupported configuration fakedist-disk, statement/query only supports 3snode-tenant-default-config (no issue given)
-[06:30:09] SHOW CLUSTER SETTINGS FOR TENANT [0];
-[06:30:09] -- XFAIL;
-[06:30:09] SHOW CLUSTER SETTINGS FOR TENANT [1];
-[06:30:10] -- XFAIL;
-[06:30:10] SHOW CLUSTER SETTINGS FOR TENANT [1111];
-[06:30:10] -- XFAIL;
-[06:30:10] SELECT variable, type, origin FROM [SHOW CLUSTER SETTINGS FOR TENANT [10]]
-WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
-[06:30:10] -- OK;
-[06:30:10] SELECT variable, type, origin FROM [SHOW CLUSTER SETTINGS FOR TENANT ""tenant-10""]
-WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
-[06:30:10] -- OK;
-[06:30:10] SELECT variable, type, public, origin FROM [SHOW ALL CLUSTER SETTINGS FOR TENANT [10]]
-WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
-[06:30:10] -- OK;
-[06:30:10] SELECT variable, type, public, origin FROM [SHOW ALL CLUSTER SETTINGS FOR TENANT ""tenant-10""]
-WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
-[06:30:10] -- OK;
-[06:30:10] SHOW CLUSTER SETTING sql.defaults.distsql;;
-[06:30:10] -- FAIL
- logic.go:2892:
-
- /home/roach/.cache/bazel/_bazel_roach/c5a4e7d36696d9cd970af2045211a7df/sandbox/processwrapper-sandbox/3738/execroot/com_github_cockroachdb_cockroach/bazel-out/k8-fastbuild/bin/pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test_/fakedist-disk_test.runfiles/com_github_cockroachdb_cockroach/pkg/sql/logictest/testdata/logic_test/cluster_settings:331: SHOW CLUSTER SETTING sql.defaults.distsql;
- expected:
- NOTICE: using global default sql.defaults.distsql is not recommended
- HINT: use the ``ALTER ROLE ... SET`` syntax to control session variable defaults at a finer-grained level. See: https://www.cockroachlabs.com/docs/v23.1/alter-role.html#set-default-session-variable-values-for-a-role
-
- but found (query options: ""noticetrace"") :
- NOTICE: using global default sql.defaults.distsql is not recommended
- HINT: use the ``ALTER ROLE ... SET`` syntax to control session variable defaults at a finer-grained level. See: https://www.cockroachlabs.com/docs/dev/alter-role.html#set-default-session-variable-values-for-a-role
-[06:30:10] -- FAIL
- logic.go:2151:
- /home/roach/.cache/bazel/_bazel_roach/c5a4e7d36696d9cd970af2045211a7df/sandbox/processwrapper-sandbox/3738/execroot/com_github_cockroachdb_cockroach/bazel-out/k8-fastbuild/bin/pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test_/fakedist-disk_test.runfiles/com_github_cockroachdb_cockroach/pkg/sql/logictest/testdata/logic_test/cluster_settings:337: too many errors encountered, skipping the rest of the input
-[06:30:10] --- done: /home/roach/.cache/bazel/_bazel_roach/c5a4e7d36696d9cd970af2045211a7df/sandbox/processwrapper-sandbox/3738/execroot/com_github_cockroachdb_cockroach/bazel-out/k8-fastbuild/bin/pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test_/fakedist-disk_test.runfiles/com_github_cockroachdb_cockroach/pkg/sql/logictest/testdata/logic_test/cluster_settings with config fakedist-disk: 71 tests, 2 failures
-[06:30:10] --- total progress: 71 statements
---- total: 71 tests, 2 failures
- --- FAIL: TestLogic_cluster_settings/tenant-cluster-settings (0.55s)
+The test failed on branch=provisional_202004061746_v19.2.6, cloud=gce:
+test artifacts and logs in: /home/agent/work/.go/src/github.com/cockroachdb/cockroach/artifacts/20200409-1864738/transfer-leases/quit/run_1
+ quit.go:59,quit.go:87,quit.go:46,quit.go:343,test_runner.go:753: wo
+
+ cluster.go:1420,context.go:135,cluster.go:1409,test_runner.go:825: dead node detection: /home/agent/work/.go/src/github.com/cockroachdb/cockroach/bin/roachprod monitor teamcity-1864738-1586444132-17-n3cpu4 --oneshot --ignore-empty-nodes: exit status 1 3: 14457
+ 2: 14433
+ 1: dead
+ Error: UNCLASSIFIED_PROBLEM:
+ - 1: dead
+ main.glob..func13
+ /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachprod/main.go:1129
+ main.wrap.func1
+ /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachprod/main.go:272
+ github.com/cockroachdb/cockroach/vendor/github.com/spf13/cobra.(*Command).execute
+ /home/agent/work/.go/src/github.com/cockroachdb/cockroach/vendor/github.com/spf13/cobra/command.go:766
+ github.com/cockroachdb/cockroach/vendor/github.com/spf13/cobra.(*Command).ExecuteC
+ /home/agent/work/.go/src/github.com/cockroachdb/cockroach/vendor/github.com/spf13/cobra/command.go:852
+ github.com/cockroachdb/cockroach/vendor/github.com/spf13/cobra.(*Command).Execute
+ /home/agent/work/.go/src/github.com/cockroachdb/cockroach/vendor/github.com/spf13/cobra/command.go:800
+ main.main
+ /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachprod/main.go:1793
+ runtime.main
+ /usr/local/go/src/runtime/proc.go:203
+ runtime.goexit
+ /usr/local/go/src/runtime/asm_amd64.s:1357
+
```
-Help
-
-See also: [How To Investigate a Go Test Failure \(internal\)](https://cockroachlabs.atlassian.net/l/c/HgfXfJgM)
-
-
-/cc @cockroachdb/sql-queries
-
+More
-[This test on roachdash](https://roachdash.crdb.dev/?filter=status:open%20t:.*TestLogic_cluster_settings.*&sort=title+created&display=lastcommented+project) | [Improve this report!](https://github.com/cockroachdb/cockroach/tree/master/pkg/cmd/internal/issues)
-
-",1.0,"pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test: TestLogic_cluster_settings failed - pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test.TestLogic_cluster_settings [failed](https://teamcity.cockroachdb.com/buildConfiguration/Cockroach_Nightlies_SqlLogicTestHighVModuleNightlyBazel/8626728?buildTab=log) with [artifacts](https://teamcity.cockroachdb.com/buildConfiguration/Cockroach_Nightlies_SqlLogicTestHighVModuleNightlyBazel/8626728?buildTab=artifacts#/) on master @ [ff67a4ba86d710db090ce700f229020365851183](https://github.com/cockroachdb/cockroach/commits/ff67a4ba86d710db090ce700f229020365851183):
+Artifacts: [/transfer-leases/quit](https://teamcity.cockroachdb.com/viewLog.html?buildId=1864738&tab=artifacts#/transfer-leases/quit)
+Related:
+- #47259 roachtest: transfer-leases/quit failed [C-test-failure](https://api.github.com/repos/cockroachdb/cockroach/labels/C-test-failure) [O-roachtest](https://api.github.com/repos/cockroachdb/cockroach/labels/O-roachtest) [O-robot](https://api.github.com/repos/cockroachdb/cockroach/labels/O-robot) [branch-release-20.1](https://api.github.com/repos/cockroachdb/cockroach/labels/branch-release-20.1) [release-blocker](https://api.github.com/repos/cockroachdb/cockroach/labels/release-blocker)
+
+- #47254 roachtest: transfer-leases/quit failed [C-test-failure](https://api.github.com/repos/cockroachdb/cockroach/labels/C-test-failure) [O-roachtest](https://api.github.com/repos/cockroachdb/cockroach/labels/O-roachtest) [O-robot](https://api.github.com/repos/cockroachdb/cockroach/labels/O-robot) [branch-release-19.2](https://api.github.com/repos/cockroachdb/cockroach/labels/branch-release-19.2)
+
+- #47184 roachtest: transfer-leases/quit failed [C-test-failure](https://api.github.com/repos/cockroachdb/cockroach/labels/C-test-failure) [O-roachtest](https://api.github.com/repos/cockroachdb/cockroach/labels/O-roachtest) [O-robot](https://api.github.com/repos/cockroachdb/cockroach/labels/O-robot) [branch-master](https://api.github.com/repos/cockroachdb/cockroach/labels/branch-master) [release-blocker](https://api.github.com/repos/cockroachdb/cockroach/labels/release-blocker)
+
+[See this test on roachdash](https://roachdash.crdb.dev/?filter=status%3Aopen+t%3A.%2Atransfer-leases%2Fquit.%2A&sort=title&restgroup=false&display=lastcommented+project)
+powered by [pkg/cmd/internal/issues](https://github.com/cockroachdb/cockroach/tree/master/pkg/cmd/internal/issues)
+",2.0,"roachtest: transfer-leases/quit failed - [(roachtest).transfer-leases/quit failed](https://teamcity.cockroachdb.com/viewLog.html?buildId=1864738&tab=buildLog) on [provisional_202004061746_v19.2.6@ee759892738f7f203ff95ec7627b90d7c47b4350](https://github.com/cockroachdb/cockroach/commits/ee759892738f7f203ff95ec7627b90d7c47b4350):
```
-[06:30:09] ALTER TENANT ALL RESET CLUSTER SETTING server.mem_profile.total_dump_size_limit;
- logictestbase.go:512: statement/query skipped with reason: unsupported configuration fakedist-disk, statement/query only supports 3node-tenant-default-configs (no issue given)
-[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [0];
-[06:30:09] -- XFAIL;
-[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [1];
-[06:30:09] -- XFAIL;
-[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [1111];
-[06:30:09] -- XFAIL;
-[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT [10];
-[06:30:09] -- OK;
-[06:30:09] SHOW CLUSTER SETTING server.mem_profile.total_dump_size_limit FOR TENANT ""tenant-10"";
-[06:30:09] -- OK;
- logictestbase.go:512: statement/query skipped with reason: unsupported configuration fakedist-disk, statement/query only supports 3snode-tenant-default-config (no issue given)
-[06:30:09] SHOW CLUSTER SETTINGS FOR TENANT [0];
-[06:30:09] -- XFAIL;
-[06:30:09] SHOW CLUSTER SETTINGS FOR TENANT [1];
-[06:30:10] -- XFAIL;
-[06:30:10] SHOW CLUSTER SETTINGS FOR TENANT [1111];
-[06:30:10] -- XFAIL;
-[06:30:10] SELECT variable, type, origin FROM [SHOW CLUSTER SETTINGS FOR TENANT [10]]
-WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
-[06:30:10] -- OK;
-[06:30:10] SELECT variable, type, origin FROM [SHOW CLUSTER SETTINGS FOR TENANT ""tenant-10""]
-WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
-[06:30:10] -- OK;
-[06:30:10] SELECT variable, type, public, origin FROM [SHOW ALL CLUSTER SETTINGS FOR TENANT [10]]
-WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
-[06:30:10] -- OK;
-[06:30:10] SELECT variable, type, public, origin FROM [SHOW ALL CLUSTER SETTINGS FOR TENANT ""tenant-10""]
-WHERE variable IN ('jobs.scheduler.enabled', 'jobs.retention_time') ORDER BY 1;
-[06:30:10] -- OK;
-[06:30:10] SHOW CLUSTER SETTING sql.defaults.distsql;;
-[06:30:10] -- FAIL
- logic.go:2892:
-
- /home/roach/.cache/bazel/_bazel_roach/c5a4e7d36696d9cd970af2045211a7df/sandbox/processwrapper-sandbox/3738/execroot/com_github_cockroachdb_cockroach/bazel-out/k8-fastbuild/bin/pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test_/fakedist-disk_test.runfiles/com_github_cockroachdb_cockroach/pkg/sql/logictest/testdata/logic_test/cluster_settings:331: SHOW CLUSTER SETTING sql.defaults.distsql;
- expected:
- NOTICE: using global default sql.defaults.distsql is not recommended
- HINT: use the ``ALTER ROLE ... SET`` syntax to control session variable defaults at a finer-grained level. See: https://www.cockroachlabs.com/docs/v23.1/alter-role.html#set-default-session-variable-values-for-a-role
-
- but found (query options: ""noticetrace"") :
- NOTICE: using global default sql.defaults.distsql is not recommended
- HINT: use the ``ALTER ROLE ... SET`` syntax to control session variable defaults at a finer-grained level. See: https://www.cockroachlabs.com/docs/dev/alter-role.html#set-default-session-variable-values-for-a-role
-[06:30:10] -- FAIL
- logic.go:2151:
- /home/roach/.cache/bazel/_bazel_roach/c5a4e7d36696d9cd970af2045211a7df/sandbox/processwrapper-sandbox/3738/execroot/com_github_cockroachdb_cockroach/bazel-out/k8-fastbuild/bin/pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test_/fakedist-disk_test.runfiles/com_github_cockroachdb_cockroach/pkg/sql/logictest/testdata/logic_test/cluster_settings:337: too many errors encountered, skipping the rest of the input
-[06:30:10] --- done: /home/roach/.cache/bazel/_bazel_roach/c5a4e7d36696d9cd970af2045211a7df/sandbox/processwrapper-sandbox/3738/execroot/com_github_cockroachdb_cockroach/bazel-out/k8-fastbuild/bin/pkg/sql/logictest/tests/fakedist-disk/fakedist-disk_test_/fakedist-disk_test.runfiles/com_github_cockroachdb_cockroach/pkg/sql/logictest/testdata/logic_test/cluster_settings with config fakedist-disk: 71 tests, 2 failures
-[06:30:10] --- total progress: 71 statements
---- total: 71 tests, 2 failures
- --- FAIL: TestLogic_cluster_settings/tenant-cluster-settings (0.55s)
+The test failed on branch=provisional_202004061746_v19.2.6, cloud=gce:
+test artifacts and logs in: /home/agent/work/.go/src/github.com/cockroachdb/cockroach/artifacts/20200409-1864738/transfer-leases/quit/run_1
+ quit.go:59,quit.go:87,quit.go:46,quit.go:343,test_runner.go:753: wo
+
+ cluster.go:1420,context.go:135,cluster.go:1409,test_runner.go:825: dead node detection: /home/agent/work/.go/src/github.com/cockroachdb/cockroach/bin/roachprod monitor teamcity-1864738-1586444132-17-n3cpu4 --oneshot --ignore-empty-nodes: exit status 1 3: 14457
+ 2: 14433
+ 1: dead
+ Error: UNCLASSIFIED_PROBLEM:
+ - 1: dead
+ main.glob..func13
+ /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachprod/main.go:1129
+ main.wrap.func1
+ /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachprod/main.go:272
+ github.com/cockroachdb/cockroach/vendor/github.com/spf13/cobra.(*Command).execute
+ /home/agent/work/.go/src/github.com/cockroachdb/cockroach/vendor/github.com/spf13/cobra/command.go:766
+ github.com/cockroachdb/cockroach/vendor/github.com/spf13/cobra.(*Command).ExecuteC
+ /home/agent/work/.go/src/github.com/cockroachdb/cockroach/vendor/github.com/spf13/cobra/command.go:852
+ github.com/cockroachdb/cockroach/vendor/github.com/spf13/cobra.(*Command).Execute
+ /home/agent/work/.go/src/github.com/cockroachdb/cockroach/vendor/github.com/spf13/cobra/command.go:800
+ main.main
+ /home/agent/work/.go/src/github.com/cockroachdb/cockroach/pkg/cmd/roachprod/main.go:1793
+ runtime.main
+ /usr/local/go/src/runtime/proc.go:203
+ runtime.goexit
+ /usr/local/go/src/runtime/asm_amd64.s:1357
+
```
-Help
-
-See also: [How To Investigate a Go Test Failure \(internal\)](https://cockroachlabs.atlassian.net/l/c/HgfXfJgM)
-
-
-/cc @cockroachdb/sql-queries
-
+More
-[This test on roachdash](https://roachdash.crdb.dev/?filter=status:open%20t:.*TestLogic_cluster_settings.*&sort=title+created&display=lastcommented+project) | [Improve this report!](https://github.com/cockroachdb/cockroach/tree/master/pkg/cmd/internal/issues)
-
-",0,pkg sql logictest tests fakedist disk fakedist disk test testlogic cluster settings failed pkg sql logictest tests fakedist disk fakedist disk test testlogic cluster settings with on master alter tenant all reset cluster setting server mem profile total dump size limit logictestbase go statement query skipped with reason unsupported configuration fakedist disk statement query only supports tenant default configs no issue given show cluster setting server mem profile total dump size limit for tenant xfail show cluster setting server mem profile total dump size limit for tenant xfail show cluster setting server mem profile total dump size limit for tenant xfail show cluster setting server mem profile total dump size limit for tenant ok show cluster setting server mem profile total dump size limit for tenant tenant ok logictestbase go statement query skipped with reason unsupported configuration fakedist disk statement query only supports tenant default config no issue given show cluster settings for tenant xfail show cluster settings for tenant xfail show cluster settings for tenant xfail select variable type origin from where variable in jobs scheduler enabled jobs retention time order by ok select variable type origin from where variable in jobs scheduler enabled jobs retention time order by ok select variable type public origin from where variable in jobs scheduler enabled jobs retention time order by ok select variable type public origin from where variable in jobs scheduler enabled jobs retention time order by ok show cluster setting sql defaults distsql fail logic go home roach cache bazel bazel roach sandbox processwrapper sandbox execroot com github cockroachdb cockroach bazel out fastbuild bin pkg sql logictest tests fakedist disk fakedist disk test fakedist disk test runfiles com github cockroachdb cockroach pkg sql logictest testdata logic test cluster settings show cluster setting sql defaults distsql expected notice using global default sql defaults distsql is not recommended hint use the alter role set syntax to control session variable defaults at a finer grained level see but found query options noticetrace notice using global default sql defaults distsql is not recommended hint use the alter role set syntax to control session variable defaults at a finer grained level see fail logic go home roach cache bazel bazel roach sandbox processwrapper sandbox execroot com github cockroachdb cockroach bazel out fastbuild bin pkg sql logictest tests fakedist disk fakedist disk test fakedist disk test runfiles com github cockroachdb cockroach pkg sql logictest testdata logic test cluster settings too many errors encountered skipping the rest of the input done home roach cache bazel bazel roach sandbox processwrapper sandbox execroot com github cockroachdb cockroach bazel out fastbuild bin pkg sql logictest tests fakedist disk fakedist disk test fakedist disk test runfiles com github cockroachdb cockroach pkg sql logictest testdata logic test cluster settings with config fakedist disk tests failures total progress statements total tests failures fail testlogic cluster settings tenant cluster settings help see also cc cockroachdb sql queries ,0
-94370,8486379988.0,IssuesEvent,2018-10-26 10:41:02,devdaydresden/devday_website,https://api.github.com/repos/devdaydresden/devday_website,opened,Improve test dada,django tests,"**Describe the solution you'd like**
-We need additional test data entries:
-- site.domain should use the appropriate value for the environment (localhost:8000, devday-test.mms-at-work.de:8080) instead of devday.de
-- the sponsoring page should link to the sponsoring app
-- a basic set of sponsoring packages should be added for the current event
-- die Seite sponsoring sollte auf die Sponsoring-App verlinken
-- es sollte ein Grunddatenbestand für Sponsoringpakete für das aktuelle Event da sein, damit man den nicht manuell pflegen muss
-",1.0,"Improve test dada - **Describe the solution you'd like**
-We need additional test data entries:
-- site.domain should use the appropriate value for the environment (localhost:8000, devday-test.mms-at-work.de:8080) instead of devday.de
-- the sponsoring page should link to the sponsoring app
-- a basic set of sponsoring packages should be added for the current event
-- die Seite sponsoring sollte auf die Sponsoring-App verlinken
-- es sollte ein Grunddatenbestand für Sponsoringpakete für das aktuelle Event da sein, damit man den nicht manuell pflegen muss
-",0,improve test dada describe the solution you d like we need additional test data entries site domain should use the appropriate value for the environment localhost devday test mms at work de instead of devday de the sponsoring page should link to the sponsoring app a basic set of sponsoring packages should be added for the current event die seite sponsoring sollte auf die sponsoring app verlinken es sollte ein grunddatenbestand für sponsoringpakete für das aktuelle event da sein damit man den nicht manuell pflegen muss ,0
-245472,26549233562.0,IssuesEvent,2023-01-20 05:24:00,nidhi7598/linux-3.0.35_CVE-2022-45934,https://api.github.com/repos/nidhi7598/linux-3.0.35_CVE-2022-45934,opened,CVE-2014-2672 (Medium) detected in linux-stable-rtv3.8.6,security vulnerability,"## CVE-2014-2672 - Medium Severity Vulnerability
- Vulnerable Library - linux-stable-rtv3.8.6
-
-
-
- Vulnerable Source Files (1)
-
+- #47254 roachtest: transfer-leases/quit failed [C-test-failure](https://api.github.com/repos/cockroachdb/cockroach/labels/C-test-failure) [O-roachtest](https://api.github.com/repos/cockroachdb/cockroach/labels/O-roachtest) [O-robot](https://api.github.com/repos/cockroachdb/cockroach/labels/O-robot) [branch-release-19.2](https://api.github.com/repos/cockroachdb/cockroach/labels/branch-release-19.2)
+
+- #47184 roachtest: transfer-leases/quit failed [C-test-failure](https://api.github.com/repos/cockroachdb/cockroach/labels/C-test-failure) [O-roachtest](https://api.github.com/repos/cockroachdb/cockroach/labels/O-roachtest) [O-robot](https://api.github.com/repos/cockroachdb/cockroach/labels/O-robot) [branch-master](https://api.github.com/repos/cockroachdb/cockroach/labels/branch-master) [release-blocker](https://api.github.com/repos/cockroachdb/cockroach/labels/release-blocker)
+
+[See this test on roachdash](https://roachdash.crdb.dev/?filter=status%3Aopen+t%3A.%2Atransfer-leases%2Fquit.%2A&sort=title&restgroup=false&display=lastcommented+project)
+powered by [pkg/cmd/internal/issues](https://github.com/cockroachdb/cockroach/tree/master/pkg/cmd/internal/issues)
+",0,roachtest transfer leases quit failed on the test failed on branch provisional cloud gce test artifacts and logs in home agent work go src github com cockroachdb cockroach artifacts transfer leases quit run quit go quit go quit go quit go test runner go wo cluster go context go cluster go test runner go dead node detection home agent work go src github com cockroachdb cockroach bin roachprod monitor teamcity oneshot ignore empty nodes exit status dead error unclassified problem dead main glob home agent work go src github com cockroachdb cockroach pkg cmd roachprod main go main wrap home agent work go src github com cockroachdb cockroach pkg cmd roachprod main go github com cockroachdb cockroach vendor github com cobra command execute home agent work go src github com cockroachdb cockroach vendor github com cobra command go github com cockroachdb cockroach vendor github com cobra command executec home agent work go src github com cockroachdb cockroach vendor github com cobra command go github com cockroachdb cockroach vendor github com cobra command execute home agent work go src github com cockroachdb cockroach vendor github com cobra command go main main home agent work go src github com cockroachdb cockroach pkg cmd roachprod main go runtime main usr local go src runtime proc go runtime goexit usr local go src runtime asm s more artifacts related roachtest transfer leases quit failed roachtest transfer leases quit failed roachtest transfer leases quit failed powered by ,0
+4096,6916831329.0,IssuesEvent,2017-11-29 05:09:01,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Show warning for `kill pid` statement,compatibility,Sine we use `kill tidb pid` instead of `kill pid`. We should return a warning for `kill pid` to notify user that their command is not executed as expected.,True,Show warning for `kill pid` statement - Sine we use `kill tidb pid` instead of `kill pid`. We should return a warning for `kill pid` to notify user that their command is not executed as expected.,1,show warning for kill pid statement sine we use kill tidb pid instead of kill pid we should return a warning for kill pid to notify user that their command is not executed as expected ,1
+11777,13891945328.0,IssuesEvent,2020-10-19 11:27:42,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,reopened,"Function des_encrypt, des_decrypt not supported",status/help-wanted type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+select des_encrypt('hello');
+select des_decrypt(NULL);
+```
+
+2. What did you expect to see?
+
+```
+des_encrypt('hello')
+??2nV??}
+des_decrypt(NULL)
+NULL
+```
+
+3. What did you see instead?
+
+```
+ERROR 1305 (42000) at line 1: FUNCTION DES_ENCRYPT does not exist
+ERROR 1305 (42000): FUNCTION DES_DECRYPT does not exist
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"Function des_encrypt, des_decrypt not supported - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+select des_encrypt('hello');
+select des_decrypt(NULL);
+```
+
+2. What did you expect to see?
+
+```
+des_encrypt('hello')
+??2nV??}
+des_decrypt(NULL)
+NULL
+```
+
+3. What did you see instead?
+
+```
+ERROR 1305 (42000) at line 1: FUNCTION DES_ENCRYPT does not exist
+ERROR 1305 (42000): FUNCTION DES_DECRYPT does not exist
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,function des encrypt des decrypt not supported please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql select des encrypt hello select des decrypt null what did you expect to see des encrypt hello des decrypt null null what did you see instead error at line function des encrypt does not exist error function des decrypt does not exist what version of tidb are you using tidb server v ,1
+75045,20612187206.0,IssuesEvent,2022-03-07 09:44:16,tensorflow/tensorflow,https://api.github.com/repos/tensorflow/tensorflow,closed,Build of unit tests fails,type:build/install subtype: ubuntu/linux TF 2.8,"Please make sure that this is a build/installation issue. As per our [GitHub Policy](https://github.com/tensorflow/tensorflow/blob/master/ISSUES.md), we only address code/doc bugs, performance issues, feature requests and build/installation issues on GitHub. tag:build_template
+
+**System information**
+- OS Platform and Distribution (e.g., Linux Ubuntu 16.04): Ubuntu 18.04
+- Mobile device (e.g. iPhone 8, Pixel 2, Samsung Galaxy) if the issue happens on mobile device: n/a
+- TensorFlow installed from (source or binary): source
+- TensorFlow version: git HEAD
+- Python version: 3.7.5
+- Installed using virtualenv? pip? conda?: no
+- Bazel version (if compiling from source): 5.0.0
+- GCC/Compiler version (if compiling from source): 10.3.0
+- CUDA/cuDNN version: n/a
+- GPU model and memory: n/a
+
+
+
+**Describe the problem**
+
+Building unit tests fails with
+
+================================================================================
+ERROR: /tmp/workspace/tensorflow-git/tensorflow/compiler/mlir/lite/quantization/BUILD:152:20: Compiling tensorflow/compiler/mlir/lite/quantization/tools/tflite_op_coverage_spec_getters_gen.cc failed: (Exit 1): gcc failed: error executing command
+ (cd /root/.cache/bazel/_bazel_root/db210f68f81d95ddcca9ae96b16ed72c/execroot/org_tensorflow && \
+ exec env - \
+ LD_LIBRARY_PATH=/opt/rh/devtoolset-10/root/usr/lib64:/opt/rh/devtoolset-10/root/usr/lib:/opt/rh/devtoolset-10/root/usr/lib64/dyninst:/opt/rh/devtoolset-10/root/usr/lib/dyninst:/usr/local/lib64:/usr/lib \
+ PATH=/tmp/workspace/venv-cp310-cp310/bin:/opt/rh/devtoolset-10/root/usr/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin \
+ PWD=/proc/self/cwd \
+ /opt/rh/devtoolset-10/root/usr/bin/gcc -U_FORTIFY_SOURCE -fstack-protector -Wall -Wunused-but-set-parameter -Wno-free-nonheap-object -fno-omit-frame-pointer -g0 -O2 '-D_FORTIFY_SOURCE=1' -DNDEBUG -ffunction-sections -fdata-sections '-std=c++11' -MD -MF bazel-out/aarch64-opt-exec-50AE0418/bin/tensorflow/compiler/mlir/lite/quantization/_objs/tflite_op_coverage_spec_getters_gen/tflite_op_coverage_spec_getters_gen.d '-frandom-seed=bazel-out/aarch64-opt-exec-50AE0418/bin/tensorflow/compiler/mlir/lite/quantization/_objs/tflite_op_coverage_spec_getters_gen/tflite_op_coverage_spec_getters_gen.o' '-DLLVM_ON_UNIX=1' '-DHAVE_BACKTRACE=1' '-DBACKTRACE_HEADER=' '-DLTDL_SHLIB_EXT="".so""' '-DLLVM_PLUGIN_EXT="".so""' '-DLLVM_ENABLE_THREADS=1' '-DHAVE_DEREGISTER_FRAME=1' '-DHAVE_LIBPTHREAD=1' '-DHAVE_PTHREAD_GETNAME_NP=1' '-DHAVE_PTHREAD_GETSPECIFIC=1' '-DHAVE_PTHREAD_H=1' '-DHAVE_PTHREAD_SETNAME_NP=1' '-DHAVE_REGISTER_FRAME=1' '-DHAVE_SETENV_R=1' '-DHAVE_STRERROR_R=1' '-DHAVE_SYSEXITS_H=1' '-DHAVE_UNISTD_H=1' -D_GNU_SOURCE '-DHAVE_LINK_H=1' '-DHAVE_LSEEK64=1' '-DHAVE_MALLINFO=1' '-DHAVE_SBRK=1' '-DHAVE_STRUCT_STAT_ST_MTIM_TV_NSEC=1' '-DLLVM_NATIVE_ARCH=""AArch64""' '-DLLVM_NATIVE_ASMPARSER=LLVMInitializeAArch64AsmParser' '-DLLVM_NATIVE_ASMPRINTER=LLVMInitializeAArch64AsmPrinter' '-DLLVM_NATIVE_DISASSEMBLER=LLVMInitializeAArch64Disassembler' '-DLLVM_NATIVE_TARGET=LLVMInitializeAArch64Target' '-DLLVM_NATIVE_TARGETINFO=LLVMInitializeAArch64TargetInfo' '-DLLVM_NATIVE_TARGETMC=LLVMInitializeAArch64TargetMC' '-DLLVM_NATIVE_TARGETMCA=LLVMInitializeAArch64TargetMCA' '-DLLVM_HOST_TRIPLE=""aarch64-unknown-linux-gnu""' '-DLLVM_DEFAULT_TARGET_TRIPLE=""aarch64-unknown-linux-gnu""' -D__STDC_LIMIT_MACROS -D__STDC_CONSTANT_MACROS -D__STDC_FORMAT_MACROS -iquote. -iquotebazel-out/aarch64-opt-exec-50AE0418/bin -iquoteexternal/com_google_absl -iquotebazel-out/aarch64-opt-exec-50AE0418/bin/external/com_google_absl -iquoteexternal/llvm-project -iquotebazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project -iquoteexternal/llvm_terminfo -iquotebazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm_terminfo -iquoteexternal/llvm_zlib -iquotebazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm_zlib -iquoteexternal/bazel_tools -iquotebazel-out/aarch64-opt-exec-50AE0418/bin/external/bazel_tools -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/BuiltinAttributeInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/BuiltinAttributesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/BuiltinDialectIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/BuiltinLocationAttributesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/BuiltinOpsIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/BuiltinTypeInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/BuiltinTypesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/CallOpInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/CastOpInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/FunctionInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/InferTypeOpInterfaceIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/OpAsmInterfaceIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/RegionKindInterfaceIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/SideEffectInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/SubElementInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/SymbolInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/TensorEncodingIncGen -isystem external/llvm-project/llvm/include -isystem bazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/llvm/include -isystem external/llvm-project/mlir/include -isystem bazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/include -g0 -w -g0 '-std=c++14' -DEIGEN_AVOID_STL_ARRAY -Iexternal/gemmlowp -Wno-sign-compare '-ftemplate-depth=900' -fno-exceptions '-DTENSORFLOW_USE_XLA=1' -pthread -fno-canonical-system-headers -Wno-builtin-macro-redefined '-D__DATE__=""redacted""' '-D__TIMESTAMP__=""redacted""' '-D__TIME__=""redacted""' -c tensorflow/compiler/mlir/lite/quantization/tools/tflite_op_coverage_spec_getters_gen.cc -o bazel-out/aarch64-opt-exec-50AE0418/bin/tensorflow/compiler/mlir/lite/quantization/_objs/tflite_op_coverage_spec_getters_gen/tflite_op_coverage_spec_getters_gen.o)
+# Configuration: 60dfdb78461e1be6bbf375554f969ad44a05ceccb450bdfffe3de8778874f0b9
+# Execution platform: @local_execution_config_platform//:platform
+tensorflow/compiler/mlir/lite/quantization/tools/tflite_op_coverage_spec_getters_gen.cc: In function 'bool CheckTypeConstraints(llvm::Init*, std::list >, bool)':
+tensorflow/compiler/mlir/lite/quantization/tools/tflite_op_coverage_spec_getters_gen.cc:139:49: error: no matching function for call to 'StrContains(llvm::StringRef&, const string&)'
+ 139 | if (!absl::StrContains(supported_types, type)) return false;
+ | ^
+In file included from tensorflow/compiler/mlir/lite/quantization/tools/tflite_op_coverage_spec_getters_gen.cc:20:
+external/com_google_absl/absl/strings/match.h:46:13: note: candidate: 'bool absl::lts_20211102::StrContains(absl::lts_20211102::string_view, absl::lts_20211102::string_view)'
+ 46 | inline bool StrContains(absl::string_view haystack,
+ | ^~~~~~~~~~~
+external/com_google_absl/absl/strings/match.h:46:43: note: no known conversion for argument 1 from 'llvm::StringRef' to 'absl::lts_20211102::string_view'
+ 46 | inline bool StrContains(absl::string_view haystack,
+ | ~~~~~~~~~~~~~~~~~~^~~~~~~~
+external/com_google_absl/absl/strings/match.h:51:13: note: candidate: 'bool absl::lts_20211102::StrContains(absl::lts_20211102::string_view, char)'
+ 51 | inline bool StrContains(absl::string_view haystack, char needle) noexcept {
+ | ^~~~~~~~~~~
+external/com_google_absl/absl/strings/match.h:51:43: note: no known conversion for argument 1 from 'llvm::StringRef' to 'absl::lts_20211102::string_view'
+ 51 | inline bool StrContains(absl::string_view haystack, char needle) noexcept {
+ | ~~~~~~~~~~~~~~~~~~^~~~~~~~
+INFO: Elapsed time: 64.881s, Critical Path: 44.85s
+
+
+**Provide the exact sequence of commands / steps that you executed before running into the problem**
+
+bazel test --test_timeout=300,500,-1,-1 --flaky_test_attempts=3 --test_output=all --cache_test_results=no --config=nonccl --verbose_failures --build_tag_filters=-no_oss,-oss_serial,-gpu,-tpu,-benchmark-test,-v1only,-no_aarch64,-requires-gpu --test_tag_filters=-no_oss,-oss_serial,-gpu,-tpu,-benchmark-test,-v1only,-no_aarch64,-requires-gpu --jobs=75 -- //tensorflow/... -//tensorflow/compiler/tf2tensorrt/... -//tensorflow/compiler/xrt/... -//tensorflow/core/tpu/... -//tensorflow/go/... -//tensorflow/java/... -//tensorflow/python/integration_testing/... -//tensorflow/tools/toolchains/... -//tensorflow/lite/... -//tensorflow/python/tools/... -//tensorflow/compiler/mlir/lite/tests:const-fold.mlir.test -//tensorflow/compiler/mlir/lite/tests:prepare-tf.mlir.test -//tensorflow/python/data/experimental/kernel_tests/service:fault_tolerance_test -//tensorflow/python/eager:function_test -//tensorflow/python/kernel_tests/linalg:self_adjoint_eig_op_test
+
+**Any other info / logs**
+Include any logs or source code that would be helpful to diagnose the problem. If including tracebacks, please include the full traceback. Large logs and files should be attached.
+",1.0,"Build of unit tests fails - Please make sure that this is a build/installation issue. As per our [GitHub Policy](https://github.com/tensorflow/tensorflow/blob/master/ISSUES.md), we only address code/doc bugs, performance issues, feature requests and build/installation issues on GitHub. tag:build_template
+
+**System information**
+- OS Platform and Distribution (e.g., Linux Ubuntu 16.04): Ubuntu 18.04
+- Mobile device (e.g. iPhone 8, Pixel 2, Samsung Galaxy) if the issue happens on mobile device: n/a
+- TensorFlow installed from (source or binary): source
+- TensorFlow version: git HEAD
+- Python version: 3.7.5
+- Installed using virtualenv? pip? conda?: no
+- Bazel version (if compiling from source): 5.0.0
+- GCC/Compiler version (if compiling from source): 10.3.0
+- CUDA/cuDNN version: n/a
+- GPU model and memory: n/a
+
+
+
+**Describe the problem**
+
+Building unit tests fails with
+
+================================================================================
+ERROR: /tmp/workspace/tensorflow-git/tensorflow/compiler/mlir/lite/quantization/BUILD:152:20: Compiling tensorflow/compiler/mlir/lite/quantization/tools/tflite_op_coverage_spec_getters_gen.cc failed: (Exit 1): gcc failed: error executing command
+ (cd /root/.cache/bazel/_bazel_root/db210f68f81d95ddcca9ae96b16ed72c/execroot/org_tensorflow && \
+ exec env - \
+ LD_LIBRARY_PATH=/opt/rh/devtoolset-10/root/usr/lib64:/opt/rh/devtoolset-10/root/usr/lib:/opt/rh/devtoolset-10/root/usr/lib64/dyninst:/opt/rh/devtoolset-10/root/usr/lib/dyninst:/usr/local/lib64:/usr/lib \
+ PATH=/tmp/workspace/venv-cp310-cp310/bin:/opt/rh/devtoolset-10/root/usr/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin \
+ PWD=/proc/self/cwd \
+ /opt/rh/devtoolset-10/root/usr/bin/gcc -U_FORTIFY_SOURCE -fstack-protector -Wall -Wunused-but-set-parameter -Wno-free-nonheap-object -fno-omit-frame-pointer -g0 -O2 '-D_FORTIFY_SOURCE=1' -DNDEBUG -ffunction-sections -fdata-sections '-std=c++11' -MD -MF bazel-out/aarch64-opt-exec-50AE0418/bin/tensorflow/compiler/mlir/lite/quantization/_objs/tflite_op_coverage_spec_getters_gen/tflite_op_coverage_spec_getters_gen.d '-frandom-seed=bazel-out/aarch64-opt-exec-50AE0418/bin/tensorflow/compiler/mlir/lite/quantization/_objs/tflite_op_coverage_spec_getters_gen/tflite_op_coverage_spec_getters_gen.o' '-DLLVM_ON_UNIX=1' '-DHAVE_BACKTRACE=1' '-DBACKTRACE_HEADER=' '-DLTDL_SHLIB_EXT="".so""' '-DLLVM_PLUGIN_EXT="".so""' '-DLLVM_ENABLE_THREADS=1' '-DHAVE_DEREGISTER_FRAME=1' '-DHAVE_LIBPTHREAD=1' '-DHAVE_PTHREAD_GETNAME_NP=1' '-DHAVE_PTHREAD_GETSPECIFIC=1' '-DHAVE_PTHREAD_H=1' '-DHAVE_PTHREAD_SETNAME_NP=1' '-DHAVE_REGISTER_FRAME=1' '-DHAVE_SETENV_R=1' '-DHAVE_STRERROR_R=1' '-DHAVE_SYSEXITS_H=1' '-DHAVE_UNISTD_H=1' -D_GNU_SOURCE '-DHAVE_LINK_H=1' '-DHAVE_LSEEK64=1' '-DHAVE_MALLINFO=1' '-DHAVE_SBRK=1' '-DHAVE_STRUCT_STAT_ST_MTIM_TV_NSEC=1' '-DLLVM_NATIVE_ARCH=""AArch64""' '-DLLVM_NATIVE_ASMPARSER=LLVMInitializeAArch64AsmParser' '-DLLVM_NATIVE_ASMPRINTER=LLVMInitializeAArch64AsmPrinter' '-DLLVM_NATIVE_DISASSEMBLER=LLVMInitializeAArch64Disassembler' '-DLLVM_NATIVE_TARGET=LLVMInitializeAArch64Target' '-DLLVM_NATIVE_TARGETINFO=LLVMInitializeAArch64TargetInfo' '-DLLVM_NATIVE_TARGETMC=LLVMInitializeAArch64TargetMC' '-DLLVM_NATIVE_TARGETMCA=LLVMInitializeAArch64TargetMCA' '-DLLVM_HOST_TRIPLE=""aarch64-unknown-linux-gnu""' '-DLLVM_DEFAULT_TARGET_TRIPLE=""aarch64-unknown-linux-gnu""' -D__STDC_LIMIT_MACROS -D__STDC_CONSTANT_MACROS -D__STDC_FORMAT_MACROS -iquote. -iquotebazel-out/aarch64-opt-exec-50AE0418/bin -iquoteexternal/com_google_absl -iquotebazel-out/aarch64-opt-exec-50AE0418/bin/external/com_google_absl -iquoteexternal/llvm-project -iquotebazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project -iquoteexternal/llvm_terminfo -iquotebazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm_terminfo -iquoteexternal/llvm_zlib -iquotebazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm_zlib -iquoteexternal/bazel_tools -iquotebazel-out/aarch64-opt-exec-50AE0418/bin/external/bazel_tools -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/BuiltinAttributeInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/BuiltinAttributesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/BuiltinDialectIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/BuiltinLocationAttributesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/BuiltinOpsIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/BuiltinTypeInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/BuiltinTypesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/CallOpInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/CastOpInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/FunctionInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/InferTypeOpInterfaceIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/OpAsmInterfaceIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/RegionKindInterfaceIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/SideEffectInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/SubElementInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/SymbolInterfacesIncGen -Ibazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/_virtual_includes/TensorEncodingIncGen -isystem external/llvm-project/llvm/include -isystem bazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/llvm/include -isystem external/llvm-project/mlir/include -isystem bazel-out/aarch64-opt-exec-50AE0418/bin/external/llvm-project/mlir/include -g0 -w -g0 '-std=c++14' -DEIGEN_AVOID_STL_ARRAY -Iexternal/gemmlowp -Wno-sign-compare '-ftemplate-depth=900' -fno-exceptions '-DTENSORFLOW_USE_XLA=1' -pthread -fno-canonical-system-headers -Wno-builtin-macro-redefined '-D__DATE__=""redacted""' '-D__TIMESTAMP__=""redacted""' '-D__TIME__=""redacted""' -c tensorflow/compiler/mlir/lite/quantization/tools/tflite_op_coverage_spec_getters_gen.cc -o bazel-out/aarch64-opt-exec-50AE0418/bin/tensorflow/compiler/mlir/lite/quantization/_objs/tflite_op_coverage_spec_getters_gen/tflite_op_coverage_spec_getters_gen.o)
+# Configuration: 60dfdb78461e1be6bbf375554f969ad44a05ceccb450bdfffe3de8778874f0b9
+# Execution platform: @local_execution_config_platform//:platform
+tensorflow/compiler/mlir/lite/quantization/tools/tflite_op_coverage_spec_getters_gen.cc: In function 'bool CheckTypeConstraints(llvm::Init*, std::list >, bool)':
+tensorflow/compiler/mlir/lite/quantization/tools/tflite_op_coverage_spec_getters_gen.cc:139:49: error: no matching function for call to 'StrContains(llvm::StringRef&, const string&)'
+ 139 | if (!absl::StrContains(supported_types, type)) return false;
+ | ^
+In file included from tensorflow/compiler/mlir/lite/quantization/tools/tflite_op_coverage_spec_getters_gen.cc:20:
+external/com_google_absl/absl/strings/match.h:46:13: note: candidate: 'bool absl::lts_20211102::StrContains(absl::lts_20211102::string_view, absl::lts_20211102::string_view)'
+ 46 | inline bool StrContains(absl::string_view haystack,
+ | ^~~~~~~~~~~
+external/com_google_absl/absl/strings/match.h:46:43: note: no known conversion for argument 1 from 'llvm::StringRef' to 'absl::lts_20211102::string_view'
+ 46 | inline bool StrContains(absl::string_view haystack,
+ | ~~~~~~~~~~~~~~~~~~^~~~~~~~
+external/com_google_absl/absl/strings/match.h:51:13: note: candidate: 'bool absl::lts_20211102::StrContains(absl::lts_20211102::string_view, char)'
+ 51 | inline bool StrContains(absl::string_view haystack, char needle) noexcept {
+ | ^~~~~~~~~~~
+external/com_google_absl/absl/strings/match.h:51:43: note: no known conversion for argument 1 from 'llvm::StringRef' to 'absl::lts_20211102::string_view'
+ 51 | inline bool StrContains(absl::string_view haystack, char needle) noexcept {
+ | ~~~~~~~~~~~~~~~~~~^~~~~~~~
+INFO: Elapsed time: 64.881s, Critical Path: 44.85s
+
+
+**Provide the exact sequence of commands / steps that you executed before running into the problem**
+
+bazel test --test_timeout=300,500,-1,-1 --flaky_test_attempts=3 --test_output=all --cache_test_results=no --config=nonccl --verbose_failures --build_tag_filters=-no_oss,-oss_serial,-gpu,-tpu,-benchmark-test,-v1only,-no_aarch64,-requires-gpu --test_tag_filters=-no_oss,-oss_serial,-gpu,-tpu,-benchmark-test,-v1only,-no_aarch64,-requires-gpu --jobs=75 -- //tensorflow/... -//tensorflow/compiler/tf2tensorrt/... -//tensorflow/compiler/xrt/... -//tensorflow/core/tpu/... -//tensorflow/go/... -//tensorflow/java/... -//tensorflow/python/integration_testing/... -//tensorflow/tools/toolchains/... -//tensorflow/lite/... -//tensorflow/python/tools/... -//tensorflow/compiler/mlir/lite/tests:const-fold.mlir.test -//tensorflow/compiler/mlir/lite/tests:prepare-tf.mlir.test -//tensorflow/python/data/experimental/kernel_tests/service:fault_tolerance_test -//tensorflow/python/eager:function_test -//tensorflow/python/kernel_tests/linalg:self_adjoint_eig_op_test
+
+**Any other info / logs**
+Include any logs or source code that would be helpful to diagnose the problem. If including tracebacks, please include the full traceback. Large logs and files should be attached.
+",0,build of unit tests fails please make sure that this is a build installation issue as per our we only address code doc bugs performance issues feature requests and build installation issues on github tag build template system information os platform and distribution e g linux ubuntu ubuntu mobile device e g iphone pixel samsung galaxy if the issue happens on mobile device n a tensorflow installed from source or binary source tensorflow version git head python version installed using virtualenv pip conda no bazel version if compiling from source gcc compiler version if compiling from source cuda cudnn version n a gpu model and memory n a describe the problem building unit tests fails with error tmp workspace tensorflow git tensorflow compiler mlir lite quantization build compiling tensorflow compiler mlir lite quantization tools tflite op coverage spec getters gen cc failed exit gcc failed error executing command cd root cache bazel bazel root execroot org tensorflow exec env ld library path opt rh devtoolset root usr opt rh devtoolset root usr lib opt rh devtoolset root usr dyninst opt rh devtoolset root usr lib dyninst usr local usr lib path tmp workspace venv bin opt rh devtoolset root usr bin usr local sbin usr local bin usr sbin usr bin sbin bin pwd proc self cwd opt rh devtoolset root usr bin gcc u fortify source fstack protector wall wunused but set parameter wno free nonheap object fno omit frame pointer d fortify source dndebug ffunction sections fdata sections std c md mf bazel out opt exec bin tensorflow compiler mlir lite quantization objs tflite op coverage spec getters gen tflite op coverage spec getters gen d frandom seed bazel out opt exec bin tensorflow compiler mlir lite quantization objs tflite op coverage spec getters gen tflite op coverage spec getters gen o dllvm on unix dhave backtrace dbacktrace header dltdl shlib ext so dllvm plugin ext so dllvm enable threads dhave deregister frame dhave libpthread dhave pthread getname np dhave pthread getspecific dhave pthread h dhave pthread setname np dhave register frame dhave setenv r dhave strerror r dhave sysexits h dhave unistd h d gnu source dhave link h dhave dhave mallinfo dhave sbrk dhave struct stat st mtim tv nsec dllvm native arch dllvm native asmparser dllvm native asmprinter dllvm native disassembler dllvm native target dllvm native targetinfo dllvm native targetmc dllvm native targetmca dllvm host triple unknown linux gnu dllvm default target triple unknown linux gnu d stdc limit macros d stdc constant macros d stdc format macros iquote iquotebazel out opt exec bin iquoteexternal com google absl iquotebazel out opt exec bin external com google absl iquoteexternal llvm project iquotebazel out opt exec bin external llvm project iquoteexternal llvm terminfo iquotebazel out opt exec bin external llvm terminfo iquoteexternal llvm zlib iquotebazel out opt exec bin external llvm zlib iquoteexternal bazel tools iquotebazel out opt exec bin external bazel tools ibazel out opt exec bin external llvm project mlir virtual includes builtinattributeinterfacesincgen ibazel out opt exec bin external llvm project mlir virtual includes builtinattributesincgen ibazel out opt exec bin external llvm project mlir virtual includes builtindialectincgen ibazel out opt exec bin external llvm project mlir virtual includes builtinlocationattributesincgen ibazel out opt exec bin external llvm project mlir virtual includes builtinopsincgen ibazel out opt exec bin external llvm project mlir virtual includes builtintypeinterfacesincgen ibazel out opt exec bin external llvm project mlir virtual includes builtintypesincgen ibazel out opt exec bin external llvm project mlir virtual includes callopinterfacesincgen ibazel out opt exec bin external llvm project mlir virtual includes castopinterfacesincgen ibazel out opt exec bin external llvm project mlir virtual includes functioninterfacesincgen ibazel out opt exec bin external llvm project mlir virtual includes infertypeopinterfaceincgen ibazel out opt exec bin external llvm project mlir virtual includes opasminterfaceincgen ibazel out opt exec bin external llvm project mlir virtual includes regionkindinterfaceincgen ibazel out opt exec bin external llvm project mlir virtual includes sideeffectinterfacesincgen ibazel out opt exec bin external llvm project mlir virtual includes subelementinterfacesincgen ibazel out opt exec bin external llvm project mlir virtual includes symbolinterfacesincgen ibazel out opt exec bin external llvm project mlir virtual includes tensorencodingincgen isystem external llvm project llvm include isystem bazel out opt exec bin external llvm project llvm include isystem external llvm project mlir include isystem bazel out opt exec bin external llvm project mlir include w std c deigen avoid stl array iexternal gemmlowp wno sign compare ftemplate depth fno exceptions dtensorflow use xla pthread fno canonical system headers wno builtin macro redefined d date redacted d timestamp redacted d time redacted c tensorflow compiler mlir lite quantization tools tflite op coverage spec getters gen cc o bazel out opt exec bin tensorflow compiler mlir lite quantization objs tflite op coverage spec getters gen tflite op coverage spec getters gen o configuration execution platform local execution config platform platform tensorflow compiler mlir lite quantization tools tflite op coverage spec getters gen cc in function bool checktypeconstraints llvm init std list bool tensorflow compiler mlir lite quantization tools tflite op coverage spec getters gen cc error no matching function for call to strcontains llvm stringref const string if absl strcontains supported types type return false in file included from tensorflow compiler mlir lite quantization tools tflite op coverage spec getters gen cc external com google absl absl strings match h note candidate bool absl lts strcontains absl lts string view absl lts string view inline bool strcontains absl string view haystack external com google absl absl strings match h note no known conversion for argument from llvm stringref to absl lts string view inline bool strcontains absl string view haystack external com google absl absl strings match h note candidate bool absl lts strcontains absl lts string view char inline bool strcontains absl string view haystack char needle noexcept external com google absl absl strings match h note no known conversion for argument from llvm stringref to absl lts string view inline bool strcontains absl string view haystack char needle noexcept info elapsed time critical path provide the exact sequence of commands steps that you executed before running into the problem bazel test test timeout flaky test attempts test output all cache test results no config nonccl verbose failures build tag filters no oss oss serial gpu tpu benchmark test no requires gpu test tag filters no oss oss serial gpu tpu benchmark test no requires gpu jobs tensorflow tensorflow compiler tensorflow compiler xrt tensorflow core tpu tensorflow go tensorflow java tensorflow python integration testing tensorflow tools toolchains tensorflow lite tensorflow python tools tensorflow compiler mlir lite tests const fold mlir test tensorflow compiler mlir lite tests prepare tf mlir test tensorflow python data experimental kernel tests service fault tolerance test tensorflow python eager function test tensorflow python kernel tests linalg self adjoint eig op test any other info logs include any logs or source code that would be helpful to diagnose the problem if including tracebacks please include the full traceback large logs and files should be attached ,0
+3361,6329602204.0,IssuesEvent,2017-07-26 03:44:04,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,overflow compability,compatibility rc3.1,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+`select -9223372036854775809;`
+
+
+2. What did you expect to see?
+
+`9223372036854775809` is overflow math.MaxInt64, but mysql convert it to Decimal type.
+
+```
+mysql> select -9223372036854775809;
+Field 1: `-9223372036854775809`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: NEWDECIMAL
+Collation: binary (63)
+Length: 20
+Max_length: 20
+Decimals: 0
+Flags: NOT_NULL BINARY NUM
+
+
++----------------------+
+| -9223372036854775809 |
++----------------------+
+| -9223372036854775809 |
++----------------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+but TiDB return 9223372036854775807 caused by int overflow, and still use LONGLONG type;
+
+```
+mysql> select -9223372036854775809;
+Field 1: `-9223372036854775809`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: LONGLONG
+Collation: binary (63)
+Length: 0
+Max_length: 19
+Decimals: 31
+Flags: BINARY NUM
+
+
++----------------------+
+| -9223372036854775809 |
++----------------------+
+| 9223372036854775807 |
++----------------------+
+1 row in set (0.00 sec)
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"overflow compability - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+`select -9223372036854775809;`
+
+
+2. What did you expect to see?
+
+`9223372036854775809` is overflow math.MaxInt64, but mysql convert it to Decimal type.
+
+```
+mysql> select -9223372036854775809;
+Field 1: `-9223372036854775809`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: NEWDECIMAL
+Collation: binary (63)
+Length: 20
+Max_length: 20
+Decimals: 0
+Flags: NOT_NULL BINARY NUM
+
+
++----------------------+
+| -9223372036854775809 |
++----------------------+
+| -9223372036854775809 |
++----------------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+but TiDB return 9223372036854775807 caused by int overflow, and still use LONGLONG type;
+
+```
+mysql> select -9223372036854775809;
+Field 1: `-9223372036854775809`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: LONGLONG
+Collation: binary (63)
+Length: 0
+Max_length: 19
+Decimals: 31
+Flags: BINARY NUM
+
+
++----------------------+
+| -9223372036854775809 |
++----------------------+
+| 9223372036854775807 |
++----------------------+
+1 row in set (0.00 sec)
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,overflow compability please answer these questions before submitting your issue thanks what did you do select what did you expect to see is overflow math but mysql convert it to decimal type mysql select field catalog def database table org table type newdecimal collation binary length max length decimals flags not null binary num row in set sec what did you see instead but tidb return caused by int overflow and still use longlong type mysql select field catalog def database table org table type longlong collation binary length max length decimals flags binary num row in set sec what version of tidb are you using tidb server v ,1
+7049,16342515565.0,IssuesEvent,2021-05-13 00:29:14,eclipse/omr,https://api.github.com/repos/eclipse/omr,opened,Prune vector IL opcodes,architecture review pending comp:compiler,"In preparation for re-architecting the vector IL opcodes to support wider vector lengths and element types, I believe some cleanup is in order to help focus our design choices on only a core set of opcodes we really need.
+
+At present, there are (at least) 109 vector IL opcodes. The vast majority of which are not used, documented, or tested, and have an incomplete implementation.
+
+Based on my investigation, we should keep the following as a base set of opcodes that we can think about expanding to wider vector lengths. There are uses for these opcodes in OpenJ9. Some of these even have Tril tests written for them. As we get more into the vector redesign more may be proposed to be pruned from this list.
+
+| IL Opcode |
+| :---------- |
+| vadd |
+| vsub |
+| vmul |
+| vdiv |
+| vneg |
+| vand |
+| vor |
+| vxor |
+| vnot |
+| vsplats |
+| v2v |
+| vl2vd |
+| vconst |
+| vload |
+| vloadi |
+| vstore |
+| vstorei |
+| vcmpeq |
+| vcmpne |
+| vcmplt |
+| vcmpgt |
+| vcmple |
+| vcmpge |
+| getvelem |
+| vsetelem |
+| v[id]setelem |
+| v[id]getelem |
+| v[bsilfd]RegLoad |
+| v[bsilfd]RegStore |
+
+The following IL opcodes may have some use when the vector opcodes are expanded to include different element sizes and may be worth keeping:
+
+| IL Opcode | Implemented Platforms |
+| :---------- | :-------------------: |
+| vicmpeq | P |
+| vicmpgt | P |
+| vicmpge | P |
+| vicmplt | P |
+| vicmple | P |
+| vdcmpeq | P |
+| vdcmpne | P |
+| vdcmpgt | P |
+| vdcmpge | P |
+| vdcmplt | P |
+| vdcmple | P |
+| vdmax | P |
+| vdmin | P |
+| vimin | P |
+| vimax | P |
+
+I recommend removing the following IL opcodes. As none of the list below has any known usage in OMR nor any known downstream projects I feel the justification to pardon any of these has to be strong enough to overcome eliminating the IL opcode now and re-introducing it later should the need arise. The advantage of introducing it again later is that it should come with proper justification, documentation, and Tril tests which are sorely lacking for all of these opcodes. Some of them could be reintroduced as intrinsics rather than opcodes.
+
+| IL Opcode | Implemented Platforms |
+| :---------- | :-------------------: |
+| virem | P |
+| vimergel | P |
+| vimergeh | P |
+| vicmpalleq | P |
+| vicmpallne | P |
+| vicmpallgt | P |
+| vicmpallge | P |
+| vicmpalllt | P |
+| vicmpallle | P |
+| vicmpanyeq | P |
+| vicmpanyne | P |
+| vicmpanygt | P |
+| vicmpanyge | P |
+| vicmpanylt | P |
+| vicmpanyle | P |
+| vdcmpalleq | P |
+| vdcmpallne | P |
+| vdcmpallgt | P |
+| vdcmpallge | P |
+| vdcmpalllt | P |
+| vdcmpallle | P |
+| vdcmpanyeq | P |
+| vdcmpanyne | P |
+| vdcmpanygt | P |
+| vdcmpanyge | P |
+| vdcmpanylt | P |
+| vdcmpanyle | P |
+| vucmplt | |
+| vucmpgt | |
+| vucmple | |
+| vucmpge | |
+| vselect | |
+| vinc | Z |
+| vdec | Z |
+| vperm | P |
+| vcom | Z |
+| vbitselect | P,Z |
+| vdmergel | P |
+| vdmergeh | P |
+| vdmsub | P |
+| vdmadd | P,Z |
+| vdnmsub | P |
+| vrem | Z |
+| vshl | Z |
+| vushr | Z |
+| vshr | Z |
+| vdsel | P |
+| vdrem | P |
+| vdsqrt | P |
+| vrand | Z |
+| vreturn | Z |
+| vcall | Z |
+| vcalli | Z |
+",1.0,"Prune vector IL opcodes - In preparation for re-architecting the vector IL opcodes to support wider vector lengths and element types, I believe some cleanup is in order to help focus our design choices on only a core set of opcodes we really need.
+
+At present, there are (at least) 109 vector IL opcodes. The vast majority of which are not used, documented, or tested, and have an incomplete implementation.
+
+Based on my investigation, we should keep the following as a base set of opcodes that we can think about expanding to wider vector lengths. There are uses for these opcodes in OpenJ9. Some of these even have Tril tests written for them. As we get more into the vector redesign more may be proposed to be pruned from this list.
+
+| IL Opcode |
+| :---------- |
+| vadd |
+| vsub |
+| vmul |
+| vdiv |
+| vneg |
+| vand |
+| vor |
+| vxor |
+| vnot |
+| vsplats |
+| v2v |
+| vl2vd |
+| vconst |
+| vload |
+| vloadi |
+| vstore |
+| vstorei |
+| vcmpeq |
+| vcmpne |
+| vcmplt |
+| vcmpgt |
+| vcmple |
+| vcmpge |
+| getvelem |
+| vsetelem |
+| v[id]setelem |
+| v[id]getelem |
+| v[bsilfd]RegLoad |
+| v[bsilfd]RegStore |
+
+The following IL opcodes may have some use when the vector opcodes are expanded to include different element sizes and may be worth keeping:
+
+| IL Opcode | Implemented Platforms |
+| :---------- | :-------------------: |
+| vicmpeq | P |
+| vicmpgt | P |
+| vicmpge | P |
+| vicmplt | P |
+| vicmple | P |
+| vdcmpeq | P |
+| vdcmpne | P |
+| vdcmpgt | P |
+| vdcmpge | P |
+| vdcmplt | P |
+| vdcmple | P |
+| vdmax | P |
+| vdmin | P |
+| vimin | P |
+| vimax | P |
+
+I recommend removing the following IL opcodes. As none of the list below has any known usage in OMR nor any known downstream projects I feel the justification to pardon any of these has to be strong enough to overcome eliminating the IL opcode now and re-introducing it later should the need arise. The advantage of introducing it again later is that it should come with proper justification, documentation, and Tril tests which are sorely lacking for all of these opcodes. Some of them could be reintroduced as intrinsics rather than opcodes.
+
+| IL Opcode | Implemented Platforms |
+| :---------- | :-------------------: |
+| virem | P |
+| vimergel | P |
+| vimergeh | P |
+| vicmpalleq | P |
+| vicmpallne | P |
+| vicmpallgt | P |
+| vicmpallge | P |
+| vicmpalllt | P |
+| vicmpallle | P |
+| vicmpanyeq | P |
+| vicmpanyne | P |
+| vicmpanygt | P |
+| vicmpanyge | P |
+| vicmpanylt | P |
+| vicmpanyle | P |
+| vdcmpalleq | P |
+| vdcmpallne | P |
+| vdcmpallgt | P |
+| vdcmpallge | P |
+| vdcmpalllt | P |
+| vdcmpallle | P |
+| vdcmpanyeq | P |
+| vdcmpanyne | P |
+| vdcmpanygt | P |
+| vdcmpanyge | P |
+| vdcmpanylt | P |
+| vdcmpanyle | P |
+| vucmplt | |
+| vucmpgt | |
+| vucmple | |
+| vucmpge | |
+| vselect | |
+| vinc | Z |
+| vdec | Z |
+| vperm | P |
+| vcom | Z |
+| vbitselect | P,Z |
+| vdmergel | P |
+| vdmergeh | P |
+| vdmsub | P |
+| vdmadd | P,Z |
+| vdnmsub | P |
+| vrem | Z |
+| vshl | Z |
+| vushr | Z |
+| vshr | Z |
+| vdsel | P |
+| vdrem | P |
+| vdsqrt | P |
+| vrand | Z |
+| vreturn | Z |
+| vcall | Z |
+| vcalli | Z |
+",0,prune vector il opcodes in preparation for re architecting the vector il opcodes to support wider vector lengths and element types i believe some cleanup is in order to help focus our design choices on only a core set of opcodes we really need at present there are at least vector il opcodes the vast majority of which are not used documented or tested and have an incomplete implementation based on my investigation we should keep the following as a base set of opcodes that we can think about expanding to wider vector lengths there are uses for these opcodes in some of these even have tril tests written for them as we get more into the vector redesign more may be proposed to be pruned from this list il opcode vadd vsub vmul vdiv vneg vand vor vxor vnot vsplats vconst vload vloadi vstore vstorei vcmpeq vcmpne vcmplt vcmpgt vcmple vcmpge getvelem vsetelem v setelem v getelem v regload v regstore the following il opcodes may have some use when the vector opcodes are expanded to include different element sizes and may be worth keeping il opcode implemented platforms vicmpeq p vicmpgt p vicmpge p vicmplt p vicmple p vdcmpeq p vdcmpne p vdcmpgt p vdcmpge p vdcmplt p vdcmple p vdmax p vdmin p vimin p vimax p i recommend removing the following il opcodes as none of the list below has any known usage in omr nor any known downstream projects i feel the justification to pardon any of these has to be strong enough to overcome eliminating the il opcode now and re introducing it later should the need arise the advantage of introducing it again later is that it should come with proper justification documentation and tril tests which are sorely lacking for all of these opcodes some of them could be reintroduced as intrinsics rather than opcodes il opcode implemented platforms virem p vimergel p vimergeh p vicmpalleq p vicmpallne p vicmpallgt p vicmpallge p vicmpalllt p vicmpallle p vicmpanyeq p vicmpanyne p vicmpanygt p vicmpanyge p vicmpanylt p vicmpanyle p vdcmpalleq p vdcmpallne p vdcmpallgt p vdcmpallge p vdcmpalllt p vdcmpallle p vdcmpanyeq p vdcmpanyne p vdcmpanygt p vdcmpanyge p vdcmpanylt p vdcmpanyle p vucmplt vucmpgt vucmple vucmpge vselect vinc z vdec z vperm p vcom z vbitselect p z vdmergel p vdmergeh p vdmsub p vdmadd p z vdnmsub p vrem z vshl z vushr z vshr z vdsel p vdrem p vdsqrt p vrand z vreturn z vcall z vcalli z ,0
+304111,9321276463.0,IssuesEvent,2019-03-27 03:07:53,k8smeetup/website-tasks,https://api.github.com/repos/k8smeetup/website-tasks,closed,/docs/reference/kubernetes-api/labels-annotations-taints.md,doc/core finished lang/zh priority/P0 version/1.12,"Path:`/docs/reference/kubernetes-api/labels-annotations-taints.md`
+
+[Source code](https://github.com/kubernetes/website/tree/release-1.12/content/en//docs/reference/kubernetes-api/labels-annotations-taints.md)",1.0,"/docs/reference/kubernetes-api/labels-annotations-taints.md - Path:`/docs/reference/kubernetes-api/labels-annotations-taints.md`
+
+[Source code](https://github.com/kubernetes/website/tree/release-1.12/content/en//docs/reference/kubernetes-api/labels-annotations-taints.md)",0, docs reference kubernetes api labels annotations taints md path: docs reference kubernetes api labels annotations taints md ,0
+12362,14623397954.0,IssuesEvent,2020-12-23 03:14:05,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,extended latin character set not support,component/charset type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```
+set names latin1;
+drop table if exists t1;
+create table t1(c varchar(1) not null, name varchar(64) not null) character set latin1;
+insert into t1 values(0xC0, 'LATIN CAPITAL LETTER A WITH GRAVE');
+```
+
+
+2. What did you expect to see?
+
+```
+mysql> create table t1(c varchar(1) not null, name varchar(64) not null);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> insert into t1 values(0xC0, 'LATIN CAPITAL LETTER A WITH GRAVE');
+Query OK, 1 row affected (0.01 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> create table t1(c varchar(1) not null, name varchar(64) not null);
+Query OK, 0 rows affected (0.08 sec)
+
+mysql> insert into t1 values(0xC0, 'LATIN CAPITAL LETTER A WITH GRAVE');
+ERROR 1366 (HY000): Incorrect value
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"extended latin character set not support - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```
+set names latin1;
+drop table if exists t1;
+create table t1(c varchar(1) not null, name varchar(64) not null) character set latin1;
+insert into t1 values(0xC0, 'LATIN CAPITAL LETTER A WITH GRAVE');
+```
+
+
+2. What did you expect to see?
+
+```
+mysql> create table t1(c varchar(1) not null, name varchar(64) not null);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> insert into t1 values(0xC0, 'LATIN CAPITAL LETTER A WITH GRAVE');
+Query OK, 1 row affected (0.01 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> create table t1(c varchar(1) not null, name varchar(64) not null);
+Query OK, 0 rows affected (0.08 sec)
+
+mysql> insert into t1 values(0xC0, 'LATIN CAPITAL LETTER A WITH GRAVE');
+ERROR 1366 (HY000): Incorrect value
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,extended latin character set not support please answer these questions before submitting your issue thanks what did you do set names drop table if exists create table c varchar not null name varchar not null character set insert into values latin capital letter a with grave what did you expect to see mysql create table c varchar not null name varchar not null query ok rows affected sec mysql insert into values latin capital letter a with grave query ok row affected sec what did you see instead mysql create table c varchar not null name varchar not null query ok rows affected sec mysql insert into values latin capital letter a with grave error incorrect value what version of tidb are you using tidb server v ,1
+10310,12297230960.0,IssuesEvent,2020-05-11 08:29:02,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Diff regexp matching result with MySQL 5.7 on multi-byte charsets,type/compatibility,"For example:
+```
+''' TiDB '''
+mysql> select version();
++---------------------------------------------+
+| version() |
++---------------------------------------------+
+| 5.7.10-TiDB-v2.0.0-rc.4-248-g25d7d74d-dirty |
++---------------------------------------------+
+1 row in set (0.01 sec)
+
+mysql> SHOW VARIABLES LIKE 'character%';
++--------------------------+--------------------------------------------------------+
+| Variable_name | Value |
++--------------------------+--------------------------------------------------------+
+| character_set_server | utf8 |
+| character_set_database | utf8 |
+| character_sets_dir | /usr/local/mysql-5.6.25-osx10.8-x86_64/share/charsets/ |
+| character_set_results | utf8 |
+| character_set_system | utf8 |
+| character_set_connection | utf8 |
+| character_set_client | utf8 |
+| character_set_filesystem | binary |
++--------------------------+--------------------------------------------------------+
+8 rows in set (0.01 sec)
+
+mysql> select ""我"" rlike ""^...$"";
++---------------------+
+| ""我"" rlike ""^...$"" |
++---------------------+
+| 0 |
++---------------------+
+1 row in set (0.00 sec)
+
+mysql> select ""我"" rlike ""^.$"";
++-------------------+
+| ""我"" rlike ""^.$"" |
++-------------------+
+| 1 |
++-------------------+
+1 row in set (0.00 sec)
+```
+
+```
+''' MySQL 5.7 '''
+mysql> select version();
++-----------+
+| version() |
++-----------+
+| 5.7.22 |
++-----------+
+1 row in set (0.00 sec)
+
+mysql> SHOW VARIABLES LIKE 'character%';
++--------------------------+-----------------------------------------------------------+
+| Variable_name | Value |
++--------------------------+-----------------------------------------------------------+
+| character_set_client | utf8 |
+| character_set_connection | utf8 |
+| character_set_database | utf8 |
+| character_set_filesystem | binary |
+| character_set_results | utf8 |
+| character_set_server | utf8 |
+| character_set_system | utf8 |
+| character_sets_dir | /usr/local/mysql-5.7.22-macos10.13-x86_64/share/charsets/ |
++--------------------------+-----------------------------------------------------------+
+8 rows in set (0.04 sec)
+
+mysql> select ""我"" rlike ""^...$"";
++---------------------+
+| ""我"" rlike ""^...$"" |
++---------------------+
+| 1 |
++---------------------+
+1 row in set (0.00 sec)
+
+mysql> select ""我"" rlike ""^.$"";
++-------------------+
+| ""我"" rlike ""^.$"" |
++-------------------+
+| 0 |
++-------------------+
+1 row in set (0.00 sec)
+
+```
+
+MySQL actually explained the per-byte matching behavior on multi-byte charsets, which differs on 8.0 and the prior versions('Prior to MySQL 8.0.4, MySQL used the Henry Spencer regular expression library to support regular expression operations, rather than International Components for Unicode (ICU).'):
+
+https://dev.mysql.com/doc/refman/8.0/en/regexp.html
+
+So, if currently TiDB aim to be compatible with MySQL 5.7, I guess this is a bug we need to fix",True,"Diff regexp matching result with MySQL 5.7 on multi-byte charsets - For example:
+```
+''' TiDB '''
+mysql> select version();
++---------------------------------------------+
+| version() |
++---------------------------------------------+
+| 5.7.10-TiDB-v2.0.0-rc.4-248-g25d7d74d-dirty |
++---------------------------------------------+
+1 row in set (0.01 sec)
+
+mysql> SHOW VARIABLES LIKE 'character%';
++--------------------------+--------------------------------------------------------+
+| Variable_name | Value |
++--------------------------+--------------------------------------------------------+
+| character_set_server | utf8 |
+| character_set_database | utf8 |
+| character_sets_dir | /usr/local/mysql-5.6.25-osx10.8-x86_64/share/charsets/ |
+| character_set_results | utf8 |
+| character_set_system | utf8 |
+| character_set_connection | utf8 |
+| character_set_client | utf8 |
+| character_set_filesystem | binary |
++--------------------------+--------------------------------------------------------+
+8 rows in set (0.01 sec)
+
+mysql> select ""我"" rlike ""^...$"";
++---------------------+
+| ""我"" rlike ""^...$"" |
++---------------------+
+| 0 |
++---------------------+
+1 row in set (0.00 sec)
+
+mysql> select ""我"" rlike ""^.$"";
++-------------------+
+| ""我"" rlike ""^.$"" |
++-------------------+
+| 1 |
++-------------------+
+1 row in set (0.00 sec)
+```
+
+```
+''' MySQL 5.7 '''
+mysql> select version();
++-----------+
+| version() |
++-----------+
+| 5.7.22 |
++-----------+
+1 row in set (0.00 sec)
+
+mysql> SHOW VARIABLES LIKE 'character%';
++--------------------------+-----------------------------------------------------------+
+| Variable_name | Value |
++--------------------------+-----------------------------------------------------------+
+| character_set_client | utf8 |
+| character_set_connection | utf8 |
+| character_set_database | utf8 |
+| character_set_filesystem | binary |
+| character_set_results | utf8 |
+| character_set_server | utf8 |
+| character_set_system | utf8 |
+| character_sets_dir | /usr/local/mysql-5.7.22-macos10.13-x86_64/share/charsets/ |
++--------------------------+-----------------------------------------------------------+
+8 rows in set (0.04 sec)
+
+mysql> select ""我"" rlike ""^...$"";
++---------------------+
+| ""我"" rlike ""^...$"" |
++---------------------+
+| 1 |
++---------------------+
+1 row in set (0.00 sec)
+
+mysql> select ""我"" rlike ""^.$"";
++-------------------+
+| ""我"" rlike ""^.$"" |
++-------------------+
+| 0 |
++-------------------+
+1 row in set (0.00 sec)
+
+```
+
+MySQL actually explained the per-byte matching behavior on multi-byte charsets, which differs on 8.0 and the prior versions('Prior to MySQL 8.0.4, MySQL used the Henry Spencer regular expression library to support regular expression operations, rather than International Components for Unicode (ICU).'):
+
+https://dev.mysql.com/doc/refman/8.0/en/regexp.html
+
+So, if currently TiDB aim to be compatible with MySQL 5.7, I guess this is a bug we need to fix",1,diff regexp matching result with mysql on multi byte charsets for example tidb mysql select version version tidb rc dirty row in set sec mysql show variables like character variable name value character set server character set database character sets dir usr local mysql share charsets character set results character set system character set connection character set client character set filesystem binary rows in set sec mysql select 我 rlike 我 rlike row in set sec mysql select 我 rlike 我 rlike row in set sec mysql mysql select version version row in set sec mysql show variables like character variable name value character set client character set connection character set database character set filesystem binary character set results character set server character set system character sets dir usr local mysql share charsets rows in set sec mysql select 我 rlike 我 rlike row in set sec mysql select 我 rlike 我 rlike row in set sec mysql actually explained the per byte matching behavior on multi byte charsets which differs on and the prior versions prior to mysql mysql used the henry spencer regular expression library to support regular expression operations rather than international components for unicode icu so if currently tidb aim to be compatible with mysql i guess this is a bug we need to fix,1
+11774,13888397906.0,IssuesEvent,2020-10-19 06:13:45,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Support for typed system variables when running SELECT @@foreign_key_checks,type/compatibility,"when client queries variable 'foreign_key_checks', tidb sends string value 'OFF' to them. But mysql server always sends '0' or '1' in spite of versions. So any client tools won't raise any exception when talks to mysql server and can parse the value of 'foreign_key_checks' to an integer, while tidb's response will lead to a failure on parsing.
+_below are the tcpdump captures:_
+
+**tidb latest**
+
+> 17:21:13.365154 IP 121-36-228-111.4000 > 192.168.0.156.49446: Flags [P.], seq 2183:2280, ack 1663, win 251, options [nop,nop,TS val 2768261666 ecr 2298205247], length 97
+E.....@.?..o...,.......&.....<9............
+..R""...?.....>....def....@@foreign_key_checks.@@foreign_key_checks...........................OFF....
+
+**mysql server 5.7**
+
+> 17:23:46.235028 IP chaoswork.mysql > chaoswork.57500: Flags [P.], seq 2113:2181, ack 1681, win 512, options [nop,nop,TS val 3449871429 ecr 3449871429], length 68
+E..x.[@.@.W""..................)......l.....
+...E...E.....*....def....@@foreign_key_checks..?................0...........
+
+**flyway encountered an exception**
+>org.flywaydb.core.internal.exception.FlywaySqlException:
+Unable to determine value for 'foreign_key_checks' variable
+ -----------------------------------------------------------
+SQL State : 22018
+Error Code : 0
+Message : Cannot determine value type from string 'OFF' at org.flywaydb.core.internal.database.mysql.MySQLConnection.getIntVariableValue(MySQLConnection.java:64) ~[flyway-core-6.2.4.jar!/:na]
+ at org.flywaydb.core.internal.database.mysql.MySQLConnection.(MySQLConnection.java:56) ~[flyway-core-6.2.4.jar!/:na]",True,"Support for typed system variables when running SELECT @@foreign_key_checks - when client queries variable 'foreign_key_checks', tidb sends string value 'OFF' to them. But mysql server always sends '0' or '1' in spite of versions. So any client tools won't raise any exception when talks to mysql server and can parse the value of 'foreign_key_checks' to an integer, while tidb's response will lead to a failure on parsing.
+_below are the tcpdump captures:_
+
+**tidb latest**
+
+> 17:21:13.365154 IP 121-36-228-111.4000 > 192.168.0.156.49446: Flags [P.], seq 2183:2280, ack 1663, win 251, options [nop,nop,TS val 2768261666 ecr 2298205247], length 97
+E.....@.?..o...,.......&.....<9............
+..R""...?.....>....def....@@foreign_key_checks.@@foreign_key_checks...........................OFF....
+
+**mysql server 5.7**
+
+> 17:23:46.235028 IP chaoswork.mysql > chaoswork.57500: Flags [P.], seq 2113:2181, ack 1681, win 512, options [nop,nop,TS val 3449871429 ecr 3449871429], length 68
+E..x.[@.@.W""..................)......l.....
+...E...E.....*....def....@@foreign_key_checks..?................0...........
+
+**flyway encountered an exception**
+>org.flywaydb.core.internal.exception.FlywaySqlException:
+Unable to determine value for 'foreign_key_checks' variable
+ -----------------------------------------------------------
+SQL State : 22018
+Error Code : 0
+Message : Cannot determine value type from string 'OFF' at org.flywaydb.core.internal.database.mysql.MySQLConnection.getIntVariableValue(MySQLConnection.java:64) ~[flyway-core-6.2.4.jar!/:na]
+ at org.flywaydb.core.internal.database.mysql.MySQLConnection.(MySQLConnection.java:56) ~[flyway-core-6.2.4.jar!/:na]",1,support for typed system variables when running select foreign key checks when client queries variable foreign key checks tidb sends string value off to them but mysql server always sends or in spite of versions so any client tools won t raise any exception when talks to mysql server and can parse the value of foreign key checks to an integer while tidb s response will lead to a failure on parsing below are the tcpdump captures tidb latest ip flags seq ack win options length e o r def foreign key checks foreign key checks off mysql server ip chaoswork mysql chaoswork flags seq ack win options length e x w l e e def foreign key checks flyway encountered an exception org flywaydb core internal exception flywaysqlexception unable to determine value for foreign key checks variable sql state error code message cannot determine value type from string off at org flywaydb core internal database mysql mysqlconnection getintvariablevalue mysqlconnection java at org flywaydb core internal database mysql mysqlconnection mysqlconnection java ,1
+73868,15286182123.0,IssuesEvent,2021-02-23 14:25:28,idonthaveafifaaddiction/IoT-Smart-Gateway,https://api.github.com/repos/idonthaveafifaaddiction/IoT-Smart-Gateway,opened,CVE-2020-28500 (Medium) detected in lodash-1.0.2.tgz,security vulnerability,"## CVE-2020-28500 - Medium Severity Vulnerability
+ Vulnerable Library - lodash-1.0.2.tgz
+
+
A utility library delivering consistency, customization, performance, and extras.
-Race condition in the ath_tx_aggr_sleep function in drivers/net/wireless/ath/ath9k/xmit.c in the Linux kernel before 3.13.7 allows remote attackers to cause a denial of service (system crash) via a large amount of network traffic that triggers certain list deletions.
+All versions of package lodash; all versions of package org.fujion.webjars:lodash are vulnerable to Regular Expression Denial of Service (ReDoS) via the toNumber, trim and trimEnd functions. Steps to reproduce (provided by reporter Liyuan Chen): var lo = require('lodash'); function build_blank (n) { var ret = ""1"" for (var i = 0; i < n; i++) { ret += "" "" } return ret + ""1""; } var s = build_blank(50000) var time0 = Date.now(); lo.trim(s) var time_cost0 = Date.now() - time0; console.log(""time_cost0: "" + time_cost0) var time1 = Date.now(); lo.toNumber(s) var time_cost1 = Date.now() - time1; console.log(""time_cost1: "" + time_cost1) var time2 = Date.now(); lo.trimEnd(s) var time_cost2 = Date.now() - time2; console.log(""time_cost2: "" + time_cost2)
-
-
-
-
-
-
-***
-Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",True,"CVE-2014-2672 (Medium) detected in linux-stable-rtv3.8.6 - ## CVE-2014-2672 - Medium Severity Vulnerability
- Vulnerable Library - linux-stable-rtv3.8.6
-
-Race condition in the ath_tx_aggr_sleep function in drivers/net/wireless/ath/ath9k/xmit.c in the Linux kernel before 3.13.7 allows remote attackers to cause a denial of service (system crash) via a large amount of network traffic that triggers certain list deletions.
+All versions of package lodash; all versions of package org.fujion.webjars:lodash are vulnerable to Regular Expression Denial of Service (ReDoS) via the toNumber, trim and trimEnd functions. Steps to reproduce (provided by reporter Liyuan Chen): var lo = require('lodash'); function build_blank (n) { var ret = ""1"" for (var i = 0; i < n; i++) { ret += "" "" } return ret + ""1""; } var s = build_blank(50000) var time0 = Date.now(); lo.trim(s) var time_cost0 = Date.now() - time0; console.log(""time_cost0: "" + time_cost0) var time1 = Date.now(); lo.toNumber(s) var time_cost1 = Date.now() - time1; console.log(""time_cost1: "" + time_cost1) var time2 = Date.now(); lo.trimEnd(s) var time_cost2 = Date.now() - time2; console.log(""time_cost2: "" + time_cost2)
-
+",0,cve medium detected in lodash tgz cve medium severity vulnerability vulnerable library lodash tgz a utility library delivering consistency customization performance and extras library home page a href path to dependency file iot smart gateway web package json path to vulnerable library iot smart gateway web node modules globule node modules lodash package json dependency hierarchy gulp tgz root library vinyl fs tgz glob watcher tgz gaze tgz globule tgz x lodash tgz vulnerable library found in head commit a href found in base branch develop vulnerability details all versions of package lodash all versions of package org fujion webjars lodash are vulnerable to regular expression denial of service redos via the tonumber trim and trimend functions steps to reproduce provided by reporter liyuan chen var lo require lodash function build blank n var ret for var i i n i ret return ret var s build blank var date now lo trim s var time date now console log time time var date now lo tonumber s var time date now console log time time var date now lo trimend s var time date now console log time time publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact low for more information on scores click a href isopenpronvulnerability false ispackagebased true isdefaultbranch true packages istransitivedependency true dependencytree gulp vinyl fs glob watcher gaze globule lodash isminimumfixversionavailable false basebranches vulnerabilityidentifier cve vulnerabilitydetails all versions of package lodash all versions of package org fujion webjars lodash are vulnerable to regular expression denial of service redos via the tonumber trim and trimend functions steps to reproduce provided by reporter liyuan chen var lo require function build blank n var ret for var i i n i ret return ret var s build blank var date now lo trim s var time date now console log time time var date now lo tonumber s var time date now console log time time var date now lo trimend s var time date now console log time time vulnerabilityurl ,0
+83599,7876177083.0,IssuesEvent,2018-06-25 23:29:17,Microsoft/vscode,https://api.github.com/repos/Microsoft/vscode,opened,Test: Webview persistence api,testplan-item,"Test for #49022 #48542
+
+Complexity: 3
+
+- [ ] Any OS
+- [ ] Any OS
+
+**Summary**
+A new api for webview serialization has been added. This allows webviews to both save their state between becoming hidden and visible, as well as saving their state when VS Code restarts
+
+**Test**
+Try adding the two types of persistence to the new webview (you can use the [cat coding example](https://github.com/Microsoft/vscode-extension-samples/blob/master/webview-sample/) for this)
+
+Visibility persistence is implemented using a `getState` and `setState` method inside the webview itself:
+
+```ts
+const vscode = acquireVsCodeApi();
+const state = vscode.getState();
+vscode.setState({ abc: 123 })
+```
+
+Serialization uses [`WebviewPanelSerializer`](https://github.com/Microsoft/vscode/blob/f5300ced7fbd0193babf05ee37860bb2d160beb7/src/vs/vscode.d.ts#L5423) and [`registerWebviewPanelSerializer`](https://github.com/Microsoft/vscode/blob/f5300ced7fbd0193babf05ee37860bb2d160beb7/src/vs/vscode.d.ts#L5942) to register a handler in the extension that can revive a webview from its state.
+
+
+**Things to test:**
+
+* Can you implement the two types of persistence?
+* Does the API documentation make sense? (I'll be writing docs for it too but have not finished these yet)
+* Are there cases where the new APIs may not work?",1.0,"Test: Webview persistence api - Test for #49022 #48542
+
+Complexity: 3
+
+- [ ] Any OS
+- [ ] Any OS
+
+**Summary**
+A new api for webview serialization has been added. This allows webviews to both save their state between becoming hidden and visible, as well as saving their state when VS Code restarts
+
+**Test**
+Try adding the two types of persistence to the new webview (you can use the [cat coding example](https://github.com/Microsoft/vscode-extension-samples/blob/master/webview-sample/) for this)
+
+Visibility persistence is implemented using a `getState` and `setState` method inside the webview itself:
+
+```ts
+const vscode = acquireVsCodeApi();
+const state = vscode.getState();
+vscode.setState({ abc: 123 })
+```
+
+Serialization uses [`WebviewPanelSerializer`](https://github.com/Microsoft/vscode/blob/f5300ced7fbd0193babf05ee37860bb2d160beb7/src/vs/vscode.d.ts#L5423) and [`registerWebviewPanelSerializer`](https://github.com/Microsoft/vscode/blob/f5300ced7fbd0193babf05ee37860bb2d160beb7/src/vs/vscode.d.ts#L5942) to register a handler in the extension that can revive a webview from its state.
+
+
+**Things to test:**
+
+* Can you implement the two types of persistence?
+* Does the API documentation make sense? (I'll be writing docs for it too but have not finished these yet)
+* Are there cases where the new APIs may not work?",0,test webview persistence api test for complexity any os any os summary a new api for webview serialization has been added this allows webviews to both save their state between becoming hidden and visible as well as saving their state when vs code restarts test try adding the two types of persistence to the new webview you can use the for this visibility persistence is implemented using a getstate and setstate method inside the webview itself ts const vscode acquirevscodeapi const state vscode getstate vscode setstate abc serialization uses and to register a handler in the extension that can revive a webview from its state things to test can you implement the two types of persistence does the api documentation make sense i ll be writing docs for it too but have not finished these yet are there cases where the new apis may not work ,0
+3272,6222643867.0,IssuesEvent,2017-07-10 09:40:10,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,The field of `select 'a' from t1;` is wrong,compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+```
+create table t1(a int);
+insert into t value(1);
+select 'a' from t1;
+```
+
+2. What did you expect to see?
+```
++---+
+| a |
++---+
+| a |
++---+
+```
+
+
+3. What did you see instead?
+```
++------+
+| 'a' |
++------+
+| a |
++------+
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"The field of `select 'a' from t1;` is wrong - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+```
+create table t1(a int);
+insert into t value(1);
+select 'a' from t1;
+```
+
+2. What did you expect to see?
+```
++---+
+| a |
++---+
+| a |
++---+
+```
+
+
+3. What did you see instead?
+```
++------+
+| 'a' |
++------+
+| a |
++------+
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,the field of select a from is wrong please answer these questions before submitting your issue thanks what did you do create table a int insert into t value select a from what did you expect to see a a what did you see instead a a what version of tidb are you using tidb server v ,1
+11031,13065168365.0,IssuesEvent,2020-07-30 19:20:31,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,ifnull should not do type conversion?,type/compatibility,"This is a compatibility issue.
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+use test;
+create table t1 (id int unsigned);
+insert into t1 values (NULL);
+select ifnull(id, -1) from t1;
+```
+
+2. What did you expect to see?
+
+This is the output when executed on MySQL
+
+```sql
+MariaDB [test]> create table t1 (id int unsigned);
+Query OK, 0 rows affected (0.13 sec)
+
+MariaDB [test]> insert into t1 values (NULL);
+Query OK, 1 row affected (0.00 sec)
+
+MariaDB [test]> select ifnull(id, -1) from t1;
++----------------+
+| ifnull(id, -1) |
++----------------+
+| -1 |
++----------------+
+1 row in set (0.00 sec)
+
+MariaDB [test]>
+
+```
+
+
+3. What did you see instead?
+
+```sql
+TiDB-Server [test]> create table t1 (id int unsigned);
+Query OK, 0 rows affected (0.01 sec)
+
+TiDB-Server [test]> insert into t1 values (NULL);
+Query OK, 1 row affected (0.00 sec)
+
+TiDB-Server [test]> select ifnull(id, -1) from t1;
++----------------------+
+| ifnull(id, -1) |
++----------------------+
+| 18446744073709551615 |
++----------------------+
+1 row in set (0.00 sec)
+```
+
+since ifnull can also so use string as second parameter, convert from int to unsinged int seems not necessary.
+
+``` sql
+
+MySQL [test]> select ifnull(id, 'a') from t1;
++-----------------+
+| ifnull(id, 'a') |
++-----------------+
+| a |
++-----------------+
+1 row in set (0.01 sec)
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+Git Commit Hash: b1a3244e73e038589ab993ab02267528254ffcb2
+
+",True,"ifnull should not do type conversion? - This is a compatibility issue.
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+use test;
+create table t1 (id int unsigned);
+insert into t1 values (NULL);
+select ifnull(id, -1) from t1;
+```
+
+2. What did you expect to see?
+
+This is the output when executed on MySQL
+
+```sql
+MariaDB [test]> create table t1 (id int unsigned);
+Query OK, 0 rows affected (0.13 sec)
+
+MariaDB [test]> insert into t1 values (NULL);
+Query OK, 1 row affected (0.00 sec)
+
+MariaDB [test]> select ifnull(id, -1) from t1;
++----------------+
+| ifnull(id, -1) |
++----------------+
+| -1 |
++----------------+
+1 row in set (0.00 sec)
+
+MariaDB [test]>
+
+```
+
+
+3. What did you see instead?
+
+```sql
+TiDB-Server [test]> create table t1 (id int unsigned);
+Query OK, 0 rows affected (0.01 sec)
+
+TiDB-Server [test]> insert into t1 values (NULL);
+Query OK, 1 row affected (0.00 sec)
+
+TiDB-Server [test]> select ifnull(id, -1) from t1;
++----------------------+
+| ifnull(id, -1) |
++----------------------+
+| 18446744073709551615 |
++----------------------+
+1 row in set (0.00 sec)
+```
+
+since ifnull can also so use string as second parameter, convert from int to unsinged int seems not necessary.
+
+``` sql
+
+MySQL [test]> select ifnull(id, 'a') from t1;
++-----------------+
+| ifnull(id, 'a') |
++-----------------+
+| a |
++-----------------+
+1 row in set (0.01 sec)
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+Git Commit Hash: b1a3244e73e038589ab993ab02267528254ffcb2
+
+",1,ifnull should not do type conversion this is a compatibility issue what did you do if possible provide a recipe for reproducing the error sql use test create table id int unsigned insert into values null select ifnull id from what did you expect to see this is the output when executed on mysql sql mariadb create table id int unsigned query ok rows affected sec mariadb insert into values null query ok row affected sec mariadb select ifnull id from ifnull id row in set sec mariadb what did you see instead sql tidb server create table id int unsigned query ok rows affected sec tidb server insert into values null query ok row affected sec tidb server select ifnull id from ifnull id row in set sec since ifnull can also so use string as second parameter convert from int to unsinged int seems not necessary sql mysql select ifnull id a from ifnull id a a row in set sec what version of tidb are you using tidb server v git commit hash ,1
+10671,12609985513.0,IssuesEvent,2020-06-12 03:25:44,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,reopened,Feature request: Support CHECKSUM TABLE command,status/help-wanted type/compatibility type/enhancement,"When importing data into TiDB we want to be sure the data is correct. A convenient command in MySQL is CHECKSUM TABLE and this command is not currently supported by TiDB.
-
-
-
+Adding it would make it easy to confirm if the data loaded in from an external source matches or not.
-***
-Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",0,cve medium detected in linux stable cve medium severity vulnerability vulnerable library linux stable julia cartwright s fork of linux stable rt git library home page a href found in head commit a href found in base branch master vulnerable source files drivers net wireless ath xmit c vulnerability details race condition in the ath tx aggr sleep function in drivers net wireless ath xmit c in the linux kernel before allows remote attackers to cause a denial of service system crash via a large amount of network traffic that triggers certain list deletions publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with mend ,0
-298070,9195554656.0,IssuesEvent,2019-03-07 02:55:34,kubeflow/katib,https://api.github.com/repos/kubeflow/katib,closed,StudyJob controller shouldn't crash if PyTorch (or other job operators not installed),area/katib kind/bug priority/p1,"See: kubeflow/kubeflow#2212
+Example I did something like:
-User reports that the StudyJob controller crashes if pytorch operator isn't installed on the cluster.
+`$ ssh mysqlhost sudo mysqldump test SomeTable | mysql -h tidbhost -P 4000 -u root -D test`
-Logs for StudyJobController
+MySQL 5.6:
```
-$ kubectl logs -n kubeflow studyjob-controller-7d77f959-pjfzf
-2019/01/06 22:43:34 Registering Components.
-2019/01/06 22:43:34 controller.AddToManager(mgr)
-2019/01/06 22:43:34 no matches for kind ""PyTorchJob"" in version ""kubeflow.org/v1beta1""
+root@mysqlhost [test]> checksum table SomeTable;
++-----------+------------+
+| Table | Checksum |
++-----------+------------+
+| SomeTable | 2867272629 |
++-----------+------------+
+1 row in set (0.01 sec)
```
-This seems like a bug. If a particular job controller isn't installed I would still expect katib and StudyJobs to work with other types of job controllers.",1.0,"StudyJob controller shouldn't crash if PyTorch (or other job operators not installed) - See: kubeflow/kubeflow#2212
-
-User reports that the StudyJob controller crashes if pytorch operator isn't installed on the cluster.
-
-Logs for StudyJobController
+TiDB:
```
-$ kubectl logs -n kubeflow studyjob-controller-7d77f959-pjfzf
-2019/01/06 22:43:34 Registering Components.
-2019/01/06 22:43:34 controller.AddToManager(mgr)
-2019/01/06 22:43:34 no matches for kind ""PyTorchJob"" in version ""kubeflow.org/v1beta1""
+root@tidbhost [test]> checksum table SomeTable;
+ERROR 1105 (HY000): line 0 column 8 near "" table SomeTable""
+root@tidbhost [test]>
```
-This seems like a bug. If a particular job controller isn't installed I would still expect katib and StudyJobs to work with other types of job controllers.",0,studyjob controller shouldn t crash if pytorch or other job operators not installed see kubeflow kubeflow user reports that the studyjob controller crashes if pytorch operator isn t installed on the cluster logs for studyjobcontroller kubectl logs n kubeflow studyjob controller pjfzf registering components controller addtomanager mgr no matches for kind pytorchjob in version kubeflow org this seems like a bug if a particular job controller isn t installed i would still expect katib and studyjobs to work with other types of job controllers ,0
-6614,8881908724.0,IssuesEvent,2019-01-14 11:34:23,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,sql_mode ALLOW_INVALID_DATES is not supported,type/compatibility,"## Feature Request
-
-**Is your feature request related to a problem? Please describe:**
-
-Relates to #2738 - currently `ALLOW_INVALID_DATES` is not supported. It is not commonly used, but could be useful for compatibility.
-
-**Describe the feature you'd like:**
-```
-# testcase
-CREATE TABLE d1 (d DATE);
-SET sql_mode='STRICT_TRANS_TABLES,ALLOW_INVALID_DATES';
-INSERT INTO d1 VALUES ('2010-00-01');
-```
-Passes in MySQL, produces this in TiDB:
-```
-MySQL [test]> SET sql_mode='STRICT_TRANS_TABLES,ALLOW_INVALID_DATES';
-ERROR 1105 (HY000): ERROR 1231 (42000): Variable 'sql_mode' can't be set to the value of 'ALLOW_INVALID_DATES'
-MySQL [test]> INSERT INTO d1 VALUES ('2010-00-01');
-ERROR 1292 (22007): Incorrect datetime value: '2010-00-01'
-```
+So providing some sort of CHECKSUM table command would be great.
+",True,"Feature request: Support CHECKSUM TABLE command - When importing data into TiDB we want to be sure the data is correct. A convenient command in MySQL is CHECKSUM TABLE and this command is not currently supported by TiDB.
-**Describe alternatives you've considered:**
-Possible to document as unsupported.
+Adding it would make it easy to confirm if the data loaded in from an external source matches or not.
-**Teachability, Documentation, Adoption, Migration Strategy:**
-Improves compatibility with MySQL.",True,"sql_mode ALLOW_INVALID_DATES is not supported - ## Feature Request
+Example I did something like:
-**Is your feature request related to a problem? Please describe:**
+`$ ssh mysqlhost sudo mysqldump test SomeTable | mysql -h tidbhost -P 4000 -u root -D test`
-Relates to #2738 - currently `ALLOW_INVALID_DATES` is not supported. It is not commonly used, but could be useful for compatibility.
+MySQL 5.6:
-**Describe the feature you'd like:**
-```
-# testcase
-CREATE TABLE d1 (d DATE);
-SET sql_mode='STRICT_TRANS_TABLES,ALLOW_INVALID_DATES';
-INSERT INTO d1 VALUES ('2010-00-01');
```
-Passes in MySQL, produces this in TiDB:
-```
-MySQL [test]> SET sql_mode='STRICT_TRANS_TABLES,ALLOW_INVALID_DATES';
-ERROR 1105 (HY000): ERROR 1231 (42000): Variable 'sql_mode' can't be set to the value of 'ALLOW_INVALID_DATES'
-MySQL [test]> INSERT INTO d1 VALUES ('2010-00-01');
-ERROR 1292 (22007): Incorrect datetime value: '2010-00-01'
+root@mysqlhost [test]> checksum table SomeTable;
++-----------+------------+
+| Table | Checksum |
++-----------+------------+
+| SomeTable | 2867272629 |
++-----------+------------+
+1 row in set (0.01 sec)
```
-**Describe alternatives you've considered:**
-Possible to document as unsupported.
-
-**Teachability, Documentation, Adoption, Migration Strategy:**
-Improves compatibility with MySQL.",1,sql mode allow invalid dates is not supported feature request is your feature request related to a problem please describe relates to currently allow invalid dates is not supported it is not commonly used but could be useful for compatibility describe the feature you d like testcase create table d date set sql mode strict trans tables allow invalid dates insert into values passes in mysql produces this in tidb mysql set sql mode strict trans tables allow invalid dates error error variable sql mode can t be set to the value of allow invalid dates mysql insert into values error incorrect datetime value describe alternatives you ve considered possible to document as unsupported teachability documentation adoption migration strategy improves compatibility with mysql ,1
-20584,30582031316.0,IssuesEvent,2023-07-21 10:24:46,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,"Default value for TEXT, BLOB or JSON columns",type/bug type/compatibility sig/sql-infra compatibility-mysql8,"## Bug Report
-
-TiDB doesn't allow a default value for TEXT, BLOB or JSON columns.
-
-### 1. Minimal reproduce step (Required)
-
-```sql
-CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT 'foo');
-CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT ('foo'));
-SHOW CREATE TABLE t1\G
-INSERT INTO t1(id) VALUES(1);
-TABLE t1;
-```
-
-### 2. What did you expect to see? (Required)
-
-With MySQL 8.1.0:
-```
-sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT 'foo');
-ERROR: 1101 (42000): BLOB, TEXT, GEOMETRY or JSON column 'c1' can't have a default value
-
-sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT ('foo'));
-Query OK, 0 rows affected (0.0586 sec)
-
-sql> SHOW CREATE TABLE t1\G
-*************************** 1. row ***************************
- Table: t1
-Create Table: CREATE TABLE `t1` (
- `id` int NOT NULL,
- `c1` text COLLATE utf8mb4_general_ci DEFAULT (_utf8mb4'foo'),
- PRIMARY KEY (`id`)
-) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_general_ci
-1 row in set (0.0184 sec)
-
-sql> INSERT INTO t1(id) VALUES(1);
-Query OK, 1 row affected (0.0076 sec)
-
-sql> TABLE t1;
-+----+-----+
-| id | c1 |
-+----+-----+
-| 1 | foo |
-+----+-----+
-1 row in set (0.0009 sec)
-```
-### 3. What did you see instead (Required)
+TiDB:
```
-sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT 'foo');
-ERROR: 1101 (42000): BLOB/TEXT/JSON column 'c1' can't have a default value
-
-sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT ('foo'));
-ERROR: 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your TiDB version for the right syntax to use line 1 column 59 near ""'foo'))""
-
-...
+root@tidbhost [test]> checksum table SomeTable;
+ERROR 1105 (HY000): line 0 column 8 near "" table SomeTable""
+root@tidbhost [test]>
```
-### 4. What is your TiDB version? (Required)
+So providing some sort of CHECKSUM table command would be great.
+",1,feature request support checksum table command when importing data into tidb we want to be sure the data is correct a convenient command in mysql is checksum table and this command is not currently supported by tidb adding it would make it easy to confirm if the data loaded in from an external source matches or not example i did something like ssh mysqlhost sudo mysqldump test sometable mysql h tidbhost p u root d test mysql root mysqlhost checksum table sometable table checksum sometable row in set sec tidb root tidbhost checksum table sometable error line column near table sometable root tidbhost so providing some sort of checksum table command would be great ,1
+55431,14008919999.0,IssuesEvent,2020-10-29 00:58:17,mwilliams7197/bootstrap,https://api.github.com/repos/mwilliams7197/bootstrap,closed,"CVE-2018-19797 (Medium) detected in node-sass-4.11.0.tgz, opennmsopennms-source-24.1.2-1 - autoclosed",security vulnerability,"## CVE-2018-19797 - Medium Severity Vulnerability
+ Vulnerable Libraries - node-sass-4.11.0.tgz, opennmsopennms-source-24.1.2-1
+
-
+node-sass-4.11.0.tgz
-```
-Release Version: v7.2.0
-Edition: Community
-Git Commit Hash: 9fd5f4a8e4f273a60fbe7d3848f85a1be8f0600b
-Git Branch: heads/refs/tags/v7.2.0
-UTC Build Time: 2023-06-27 15:04:42
-GoVersion: go1.20.5
-Race Enabled: false
-Check Table Before Drop: false
-Store: tikv
-```",True,"Default value for TEXT, BLOB or JSON columns - ## Bug Report
-
-TiDB doesn't allow a default value for TEXT, BLOB or JSON columns.
-
-### 1. Minimal reproduce step (Required)
-
-```sql
-CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT 'foo');
-CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT ('foo'));
-SHOW CREATE TABLE t1\G
-INSERT INTO t1(id) VALUES(1);
-TABLE t1;
-```
+
Path to vulnerable library: bootstrap/node_modules/node-sass/package.json
+
-### 2. What did you expect to see? (Required)
+Dependency Hierarchy:
+ - :x: **node-sass-4.11.0.tgz** (Vulnerable Library)
+
-With MySQL 8.1.0:
-```
-sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT 'foo');
-ERROR: 1101 (42000): BLOB, TEXT, GEOMETRY or JSON column 'c1' can't have a default value
-
-sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT ('foo'));
-Query OK, 0 rows affected (0.0586 sec)
-
-sql> SHOW CREATE TABLE t1\G
-*************************** 1. row ***************************
- Table: t1
-Create Table: CREATE TABLE `t1` (
- `id` int NOT NULL,
- `c1` text COLLATE utf8mb4_general_ci DEFAULT (_utf8mb4'foo'),
- PRIMARY KEY (`id`)
-) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_general_ci
-1 row in set (0.0184 sec)
-
-sql> INSERT INTO t1(id) VALUES(1);
-Query OK, 1 row affected (0.0076 sec)
-
-sql> TABLE t1;
-+----+-----+
-| id | c1 |
-+----+-----+
-| 1 | foo |
-+----+-----+
-1 row in set (0.0009 sec)
-```
-### 3. What did you see instead (Required)
+
Found in base branch: v4-dev
+
+
+
+ Vulnerability Details
+
+
+In LibSass 3.5.5, a NULL Pointer Dereference in the function Sass::Selector_List::populate_extends in SharedPtr.hpp (used by ast.cpp and ast_selectors.cpp) may cause a Denial of Service (application crash) via a crafted sass input file.
-```
-sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT 'foo');
-ERROR: 1101 (42000): BLOB/TEXT/JSON column 'c1' can't have a default value
+
-sql> CREATE TABLE t1 (id INT PRIMARY KEY, c1 TEXT DEFAULT ('foo'));
-ERROR: 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your TiDB version for the right syntax to use line 1 column 59 near ""'foo'))""
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Network
+ - Attack Complexity: Low
+ - Privileges Required: None
+ - User Interaction: Required
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: None
+ - Integrity Impact: None
+ - Availability Impact: High
+
+For more information on CVSS3 Scores, click here.
+
+
+
+ Suggested Fix
+
-### 4. What is your TiDB version? (Required)
+
+
+
-
+***
+
+- [ ] Check this box to open an automated fix PR
+
-```
-Release Version: v7.2.0
-Edition: Community
-Git Commit Hash: 9fd5f4a8e4f273a60fbe7d3848f85a1be8f0600b
-Git Branch: heads/refs/tags/v7.2.0
-UTC Build Time: 2023-06-27 15:04:42
-GoVersion: go1.20.5
-Race Enabled: false
-Check Table Before Drop: false
-Store: tikv
-```",1,default value for text blob or json columns bug report tidb doesn t allow a default value for text blob or json columns minimal reproduce step required sql create table id int primary key text default foo create table id int primary key text default foo show create table g insert into id values table what did you expect to see required with mysql sql create table id int primary key text default foo error blob text geometry or json column can t have a default value sql create table id int primary key text default foo query ok rows affected sec sql show create table g row table create table create table id int not null text collate general ci default foo primary key id engine innodb default charset collate general ci row in set sec sql insert into id values query ok row affected sec sql table id foo row in set sec what did you see instead required sql create table id int primary key text default foo error blob text json column can t have a default value sql create table id int primary key text default foo error you have an error in your sql syntax check the manual that corresponds to your tidb version for the right syntax to use line column near foo what is your tidb version required release version edition community git commit hash git branch heads refs tags utc build time goversion race enabled false check table before drop false store tikv ,1
-8816,10764654481.0,IssuesEvent,2019-11-01 08:56:17,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Support use `on duplicate key update b=default` in generated columns,type/bug type/compatibility,"## Bug Report
+",True,"CVE-2018-19797 (Medium) detected in node-sass-4.11.0.tgz, opennmsopennms-source-24.1.2-1 - autoclosed - ## CVE-2018-19797 - Medium Severity Vulnerability
+ Vulnerable Libraries - node-sass-4.11.0.tgz, opennmsopennms-source-24.1.2-1
+
-Please answer these questions before submitting your issue. Thanks!
+node-sass-4.11.0.tgz
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-```
-mysql> create table t1 (a int unique,
- -> b int generated always as (-a) virtual,
- -> c int generated always as (-a) stored);
-Query OK, 0 rows affected (0.01 sec)
+
-mysql> insert into t1 values (1,default,default)
- -> on duplicate key update a=2, b=default;
+
Found in base branch: v4-dev
+
+
+
+ Vulnerability Details
+
+
+In LibSass 3.5.5, a NULL Pointer Dereference in the function Sass::Selector_List::populate_extends in SharedPtr.hpp (used by ast.cpp and ast_selectors.cpp) may cause a Denial of Service (application crash) via a crafted sass input file.
-```
-2. What did you expect to see?
+
-```
-Query OK, 1 row affected (0.01 sec)
-```
+
+
+
+***
+
+- [ ] Check this box to open an automated fix PR
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-```
-Release Version: v4.0.0-alpha-693-gada724a2a
-```
-",True,"Support use `on duplicate key update b=default` in generated columns - ## Bug Report
+",0,cve medium detected in node sass tgz opennmsopennms source autoclosed cve medium severity vulnerability vulnerable libraries node sass tgz opennmsopennms source node sass tgz wrapper around libsass library home page a href path to dependency file bootstrap package json path to vulnerable library bootstrap node modules node sass package json dependency hierarchy x node sass tgz vulnerable library found in base branch dev vulnerability details in libsass a null pointer dereference in the function sass selector list populate extends in sharedptr hpp used by ast cpp and ast selectors cpp may cause a denial of service application crash via a crafted sass input file publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution libsass check this box to open an automated fix pr isopenpronvulnerability false ispackagebased true isdefaultbranch true packages vulnerabilityidentifier cve vulnerabilitydetails in libsass a null pointer dereference in the function sass selector list populate extends in sharedptr hpp used by ast cpp and ast selectors cpp may cause a denial of service application crash via a crafted sass input file vulnerabilityurl ,0
+6054,8489350550.0,IssuesEvent,2018-10-26 19:36:28,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,LOAD DATA LOCAL INFILE does not update processlist,type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+I imported sample data in 8 threads into TiDB using `LOAD DATA LOCAL INFILE` (script called from an xargs on ls):
+```
+#!/bin/sh
+echo $1
+mysql bikeshare -e ""LOAD DATA LOCAL INFILE '$1' INTO TABLE trips FIELDS TERMINATED BY ',' ENCLOSED BY '\""' LINES TERMINATED BY '\r\n' (duration, start_date, end_date, start_station_number, start_station, end_station_number, end_station, bike_number, member_type)"";
+```
+I was trying to see the status of the files in `SHOW PROCESSLIST` or `SHOW FULL PROCESSLIST`:
+
+```
+mysql> show full processlist;
++------+------+-----------+-----------+---------+------+-------+-----------------------+------+
+| Id | User | Host | db | Command | Time | State | Info | Mem |
++------+------+-----------+-----------+---------+------+-------+-----------------------+------+
+| 58 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
+| 60 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
+| 7 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
+| 63 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
+| 52 | root | 127.0.0.1 | | Query | 0 | 2 | show full processlist | 0 |
+| 64 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
+| 65 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
+| 66 | root | 127.0.0.1 | | Query | 25 | 2 | select sleep(60) | 0 |
+| 62 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
+| 54 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
++------+------+-----------+-----------+---------+------+-------+-----------------------+------+
+10 rows in set (0.00 sec)
+```
+
+2. What did you expect to see?
+
+It looks like the `Time` and `Info` columns are not updated for `LOAD DATA LOCAL INFILE`. There is an existing bug report on `State` not updating. For a normal select query, `Time` and `Info` update fine.
+
+3. What did you see instead?
+
+Same behavior as a long-running select. Here is a MySQL 8.0 example (it is useful to see `info` populated):
+
+```
+mysql [localhost] {msandbox} ((none)) > show processlist;
++----+-----------------+-----------+-----------+---------+------+------------------------+------------------------------------------------------------------------------------------------------+
+| Id | User | Host | db | Command | Time | State | Info |
++----+-----------------+-----------+-----------+---------+------+------------------------+------------------------------------------------------------------------------------------------------+
+| 4 | event_scheduler | localhost | NULL | Daemon | 1439 | Waiting on empty queue | NULL |
+| 37 | msandbox | localhost | NULL | Query | 0 | starting | show processlist |
+| 55 | msandbox | localhost | bikeshare | Query | 439 | query end | LOAD DATA LOCAL INFILE '2016Q3-capitalbikeshare-tripdata.csv' INTO TABLE trips FIELDS TERMINATED BY |
+| 60 | msandbox | localhost | bikeshare | Query | 439 | executing | LOAD DATA LOCAL INFILE '2017Q3-capitalbikeshare-tripdata.csv' INTO TABLE trips FIELDS TERMINATED BY |
+| 62 | msandbox | localhost | bikeshare | Query | 439 | executing | LOAD DATA LOCAL INFILE '2017Q2-capitalbikeshare-tripdata.csv' INTO TABLE trips FIELDS TERMINATED BY |
++----+-----------------+-----------+-----------+---------+------+------------------------+------------------------------------------------------------------------------------------------------+
+5 rows in set (0.00 sec)
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+I'm running a branch which has tracing. I built it today:
+```
+mysql> select tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: rc1-3104-g51046aa7
+Git Commit Hash: 51046aa717e782d3843ae2c91f0a0952de05a4e5
+Git Branch: tidb_tracing_prototype
+UTC Build Time: 2018-08-23 08:21:06
+GoVersion: go version go1.10.1 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+1 row in set (0.00 sec)
+```",True,"LOAD DATA LOCAL INFILE does not update processlist - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+I imported sample data in 8 threads into TiDB using `LOAD DATA LOCAL INFILE` (script called from an xargs on ls):
+```
+#!/bin/sh
+echo $1
+mysql bikeshare -e ""LOAD DATA LOCAL INFILE '$1' INTO TABLE trips FIELDS TERMINATED BY ',' ENCLOSED BY '\""' LINES TERMINATED BY '\r\n' (duration, start_date, end_date, start_station_number, start_station, end_station_number, end_station, bike_number, member_type)"";
+```
+I was trying to see the status of the files in `SHOW PROCESSLIST` or `SHOW FULL PROCESSLIST`:
+
+```
+mysql> show full processlist;
++------+------+-----------+-----------+---------+------+-------+-----------------------+------+
+| Id | User | Host | db | Command | Time | State | Info | Mem |
++------+------+-----------+-----------+---------+------+-------+-----------------------+------+
+| 58 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
+| 60 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
+| 7 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
+| 63 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
+| 52 | root | 127.0.0.1 | | Query | 0 | 2 | show full processlist | 0 |
+| 64 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
+| 65 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
+| 66 | root | 127.0.0.1 | | Query | 25 | 2 | select sleep(60) | 0 |
+| 62 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
+| 54 | root | 127.0.0.1 | bikeshare | Query | 0 | 2 | | 0 |
++------+------+-----------+-----------+---------+------+-------+-----------------------+------+
+10 rows in set (0.00 sec)
+```
+
+2. What did you expect to see?
+
+It looks like the `Time` and `Info` columns are not updated for `LOAD DATA LOCAL INFILE`. There is an existing bug report on `State` not updating. For a normal select query, `Time` and `Info` update fine.
+
+3. What did you see instead?
+
+Same behavior as a long-running select. Here is a MySQL 8.0 example (it is useful to see `info` populated):
+
+```
+mysql [localhost] {msandbox} ((none)) > show processlist;
++----+-----------------+-----------+-----------+---------+------+------------------------+------------------------------------------------------------------------------------------------------+
+| Id | User | Host | db | Command | Time | State | Info |
++----+-----------------+-----------+-----------+---------+------+------------------------+------------------------------------------------------------------------------------------------------+
+| 4 | event_scheduler | localhost | NULL | Daemon | 1439 | Waiting on empty queue | NULL |
+| 37 | msandbox | localhost | NULL | Query | 0 | starting | show processlist |
+| 55 | msandbox | localhost | bikeshare | Query | 439 | query end | LOAD DATA LOCAL INFILE '2016Q3-capitalbikeshare-tripdata.csv' INTO TABLE trips FIELDS TERMINATED BY |
+| 60 | msandbox | localhost | bikeshare | Query | 439 | executing | LOAD DATA LOCAL INFILE '2017Q3-capitalbikeshare-tripdata.csv' INTO TABLE trips FIELDS TERMINATED BY |
+| 62 | msandbox | localhost | bikeshare | Query | 439 | executing | LOAD DATA LOCAL INFILE '2017Q2-capitalbikeshare-tripdata.csv' INTO TABLE trips FIELDS TERMINATED BY |
++----+-----------------+-----------+-----------+---------+------+------------------------+------------------------------------------------------------------------------------------------------+
+5 rows in set (0.00 sec)
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+I'm running a branch which has tracing. I built it today:
+```
+mysql> select tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: rc1-3104-g51046aa7
+Git Commit Hash: 51046aa717e782d3843ae2c91f0a0952de05a4e5
+Git Branch: tidb_tracing_prototype
+UTC Build Time: 2018-08-23 08:21:06
+GoVersion: go version go1.10.1 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+1 row in set (0.00 sec)
+```",1,load data local infile does not update processlist please answer these questions before submitting your issue thanks what did you do i imported sample data in threads into tidb using load data local infile script called from an xargs on ls bin sh echo mysql bikeshare e load data local infile into table trips fields terminated by enclosed by lines terminated by r n duration start date end date start station number start station end station number end station bike number member type i was trying to see the status of the files in show processlist or show full processlist mysql show full processlist id user host db command time state info mem root bikeshare query root bikeshare query root bikeshare query root bikeshare query root query show full processlist root bikeshare query root bikeshare query root query select sleep root bikeshare query root bikeshare query rows in set sec what did you expect to see it looks like the time and info columns are not updated for load data local infile there is an existing bug report on state not updating for a normal select query time and info update fine what did you see instead same behavior as a long running select here is a mysql example it is useful to see info populated mysql msandbox none show processlist id user host db command time state info event scheduler localhost null daemon waiting on empty queue null msandbox localhost null query starting show processlist msandbox localhost bikeshare query query end load data local infile capitalbikeshare tripdata csv into table trips fields terminated by msandbox localhost bikeshare query executing load data local infile capitalbikeshare tripdata csv into table trips fields terminated by msandbox localhost bikeshare query executing load data local infile capitalbikeshare tripdata csv into table trips fields terminated by rows in set sec what version of tidb are you using tidb server v or run select tidb version on tidb i m running a branch which has tracing i built it today mysql select tidb version g row tidb version release version git commit hash git branch tidb tracing prototype utc build time goversion go version linux race enabled false tikv min version alpha row in set sec ,1
+11073,13098917162.0,IssuesEvent,2020-08-03 20:28:55,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Privilege check failed error to be consistent with MySQL,type/compatibility type/duplicate,"https://github.com/pingcap/tidb/blob/master/planner/core/planbuilder.go#L1208
+
+visitInfo.err is used to return to the client when the privilege check is failed. we should keep the error message consistent with MySQL, using `nil` will return only `privilege check fail`
+
+```
+// CheckPrivilege checks the privilege for a user.
+func CheckPrivilege(pm privilege.Manager, vs []visitInfo) error {
+ for _, v := range vs {
+ if !pm.RequestVerification(v.db, v.table, v.column, v.privilege) {
+ if v.err == nil {
+ return ErrPrivilegeCheckFail
+ }
+ return v.err
+ }
+ }
+ return nil
+}
+```",True,"Privilege check failed error to be consistent with MySQL - https://github.com/pingcap/tidb/blob/master/planner/core/planbuilder.go#L1208
+
+visitInfo.err is used to return to the client when the privilege check is failed. we should keep the error message consistent with MySQL, using `nil` will return only `privilege check fail`
+
+```
+// CheckPrivilege checks the privilege for a user.
+func CheckPrivilege(pm privilege.Manager, vs []visitInfo) error {
+ for _, v := range vs {
+ if !pm.RequestVerification(v.db, v.table, v.column, v.privilege) {
+ if v.err == nil {
+ return ErrPrivilegeCheckFail
+ }
+ return v.err
+ }
+ }
+ return nil
+}
+```",1,privilege check failed error to be consistent with mysql visitinfo err is used to return to the client when the privilege check is failed we should keep the error message consistent with mysql using nil will return only privilege check fail checkprivilege checks the privilege for a user func checkprivilege pm privilege manager vs visitinfo error for v range vs if pm requestverification v db v table v column v privilege if v err nil return errprivilegecheckfail return v err return nil ,1
+583350,17383026475.0,IssuesEvent,2021-08-01 04:32:02,huridocs/uwazi,https://api.github.com/repos/huridocs/uwazi,closed,Certain entities cannot be edited,Bug Priority: High Sprint,"In one of the instances, some country entities cannot be edited.
+
+1. Filter for 'Countries'
+2. Select 'Uruguay': A generic error message will show (""An error has occured"")
+3. Click 'Edit': The same error message shows and editing is not possible
+
+This error occurs only for some of the countries. It has not been observed with any other document type.
+All countries have geolocations and most are connected with other entities via relationships.",1.0,"Certain entities cannot be edited - In one of the instances, some country entities cannot be edited.
+
+1. Filter for 'Countries'
+2. Select 'Uruguay': A generic error message will show (""An error has occured"")
+3. Click 'Edit': The same error message shows and editing is not possible
+
+This error occurs only for some of the countries. It has not been observed with any other document type.
+All countries have geolocations and most are connected with other entities via relationships.",0,certain entities cannot be edited in one of the instances some country entities cannot be edited filter for countries select uruguay a generic error message will show an error has occured click edit the same error message shows and editing is not possible this error occurs only for some of the countries it has not been observed with any other document type all countries have geolocations and most are connected with other entities via relationships ,0
+7733,9973786046.0,IssuesEvent,2019-07-09 09:07:42,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Function information in error message should take along with database name,for new contributors help wanted type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```mysql
+SELECT xxx( NULL );
+```
+
+2. What did you expect to see?
+
+```
+ERROR 1305 (42000): FUNCTION randgen_test.xxx does not exist
+```
+
+3. What did you see instead?
+
+Function information should be . format.
+```
+ERROR 1305 (42000): FUNCTION xxx does not exist
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+",True,"Function information in error message should take along with database name - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```mysql
+SELECT xxx( NULL );
+```
+
+2. What did you expect to see?
+
+```
+ERROR 1305 (42000): FUNCTION randgen_test.xxx does not exist
+```
+
+3. What did you see instead?
+
+Function information should be . format.
+```
+ERROR 1305 (42000): FUNCTION xxx does not exist
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+",1,function information in error message should take along with database name bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error mysql select xxx null what did you expect to see error function randgen test xxx does not exist what did you see instead function information should be format error function xxx does not exist what version of tidb are you using tidb server v or run select tidb version on tidb ,1
+66508,20252405379.0,IssuesEvent,2022-02-14 19:16:03,idaholab/HERON,https://api.github.com/repos/idaholab/HERON,opened,[DEFECT] Building documentation broken for Windows,defect,"--------
+Defect Description
+--------
+
+**Describe the defect**
+
+##### What did you expect to see happen?
+There seem to be two methods to build the documentation on Windows. At least one of these methods should work.
+
+##### What did you see instead?
+Method 1:
+Using git bash, running `bash make_docs.sh` under /HERON/doc/ gives the following error:
+```
+Building manuals ...
+... building in user_manual...
+bash: make_win.sh: No such file or directory
+... ... failed to make docs in user_manual
+```
+
+Method 2:
+Using git bash, running `bash make_docs.bat` under /HERON/doc/user_manual/ gives the following error:
+```
+Starting to compile manual...
+make_docs.bat: line 4: copy_tex.sh: command not found
+```
+
+##### Do you have a suggested fix for the development team?
+For method 1, there needs to be a `make_win.sh` file.
+For method 2, changing line 4 of `make_docs.bat` to `bash copy_tex.sh` should fix this issue.
+
+**Describe how to Reproduce**
+Steps to reproduce the behavior:
+1. Run `bash make_docs.sh` under /HERON/doc/ with git bash on Windows
+2. Run `bash make_docs.bat` under /HERON/doc/user_manual/ with git bash on Windows
+3.
+4.
+
+**Screenshots and Input Files**
+Please attach the input file(s) that generate this error. The simpler the input, the faster we can find the issue.
+
+**Platform (please complete the following information):**
+ - OS: Windows
+ - Version: 10
+ - Dependencies Installation: CONDA
+
+----------------
+For Change Control Board: Issue Review
+----------------
+This review should occur before any development is performed as a response to this issue.
+- [ ] 1. Is it tagged with a type: defect or task?
+- [ ] 2. Is it tagged with a priority: critical, normal or minor?
+- [ ] 3. If it will impact requirements or requirements tests, is it tagged with requirements?
+- [ ] 4. If it is a defect, can it cause wrong results for users? If so an email needs to be sent to the users.
+- [ ] 5. Is a rationale provided? (Such as explaining why the improvement is needed or why current code is wrong.)
+
+-------
+For Change Control Board: Issue Closure
+-------
+This review should occur when the issue is imminently going to be closed.
+- [ ] 1. If the issue is a defect, is the defect fixed?
+- [ ] 2. If the issue is a defect, is the defect tested for in the regression test system? (If not explain why not.)
+- [ ] 3. If the issue can impact users, has an email to the users group been written (the email should specify if the defect impacts stable or master)?
+- [ ] 4. If the issue is a defect, does it impact the latest release branch? If yes, is there any issue tagged with release (create if needed)?
+- [ ] 5. If the issue is being closed without a pull request, has an explanation of why it is being closed been provided?
+",1.0,"[DEFECT] Building documentation broken for Windows - --------
+Defect Description
+--------
+
+**Describe the defect**
+
+##### What did you expect to see happen?
+There seem to be two methods to build the documentation on Windows. At least one of these methods should work.
+
+##### What did you see instead?
+Method 1:
+Using git bash, running `bash make_docs.sh` under /HERON/doc/ gives the following error:
+```
+Building manuals ...
+... building in user_manual...
+bash: make_win.sh: No such file or directory
+... ... failed to make docs in user_manual
+```
+
+Method 2:
+Using git bash, running `bash make_docs.bat` under /HERON/doc/user_manual/ gives the following error:
+```
+Starting to compile manual...
+make_docs.bat: line 4: copy_tex.sh: command not found
+```
+
+##### Do you have a suggested fix for the development team?
+For method 1, there needs to be a `make_win.sh` file.
+For method 2, changing line 4 of `make_docs.bat` to `bash copy_tex.sh` should fix this issue.
+
+**Describe how to Reproduce**
+Steps to reproduce the behavior:
+1. Run `bash make_docs.sh` under /HERON/doc/ with git bash on Windows
+2. Run `bash make_docs.bat` under /HERON/doc/user_manual/ with git bash on Windows
+3.
+4.
+
+**Screenshots and Input Files**
+Please attach the input file(s) that generate this error. The simpler the input, the faster we can find the issue.
+
+**Platform (please complete the following information):**
+ - OS: Windows
+ - Version: 10
+ - Dependencies Installation: CONDA
+
+----------------
+For Change Control Board: Issue Review
+----------------
+This review should occur before any development is performed as a response to this issue.
+- [ ] 1. Is it tagged with a type: defect or task?
+- [ ] 2. Is it tagged with a priority: critical, normal or minor?
+- [ ] 3. If it will impact requirements or requirements tests, is it tagged with requirements?
+- [ ] 4. If it is a defect, can it cause wrong results for users? If so an email needs to be sent to the users.
+- [ ] 5. Is a rationale provided? (Such as explaining why the improvement is needed or why current code is wrong.)
+
+-------
+For Change Control Board: Issue Closure
+-------
+This review should occur when the issue is imminently going to be closed.
+- [ ] 1. If the issue is a defect, is the defect fixed?
+- [ ] 2. If the issue is a defect, is the defect tested for in the regression test system? (If not explain why not.)
+- [ ] 3. If the issue can impact users, has an email to the users group been written (the email should specify if the defect impacts stable or master)?
+- [ ] 4. If the issue is a defect, does it impact the latest release branch? If yes, is there any issue tagged with release (create if needed)?
+- [ ] 5. If the issue is being closed without a pull request, has an explanation of why it is being closed been provided?
+",0, building documentation broken for windows defect description describe the defect what did you expect to see happen there seem to be two methods to build the documentation on windows at least one of these methods should work what did you see instead method using git bash running bash make docs sh under heron doc gives the following error building manuals building in user manual bash make win sh no such file or directory failed to make docs in user manual method using git bash running bash make docs bat under heron doc user manual gives the following error starting to compile manual make docs bat line copy tex sh command not found do you have a suggested fix for the development team for method there needs to be a make win sh file for method changing line of make docs bat to bash copy tex sh should fix this issue describe how to reproduce steps to reproduce the behavior run bash make docs sh under heron doc with git bash on windows run bash make docs bat under heron doc user manual with git bash on windows screenshots and input files please attach the input file s that generate this error the simpler the input the faster we can find the issue platform please complete the following information os windows version dependencies installation conda for change control board issue review this review should occur before any development is performed as a response to this issue is it tagged with a type defect or task is it tagged with a priority critical normal or minor if it will impact requirements or requirements tests is it tagged with requirements if it is a defect can it cause wrong results for users if so an email needs to be sent to the users is a rationale provided such as explaining why the improvement is needed or why current code is wrong for change control board issue closure this review should occur when the issue is imminently going to be closed if the issue is a defect is the defect fixed if the issue is a defect is the defect tested for in the regression test system if not explain why not if the issue can impact users has an email to the users group been written the email should specify if the defect impacts stable or master if the issue is a defect does it impact the latest release branch if yes is there any issue tagged with release create if needed if the issue is being closed without a pull request has an explanation of why it is being closed been provided ,0
+20510,30333744748.0,IssuesEvent,2023-07-11 08:15:55,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Sleep in subquery not executed correctly,type/bug type/compatibility sig/sql-infra severity/minor compatibility-mysql8,"## Bug Report
+
+When calling `SLEEP()` multiple times in separate subqueries the execution time is not the expected execution time.
+
+### 1. Minimal reproduce step (Required)
+
+```
+SELECT SLEEP(2) UNION ALL SELECT SLEEP(3);
+SELECT SLEEP(2),SLEEP(3);
+```
+
+### 2. What did you expect to see? (Required)
+
+Both statements taking 5s each.
+
+### 3. What did you see instead (Required)
+
+```
+mysql> SELECT SLEEP(2) UNION ALL SELECT SLEEP(3);
++----------+
+| SLEEP(2) |
++----------+
+| 0 |
+| 0 |
++----------+
+2 rows in set (3.00 sec)
+
+mysql> SELECT SLEEP(2),SLEEP(3);
++----------+----------+
+| SLEEP(2) | SLEEP(3) |
++----------+----------+
+| 0 | 0 |
++----------+----------+
+1 row in set (5.00 sec)
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+
+```
+Release Version: v7.3.0-alpha-160-g90dabc0433
+Edition: Community
+Git Commit Hash: 90dabc0433a75db650ac683897d264ef58d63a73
+Git Branch: master
+UTC Build Time: 2023-07-11 07:57:57
+GoVersion: go1.20.5
+Race Enabled: false
+Check Table Before Drop: false
+Store: unistore
+```",True,"Sleep in subquery not executed correctly - ## Bug Report
+
+When calling `SLEEP()` multiple times in separate subqueries the execution time is not the expected execution time.
+
+### 1. Minimal reproduce step (Required)
+
+```
+SELECT SLEEP(2) UNION ALL SELECT SLEEP(3);
+SELECT SLEEP(2),SLEEP(3);
+```
+
+### 2. What did you expect to see? (Required)
+
+Both statements taking 5s each.
+
+### 3. What did you see instead (Required)
+
+```
+mysql> SELECT SLEEP(2) UNION ALL SELECT SLEEP(3);
++----------+
+| SLEEP(2) |
++----------+
+| 0 |
+| 0 |
++----------+
+2 rows in set (3.00 sec)
+
+mysql> SELECT SLEEP(2),SLEEP(3);
++----------+----------+
+| SLEEP(2) | SLEEP(3) |
++----------+----------+
+| 0 | 0 |
++----------+----------+
+1 row in set (5.00 sec)
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+
+```
+Release Version: v7.3.0-alpha-160-g90dabc0433
+Edition: Community
+Git Commit Hash: 90dabc0433a75db650ac683897d264ef58d63a73
+Git Branch: master
+UTC Build Time: 2023-07-11 07:57:57
+GoVersion: go1.20.5
+Race Enabled: false
+Check Table Before Drop: false
+Store: unistore
+```",1,sleep in subquery not executed correctly bug report when calling sleep multiple times in separate subqueries the execution time is not the expected execution time minimal reproduce step required select sleep union all select sleep select sleep sleep what did you expect to see required both statements taking each what did you see instead required mysql select sleep union all select sleep sleep rows in set sec mysql select sleep sleep sleep sleep row in set sec what is your tidb version required release version alpha edition community git commit hash git branch master utc build time goversion race enabled false check table before drop false store unistore ,1
+16433,22197872300.0,IssuesEvent,2022-06-07 08:35:49,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Derived table without alias is not resulting error in TiDB.,type/compatibility sig/execution sig/sql-infra,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+```sql
+drop table if exists t1,t2;
+CREATE TABLE t1 ( a INT );
+INSERT INTO t1 VALUES ( 1 );
+CREATE TABLE t2 ( a INT );
+INSERT INTO t2 VALUES ( 2 );
+
+SELECT * FROM ((((SELECT 1 FROM t1)) UNION SELECT 2 FROM t1));
+```
+
+### 2. What did you expect to see? (Required)
+```sql
+mysql> SELECT * FROM ((((SELECT 1 FROM t1)) UNION SELECT 2 FROM t1));
+ERROR 1248 (42000): Every derived table must have its own alias
+```
+### 3. What did you see instead (Required)
+```sql
+mysql> SELECT * FROM ((((SELECT 1 FROM t1)) UNION SELECT 2 FROM t1));
++------+
+| 1 |
++------+
+| 2 |
+| 1 |
++------+
+2 rows in set (0.00 sec)
+```
+### 4. What is your TiDB version? (Required)
+
+```sql
+mysql> select version();
++-----------------------------------------------+
+| version() |
++-----------------------------------------------+
+| 5.7.25-TiDB-v6.1.0-alpha-482-g81a852077-dirty |
++-----------------------------------------------+
+```
+
+",True,"Derived table without alias is not resulting error in TiDB. - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+```sql
+drop table if exists t1,t2;
+CREATE TABLE t1 ( a INT );
+INSERT INTO t1 VALUES ( 1 );
+CREATE TABLE t2 ( a INT );
+INSERT INTO t2 VALUES ( 2 );
+
+SELECT * FROM ((((SELECT 1 FROM t1)) UNION SELECT 2 FROM t1));
+```
+
+### 2. What did you expect to see? (Required)
+```sql
+mysql> SELECT * FROM ((((SELECT 1 FROM t1)) UNION SELECT 2 FROM t1));
+ERROR 1248 (42000): Every derived table must have its own alias
+```
+### 3. What did you see instead (Required)
+```sql
+mysql> SELECT * FROM ((((SELECT 1 FROM t1)) UNION SELECT 2 FROM t1));
++------+
+| 1 |
++------+
+| 2 |
+| 1 |
++------+
+2 rows in set (0.00 sec)
+```
+### 4. What is your TiDB version? (Required)
+
+```sql
+mysql> select version();
++-----------------------------------------------+
+| version() |
++-----------------------------------------------+
+| 5.7.25-TiDB-v6.1.0-alpha-482-g81a852077-dirty |
++-----------------------------------------------+
+```
+
+",1,derived table without alias is not resulting error in tidb bug report please answer these questions before submitting your issue thanks minimal reproduce step required sql drop table if exists create table a int insert into values create table a int insert into values select from select from union select from what did you expect to see required sql mysql select from select from union select from error every derived table must have its own alias what did you see instead required sql mysql select from select from union select from rows in set sec what is your tidb version required sql mysql select version version tidb alpha dirty ,1
+9296,11306791735.0,IssuesEvent,2020-01-18 16:31:55,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,"Add MySQL datatype aliases serial, dec, fixed",type/compatibility,"`serial` is an alias for BIGINT UNSIGNED NOT NULL AUTO_INCREMENT UNIQUE.
-Please answer these questions before submitting your issue. Thanks!
+`dec` and `fixed` are alias for decimal.
+",True,"Add MySQL datatype aliases serial, dec, fixed - `serial` is an alias for BIGINT UNSIGNED NOT NULL AUTO_INCREMENT UNIQUE.
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-```
-mysql> create table t1 (a int unique,
- -> b int generated always as (-a) virtual,
- -> c int generated always as (-a) stored);
-Query OK, 0 rows affected (0.01 sec)
+`dec` and `fixed` are alias for decimal.
+",1,add mysql datatype aliases serial dec fixed serial is an alias for bigint unsigned not null auto increment unique dec and fixed are alias for decimal ,1
+601481,18410943782.0,IssuesEvent,2021-10-13 05:39:10,dataware-tools/dataware-tools,https://api.github.com/repos/dataware-tools/dataware-tools,closed,Refactoring OpenAPI clients,kind/feature wg/web-app priority/high,"## Purpose
+Feature request
+
+## Description
+APIクライアントを `app-common` にまとめるのではなく、各APIリポジトリ内の GitHub Packages として公開したい
+
+## Repositories
+- [x] api-meta-store
+- [x] api-permission-manager
+- [x] api-job-store
+- [x] api-file-provider
+- [x] api-template-fastapi",1.0,"Refactoring OpenAPI clients - ## Purpose
+Feature request
+
+## Description
+APIクライアントを `app-common` にまとめるのではなく、各APIリポジトリ内の GitHub Packages として公開したい
+
+## Repositories
+- [x] api-meta-store
+- [x] api-permission-manager
+- [x] api-job-store
+- [x] api-file-provider
+- [x] api-template-fastapi",0,refactoring openapi clients purpose feature request description apiクライアントを app common にまとめるのではなく、各apiリポジトリ内の github packages として公開したい repositories api meta store api permission manager api job store api file provider api template fastapi,0
+34643,9424548927.0,IssuesEvent,2019-04-11 14:19:35,libuv/libuv,https://api.github.com/repos/libuv/libuv,closed,build: out-of-tree autotools build fails `make distcheck`,build,"Depends on #2198, otherwise you won't get this far.
+
+Probably related to #2099 somehow so cc @vtjnash.
+```
+$ mkdir -p out/auto && cd out/auto && sh ../../autogen.sh && ../../configure && make distcheck
+# ...
+configure: creating ./config.status
+config.status: creating Makefile
+config.status: creating libuv.pc
+config.status: linking ../../test/fixtures/empty_file to test/fixtures/empty_file
+config.status: error: ../../test/fixtures/empty_file: file not found
+make: *** [distcheck] Error 1
+```
+(Apologies if this has been reported already. I remember discussion but I can't find it back.)",1.0,"build: out-of-tree autotools build fails `make distcheck` - Depends on #2198, otherwise you won't get this far.
+
+Probably related to #2099 somehow so cc @vtjnash.
+```
+$ mkdir -p out/auto && cd out/auto && sh ../../autogen.sh && ../../configure && make distcheck
+# ...
+configure: creating ./config.status
+config.status: creating Makefile
+config.status: creating libuv.pc
+config.status: linking ../../test/fixtures/empty_file to test/fixtures/empty_file
+config.status: error: ../../test/fixtures/empty_file: file not found
+make: *** [distcheck] Error 1
+```
+(Apologies if this has been reported already. I remember discussion but I can't find it back.)",0,build out of tree autotools build fails make distcheck depends on otherwise you won t get this far probably related to somehow so cc vtjnash mkdir p out auto cd out auto sh autogen sh configure make distcheck configure creating config status config status creating makefile config status creating libuv pc config status linking test fixtures empty file to test fixtures empty file config status error test fixtures empty file file not found make error apologies if this has been reported already i remember discussion but i can t find it back ,0
+7306,9555134683.0,IssuesEvent,2019-05-03 01:21:02,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,`desc` is not compatible with MySQL,for new contributors type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```
+➜ tidiff git:(master) ✗ tidiff --mysql.db=tt --tidb.db=tt 'select version()'
+MySQL(127.0.0.1:3306)> select version()
++-----------+
+| version() |
++-----------+
+| 8.0.16 |
++-----------+
+1 row in set (0.001 sec)
+
+TiDB(127.0.0.1:4000)> select version()
++------------------------------------------+
+| version() |
++------------------------------------------+
+| 5.7.25-TiDB-v3.0.0-beta.1-187-g5876abd70 |
++------------------------------------------+
+1 row in set (0.004 sec)
+
+➜ tidiff git:(master) ✗ tidiff --mysql.db=tt --tidb.db=tt 'create table t2 (a timestamp default current_timestamp on update current_timestamp)'
+MySQL(127.0.0.1:3306)> create table t2 (a timestamp default current_timestamp on update current_timestamp)
+Empty set
+0 row in set (0.007 sec)
+
+TiDB(127.0.0.1:4000)> create table t2 (a timestamp default current_timestamp on update current_timestamp)
+Empty set
+0 row in set (0.010 sec)
+
+➜ tidiff git:(master) ✗ tidiff --mysql.db=tt --tidb.db=tt desc t2
+MySQL(127.0.0.1:3306)> desc t2
++----------------------------------------------------------------------------------------------------+
+| Field | Type | Null | Key | Default | Extra |
++----------------------------------------------------------------------------------------------------+
+| a | timestamp | YES | | CURRENT_TIMESTAMP | DEFAULT_GENERATED on update CURRENT_TIMESTAMP |
++----------------------------------------------------------------------------------------------------+
+1 row in set (0.004 sec)
+
+TiDB(127.0.0.1:4000)> desc t2
++----------------------------------------------------------------------------------+
+| Field | Type | Null | Key | Default | Extra |
++----------------------------------------------------------------------------------+
+| a | timestamp | YES | | CURRENT_TIMESTAMP | on update CURRENT_TIMESTAMP |
++----------------------------------------------------------------------------------+
+1 row in set (0.004 sec)
+```
+
+2. What did you expect to see?
+
+The result shoud be same as MySQL
+
+3. What did you see instead?
+
+Showing above.
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```TiDB(127.0.0.1:4000)> select tidb_version()
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta.1-187-g5876abd70
+Git Commit Hash: 5876abd70ccc054704ab0e8cbf02ed129c6efc76
+Git Branch: refine-point-get-failpoint
+UTC Build Time: 2019-04-30 03:35:49
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.003 sec)
+```
+
+",True,"`desc` is not compatible with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```
+➜ tidiff git:(master) ✗ tidiff --mysql.db=tt --tidb.db=tt 'select version()'
+MySQL(127.0.0.1:3306)> select version()
++-----------+
+| version() |
++-----------+
+| 8.0.16 |
++-----------+
+1 row in set (0.001 sec)
+
+TiDB(127.0.0.1:4000)> select version()
++------------------------------------------+
+| version() |
++------------------------------------------+
+| 5.7.25-TiDB-v3.0.0-beta.1-187-g5876abd70 |
++------------------------------------------+
+1 row in set (0.004 sec)
+
+➜ tidiff git:(master) ✗ tidiff --mysql.db=tt --tidb.db=tt 'create table t2 (a timestamp default current_timestamp on update current_timestamp)'
+MySQL(127.0.0.1:3306)> create table t2 (a timestamp default current_timestamp on update current_timestamp)
+Empty set
+0 row in set (0.007 sec)
+
+TiDB(127.0.0.1:4000)> create table t2 (a timestamp default current_timestamp on update current_timestamp)
+Empty set
+0 row in set (0.010 sec)
+
+➜ tidiff git:(master) ✗ tidiff --mysql.db=tt --tidb.db=tt desc t2
+MySQL(127.0.0.1:3306)> desc t2
++----------------------------------------------------------------------------------------------------+
+| Field | Type | Null | Key | Default | Extra |
++----------------------------------------------------------------------------------------------------+
+| a | timestamp | YES | | CURRENT_TIMESTAMP | DEFAULT_GENERATED on update CURRENT_TIMESTAMP |
++----------------------------------------------------------------------------------------------------+
+1 row in set (0.004 sec)
+
+TiDB(127.0.0.1:4000)> desc t2
++----------------------------------------------------------------------------------+
+| Field | Type | Null | Key | Default | Extra |
++----------------------------------------------------------------------------------+
+| a | timestamp | YES | | CURRENT_TIMESTAMP | on update CURRENT_TIMESTAMP |
++----------------------------------------------------------------------------------+
+1 row in set (0.004 sec)
+```
+
+2. What did you expect to see?
+
+The result shoud be same as MySQL
+
+3. What did you see instead?
+
+Showing above.
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```TiDB(127.0.0.1:4000)> select tidb_version()
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta.1-187-g5876abd70
+Git Commit Hash: 5876abd70ccc054704ab0e8cbf02ed129c6efc76
+Git Branch: refine-point-get-failpoint
+UTC Build Time: 2019-04-30 03:35:49
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.003 sec)
+```
+
+",1, desc is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error ➜ tidiff git master ✗ tidiff mysql db tt tidb db tt select version mysql select version version row in set sec tidb select version version tidb beta row in set sec ➜ tidiff git master ✗ tidiff mysql db tt tidb db tt create table a timestamp default current timestamp on update current timestamp mysql create table a timestamp default current timestamp on update current timestamp empty set row in set sec tidb create table a timestamp default current timestamp on update current timestamp empty set row in set sec ➜ tidiff git master ✗ tidiff mysql db tt tidb db tt desc mysql desc field type null key default extra a timestamp yes current timestamp default generated on update current timestamp row in set sec tidb desc field type null key default extra a timestamp yes current timestamp on update current timestamp row in set sec what did you expect to see the result shoud be same as mysql what did you see instead showing above what version of tidb are you using tidb server v or run select tidb version on tidb tidb select tidb version tidb version release version beta git commit hash git branch refine point get failpoint utc build time goversion go version darwin race enabled false tikv min version alpha check table before drop false row in set sec ,1
+5707,8176003887.0,IssuesEvent,2018-08-28 05:36:37,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,insert timestamp failure with 0000-00-00 00:00:00.000000 in prepare statement,type/bug type/compatibility,"1. What did you do?
+
+```
+ CREATE TABLE timestamp_insert ( id INT NOT NULL PRIMARY KEY, tstamp TIMESTAMP NOT NULL )
+```
+then prepare and exec a insert 0000-00-00 00:00:00.000000 into `tstamp`
+
+```
+ stmt= const_cast(""INSERT INTO timestamp_insert ( id, tstamp ) VALUES ( ?, ? )"");
+ if(mysql_stmt_prepare(mysql_stmt, stmt, strlen(stmt)))
+ {
+ my_chk_stmt(&mysql, mysql_stmt, __LINE__);
+ }
+
+ memset(mysql_bind_param, 0, sizeof(mysql_bind_param));
+ mysql_bind_param[0].buffer_type= MYSQL_TYPE_LONG;
+ mysql_bind_param[0].buffer= (char*)&id;
+ mysql_bind_param[0].is_null= 0;
+ mysql_bind_param[0].length= 0;
+ mysql_bind_param[1].buffer_type= MYSQL_TYPE_TIMESTAMP;
+ mysql_bind_param[1].buffer= &tstamp;
+ mysql_bind_param[1].is_null= 0;
+ mysql_bind_param[1].length= 0;
+ if(mysql_stmt_bind_param(mysql_stmt, mysql_bind_param))
+ {
+ my_chk_stmt(&mysql, mysql_stmt, __LINE__);
+ }
+
+ id= 2;
+ tstamp.year= 0;
+ tstamp.month= 0;
+ tstamp.day= 0;
+ tstamp.hour= 0;
+ tstamp.minute= 0;
+ tstamp.second= 0;
+ tstamp.second_part= 0;
+
+ if(mysql_stmt_execute(mysql_stmt))
+ {
+ my_chk_stmt(&mysql, mysql_stmt, __LINE__);
+ }
+```
+
+
+2. What did you expect to see?
+
+```
+success
+```
+
+3. What did you see instead?
+
+```
+1292 : invalid time format: '0'
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+2.1.0.rc1
+```
+",True,"insert timestamp failure with 0000-00-00 00:00:00.000000 in prepare statement - 1. What did you do?
+
+```
+ CREATE TABLE timestamp_insert ( id INT NOT NULL PRIMARY KEY, tstamp TIMESTAMP NOT NULL )
+```
+then prepare and exec a insert 0000-00-00 00:00:00.000000 into `tstamp`
+
+```
+ stmt= const_cast(""INSERT INTO timestamp_insert ( id, tstamp ) VALUES ( ?, ? )"");
+ if(mysql_stmt_prepare(mysql_stmt, stmt, strlen(stmt)))
+ {
+ my_chk_stmt(&mysql, mysql_stmt, __LINE__);
+ }
+
+ memset(mysql_bind_param, 0, sizeof(mysql_bind_param));
+ mysql_bind_param[0].buffer_type= MYSQL_TYPE_LONG;
+ mysql_bind_param[0].buffer= (char*)&id;
+ mysql_bind_param[0].is_null= 0;
+ mysql_bind_param[0].length= 0;
+ mysql_bind_param[1].buffer_type= MYSQL_TYPE_TIMESTAMP;
+ mysql_bind_param[1].buffer= &tstamp;
+ mysql_bind_param[1].is_null= 0;
+ mysql_bind_param[1].length= 0;
+ if(mysql_stmt_bind_param(mysql_stmt, mysql_bind_param))
+ {
+ my_chk_stmt(&mysql, mysql_stmt, __LINE__);
+ }
+
+ id= 2;
+ tstamp.year= 0;
+ tstamp.month= 0;
+ tstamp.day= 0;
+ tstamp.hour= 0;
+ tstamp.minute= 0;
+ tstamp.second= 0;
+ tstamp.second_part= 0;
+
+ if(mysql_stmt_execute(mysql_stmt))
+ {
+ my_chk_stmt(&mysql, mysql_stmt, __LINE__);
+ }
+```
+
+
+2. What did you expect to see?
+
+```
+success
+```
+
+3. What did you see instead?
+
+```
+1292 : invalid time format: '0'
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+2.1.0.rc1
+```
+",1,insert timestamp failure with in prepare statement what did you do create table timestamp insert id int not null primary key tstamp timestamp not null then prepare and exec a insert into tstamp stmt const cast insert into timestamp insert id tstamp values if mysql stmt prepare mysql stmt stmt strlen stmt my chk stmt mysql mysql stmt line memset mysql bind param sizeof mysql bind param mysql bind param buffer type mysql type long mysql bind param buffer char id mysql bind param is null mysql bind param length mysql bind param buffer type mysql type timestamp mysql bind param buffer tstamp mysql bind param is null mysql bind param length if mysql stmt bind param mysql stmt mysql bind param my chk stmt mysql mysql stmt line id tstamp year tstamp month tstamp day tstamp hour tstamp minute tstamp second tstamp second part if mysql stmt execute mysql stmt my chk stmt mysql mysql stmt line what did you expect to see success what did you see instead invalid time format what version of tidb are you using tidb server v or run select tidb version on tidb ,1
+56287,6972766777.0,IssuesEvent,2017-12-11 18:07:04,ludumdare/ludumdare,https://api.github.com/repos/ludumdare/ludumdare,closed,CORE: Notifications and Subscriptions,core design MIKE,"Some related issues:
+- the `@host` shorthand: https://github.com/ludumdare/ludumdare/issues/8
+- on orphaned accounts, and their implications: https://github.com/ludumdare/ludumdare/issues/3
+- popup a dialog when you publish telling you who's getting notified https://github.com/ludumdare/ludumdare/issues/193
+",1.0,"CORE: Notifications and Subscriptions - Some related issues:
+- the `@host` shorthand: https://github.com/ludumdare/ludumdare/issues/8
+- on orphaned accounts, and their implications: https://github.com/ludumdare/ludumdare/issues/3
+- popup a dialog when you publish telling you who's getting notified https://github.com/ludumdare/ludumdare/issues/193
+",0,core notifications and subscriptions some related issues the host shorthand on orphaned accounts and their implications popup a dialog when you publish telling you who s getting notified ,0
+2912,2645208691.0,IssuesEvent,2015-03-12 21:17:21,NAVADMC/ADSM,https://api.github.com/repos/NAVADMC/ADSM,closed,CSV with Wrong Format,User Testing,"I attempted to load the csv files from the Herdid folder. It had these fields:
+![Uploading Headers.png . . .]()
+
+And an error message popped up: Unrecognized csv header format. Please use: size, longitude, status, latitude, production-type
+",1.0,"CSV with Wrong Format - I attempted to load the csv files from the Herdid folder. It had these fields:
+![Uploading Headers.png . . .]()
+
+And an error message popped up: Unrecognized csv header format. Please use: size, longitude, status, latitude, production-type
+",0,csv with wrong format i attempted to load the csv files from the herdid folder it had these fields and an error message popped up unrecognized csv header format please use size longitude status latitude production type ,0
+177276,6576296424.0,IssuesEvent,2017-09-11 19:16:26,HHS81/c182s,https://api.github.com/repos/HHS81/c182s,opened,Heading Indicator should be vacuum driven,bug middle priority,"The heading Indicator should be vacuum driven. But the Flightgear model simualtes an electric driven heading indicator.
+
+Where can it be changed?",1.0,"Heading Indicator should be vacuum driven - The heading Indicator should be vacuum driven. But the Flightgear model simualtes an electric driven heading indicator.
+
+Where can it be changed?",0,heading indicator should be vacuum driven the heading indicator should be vacuum driven but the flightgear model simualtes an electric driven heading indicator where can it be changed ,0
+5795,8244393157.0,IssuesEvent,2018-09-11 06:03:36,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,syntax .tbl_name is not supported,type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+MySQL [mysql]> use mysql;
+Database changed
+MySQL [mysql]> select * from .db;
+ERROR 1105 (HY000): line 0 column 15 near ""db"" (total length 17)
+```
+
+refer: https://dev.mysql.com/doc/refman/5.7/en/identifier-qualifiers.html
+",True,"syntax .tbl_name is not supported - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+MySQL [mysql]> use mysql;
+Database changed
+MySQL [mysql]> select * from .db;
+ERROR 1105 (HY000): line 0 column 15 near ""db"" (total length 17)
+```
+
+refer: https://dev.mysql.com/doc/refman/5.7/en/identifier-qualifiers.html
+",1,syntax tbl name is not supported please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql mysql use mysql database changed mysql select from db error line column near db total length refer ,1
+7090,9375182626.0,IssuesEvent,2019-04-04 02:49:02,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Table name and column name can not be scientific notation,type/bug type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+create table 1ea10 (1a20 int,1e int);
+```
+
+2. What did you expect to see?
+
+Query OK, 0 rows affected (0.02 sec)
+
+3. What did you see instead?
+
+ERROR 1105 (HY000): line 0 column 15 near ""a10 (1a20 int,1e int)""float literal: strconv.ParseFloat: parsing ""1e"": invalid syntax (total length 36)
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"Table name and column name can not be scientific notation - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+create table 1ea10 (1a20 int,1e int);
+```
+
+2. What did you expect to see?
+
+Query OK, 0 rows affected (0.02 sec)
+
+3. What did you see instead?
+
+ERROR 1105 (HY000): line 0 column 15 near ""a10 (1a20 int,1e int)""float literal: strconv.ParseFloat: parsing ""1e"": invalid syntax (total length 36)
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,table name and column name can not be scientific notation please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql create table int int what did you expect to see query ok rows affected sec what did you see instead error line column near int int float literal strconv parsefloat parsing invalid syntax total length what version of tidb are you using tidb server v ,1
+55372,6473317536.0,IssuesEvent,2017-08-17 15:38:48,javaee/glassfish,https://api.github.com/repos/javaee/glassfish,closed,Add dev-tests to validate behavior around caller principal as defined in JSR 375 specification,5-0-approved 5-0-review Component: test Priority: Major Type: Task,"## Environment Details
+* GlassFish Version : 5.0
+----------
+## Description
+JSR 375 defines expected behaviour around caller principal. This issue is to track inclusion of corresponding dev-tests in Glassfish.",1.0,"Add dev-tests to validate behavior around caller principal as defined in JSR 375 specification - ## Environment Details
+* GlassFish Version : 5.0
+----------
+## Description
+JSR 375 defines expected behaviour around caller principal. This issue is to track inclusion of corresponding dev-tests in Glassfish.",0,add dev tests to validate behavior around caller principal as defined in jsr specification environment details glassfish version description jsr defines expected behaviour around caller principal this issue is to track inclusion of corresponding dev tests in glassfish ,0
+132962,18278504758.0,IssuesEvent,2021-10-04 22:11:16,ghc-dev/Michael-Hicks,https://api.github.com/repos/ghc-dev/Michael-Hicks,opened,CVE-2021-23382 (Medium) detected in postcss-4.1.16.tgz,security vulnerability,"## CVE-2021-23382 - Medium Severity Vulnerability
+ Vulnerable Library - postcss-4.1.16.tgz
-mysql> insert into t1 values (1,default,default);
-Query OK, 1 row affected (0.01 sec)
+
+
+The package postcss before 8.2.13 are vulnerable to Regular Expression Denial of Service (ReDoS) via getAnnotationURL() and loadAnnotation() in lib/previous-map.js. The vulnerable regexes are caused mainly by the sub-pattern \/\*\s* sourceMappingURL=(.*).
-```
-2. What did you expect to see?
+
-```
-Query OK, 1 row affected (0.01 sec)
-```
+
+
+
+",True,"CVE-2021-23382 (Medium) detected in postcss-4.1.16.tgz - ## CVE-2021-23382 - Medium Severity Vulnerability
+ Vulnerable Library - postcss-4.1.16.tgz
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-```
-Release Version: v4.0.0-alpha-693-gada724a2a
-```
-",1,support use on duplicate key update b default in generated columns bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error mysql create table a int unique b int generated always as a virtual c int generated always as a stored query ok rows affected sec mysql insert into values default default query ok row affected sec mysql insert into values default default on duplicate key update a b default what did you expect to see error the value specified for generated column b in table is not allowed what did you see instead query ok row affected sec what version of tidb are you using tidb server v or run select tidb version on tidb release version alpha ,1
-18564,25821598639.0,IssuesEvent,2022-12-12 09:58:53,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,force index behaviour not same as mysql,type/compatibility good first issue sig/planner compatibility-mysql8,"## Bug Report
+
+
+The package postcss before 8.2.13 are vulnerable to Regular Expression Denial of Service (ReDoS) via getAnnotationURL() and loadAnnotation() in lib/previous-map.js. The vulnerable regexes are caused mainly by the sub-pattern \/\*\s* sourceMappingURL=(.*).
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-```
-# ----- step 1: create table
-CREATE TABLE `projects_send` (
- `entry` bigint(20) unsigned NOT NULL AUTO_INCREMENT COMMENT 'id',
- `projectid` int(8) NOT NULL COMMENT 'ID',
- `status` tinyint(1) unsigned NOT NULL DEFAULT '0' COMMENT '状态(0:not send;1:sent;2:back)',
- `sendtime` datetime NOT NULL COMMENT 'senttime',
- PRIMARY KEY (`entry`) USING BTREE,
- KEY `idx_sendtime_status_projectid` (`sendtime`,`status`,`projectid`) USING BTREE,
- KEY `idx_sendtime_status` (`sendtime`,`status`) USING BTREE
-) ENGINE=InnoDB AUTO_INCREMENT=1 DEFAULT CHARSET=utf8;
-
-# ----- step 2: EXPLAIN on tidb & mysql
-
-#1. tidb & mysql same
-mysql>
-EXPLAIN select * from projects_send force index(idx_sendtime) where sendtime > ""2020-01-01"";
-Key 'idx_sendtime' doesnt exist in table 'projects_send'
-
-#2. tidb & mysql same
-mysql>
-EXPLAIN select * from projects_send force index(idx_sendtime_status) where sendtime > ""2020-01-01"";
-+----+-------------+---------------+-------+---------------------+---------------------+---------+------+------+--------------------------+
-| id | select_type | table | type | possible_keys | key | key_len | ref | rows | Extra |
-+----+-------------+---------------+-------+---------------------+---------------------+---------+------+------+--------------------------+
-| 1 | SIMPLE | projects_send | index | idx_sendtime_status | idx_sendtime_status | 10 | NULL | 1 | Using where; Using index |
-+----+-------------+---------------+-------+---------------------+---------------------+---------+------+------+--------------------------+
-
-#3. tidb & mysql not same: tidb show index not exist
-mysql>
-EXPLAIN select * from projects_send force index(idx_sendtime_status_pro) where sendtime > ""2020-01-01"";
-+----+-------------+---------------+-------+-------------------------------+-------------------------------+---------+------+------+--------------------------+
-| id | select_type | table | type | possible_keys | key | key_len | ref | rows | Extra |
-+----+-------------+---------------+-------+-------------------------------+-------------------------------+---------+------+------+--------------------------+
-| 1 | SIMPLE | projects_send | index | idx_sendtime_status_projectid | idx_sendtime_status_projectid | 10 | NULL | 1 | Using where; Using index |
-+----+-------------+---------------+-------+-------------------------------+-------------------------------+---------+------+------+--------------------------+
-1 row in set (0.14 sec)
-
-#on mysql the only one same prefix index idx_sendtime_status_pro can be used, but on tidb only the same name index can be use
-```
-2. What did you expect to see?
+
Path to dependency file: /src/project/data-science/requirements.txt
+
Path to vulnerable library: /src/project/data-science/requirements.txt
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-Release Version: v3.0.8
-Git Commit Hash: 8f13cf1449bd8903ff465a4f12ed89ecbac858a4
-Git Branch: HEAD
-UTC Build Time: 2019-12-31 11:14:59
-GoVersion: go version go1.13 linux/amd64
-Race Enabled: false
-TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
-Check Table Before Drop: false
-",True,"force index behaviour not same as mysql - ## Bug Report
+Dependency Hierarchy:
+ - jupyter-1.0.0-py2.py3-none-any.whl (Root Library)
+ - jupyter_console-6.6.3-py3-none-any.whl
+ - :x: **ipython-7.34.0-py3-none-any.whl** (Vulnerable Library)
+
+
+IPython (Interactive Python) is a command shell for interactive computing in multiple programming languages, originally developed for the Python programming language. Versions prior to 8.1.0 are subject to a command injection vulnerability with very specific prerequisites. This vulnerability requires that the function `IPython.utils.terminal.set_term_title` be called on Windows in a Python environment where ctypes is not available. The dependency on `ctypes` in `IPython.utils._process_win32` prevents the vulnerable code from ever being reached in the ipython binary. However, as a library that could be used by another tool `set_term_title` could be called and hence introduce a vulnerability. Should an attacker get untrusted input to an instance of this function they would be able to inject shell commands as current process and limited to the scope of the current process. Users of ipython as a library are advised to upgrade. Users unable to upgrade should ensure that any calls to the `IPython.utils.terminal.set_term_title` function are done with trusted or filtered input.
-Please answer these questions before submitting your issue. Thanks!
+
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-```
-# ----- step 1: create table
-CREATE TABLE `projects_send` (
- `entry` bigint(20) unsigned NOT NULL AUTO_INCREMENT COMMENT 'id',
- `projectid` int(8) NOT NULL COMMENT 'ID',
- `status` tinyint(1) unsigned NOT NULL DEFAULT '0' COMMENT '状态(0:not send;1:sent;2:back)',
- `sendtime` datetime NOT NULL COMMENT 'senttime',
- PRIMARY KEY (`entry`) USING BTREE,
- KEY `idx_sendtime_status_projectid` (`sendtime`,`status`,`projectid`) USING BTREE,
- KEY `idx_sendtime_status` (`sendtime`,`status`) USING BTREE
-) ENGINE=InnoDB AUTO_INCREMENT=1 DEFAULT CHARSET=utf8;
-
-# ----- step 2: EXPLAIN on tidb & mysql
-
-#1. tidb & mysql same
-mysql>
-EXPLAIN select * from projects_send force index(idx_sendtime) where sendtime > ""2020-01-01"";
-Key 'idx_sendtime' doesnt exist in table 'projects_send'
-
-#2. tidb & mysql same
-mysql>
-EXPLAIN select * from projects_send force index(idx_sendtime_status) where sendtime > ""2020-01-01"";
-+----+-------------+---------------+-------+---------------------+---------------------+---------+------+------+--------------------------+
-| id | select_type | table | type | possible_keys | key | key_len | ref | rows | Extra |
-+----+-------------+---------------+-------+---------------------+---------------------+---------+------+------+--------------------------+
-| 1 | SIMPLE | projects_send | index | idx_sendtime_status | idx_sendtime_status | 10 | NULL | 1 | Using where; Using index |
-+----+-------------+---------------+-------+---------------------+---------------------+---------+------+------+--------------------------+
-
-#3. tidb & mysql not same: tidb show index not exist
-mysql>
-EXPLAIN select * from projects_send force index(idx_sendtime_status_pro) where sendtime > ""2020-01-01"";
-+----+-------------+---------------+-------+-------------------------------+-------------------------------+---------+------+------+--------------------------+
-| id | select_type | table | type | possible_keys | key | key_len | ref | rows | Extra |
-+----+-------------+---------------+-------+-------------------------------+-------------------------------+---------+------+------+--------------------------+
-| 1 | SIMPLE | projects_send | index | idx_sendtime_status_projectid | idx_sendtime_status_projectid | 10 | NULL | 1 | Using where; Using index |
-+----+-------------+---------------+-------+-------------------------------+-------------------------------+---------+------+------+--------------------------+
-1 row in set (0.14 sec)
-
-#on mysql the only one same prefix index idx_sendtime_status_pro can be used, but on tidb only the same name index can be use
-```
-2. What did you expect to see?
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Local
+ - Attack Complexity: High
+ - Privileges Required: None
+ - User Interaction: Required
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: High
+ - Integrity Impact: High
+ - Availability Impact: High
+
+For more information on CVSS3 Scores, click here.
+
+
+
+ Suggested Fix
+
+
+
+
-3. What did you see instead?
+***
+Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",True,"CVE-2023-24816 (High) detected in ipython-7.34.0-py3-none-any.whl - ## CVE-2023-24816 - High Severity Vulnerability
+ Vulnerable Library - ipython-7.34.0-py3-none-any.whl
+
+
+IPython (Interactive Python) is a command shell for interactive computing in multiple programming languages, originally developed for the Python programming language. Versions prior to 8.1.0 are subject to a command injection vulnerability with very specific prerequisites. This vulnerability requires that the function `IPython.utils.terminal.set_term_title` be called on Windows in a Python environment where ctypes is not available. The dependency on `ctypes` in `IPython.utils._process_win32` prevents the vulnerable code from ever being reached in the ipython binary. However, as a library that could be used by another tool `set_term_title` could be called and hence introduce a vulnerability. Should an attacker get untrusted input to an instance of this function they would be able to inject shell commands as current process and limited to the scope of the current process. Users of ipython as a library are advised to upgrade. Users unable to upgrade should ensure that any calls to the `IPython.utils.terminal.set_term_title` function are done with trusted or filtered input.
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-Release Version: v3.0.8
-Git Commit Hash: 8f13cf1449bd8903ff465a4f12ed89ecbac858a4
-Git Branch: HEAD
-UTC Build Time: 2019-12-31 11:14:59
-GoVersion: go version go1.13 linux/amd64
-Race Enabled: false
-TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
-Check Table Before Drop: false
-",1,force index behaviour not same as mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error step create table create table projects send entry bigint unsigned not null auto increment comment id projectid int not null comment id status tinyint unsigned not null default comment 状态 not send sent back sendtime datetime not null comment senttime primary key entry using btree key idx sendtime status projectid sendtime status projectid using btree key idx sendtime status sendtime status using btree engine innodb auto increment default charset step explain on tidb mysql tidb mysql same mysql explain select from projects send force index idx sendtime where sendtime key idx sendtime doesnt exist in table projects send tidb mysql same mysql explain select from projects send force index idx sendtime status where sendtime id select type table type possible keys key key len ref rows extra simple projects send index idx sendtime status idx sendtime status null using where using index tidb mysql not same tidb show index not exist mysql explain select from projects send force index idx sendtime status pro where sendtime id select type table type possible keys key key len ref rows extra simple projects send index idx sendtime status projectid idx sendtime status projectid null using where using index row in set sec on mysql the only one same prefix index idx sendtime status pro can be used but on tidb only the same name index can be use what did you expect to see what did you see instead what version of tidb are you using tidb server v or run select tidb version on tidb release version git commit hash git branch head utc build time goversion go version linux race enabled false tikv min version check table before drop false ,1
-11624,13671944268.0,IssuesEvent,2020-09-29 07:48:08,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,_utf8 not supported,component/parser type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Local
+ - Attack Complexity: High
+ - Privileges Required: None
+ - User Interaction: Required
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: High
+ - Integrity Impact: High
+ - Availability Impact: High
+
+For more information on CVSS3 Scores, click here.
+
+
+
+ Suggested Fix
+
-2. What did you expect to see?
+
+
+
-```
-mysql> select left(_utf8 0xD0B0D0B1D0B2,1);
-+------------------------------+
-| left(_utf8 0xD0B0D0B1D0B2,1) |
-+------------------------------+
-| а |
-+------------------------------+
-1 row in set (0.01 sec)
-```
+***
+Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",0,cve high detected in ipython none any whl cve high severity vulnerability vulnerable library ipython none any whl ipython productive interactive computing library home page a href path to dependency file src project data science requirements txt path to vulnerable library src project data science requirements txt dependency hierarchy jupyter none any whl root library jupyter console none any whl x ipython none any whl vulnerable library found in head commit a href found in base branch main vulnerability details ipython interactive python is a command shell for interactive computing in multiple programming languages originally developed for the python programming language versions prior to are subject to a command injection vulnerability with very specific prerequisites this vulnerability requires that the function ipython utils terminal set term title be called on windows in a python environment where ctypes is not available the dependency on ctypes in ipython utils process prevents the vulnerable code from ever being reached in the ipython binary however as a library that could be used by another tool set term title could be called and hence introduce a vulnerability should an attacker get untrusted input to an instance of this function they would be able to inject shell commands as current process and limited to the scope of the current process users of ipython as a library are advised to upgrade users unable to upgrade should ensure that any calls to the ipython utils terminal set term title function are done with trusted or filtered input publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity high privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution ipython step up your open source security game with mend ,0
+184790,14289965887.0,IssuesEvent,2020-11-23 20:06:49,github-vet/rangeclosure-findings,https://api.github.com/repos/github-vet/rangeclosure-findings,closed,antoniorea/rickfast-docker: integration-cli/docker_cli_help_test.go; 98 LoC,fresh medium test,"
+Found a possible issue in [antoniorea/rickfast-docker](https://www.github.com/antoniorea/rickfast-docker) at [integration-cli/docker_cli_help_test.go](https://github.com/antoniorea/rickfast-docker/blob/75c36bcc64a5597919a16a7d43463f7e7c5e1499/integration-cli/docker_cli_help_test.go#L45-L142)
-3. What did you see instead?
+The below snippet of Go code triggered static analysis which searches for goroutines and/or defer statements
+which capture loop variables.
-```
-mysql> select left(_utf8 0xD0B0D0B1D0B2,1);
-ERROR 1105 (HY000): line 0 column 32 near "",1)"" (total length 35)
-```
+[Click here to see the code in its original context.](https://github.com/antoniorea/rickfast-docker/blob/75c36bcc64a5597919a16a7d43463f7e7c5e1499/integration-cli/docker_cli_help_test.go#L45-L142)
-4. What version of TiDB are you using (`tidb-server -V`)?
+
+Click here to show the 98 line(s) of Go which triggered the analyzer.
-",True,"_utf8 not supported - Please answer these questions before submitting your issue. Thanks!
+```go
+ for _, home := range homes {
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+ // Dup baseEnvs and add our new HOME value
+ newEnvs := make([]string, len(baseEnvs)+1)
+ copy(newEnvs, baseEnvs)
+ newEnvs[len(newEnvs)-1] = homeKey + ""="" + home
-```sql
-select left(_utf8 0xD0B0D0B1D0B2,1)
-```
+ scanForHome := runtime.GOOS != ""windows"" && home != ""/""
-2. What did you expect to see?
+ // Check main help text to make sure its not over 80 chars
+ helpCmd := exec.Command(dockerBinary, ""help"")
+ helpCmd.Env = newEnvs
+ out, _, err := runCommandWithOutput(helpCmd)
+ c.Assert(err, checker.IsNil, check.Commentf(out))
+ lines := strings.Split(out, ""\n"")
+ for _, line := range lines {
+ // All lines should not end with a space
+ c.Assert(line, checker.Not(checker.HasSuffix), "" "", check.Commentf(""Line should not end with a space""))
-```
-mysql> select left(_utf8 0xD0B0D0B1D0B2,1);
-+------------------------------+
-| left(_utf8 0xD0B0D0B1D0B2,1) |
-+------------------------------+
-| а |
-+------------------------------+
-1 row in set (0.01 sec)
-```
+ if scanForHome && strings.Contains(line, `=`+home) {
+ c.Fatalf(""Line should use '%q' instead of %q:\n%s"", homedir.GetShortcutString(), home, line)
+ }
+ if runtime.GOOS != ""windows"" {
+ i := strings.Index(line, homedir.GetShortcutString())
+ if i >= 0 && i != len(line)-1 && line[i+1] != '/' {
+ c.Fatalf(""Main help should not have used home shortcut:\n%s"", line)
+ }
+ }
+ }
-3. What did you see instead?
+ // Make sure each cmd's help text fits within 90 chars and that
+ // on non-windows system we use ~ when possible (to shorten things).
+ // Pull the list of commands from the ""Commands:"" section of docker help
+ helpCmd = exec.Command(dockerBinary, ""help"")
+ helpCmd.Env = newEnvs
+ out, _, err = runCommandWithOutput(helpCmd)
+ c.Assert(err, checker.IsNil, check.Commentf(out))
+ i := strings.Index(out, ""Commands:"")
+ c.Assert(i, checker.GreaterOrEqualThan, 0, check.Commentf(""Missing 'Commands:' in:\n%s"", out))
-```
-mysql> select left(_utf8 0xD0B0D0B1D0B2,1);
-ERROR 1105 (HY000): line 0 column 32 near "",1)"" (total length 35)
-```
+ cmds := []string{}
+ // Grab all chars starting at ""Commands:""
+ helpOut := strings.Split(out[i:], ""\n"")
+ // First line is just ""Commands:""
+ if isLocalDaemon {
+ // Replace first line with ""daemon"" command since it's not part of the list of commands.
+ helpOut[0] = "" daemon""
+ } else {
+ // Skip first line
+ helpOut = helpOut[1:]
+ }
-4. What version of TiDB are you using (`tidb-server -V`)?
+ // Create the list of commands we want to test
+ cmdsToTest := []string{}
+ for _, cmd := range helpOut {
+ // Stop on blank line or non-idented line
+ if cmd == """" || !unicode.IsSpace(rune(cmd[0])) {
+ break
+ }
-",1, not supported please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql select left what did you expect to see mysql select left left а row in set sec what did you see instead mysql select left error line column near total length what version of tidb are you using tidb server v ,1
-13155,15496099739.0,IssuesEvent,2021-03-11 02:03:37,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,reopened,Test compatibility using DataGrip,status/help-wanted type/compatibility,"DataGrip is a Database management systems that support many databases, including MySQL. See https://www.jetbrains.com/datagrip/
-",True,"Test compatibility using DataGrip - DataGrip is a Database management systems that support many databases, including MySQL. See https://www.jetbrains.com/datagrip/
-",1,test compatibility using datagrip datagrip is a database management systems that support many databases including mysql see ,1
-5495,7937199932.0,IssuesEvent,2018-07-09 12:06:28,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,"Intellij IDEA database plugin return an error ""Unknown column 'generation_expression' in 'field list'""",help wanted type/compatibility,"Error encountered when performing Introspect schema xlqy: Unknown column 'generation_expression' in 'field list'.
-Unknown column 'generation_expression' in 'field list'",True,"Intellij IDEA database plugin return an error ""Unknown column 'generation_expression' in 'field list'"" - Error encountered when performing Introspect schema xlqy: Unknown column 'generation_expression' in 'field list'.
-Unknown column 'generation_expression' in 'field list'",1,intellij idea database plugin return an error unknown column generation expression in field list error encountered when performing introspect schema xlqy unknown column generation expression in field list unknown column generation expression in field list ,1
-12085,14247181455.0,IssuesEvent,2020-11-19 11:04:55,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Comparison result is incorrect between year column and int constant,challenge-program component/executor picked severity/critical sig/execution type/bug type/compatibility,"## Bug Report
+ // Grab just the first word of each line
+ cmd = strings.Split(strings.TrimSpace(cmd), "" "")[0]
+ cmds = append(cmds, cmd) // Saving count for later
-Please answer these questions before submitting your issue. Thanks!
+ cmdsToTest = append(cmdsToTest, cmd)
+ }
-### 1. Minimal reproduce step (Required)
+ // Add some 'two word' commands - would be nice to automatically
+ // calculate this list - somehow
+ cmdsToTest = append(cmdsToTest, ""volume create"")
+ cmdsToTest = append(cmdsToTest, ""volume inspect"")
+ cmdsToTest = append(cmdsToTest, ""volume ls"")
+ cmdsToTest = append(cmdsToTest, ""volume rm"")
+ cmdsToTest = append(cmdsToTest, ""network connect"")
+ cmdsToTest = append(cmdsToTest, ""network create"")
+ cmdsToTest = append(cmdsToTest, ""network disconnect"")
+ cmdsToTest = append(cmdsToTest, ""network inspect"")
+ cmdsToTest = append(cmdsToTest, ""network ls"")
+ cmdsToTest = append(cmdsToTest, ""network rm"")
-
+ // Divide the list of commands into go routines and run the func testcommand on the commands in parallel
+ // to save runtime of test
-``` mysql
-create table t2 (a year(4));
-insert into t2 values(69);
-select * from t2 where a <= 69;
-```
+ errChan := make(chan error)
-### 2. What did you expect to see? (Required)
+ for index := 0; index < len(cmdsToTest); index++ {
+ go func(index int) {
+ errChan <- testCommand(cmdsToTest[index], newEnvs, scanForHome, home)
+ }(index)
+ }
-In mysql 8.0
+ for index := 0; index < len(cmdsToTest); index++ {
+ err := <-errChan
+ if err != nil {
+ c.Fatal(err)
+ }
+ }
+ }
-``` mysql
-mysql> select * from t2 where a <= 69;
-+------+
-| a |
-+------+
-| 2069 |
-+------+
-1 row in set (0.00 sec)
```
+
-### 3. What did you see instead (Required)
-
-``` mysql
-mysql> select * from t2 where a <= 69;
-Empty set (0.00 sec)
-
-mysql> explain select * from t2 where a <= 69;
-+-------------------------+---------+-----------+---------------+--------------------------------+
-| id | estRows | task | access object | operator info |
-+-------------------------+---------+-----------+---------------+--------------------------------+
-| TableReader_7 | 1.00 | root | | data:Selection_6 |
-| └─Selection_6 | 1.00 | cop[tikv] | | le(test.t2.a, 69) |
-| └─TableFullScan_5 | 3.00 | cop[tikv] | table:t2 | keep order:false, stats:pseudo |
-+-------------------------+---------+-----------+---------------+--------------------------------+
-3 rows in set (0.00 sec)
-```
+Leave a reaction on this issue to contribute to the project by classifying this instance as a **Bug** :-1:, **Mitigated** :+1:, or **Desirable Behavior** :rocket:
+See the descriptions of the classifications [here](https://github.com/github-vet/rangeclosure-findings#how-can-i-help) for more information.
-`69` should be adjusted to `2069`.
-
-### 4. What is your TiDB version? (Required)
-
-
-
-``` mysql
-mysql> select tidb_version();
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: None
-Edition: Community
-Git Commit Hash: None
-Git Branch: None
-UTC Build Time: None
-GoVersion: go1.15
-Race Enabled: false
-TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
-Check Table Before Drop: false |
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-1 row in set (0.00 sec)
-```
+commit ID: 75c36bcc64a5597919a16a7d43463f7e7c5e1499
+",1.0,"antoniorea/rickfast-docker: integration-cli/docker_cli_help_test.go; 98 LoC -
+Found a possible issue in [antoniorea/rickfast-docker](https://www.github.com/antoniorea/rickfast-docker) at [integration-cli/docker_cli_help_test.go](https://github.com/antoniorea/rickfast-docker/blob/75c36bcc64a5597919a16a7d43463f7e7c5e1499/integration-cli/docker_cli_help_test.go#L45-L142)
-## Score
+The below snippet of Go code triggered static analysis which searches for goroutines and/or defer statements
+which capture loop variables.
-- 600
+[Click here to see the code in its original context.](https://github.com/antoniorea/rickfast-docker/blob/75c36bcc64a5597919a16a7d43463f7e7c5e1499/integration-cli/docker_cli_help_test.go#L45-L142)
-## Mentor
+
+Click here to show the 98 line(s) of Go which triggered the analyzer.
-* @lzmhhh123 ",True,"Comparison result is incorrect between year column and int constant - ## Bug Report
+```go
+ for _, home := range homes {
-Please answer these questions before submitting your issue. Thanks!
+ // Dup baseEnvs and add our new HOME value
+ newEnvs := make([]string, len(baseEnvs)+1)
+ copy(newEnvs, baseEnvs)
+ newEnvs[len(newEnvs)-1] = homeKey + ""="" + home
-### 1. Minimal reproduce step (Required)
+ scanForHome := runtime.GOOS != ""windows"" && home != ""/""
-
+ // Check main help text to make sure its not over 80 chars
+ helpCmd := exec.Command(dockerBinary, ""help"")
+ helpCmd.Env = newEnvs
+ out, _, err := runCommandWithOutput(helpCmd)
+ c.Assert(err, checker.IsNil, check.Commentf(out))
+ lines := strings.Split(out, ""\n"")
+ for _, line := range lines {
+ // All lines should not end with a space
+ c.Assert(line, checker.Not(checker.HasSuffix), "" "", check.Commentf(""Line should not end with a space""))
-``` mysql
-create table t2 (a year(4));
-insert into t2 values(69);
-select * from t2 where a <= 69;
-```
+ if scanForHome && strings.Contains(line, `=`+home) {
+ c.Fatalf(""Line should use '%q' instead of %q:\n%s"", homedir.GetShortcutString(), home, line)
+ }
+ if runtime.GOOS != ""windows"" {
+ i := strings.Index(line, homedir.GetShortcutString())
+ if i >= 0 && i != len(line)-1 && line[i+1] != '/' {
+ c.Fatalf(""Main help should not have used home shortcut:\n%s"", line)
+ }
+ }
+ }
-### 2. What did you expect to see? (Required)
+ // Make sure each cmd's help text fits within 90 chars and that
+ // on non-windows system we use ~ when possible (to shorten things).
+ // Pull the list of commands from the ""Commands:"" section of docker help
+ helpCmd = exec.Command(dockerBinary, ""help"")
+ helpCmd.Env = newEnvs
+ out, _, err = runCommandWithOutput(helpCmd)
+ c.Assert(err, checker.IsNil, check.Commentf(out))
+ i := strings.Index(out, ""Commands:"")
+ c.Assert(i, checker.GreaterOrEqualThan, 0, check.Commentf(""Missing 'Commands:' in:\n%s"", out))
-In mysql 8.0
+ cmds := []string{}
+ // Grab all chars starting at ""Commands:""
+ helpOut := strings.Split(out[i:], ""\n"")
+ // First line is just ""Commands:""
+ if isLocalDaemon {
+ // Replace first line with ""daemon"" command since it's not part of the list of commands.
+ helpOut[0] = "" daemon""
+ } else {
+ // Skip first line
+ helpOut = helpOut[1:]
+ }
-``` mysql
-mysql> select * from t2 where a <= 69;
-+------+
-| a |
-+------+
-| 2069 |
-+------+
-1 row in set (0.00 sec)
-```
+ // Create the list of commands we want to test
+ cmdsToTest := []string{}
+ for _, cmd := range helpOut {
+ // Stop on blank line or non-idented line
+ if cmd == """" || !unicode.IsSpace(rune(cmd[0])) {
+ break
+ }
-### 3. What did you see instead (Required)
-
-``` mysql
-mysql> select * from t2 where a <= 69;
-Empty set (0.00 sec)
-
-mysql> explain select * from t2 where a <= 69;
-+-------------------------+---------+-----------+---------------+--------------------------------+
-| id | estRows | task | access object | operator info |
-+-------------------------+---------+-----------+---------------+--------------------------------+
-| TableReader_7 | 1.00 | root | | data:Selection_6 |
-| └─Selection_6 | 1.00 | cop[tikv] | | le(test.t2.a, 69) |
-| └─TableFullScan_5 | 3.00 | cop[tikv] | table:t2 | keep order:false, stats:pseudo |
-+-------------------------+---------+-----------+---------------+--------------------------------+
-3 rows in set (0.00 sec)
-```
+ // Grab just the first word of each line
+ cmd = strings.Split(strings.TrimSpace(cmd), "" "")[0]
+ cmds = append(cmds, cmd) // Saving count for later
-`69` should be adjusted to `2069`.
-
-### 4. What is your TiDB version? (Required)
-
-
-
-``` mysql
-mysql> select tidb_version();
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: None
-Edition: Community
-Git Commit Hash: None
-Git Branch: None
-UTC Build Time: None
-GoVersion: go1.15
-Race Enabled: false
-TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
-Check Table Before Drop: false |
-+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-1 row in set (0.00 sec)
-```
+ cmdsToTest = append(cmdsToTest, cmd)
+ }
-## Score
+ // Add some 'two word' commands - would be nice to automatically
+ // calculate this list - somehow
+ cmdsToTest = append(cmdsToTest, ""volume create"")
+ cmdsToTest = append(cmdsToTest, ""volume inspect"")
+ cmdsToTest = append(cmdsToTest, ""volume ls"")
+ cmdsToTest = append(cmdsToTest, ""volume rm"")
+ cmdsToTest = append(cmdsToTest, ""network connect"")
+ cmdsToTest = append(cmdsToTest, ""network create"")
+ cmdsToTest = append(cmdsToTest, ""network disconnect"")
+ cmdsToTest = append(cmdsToTest, ""network inspect"")
+ cmdsToTest = append(cmdsToTest, ""network ls"")
+ cmdsToTest = append(cmdsToTest, ""network rm"")
-- 600
+ // Divide the list of commands into go routines and run the func testcommand on the commands in parallel
+ // to save runtime of test
-## Mentor
+ errChan := make(chan error)
-* @lzmhhh123 ",1,comparison result is incorrect between year column and int constant bug report please answer these questions before submitting your issue thanks minimal reproduce step required mysql create table a year insert into values select from where a what did you expect to see required in mysql mysql mysql select from where a a row in set sec what did you see instead required mysql mysql select from where a empty set sec mysql explain select from where a id estrows task access object operator info tablereader root data selection └─selection cop le test a └─tablefullscan cop table keep order false stats pseudo rows in set sec should be adjusted to what is your tidb version required mysql mysql select tidb version tidb version release version none edition community git commit hash none git branch none utc build time none goversion race enabled false tikv min version check table before drop false row in set sec score mentor ,1
-5800,8247240513.0,IssuesEvent,2018-09-11 15:02:16,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,"""div"" scientific notation values out of range",help wanted type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+ for index := 0; index < len(cmdsToTest); index++ {
+ go func(index int) {
+ errChan <- testCommand(cmdsToTest[index], newEnvs, scanForHome, home)
+ }(index)
+ }
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+ for index := 0; index < len(cmdsToTest); index++ {
+ err := <-errChan
+ if err != nil {
+ c.Fatal(err)
+ }
+ }
+ }
-```sql
-select (1.175494351E-37 div 1.7976931348623157E+308);
```
+
-2. What did you expect to see?
+Leave a reaction on this issue to contribute to the project by classifying this instance as a **Bug** :-1:, **Mitigated** :+1:, or **Desirable Behavior** :rocket:
+See the descriptions of the classifications [here](https://github.com/github-vet/rangeclosure-findings#how-can-i-help) for more information.
-```
-+-----------------------------------------------+
-| (1.175494351E-37 div 1.7976931348623157E+308) |
-+-----------------------------------------------+
-| 0 |
-+-----------------------------------------------+
-```
+commit ID: 75c36bcc64a5597919a16a7d43463f7e7c5e1499
+",0,antoniorea rickfast docker integration cli docker cli help test go loc found a possible issue in at the below snippet of go code triggered static analysis which searches for goroutines and or defer statements which capture loop variables click here to show the line s of go which triggered the analyzer go for home range homes dup baseenvs and add our new home value newenvs make string len baseenvs copy newenvs baseenvs newenvs homekey home scanforhome runtime goos windows home check main help text to make sure its not over chars helpcmd exec command dockerbinary help helpcmd env newenvs out err runcommandwithoutput helpcmd c assert err checker isnil check commentf out lines strings split out n for line range lines all lines should not end with a space c assert line checker not checker hassuffix check commentf line should not end with a space if scanforhome strings contains line home c fatalf line should use q instead of q n s homedir getshortcutstring home line if runtime goos windows i strings index line homedir getshortcutstring if i i len line line c fatalf main help should not have used home shortcut n s line make sure each cmd s help text fits within chars and that on non windows system we use when possible to shorten things pull the list of commands from the commands section of docker help helpcmd exec command dockerbinary help helpcmd env newenvs out err runcommandwithoutput helpcmd c assert err checker isnil check commentf out i strings index out commands c assert i checker greaterorequalthan check commentf missing commands in n s out cmds string grab all chars starting at commands helpout strings split out n first line is just commands if islocaldaemon replace first line with daemon command since it s not part of the list of commands helpout daemon else skip first line helpout helpout create the list of commands we want to test cmdstotest string for cmd range helpout stop on blank line or non idented line if cmd unicode isspace rune cmd break grab just the first word of each line cmd strings split strings trimspace cmd cmds append cmds cmd saving count for later cmdstotest append cmdstotest cmd add some two word commands would be nice to automatically calculate this list somehow cmdstotest append cmdstotest volume create cmdstotest append cmdstotest volume inspect cmdstotest append cmdstotest volume ls cmdstotest append cmdstotest volume rm cmdstotest append cmdstotest network connect cmdstotest append cmdstotest network create cmdstotest append cmdstotest network disconnect cmdstotest append cmdstotest network inspect cmdstotest append cmdstotest network ls cmdstotest append cmdstotest network rm divide the list of commands into go routines and run the func testcommand on the commands in parallel to save runtime of test errchan make chan error for index index len cmdstotest index go func index int errchan testcommand cmdstotest newenvs scanforhome home index for index index len cmdstotest index err errchan if err nil c fatal err leave a reaction on this issue to contribute to the project by classifying this instance as a bug mitigated or desirable behavior rocket see the descriptions of the classifications for more information commit id ,0
+5749,8205081047.0,IssuesEvent,2018-09-03 08:59:40,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,insert a id > 9223372036854775807 should not raise an error,type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```sql
+create table bug43196 (`id` bigint(20) unsigned NOT NULL AUTO_INCREMENT PRIMARY KEY, `a` bigint(20) unsigned NOT NULL);
+insert into bug43196(id,a) values(18446744073709551200,1);
+```
+
+2. What did you expect to see?
+No error.
+
+
+3. What did you see instead?
+ERROR 1690 (22003): constant 18446744073709551200 overflows bigint
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+e04f74b031f5b47dba79537e7780356bc96745c5
+",True,"insert a id > 9223372036854775807 should not raise an error - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```sql
+create table bug43196 (`id` bigint(20) unsigned NOT NULL AUTO_INCREMENT PRIMARY KEY, `a` bigint(20) unsigned NOT NULL);
+insert into bug43196(id,a) values(18446744073709551200,1);
+```
+
+2. What did you expect to see?
+No error.
+
+
+3. What did you see instead?
+ERROR 1690 (22003): constant 18446744073709551200 overflows bigint
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+e04f74b031f5b47dba79537e7780356bc96745c5
+",1,insert a id should not raise an error please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql create table id bigint unsigned not null auto increment primary key a bigint unsigned not null insert into id a values what did you expect to see no error what did you see instead error constant overflows bigint what version of tidb are you using tidb server v or run select tidb version on tidb ,1
+231643,25525475817.0,IssuesEvent,2022-11-29 01:37:18,kapseliboi/WeiPay,https://api.github.com/repos/kapseliboi/WeiPay,reopened,"CVE-2021-43138 (High) detected in async-2.0.0.tgz, async-2.6.2.tgz",security vulnerability,"## CVE-2021-43138 - High Severity Vulnerability
+ Vulnerable Libraries - async-2.0.0.tgz, async-2.6.2.tgz
+
-3. What did you see instead?
+async-2.0.0.tgz
-```
-ERROR 1690 (22003): %s value is out of range in '%s'
-```
+
Higher-order functions and common patterns for asynchronous code
Path to vulnerable library: /node_modules/socketcluster-server/node_modules/async/package.json,/node_modules/sc-broker-cluster/node_modules/async/package.json,/node_modules/socketcluster/node_modules/async/package.json
+
-4. What version of TiDB are you using (`tidb-server -V`)?
+Dependency Hierarchy:
+ - remotedev-rn-debugger-0.8.3.tgz (Root Library)
+ - remotedev-server-0.2.7.tgz
+ - socketcluster-8.0.2.tgz
+ - :x: **async-2.0.0.tgz** (Vulnerable Library)
+
+async-2.6.2.tgz
-",True,"""div"" scientific notation values out of range - Please answer these questions before submitting your issue. Thanks!
+
Higher-order functions and common patterns for asynchronous code
Path to vulnerable library: /node_modules/async/package.json
+
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+Dependency Hierarchy:
+ - react-native-0.55.4.tgz (Root Library)
+ - metro-0.30.2.tgz
+ - :x: **async-2.6.2.tgz** (Vulnerable Library)
+
-```sql
-select (1.175494351E-37 div 1.7976931348623157E+308);
-```
+
Found in base branch: stable
+
+
+
+ Vulnerability Details
+
+
+In Async before 2.6.4 and 3.x before 3.2.2, a malicious user can obtain privileges via the mapValues() method, aka lib/internal/iterator.js createObjectIterator prototype pollution.
-2. What did you expect to see?
+
Direct dependency fix Resolution (react-native): 0.65.0
-```
-ERROR 1690 (22003): %s value is out of range in '%s'
-```
+
+
+
-4. What version of TiDB are you using (`tidb-server -V`)?
+***
+Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",True,"CVE-2021-43138 (High) detected in async-2.0.0.tgz, async-2.6.2.tgz - ## CVE-2021-43138 - High Severity Vulnerability
+ Vulnerable Libraries - async-2.0.0.tgz, async-2.6.2.tgz
+
-",1, div scientific notation values out of range please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql select div what did you expect to see div what did you see instead error s value is out of range in s what version of tidb are you using tidb server v ,1
-451606,13039229324.0,IssuesEvent,2020-07-28 16:24:07,googleapis/release-please,https://api.github.com/repos/googleapis/release-please,closed,Cannot read property 'sha' of undefined (Java),priority: p2 type: bug,"We're seeing a bunch of these in the `repo-automation-bots` logs:
+async-2.0.0.tgz
Path to vulnerable library: /node_modules/socketcluster-server/node_modules/async/package.json,/node_modules/sc-broker-cluster/node_modules/async/package.json,/node_modules/socketcluster/node_modules/async/package.json
+
-It looks like it's possible for the number of commits in this situation to be 0:
+Dependency Hierarchy:
+ - remotedev-rn-debugger-0.8.3.tgz (Root Library)
+ - remotedev-server-0.2.7.tgz
+ - socketcluster-8.0.2.tgz
+ - :x: **async-2.0.0.tgz** (Vulnerable Library)
+
Path to vulnerable library: /node_modules/async/package.json
+
-In this case, the size of the value returned from `this.commits` is 0. ",1.0,"Cannot read property 'sha' of undefined (Java) - We're seeing a bunch of these in the `repo-automation-bots` logs:
+Dependency Hierarchy:
+ - react-native-0.55.4.tgz (Root Library)
+ - metro-0.30.2.tgz
+ - :x: **async-2.6.2.tgz** (Vulnerable Library)
+
+
+In Async before 2.6.4 and 3.x before 3.2.2, a malicious user can obtain privileges via the mapValues() method, aka lib/internal/iterator.js createObjectIterator prototype pollution.
-It looks like it's possible for the number of commits in this situation to be 0:
+
+For more information on CVSS3 Scores, click here.
+
+
+
+ Suggested Fix
+
-In this case, the size of the value returned from `this.commits` is 0. ",0,cannot read property sha of undefined java we re seeing a bunch of these in the repo automation bots logs typeerror cannot read property sha of undefined at javayoshi run workspace node modules release please build src releasers java yoshi js it looks like it s possible for the number of commits in this situation to be js if this snapshot const latestcommit await this commits latesttag latesttag sha undefined true prsha latestcommit sha in this case the size of the value returned from this commits is ,0
-11111,13131607739.0,IssuesEvent,2020-08-06 17:19:47,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,error message is not compatible with MySQL,good-first-issue status/help-wanted type/compatibility,"## Bug Report
-
-Please answer these questions before submitting your issue. Thanks!
+
Direct dependency fix Resolution (react-native): 0.65.0
-1. What did you do?
-``` sql
-create table t(a int);
-select a as b from t group by values(b);
-```
+
+
+
-2. What did you expect to see?
-``` sql
-mysql> SELECT a AS b FROM t GROUP BY VALUES(b);
-ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column 'test.t.a' which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by
-```
+***
+Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",0,cve high detected in async tgz async tgz cve high severity vulnerability vulnerable libraries async tgz async tgz async tgz higher order functions and common patterns for asynchronous code library home page a href path to dependency file package json path to vulnerable library node modules socketcluster server node modules async package json node modules sc broker cluster node modules async package json node modules socketcluster node modules async package json dependency hierarchy remotedev rn debugger tgz root library remotedev server tgz socketcluster tgz x async tgz vulnerable library async tgz higher order functions and common patterns for asynchronous code library home page a href path to dependency file package json path to vulnerable library node modules async package json dependency hierarchy react native tgz root library metro tgz x async tgz vulnerable library found in base branch stable vulnerability details in async before and x before a malicious user can obtain privileges via the mapvalues method aka lib internal iterator js createobjectiterator prototype pollution publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution async direct dependency fix resolution react native step up your open source security game with mend ,0
+386091,11431716118.0,IssuesEvent,2020-02-04 12:44:49,googleapis/teeny-request,https://api.github.com/repos/googleapis/teeny-request,closed,Synthesis failed for teeny-request,autosynth failure priority: p1 type: bug,"Hello! Autosynth couldn't regenerate teeny-request. :broken_heart:
+Here's the output from running `synth.py`:
-3. What did you see instead?
-Column name is lost.
-``` sql
-tidb> SELECT a AS b FROM t GROUP BY VALUES(b);
-ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column '' which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by
```
+Cloning into 'working_repo'...
+Switched to branch 'autosynth'
+Running synthtool
+['/tmpfs/src/git/autosynth/env/bin/python3', '-m', 'synthtool', 'synth.py', '--']
+synthtool > Executing /tmpfs/src/git/autosynth/working_repo/synth.py.
+.eslintignore
+.eslintrc.yml
+.github/ISSUE_TEMPLATE/bug_report.md
+.github/ISSUE_TEMPLATE/feature_request.md
+.github/ISSUE_TEMPLATE/support_request.md
+.github/PULL_REQUEST_TEMPLATE.md
+synthtool > Wrote metadata to synth.metadata.
+Traceback (most recent call last):
+ File ""/home/kbuilder/.pyenv/versions/3.6.1/lib/python3.6/runpy.py"", line 193, in _run_module_as_main
+ ""__main__"", mod_spec)
+ File ""/home/kbuilder/.pyenv/versions/3.6.1/lib/python3.6/runpy.py"", line 85, in _run_code
+ exec(code, run_globals)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/synthtool/__main__.py"", line 99, in
+ main()
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/click/core.py"", line 764, in __call__
+ return self.main(*args, **kwargs)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/click/core.py"", line 717, in main
+ rv = self.invoke(ctx)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/click/core.py"", line 956, in invoke
+ return ctx.invoke(self.callback, **ctx.params)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/click/core.py"", line 555, in invoke
+ return callback(*args, **kwargs)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/synthtool/__main__.py"", line 91, in main
+ spec.loader.exec_module(synth_module) # type: ignore
+ File """", line 678, in exec_module
+ File """", line 205, in _call_with_frames_removed
+ File ""/tmpfs/src/git/autosynth/working_repo/synth.py"", line 6, in
+ templates = common_templates.node_library()
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/synthtool/gcp/common.py"", line 89, in node_library
+ return self._generic_library(""node_library"", **kwargs)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/synthtool/gcp/common.py"", line 49, in _generic_library
+ result = t.render(**kwargs)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/synthtool/sources/templates.py"", line 83, in render
+ _render_to_path(self.env, template_name, self.dir, kwargs)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/synthtool/sources/templates.py"", line 53, in _render_to_path
+ output.dump(fh)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/jinja2/environment.py"", line 1313, in dump
+ fp.writelines(iterable)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/jinja2/environment.py"", line 1357, in __next__
+ return self._next()
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/jinja2/environment.py"", line 1125, in generate
+ yield self.environment.handle_exception()
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/jinja2/environment.py"", line 832, in handle_exception
+ reraise(*rewrite_traceback_stack(source=source))
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/jinja2/_compat.py"", line 28, in reraise
+ raise value.with_traceback(tb)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/synthtool/gcp/templates/node_library/.github/PULL_REQUEST_TEMPLATE.md"", line 2, in top-level template code
+ - [ ] Make sure to open an issue as a [bug/issue](https://github.com/{{ metadata['repo']['repo'] }}/issues/new/choose) before writing your code! That way we can discuss the change, evaluate designs, and agree on the general idea
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/jinja2/environment.py"", line 452, in getitem
+ return obj[argument]
+jinja2.exceptions.UndefinedError: 'dict object' has no attribute 'repo'
+Synthesis failed
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
```
-select tidb_version();
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v2.1.0-rc.3-1-geb617c5f9
-Git Commit Hash: eb617c5f9f75c38d75fa848b6732c6071e66ab3e
-Git Branch: master
-UTC Build Time: 2018-09-30 03:35:34
-GoVersion: go version go1.10.3 darwin/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false |
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-1 row in set (0.00 sec)
-```
-",True,"error message is not compatible with MySQL - ## Bug Report
-Please answer these questions before submitting your issue. Thanks!
+Google internal developers can see the full log [here](https://sponge/bee1fa8c-0b9b-4d56-a419-93e64f79e233).
+",1.0,"Synthesis failed for teeny-request - Hello! Autosynth couldn't regenerate teeny-request. :broken_heart:
-1. What did you do?
-``` sql
-create table t(a int);
-select a as b from t group by values(b);
-```
+Here's the output from running `synth.py`:
-2. What did you expect to see?
-``` sql
-mysql> SELECT a AS b FROM t GROUP BY VALUES(b);
-ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column 'test.t.a' which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by
```
+Cloning into 'working_repo'...
+Switched to branch 'autosynth'
+Running synthtool
+['/tmpfs/src/git/autosynth/env/bin/python3', '-m', 'synthtool', 'synth.py', '--']
+synthtool > Executing /tmpfs/src/git/autosynth/working_repo/synth.py.
+.eslintignore
+.eslintrc.yml
+.github/ISSUE_TEMPLATE/bug_report.md
+.github/ISSUE_TEMPLATE/feature_request.md
+.github/ISSUE_TEMPLATE/support_request.md
+.github/PULL_REQUEST_TEMPLATE.md
+synthtool > Wrote metadata to synth.metadata.
+Traceback (most recent call last):
+ File ""/home/kbuilder/.pyenv/versions/3.6.1/lib/python3.6/runpy.py"", line 193, in _run_module_as_main
+ ""__main__"", mod_spec)
+ File ""/home/kbuilder/.pyenv/versions/3.6.1/lib/python3.6/runpy.py"", line 85, in _run_code
+ exec(code, run_globals)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/synthtool/__main__.py"", line 99, in
+ main()
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/click/core.py"", line 764, in __call__
+ return self.main(*args, **kwargs)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/click/core.py"", line 717, in main
+ rv = self.invoke(ctx)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/click/core.py"", line 956, in invoke
+ return ctx.invoke(self.callback, **ctx.params)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/click/core.py"", line 555, in invoke
+ return callback(*args, **kwargs)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/synthtool/__main__.py"", line 91, in main
+ spec.loader.exec_module(synth_module) # type: ignore
+ File """", line 678, in exec_module
+ File """", line 205, in _call_with_frames_removed
+ File ""/tmpfs/src/git/autosynth/working_repo/synth.py"", line 6, in
+ templates = common_templates.node_library()
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/synthtool/gcp/common.py"", line 89, in node_library
+ return self._generic_library(""node_library"", **kwargs)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/synthtool/gcp/common.py"", line 49, in _generic_library
+ result = t.render(**kwargs)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/synthtool/sources/templates.py"", line 83, in render
+ _render_to_path(self.env, template_name, self.dir, kwargs)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/synthtool/sources/templates.py"", line 53, in _render_to_path
+ output.dump(fh)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/jinja2/environment.py"", line 1313, in dump
+ fp.writelines(iterable)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/jinja2/environment.py"", line 1357, in __next__
+ return self._next()
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/jinja2/environment.py"", line 1125, in generate
+ yield self.environment.handle_exception()
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/jinja2/environment.py"", line 832, in handle_exception
+ reraise(*rewrite_traceback_stack(source=source))
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/jinja2/_compat.py"", line 28, in reraise
+ raise value.with_traceback(tb)
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/synthtool/gcp/templates/node_library/.github/PULL_REQUEST_TEMPLATE.md"", line 2, in top-level template code
+ - [ ] Make sure to open an issue as a [bug/issue](https://github.com/{{ metadata['repo']['repo'] }}/issues/new/choose) before writing your code! That way we can discuss the change, evaluate designs, and agree on the general idea
+ File ""/tmpfs/src/git/autosynth/env/lib/python3.6/site-packages/jinja2/environment.py"", line 452, in getitem
+ return obj[argument]
+jinja2.exceptions.UndefinedError: 'dict object' has no attribute 'repo'
+Synthesis failed
-3. What did you see instead?
-Column name is lost.
-``` sql
-tidb> SELECT a AS b FROM t GROUP BY VALUES(b);
-ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column '' which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by
```
+Google internal developers can see the full log [here](https://sponge/bee1fa8c-0b9b-4d56-a419-93e64f79e233).
+",0,synthesis failed for teeny request hello autosynth couldn t regenerate teeny request broken heart here s the output from running synth py cloning into working repo switched to branch autosynth running synthtool synthtool executing tmpfs src git autosynth working repo synth py eslintignore eslintrc yml github issue template bug report md github issue template feature request md github issue template support request md github pull request template md synthtool wrote metadata to synth metadata traceback most recent call last file home kbuilder pyenv versions lib runpy py line in run module as main main mod spec file home kbuilder pyenv versions lib runpy py line in run code exec code run globals file tmpfs src git autosynth env lib site packages synthtool main py line in main file tmpfs src git autosynth env lib site packages click core py line in call return self main args kwargs file tmpfs src git autosynth env lib site packages click core py line in main rv self invoke ctx file tmpfs src git autosynth env lib site packages click core py line in invoke return ctx invoke self callback ctx params file tmpfs src git autosynth env lib site packages click core py line in invoke return callback args kwargs file tmpfs src git autosynth env lib site packages synthtool main py line in main spec loader exec module synth module type ignore file line in exec module file line in call with frames removed file tmpfs src git autosynth working repo synth py line in templates common templates node library file tmpfs src git autosynth env lib site packages synthtool gcp common py line in node library return self generic library node library kwargs file tmpfs src git autosynth env lib site packages synthtool gcp common py line in generic library result t render kwargs file tmpfs src git autosynth env lib site packages synthtool sources templates py line in render render to path self env template name self dir kwargs file tmpfs src git autosynth env lib site packages synthtool sources templates py line in render to path output dump fh file tmpfs src git autosynth env lib site packages environment py line in dump fp writelines iterable file tmpfs src git autosynth env lib site packages environment py line in next return self next file tmpfs src git autosynth env lib site packages environment py line in generate yield self environment handle exception file tmpfs src git autosynth env lib site packages environment py line in handle exception reraise rewrite traceback stack source source file tmpfs src git autosynth env lib site packages compat py line in reraise raise value with traceback tb file tmpfs src git autosynth env lib site packages synthtool gcp templates node library github pull request template md line in top level template code make sure to open an issue as a metadata issues new choose before writing your code that way we can discuss the change evaluate designs and agree on the general idea file tmpfs src git autosynth env lib site packages environment py line in getitem return obj exceptions undefinederror dict object has no attribute repo synthesis failed google internal developers can see the full log ,0
+10630,12539780765.0,IssuesEvent,2020-06-05 09:12:28,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,delete the `TiDB` value of `tidb_isolation_read_engines`,compatibility-breaker component/session type/enhancement,"## Development Task
+
+The system tables in `information_schema` and `metrics_schema` are in-memory tables of TiDB server. The queries of them are controlled by the value of `tidb_isolation_read_engines`(""tidb""), which is very unfriendly for users. So we decide to delete it.",True,"delete the `TiDB` value of `tidb_isolation_read_engines` - ## Development Task
+
+The system tables in `information_schema` and `metrics_schema` are in-memory tables of TiDB server. The queries of them are controlled by the value of `tidb_isolation_read_engines`(""tidb""), which is very unfriendly for users. So we decide to delete it.",1,delete the tidb value of tidb isolation read engines development task the system tables in information schema and metrics schema are in memory tables of tidb server the queries of them are controlled by the value of tidb isolation read engines tidb which is very unfriendly for users so we decide to delete it ,1
+11096,13124637047.0,IssuesEvent,2020-08-06 04:25:07,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,compatibility with schemaspy,type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+I created foreign keys that show up in the information schema and then ran schema spy
+
+``` bash
+#!/usr/bin/env bash
+set -euo pipefail
+
+mkdir -p doc/schema
+sudo chown -R 1000:1000 doc/schema/
+./scripts/docker -v ""$PWD/doc/schema:/output"" schemaspy/schemaspy -u root -db -t mysql -port 4000 -host -s
+sudo chown -R $(whoami):$(whoami) doc/schema/
+```
+
+Foreign keys show up with this query:
+
+```
+ SELECT
+ -> TABLE_NAME,COLUMN_NAME,CONSTRAINT_NAME, REFERENCED_TABLE_NAME,REFERENCED_COLUMN_NAME
+ -> FROM
+ -> INFORMATION_SCHEMA.KEY_COLUMN_USAGE
+ -> WHERE
+ -> REFERENCED_TABLE_SCHEMA = '' AND
+ -> REFERENCED_TABLE_NAME = 'clusters';
+```
+
+2. What did you expect to see?
+
+Entity relations at relationships.html
+
+
+3. What did you see instead?
+
+All Relationships
+×
+ Missed Relationships!
+No relationships were detected in the schema.
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+pingcap/tidb:v2.1.0-rc.4",True,"compatibility with schemaspy - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+I created foreign keys that show up in the information schema and then ran schema spy
+
+``` bash
+#!/usr/bin/env bash
+set -euo pipefail
+
+mkdir -p doc/schema
+sudo chown -R 1000:1000 doc/schema/
+./scripts/docker -v ""$PWD/doc/schema:/output"" schemaspy/schemaspy -u root -db -t mysql -port 4000 -host -s
+sudo chown -R $(whoami):$(whoami) doc/schema/
+```
+
+Foreign keys show up with this query:
+
+```
+ SELECT
+ -> TABLE_NAME,COLUMN_NAME,CONSTRAINT_NAME, REFERENCED_TABLE_NAME,REFERENCED_COLUMN_NAME
+ -> FROM
+ -> INFORMATION_SCHEMA.KEY_COLUMN_USAGE
+ -> WHERE
+ -> REFERENCED_TABLE_SCHEMA = '' AND
+ -> REFERENCED_TABLE_NAME = 'clusters';
+```
+
+2. What did you expect to see?
+
+Entity relations at relationships.html
+
+
+3. What did you see instead?
+
+All Relationships
+×
+ Missed Relationships!
+No relationships were detected in the schema.
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+pingcap/tidb:v2.1.0-rc.4",1,compatibility with schemaspy bug report please answer these questions before submitting your issue thanks what did you do i created foreign keys that show up in the information schema and then ran schema spy bash usr bin env bash set euo pipefail mkdir p doc schema sudo chown r doc schema scripts docker v pwd doc schema output schemaspy schemaspy u root db t mysql port host s sudo chown r whoami whoami doc schema foreign keys show up with this query select table name column name constraint name referenced table name referenced column name from information schema key column usage where referenced table schema and referenced table name clusters what did you expect to see entity relations at relationships html what did you see instead all relationships × missed relationships no relationships were detected in the schema what version of tidb are you using tidb server v or run select tidb version on tidb pingcap tidb rc ,1
+5799,8247236186.0,IssuesEvent,2018-09-11 15:01:38,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Date time literal compability,help wanted type/compatibility,"Please Add below syntax support.
+
+```
+DATE 'str'
+TIME 'str'
+TIMESTAMP 'str'
+```
+
+https://dev.mysql.com/doc/refman/5.7/en/date-and-time-literals.html
+
+",True,"Date time literal compability - Please Add below syntax support.
+
+```
+DATE 'str'
+TIME 'str'
+TIMESTAMP 'str'
+```
+
+https://dev.mysql.com/doc/refman/5.7/en/date-and-time-literals.html
+
+",1,date time literal compability please add below syntax support date str time str timestamp str ,1
+6239,8638222438.0,IssuesEvent,2018-11-23 14:03:32,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,GRANT statements do not invalidate privilege cache,type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```
+CREATE USER ted;
+```
+
+Immediately after:
+
+```
+mysql -u ted
+```
+
+2. What did you expect to see?
+
+Login should work.
+
+3. What did you see instead?
+
+Error (requires `FLUSH PRIVILEGES` to be run).
+
+For MySQL the following commands imply `FLUSH PRIVILEGES`:
+- GRANT
+- CREATE USER
+- SET PASSWORD
+- REVOKE
+- DROP USER
+
+The TiDB test suite also contains a lot of `FLUSH PRIVILEGES` commands that for MySQL compatibility would not be required.
+
+This has the greatest impact on users that have permission to change their password, but don't have the ability to `FLUSH PRIVILEGES`! (fixed in https://github.com/pingcap/tidb/pull/8426 ) i.e. it is a very weird semantic for the change to take effect much further down the line.
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+mysql> select tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v2.1.0-rc.3-213-g4ec77d5cb
+Git Commit Hash: 4ec77d5cbe2536b587afa457a7dcc06bac61eda4
+Git Branch: set-password
+UTC Build Time: 2018-11-23 01:59:37
+GoVersion: go version go1.11 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false
+1 row in set (0.00 sec)
+```
+",True,"GRANT statements do not invalidate privilege cache - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```
+CREATE USER ted;
+```
+
+Immediately after:
+
+```
+mysql -u ted
+```
+
+2. What did you expect to see?
+
+Login should work.
+
+3. What did you see instead?
+
+Error (requires `FLUSH PRIVILEGES` to be run).
+
+For MySQL the following commands imply `FLUSH PRIVILEGES`:
+- GRANT
+- CREATE USER
+- SET PASSWORD
+- REVOKE
+- DROP USER
+
+The TiDB test suite also contains a lot of `FLUSH PRIVILEGES` commands that for MySQL compatibility would not be required.
+
+This has the greatest impact on users that have permission to change their password, but don't have the ability to `FLUSH PRIVILEGES`! (fixed in https://github.com/pingcap/tidb/pull/8426 ) i.e. it is a very weird semantic for the change to take effect much further down the line.
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+mysql> select tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v2.1.0-rc.3-213-g4ec77d5cb
+Git Commit Hash: 4ec77d5cbe2536b587afa457a7dcc06bac61eda4
+Git Branch: set-password
+UTC Build Time: 2018-11-23 01:59:37
+GoVersion: go version go1.11 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false
+1 row in set (0.00 sec)
+```
+",1,grant statements do not invalidate privilege cache bug report please answer these questions before submitting your issue thanks what did you do create user ted immediately after mysql u ted what did you expect to see login should work what did you see instead error requires flush privileges to be run for mysql the following commands imply flush privileges grant create user set password revoke drop user the tidb test suite also contains a lot of flush privileges commands that for mysql compatibility would not be required this has the greatest impact on users that have permission to change their password but don t have the ability to flush privileges fixed in i e it is a very weird semantic for the change to take effect much further down the line what version of tidb are you using tidb server v or run select tidb version on tidb mysql select tidb version g row tidb version release version rc git commit hash git branch set password utc build time goversion go version linux race enabled false tikv min version alpha check table before drop false row in set sec ,1
+146715,23111894520.0,IssuesEvent,2022-07-27 13:41:10,Kong/insomnia,https://api.github.com/repos/Kong/insomnia,closed,[Feature request] Improve handling of user importing existing project from Git into empty document,A-ui-ux A-design C-improvement needs-triage,"I didn't realize the proper way to import an existing workspace from Git into Insomnia was to select Create -> Import From Git Clone. The path I started with was Create -> Blank Document, then tried to set up Git Sync then do a pull, which returned this error:
+
+
+
+I know I'm not the only one who's done this before. :)
+
+I think we should assume this is a likely path a new user might take and either 1) return a more meaningful error and guide them to the right way to set up a project from a Git clone, 2) recognize user intent and just clone the Git repo into the empty doc, or 3) something else? Thanks!
+
+",1.0,"[Feature request] Improve handling of user importing existing project from Git into empty document - I didn't realize the proper way to import an existing workspace from Git into Insomnia was to select Create -> Import From Git Clone. The path I started with was Create -> Blank Document, then tried to set up Git Sync then do a pull, which returned this error:
+
+
+
+I know I'm not the only one who's done this before. :)
+
+I think we should assume this is a likely path a new user might take and either 1) return a more meaningful error and guide them to the right way to set up a project from a Git clone, 2) recognize user intent and just clone the Git repo into the empty doc, or 3) something else? Thanks!
+
+",0, improve handling of user importing existing project from git into empty document i didn t realize the proper way to import an existing workspace from git into insomnia was to select create import from git clone the path i started with was create blank document then tried to set up git sync then do a pull which returned this error i know i m not the only one who s done this before i think we should assume this is a likely path a new user might take and either return a more meaningful error and guide them to the right way to set up a project from a git clone recognize user intent and just clone the git repo into the empty doc or something else thanks ,0
+11866,13999627955.0,IssuesEvent,2020-10-28 11:06:27,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,expression: let str_to_date() works the same as that in MYSQL,component/expression feature/accepted type/compatibility type/feature-request,"## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+https://github.com/pingcap/tidb/issues/18370 although is fixed, but it need to solve some unexpections.
+
+**Describe the feature you'd like:**
+
+```
+mysql> SELECT STR_TO_DATE('2020-07-04 11:22:33 PM c', '%Y-%m-%d %r');
++--------------------------------------------------------+
+| STR_TO_DATE('2020-07-04 11:22:33 PM c', '%Y-%m-%d %r') |
++--------------------------------------------------------+
+| 2020-07-04 23:22:33 |
++--------------------------------------------------------+
+1 row in set (0.00 sec) // it should throw a warning.
+
+mysql> SELECT STR_TO_DATE('11:22:33 PM', ' %r');
++-----------------------------------+
+| STR_TO_DATE('11:22:33 PM', ' %r') |
++-----------------------------------+
+| NULL |
++-----------------------------------+
+1 row in set, 1 warning (0.00 sec) // should work normally.
+
+mysql> show warnings;
++---------+------+-------------------------------------------------+
+| Level | Code | Message |
++---------+------+-------------------------------------------------+
+| Warning | 1292 | Incorrect datetime value: '0000-00-00 23:22:33' |
++---------+------+-------------------------------------------------+
+1 row in set (0.00 sec)
+
+
+```
+**Describe alternatives you've considered:**
+
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+
+",True,"expression: let str_to_date() works the same as that in MYSQL - ## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+https://github.com/pingcap/tidb/issues/18370 although is fixed, but it need to solve some unexpections.
+
+**Describe the feature you'd like:**
+
+```
+mysql> SELECT STR_TO_DATE('2020-07-04 11:22:33 PM c', '%Y-%m-%d %r');
++--------------------------------------------------------+
+| STR_TO_DATE('2020-07-04 11:22:33 PM c', '%Y-%m-%d %r') |
++--------------------------------------------------------+
+| 2020-07-04 23:22:33 |
++--------------------------------------------------------+
+1 row in set (0.00 sec) // it should throw a warning.
+
+mysql> SELECT STR_TO_DATE('11:22:33 PM', ' %r');
++-----------------------------------+
+| STR_TO_DATE('11:22:33 PM', ' %r') |
++-----------------------------------+
+| NULL |
++-----------------------------------+
+1 row in set, 1 warning (0.00 sec) // should work normally.
+
+mysql> show warnings;
++---------+------+-------------------------------------------------+
+| Level | Code | Message |
++---------+------+-------------------------------------------------+
+| Warning | 1292 | Incorrect datetime value: '0000-00-00 23:22:33' |
++---------+------+-------------------------------------------------+
+1 row in set (0.00 sec)
+
+
+```
+**Describe alternatives you've considered:**
+
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+
+",1,expression let str to date works the same as that in mysql feature request is your feature request related to a problem please describe although is fixed but it need to solve some unexpections describe the feature you d like mysql select str to date pm c y m d r str to date pm c y m d r row in set sec it should throw a warning mysql select str to date pm r str to date pm r null row in set warning sec should work normally mysql show warnings level code message warning incorrect datetime value row in set sec describe alternatives you ve considered teachability documentation adoption migration strategy ,1
+707553,24309520554.0,IssuesEvent,2022-09-29 20:43:01,PavlAvstin/OZ-CSC-480-HCI-521-Fall-2022,https://api.github.com/repos/PavlAvstin/OZ-CSC-480-HCI-521-Fall-2022,opened,"""Priority Rating for Feature 9"": Missing 'Feature 9' Rating",Quality Assurance Usability Criticality: Moderate Features User Stories and Priority Ratings 1 Missing,"Defect: Missing Feature 9 on the Priority Rating Chart.
+
+Location: ""Priority Rating Chart""
+
+Recommended Fix: Take a quick poll and determine Feature 9's priority and add it to the appropriate spot on the chart.
+
+Criticality: Moderate",1.0,"""Priority Rating for Feature 9"": Missing 'Feature 9' Rating - Defect: Missing Feature 9 on the Priority Rating Chart.
+
+Location: ""Priority Rating Chart""
+
+Recommended Fix: Take a quick poll and determine Feature 9's priority and add it to the appropriate spot on the chart.
+
+Criticality: Moderate",0, priority rating for feature missing feature rating defect missing feature on the priority rating chart location priority rating chart recommended fix take a quick poll and determine feature s priority and add it to the appropriate spot on the chart criticality moderate,0
+9721,11773930222.0,IssuesEvent,2020-03-16 08:28:15,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Support implicit primary key,type/compatibility type/enhancement,"## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+
+In MySQL 8.0, a table with no explicit primary key may still have an effective implicit primary key if it has any UNIQUE indexes on `NOT NULL` columns. In this case, the first such index places the same constraint on table rows as an explicit primary key and that index cannot be made invisible. Consider the following table definition:
+```sql
+CREATE TABLE t2 (
+ i INT NOT NULL,
+ j INT NOT NULL,
+ UNIQUE j_idx (j)
+) ENGINE = InnoDB;
+```
+The key `j_idx` will became a primary key, even if we do not assign `primary key` explicitly.
+
+**Describe the feature you'd like:**
+
+
+
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+
+
+[MySQL document](https://dev.mysql.com/doc/refman/8.0/en/invisible-indexes.html)",True,"Support implicit primary key - ## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+
+In MySQL 8.0, a table with no explicit primary key may still have an effective implicit primary key if it has any UNIQUE indexes on `NOT NULL` columns. In this case, the first such index places the same constraint on table rows as an explicit primary key and that index cannot be made invisible. Consider the following table definition:
+```sql
+CREATE TABLE t2 (
+ i INT NOT NULL,
+ j INT NOT NULL,
+ UNIQUE j_idx (j)
+) ENGINE = InnoDB;
+```
+The key `j_idx` will became a primary key, even if we do not assign `primary key` explicitly.
+
+**Describe the feature you'd like:**
+
+
+
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+
+
+[MySQL document](https://dev.mysql.com/doc/refman/8.0/en/invisible-indexes.html)",1,support implicit primary key feature request is your feature request related to a problem please describe in mysql a table with no explicit primary key may still have an effective implicit primary key if it has any unique indexes on not null columns in this case the first such index places the same constraint on table rows as an explicit primary key and that index cannot be made invisible consider the following table definition sql create table i int not null j int not null unique j idx j engine innodb the key j idx will became a primary key even if we do not assign primary key explicitly describe the feature you d like teachability documentation adoption migration strategy ,1
+75101,9818470246.0,IssuesEvent,2019-06-13 19:20:07,YBogomolov/kleisli-ts,https://api.github.com/repos/YBogomolov/kleisli-ts,opened,Add documentation,documentation,"Describe API in readme or in separate document.
+
+Explore possibilities of generating docs from TSDoc.",1.0,"Add documentation - Describe API in readme or in separate document.
+
+Explore possibilities of generating docs from TSDoc.",0,add documentation describe api in readme or in separate document explore possibilities of generating docs from tsdoc ,0
+17231,23759511348.0,IssuesEvent,2022-09-01 07:40:17,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,`order by` of json value is different with MySQL,type/enhancement type/compatibility component/json,"## Enhancement
+
+```sql
+create table t(i INT, j JSON);
+
+insert into t values (0,'[1,2,3,4]');
+insert into t values (0,'[1,2,3]');
+insert into t values (0,'[5]');
+```
+
+Then consider the following two query:
+
+```sql
+select j from t order by j;
+select j from t where j > json_array(5);
+```
+
+The first line returns:
+```
++--------------+
+| j |
++--------------+
+| [5] |
+| [1, 2, 3] |
+| [1, 2, 3, 4] |
++--------------+
+```
+
+It indicates that `[5]` is the smallest one. However, the second one returns:
+
+```
+Empty Set
+```
+
+It shows no one is greater than `[5]`. It's not consistent :cry: .
+
+For TiDB, it follows the json order, and returns:
+
+```
++--------------+
+| j |
++--------------+
+| [1, 2, 3] |
+| [1, 2, 3, 4] |
+| [5] |
++--------------+
+```
+
+For the first selection.
+",True,"`order by` of json value is different with MySQL - ## Enhancement
+
+```sql
+create table t(i INT, j JSON);
+
+insert into t values (0,'[1,2,3,4]');
+insert into t values (0,'[1,2,3]');
+insert into t values (0,'[5]');
+```
+
+Then consider the following two query:
+
+```sql
+select j from t order by j;
+select j from t where j > json_array(5);
+```
+
+The first line returns:
+```
++--------------+
+| j |
++--------------+
+| [5] |
+| [1, 2, 3] |
+| [1, 2, 3, 4] |
++--------------+
+```
+
+It indicates that `[5]` is the smallest one. However, the second one returns:
+
+```
+Empty Set
+```
+
+It shows no one is greater than `[5]`. It's not consistent :cry: .
+
+For TiDB, it follows the json order, and returns:
+
+```
++--------------+
+| j |
++--------------+
+| [1, 2, 3] |
+| [1, 2, 3, 4] |
+| [5] |
++--------------+
+```
+
+For the first selection.
+",1, order by of json value is different with mysql enhancement sql create table t i int j json insert into t values insert into t values insert into t values then consider the following two query sql select j from t order by j select j from t where j json array the first line returns j it indicates that is the smallest one however the second one returns empty set it shows no one is greater than it s not consistent cry for tidb it follows the json order and returns j for the first selection ,1
+3435,6402529235.0,IssuesEvent,2017-08-06 10:27:05,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,parser: `DISTINCTROW` is not supported,compatibility easy rc3.1,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```
+CREATE TABLE t1 (email varchar(50), infoID BIGINT, dateentered DATETIME);
+CREATE TABLE t2 (infoID BIGINT, shipcode varchar(10));
+
+INSERT INTO t1 (email, infoID, dateentered) VALUES('test1@testdomain.com', 1, '2002-07-30 22:56:38');
+INSERT INTO t2(infoID, shipcode) VALUES(1, 'Z001');
+SELECT DISTINCTROW email, shipcode FROM t1, t2 WHERE t1.infoID=t2.infoID;
+```
+
+2. What did you expect to see?
+
+```
+mysql> CREATE TABLE t1 (email varchar(50), infoID BIGINT, dateentered DATETIME);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> CREATE TABLE t2 (infoID BIGINT, shipcode varchar(10));
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> INSERT INTO t1 (email, infoID, dateentered) VALUES('test1@testdomain.com', 1, '2002-07-30 22:56:38');
+Query OK, 1 row affected (0.00 sec)
+
+mysql> INSERT INTO t2(infoID, shipcode) VALUES(1, 'Z001');
+Query OK, 1 row affected (0.01 sec)
+
+mysql> SELECT DISTINCTROW email, shipcode FROM t1, t2 WHERE t1.infoID=t2.infoID;
++----------------------+----------+
+| email | shipcode |
++----------------------+----------+
+| test1@testdomain.com | Z001 |
++----------------------+----------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> CREATE TABLE t1 (email varchar(50), infoID BIGINT, dateentered DATETIME);
+Query OK, 0 rows affected (0.09 sec)
+
+mysql> CREATE TABLE t2 (infoID BIGINT, shipcode varchar(10));
+Query OK, 0 rows affected (0.09 sec)
+
+mysql> INSERT INTO t1 (email, infoID, dateentered) VALUES('test1@testdomain.com', 1, '2002-07-30 22:56:38');
+Query OK, 1 row affected (0.01 sec)
+
+mysql> INSERT INTO t2(infoID, shipcode) VALUES(1, 'Z001');
+Query OK, 1 row affected (0.01 sec)
+
+mysql> SELECT DISTINCTROW email, shipcode FROM t1, t2 WHERE t1.infoID=t2.infoID;
+ERROR 1105 (HY000): unknown column distinctrow
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"parser: `DISTINCTROW` is not supported - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```
+CREATE TABLE t1 (email varchar(50), infoID BIGINT, dateentered DATETIME);
+CREATE TABLE t2 (infoID BIGINT, shipcode varchar(10));
+
+INSERT INTO t1 (email, infoID, dateentered) VALUES('test1@testdomain.com', 1, '2002-07-30 22:56:38');
+INSERT INTO t2(infoID, shipcode) VALUES(1, 'Z001');
+SELECT DISTINCTROW email, shipcode FROM t1, t2 WHERE t1.infoID=t2.infoID;
+```
+
+2. What did you expect to see?
+
+```
+mysql> CREATE TABLE t1 (email varchar(50), infoID BIGINT, dateentered DATETIME);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> CREATE TABLE t2 (infoID BIGINT, shipcode varchar(10));
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> INSERT INTO t1 (email, infoID, dateentered) VALUES('test1@testdomain.com', 1, '2002-07-30 22:56:38');
+Query OK, 1 row affected (0.00 sec)
+
+mysql> INSERT INTO t2(infoID, shipcode) VALUES(1, 'Z001');
+Query OK, 1 row affected (0.01 sec)
+
+mysql> SELECT DISTINCTROW email, shipcode FROM t1, t2 WHERE t1.infoID=t2.infoID;
++----------------------+----------+
+| email | shipcode |
++----------------------+----------+
+| test1@testdomain.com | Z001 |
++----------------------+----------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> CREATE TABLE t1 (email varchar(50), infoID BIGINT, dateentered DATETIME);
+Query OK, 0 rows affected (0.09 sec)
+
+mysql> CREATE TABLE t2 (infoID BIGINT, shipcode varchar(10));
+Query OK, 0 rows affected (0.09 sec)
+
+mysql> INSERT INTO t1 (email, infoID, dateentered) VALUES('test1@testdomain.com', 1, '2002-07-30 22:56:38');
+Query OK, 1 row affected (0.01 sec)
+
+mysql> INSERT INTO t2(infoID, shipcode) VALUES(1, 'Z001');
+Query OK, 1 row affected (0.01 sec)
+
+mysql> SELECT DISTINCTROW email, shipcode FROM t1, t2 WHERE t1.infoID=t2.infoID;
+ERROR 1105 (HY000): unknown column distinctrow
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,parser distinctrow is not supported please answer these questions before submitting your issue thanks what did you do create table email varchar infoid bigint dateentered datetime create table infoid bigint shipcode varchar insert into email infoid dateentered values testdomain com insert into infoid shipcode values select distinctrow email shipcode from where infoid infoid what did you expect to see mysql create table email varchar infoid bigint dateentered datetime query ok rows affected sec mysql create table infoid bigint shipcode varchar query ok rows affected sec mysql insert into email infoid dateentered values testdomain com query ok row affected sec mysql insert into infoid shipcode values query ok row affected sec mysql select distinctrow email shipcode from where infoid infoid email shipcode testdomain com row in set sec what did you see instead mysql create table email varchar infoid bigint dateentered datetime query ok rows affected sec mysql create table infoid bigint shipcode varchar query ok rows affected sec mysql insert into email infoid dateentered values testdomain com query ok row affected sec mysql insert into infoid shipcode values query ok row affected sec mysql select distinctrow email shipcode from where infoid infoid error unknown column distinctrow what version of tidb are you using tidb server v ,1
+38339,8460130975.0,IssuesEvent,2018-10-22 17:56:06,stan-dev/stan,https://api.github.com/repos/stan-dev/stan,opened,fix parser warnings for semicolons in function arguments,bug code cleanup language,"#### Summary:
+
+The parser is producing a confusing warning for the following ill-formed Stan program:
+
+```
+transformed data {
+ real x = atan2(2 ; 3);
+}
+```
+
+
+#### Current Output:
+
+```
+SYNTAX ERROR, MESSAGE(S) FROM PARSER:
+ error in '/Users/carp/temp2/confusing.stan' at line 2, column 17
+ -------------------------------------------------
+ 1: transformed data {
+ 2: real x = atan2(2 ; 3);
+ ^
+ 3: }
+ -------------------------------------------------
+
+PARSER EXPECTED: ""(""
+
+```
+
+
+#### Expected Output:
+
+Something like ""expected , or )"" pointing before the semicolon.
+
+
+#### Current Version:
+v2.18.0
+",1.0,"fix parser warnings for semicolons in function arguments - #### Summary:
+
+The parser is producing a confusing warning for the following ill-formed Stan program:
+
+```
+transformed data {
+ real x = atan2(2 ; 3);
+}
+```
+
+
+#### Current Output:
+
+```
+SYNTAX ERROR, MESSAGE(S) FROM PARSER:
+ error in '/Users/carp/temp2/confusing.stan' at line 2, column 17
+ -------------------------------------------------
+ 1: transformed data {
+ 2: real x = atan2(2 ; 3);
+ ^
+ 3: }
+ -------------------------------------------------
+
+PARSER EXPECTED: ""(""
+
+```
+
+
+#### Expected Output:
+
+Something like ""expected , or )"" pointing before the semicolon.
+
+
+#### Current Version:
+v2.18.0
+",0,fix parser warnings for semicolons in function arguments summary the parser is producing a confusing warning for the following ill formed stan program transformed data real x current output syntax error message s from parser error in users carp confusing stan at line column transformed data real x parser expected expected output something like expected or pointing before the semicolon current version ,0
+646171,21040005904.0,IssuesEvent,2022-03-31 11:25:46,projectdiscovery/naabu,https://api.github.com/repos/projectdiscovery/naabu,closed,Functional test implementation,Priority: Medium Status: Completed Type: Enhancement,"**Is your feature request related to a problem? Please describe.**
+Feature X can be broken while adding feature Y and go unnoticed.
+
+**Describe the solution you'd like**
+
+Functional test implementation similar to [nuclei](https://github.com/projectdiscovery/nuclei/tree/master/v2/cmd/functional-test) to run pre-defined [testcases.txt](https://github.com/projectdiscovery/nuclei/blob/master/v2/cmd/functional-test/testcases.txt) to compare results between current branch and last released version.",1.0,"Functional test implementation - **Is your feature request related to a problem? Please describe.**
+Feature X can be broken while adding feature Y and go unnoticed.
+
+**Describe the solution you'd like**
+
+Functional test implementation similar to [nuclei](https://github.com/projectdiscovery/nuclei/tree/master/v2/cmd/functional-test) to run pre-defined [testcases.txt](https://github.com/projectdiscovery/nuclei/blob/master/v2/cmd/functional-test/testcases.txt) to compare results between current branch and last released version.",0,functional test implementation is your feature request related to a problem please describe feature x can be broken while adding feature y and go unnoticed describe the solution you d like functional test implementation similar to to run pre defined to compare results between current branch and last released version ,0
+3289,6254682874.0,IssuesEvent,2017-07-14 03:22:10,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Support for setting global variable with `on` and `off`,compatibility help wanted rc3.1,"
+1. What did you expect to see?
+```
+mysql> set global avoid_temporal_upgrade = on;
+Query OK, 0 rows affected, 1 warning (0.00 sec)
+```
+
+2. What did you see instead?
+```
+mysql> set global avoid_temporal_upgrade = on;
+ERROR 1105 (HY000): line 0 column 38 near """" (total length 38)
+```
+",True,"Support for setting global variable with `on` and `off` -
+1. What did you expect to see?
+```
+mysql> set global avoid_temporal_upgrade = on;
+Query OK, 0 rows affected, 1 warning (0.00 sec)
+```
+
+2. What did you see instead?
+```
+mysql> set global avoid_temporal_upgrade = on;
+ERROR 1105 (HY000): line 0 column 38 near """" (total length 38)
+```
+",1,support for setting global variable with on and off what did you expect to see mysql set global avoid temporal upgrade on query ok rows affected warning sec what did you see instead mysql set global avoid temporal upgrade on error line column near total length ,1
+641504,20828421844.0,IssuesEvent,2022-03-19 02:50:06,apache/dolphinscheduler,https://api.github.com/repos/apache/dolphinscheduler,closed,[Bug][UI Next][V1.0.0-Alpha] The workflow status field of the task definition page does not support Chinese.,bug UI priority:middle,"### Search before asking
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-```
-select tidb_version();
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v2.1.0-rc.3-1-geb617c5f9
-Git Commit Hash: eb617c5f9f75c38d75fa848b6732c6071e66ab3e
-Git Branch: master
-UTC Build Time: 2018-09-30 03:35:34
-GoVersion: go version go1.10.3 darwin/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false |
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-1 row in set (0.00 sec)
-```
-",1,error message is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do sql create table t a int select a as b from t group by values b what did you expect to see sql mysql select a as b from t group by values b error expression of select list is not in group by clause and contains nonaggregated column test t a which is not functionally dependent on columns in group by clause this is incompatible with sql mode only full group by what did you see instead column name is lost sql tidb select a as b from t group by values b error expression of select list is not in group by clause and contains nonaggregated column which is not functionally dependent on columns in group by clause this is incompatible with sql mode only full group by what version of tidb are you using tidb server v or run select tidb version on tidb select tidb version tidb version release version rc git commit hash git branch master utc build time goversion go version darwin race enabled false tikv min version alpha check table before drop false row in set sec ,1
-239038,26201190674.0,IssuesEvent,2023-01-03 17:37:19,samq-ghdemo/monorepo-dotnet,https://api.github.com/repos/samq-ghdemo/monorepo-dotnet,closed,dotnetcore-sample-1.0.0: 7 vulnerabilities (highest severity is: 8.8) - autoclosed,security vulnerability," Vulnerable Library - dotnetcore-sample-1.0.0
+- [X] I had searched in the [issues](https://github.com/apache/dolphinscheduler/issues?q=is%3Aissue) and found no similar issues.
-
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/system.security.cryptography.xml/4.4.0/system.security.cryptography.xml.4.4.0.nupkg
*For some transitive vulnerabilities, there is no version of direct dependency with a fix. Check the section ""Details"" below to see if there is a version of transitive dependency where vulnerability is fixed.
+### What you expected to happen
-## Details
+The workflow status field of the task definition page does not support Chinese.
-
+### How to reproduce
- CVE-2018-0787
+Support chinese.
+### Anything else
-### Vulnerable Libraries - microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg, microsoft.aspnetcore.httpoverrides.2.0.0.nupkg
-
+_No response_
+### Version
-### microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
+dev
-
Core components of ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
-
+### Are you willing to submit PR?
-Dependency Hierarchy:
- - dotnetcore-sample-1.0.0 (Root Library)
- - microsoft.aspnetcore.2.0.0.nupkg
- - microsoft.aspnetcore.server.kestrel.2.0.0.nupkg
- - :x: **microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg** (Vulnerable Library)
+- [X] Yes I am willing to submit a PR!
+### Code of Conduct
-### microsoft.aspnetcore.httpoverrides.2.0.0.nupkg
+- [X] I agree to follow this project's [Code of Conduct](https://www.apache.org/foundation/policies/conduct)
+",1.0,"[Bug][UI Next][V1.0.0-Alpha] The workflow status field of the task definition page does not support Chinese. - ### Search before asking
-
ASP.NET Core basic middleware for supporting HTTP method overrides. Includes:
-* X-Forwarded-* header...
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.httpoverrides/2.0.0/microsoft.aspnetcore.httpoverrides.2.0.0.nupkg
-
+- [X] I had searched in the [issues](https://github.com/apache/dolphinscheduler/issues?q=is%3Aissue) and found no similar issues.
-Dependency Hierarchy:
- - dotnetcore-sample-1.0.0 (Root Library)
- - microsoft.aspnetcore.2.0.0.nupkg
- - microsoft.aspnetcore.server.iisintegration.2.0.0.nupkg
- - :x: **microsoft.aspnetcore.httpoverrides.2.0.0.nupkg** (Vulnerable Library)
+### What happened
-
-
-ASP.NET Core 1.0. 1.1, and 2.0 allow an elevation of privilege vulnerability due to how web applications that are created from templates validate web requests, aka ""ASP.NET Core Elevation Of Privilege Vulnerability"".
+### What you expected to happen
-
+dev
-
+### Are you willing to submit PR?
-
+- [X] Yes I am willing to submit a PR!
-
+### Code of Conduct
- WS-2018-0608
+- [X] I agree to follow this project's [Code of Conduct](https://www.apache.org/foundation/policies/conduct)
+",0, the workflow status field of the task definition page does not support chinese search before asking i had searched in the and found no similar issues what happened what you expected to happen the workflow status field of the task definition page does not support chinese how to reproduce support chinese anything else no response version dev are you willing to submit pr yes i am willing to submit a pr code of conduct i agree to follow this project s ,0
+3504,6487208940.0,IssuesEvent,2017-08-20 04:45:34,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,some querys that has `DISTINCT` and `ORDER BY` should be invalid,compatibility enhancement todo,"## 1. What did you do?
+
+```sql
+drop table if exists t;
+create table t(a bigint, b bigint, c bigint);
+insert into t values(1, 2, 1), (1, 2, 2), (1, 3, 1), (1, 3, 2);
+select distinct a, b from t order by c;
+```
+
+To order the result, duplicates must be eliminated first. But to do so, which row should we keep ? This choice influences the retained value of `c`, which in turn influences ordering and makes it arbitrary as well.
+
+In MySQL, a query that has `DISTINCT` and `ORDER BY` is rejected as invalid if any `ORDER BY` expression does not satisfy at least one of these conditions:
+- The expression is equal to one in the select list
+- All columns referenced by the expression and belonging to the query's selected tables are elements of the select list
+
+## 2. What did you expect to see?
+
+```sql
+MySQL > select distinct a, b from t order by c;
+ERROR 3065 (HY000): Expression #1 of ORDER BY clause is not in SELECT list, references column 'test.t.c' which is not in SELECT list; this is incompatible with DISTINCT
+```
+
+## 3. What did you see instead?
+
+```sql
+TiDB > select distinct a, b from t order by c;
++------+------+
+| a | b |
++------+------+
+| 1 | 2 |
+| 1 | 3 |
++------+------+
+2 rows in set (0.00 sec)
+```
+
+```sql
+TiDB > desc select distinct a, b from t order by c;
++---------------+--------------+---------------+------+--------------------------------------------------------------------------------------------------------------+-------+
+| id | parents | children | task | operator info | count |
++---------------+--------------+---------------+------+--------------------------------------------------------------------------------------------------------------+-------+
+| TableScan_7 | HashAgg_6 | | cop | table:t, range:(-inf,+inf), keep order:false | 4 |
+| HashAgg_6 | | TableScan_7 | cop | type:complete, group by:test.t.a, test.t.b, funcs:firstrow(test.t.a), firstrow(test.t.b), firstrow(test.t.c) | 1 |
+| TableReader_9 | HashAgg_8 | | root | data:HashAgg_6 | 1 |
+| HashAgg_8 | Sort_4 | TableReader_9 | root | type:final, group by:, , funcs:firstrow(col_0), firstrow(col_1), firstrow(col_2) | 1 |
+| Sort_4 | Projection_5 | HashAgg_8 | root | test.t.c:asc | 1 |
+| Projection_5 | | Sort_4 | root | test.t.a, test.t.b | 1 |
++---------------+--------------+---------------+------+--------------------------------------------------------------------------------------------------------------+-------+
+6 rows in set (0.00 sec)
+```
+## 4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"some querys that has `DISTINCT` and `ORDER BY` should be invalid - ## 1. What did you do?
+
+```sql
+drop table if exists t;
+create table t(a bigint, b bigint, c bigint);
+insert into t values(1, 2, 1), (1, 2, 2), (1, 3, 1), (1, 3, 2);
+select distinct a, b from t order by c;
+```
+
+To order the result, duplicates must be eliminated first. But to do so, which row should we keep ? This choice influences the retained value of `c`, which in turn influences ordering and makes it arbitrary as well.
+
+In MySQL, a query that has `DISTINCT` and `ORDER BY` is rejected as invalid if any `ORDER BY` expression does not satisfy at least one of these conditions:
+- The expression is equal to one in the select list
+- All columns referenced by the expression and belonging to the query's selected tables are elements of the select list
+
+## 2. What did you expect to see?
+
+```sql
+MySQL > select distinct a, b from t order by c;
+ERROR 3065 (HY000): Expression #1 of ORDER BY clause is not in SELECT list, references column 'test.t.c' which is not in SELECT list; this is incompatible with DISTINCT
+```
+
+## 3. What did you see instead?
+
+```sql
+TiDB > select distinct a, b from t order by c;
++------+------+
+| a | b |
++------+------+
+| 1 | 2 |
+| 1 | 3 |
++------+------+
+2 rows in set (0.00 sec)
+```
+
+```sql
+TiDB > desc select distinct a, b from t order by c;
++---------------+--------------+---------------+------+--------------------------------------------------------------------------------------------------------------+-------+
+| id | parents | children | task | operator info | count |
++---------------+--------------+---------------+------+--------------------------------------------------------------------------------------------------------------+-------+
+| TableScan_7 | HashAgg_6 | | cop | table:t, range:(-inf,+inf), keep order:false | 4 |
+| HashAgg_6 | | TableScan_7 | cop | type:complete, group by:test.t.a, test.t.b, funcs:firstrow(test.t.a), firstrow(test.t.b), firstrow(test.t.c) | 1 |
+| TableReader_9 | HashAgg_8 | | root | data:HashAgg_6 | 1 |
+| HashAgg_8 | Sort_4 | TableReader_9 | root | type:final, group by:, , funcs:firstrow(col_0), firstrow(col_1), firstrow(col_2) | 1 |
+| Sort_4 | Projection_5 | HashAgg_8 | root | test.t.c:asc | 1 |
+| Projection_5 | | Sort_4 | root | test.t.a, test.t.b | 1 |
++---------------+--------------+---------------+------+--------------------------------------------------------------------------------------------------------------+-------+
+6 rows in set (0.00 sec)
+```
+## 4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,some querys that has distinct and order by should be invalid what did you do sql drop table if exists t create table t a bigint b bigint c bigint insert into t values select distinct a b from t order by c to order the result duplicates must be eliminated first but to do so which row should we keep this choice influences the retained value of c which in turn influences ordering and makes it arbitrary as well in mysql a query that has distinct and order by is rejected as invalid if any order by expression does not satisfy at least one of these conditions the expression is equal to one in the select list all columns referenced by the expression and belonging to the query s selected tables are elements of the select list what did you expect to see sql mysql select distinct a b from t order by c error expression of order by clause is not in select list references column test t c which is not in select list this is incompatible with distinct what did you see instead sql tidb select distinct a b from t order by c a b rows in set sec sql tidb desc select distinct a b from t order by c id parents children task operator info count tablescan hashagg cop table t range inf inf keep order false hashagg tablescan cop type complete group by test t a test t b funcs firstrow test t a firstrow test t b firstrow test t c tablereader hashagg root data hashagg hashagg sort tablereader root type final group by funcs firstrow col firstrow col firstrow col sort projection hashagg root test t c asc projection sort root test t a test t b rows in set sec what version of tidb are you using tidb server v ,1
+23344,2658361183.0,IssuesEvent,2015-03-18 15:14:58,IQSS/dataverse,https://api.github.com/repos/IQSS/dataverse,closed,File Download: Downloading tabular data always results in .tab regardless of what is selected.,Component: File Upload & Handling Priority: High Status: QA Type: Bug,"
+When downloading from tabular data menu, whether zip, rdata, original file, always gets .tab",1.0,"File Download: Downloading tabular data always results in .tab regardless of what is selected. -
+When downloading from tabular data menu, whether zip, rdata, original file, always gets .tab",0,file download downloading tabular data always results in tab regardless of what is selected when downloading from tabular data menu whether zip rdata original file always gets tab,0
+825855,31475487233.0,IssuesEvent,2023-08-30 10:23:10,matrixorigin/matrixone,https://api.github.com/repos/matrixorigin/matrixone,opened,[Feature Request]: filling query ,kind/feature source/on-demand priority/p-1,"### Is there an existing issue for the same feature request?
+- [X] I have checked the existing issues.
-### Vulnerable Libraries - microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg, microsoft.aspnetcore.server.kestrel.transport.abstractions.2.0.0.nupkg, microsoft.aspnetcore.server.kestrel.transport.libuv.2.0.0.nupkg
-
+### Is your feature request related to a problem?
+_No response_
-### microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
+### Describe the feature you'd like
-
Core components of ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
-
+fill(expr)
+
+**No filling**: NONE (default filling mode).
+**Value filling**: Filling with a fixed value, where you need to specify the value to fill. For example: FILL(VALUE, 1.23). It is important to note that the final filling value depends on the type of the corresponding column. For example, if the column is of type INT, the filling value will be 1.
+**Previous filling**: Filling with the previous non-NULL value. For example: FILL(PREV).
+**Null filling**: Filling with NULL values. For example: FILL(NULL).
+**Linear filling**: Filling with linear interpolation based on the nearest non-NULL values before and after. For example: FILL(LINEAR).
+**Next filling**: Filling with the next non-NULL value. For example: FILL(NEXT).
-Dependency Hierarchy:
- - dotnetcore-sample-1.0.0 (Root Library)
- - microsoft.aspnetcore.2.0.0.nupkg
- - microsoft.aspnetcore.server.kestrel.2.0.0.nupkg
- - :x: **microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg** (Vulnerable Library)
+### Describe implementation you've considered
+_No response_
-### microsoft.aspnetcore.server.kestrel.transport.abstractions.2.0.0.nupkg
+### Documentation, Adoption, Use Case, Migration Strategy
-
Transport abstractions for the ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.transport.abstractions/2.0.0/microsoft.aspnetcore.server.kestrel.transport.abstractions.2.0.0.nupkg
-
+```Markdown
+Example:
+
+CREATE TABLE temperature (
+ timestamp TIMESTAMP,
+ value FLOAT
+);
+
+INSERT INTO temperature VALUES ('2023-08-29 00:00:00', 25.0);
+INSERT INTO temperature VALUES ('2023-08-29 01:00:00', 27.0);
+INSERT INTO temperature VALUES ('2023-08-29 02:00:00', NULL);
+INSERT INTO temperature VALUES ('2023-08-29 03:00:00', NULL);
+INSERT INTO temperature VALUES ('2023-08-29 04:00:00', 28.0);
+INSERT INTO temperature VALUES ('2023-08-29 05:00:00', 30.0);
+
+SELECT timestamp, FILL(LINEAR) AS value FROM temperature;
+```
-Dependency Hierarchy:
- - dotnetcore-sample-1.0.0 (Root Library)
- - microsoft.aspnetcore.2.0.0.nupkg
- - microsoft.aspnetcore.server.kestrel.2.0.0.nupkg
- - microsoft.aspnetcore.server.kestrel.transport.libuv.2.0.0.nupkg
- - :x: **microsoft.aspnetcore.server.kestrel.transport.abstractions.2.0.0.nupkg** (Vulnerable Library)
+### Additional information
-### microsoft.aspnetcore.server.kestrel.transport.libuv.2.0.0.nupkg
+_No response_",1.0,"[Feature Request]: filling query - ### Is there an existing issue for the same feature request?
-
Libuv transport for the ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.transport.libuv/2.0.0/microsoft.aspnetcore.server.kestrel.transport.libuv.2.0.0.nupkg
-
+- [X] I have checked the existing issues.
-Dependency Hierarchy:
- - dotnetcore-sample-1.0.0 (Root Library)
- - microsoft.aspnetcore.2.0.0.nupkg
- - microsoft.aspnetcore.server.kestrel.2.0.0.nupkg
- - :x: **microsoft.aspnetcore.server.kestrel.transport.libuv.2.0.0.nupkg** (Vulnerable Library)
+### Is your feature request related to a problem?
+_No response_
-
-
+### Describe the feature you'd like
-
+fill(expr)
+
+**No filling**: NONE (default filling mode).
+**Value filling**: Filling with a fixed value, where you need to specify the value to fill. For example: FILL(VALUE, 1.23). It is important to note that the final filling value depends on the type of the corresponding column. For example, if the column is of type INT, the filling value will be 1.
+**Previous filling**: Filling with the previous non-NULL value. For example: FILL(PREV).
+**Null filling**: Filling with NULL values. For example: FILL(NULL).
+**Linear filling**: Filling with linear interpolation based on the nearest non-NULL values before and after. For example: FILL(LINEAR).
+**Next filling**: Filling with the next non-NULL value. For example: FILL(NEXT).
-### Vulnerability Details
-
-
-A vulnerability was discovered in versions 2.x of ASP.NET Core where a specially crafted request can cause excess resource consumption in Kestrel.
+### Describe implementation you've considered
-
+```Markdown
+Example:
+
+CREATE TABLE temperature (
+ timestamp TIMESTAMP,
+ value FLOAT
+);
+
+INSERT INTO temperature VALUES ('2023-08-29 00:00:00', 25.0);
+INSERT INTO temperature VALUES ('2023-08-29 01:00:00', 27.0);
+INSERT INTO temperature VALUES ('2023-08-29 02:00:00', NULL);
+INSERT INTO temperature VALUES ('2023-08-29 03:00:00', NULL);
+INSERT INTO temperature VALUES ('2023-08-29 04:00:00', 28.0);
+INSERT INTO temperature VALUES ('2023-08-29 05:00:00', 30.0);
+
+SELECT timestamp, FILL(LINEAR) AS value FROM temperature;
+```
-Base Score Metrics:
-- Exploitability Metrics:
- - Attack Vector: Network
- - Attack Complexity: Low
- - Privileges Required: None
- - User Interaction: None
- - Scope: Unchanged
-- Impact Metrics:
- - Confidentiality Impact: None
- - Integrity Impact: None
- - Availability Impact: High
-
-For more information on CVSS3 Scores, click here.
-
-
+### Additional information
-### Suggested Fix
-
+_No response_",0, filling query is there an existing issue for the same feature request i have checked the existing issues is your feature request related to a problem no response describe the feature you d like fill expr no filling none default filling mode value filling filling with a fixed value where you need to specify the value to fill for example fill value it is important to note that the final filling value depends on the type of the corresponding column for example if the column is of type int the filling value will be previous filling filling with the previous non null value for example fill prev null filling filling with null values for example fill null linear filling filling with linear interpolation based on the nearest non null values before and after for example fill linear next filling filling with the next non null value for example fill next describe implementation you ve considered no response documentation adoption use case migration strategy markdown example create table temperature timestamp timestamp value float insert into temperature values insert into temperature values insert into temperature values null insert into temperature values null insert into temperature values insert into temperature values select timestamp fill linear as value from temperature additional information no response ,0
+7013,9301980842.0,IssuesEvent,2019-03-24 04:20:05,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,`select constants which have a plus prefix` is not same with MySQL,help wanted type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+In TiDB:
+mysql> select +1000;
++-------+
+| +1000 |
++-------+
+| 1000 |
++-------+
+1 row in set (0.00 sec)
+In MySQL:
+mysql> select +1000;
++------+
+| 1000 |
++------+
+| 1000 |
++------+
+1 row in set (0.00 sec)
+
+
+2. What did you expect to see?
+No plus display before column name.
+
+3. What did you see instead?
+A plus before column name.
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+mysql> select tidb_version();
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-202-g85b1cd7-dirty
+Git Commit Hash: 85b1cd7aa2d21119e39d4cc9a317557aaf7aa13c
+Git Branch: master
+UTC Build Time: 2019-03-12 12:17:58
+GoVersion: go version go1.12 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+",True,"`select constants which have a plus prefix` is not same with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+In TiDB:
+mysql> select +1000;
++-------+
+| +1000 |
++-------+
+| 1000 |
++-------+
+1 row in set (0.00 sec)
+In MySQL:
+mysql> select +1000;
++------+
+| 1000 |
++------+
+| 1000 |
++------+
+1 row in set (0.00 sec)
+
+
+2. What did you expect to see?
+No plus display before column name.
+
+3. What did you see instead?
+A plus before column name.
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+mysql> select tidb_version();
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-202-g85b1cd7-dirty
+Git Commit Hash: 85b1cd7aa2d21119e39d4cc9a317557aaf7aa13c
+Git Branch: master
+UTC Build Time: 2019-03-12 12:17:58
+GoVersion: go version go1.12 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+",1, select constants which have a plus prefix is not same with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error in tidb mysql select row in set sec in mysql mysql select row in set sec what did you expect to see no plus display before column name what did you see instead a plus before column name what version of tidb are you using tidb server v or run select tidb version on tidb mysql select tidb version tidb version release version beta dirty git commit hash git branch master utc build time goversion go version linux race enabled false tikv min version alpha check table before drop false row in set sec ,1
+10287,8872808847.0,IssuesEvent,2019-01-11 16:20:24,terraform-providers/terraform-provider-aws,https://api.github.com/repos/terraform-providers/terraform-provider-aws,closed,Resource aws_emr_cluster doesn't support import,enhancement service/emr,"
+
+### Community Note
+
+* Please vote on this issue by adding a 👍 [reaction](https://blog.github.com/2016-03-10-add-reactions-to-pull-requests-issues-and-comments/) to the original issue to help the community and maintainers prioritize this request
+* Please do not leave ""+1"" or ""me too"" comments, they generate extra noise for issue followers and do not help prioritize the request
+* If you are interested in working on this issue or have submitted a pull request, please leave a comment
+
+
+
+### Description
+We'd like to import our existing EMR clusters into terraform
+
+### New or Affected Resource(s)
+
+* aws_emr_cluster
+
+### Potential Terraform Configuration
+
+terraform import aws_emr_cluster.emr-test-cluster j-XXXXXXXXXXXXX
+
+### References
+
+
+
+* https://www.terraform.io/docs/providers/aws/r/emr_cluster.html
+",1.0,"Resource aws_emr_cluster doesn't support import -
+
+### Community Note
+
+* Please vote on this issue by adding a 👍 [reaction](https://blog.github.com/2016-03-10-add-reactions-to-pull-requests-issues-and-comments/) to the original issue to help the community and maintainers prioritize this request
+* Please do not leave ""+1"" or ""me too"" comments, they generate extra noise for issue followers and do not help prioritize the request
+* If you are interested in working on this issue or have submitted a pull request, please leave a comment
+
+
+
+### Description
+We'd like to import our existing EMR clusters into terraform
+
+### New or Affected Resource(s)
+
+* aws_emr_cluster
+
+### Potential Terraform Configuration
+
+terraform import aws_emr_cluster.emr-test-cluster j-XXXXXXXXXXXXX
+
+### References
+
+
+
+* https://www.terraform.io/docs/providers/aws/r/emr_cluster.html
+",0,resource aws emr cluster doesn t support import community note please vote on this issue by adding a 👍 to the original issue to help the community and maintainers prioritize this request please do not leave or me too comments they generate extra noise for issue followers and do not help prioritize the request if you are interested in working on this issue or have submitted a pull request please leave a comment description we d like to import our existing emr clusters into terraform new or affected resource s aws emr cluster potential terraform configuration terraform import aws emr cluster emr test cluster j xxxxxxxxxxxxx references information about referencing github issues are there any other github issues open or closed or pull requests that should be linked here vendor blog posts or documentation for example ,0
+175215,13540303183.0,IssuesEvent,2020-09-16 14:30:21,microsoft/botframework-sdk,https://api.github.com/repos/microsoft/botframework-sdk,closed,"DCR: As an NLU engineer, I would like to be able to run batch tests scripts against my language models to validate the utterances and entities my bot needs to work get resolved as expected",NLU Testing,"## Issue
+The natural language understanding models used by a bot evolve independently of the underlying code, the LUIS portal provides a batch testing UI but it is not scriptable and can't be used in continuous integration or continuous delivery.
+
+## Proposed change
+We need a batch testing API that can be invoked and asserted from the Azure CLI to ensure the key utterances and entities are still resolved after the model changes.
+
+The API should take a json file that follows the [batch testing format](https://docs.microsoft.com/en-us/azure/cognitive-services/luis/luis-concept-batch-test#batch-file-format) define by LUIS and output the results in a document format that can be parsed and asserted through automated tools.",1.0,"DCR: As an NLU engineer, I would like to be able to run batch tests scripts against my language models to validate the utterances and entities my bot needs to work get resolved as expected - ## Issue
+The natural language understanding models used by a bot evolve independently of the underlying code, the LUIS portal provides a batch testing UI but it is not scriptable and can't be used in continuous integration or continuous delivery.
+
+## Proposed change
+We need a batch testing API that can be invoked and asserted from the Azure CLI to ensure the key utterances and entities are still resolved after the model changes.
+
+The API should take a json file that follows the [batch testing format](https://docs.microsoft.com/en-us/azure/cognitive-services/luis/luis-concept-batch-test#batch-file-format) define by LUIS and output the results in a document format that can be parsed and asserted through automated tools.",0,dcr as an nlu engineer i would like to be able to run batch tests scripts against my language models to validate the utterances and entities my bot needs to work get resolved as expected issue the natural language understanding models used by a bot evolve independently of the underlying code the luis portal provides a batch testing ui but it is not scriptable and can t be used in continuous integration or continuous delivery proposed change we need a batch testing api that can be invoked and asserted from the azure cli to ensure the key utterances and entities are still resolved after the model changes the api should take a json file that follows the define by luis and output the results in a document format that can be parsed and asserted through automated tools ,0
+7145,9430605819.0,IssuesEvent,2019-04-12 09:25:49,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,json_key is not same with MySQL,type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```sql
+select json_keys(NULL);
+select json_keys(NULL, '$.b');
+select json_keys(NULL, NULL);
+select json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', '$.a');
+select json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', NULL);
+```
+
+2. What did you expect to see?
+## In MySQL
+```SQL
+mysql> select version();
++-------------------------+
+| version() |
++-------------------------+
+| 5.7.25-0ubuntu0.18.04.2 |
++-------------------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys(NULL);
++-----------------+
+| json_keys(NULL) |
++-----------------+
+| NULL |
++-----------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys(NULL, '$.b');
++------------------------+
+| json_keys(NULL, '$.b') |
++------------------------+
+| NULL |
++------------------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys(NULL, NULL);
++-----------------------+
+| json_keys(NULL, NULL) |
++-----------------------+
+| NULL |
++-----------------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', '$.a');
++---------------------------------------------------------+
+| json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', '$.a') |
++---------------------------------------------------------+
+| NULL |
++---------------------------------------------------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', NULL);
++--------------------------------------------------------+
+| json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', NULL) |
++--------------------------------------------------------+
+| NULL |
++--------------------------------------------------------+
+1 row in set (0.00 sec)
+
+mysql>
+```
+
+
+3. What did you see instead?
+## In TiDB
+```SQL
+
+mysql> select json_keys(NULL);
++-----------------+
+| json_keys(NULL) |
++-----------------+
+| NULL |
++-----------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys(NULL, '$.b');
++------------------------+
+| json_keys(NULL, '$.b') |
++------------------------+
+| NULL |
++------------------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys(NULL, NULL);
++-----------------------+
+| json_keys(NULL, NULL) |
++-----------------------+
+| NULL |
++-----------------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', '$.a');
+ERROR 3146 (22032): Invalid data type for JSON data
+mysql> select json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', NULL);
++--------------------------------------------------------+
+| json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', NULL) |
++--------------------------------------------------------+
+| NULL |
++--------------------------------------------------------+
+1 row in set (0.01 sec)
+
+mysql> select tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v3.0.0-beta-321-gc6a757b24
+Git Commit Hash: c6a757b2435965a72ada9d61ea8b7a367bd89b5f
+Git Branch: master
+UTC Build Time: 2019-04-02 02:38:04
+GoVersion: go version go1.12.1 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false
+1 row in set (0.00 sec)
+
+mysql>
+```",True,"json_key is not same with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```sql
+select json_keys(NULL);
+select json_keys(NULL, '$.b');
+select json_keys(NULL, NULL);
+select json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', '$.a');
+select json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', NULL);
+```
+
+2. What did you expect to see?
+## In MySQL
+```SQL
+mysql> select version();
++-------------------------+
+| version() |
++-------------------------+
+| 5.7.25-0ubuntu0.18.04.2 |
++-------------------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys(NULL);
++-----------------+
+| json_keys(NULL) |
++-----------------+
+| NULL |
++-----------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys(NULL, '$.b');
++------------------------+
+| json_keys(NULL, '$.b') |
++------------------------+
+| NULL |
++------------------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys(NULL, NULL);
++-----------------------+
+| json_keys(NULL, NULL) |
++-----------------------+
+| NULL |
++-----------------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', '$.a');
++---------------------------------------------------------+
+| json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', '$.a') |
++---------------------------------------------------------+
+| NULL |
++---------------------------------------------------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', NULL);
++--------------------------------------------------------+
+| json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', NULL) |
++--------------------------------------------------------+
+| NULL |
++--------------------------------------------------------+
+1 row in set (0.00 sec)
+
+mysql>
+```
+
+
+3. What did you see instead?
+## In TiDB
+```SQL
+
+mysql> select json_keys(NULL);
++-----------------+
+| json_keys(NULL) |
++-----------------+
+| NULL |
++-----------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys(NULL, '$.b');
++------------------------+
+| json_keys(NULL, '$.b') |
++------------------------+
+| NULL |
++------------------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys(NULL, NULL);
++-----------------------+
+| json_keys(NULL, NULL) |
++-----------------------+
+| NULL |
++-----------------------+
+1 row in set (0.00 sec)
+
+mysql> select json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', '$.a');
+ERROR 3146 (22032): Invalid data type for JSON data
+mysql> select json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', NULL);
++--------------------------------------------------------+
+| json_keys('{""a"": 1, ""b"": {""e"": ""foo"", ""b"": 3}}', NULL) |
++--------------------------------------------------------+
+| NULL |
++--------------------------------------------------------+
+1 row in set (0.01 sec)
+
+mysql> select tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v3.0.0-beta-321-gc6a757b24
+Git Commit Hash: c6a757b2435965a72ada9d61ea8b7a367bd89b5f
+Git Branch: master
+UTC Build Time: 2019-04-02 02:38:04
+GoVersion: go version go1.12.1 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false
+1 row in set (0.00 sec)
+
+mysql>
+```",1,json key is not same with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql select json keys null select json keys null b select json keys null null select json keys a b e foo b a select json keys a b e foo b null what did you expect to see in mysql sql mysql select version version row in set sec mysql select json keys null json keys null null row in set sec mysql select json keys null b json keys null b null row in set sec mysql select json keys null null json keys null null null row in set sec mysql select json keys a b e foo b a json keys a b e foo b a null row in set sec mysql select json keys a b e foo b null json keys a b e foo b null null row in set sec mysql what did you see instead in tidb sql mysql select json keys null json keys null null row in set sec mysql select json keys null b json keys null b null row in set sec mysql select json keys null null json keys null null null row in set sec mysql select json keys a b e foo b a error invalid data type for json data mysql select json keys a b e foo b null json keys a b e foo b null null row in set sec mysql select tidb version g row tidb version release version beta git commit hash git branch master utc build time goversion go version linux race enabled false tikv min version alpha check table before drop false row in set sec mysql ,1
+13869,16593796542.0,IssuesEvent,2021-06-01 10:59:39,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Support column type conversion between non-varchar to varchar,compatibility-breaker sig/sql-infra type/feature-request,"## Development Task
+
+We forbid changing column type conversion between non-varchar to varchar in master/v5.0.x(PR: #23688). Before #23688, this feature(conversion between char to varchar) was originally supported by modifying only the column structure without modifying the data.
+However, it was later found that some scenarios(these cases are executed on the branch which before forbidding this feature) could not be handled in this way, such as:
+```
+tidb> create table t(a int, b varchar(10), primary key(a, b));
+Query OK, 0 rows affected (0.01 sec)
+tidb> insert into t values (1, ""aaa "");
+Query OK, 1 row affected (0.00 sec)
+tidb> alter table t change column b b char(10);
+Query OK, 0 rows affected (0.01 sec)
+tidb> Create table t1 like t;
+Query OK, 0 rows affected (0.00 sec)
+tidb> insert into t1 values (1, ""aaa "");
+Query OK, 1 row affected (0.01 sec)
+
+tidb> select * from t;
++---+--------+
+| a | b |
++---+--------+
+| 1 | aaa |
++---+--------+
+1 row in set (0.00 sec)
+tidb> select * from t1;
++---+-----+
+| a | b |
++---+-----+
+| 1 | aaa |
++---+-----+
+1 row in set (0.00 sec)
+
+tidb> admin check table t;
+Query OK, 0 rows affected (0.01 sec)
+```
+
+Currently, we are working to support changing column types (not only changing column properties but also changing how column data is handled). This feature can also be supported by the way to modify the data which need to set`SET GLOBAL TIDB_ENABLE_CHANGE_COLUMN_TYPE = 1`.
+
+
+## Materials
+[old way to column type change](https://github.com/pingcap/tidb/blob/master/docs/design/2018-10-08-online-DDL.md#modify-column-operation)
+[new way to to column type change proposal](https://github.com/pingcap/tidb/blob/master/docs/design/2020-07-07-change-column-types.md)
+Related to issue: #23624, #23852.",True,"Support column type conversion between non-varchar to varchar - ## Development Task
+
+We forbid changing column type conversion between non-varchar to varchar in master/v5.0.x(PR: #23688). Before #23688, this feature(conversion between char to varchar) was originally supported by modifying only the column structure without modifying the data.
+However, it was later found that some scenarios(these cases are executed on the branch which before forbidding this feature) could not be handled in this way, such as:
+```
+tidb> create table t(a int, b varchar(10), primary key(a, b));
+Query OK, 0 rows affected (0.01 sec)
+tidb> insert into t values (1, ""aaa "");
+Query OK, 1 row affected (0.00 sec)
+tidb> alter table t change column b b char(10);
+Query OK, 0 rows affected (0.01 sec)
+tidb> Create table t1 like t;
+Query OK, 0 rows affected (0.00 sec)
+tidb> insert into t1 values (1, ""aaa "");
+Query OK, 1 row affected (0.01 sec)
+
+tidb> select * from t;
++---+--------+
+| a | b |
++---+--------+
+| 1 | aaa |
++---+--------+
+1 row in set (0.00 sec)
+tidb> select * from t1;
++---+-----+
+| a | b |
++---+-----+
+| 1 | aaa |
++---+-----+
+1 row in set (0.00 sec)
+
+tidb> admin check table t;
+Query OK, 0 rows affected (0.01 sec)
+```
+
+Currently, we are working to support changing column types (not only changing column properties but also changing how column data is handled). This feature can also be supported by the way to modify the data which need to set`SET GLOBAL TIDB_ENABLE_CHANGE_COLUMN_TYPE = 1`.
+
+
+## Materials
+[old way to column type change](https://github.com/pingcap/tidb/blob/master/docs/design/2018-10-08-online-DDL.md#modify-column-operation)
+[new way to to column type change proposal](https://github.com/pingcap/tidb/blob/master/docs/design/2020-07-07-change-column-types.md)
+Related to issue: #23624, #23852.",1,support column type conversion between non varchar to varchar development task we forbid changing column type conversion between non varchar to varchar in master x pr before this feature conversion between char to varchar was originally supported by modifying only the column structure without modifying the data however it was later found that some scenarios these cases are executed on the branch which before forbidding this feature could not be handled in this way such as tidb create table t a int b varchar primary key a b query ok rows affected sec tidb insert into t values aaa query ok row affected sec tidb alter table t change column b b char query ok rows affected sec tidb create table like t query ok rows affected sec tidb insert into values aaa query ok row affected sec tidb select from t a b aaa row in set sec tidb select from a b aaa row in set sec tidb admin check table t query ok rows affected sec currently we are working to support changing column types not only changing column properties but also changing how column data is handled this feature can also be supported by the way to modify the data which need to set set global tidb enable change column type materials related to issue ,1
+7329,9575840046.0,IssuesEvent,2019-05-07 07:37:23,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,addition between `time` and `interval` is not compatible with Mysql,for new contributors help wanted type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+SELECT time('12:34:56') + INTERVAL 1 SECOND;
+```
+
+2. What did you expect to see?
+In Mysql
+```
+mysql> select time('12:34:56') + interval 1 second;
++--------------------------------------+
+| time('12:34:56') + interval 1 second |
++--------------------------------------+
+| 12:34:57 |
++--------------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+In TiDB
+```
+mysql> select time('12:34:56') + interval 1 second;
++--------------------------------------+
+| time('12:34:56') + interval 1 second |
++--------------------------------------+
+| 2019-04-30 12:34:57 |
++--------------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```tidb_version(): Release Version: v3.0.0-beta-463-g36bb1ae89```
+
+
+In mysql's document:
+
+`time('12:34:56') + interval 1 second` is same as `date_add(time('12:34:56'), interval 1 second)`
+
+And
+
+> The date argument specifies the starting date or datetime value. expr is an expression specifying the interval value to be added or subtracted from the starting date.",True,"addition between `time` and `interval` is not compatible with Mysql - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+SELECT time('12:34:56') + INTERVAL 1 SECOND;
+```
+
+2. What did you expect to see?
+In Mysql
+```
+mysql> select time('12:34:56') + interval 1 second;
++--------------------------------------+
+| time('12:34:56') + interval 1 second |
++--------------------------------------+
+| 12:34:57 |
++--------------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+In TiDB
+```
+mysql> select time('12:34:56') + interval 1 second;
++--------------------------------------+
+| time('12:34:56') + interval 1 second |
++--------------------------------------+
+| 2019-04-30 12:34:57 |
++--------------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```tidb_version(): Release Version: v3.0.0-beta-463-g36bb1ae89```
+
+
+In mysql's document:
+
+`time('12:34:56') + interval 1 second` is same as `date_add(time('12:34:56'), interval 1 second)`
+
+And
+
+> The date argument specifies the starting date or datetime value. expr is an expression specifying the interval value to be added or subtracted from the starting date.",1,addition between time and interval is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql select time interval second what did you expect to see in mysql mysql select time interval second time interval second row in set sec what did you see instead in tidb mysql select time interval second time interval second row in set sec what version of tidb are you using tidb server v or run select tidb version on tidb tidb version release version beta in mysql s document time interval second is same as date add time interval second and the date argument specifies the starting date or datetime value expr is an expression specifying the interval value to be added or subtracted from the starting date ,1
+611074,18944249431.0,IssuesEvent,2021-11-18 08:24:55,metabase/metabase,https://api.github.com/repos/metabase/metabase,closed,Allow to make scatter plots with categorical feature for y axis,Priority:P3 Type:New Feature Visualization/Charts,"Unfortunately when you want to use the metabase scatter plot for visualization it only accepts numerical data for y axis.
+
+Suppose I want a 2-d plot which x and y axis are my two categorical features and the size of bubble for the number of occurrences.
+
+It is a very common plot but metabase does not support it. You can choose your x axis from one of your categorical columns but y axis must be numerical which is not the case in most of scatter plot usage scenarios.
+
+:arrow_down: Please click the :+1: reaction instead of leaving a `+1` or `update?` comment",1.0,"Allow to make scatter plots with categorical feature for y axis - Unfortunately when you want to use the metabase scatter plot for visualization it only accepts numerical data for y axis.
+
+Suppose I want a 2-d plot which x and y axis are my two categorical features and the size of bubble for the number of occurrences.
+
+It is a very common plot but metabase does not support it. You can choose your x axis from one of your categorical columns but y axis must be numerical which is not the case in most of scatter plot usage scenarios.
+
+:arrow_down: Please click the :+1: reaction instead of leaving a `+1` or `update?` comment",0,allow to make scatter plots with categorical feature for y axis unfortunately when you want to use the metabase scatter plot for visualization it only accepts numerical data for y axis suppose i want a d plot which x and y axis are my two categorical features and the size of bubble for the number of occurrences it is a very common plot but metabase does not support it you can choose your x axis from one of your categorical columns but y axis must be numerical which is not the case in most of scatter plot usage scenarios arrow down please click the reaction instead of leaving a or update comment,0
+9812,8180821244.0,IssuesEvent,2018-08-28 20:42:25,grails/grails-core,https://api.github.com/repos/grails/grails-core,closed,Certificate at https://repo.grails.org has expired ,In Progress Infrastructure,"The certificate at https://repo.grails.org has expired and is failing our builds.
+
+",1.0,"Certificate at https://repo.grails.org has expired - The certificate at https://repo.grails.org has expired and is failing our builds.
+
+",0,certificate at has expired the certificate at has expired and is failing our builds img width alt screen shot at pm src ,0
+8080,10208742730.0,IssuesEvent,2019-08-14 10:54:16,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,JDBC to TiDB useCursorFetch error...,component/mysql-protocol type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+the jdbc url is :
+jdbc:mysql://xxx?serverTimezone=Asia/Shanghai&max_allowed_packet=-1&autoReconnect=true&useUnicode=true&characterEncoding=utf8&useSSL=true&useCursorFetch=true&defaultFetchSize=10000
+
+
+org.springframework.jdbc.UncategorizedSQLException: StatementCallback; uncategorized SQLException for SQL [select max(marstime) from xxx.Account]; SQL state [HY000]; error code [1105]; ERROR 1105 (HY000): unsupported flag 1; nested exception is java.sql.SQLException: ERROR 1105 (HY000): unsupported flag 1
+ at org.springframework.jdbc.support.AbstractFallbackSQLExceptionTranslator.translate(AbstractFallbackSQLExceptionTranslator.java:89)
+ at org.springframework.jdbc.support.AbstractFallbackSQLExceptionTranslator.translate(AbstractFallbackSQLExceptionTranslator.java:81)
+ at org.springframework.jdbc.support.AbstractFallbackSQLExceptionTranslator.translate(AbstractFallbackSQLExceptionTranslator.java:81)
+ at org.springframework.jdbc.core.JdbcTemplate.translateException(JdbcTemplate.java:1414)
+ at org.springframework.jdbc.core.JdbcTemplate.execute(JdbcTemplate.java:388)
+ at org.springframework.jdbc.core.JdbcTemplate.query(JdbcTemplate.java:452)
+ at org.springframework.jdbc.core.JdbcTemplate.query(JdbcTemplate.java:462)
+ at org.springframework.jdbc.core.JdbcTemplate.queryForObject(JdbcTemplate.java:473)
+ at org.springframework.jdbc.core.JdbcTemplate.queryForObject(JdbcTemplate.java:480)
+ at com.netease.mars.source.AccountSource.run(AccountSource.java:106)
+ at org.apache.flink.streaming.api.operators.StreamSource.run(StreamSource.java:94)
+ at org.apache.flink.streaming.api.operators.StreamSource.run(StreamSource.java:58)
+ at org.apache.flink.streaming.runtime.tasks.SourceStreamTask.run(SourceStreamTask.java:99)
+ at org.apache.flink.streaming.runtime.tasks.StoppableSourceStreamTask.run(StoppableSourceStreamTask.java:45)
+ at org.apache.flink.streaming.runtime.tasks.StreamTask.invoke(StreamTask.java:300)
+ at org.apache.flink.runtime.taskmanager.Task.run(Task.java:704)
+ at java.lang.Thread.run(Thread.java:748)
+Caused by: java.sql.SQLException: ERROR 1105 (HY000): unsupported flag 1
+ at com.mysql.cj.jdbc.exceptions.SQLError.createSQLException(SQLError.java:129)
+ at com.mysql.cj.jdbc.exceptions.SQLError.createSQLException(SQLError.java:97)
+ at com.mysql.cj.jdbc.exceptions.SQLExceptionsMapping.translateException(SQLExceptionsMapping.java:122)
+ at com.mysql.cj.jdbc.ServerPreparedStatement.serverExecute(ServerPreparedStatement.java:633)
+ at com.mysql.cj.jdbc.ServerPreparedStatement.executeInternal(ServerPreparedStatement.java:414)
+ at com.mysql.cj.jdbc.ClientPreparedStatement.execute(ClientPreparedStatement.java:392)
+ at com.mysql.cj.jdbc.StatementImpl.createResultSetUsingServerFetch(StatementImpl.java:582)
+ at com.mysql.cj.jdbc.StatementImpl.executeQuery(StatementImpl.java:1158)
+ at com.alibaba.druid.pool.DruidPooledStatement.executeQuery(DruidPooledStatement.java:230)
+ at org.springframework.jdbc.core.JdbcTemplate$1QueryStatementCallback.doInStatement(JdbcTemplate.java:439)
+ at org.springframework.jdbc.core.JdbcTemplate.execute(JdbcTemplate.java:376)
+
+
+2. What did you expect to see?
+
+
+
+3. What did you see instead?
+
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+
+mysql> select tidb_version();
++--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v2.0.11
+Git Commit Hash: 83889a5d821f40412be1af2ad2f2393737f517fd
+Git Branch: release-2.0
+UTC Build Time: 2019-01-03 09:27:12
+GoVersion: go version go1.11.2 linux/amd64
+TiKV Min Version: 2.0.0-rc.4.1
+",True,"JDBC to TiDB useCursorFetch error... - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+the jdbc url is :
+jdbc:mysql://xxx?serverTimezone=Asia/Shanghai&max_allowed_packet=-1&autoReconnect=true&useUnicode=true&characterEncoding=utf8&useSSL=true&useCursorFetch=true&defaultFetchSize=10000
+
+
+org.springframework.jdbc.UncategorizedSQLException: StatementCallback; uncategorized SQLException for SQL [select max(marstime) from xxx.Account]; SQL state [HY000]; error code [1105]; ERROR 1105 (HY000): unsupported flag 1; nested exception is java.sql.SQLException: ERROR 1105 (HY000): unsupported flag 1
+ at org.springframework.jdbc.support.AbstractFallbackSQLExceptionTranslator.translate(AbstractFallbackSQLExceptionTranslator.java:89)
+ at org.springframework.jdbc.support.AbstractFallbackSQLExceptionTranslator.translate(AbstractFallbackSQLExceptionTranslator.java:81)
+ at org.springframework.jdbc.support.AbstractFallbackSQLExceptionTranslator.translate(AbstractFallbackSQLExceptionTranslator.java:81)
+ at org.springframework.jdbc.core.JdbcTemplate.translateException(JdbcTemplate.java:1414)
+ at org.springframework.jdbc.core.JdbcTemplate.execute(JdbcTemplate.java:388)
+ at org.springframework.jdbc.core.JdbcTemplate.query(JdbcTemplate.java:452)
+ at org.springframework.jdbc.core.JdbcTemplate.query(JdbcTemplate.java:462)
+ at org.springframework.jdbc.core.JdbcTemplate.queryForObject(JdbcTemplate.java:473)
+ at org.springframework.jdbc.core.JdbcTemplate.queryForObject(JdbcTemplate.java:480)
+ at com.netease.mars.source.AccountSource.run(AccountSource.java:106)
+ at org.apache.flink.streaming.api.operators.StreamSource.run(StreamSource.java:94)
+ at org.apache.flink.streaming.api.operators.StreamSource.run(StreamSource.java:58)
+ at org.apache.flink.streaming.runtime.tasks.SourceStreamTask.run(SourceStreamTask.java:99)
+ at org.apache.flink.streaming.runtime.tasks.StoppableSourceStreamTask.run(StoppableSourceStreamTask.java:45)
+ at org.apache.flink.streaming.runtime.tasks.StreamTask.invoke(StreamTask.java:300)
+ at org.apache.flink.runtime.taskmanager.Task.run(Task.java:704)
+ at java.lang.Thread.run(Thread.java:748)
+Caused by: java.sql.SQLException: ERROR 1105 (HY000): unsupported flag 1
+ at com.mysql.cj.jdbc.exceptions.SQLError.createSQLException(SQLError.java:129)
+ at com.mysql.cj.jdbc.exceptions.SQLError.createSQLException(SQLError.java:97)
+ at com.mysql.cj.jdbc.exceptions.SQLExceptionsMapping.translateException(SQLExceptionsMapping.java:122)
+ at com.mysql.cj.jdbc.ServerPreparedStatement.serverExecute(ServerPreparedStatement.java:633)
+ at com.mysql.cj.jdbc.ServerPreparedStatement.executeInternal(ServerPreparedStatement.java:414)
+ at com.mysql.cj.jdbc.ClientPreparedStatement.execute(ClientPreparedStatement.java:392)
+ at com.mysql.cj.jdbc.StatementImpl.createResultSetUsingServerFetch(StatementImpl.java:582)
+ at com.mysql.cj.jdbc.StatementImpl.executeQuery(StatementImpl.java:1158)
+ at com.alibaba.druid.pool.DruidPooledStatement.executeQuery(DruidPooledStatement.java:230)
+ at org.springframework.jdbc.core.JdbcTemplate$1QueryStatementCallback.doInStatement(JdbcTemplate.java:439)
+ at org.springframework.jdbc.core.JdbcTemplate.execute(JdbcTemplate.java:376)
+
+
+2. What did you expect to see?
+
+
+
+3. What did you see instead?
+
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+
+mysql> select tidb_version();
++--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v2.0.11
+Git Commit Hash: 83889a5d821f40412be1af2ad2f2393737f517fd
+Git Branch: release-2.0
+UTC Build Time: 2019-01-03 09:27:12
+GoVersion: go version go1.11.2 linux/amd64
+TiKV Min Version: 2.0.0-rc.4.1
+",1,jdbc to tidb usecursorfetch error bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error the jdbc url is : jdbc mysql xxx servertimezone asia shanghai max allowed packet autoreconnect true useunicode true characterencoding usessl true usecursorfetch true defaultfetchsize org springframework jdbc uncategorizedsqlexception statementcallback uncategorized sqlexception for sql sql state error code error unsupported flag nested exception is java sql sqlexception error unsupported flag at org springframework jdbc support abstractfallbacksqlexceptiontranslator translate abstractfallbacksqlexceptiontranslator java at org springframework jdbc support abstractfallbacksqlexceptiontranslator translate abstractfallbacksqlexceptiontranslator java at org springframework jdbc support abstractfallbacksqlexceptiontranslator translate abstractfallbacksqlexceptiontranslator java at org springframework jdbc core jdbctemplate translateexception jdbctemplate java at org springframework jdbc core jdbctemplate execute jdbctemplate java at org springframework jdbc core jdbctemplate query jdbctemplate java at org springframework jdbc core jdbctemplate query jdbctemplate java at org springframework jdbc core jdbctemplate queryforobject jdbctemplate java at org springframework jdbc core jdbctemplate queryforobject jdbctemplate java at com netease mars source accountsource run accountsource java at org apache flink streaming api operators streamsource run streamsource java at org apache flink streaming api operators streamsource run streamsource java at org apache flink streaming runtime tasks sourcestreamtask run sourcestreamtask java at org apache flink streaming runtime tasks stoppablesourcestreamtask run stoppablesourcestreamtask java at org apache flink streaming runtime tasks streamtask invoke streamtask java at org apache flink runtime taskmanager task run task java at java lang thread run thread java caused by java sql sqlexception error unsupported flag at com mysql cj jdbc exceptions sqlerror createsqlexception sqlerror java at com mysql cj jdbc exceptions sqlerror createsqlexception sqlerror java at com mysql cj jdbc exceptions sqlexceptionsmapping translateexception sqlexceptionsmapping java at com mysql cj jdbc serverpreparedstatement serverexecute serverpreparedstatement java at com mysql cj jdbc serverpreparedstatement executeinternal serverpreparedstatement java at com mysql cj jdbc clientpreparedstatement execute clientpreparedstatement java at com mysql cj jdbc statementimpl createresultsetusingserverfetch statementimpl java at com mysql cj jdbc statementimpl executequery statementimpl java at com alibaba druid pool druidpooledstatement executequery druidpooledstatement java at org springframework jdbc core jdbctemplate doinstatement jdbctemplate java at org springframework jdbc core jdbctemplate execute jdbctemplate java what did you expect to see what did you see instead what version of tidb are you using tidb server v or run select tidb version on tidb mysql select tidb version tidb version release version git commit hash git branch release utc build time goversion go version linux tikv min version rc ,1
+17606,3012747759.0,IssuesEvent,2015-07-29 02:09:39,yawlfoundation/yawl,https://api.github.com/repos/yawlfoundation/yawl,closed,[CLOSED] Resourcing information to be checked by editor,auto-migrated Milestone-Release2.0 Priority-High Type-Defect," **Issue by [GoogleCodeExporter](https://github.com/GoogleCodeExporter)**
+_Monday Jul 27, 2015 at 03:20 GMT_
+_Originally opened as https://github.com/adamsmj/yawl/issues/9_
-
+----
-
+```
+The editor should check whether the resourcing information that is
+specified for a certain specification is still in line with the latest in
+the resourcing database (e.g. suppose a role/participant is used that has
+been deleted in the mean time).
-
+
+```
-
+Original issue reported on code.google.com by `arthurte...@gmail.com` on 18 Jul 2008 at 4:52
+",1.0,"[CLOSED] Resourcing information to be checked by editor - **Issue by [GoogleCodeExporter](https://github.com/GoogleCodeExporter)**
+_Monday Jul 27, 2015 at 03:20 GMT_
+_Originally opened as https://github.com/adamsmj/yawl/issues/9_
- CVE-2018-0808
+----
+```
+The editor should check whether the resourcing information that is
+specified for a certain specification is still in line with the latest in
+the resourcing database (e.g. suppose a role/participant is used that has
+been deleted in the mean time).
-### Vulnerable Libraries - microsoft.aspnetcore.server.iisintegration.2.0.0.nupkg, microsoft.aspnetcore.hosting.2.0.0.nupkg
-
+
+```
+Original issue reported on code.google.com by `arthurte...@gmail.com` on 18 Jul 2008 at 4:52
+",0, resourcing information to be checked by editor issue by monday jul at gmt originally opened as the editor should check whether the resourcing information that is specified for a certain specification is still in line with the latest in the resourcing database e g suppose a role participant is used that has been deleted in the mean time original issue reported on code google com by arthurte gmail com on jul at ,0
+305394,26387066255.0,IssuesEvent,2023-01-12 13:06:52,rhinstaller/kickstart-tests,https://api.github.com/repos/rhinstaller/kickstart-tests,closed,repo-include failing on rhel8 and rhel9: *** wrong version of package-1 was installed,disabled test,"repo-include test is failing on rhel8 and rhel9 scenarios:
+```
+stdout:
+*** wrong version of package-1 was installed
+*** unable to find marker for package-1
+
+2022-02-17 01:22:42,172 INFO: RESULT:repo-include:7f8a0daed3b6:FAILED:Validation failed with return code 1
+```
+[kstest.log](https://github.com/rhinstaller/kickstart-tests/files/8086557/kstest.log)
+[virt-install.log](https://github.com/rhinstaller/kickstart-tests/files/8086559/virt-install.log)
+",1.0,"repo-include failing on rhel8 and rhel9: *** wrong version of package-1 was installed - repo-include test is failing on rhel8 and rhel9 scenarios:
+```
+stdout:
+*** wrong version of package-1 was installed
+*** unable to find marker for package-1
+
+2022-02-17 01:22:42,172 INFO: RESULT:repo-include:7f8a0daed3b6:FAILED:Validation failed with return code 1
+```
+[kstest.log](https://github.com/rhinstaller/kickstart-tests/files/8086557/kstest.log)
+[virt-install.log](https://github.com/rhinstaller/kickstart-tests/files/8086559/virt-install.log)
+",0,repo include failing on and wrong version of package was installed repo include test is failing on and scenarios stdout wrong version of package was installed unable to find marker for package info result repo include failed validation failed with return code ,0
+558234,16528944914.0,IssuesEvent,2021-05-27 01:31:47,eclipse-ee4j/glassfish,https://api.github.com/repos/eclipse-ee4j/glassfish,closed,Provide default value for all attributes of the config bean without requiring the instance be created first.,Component: rest-interface ERR: Assignee Priority: Major Stale Type: New Feature,"This is related to #20192.
+REST should be able to provide the default value just by given the ConfigBean type, eg. jdbc-resource, thread-pool, virtual-server etc.
+But currently unless this attribute is one of the create command param, it cannot do that.
+The limitation is that not all default value is available unless the instance is created first.
-### microsoft.aspnetcore.server.iisintegration.2.0.0.nupkg
+Want to request REST to provide a way to give all the default value of any attributes without requiring:
+1\. the attribute be one of the params for create command
+2\. the resource has to be created first to be able to get those default value.
+#### Affected Versions
+[4.0_dev]",1.0,"Provide default value for all attributes of the config bean without requiring the instance be created first. - This is related to #20192.
+REST should be able to provide the default value just by given the ConfigBean type, eg. jdbc-resource, thread-pool, virtual-server etc.
+But currently unless this attribute is one of the create command param, it cannot do that.
+The limitation is that not all default value is available unless the instance is created first.
-
ASP.NET Core components for working with the IIS AspNetCoreModule.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.iisintegration/2.0.0/microsoft.aspnetcore.server.iisintegration.2.0.0.nupkg
-
+Want to request REST to provide a way to give all the default value of any attributes without requiring:
+1\. the attribute be one of the params for create command
+2\. the resource has to be created first to be able to get those default value.
+#### Affected Versions
+[4.0_dev]",0,provide default value for all attributes of the config bean without requiring the instance be created first this is related to rest should be able to provide the default value just by given the configbean type eg jdbc resource thread pool virtual server etc but currently unless this attribute is one of the create command param it cannot do that the limitation is that not all default value is available unless the instance is created first want to request rest to provide a way to give all the default value of any attributes without requiring the attribute be one of the params for create command the resource has to be created first to be able to get those default value affected versions ,0
+203256,15359239791.0,IssuesEvent,2021-03-01 15:38:44,hashgraph/hedera-mirror-node,https://api.github.com/repos/hashgraph/hedera-mirror-node,opened,RecordFileParserPerformanceTest times out in CircleCi,P3 bug test,"
+
+**Detailed Description**
+https://app.circleci.com/pipelines/github/hashgraph/hedera-mirror-node/6248/workflows/c52d402b-7bf3-4b49-b386-91ad18116820/jobs/17965/steps
+
+```
+2021-03-01T09:23:28.771-0600 INFO main c.h.m.i.p.r.RecordFileParserPerformanceTest No active profile set, falling back to default profiles: default
+2021-03-01T09:23:32.694-0600 INFO main c.h.m.i.c.MetricsConfiguration Collecting table metrics: []
+2021-03-01T09:23:32.738-0600 INFO main c.h.m.i.c.CredentialsProviderConfiguration Setting up S3 async client using AWS Default Credentials Provider
+2021-03-01T09:23:33.044-0600 INFO main o.f.c.i.c.DbMigrate Current version of schema ""public"": << Empty Schema >>
+2021-03-01T09:23:33.077-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.0 - Init""
+2021-03-01T09:23:33.207-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.1 - update""
+2021-03-01T09:23:33.228-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.2 - procedures""
+2021-03-01T09:23:33.257-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.3 - procedures""
+2021-03-01T09:23:33.268-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.4 - update""
+2021-03-01T09:23:33.280-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.5 - file create patch""
+2021-03-01T09:23:33.289-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.7 - application status""
+2021-03-01T09:23:33.301-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.9 - index""
+2021-03-01T09:23:33.308-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.9.1 - transactions indexes""
+2021-03-01T09:23:33.317-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.10.0 - account balances""
+2021-03-01T09:23:33.336-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.10.1 - freeze transaction""
+2021-03-01T09:23:33.346-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.10.2 - response codes""
+2021-03-01T09:23:33.353-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.10.3 - account balances""
+2021-03-01T09:23:33.364-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.0 - entity key""
+2021-03-01T09:23:33.374-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.1 - remove deprecated""
+2021-03-01T09:23:33.389-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.2 - transactions pk""
+2021-03-01T09:23:33.420-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.3 - entity key""
+2021-03-01T09:23:33.425-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.4 - duplicate entities""
+2021-03-01T09:23:33.434-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.5 - entity create""
+2021-03-01T09:23:33.440-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.5.1 - response codes""
+2021-03-01T09:23:33.447-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.6 - Missing Entities""
+2021-03-01T09:23:33.449-0600 WARN main c.h.m.i.m.V1_11_6__Missing_Entities Skipping entity import due to missing file /root/project/hedera-mirror-importer/./data/accountInfo.txt
+2021-03-01T09:23:33.455-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.12 - transactions maxfee duration""
+2021-03-01T09:23:33.459-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.13 - transaction hash""
+2021-03-01T09:23:33.464-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.14 - response codes""
+2021-03-01T09:23:33.469-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.15 - unknown transaction types""
+2021-03-01T09:23:33.483-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.16 - cryptotransferlist realm num""
+2021-03-01T09:23:33.496-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.17.0 - hcs support""
+2021-03-01T09:23:33.509-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.17.1 - f entity create""
+2021-03-01T09:23:33.517-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.17.2 - transaction bytes""
+2021-03-01T09:23:33.522-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.17.3 - drop f entity create""
+2021-03-01T09:23:33.528-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.17.4 - hcs proto changes""
+2021-03-01T09:23:33.538-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.17.5 - fix mirror api permissions""
+2021-03-01T09:23:33.545-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.18.0 - non fee transfers""
+2021-03-01T09:23:33.554-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.19.0 - drop fks trigger unused indexes""
+2021-03-01T09:23:33.568-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.20 - drop file id""
+2021-03-01T09:23:33.575-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.21 - add topicmessage seqindex""
+2021-03-01T09:23:33.581-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.22 - remove unused components""
+2021-03-01T09:23:33.590-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.23.0 - r5 rc4 proto updates""
+2021-03-01T09:23:33.596-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.23.1 - add topicmessage runninghashversion""
+2021-03-01T09:23:33.601-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.24.0 - remove bypass state""
+2021-03-01T09:23:33.606-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.24.1 - t record files timestamps""
+2021-03-01T09:23:33.616-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.25.0 - denormalize entities""
+2021-03-01T09:23:33.633-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.25.1 - denormalize transfer tables""
+2021-03-01T09:23:33.643-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.26.0 - topic message fragmentation""
+2021-03-01T09:23:33.648-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.26.1 - pg notify""
+2021-03-01T09:23:33.653-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.26.2 - drop notify trigger""
+2021-03-01T09:23:33.657-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.27.0 - add event streams""
+2021-03-01T09:23:33.663-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.27.1 - populate consensus start end for record files""
+2021-03-01T09:23:33.674-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.27.2 - update name of record file to filename""
+2021-03-01T09:23:33.679-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.27.3 - rename tables""
+2021-03-01T09:23:33.685-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.28.0 - address book""
+2021-03-01T09:23:33.697-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.28.2 - record file index consensus end""
+2021-03-01T09:23:33.703-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.29.0 - store verification node in stream file tables""
+2021-03-01T09:23:33.718-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.30.0 - balance entity id""
+2021-03-01T09:23:33.728-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.30.1 - hts support""
+2021-03-01T09:23:33.744-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.31.0 - fix address book 102""
+2021-03-01T09:23:33.749-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.31.1 - token symbol size 100""
+2021-03-01T09:23:33.754-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.31.2 - remove invalid entities""
+2021-03-01T09:23:33.768-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.31.3 - delete token transfers transaction type""
+2021-03-01T09:23:33.772-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.32.1 - update transaction index""
+2021-03-01T09:23:33.778-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.33.0 - drop token account id""
+2021-03-01T09:23:33.791-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.33.1 - update record file""
+2021-03-01T09:23:33.808-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.34.0 - schedule support""
+2021-03-01T09:23:33.819-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.34.1 - transaction schedule""
+2021-03-01T09:23:33.830-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.34.2 - rename record file hash""
+2021-03-01T09:23:33.838-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.35.0 - update schedule response codes""
+2021-03-01T09:23:33.846-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.35.1 - remove filesystem""
+2021-03-01T09:23:33.859-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.35.2 - schedule index""
+2021-03-01T09:23:33.866-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.35.3 - record file block index""
+2021-03-01T09:23:33.875-0600 INFO main o.f.c.i.c.DbMigrate Successfully applied 69 migrations to schema ""public"" (execution time 00:00.843s)
+2021-03-01T09:23:36.989-0600 INFO main c.h.m.i.c.MirrorImporterConfiguration Configured to download from S3 in region us-east-1 with bucket name 'test'
+2021-03-01T09:23:41.482-0600 INFO main c.h.m.i.p.r.RecordFileParserPerformanceTest Started RecordFileParserPerformanceTest in 14.229 seconds (JVM running for 17.578)
+2021-03-01T09:23:42.404-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_02_56.025429000Z.rcd
+2021-03-01T09:23:43.013-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_02_58.019176000Z.rcd
+2021-03-01T09:23:43.236-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_00.032295000Z.rcd
+2021-03-01T09:23:43.488-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_02.031984000Z.rcd
+2021-03-01T09:23:43.851-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_04.004057000Z.rcd
+2021-03-01T09:23:56.260-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_06.001417000Z.rcd
+2021-03-01T09:23:56.362-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_08.002071000Z.rcd
+2021-03-01T09:23:56.497-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_10.016188000Z.rcd
+2021-03-01T09:23:56.630-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_12.001771000Z.rcd
+2021-03-01T09:23:56.988-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_14.015461000Z.rcd
+2021-03-01T09:23:57.077-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_16.061108000Z.rcd
+2021-03-01T09:23:57.992-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_18.004362000Z.rcd
+2021-03-01T09:23:58.407-0600 INFO main c.h.m.i.p.r.RecordFileParserPerformanceTest Executing: parse()
+2021-03-01T09:23:58.556-0600 INFO main c.h.m.i.c.MirrorDateRangePropertiesProcessor RECORD: parser will parse items in the range [1970-01-01T00:00:00Z, 2262-04-11T23:47:16.854775807Z]
+2021-03-01T09:24:00.892-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 12654 rows to transaction table in 343.9 ms
+2021-03-01T09:24:01.439-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 50588 rows to crypto_transfer table in 483.9 ms
+2021-03-01T09:24:01.516-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 17 entities in 76.62 ms
+2021-03-01T09:24:01.516-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 2.097 s
+2021-03-01T09:24:01.573-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 12654 transactions from record file 2021-01-14T20_02_56.025429000Z.rcd in 3.118 s. Success: true
+2021-03-01T09:24:02.475-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 12378 rows to transaction table in 546.3 ms
+2021-03-01T09:24:03.535-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 49477 rows to crypto_transfer table in 1.039 s
+2021-03-01T09:24:03.548-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 17 entities in 12.97 ms
+2021-03-01T09:24:03.548-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 1.786 s
+2021-03-01T09:24:03.550-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 12378 transactions from record file 2021-01-14T20_02_58.019176000Z.rcd in 1.892 s. Success: true
+2021-03-01T09:24:04.588-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 11649 rows to transaction table in 488.3 ms
+2021-03-01T09:24:04.757-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 46575 rows to crypto_transfer table in 149.5 ms
+2021-03-01T09:24:04.770-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 17 entities in 12.78 ms
+2021-03-01T09:24:04.770-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 1.117 s
+2021-03-01T09:24:04.771-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 11649 transactions from record file 2021-01-14T20_03_00.032295000Z.rcd in 1.184 s. Success: true
+2021-03-01T09:24:06.210-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 11196 rows to transaction table in 1.325 s
+2021-03-01T09:24:06.425-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 44753 rows to crypto_transfer table in 190.2 ms
+2021-03-01T09:24:06.437-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 11.89 ms
+2021-03-01T09:24:06.437-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 1.592 s
+2021-03-01T09:24:06.439-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 11196 transactions from record file 2021-01-14T20_03_02.031984000Z.rcd in 1.650 s. Success: true
+2021-03-01T09:24:07.169-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 10500 rows to transaction table in 626.7 ms
+2021-03-01T09:24:07.906-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 41979 rows to crypto_transfer table in 719.5 ms
+2021-03-01T09:24:07.919-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 12.65 ms
+2021-03-01T09:24:07.919-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 1.422 s
+2021-03-01T09:24:07.921-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 10500 transactions from record file 2021-01-14T20_03_04.004057000Z.rcd in 1.473 s. Success: true
+2021-03-01T09:24:08.607-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 11427 rows to transaction table in 551.0 ms
+2021-03-01T09:24:09.021-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 45665 rows to crypto_transfer table in 396.4 ms
+2021-03-01T09:24:09.033-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 17 entities in 12.04 ms
+2021-03-01T09:24:09.034-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 1.047 s
+2021-03-01T09:24:09.035-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 11427 transactions from record file 2021-01-14T20_03_06.001417000Z.rcd in 1.107 s. Success: true
+2021-03-01T09:24:09.424-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 11771 rows to transaction table in 115.9 ms
+2021-03-01T09:24:09.804-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 47053 rows to crypto_transfer table in 358.5 ms
+2021-03-01T09:24:09.816-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 11.80 ms
+2021-03-01T09:24:09.816-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 634.3 ms
+2021-03-01T09:24:09.817-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 11771 transactions from record file 2021-01-14T20_03_08.002071000Z.rcd in 719.5 ms. Success: true
+2021-03-01T09:24:10.178-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 10895 rows to transaction table in 230.7 ms
+2021-03-01T09:24:10.523-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 43554 rows to crypto_transfer table in 327.1 ms
+2021-03-01T09:24:10.535-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 11.07 ms
+2021-03-01T09:24:10.535-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 645.9 ms
+2021-03-01T09:24:10.537-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 10895 transactions from record file 2021-01-14T20_03_10.016188000Z.rcd in 711.1 ms. Success: true
+2021-03-01T09:24:10.739-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 10642 rows to transaction table in 98.91 ms
+2021-03-01T09:24:10.930-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 42537 rows to crypto_transfer table in 170.9 ms
+2021-03-01T09:24:10.943-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 13.00 ms
+2021-03-01T09:24:10.944-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 341.4 ms
+2021-03-01T09:24:10.947-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 10642 transactions from record file 2021-01-14T20_03_12.001771000Z.rcd in 400.9 ms. Success: true
+2021-03-01T09:24:13.375-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 11801 rows to transaction table in 2.272 s
+2021-03-01T09:24:13.747-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 47174 rows to crypto_transfer table in 353.5 ms
+2021-03-01T09:24:13.761-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 12.79 ms
+2021-03-01T09:24:13.761-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 2.722 s
+2021-03-01T09:24:13.762-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 11801 transactions from record file 2021-01-14T20_03_14.015461000Z.rcd in 2.808 s. Success: true
+2021-03-01T09:24:14.249-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 11044 rows to transaction table in 302.3 ms
+2021-03-01T09:24:14.583-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 44158 rows to crypto_transfer table in 321.3 ms
+2021-03-01T09:24:14.602-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 10.98 ms
+2021-03-01T09:24:14.602-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 694.9 ms
+2021-03-01T09:24:14.603-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 11044 transactions from record file 2021-01-14T20_03_16.061108000Z.rcd in 801.3 ms. Success: true
+2021-03-01T09:24:14.910-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 10665 rows to transaction table in 226.0 ms
+2021-03-01T09:24:15.265-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 42630 rows to crypto_transfer table in 338.9 ms
+2021-03-01T09:24:15.276-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 10.03 ms
+2021-03-01T09:24:15.276-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 618.4 ms
+2021-03-01T09:24:15.277-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 10665 transactions from record file 2021-01-14T20_03_18.004362000Z.rcd in 663.4 ms. Success: true
+[ERROR] Tests run: 1, Failures: 0, Errors: 1, Skipped: 0, Time elapsed: 49.831 s <<< FAILURE! - in com.hedera.mirror.importer.parser.record.RecordFileParserPerformanceTest
+[ERROR] com.hedera.mirror.importer.parser.record.RecordFileParserPerformanceTest.parse Time elapsed: 17.606 s <<< ERROR!
+java.util.concurrent.TimeoutException: parse() timed out after 15 seconds
+```
+
+**Actual Behavior**
+Steps to reproduce the behavior:
+1. Go to '...'
+2. Click on '....'
+3. Scroll down to '....'
+
+**Expected Behavior**
+
+**Environment:**
+- Java: [e.g. OpenJDK 11.0.4]
+- Node: [e.g. v12.9.1-x86]
+- OS: [e.g. Ubuntu 18.04]
+- Version: [e.g. 1.0.1]
+
+**Additional Context**
+
+",1.0,"RecordFileParserPerformanceTest times out in CircleCi -
+
+**Detailed Description**
+https://app.circleci.com/pipelines/github/hashgraph/hedera-mirror-node/6248/workflows/c52d402b-7bf3-4b49-b386-91ad18116820/jobs/17965/steps
+
+```
+2021-03-01T09:23:28.771-0600 INFO main c.h.m.i.p.r.RecordFileParserPerformanceTest No active profile set, falling back to default profiles: default
+2021-03-01T09:23:32.694-0600 INFO main c.h.m.i.c.MetricsConfiguration Collecting table metrics: []
+2021-03-01T09:23:32.738-0600 INFO main c.h.m.i.c.CredentialsProviderConfiguration Setting up S3 async client using AWS Default Credentials Provider
+2021-03-01T09:23:33.044-0600 INFO main o.f.c.i.c.DbMigrate Current version of schema ""public"": << Empty Schema >>
+2021-03-01T09:23:33.077-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.0 - Init""
+2021-03-01T09:23:33.207-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.1 - update""
+2021-03-01T09:23:33.228-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.2 - procedures""
+2021-03-01T09:23:33.257-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.3 - procedures""
+2021-03-01T09:23:33.268-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.4 - update""
+2021-03-01T09:23:33.280-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.5 - file create patch""
+2021-03-01T09:23:33.289-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.7 - application status""
+2021-03-01T09:23:33.301-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.9 - index""
+2021-03-01T09:23:33.308-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.9.1 - transactions indexes""
+2021-03-01T09:23:33.317-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.10.0 - account balances""
+2021-03-01T09:23:33.336-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.10.1 - freeze transaction""
+2021-03-01T09:23:33.346-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.10.2 - response codes""
+2021-03-01T09:23:33.353-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.10.3 - account balances""
+2021-03-01T09:23:33.364-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.0 - entity key""
+2021-03-01T09:23:33.374-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.1 - remove deprecated""
+2021-03-01T09:23:33.389-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.2 - transactions pk""
+2021-03-01T09:23:33.420-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.3 - entity key""
+2021-03-01T09:23:33.425-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.4 - duplicate entities""
+2021-03-01T09:23:33.434-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.5 - entity create""
+2021-03-01T09:23:33.440-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.5.1 - response codes""
+2021-03-01T09:23:33.447-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.11.6 - Missing Entities""
+2021-03-01T09:23:33.449-0600 WARN main c.h.m.i.m.V1_11_6__Missing_Entities Skipping entity import due to missing file /root/project/hedera-mirror-importer/./data/accountInfo.txt
+2021-03-01T09:23:33.455-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.12 - transactions maxfee duration""
+2021-03-01T09:23:33.459-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.13 - transaction hash""
+2021-03-01T09:23:33.464-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.14 - response codes""
+2021-03-01T09:23:33.469-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.15 - unknown transaction types""
+2021-03-01T09:23:33.483-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.16 - cryptotransferlist realm num""
+2021-03-01T09:23:33.496-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.17.0 - hcs support""
+2021-03-01T09:23:33.509-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.17.1 - f entity create""
+2021-03-01T09:23:33.517-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.17.2 - transaction bytes""
+2021-03-01T09:23:33.522-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.17.3 - drop f entity create""
+2021-03-01T09:23:33.528-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.17.4 - hcs proto changes""
+2021-03-01T09:23:33.538-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.17.5 - fix mirror api permissions""
+2021-03-01T09:23:33.545-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.18.0 - non fee transfers""
+2021-03-01T09:23:33.554-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.19.0 - drop fks trigger unused indexes""
+2021-03-01T09:23:33.568-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.20 - drop file id""
+2021-03-01T09:23:33.575-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.21 - add topicmessage seqindex""
+2021-03-01T09:23:33.581-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.22 - remove unused components""
+2021-03-01T09:23:33.590-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.23.0 - r5 rc4 proto updates""
+2021-03-01T09:23:33.596-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.23.1 - add topicmessage runninghashversion""
+2021-03-01T09:23:33.601-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.24.0 - remove bypass state""
+2021-03-01T09:23:33.606-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.24.1 - t record files timestamps""
+2021-03-01T09:23:33.616-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.25.0 - denormalize entities""
+2021-03-01T09:23:33.633-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.25.1 - denormalize transfer tables""
+2021-03-01T09:23:33.643-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.26.0 - topic message fragmentation""
+2021-03-01T09:23:33.648-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.26.1 - pg notify""
+2021-03-01T09:23:33.653-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.26.2 - drop notify trigger""
+2021-03-01T09:23:33.657-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.27.0 - add event streams""
+2021-03-01T09:23:33.663-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.27.1 - populate consensus start end for record files""
+2021-03-01T09:23:33.674-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.27.2 - update name of record file to filename""
+2021-03-01T09:23:33.679-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.27.3 - rename tables""
+2021-03-01T09:23:33.685-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.28.0 - address book""
+2021-03-01T09:23:33.697-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.28.2 - record file index consensus end""
+2021-03-01T09:23:33.703-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.29.0 - store verification node in stream file tables""
+2021-03-01T09:23:33.718-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.30.0 - balance entity id""
+2021-03-01T09:23:33.728-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.30.1 - hts support""
+2021-03-01T09:23:33.744-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.31.0 - fix address book 102""
+2021-03-01T09:23:33.749-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.31.1 - token symbol size 100""
+2021-03-01T09:23:33.754-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.31.2 - remove invalid entities""
+2021-03-01T09:23:33.768-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.31.3 - delete token transfers transaction type""
+2021-03-01T09:23:33.772-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.32.1 - update transaction index""
+2021-03-01T09:23:33.778-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.33.0 - drop token account id""
+2021-03-01T09:23:33.791-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.33.1 - update record file""
+2021-03-01T09:23:33.808-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.34.0 - schedule support""
+2021-03-01T09:23:33.819-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.34.1 - transaction schedule""
+2021-03-01T09:23:33.830-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.34.2 - rename record file hash""
+2021-03-01T09:23:33.838-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.35.0 - update schedule response codes""
+2021-03-01T09:23:33.846-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.35.1 - remove filesystem""
+2021-03-01T09:23:33.859-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.35.2 - schedule index""
+2021-03-01T09:23:33.866-0600 INFO main o.f.c.i.c.DbMigrate Migrating schema ""public"" to version ""1.35.3 - record file block index""
+2021-03-01T09:23:33.875-0600 INFO main o.f.c.i.c.DbMigrate Successfully applied 69 migrations to schema ""public"" (execution time 00:00.843s)
+2021-03-01T09:23:36.989-0600 INFO main c.h.m.i.c.MirrorImporterConfiguration Configured to download from S3 in region us-east-1 with bucket name 'test'
+2021-03-01T09:23:41.482-0600 INFO main c.h.m.i.p.r.RecordFileParserPerformanceTest Started RecordFileParserPerformanceTest in 14.229 seconds (JVM running for 17.578)
+2021-03-01T09:23:42.404-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_02_56.025429000Z.rcd
+2021-03-01T09:23:43.013-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_02_58.019176000Z.rcd
+2021-03-01T09:23:43.236-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_00.032295000Z.rcd
+2021-03-01T09:23:43.488-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_02.031984000Z.rcd
+2021-03-01T09:23:43.851-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_04.004057000Z.rcd
+2021-03-01T09:23:56.260-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_06.001417000Z.rcd
+2021-03-01T09:23:56.362-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_08.002071000Z.rcd
+2021-03-01T09:23:56.497-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_10.016188000Z.rcd
+2021-03-01T09:23:56.630-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_12.001771000Z.rcd
+2021-03-01T09:23:56.988-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_14.015461000Z.rcd
+2021-03-01T09:23:57.077-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_16.061108000Z.rcd
+2021-03-01T09:23:57.992-0600 INFO main c.h.m.i.r.r.CompositeRecordFileReader Loading record format version 5 from record file: 2021-01-14T20_03_18.004362000Z.rcd
+2021-03-01T09:23:58.407-0600 INFO main c.h.m.i.p.r.RecordFileParserPerformanceTest Executing: parse()
+2021-03-01T09:23:58.556-0600 INFO main c.h.m.i.c.MirrorDateRangePropertiesProcessor RECORD: parser will parse items in the range [1970-01-01T00:00:00Z, 2262-04-11T23:47:16.854775807Z]
+2021-03-01T09:24:00.892-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 12654 rows to transaction table in 343.9 ms
+2021-03-01T09:24:01.439-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 50588 rows to crypto_transfer table in 483.9 ms
+2021-03-01T09:24:01.516-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 17 entities in 76.62 ms
+2021-03-01T09:24:01.516-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 2.097 s
+2021-03-01T09:24:01.573-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 12654 transactions from record file 2021-01-14T20_02_56.025429000Z.rcd in 3.118 s. Success: true
+2021-03-01T09:24:02.475-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 12378 rows to transaction table in 546.3 ms
+2021-03-01T09:24:03.535-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 49477 rows to crypto_transfer table in 1.039 s
+2021-03-01T09:24:03.548-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 17 entities in 12.97 ms
+2021-03-01T09:24:03.548-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 1.786 s
+2021-03-01T09:24:03.550-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 12378 transactions from record file 2021-01-14T20_02_58.019176000Z.rcd in 1.892 s. Success: true
+2021-03-01T09:24:04.588-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 11649 rows to transaction table in 488.3 ms
+2021-03-01T09:24:04.757-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 46575 rows to crypto_transfer table in 149.5 ms
+2021-03-01T09:24:04.770-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 17 entities in 12.78 ms
+2021-03-01T09:24:04.770-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 1.117 s
+2021-03-01T09:24:04.771-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 11649 transactions from record file 2021-01-14T20_03_00.032295000Z.rcd in 1.184 s. Success: true
+2021-03-01T09:24:06.210-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 11196 rows to transaction table in 1.325 s
+2021-03-01T09:24:06.425-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 44753 rows to crypto_transfer table in 190.2 ms
+2021-03-01T09:24:06.437-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 11.89 ms
+2021-03-01T09:24:06.437-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 1.592 s
+2021-03-01T09:24:06.439-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 11196 transactions from record file 2021-01-14T20_03_02.031984000Z.rcd in 1.650 s. Success: true
+2021-03-01T09:24:07.169-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 10500 rows to transaction table in 626.7 ms
+2021-03-01T09:24:07.906-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 41979 rows to crypto_transfer table in 719.5 ms
+2021-03-01T09:24:07.919-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 12.65 ms
+2021-03-01T09:24:07.919-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 1.422 s
+2021-03-01T09:24:07.921-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 10500 transactions from record file 2021-01-14T20_03_04.004057000Z.rcd in 1.473 s. Success: true
+2021-03-01T09:24:08.607-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 11427 rows to transaction table in 551.0 ms
+2021-03-01T09:24:09.021-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 45665 rows to crypto_transfer table in 396.4 ms
+2021-03-01T09:24:09.033-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 17 entities in 12.04 ms
+2021-03-01T09:24:09.034-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 1.047 s
+2021-03-01T09:24:09.035-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 11427 transactions from record file 2021-01-14T20_03_06.001417000Z.rcd in 1.107 s. Success: true
+2021-03-01T09:24:09.424-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 11771 rows to transaction table in 115.9 ms
+2021-03-01T09:24:09.804-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 47053 rows to crypto_transfer table in 358.5 ms
+2021-03-01T09:24:09.816-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 11.80 ms
+2021-03-01T09:24:09.816-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 634.3 ms
+2021-03-01T09:24:09.817-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 11771 transactions from record file 2021-01-14T20_03_08.002071000Z.rcd in 719.5 ms. Success: true
+2021-03-01T09:24:10.178-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 10895 rows to transaction table in 230.7 ms
+2021-03-01T09:24:10.523-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 43554 rows to crypto_transfer table in 327.1 ms
+2021-03-01T09:24:10.535-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 11.07 ms
+2021-03-01T09:24:10.535-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 645.9 ms
+2021-03-01T09:24:10.537-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 10895 transactions from record file 2021-01-14T20_03_10.016188000Z.rcd in 711.1 ms. Success: true
+2021-03-01T09:24:10.739-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 10642 rows to transaction table in 98.91 ms
+2021-03-01T09:24:10.930-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 42537 rows to crypto_transfer table in 170.9 ms
+2021-03-01T09:24:10.943-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 13.00 ms
+2021-03-01T09:24:10.944-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 341.4 ms
+2021-03-01T09:24:10.947-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 10642 transactions from record file 2021-01-14T20_03_12.001771000Z.rcd in 400.9 ms. Success: true
+2021-03-01T09:24:13.375-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 11801 rows to transaction table in 2.272 s
+2021-03-01T09:24:13.747-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 47174 rows to crypto_transfer table in 353.5 ms
+2021-03-01T09:24:13.761-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 12.79 ms
+2021-03-01T09:24:13.761-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 2.722 s
+2021-03-01T09:24:13.762-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 11801 transactions from record file 2021-01-14T20_03_14.015461000Z.rcd in 2.808 s. Success: true
+2021-03-01T09:24:14.249-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 11044 rows to transaction table in 302.3 ms
+2021-03-01T09:24:14.583-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 44158 rows to crypto_transfer table in 321.3 ms
+2021-03-01T09:24:14.602-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 10.98 ms
+2021-03-01T09:24:14.602-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 694.9 ms
+2021-03-01T09:24:14.603-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 11044 transactions from record file 2021-01-14T20_03_16.061108000Z.rcd in 801.3 ms. Success: true
+2021-03-01T09:24:14.910-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 10665 rows to transaction table in 226.0 ms
+2021-03-01T09:24:15.265-0600 INFO main c.h.m.i.p.r.e.s.PgCopy Copied 42630 rows to crypto_transfer table in 338.9 ms
+2021-03-01T09:24:15.276-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Inserted 16 entities in 10.03 ms
+2021-03-01T09:24:15.276-0600 INFO main c.h.m.i.p.r.e.s.SqlEntityListener Completed batch inserts in 618.4 ms
+2021-03-01T09:24:15.277-0600 INFO main c.h.m.i.p.r.RecordFileParser Finished parsing 10665 transactions from record file 2021-01-14T20_03_18.004362000Z.rcd in 663.4 ms. Success: true
+[ERROR] Tests run: 1, Failures: 0, Errors: 1, Skipped: 0, Time elapsed: 49.831 s <<< FAILURE! - in com.hedera.mirror.importer.parser.record.RecordFileParserPerformanceTest
+[ERROR] com.hedera.mirror.importer.parser.record.RecordFileParserPerformanceTest.parse Time elapsed: 17.606 s <<< ERROR!
+java.util.concurrent.TimeoutException: parse() timed out after 15 seconds
+```
+
+**Actual Behavior**
+Steps to reproduce the behavior:
+1. Go to '...'
+2. Click on '....'
+3. Scroll down to '....'
+
+**Expected Behavior**
+
+**Environment:**
+- Java: [e.g. OpenJDK 11.0.4]
+- Node: [e.g. v12.9.1-x86]
+- OS: [e.g. Ubuntu 18.04]
+- Version: [e.g. 1.0.1]
+
+**Additional Context**
+
+",0,recordfileparserperformancetest times out in circleci thanks for submitting a bug report before submitting try searching the existing issues to see if your issue has already been reported try asking on our discord group if you re reporting a security vulnerability please email security hedera com instead of opening an issue detailed description info main c h m i p r recordfileparserperformancetest no active profile set falling back to default profiles default info main c h m i c metricsconfiguration collecting table metrics info main c h m i c credentialsproviderconfiguration setting up async client using aws default credentials provider info main o f c i c dbmigrate current version of schema public info main o f c i c dbmigrate migrating schema public to version init info main o f c i c dbmigrate migrating schema public to version update info main o f c i c dbmigrate migrating schema public to version procedures info main o f c i c dbmigrate migrating schema public to version procedures info main o f c i c dbmigrate migrating schema public to version update info main o f c i c dbmigrate migrating schema public to version file create patch info main o f c i c dbmigrate migrating schema public to version application status info main o f c i c dbmigrate migrating schema public to version index info main o f c i c dbmigrate migrating schema public to version transactions indexes info main o f c i c dbmigrate migrating schema public to version account balances info main o f c i c dbmigrate migrating schema public to version freeze transaction info main o f c i c dbmigrate migrating schema public to version response codes info main o f c i c dbmigrate migrating schema public to version account balances info main o f c i c dbmigrate migrating schema public to version entity key info main o f c i c dbmigrate migrating schema public to version remove deprecated info main o f c i c dbmigrate migrating schema public to version transactions pk info main o f c i c dbmigrate migrating schema public to version entity key info main o f c i c dbmigrate migrating schema public to version duplicate entities info main o f c i c dbmigrate migrating schema public to version entity create info main o f c i c dbmigrate migrating schema public to version response codes info main o f c i c dbmigrate migrating schema public to version missing entities warn main c h m i m missing entities skipping entity import due to missing file root project hedera mirror importer data accountinfo txt info main o f c i c dbmigrate migrating schema public to version transactions maxfee duration info main o f c i c dbmigrate migrating schema public to version transaction hash info main o f c i c dbmigrate migrating schema public to version response codes info main o f c i c dbmigrate migrating schema public to version unknown transaction types info main o f c i c dbmigrate migrating schema public to version cryptotransferlist realm num info main o f c i c dbmigrate migrating schema public to version hcs support info main o f c i c dbmigrate migrating schema public to version f entity create info main o f c i c dbmigrate migrating schema public to version transaction bytes info main o f c i c dbmigrate migrating schema public to version drop f entity create info main o f c i c dbmigrate migrating schema public to version hcs proto changes info main o f c i c dbmigrate migrating schema public to version fix mirror api permissions info main o f c i c dbmigrate migrating schema public to version non fee transfers info main o f c i c dbmigrate migrating schema public to version drop fks trigger unused indexes info main o f c i c dbmigrate migrating schema public to version drop file id info main o f c i c dbmigrate migrating schema public to version add topicmessage seqindex info main o f c i c dbmigrate migrating schema public to version remove unused components info main o f c i c dbmigrate migrating schema public to version proto updates info main o f c i c dbmigrate migrating schema public to version add topicmessage runninghashversion info main o f c i c dbmigrate migrating schema public to version remove bypass state info main o f c i c dbmigrate migrating schema public to version t record files timestamps info main o f c i c dbmigrate migrating schema public to version denormalize entities info main o f c i c dbmigrate migrating schema public to version denormalize transfer tables info main o f c i c dbmigrate migrating schema public to version topic message fragmentation info main o f c i c dbmigrate migrating schema public to version pg notify info main o f c i c dbmigrate migrating schema public to version drop notify trigger info main o f c i c dbmigrate migrating schema public to version add event streams info main o f c i c dbmigrate migrating schema public to version populate consensus start end for record files info main o f c i c dbmigrate migrating schema public to version update name of record file to filename info main o f c i c dbmigrate migrating schema public to version rename tables info main o f c i c dbmigrate migrating schema public to version address book info main o f c i c dbmigrate migrating schema public to version record file index consensus end info main o f c i c dbmigrate migrating schema public to version store verification node in stream file tables info main o f c i c dbmigrate migrating schema public to version balance entity id info main o f c i c dbmigrate migrating schema public to version hts support info main o f c i c dbmigrate migrating schema public to version fix address book info main o f c i c dbmigrate migrating schema public to version token symbol size info main o f c i c dbmigrate migrating schema public to version remove invalid entities info main o f c i c dbmigrate migrating schema public to version delete token transfers transaction type info main o f c i c dbmigrate migrating schema public to version update transaction index info main o f c i c dbmigrate migrating schema public to version drop token account id info main o f c i c dbmigrate migrating schema public to version update record file info main o f c i c dbmigrate migrating schema public to version schedule support info main o f c i c dbmigrate migrating schema public to version transaction schedule info main o f c i c dbmigrate migrating schema public to version rename record file hash info main o f c i c dbmigrate migrating schema public to version update schedule response codes info main o f c i c dbmigrate migrating schema public to version remove filesystem info main o f c i c dbmigrate migrating schema public to version schedule index info main o f c i c dbmigrate migrating schema public to version record file block index info main o f c i c dbmigrate successfully applied migrations to schema public execution time info main c h m i c mirrorimporterconfiguration configured to download from in region us east with bucket name test info main c h m i p r recordfileparserperformancetest started recordfileparserperformancetest in seconds jvm running for info main c h m i r r compositerecordfilereader loading record format version from record file rcd info main c h m i r r compositerecordfilereader loading record format version from record file rcd info main c h m i r r compositerecordfilereader loading record format version from record file rcd info main c h m i r r compositerecordfilereader loading record format version from record file rcd info main c h m i r r compositerecordfilereader loading record format version from record file rcd info main c h m i r r compositerecordfilereader loading record format version from record file rcd info main c h m i r r compositerecordfilereader loading record format version from record file rcd info main c h m i r r compositerecordfilereader loading record format version from record file rcd info main c h m i r r compositerecordfilereader loading record format version from record file rcd info main c h m i r r compositerecordfilereader loading record format version from record file rcd info main c h m i r r compositerecordfilereader loading record format version from record file rcd info main c h m i r r compositerecordfilereader loading record format version from record file rcd info main c h m i p r recordfileparserperformancetest executing parse info main c h m i c mirrordaterangepropertiesprocessor record parser will parse items in the range info main c h m i p r e s pgcopy copied rows to transaction table in ms info main c h m i p r e s pgcopy copied rows to crypto transfer table in ms info main c h m i p r e s sqlentitylistener inserted entities in ms info main c h m i p r e s sqlentitylistener completed batch inserts in s info main c h m i p r recordfileparser finished parsing transactions from record file rcd in s success true info main c h m i p r e s pgcopy copied rows to transaction table in ms info main c h m i p r e s pgcopy copied rows to crypto transfer table in s info main c h m i p r e s sqlentitylistener inserted entities in ms info main c h m i p r e s sqlentitylistener completed batch inserts in s info main c h m i p r recordfileparser finished parsing transactions from record file rcd in s success true info main c h m i p r e s pgcopy copied rows to transaction table in ms info main c h m i p r e s pgcopy copied rows to crypto transfer table in ms info main c h m i p r e s sqlentitylistener inserted entities in ms info main c h m i p r e s sqlentitylistener completed batch inserts in s info main c h m i p r recordfileparser finished parsing transactions from record file rcd in s success true info main c h m i p r e s pgcopy copied rows to transaction table in s info main c h m i p r e s pgcopy copied rows to crypto transfer table in ms info main c h m i p r e s sqlentitylistener inserted entities in ms info main c h m i p r e s sqlentitylistener completed batch inserts in s info main c h m i p r recordfileparser finished parsing transactions from record file rcd in s success true info main c h m i p r e s pgcopy copied rows to transaction table in ms info main c h m i p r e s pgcopy copied rows to crypto transfer table in ms info main c h m i p r e s sqlentitylistener inserted entities in ms info main c h m i p r e s sqlentitylistener completed batch inserts in s info main c h m i p r recordfileparser finished parsing transactions from record file rcd in s success true info main c h m i p r e s pgcopy copied rows to transaction table in ms info main c h m i p r e s pgcopy copied rows to crypto transfer table in ms info main c h m i p r e s sqlentitylistener inserted entities in ms info main c h m i p r e s sqlentitylistener completed batch inserts in s info main c h m i p r recordfileparser finished parsing transactions from record file rcd in s success true info main c h m i p r e s pgcopy copied rows to transaction table in ms info main c h m i p r e s pgcopy copied rows to crypto transfer table in ms info main c h m i p r e s sqlentitylistener inserted entities in ms info main c h m i p r e s sqlentitylistener completed batch inserts in ms info main c h m i p r recordfileparser finished parsing transactions from record file rcd in ms success true info main c h m i p r e s pgcopy copied rows to transaction table in ms info main c h m i p r e s pgcopy copied rows to crypto transfer table in ms info main c h m i p r e s sqlentitylistener inserted entities in ms info main c h m i p r e s sqlentitylistener completed batch inserts in ms info main c h m i p r recordfileparser finished parsing transactions from record file rcd in ms success true info main c h m i p r e s pgcopy copied rows to transaction table in ms info main c h m i p r e s pgcopy copied rows to crypto transfer table in ms info main c h m i p r e s sqlentitylistener inserted entities in ms info main c h m i p r e s sqlentitylistener completed batch inserts in ms info main c h m i p r recordfileparser finished parsing transactions from record file rcd in ms success true info main c h m i p r e s pgcopy copied rows to transaction table in s info main c h m i p r e s pgcopy copied rows to crypto transfer table in ms info main c h m i p r e s sqlentitylistener inserted entities in ms info main c h m i p r e s sqlentitylistener completed batch inserts in s info main c h m i p r recordfileparser finished parsing transactions from record file rcd in s success true info main c h m i p r e s pgcopy copied rows to transaction table in ms info main c h m i p r e s pgcopy copied rows to crypto transfer table in ms info main c h m i p r e s sqlentitylistener inserted entities in ms info main c h m i p r e s sqlentitylistener completed batch inserts in ms info main c h m i p r recordfileparser finished parsing transactions from record file rcd in ms success true info main c h m i p r e s pgcopy copied rows to transaction table in ms info main c h m i p r e s pgcopy copied rows to crypto transfer table in ms info main c h m i p r e s sqlentitylistener inserted entities in ms info main c h m i p r e s sqlentitylistener completed batch inserts in ms info main c h m i p r recordfileparser finished parsing transactions from record file rcd in ms success true tests run failures errors skipped time elapsed s failure in com hedera mirror importer parser record recordfileparserperformancetest com hedera mirror importer parser record recordfileparserperformancetest parse time elapsed s error java util concurrent timeoutexception parse timed out after seconds actual behavior steps to reproduce the behavior go to click on scroll down to expected behavior environment java node os version additional context ,0
+3380,6346700935.0,IssuesEvent,2017-07-28 03:27:37,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Built-in function SOUNDEX not supported,compatibility rc3.1,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```
+create table t1 (id integer, a varchar(100) character set utf8 collate utf8_unicode_ci);
+insert into t1 values (1, 'Test');
+select * from t1 where soundex(a) = soundex('Test');
+```
+
+2. What did you expect to see?
+
+```
++------+------+
+| id | a |
++------+------+
+| 1 | Test |
++------+------+
+1 row in set (0.01 sec)
+```
+
+3. What did you see instead?
+
+```
+ERROR 1105 (HY000): line 0 column 31 near ""a) = soundex('Test')"" (total length 51)
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"Built-in function SOUNDEX not supported - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```
+create table t1 (id integer, a varchar(100) character set utf8 collate utf8_unicode_ci);
+insert into t1 values (1, 'Test');
+select * from t1 where soundex(a) = soundex('Test');
+```
+
+2. What did you expect to see?
+
+```
++------+------+
+| id | a |
++------+------+
+| 1 | Test |
++------+------+
+1 row in set (0.01 sec)
+```
+
+3. What did you see instead?
+
+```
+ERROR 1105 (HY000): line 0 column 31 near ""a) = soundex('Test')"" (total length 51)
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,built in function soundex not supported please answer these questions before submitting your issue thanks what did you do create table id integer a varchar character set collate unicode ci insert into values test select from where soundex a soundex test what did you expect to see id a test row in set sec what did you see instead error line column near a soundex test total length what version of tidb are you using tidb server v ,1
+385592,26644872795.0,IssuesEvent,2023-01-25 09:11:43,ebi-ait/hca-ebi-wrangler-central,https://api.github.com/repos/ebi-ait/hca-ebi-wrangler-central,closed,SOP - Inform the contributors after wrangling,documentation operations,"To increase community engagement, we should send an email after wrangling any dataset from a publication or repository (GEO). After verifying the wrangled dataset is live on the Data Portal, we should inform about it the contributors.
+Add a new template email: after verifying a dataset is live on the Data Portal, we should inform the original contributors of the dataset. A good practice would be to ask them for feedback and to join the conversation on slack.
-Dependency Hierarchy:
- - dotnetcore-sample-1.0.0 (Root Library)
- - microsoft.aspnetcore.2.0.0.nupkg
- - :x: **microsoft.aspnetcore.server.iisintegration.2.0.0.nupkg** (Vulnerable Library)
+This idea comes from one of our DCP meetings, to increase community engagement and as a wrangler's best practice
+Completed when:
-### microsoft.aspnetcore.hosting.2.0.0.nupkg
+- [x] A new template email has been created
+- [x] Our SOPs are updated to reflect this process",1.0,"SOP - Inform the contributors after wrangling - To increase community engagement, we should send an email after wrangling any dataset from a publication or repository (GEO). After verifying the wrangled dataset is live on the Data Portal, we should inform about it the contributors.
+Add a new template email: after verifying a dataset is live on the Data Portal, we should inform the original contributors of the dataset. A good practice would be to ask them for feedback and to join the conversation on slack.
-
ASP.NET Core hosting infrastructure and startup logic for web applications.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.hosting/2.0.0/microsoft.aspnetcore.hosting.2.0.0.nupkg
-
+This idea comes from one of our DCP meetings, to increase community engagement and as a wrangler's best practice
-Dependency Hierarchy:
- - dotnetcore-sample-1.0.0 (Root Library)
- - microsoft.aspnetcore.2.0.0.nupkg
- - microsoft.aspnetcore.server.kestrel.2.0.0.nupkg
- - :x: **microsoft.aspnetcore.hosting.2.0.0.nupkg** (Vulnerable Library)
+Completed when:
+- [x] A new template email has been created
+- [x] Our SOPs are updated to reflect this process",0,sop inform the contributors after wrangling to increase community engagement we should send an email after wrangling any dataset from a publication or repository geo after verifying the wrangled dataset is live on the data portal we should inform about it the contributors add a new template email after verifying a dataset is live on the data portal we should inform the original contributors of the dataset a good practice would be to ask them for feedback and to join the conversation on slack this idea comes from one of our dcp meetings to increase community engagement and as a wrangler s best practice completed when a new template email has been created our sops are updated to reflect this process,0
+11634,5052548446.0,IssuesEvent,2016-12-21 02:48:53,rust-lang/rust,https://api.github.com/repos/rust-lang/rust,closed,rustbuild: Dist on cross builds produce way too many tarballs,A-rustbuild,"The [dist step](https://buildbot.rust-lang.org/builders/nightly-dist-rustc-cross-host-linux/builds/281/steps/distcheck/logs/stdio) on cross builds takes over half an hour, and that's a crazy amount of time for something which should take at most 5 minutes.
+
+The [list of tarballs created](https://gist.github.com/alexcrichton/0ef4bdfcb3514e1ff5362394056feb4d) is massively duplicated. Namely we create around 60 source tarballs (!!). Looks like we're also packaging up the standard library dozens of times for the same target.
+
+My guess as to what's happening is that by default rustbuild is doing a cross product of (host x target) and doing all the builds. We should skip a massive number of them for distribution and ideally not even put them into the step list at all!
+
+Note that this isn't a fire at the moment as everything's just overwriting what was previously created, but this sounds like something that *could* become a fire!
+
+Should also be a relatively easy bug to knock out for anyone who wants to become familiar with rustbuild!",1.0,"rustbuild: Dist on cross builds produce way too many tarballs - The [dist step](https://buildbot.rust-lang.org/builders/nightly-dist-rustc-cross-host-linux/builds/281/steps/distcheck/logs/stdio) on cross builds takes over half an hour, and that's a crazy amount of time for something which should take at most 5 minutes.
+
+The [list of tarballs created](https://gist.github.com/alexcrichton/0ef4bdfcb3514e1ff5362394056feb4d) is massively duplicated. Namely we create around 60 source tarballs (!!). Looks like we're also packaging up the standard library dozens of times for the same target.
+
+My guess as to what's happening is that by default rustbuild is doing a cross product of (host x target) and doing all the builds. We should skip a massive number of them for distribution and ideally not even put them into the step list at all!
+
+Note that this isn't a fire at the moment as everything's just overwriting what was previously created, but this sounds like something that *could* become a fire!
+
+Should also be a relatively easy bug to knock out for anyone who wants to become familiar with rustbuild!",0,rustbuild dist on cross builds produce way too many tarballs the on cross builds takes over half an hour and that s a crazy amount of time for something which should take at most minutes the is massively duplicated namely we create around source tarballs looks like we re also packaging up the standard library dozens of times for the same target my guess as to what s happening is that by default rustbuild is doing a cross product of host x target and doing all the builds we should skip a massive number of them for distribution and ideally not even put them into the step list at all note that this isn t a fire at the moment as everything s just overwriting what was previously created but this sounds like something that could become a fire should also be a relatively easy bug to knock out for anyone who wants to become familiar with rustbuild ,0
+11105,13130760190.0,IssuesEvent,2020-08-06 15:51:17,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,support string convert to number in best effort during compare.,status/help-wanted type/compatibility,"1. What did you do?
+```
+CREATE TABLE `test3` (`id` int(11) DEFAULT NULL);
+CREATE TABLE `test4` (`k` varchar(3) DEFAULT NULL);
+
+insert into test3 values (1);
+insert into test4 values (""1-2"");
+
+select * from test3 a inner join test4 b on a.id = b.k;
+```
+
+
+2. What did you expect to see?
+
+```
+mysql> select * from test3 a inner join test4 b on a.id = b.k;
++------+------+
+| id | k |
++------+------+
+| 1 | 1-2 |
++------+------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+ERROR 1105 (HY000): strconv.ParseFloat: parsing ""1-2"": invalid syntax
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+| Release Version: v2.0.0
+Git Commit Hash: 637e130e6a9ba2e54e158131c0466233db39a60e
+Git Branch: release-2.0
+UTC Build Time: 2018-04-27 11:43:00
+GoVersion: go version go1.10 linux/amd64
+TiKV Min Version: 2.0.0-rc.4.1 |
+```
+",True,"support string convert to number in best effort during compare. - 1. What did you do?
+```
+CREATE TABLE `test3` (`id` int(11) DEFAULT NULL);
+CREATE TABLE `test4` (`k` varchar(3) DEFAULT NULL);
+
+insert into test3 values (1);
+insert into test4 values (""1-2"");
+
+select * from test3 a inner join test4 b on a.id = b.k;
+```
+
+
+2. What did you expect to see?
+
+```
+mysql> select * from test3 a inner join test4 b on a.id = b.k;
++------+------+
+| id | k |
++------+------+
+| 1 | 1-2 |
++------+------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+ERROR 1105 (HY000): strconv.ParseFloat: parsing ""1-2"": invalid syntax
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+| Release Version: v2.0.0
+Git Commit Hash: 637e130e6a9ba2e54e158131c0466233db39a60e
+Git Branch: release-2.0
+UTC Build Time: 2018-04-27 11:43:00
+GoVersion: go version go1.10 linux/amd64
+TiKV Min Version: 2.0.0-rc.4.1 |
+```
+",1,support string convert to number in best effort during compare what did you do create table id int default null create table k varchar default null insert into values insert into values select from a inner join b on a id b k what did you expect to see mysql select from a inner join b on a id b k id k row in set sec what did you see instead error strconv parsefloat parsing invalid syntax what version of tidb are you using tidb server v or run select tidb version on tidb release version git commit hash git branch release utc build time goversion go version linux tikv min version rc ,1
+16233,21796759895.0,IssuesEvent,2022-05-15 18:53:51,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,TiDB gives a different result with `SET GLOBAL table_open_cache=-1;` ,type/compatibility,"## Bug Report
+
+
+### 1. Minimal reproduce step
+```sql
+SET GLOBAL table_open_cache=-1;
+SHOW VARIABLES LIKE 'table_open_cache';
+```
+
+### 2. What did you expect to see?
+```sql
+mysql> SHOW VARIABLES LIKE 'table_open_cache';
++------------------+-------+
+| Variable_name | Value |
++------------------+-------+
+| table_open_cache | 1 |
++------------------+-------+
+1 row in set (0.03 sec)
+```
+
+### 3. What did you see instead
+```sql
+TiDB> SHOW VARIABLES LIKE 'table_open_cache';
++------------------+-------+
+| Variable_name | Value |
++------------------+-------+
+| table_open_cache | -1 |
++------------------+-------+
+1 row in set (0.01 sec)
+```
+
+### 4. What is your TiDB version?
+```sql
+tidb_version(): Release Version: v5.2.2
+Edition: Community
+Git Commit Hash: da1c21fd45a4ea5900ac16d2f4a248143f378d18
+Git Branch: heads/refs/tags/v5.2.2
+UTC Build Time: 2021-10-20 06:03:29
+GoVersion: go1.16.4
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+```
+
+",True,"TiDB gives a different result with `SET GLOBAL table_open_cache=-1;` - ## Bug Report
+
+
+### 1. Minimal reproduce step
+```sql
+SET GLOBAL table_open_cache=-1;
+SHOW VARIABLES LIKE 'table_open_cache';
+```
+
+### 2. What did you expect to see?
+```sql
+mysql> SHOW VARIABLES LIKE 'table_open_cache';
++------------------+-------+
+| Variable_name | Value |
++------------------+-------+
+| table_open_cache | 1 |
++------------------+-------+
+1 row in set (0.03 sec)
+```
+
+### 3. What did you see instead
+```sql
+TiDB> SHOW VARIABLES LIKE 'table_open_cache';
++------------------+-------+
+| Variable_name | Value |
++------------------+-------+
+| table_open_cache | -1 |
++------------------+-------+
+1 row in set (0.01 sec)
+```
+
+### 4. What is your TiDB version?
+```sql
+tidb_version(): Release Version: v5.2.2
+Edition: Community
+Git Commit Hash: da1c21fd45a4ea5900ac16d2f4a248143f378d18
+Git Branch: heads/refs/tags/v5.2.2
+UTC Build Time: 2021-10-20 06:03:29
+GoVersion: go1.16.4
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+```
+
+",1,tidb gives a different result with set global table open cache bug report minimal reproduce step sql set global table open cache show variables like table open cache what did you expect to see sql mysql show variables like table open cache variable name value table open cache row in set sec what did you see instead sql tidb show variables like table open cache variable name value table open cache row in set sec what is your tidb version sql tidb version release version edition community git commit hash git branch heads refs tags utc build time goversion race enabled false tikv min version check table before drop false ,1
+11070,13097298340.0,IssuesEvent,2020-08-03 17:12:02,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,The result of `show variables` is not compatible with MySQL,status/help-wanted type/compatibility type/duplicate,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+select @@global.sql_log_bin;
+show variables like ""sql_log_bin"";
+```
+
+2. What did you expect to see?
+Your MySQL connection id is 172
+Server version: 5.7.20 Homebrew
+```
+mysql> select @@global.sql_log_bin;
++----------------------+
+| @@global.sql_log_bin |
++----------------------+
+| 1 |
++----------------------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> show variables like ""sql_log_bin"";
++---------------+-------+
+| Variable_name | Value |
++---------------+-------+
+| sql_log_bin | ON |
++---------------+-------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+```
+tidb> select @@global.sql_log_bin;
++----------------------+
+| @@global.sql_log_bin |
++----------------------+
+| 1 |
++----------------------+
+1 row in set (0.00 sec)
+
+tidb> show variables like ""sql_log_bin"";
++---------------+-------+
+| Variable_name | Value |
++---------------+-------+
+| sql_log_bin | 1 |
++---------------+-------+
+1 row in set (0.02 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+Release Version: v3.0.0-beta-69-g84d1513b0-dirty
+Git Commit Hash: 84d1513b09222c60ffba2d3397b6745e5148a603
+Git Branch: master",True,"The result of `show variables` is not compatible with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+select @@global.sql_log_bin;
+show variables like ""sql_log_bin"";
+```
+
+2. What did you expect to see?
+Your MySQL connection id is 172
+Server version: 5.7.20 Homebrew
+```
+mysql> select @@global.sql_log_bin;
++----------------------+
+| @@global.sql_log_bin |
++----------------------+
+| 1 |
++----------------------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> show variables like ""sql_log_bin"";
++---------------+-------+
+| Variable_name | Value |
++---------------+-------+
+| sql_log_bin | ON |
++---------------+-------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+```
+tidb> select @@global.sql_log_bin;
++----------------------+
+| @@global.sql_log_bin |
++----------------------+
+| 1 |
++----------------------+
+1 row in set (0.00 sec)
+
+tidb> show variables like ""sql_log_bin"";
++---------------+-------+
+| Variable_name | Value |
++---------------+-------+
+| sql_log_bin | 1 |
++---------------+-------+
+1 row in set (0.02 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+Release Version: v3.0.0-beta-69-g84d1513b0-dirty
+Git Commit Hash: 84d1513b09222c60ffba2d3397b6745e5148a603
+Git Branch: master",1,the result of show variables is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error select global sql log bin show variables like sql log bin what did you expect to see your mysql connection id is server version homebrew mysql select global sql log bin global sql log bin row in set warning sec mysql show variables like sql log bin variable name value sql log bin on row in set sec what did you see instead tidb select global sql log bin global sql log bin row in set sec tidb show variables like sql log bin variable name value sql log bin row in set sec what version of tidb are you using tidb server v or run select tidb version on tidb release version beta dirty git commit hash git branch master,1
+136366,11047445288.0,IssuesEvent,2019-12-09 18:59:23,dexpenses/dexpenses-extract,https://api.github.com/repos/dexpenses/dexpenses-extract,closed,Implement test receipt normal/dransfeld-rewe-debit,enhancement test-data,"Receipt to implement:
+",1.0,"Implement test receipt normal/dransfeld-rewe-debit - Receipt to implement:
+",0,implement test receipt normal dransfeld rewe debit receipt to implement normal dransfeld rewe debit ,0
+7181,9473698991.0,IssuesEvent,2019-04-19 03:23:17,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,not support show open table ,help wanted type/compatibility,"## Bug Report
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+I use heidisql, and meet error caused by unsupported `show open tables` command.
+
+
+2. What did you expect to see?
+
+no error
+
+3. What did you see instead?
+
+```
+ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your TiDB version for the right syntax to use line 1 column 9 near ""OPEN TABLES""
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+",True,"not support show open table - ## Bug Report
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+I use heidisql, and meet error caused by unsupported `show open tables` command.
+
+
+2. What did you expect to see?
+
+no error
+
+3. What did you see instead?
+
+```
+ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your TiDB version for the right syntax to use line 1 column 9 near ""OPEN TABLES""
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+",1,not support show open table bug report what did you do if possible provide a recipe for reproducing the error i use heidisql and meet error caused by unsupported show open tables command what did you expect to see no error what did you see instead error you have an error in your sql syntax check the manual that corresponds to your tidb version for the right syntax to use line column near open tables what version of tidb are you using tidb server v or run select tidb version on tidb ,1
+3637,6524200471.0,IssuesEvent,2017-08-29 11:45:09,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Incorrect Decimal inference for float literal,bug compatibility for-new-contributors help wanted,"MySQL:
+
+```
+mysql> SELECT 151113102019e0;
+Field 1: `151113102019e0`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: DOUBLE
+Collation: binary (63)
+Length: 14
+Max_length: 12
+Decimals: 31
+Flags: NOT_NULL BINARY NUM
+
+
++----------------+
+| 151113102019e0 |
++----------------+
+| 151113102019 |
++----------------+
+1 row in set (0.00 sec)
+
+mysql> SELECT 15111310201912e-2;
+Field 1: `15111310201912e-2`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: DOUBLE
+Collation: binary (63)
+Length: 17
+Max_length: 15
+Decimals: 31
+Flags: NOT_NULL BINARY NUM
+
+
++-------------------+
+| 15111310201912e-2 |
++-------------------+
+| 151113102019.12 |
++-------------------+
+1 row in set (0.00 sec)
+```
+
+TiDB:
+
+```
+mysql> SELECT 151113102019e0;
+Field 1: `151113102019e0`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: DOUBLE
+Collation: binary (63)
+Length: 12
+Max_length: 25
+Decimals: 12
+Flags: BINARY NUM
+
+
++---------------------------+
+| 151113102019e0 |
++---------------------------+
+| 151113102019.000000000000 |
++---------------------------+
+1 row in set (0.00 sec)
+
+mysql> SELECT 15111310201912e-2;
+Field 1: `15111310201912e-2`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: DOUBLE
+Collation: binary (63)
+Length: 15
+Max_length: 15
+Decimals: 2
+Flags: BINARY NUM
+
+
++-------------------+
+| 15111310201912e-2 |
++-------------------+
+| 151113102019.12 |
++-------------------+
+1 row in set (0.00 sec)
+```",True,"Incorrect Decimal inference for float literal - MySQL:
+
+```
+mysql> SELECT 151113102019e0;
+Field 1: `151113102019e0`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: DOUBLE
+Collation: binary (63)
+Length: 14
+Max_length: 12
+Decimals: 31
+Flags: NOT_NULL BINARY NUM
+
+
++----------------+
+| 151113102019e0 |
++----------------+
+| 151113102019 |
++----------------+
+1 row in set (0.00 sec)
+
+mysql> SELECT 15111310201912e-2;
+Field 1: `15111310201912e-2`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: DOUBLE
+Collation: binary (63)
+Length: 17
+Max_length: 15
+Decimals: 31
+Flags: NOT_NULL BINARY NUM
+
+
++-------------------+
+| 15111310201912e-2 |
++-------------------+
+| 151113102019.12 |
++-------------------+
+1 row in set (0.00 sec)
+```
+
+TiDB:
+
+```
+mysql> SELECT 151113102019e0;
+Field 1: `151113102019e0`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: DOUBLE
+Collation: binary (63)
+Length: 12
+Max_length: 25
+Decimals: 12
+Flags: BINARY NUM
+
+
++---------------------------+
+| 151113102019e0 |
++---------------------------+
+| 151113102019.000000000000 |
++---------------------------+
+1 row in set (0.00 sec)
+
+mysql> SELECT 15111310201912e-2;
+Field 1: `15111310201912e-2`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: DOUBLE
+Collation: binary (63)
+Length: 15
+Max_length: 15
+Decimals: 2
+Flags: BINARY NUM
+
+
++-------------------+
+| 15111310201912e-2 |
++-------------------+
+| 151113102019.12 |
++-------------------+
+1 row in set (0.00 sec)
+```",1,incorrect decimal inference for float literal mysql mysql select field catalog def database table org table type double collation binary length max length decimals flags not null binary num row in set sec mysql select field catalog def database table org table type double collation binary length max length decimals flags not null binary num row in set sec tidb mysql select field catalog def database table org table type double collation binary length max length decimals flags binary num row in set sec mysql select field catalog def database table org table type double collation binary length max length decimals flags binary num row in set sec ,1
+7853,10062951627.0,IssuesEvent,2019-07-23 03:29:31,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,alter database syntax support.,type/compatibility,"TiDB:
+
+```
+mysql> alter database test1 character set utf8 COLLATE uft8_general_ci;
+ERROR 1105 (HY000): line 0 column 14 near "" test1 character set utf8 COLLATE uft8_general_ci"" (total length 63)
+mysql> alter database test1 character set utf8 COLLATE uft8_general_ci;
+ERROR 1105 (HY000): line 0 column 14 near "" test1 character set utf8 COLLATE uft8_general_ci"" (total length 63)
+```
+
+see https://dev.mysql.com/doc/refman/5.7/en/alter-database.html",True,"alter database syntax support. - TiDB:
+
+```
+mysql> alter database test1 character set utf8 COLLATE uft8_general_ci;
+ERROR 1105 (HY000): line 0 column 14 near "" test1 character set utf8 COLLATE uft8_general_ci"" (total length 63)
+mysql> alter database test1 character set utf8 COLLATE uft8_general_ci;
+ERROR 1105 (HY000): line 0 column 14 near "" test1 character set utf8 COLLATE uft8_general_ci"" (total length 63)
+```
+
+see https://dev.mysql.com/doc/refman/5.7/en/alter-database.html",1,alter database syntax support tidb mysql alter database character set collate general ci error line column near character set collate general ci total length mysql alter database character set collate general ci error line column near character set collate general ci total length see ,1
+18496,25582848919.0,IssuesEvent,2022-12-01 06:40:03,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,BR: 6.2.0 system table mysql.user can't be restored to 6.4.0,type/bug compatibility-breaker severity/critical component/br affects-6.2 affects-6.3 affects-6.4,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+tidb changed mysql.user schema in 6.4.0
+version95 add a column `User_attributes` to `mysql.user`
+version98 add a column `Token_issuer` to `mysql.user`
+
+when restore 6.2.0 mysql.user to 6.4.0 will report :
+Error: column count mismatch, table: user, col in cluster: 38, col in backup: 37: [BR:Restore:ErrR
+
+### 2. What did you expect to see? (Required)
+restore success
+### 3. What did you see instead (Required)
+Error: column count mismatch, table: user, col in cluster: 38, col in backup: 37: [BR:Restore:ErrR
+### 4. What is your TiDB version? (Required)
+
+master
+
+",True,"BR: 6.2.0 system table mysql.user can't be restored to 6.4.0 - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+tidb changed mysql.user schema in 6.4.0
+version95 add a column `User_attributes` to `mysql.user`
+version98 add a column `Token_issuer` to `mysql.user`
+
+when restore 6.2.0 mysql.user to 6.4.0 will report :
+Error: column count mismatch, table: user, col in cluster: 38, col in backup: 37: [BR:Restore:ErrR
+
+### 2. What did you expect to see? (Required)
+restore success
+### 3. What did you see instead (Required)
+Error: column count mismatch, table: user, col in cluster: 38, col in backup: 37: [BR:Restore:ErrR
+### 4. What is your TiDB version? (Required)
+
+master
+
+",1,br system table mysql user can t be restored to bug report please answer these questions before submitting your issue thanks minimal reproduce step required tidb changed mysql user schema in add a column user attributes to mysql user add a column token issuer to mysql user when restore mysql user to will report error column count mismatch table user col in cluster col in backup br restore errr what did you expect to see required restore success what did you see instead required error column count mismatch table user col in cluster col in backup br restore errr what is your tidb version required master ,1
+237379,18158501210.0,IssuesEvent,2021-09-27 06:44:44,aravindm711/ESNSE,https://api.github.com/repos/aravindm711/ESNSE,opened,Abstract for search engine,documentation,"Things to be done,
+- Problem statement
+- Goals
+- Implementation
+- Tools and technologies
+",1.0,"Abstract for search engine - Things to be done,
+- Problem statement
+- Goals
+- Implementation
+- Tools and technologies
+",0,abstract for search engine things to be done problem statement goals implementation tools and technologies ,0
+230317,7606824554.0,IssuesEvent,2018-04-30 14:36:10,openshiftio/openshift.io,https://api.github.com/repos/openshiftio/openshift.io,closed,Some user accounts are seeing a continuous stream of - f8osoproxy 401 errors,SEV2-high area/auth priority/P0 team/auth type/bug,"This problem started on my user account on April 27. After logging in, I was unable to create a new quickstart.
+
+The Chrome console showed a continuous stream of these errors:
+```
+WebSocket connection to 'wss://f8osoproxy-test-dsaas-
+production.09b5.dsaas.openshiftapps.com/oapi/v1/namespaces/ldimaggi/builds?
+watch=true&access_token=...' failed: HTTP Authentication failed; no valid credentials available
+```
+NOTE: In the above example - I removed the text of the token and username.
+
+The resolution for the problem was to refresh the OpenShift Online connection:
+
+
+The cause for the problem is unclear - is this happening to older accounts because a token is expiring? My account was created on: 2017-04-24
+
+
+
+",1.0,"Some user accounts are seeing a continuous stream of - f8osoproxy 401 errors - This problem started on my user account on April 27. After logging in, I was unable to create a new quickstart.
+
+The Chrome console showed a continuous stream of these errors:
+```
+WebSocket connection to 'wss://f8osoproxy-test-dsaas-
+production.09b5.dsaas.openshiftapps.com/oapi/v1/namespaces/ldimaggi/builds?
+watch=true&access_token=...' failed: HTTP Authentication failed; no valid credentials available
+```
+NOTE: In the above example - I removed the text of the token and username.
+
+The resolution for the problem was to refresh the OpenShift Online connection:
+
+
+The cause for the problem is unclear - is this happening to older accounts because a token is expiring? My account was created on: 2017-04-24
+
+
+
+",0,some user accounts are seeing a continuous stream of errors this problem started on my user account on april after logging in i was unable to create a new quickstart the chrome console showed a continuous stream of these errors websocket connection to wss test dsaas production dsaas openshiftapps com oapi namespaces ldimaggi builds watch true access token failed http authentication failed no valid credentials available note in the above example i removed the text of the token and username the resolution for the problem was to refresh the openshift online connection the cause for the problem is unclear is this happening to older accounts because a token is expiring my account was created on ,0
+86695,8047419660.0,IssuesEvent,2018-08-01 00:33:38,ipfs/go-ipfs,https://api.github.com/repos/ipfs/go-ipfs,closed,`foofoo.block` has more links than UnixFS `Blocksizes`,testing,"I'm refactoring the DAG reader (https://github.com/ipfs/go-ipfs/pull/5257) and I'm having an [error](https://github.com/ipfs/go-ipfs/pull/5257/files#diff-0046ca7d126fec814fde6c7ffc49ab0dR277) in the test file [`t0110-gateway.sh`](https://github.com/ipfs/go-ipfs/blob/e71dce5dfba3616e5ade4abf0844925389497a56/test/sharness/t0110-gateway.sh#L164) where the [`foofoo.block`](https://github.com/ipfs/go-ipfs/blob/e71dce5dfba3616e5ade4abf0844925389497a56/test/sharness/t0110-gateway.sh#L160) file, which is saved as a block and retrieved as a file DAG through the gateway, would appear to have an inconsistency between its number of DAG links and its number of UnixFS `Blocksizes`, is this expected in the test? If not, how could I regenerate that file with the UnixFS format fixed?
+
+/cc @magik6k ",1.0,"`foofoo.block` has more links than UnixFS `Blocksizes` - I'm refactoring the DAG reader (https://github.com/ipfs/go-ipfs/pull/5257) and I'm having an [error](https://github.com/ipfs/go-ipfs/pull/5257/files#diff-0046ca7d126fec814fde6c7ffc49ab0dR277) in the test file [`t0110-gateway.sh`](https://github.com/ipfs/go-ipfs/blob/e71dce5dfba3616e5ade4abf0844925389497a56/test/sharness/t0110-gateway.sh#L164) where the [`foofoo.block`](https://github.com/ipfs/go-ipfs/blob/e71dce5dfba3616e5ade4abf0844925389497a56/test/sharness/t0110-gateway.sh#L160) file, which is saved as a block and retrieved as a file DAG through the gateway, would appear to have an inconsistency between its number of DAG links and its number of UnixFS `Blocksizes`, is this expected in the test? If not, how could I regenerate that file with the UnixFS format fixed?
+
+/cc @magik6k ",0, foofoo block has more links than unixfs blocksizes i m refactoring the dag reader and i m having an in the test file where the file which is saved as a block and retrieved as a file dag through the gateway would appear to have an inconsistency between its number of dag links and its number of unixfs blocksizes is this expected in the test if not how could i regenerate that file with the unixfs format fixed cc ,0
+11080,13100718142.0,IssuesEvent,2020-08-04 01:27:46,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,The result of Function COALESCE is different from MySQL. ,component/expression status/help-wanted type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```mysql
+create table test2 ( a decimal(40,20) unsigned);
+insert into test2 value(12.98731000000000000000);
+select cast(COALESCE(a, 'xxx' ) as unsigned) from test2;
+```
+
+2. What did you expect to see?
+
+In MySQL,
+```mysql
+mysql> select cast(COALESCE(a, 'xxx' ) as unsigned) from test2;
++---------------------------------------+
+| cast(COALESCE(a, 'xxx' ) as unsigned) |
++---------------------------------------+
+| 12 |
++---------------------------------------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> show warnings;
++---------+------+--------------------------------------------------------------+
+| Level | Code | Message |
++---------+------+--------------------------------------------------------------+
+| Warning | 1292 | Truncated incorrect INTEGER value: '12.98731000000000000000' |
++---------+------+--------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+In TiDB,
+```mysql
+mysql> select cast(COALESCE(a, 'xxx' ) as unsigned) from test2;
++---------------------------------------+
+| cast(COALESCE(a, 'xxx' ) as unsigned) |
++---------------------------------------+
+| 13 |
++---------------------------------------+
+1 row in set (0.01 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+8c20289c7",True,"The result of Function COALESCE is different from MySQL. - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```mysql
+create table test2 ( a decimal(40,20) unsigned);
+insert into test2 value(12.98731000000000000000);
+select cast(COALESCE(a, 'xxx' ) as unsigned) from test2;
+```
+
+2. What did you expect to see?
+
+In MySQL,
+```mysql
+mysql> select cast(COALESCE(a, 'xxx' ) as unsigned) from test2;
++---------------------------------------+
+| cast(COALESCE(a, 'xxx' ) as unsigned) |
++---------------------------------------+
+| 12 |
++---------------------------------------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> show warnings;
++---------+------+--------------------------------------------------------------+
+| Level | Code | Message |
++---------+------+--------------------------------------------------------------+
+| Warning | 1292 | Truncated incorrect INTEGER value: '12.98731000000000000000' |
++---------+------+--------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+In TiDB,
+```mysql
+mysql> select cast(COALESCE(a, 'xxx' ) as unsigned) from test2;
++---------------------------------------+
+| cast(COALESCE(a, 'xxx' ) as unsigned) |
++---------------------------------------+
+| 13 |
++---------------------------------------+
+1 row in set (0.01 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+8c20289c7",1,the result of function coalesce is different from mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error mysql create table a decimal unsigned insert into value select cast coalesce a xxx as unsigned from what did you expect to see in mysql mysql mysql select cast coalesce a xxx as unsigned from cast coalesce a xxx as unsigned row in set warning sec mysql show warnings level code message warning truncated incorrect integer value row in set sec what did you see instead in tidb mysql mysql select cast coalesce a xxx as unsigned from cast coalesce a xxx as unsigned row in set sec what version of tidb are you using tidb server v or run select tidb version on tidb ,1
+665237,22304417143.0,IssuesEvent,2022-06-13 11:45:18,ICST-Technion/WelliBe,https://api.github.com/repos/ICST-Technion/WelliBe,closed,Create a page where the user can send thank you notes to its doctors,medium priority feature,slides 16-20 in the presentation.,1.0,Create a page where the user can send thank you notes to its doctors - slides 16-20 in the presentation.,0,create a page where the user can send thank you notes to its doctors slides in the presentation ,0
+143939,22205566780.0,IssuesEvent,2022-06-07 14:37:38,patternfly/patternfly-org,https://api.github.com/repos/patternfly/patternfly-org,opened,Create guidelines for the Panel component,PF4 design Guidelines,"https://www.patternfly.org/v4/components/panel/design-guidelines
-
-
+Add guidelines including:
+- what is a panel
+- when to use a panel
+- examples of panel in use
-
+Also mention that it works with the primary detail component, selectable tables etc....",1.0,"Create guidelines for the Panel component - https://www.patternfly.org/v4/components/panel/design-guidelines
-### Vulnerability Details
-
-
-ASP.NET Core 1.0. 1.1, and 2.0 allow an elevation of privilege vulnerability due to how ASP.NET web applications handle web requests, aka ""ASP.NET Core Elevation Of Privilege Vulnerability"". This CVE is unique from CVE-2018-0784.
+Add guidelines including:
+- what is a panel
+- when to use a panel
+- examples of panel in use
-
-
+Also mention that it works with the primary detail component, selectable tables etc....",0,create guidelines for the panel component add guidelines including what is a panel when to use a panel examples of panel in use also mention that it works with the primary detail component selectable tables etc ,0
+184976,14291776599.0,IssuesEvent,2020-11-23 23:25:29,github-vet/rangeclosure-findings,https://api.github.com/repos/github-vet/rangeclosure-findings,closed,tuuuz/etcd: tests/integration/clientv3/txn_test.go; 23 LoC,fresh small test,"
+Found a possible issue in [tuuuz/etcd](https://www.github.com/tuuuz/etcd) at [tests/integration/clientv3/txn_test.go](https://github.com/tuuuz/etcd/blob/31a1226ec4edcd20180090f9a45250f29331bf89/tests/integration/clientv3/txn_test.go#L118-L140)
-
+The below snippet of Go code triggered static analysis which searches for goroutines and/or defer statements
+which capture loop variables.
-### CVSS 3 Score Details (7.5)
-
+[Click here to see the code in its original context.](https://github.com/tuuuz/etcd/blob/31a1226ec4edcd20180090f9a45250f29331bf89/tests/integration/clientv3/txn_test.go#L118-L140)
-Base Score Metrics:
-- Exploitability Metrics:
- - Attack Vector: Network
- - Attack Complexity: Low
- - Privileges Required: None
- - User Interaction: None
- - Scope: Unchanged
-- Impact Metrics:
- - Confidentiality Impact: None
- - Integrity Impact: None
- - Availability Impact: High
-
-For more information on CVSS3 Scores, click here.
-
+
+Click here to show the 23 line(s) of Go which triggered the analyzer.
-
+```go
+ for i := range thenOps {
+ clus.Members[0].Stop(t)
+ <-clus.Members[0].StopNotify()
-### Suggested Fix
-
+ donec := make(chan struct{}, 1)
+ go func() {
+ _, err := kv.Txn(context.TODO()).Then(thenOps[i]...).Commit()
+ if err != nil {
+ t.Errorf(""expected response, got error %v"", err)
+ }
+ donec <- struct{}{}
+ }()
+ // wait for txn to fail on disconnect
+ time.Sleep(100 * time.Millisecond)
-
+ // restart node; client should resume
+ clus.Members[0].Restart(t)
+ select {
+ case <-donec:
+ case <-time.After(2 * clus.Members[1].ServerConfig.ReqTimeout()):
+ t.Fatalf(""waited too long"")
+ }
+ }
-
+```
+
-
+Leave a reaction on this issue to contribute to the project by classifying this instance as a **Bug** :-1:, **Mitigated** :+1:, or **Desirable Behavior** :rocket:
+See the descriptions of the classifications [here](https://github.com/github-vet/rangeclosure-findings#how-can-i-help) for more information.
-
+commit ID: 31a1226ec4edcd20180090f9a45250f29331bf89
+",1.0,"tuuuz/etcd: tests/integration/clientv3/txn_test.go; 23 LoC -
+Found a possible issue in [tuuuz/etcd](https://www.github.com/tuuuz/etcd) at [tests/integration/clientv3/txn_test.go](https://github.com/tuuuz/etcd/blob/31a1226ec4edcd20180090f9a45250f29331bf89/tests/integration/clientv3/txn_test.go#L118-L140)
- WS-2018-0607
+The below snippet of Go code triggered static analysis which searches for goroutines and/or defer statements
+which capture loop variables.
+[Click here to see the code in its original context.](https://github.com/tuuuz/etcd/blob/31a1226ec4edcd20180090f9a45250f29331bf89/tests/integration/clientv3/txn_test.go#L118-L140)
-### Vulnerable Library - microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
+
+Click here to show the 23 line(s) of Go which triggered the analyzer.
-
Core components of ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
+```go
+ for i := range thenOps {
+ clus.Members[0].Stop(t)
+ <-clus.Members[0].StopNotify()
+
+ donec := make(chan struct{}, 1)
+ go func() {
+ _, err := kv.Txn(context.TODO()).Then(thenOps[i]...).Commit()
+ if err != nil {
+ t.Errorf(""expected response, got error %v"", err)
+ }
+ donec <- struct{}{}
+ }()
+ // wait for txn to fail on disconnect
+ time.Sleep(100 * time.Millisecond)
+
+ // restart node; client should resume
+ clus.Members[0].Restart(t)
+ select {
+ case <-donec:
+ case <-time.After(2 * clus.Members[1].ServerConfig.ReqTimeout()):
+ t.Fatalf(""waited too long"")
+ }
+ }
+
+```
+
+
+Leave a reaction on this issue to contribute to the project by classifying this instance as a **Bug** :-1:, **Mitigated** :+1:, or **Desirable Behavior** :rocket:
+See the descriptions of the classifications [here](https://github.com/github-vet/rangeclosure-findings#how-can-i-help) for more information.
+
+commit ID: 31a1226ec4edcd20180090f9a45250f29331bf89
+",0,tuuuz etcd tests integration txn test go loc found a possible issue in at the below snippet of go code triggered static analysis which searches for goroutines and or defer statements which capture loop variables click here to show the line s of go which triggered the analyzer go for i range thenops clus members stop t clus members stopnotify donec make chan struct go func err kv txn context todo then thenops commit if err nil t errorf expected response got error v err donec struct wait for txn to fail on disconnect time sleep time millisecond restart node client should resume clus members restart t select case donec case time after clus members serverconfig reqtimeout t fatalf waited too long leave a reaction on this issue to contribute to the project by classifying this instance as a bug mitigated or desirable behavior rocket see the descriptions of the classifications for more information commit id ,0
+326279,9954632773.0,IssuesEvent,2019-07-05 08:55:11,canonical-web-and-design/vanilla-framework,https://api.github.com/repos/canonical-web-and-design/vanilla-framework,closed,[Docs] Remove p-icon--chevron from the icon list,Priority: Medium,"## Bug
+- Remove `p-icon--chevron` from the icon list. Currently, it's an empty state as it's been updated to be used as `p-icon--contextual-menu`
+- Remove both use-cases under [standard](https://docs.vanillaframework.io/patterns/icons/#standard) and [standard dark](https://docs.vanillaframework.io/patterns/icons/#standard-dark)
+
+### Screenshot
+
+",1.0,"[Docs] Remove p-icon--chevron from the icon list - ## Bug
+- Remove `p-icon--chevron` from the icon list. Currently, it's an empty state as it's been updated to be used as `p-icon--contextual-menu`
+- Remove both use-cases under [standard](https://docs.vanillaframework.io/patterns/icons/#standard) and [standard dark](https://docs.vanillaframework.io/patterns/icons/#standard-dark)
+
+### Screenshot
+
+",0, remove p icon chevron from the icon list bug remove p icon chevron from the icon list currently it s an empty state as it s been updated to be used as p icon contextual menu remove both use cases under and screenshot img width alt screenshot at src ,0
+8328,2981466910.0,IssuesEvent,2015-07-17 01:26:15,Azure/azure-xplat-cli,https://api.github.com/repos/Azure/azure-xplat-cli,closed,ASM: VM correcting endpoint parameter names,ASM IAAS Ready For Test,"The parameters for the 'vm endpoint' commands should be consistent with portal & power shell.
+
+The parameter 'lb-port' should renamed to 'public-port'
+The parameter 'vm-port' should be renamed to 'local-port' or private-port
+",1.0,"ASM: VM correcting endpoint parameter names - The parameters for the 'vm endpoint' commands should be consistent with portal & power shell.
+
+The parameter 'lb-port' should renamed to 'public-port'
+The parameter 'vm-port' should be renamed to 'local-port' or private-port
+",0,asm vm correcting endpoint parameter names the parameters for the vm endpoint commands should be consistent with portal power shell the parameter lb port should renamed to public port the parameter vm port should be renamed to local port or private port ,0
+5830,4019901221.0,IssuesEvent,2016-05-16 16:29:07,minuscode/minuscode.github.io,https://api.github.com/repos/minuscode/minuscode.github.io,closed,Insufficient differentiation for active work filter,accessibility usability,"Active work filter doesn't have enough visual differentiation.
+It used #932a3a instead of the default #c94055
+
+For a perceptible differentiation we need both a change on color and form.
+
+",True,"Insufficient differentiation for active work filter - Active work filter doesn't have enough visual differentiation.
+It used #932a3a instead of the default #c94055
+
+For a perceptible differentiation we need both a change on color and form.
+
+",0,insufficient differentiation for active work filter active work filter doesn t have enough visual differentiation it used instead of the default for a perceptible differentiation we need both a change on color and form ,0
+56320,11569837202.0,IssuesEvent,2020-02-20 18:20:29,joomla/joomla-cms,https://api.github.com/repos/joomla/joomla-cms,closed,"[4] Save failed with the following error: Joomla\Component\Finder\Administrator\Table\MapTable::_getNode(1, id) failed.",Information Required No Code Attached Yet,"### Steps to reproduce the issue
+Backend try to save an article
+
+
+### Actual result
+The article is saved but there is a warn message
+
+
+### System information (as much as possible)
+Joomla 4 beta1-dev (nightly build)
+
+
+### error
+Save failed with the following error: Joomla\Component\Finder\Administrator\Table\MapTable::_getNode(1, id) failed.
+",1.0,"[4] Save failed with the following error: Joomla\Component\Finder\Administrator\Table\MapTable::_getNode(1, id) failed. - ### Steps to reproduce the issue
+Backend try to save an article
+
+
+### Actual result
+The article is saved but there is a warn message
+
+
+### System information (as much as possible)
+Joomla 4 beta1-dev (nightly build)
+
+
+### error
+Save failed with the following error: Joomla\Component\Finder\Administrator\Table\MapTable::_getNode(1, id) failed.
+",0, save failed with the following error joomla component finder administrator table maptable getnode id failed steps to reproduce the issue backend try to save an article actual result the article is saved but there is a warn message system information as much as possible joomla dev nightly build error save failed with the following error joomla component finder administrator table maptable getnode id failed ,0
+324036,23980397257.0,IssuesEvent,2022-09-13 14:39:41,MetroStar/ib_manifest_util,https://api.github.com/repos/MetroStar/ib_manifest_util,opened,[META] Fill out documentation pages,impact: high area: documentation 📖,"## Summary
+
+Need docs for:
+* [ ] update repo
+* [ ] download packages
+
+## Related to
+
+#37 must be merged first
+",1.0,"[META] Fill out documentation pages - ## Summary
+
+Need docs for:
+* [ ] update repo
+* [ ] download packages
+
+## Related to
+
+#37 must be merged first
+",0, fill out documentation pages summary need docs for update repo download packages related to must be merged first ,0
+5069,7669083261.0,IssuesEvent,2018-05-14 08:31:41,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Different results from MySQL and tidb,compatibility,"1. What did you do?
+Execute the statement: `select 1, 2, 3 from dual union select * from t limit 1 offset 2;`.
+
+
+2. What did you expect to see?
+http://sqlfiddle.com/#!9/ce0a4a/1
+
+3. What did you see instead?
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+Release Version: v2.0.0-rc.1
+Git Commit Hash: 4a52a6ae580224a62b2c17707e64720af26c88fd
+Git Branch: release-2.0
+UTC Build Time: 2018-03-09 02:12:41
+GoVersion: go version go1.10 linux/amd64
+TiKV Min Version: 1.1.0-dev.2
+```
+",True,"Different results from MySQL and tidb - 1. What did you do?
+Execute the statement: `select 1, 2, 3 from dual union select * from t limit 1 offset 2;`.
+
+
+2. What did you expect to see?
+http://sqlfiddle.com/#!9/ce0a4a/1
+
+3. What did you see instead?
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+Release Version: v2.0.0-rc.1
+Git Commit Hash: 4a52a6ae580224a62b2c17707e64720af26c88fd
+Git Branch: release-2.0
+UTC Build Time: 2018-03-09 02:12:41
+GoVersion: go version go1.10 linux/amd64
+TiKV Min Version: 1.1.0-dev.2
+```
+",1,different results from mysql and tidb what did you do execute the statement select from dual union select from t limit offset what did you expect to see what did you see instead what version of tidb are you using tidb server v or run select tidb version on tidb release version rc git commit hash git branch release utc build time goversion go version linux tikv min version dev ,1
+6247,8641062532.0,IssuesEvent,2018-11-24 13:49:57,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Incorrect CEIL/FLOOR infer type,type/compatibility,"```mysql
+create table t (
+ c_int int,
+ c_int_unsigned int unsigned,
+ c_bigint bigint,
+ c_bigint_unsigned bigint unsigned,
+ c_float float,
+ c_float_unsigned float unsigned,
+ c_double double,
+ c_double_unsigned double unsigned,
+ c_decimal decimal(6, 3),
+ c_decimal_unsigned decimal(10, 3) unsigned,
+ c_datetime datetime(2),
+ c_time time,
+ c_timestamp timestamp,
+ c_char char(20),
+ c_char_binary char(20) binary,
+ c_varchar varchar(20),
+ c_varchar_binary varchar(20) binary,
+ c_binary binary(20),
+ c_varbinary varbinary(20),
+ c_text text,
+ c_blob blob,
+ c_text_binary text binary,
+ c_set set('a', 'b', 'c'),
+ c_enum enum('a', 'b', 'c'));
+
+SELECT FLOOR(c_int), FLOOR(c_int_unsigned), FLOOR(c_bigint), FLOOR(c_bigint_unsigned), FLOOR(c_float), FLOOR(c_float_unsigned), FLOOR(c_double), FLOOR(c_double_unsigned), FLOOR(c_decimal), FLOOR(c_decimal_unsigned), FLOOR(c_datetime), FLOOR(c_time), FLOOR(c_timestamp), FLOOR(c_char), FLOOR(c_char_binary), FLOOR(c_varchar), FLOOR(c_varchar_binary), FLOOR(c_binary), FLOOR(c_varbinary), FLOOR(c_text), FLOOR(c_blob), FLOOR(c_text_binary), FLOOR(c_set), FLOOR(c_enum) FROM t;
+```
+
+```diff
+--- diff-mysql.txt 2017-08-10 16:26:03.000000000 +0800
++++ diff-tidb.txt 2017-08-10 16:26:38.000000000 +0800
+@@ -1,290 +1,290 @@
+ Field 1: `FLOOR(c_int)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: LONGLONG
+ Collation: binary (63)
+-Length: 13
++Length: 11
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 2: `FLOOR(c_int_unsigned)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+-Type: LONGLONG
++Type: NEWDECIMAL
+ Collation: binary (63)
+-Length: 12
++Length: 11
+ Max_length: 0
+ Decimals: 0
+-Flags: UNSIGNED BINARY NUM
++Flags: BINARY NUM
+
+ Field 3: `FLOOR(c_bigint)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+-Type: NEWDECIMAL
++Type: LONGLONG
+ Collation: binary (63)
+-Length: 17
++Length: 21
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 4: `FLOOR(c_bigint_unsigned)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: NEWDECIMAL
+ Collation: binary (63)
+-Length: 17
++Length: 21
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 5: `FLOOR(c_float)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 0
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 6: `FLOOR(c_float_unsigned)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 0
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 7: `FLOOR(c_double)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 0
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 8: `FLOOR(c_double_unsigned)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 0
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 9: `FLOOR(c_decimal)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: LONGLONG
+ Collation: binary (63)
+ Length: 6
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 10: `FLOOR(c_decimal_unsigned)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: LONGLONG
+ Collation: binary (63)
+-Length: 9
++Length: 10
+ Max_length: 0
+ Decimals: 0
+-Flags: UNSIGNED BINARY NUM
++Flags: BINARY NUM
+
+ Field 11: `FLOOR(c_datetime)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 12: `FLOOR(c_time)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 13: `FLOOR(c_timestamp)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+-Flags: NOT_NULL BINARY NUM
++Flags: BINARY NUM
+
+ Field 14: `FLOOR(c_char)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 15: `FLOOR(c_char_binary)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 16: `FLOOR(c_varchar)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 17: `FLOOR(c_varchar_binary)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 18: `FLOOR(c_binary)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 19: `FLOOR(c_varbinary)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 20: `FLOOR(c_text)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 21: `FLOOR(c_blob)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 22: `FLOOR(c_text_binary)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 23: `FLOOR(c_set)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 24: `FLOOR(c_enum)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+
+ 0 rows in set (0.00 sec)
+
+```",True,"Incorrect CEIL/FLOOR infer type - ```mysql
+create table t (
+ c_int int,
+ c_int_unsigned int unsigned,
+ c_bigint bigint,
+ c_bigint_unsigned bigint unsigned,
+ c_float float,
+ c_float_unsigned float unsigned,
+ c_double double,
+ c_double_unsigned double unsigned,
+ c_decimal decimal(6, 3),
+ c_decimal_unsigned decimal(10, 3) unsigned,
+ c_datetime datetime(2),
+ c_time time,
+ c_timestamp timestamp,
+ c_char char(20),
+ c_char_binary char(20) binary,
+ c_varchar varchar(20),
+ c_varchar_binary varchar(20) binary,
+ c_binary binary(20),
+ c_varbinary varbinary(20),
+ c_text text,
+ c_blob blob,
+ c_text_binary text binary,
+ c_set set('a', 'b', 'c'),
+ c_enum enum('a', 'b', 'c'));
+
+SELECT FLOOR(c_int), FLOOR(c_int_unsigned), FLOOR(c_bigint), FLOOR(c_bigint_unsigned), FLOOR(c_float), FLOOR(c_float_unsigned), FLOOR(c_double), FLOOR(c_double_unsigned), FLOOR(c_decimal), FLOOR(c_decimal_unsigned), FLOOR(c_datetime), FLOOR(c_time), FLOOR(c_timestamp), FLOOR(c_char), FLOOR(c_char_binary), FLOOR(c_varchar), FLOOR(c_varchar_binary), FLOOR(c_binary), FLOOR(c_varbinary), FLOOR(c_text), FLOOR(c_blob), FLOOR(c_text_binary), FLOOR(c_set), FLOOR(c_enum) FROM t;
+```
+
+```diff
+--- diff-mysql.txt 2017-08-10 16:26:03.000000000 +0800
++++ diff-tidb.txt 2017-08-10 16:26:38.000000000 +0800
+@@ -1,290 +1,290 @@
+ Field 1: `FLOOR(c_int)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: LONGLONG
+ Collation: binary (63)
+-Length: 13
++Length: 11
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 2: `FLOOR(c_int_unsigned)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+-Type: LONGLONG
++Type: NEWDECIMAL
+ Collation: binary (63)
+-Length: 12
++Length: 11
+ Max_length: 0
+ Decimals: 0
+-Flags: UNSIGNED BINARY NUM
++Flags: BINARY NUM
+
+ Field 3: `FLOOR(c_bigint)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+-Type: NEWDECIMAL
++Type: LONGLONG
+ Collation: binary (63)
+-Length: 17
++Length: 21
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 4: `FLOOR(c_bigint_unsigned)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: NEWDECIMAL
+ Collation: binary (63)
+-Length: 17
++Length: 21
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 5: `FLOOR(c_float)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 0
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 6: `FLOOR(c_float_unsigned)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 0
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 7: `FLOOR(c_double)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 0
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 8: `FLOOR(c_double_unsigned)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 0
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 9: `FLOOR(c_decimal)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: LONGLONG
+ Collation: binary (63)
+ Length: 6
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 10: `FLOOR(c_decimal_unsigned)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: LONGLONG
+ Collation: binary (63)
+-Length: 9
++Length: 10
+ Max_length: 0
+ Decimals: 0
+-Flags: UNSIGNED BINARY NUM
++Flags: BINARY NUM
+
+ Field 11: `FLOOR(c_datetime)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 12: `FLOOR(c_time)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 13: `FLOOR(c_timestamp)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+-Flags: NOT_NULL BINARY NUM
++Flags: BINARY NUM
+
+ Field 14: `FLOOR(c_char)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 15: `FLOOR(c_char_binary)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 16: `FLOOR(c_varchar)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 17: `FLOOR(c_varchar_binary)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 18: `FLOOR(c_binary)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 19: `FLOOR(c_varbinary)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 20: `FLOOR(c_text)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 21: `FLOOR(c_blob)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 22: `FLOOR(c_text_binary)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 23: `FLOOR(c_set)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+ Field 24: `FLOOR(c_enum)`
+ Catalog: `def`
+ Database: ``
+ Table: ``
+ Org_table: ``
+ Type: DOUBLE
+ Collation: binary (63)
+-Length: 17
++Length: 23
+ Max_length: 0
+ Decimals: 0
+ Flags: BINARY NUM
+
+
+ 0 rows in set (0.00 sec)
+
+```",1,incorrect ceil floor infer type mysql create table t c int int c int unsigned int unsigned c bigint bigint c bigint unsigned bigint unsigned c float float c float unsigned float unsigned c double double c double unsigned double unsigned c decimal decimal c decimal unsigned decimal unsigned c datetime datetime c time time c timestamp timestamp c char char c char binary char binary c varchar varchar c varchar binary varchar binary c binary binary c varbinary varbinary c text text c blob blob c text binary text binary c set set a b c c enum enum a b c select floor c int floor c int unsigned floor c bigint floor c bigint unsigned floor c float floor c float unsigned floor c double floor c double unsigned floor c decimal floor c decimal unsigned floor c datetime floor c time floor c timestamp floor c char floor c char binary floor c varchar floor c varchar binary floor c binary floor c varbinary floor c text floor c blob floor c text binary floor c set floor c enum from t diff diff mysql txt diff tidb txt field floor c int catalog def database table org table type longlong collation binary length length max length decimals flags binary num field floor c int unsigned catalog def database table org table type longlong type newdecimal collation binary length length max length decimals flags unsigned binary num flags binary num field floor c bigint catalog def database table org table type newdecimal type longlong collation binary length length max length decimals flags binary num field floor c bigint unsigned catalog def database table org table type newdecimal collation binary length length max length decimals flags binary num field floor c float catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c float unsigned catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c double catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c double unsigned catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c decimal catalog def database table org table type longlong collation binary length max length decimals flags binary num field floor c decimal unsigned catalog def database table org table type longlong collation binary length length max length decimals flags unsigned binary num flags binary num field floor c datetime catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c time catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c timestamp catalog def database table org table type double collation binary length length max length decimals flags not null binary num flags binary num field floor c char catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c char binary catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c varchar catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c varchar binary catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c binary catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c varbinary catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c text catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c blob catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c text binary catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c set catalog def database table org table type double collation binary length length max length decimals flags binary num field floor c enum catalog def database table org table type double collation binary length length max length decimals flags binary num rows in set sec ,1
+6175,8578663847.0,IssuesEvent,2018-11-13 06:16:32,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,incorrect column value of type `year` for zero input,component/server type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+From TiDB:
+```
+mysql> create table tbl(a year(4));
+Query OK, 0 rows affected (0.13 sec)
+
+mysql> insert into tbl values(0);
+Query OK, 1 row affected (0.00 sec)
+
+mysql> select * from tbl;
++------+
+| a |
++------+
+| 2000 |
++------+
+1 row in set (0.00 sec)
+
+mysql> insert into tbl values('0');
+Query OK, 1 row affected (0.00 sec)
+
+mysql> select * from tbl;
++------+
+| a |
++------+
+| 2000 |
+| 2000 |
++------+
+2 rows in set (0.00 sec)
+```
+
+2. What did you expect to see?
+
+From MySQL:
+```
+mysql> create table tbl(a year(4));
+Query OK, 0 rows affected (0.02 sec)
+
+mysql> insert into tbl values(0);
+Query OK, 1 row affected (0.01 sec)
+
+mysql> select * from tbl;
++------+
+| a |
++------+
+| 0000 |
++------+
+1 row in set (0.00 sec)
+
+mysql> insert into tbl values('0');
+Query OK, 1 row affected (0.01 sec)
+
+mysql> select * from tbl;
++------+
+| a |
++------+
+| 0000 |
+| 2000 |
++------+
+2 rows in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+Incompatible behavior with MySQL. According to https://dev.mysql.com/doc/refman/5.7/en/two-digit-years.html:
+> For YEAR, the rules are the same, with this exception: A numeric 00 inserted into YEAR(4) results in 0000 rather than 2000. To specify zero for YEAR(4) and have it be interpreted as 2000, specify it as a string '0' or '00'.
+
+We need to handle this exception.
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+mysql> select version();
++--------------------------------------+
+| version() |
++--------------------------------------+
+| 5.7.10-TiDB-v2.1.0-rc.3-175-gf7d8ca6 |
++--------------------------------------+
+1 row in set (0.00 sec)
+```",True,"incorrect column value of type `year` for zero input - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+From TiDB:
+```
+mysql> create table tbl(a year(4));
+Query OK, 0 rows affected (0.13 sec)
+
+mysql> insert into tbl values(0);
+Query OK, 1 row affected (0.00 sec)
+
+mysql> select * from tbl;
++------+
+| a |
++------+
+| 2000 |
++------+
+1 row in set (0.00 sec)
+
+mysql> insert into tbl values('0');
+Query OK, 1 row affected (0.00 sec)
+
+mysql> select * from tbl;
++------+
+| a |
++------+
+| 2000 |
+| 2000 |
++------+
+2 rows in set (0.00 sec)
+```
+
+2. What did you expect to see?
+
+From MySQL:
+```
+mysql> create table tbl(a year(4));
+Query OK, 0 rows affected (0.02 sec)
+
+mysql> insert into tbl values(0);
+Query OK, 1 row affected (0.01 sec)
+
+mysql> select * from tbl;
++------+
+| a |
++------+
+| 0000 |
++------+
+1 row in set (0.00 sec)
+
+mysql> insert into tbl values('0');
+Query OK, 1 row affected (0.01 sec)
+
+mysql> select * from tbl;
++------+
+| a |
++------+
+| 0000 |
+| 2000 |
++------+
+2 rows in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+Incompatible behavior with MySQL. According to https://dev.mysql.com/doc/refman/5.7/en/two-digit-years.html:
+> For YEAR, the rules are the same, with this exception: A numeric 00 inserted into YEAR(4) results in 0000 rather than 2000. To specify zero for YEAR(4) and have it be interpreted as 2000, specify it as a string '0' or '00'.
+
+We need to handle this exception.
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+mysql> select version();
++--------------------------------------+
+| version() |
++--------------------------------------+
+| 5.7.10-TiDB-v2.1.0-rc.3-175-gf7d8ca6 |
++--------------------------------------+
+1 row in set (0.00 sec)
+```",1,incorrect column value of type year for zero input bug report please answer these questions before submitting your issue thanks what did you do from tidb mysql create table tbl a year query ok rows affected sec mysql insert into tbl values query ok row affected sec mysql select from tbl a row in set sec mysql insert into tbl values query ok row affected sec mysql select from tbl a rows in set sec what did you expect to see from mysql mysql create table tbl a year query ok rows affected sec mysql insert into tbl values query ok row affected sec mysql select from tbl a row in set sec mysql insert into tbl values query ok row affected sec mysql select from tbl a rows in set sec what did you see instead incompatible behavior with mysql according to for year the rules are the same with this exception a numeric inserted into year results in rather than to specify zero for year and have it be interpreted as specify it as a string or we need to handle this exception what version of tidb are you using tidb server v or run select tidb version on tidb mysql select version version tidb rc row in set sec ,1
+372177,25985418881.0,IssuesEvent,2022-12-19 23:20:45,smclaughlan/GWJ52,https://api.github.com/repos/smclaughlan/GWJ52,closed,FEATURE: Modify GLUEProjectile1.tscn and GLUEProjectile2.tscn for projectile shape,documentation enhancement Active,"(they're still called GLUE, despite being projectiles) - @plexsoup
+As a user, I want projectiles from blue towers to be shorter, fatter, and have be more rounded.",1.0,"FEATURE: Modify GLUEProjectile1.tscn and GLUEProjectile2.tscn for projectile shape - (they're still called GLUE, despite being projectiles) - @plexsoup
+As a user, I want projectiles from blue towers to be shorter, fatter, and have be more rounded.",0,feature modify tscn and tscn for projectile shape they re still called glue despite being projectiles plexsoup as a user i want projectiles from blue towers to be shorter fatter and have be more rounded ,0
+14660,8658625739.0,IssuesEvent,2018-11-28 01:54:22,stellar/stellar-core,https://api.github.com/repos/stellar/stellar-core,opened,investigate using a different sql library (or our own),discussion enhancement performance,"From the preliminary investigation done in https://github.com/bobg/stellar-core/tree/accum it looks like bypassing soci yields a large speed increase (on bobg's machine it halved applying buckets).
+
+Some of the changes (upsert) only had a small impact (less than 5%), most gains seem to come from direct calls to the client library.",True,"investigate using a different sql library (or our own) - From the preliminary investigation done in https://github.com/bobg/stellar-core/tree/accum it looks like bypassing soci yields a large speed increase (on bobg's machine it halved applying buckets).
+
+Some of the changes (upsert) only had a small impact (less than 5%), most gains seem to come from direct calls to the client library.",0,investigate using a different sql library or our own from the preliminary investigation done in it looks like bypassing soci yields a large speed increase on bobg s machine it halved applying buckets some of the changes upsert only had a small impact less than most gains seem to come from direct calls to the client library ,0
+13293,15683544813.0,IssuesEvent,2021-03-25 08:55:14,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,count() is incompatible with mysql and tidb,type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+```mysql
+CREATE TABLE `t1` (
+ `COL1` varchar(10) CHARACTER SET utf8mb4 COLLATE utf8mb4_general_ci NOT NULL
+) ENGINE = InnoDB CHARACTER SET = utf8mb4 COLLATE = utf8mb4_general_ci ROW_FORMAT = Dynamic;
+insert into t1 values(""tidb"");
+```
+
+
+### 2. What did you expect to see? (Required)
+```mysql
+mysql:
+mysql> select col1 from t1 group by col1 having count(col1) = ""1e64"";
+Empty set
+
+```
+### 3. What did you see instead (Required)
+```mysql
+tidb:
+mysql> select col1 from t1 group by col1 having count(col1) = ""1e20"";
+Empty set
+
+mysql> select col1 from t1 group by col1 having count(col1) = ""1e64"";
++------+
+| col1 |
++------+
+| tidb |
++------+
+1 row in set (0.59 sec)
+
+```
+### 4. What is your TiDB version? (Required)
+```mysql
+Release Version: v4.0.0-beta.2-2444-g5715eefd2-dirty
+Edition: Community
+Git Commit Hash: 5715eefd2b2febdd6e3b64413bb066f4d425a3dc
+Git Branch: master
+UTC Build Time: 2021-03-24 14:28:28
+GoVersion: go1.13
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+```
+
+
+",True,"count() is incompatible with mysql and tidb - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+```mysql
+CREATE TABLE `t1` (
+ `COL1` varchar(10) CHARACTER SET utf8mb4 COLLATE utf8mb4_general_ci NOT NULL
+) ENGINE = InnoDB CHARACTER SET = utf8mb4 COLLATE = utf8mb4_general_ci ROW_FORMAT = Dynamic;
+insert into t1 values(""tidb"");
+```
+
+
+### 2. What did you expect to see? (Required)
+```mysql
+mysql:
+mysql> select col1 from t1 group by col1 having count(col1) = ""1e64"";
+Empty set
+
+```
+### 3. What did you see instead (Required)
+```mysql
+tidb:
+mysql> select col1 from t1 group by col1 having count(col1) = ""1e20"";
+Empty set
+
+mysql> select col1 from t1 group by col1 having count(col1) = ""1e64"";
++------+
+| col1 |
++------+
+| tidb |
++------+
+1 row in set (0.59 sec)
+
+```
+### 4. What is your TiDB version? (Required)
+```mysql
+Release Version: v4.0.0-beta.2-2444-g5715eefd2-dirty
+Edition: Community
+Git Commit Hash: 5715eefd2b2febdd6e3b64413bb066f4d425a3dc
+Git Branch: master
+UTC Build Time: 2021-03-24 14:28:28
+GoVersion: go1.13
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+```
+
+
+",1,count is incompatible with mysql and tidb bug report please answer these questions before submitting your issue thanks minimal reproduce step required mysql create table varchar character set collate general ci not null engine innodb character set collate general ci row format dynamic insert into values tidb what did you expect to see required mysql mysql mysql select from group by having count empty set what did you see instead required mysql tidb mysql select from group by having count empty set mysql select from group by having count tidb row in set sec what is your tidb version required mysql release version beta dirty edition community git commit hash git branch master utc build time goversion race enabled false tikv min version check table before drop false ,1
+109759,9413157574.0,IssuesEvent,2019-04-10 07:01:59,smart-signature/smart-signature-future,https://api.github.com/repos/smart-signature/smart-signature-future,closed,【赞赏界面】1. 赞赏金额输入框中限制只可输入数字 2. 改评论输入框行高,Need to be tested good first issue p2,"## 开发需求清单
+- [x] 赞赏金额输入框正则限制的内容仅为合法的浮点数
+- [x] 赞赏评论输入框显示拓展到4行文字高度
+
+## 备注
+
+",1.0,"【赞赏界面】1. 赞赏金额输入框中限制只可输入数字 2. 改评论输入框行高 - ## 开发需求清单
+- [x] 赞赏金额输入框正则限制的内容仅为合法的浮点数
+- [x] 赞赏评论输入框显示拓展到4行文字高度
+
+## 备注
+
+",0,【赞赏界面】 赞赏金额输入框中限制只可输入数字 改评论输入框行高 开发需求清单 赞赏金额输入框正则限制的内容仅为合法的浮点数 备注 ,0
+11010,13046793697.0,IssuesEvent,2020-07-29 09:35:10,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,SHOW CREATE TABLE should show added foreign keys,type/compatibility,"## Bug Report
+
+See #8303: I do not know how to create a proper Entity-Relationship diagram with TiDB due to this issue.
+Additionally, it may not be possible to retrieve the name of an added foreign key (needed for dropping it).
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+Created a table, then as a separate step added foreign keys, then ran `SHOW CREATE
`.
+
+2. What did you expect to see?
+
+Foreign keys among the output.
+
+3. What did you see instead?
+
+No foreign keys.
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+pingcap/tidb:v2.1.0-rc.4",True,"SHOW CREATE TABLE should show added foreign keys - ## Bug Report
+
+See #8303: I do not know how to create a proper Entity-Relationship diagram with TiDB due to this issue.
+Additionally, it may not be possible to retrieve the name of an added foreign key (needed for dropping it).
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+Created a table, then as a separate step added foreign keys, then ran `SHOW CREATE
`.
+
+2. What did you expect to see?
+
+Foreign keys among the output.
+
+3. What did you see instead?
+
+No foreign keys.
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+pingcap/tidb:v2.1.0-rc.4",1,show create table should show added foreign keys bug report see i do not know how to create a proper entity relationship diagram with tidb due to this issue additionally it may not be possible to retrieve the name of an added foreign key needed for dropping it please answer these questions before submitting your issue thanks what did you do created a table then as a separate step added foreign keys then ran show create what did you expect to see foreign keys among the output what did you see instead no foreign keys what version of tidb are you using tidb server v or run select tidb version on tidb pingcap tidb rc ,1
+6691,8968057582.0,IssuesEvent,2019-01-29 06:35:07,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,"""show create table"" shows that the generated column is inconsistent with MySQL",help wanted type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+create table t(c int, b int as (c + 1));
+show create table t;
+```
+2. What did you expect to see?
+mysql> create table t(c int, b int as (c + 1));
+Query OK, 0 rows affected (0.03 sec)
+
+mysql> show create table t;
++-------+-------------------------------------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+-------------------------------------------------------------------------------------------------------------------------------------------+
+| t | CREATE TABLE `t` (
+ `c` int(11) DEFAULT NULL,
+ `b` int(11) GENERATED ALWAYS AS ((`c` + 1)) VIRTUAL
+) ENGINE=InnoDB DEFAULT CHARSET=utf8 |
++-------+-------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+
+
+
+3. What did you see instead?
+tidb> create table t(c int, b int as (c + 1));
+Query OK, 0 rows affected (0.01 sec)
+
+tidb> show create table t;
++-------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| t | CREATE TABLE `t` (
+ `c` int(11) DEFAULT NULL,
+ `b` int(11) GENERATED ALWAYS AS (`c` + 1) VIRTUAL **DEFAULT NULL**
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_bin |
++-------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+Release Version: v3.0.0-beta-18-g7648317da
+Git Commit Hash: 7648317dad4fe4b076158339fd205dfa76b0d5ea
+Git Branch: master
+UTC Build Time: 2019-01-28 07:42:09
+",True,"""show create table"" shows that the generated column is inconsistent with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+create table t(c int, b int as (c + 1));
+show create table t;
+```
+2. What did you expect to see?
+mysql> create table t(c int, b int as (c + 1));
+Query OK, 0 rows affected (0.03 sec)
+
+mysql> show create table t;
++-------+-------------------------------------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+-------------------------------------------------------------------------------------------------------------------------------------------+
+| t | CREATE TABLE `t` (
+ `c` int(11) DEFAULT NULL,
+ `b` int(11) GENERATED ALWAYS AS ((`c` + 1)) VIRTUAL
+) ENGINE=InnoDB DEFAULT CHARSET=utf8 |
++-------+-------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+
+
+
+3. What did you see instead?
+tidb> create table t(c int, b int as (c + 1));
+Query OK, 0 rows affected (0.01 sec)
+
+tidb> show create table t;
++-------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| t | CREATE TABLE `t` (
+ `c` int(11) DEFAULT NULL,
+ `b` int(11) GENERATED ALWAYS AS (`c` + 1) VIRTUAL **DEFAULT NULL**
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_bin |
++-------+-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+Release Version: v3.0.0-beta-18-g7648317da
+Git Commit Hash: 7648317dad4fe4b076158339fd205dfa76b0d5ea
+Git Branch: master
+UTC Build Time: 2019-01-28 07:42:09
+",1, show create table shows that the generated column is inconsistent with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error create table t c int b int as c show create table t what did you expect to see mysql create table t c int b int as c query ok rows affected sec mysql show create table t table create table t create table t c int default null b int generated always as c virtual engine innodb default charset row in set sec what did you see instead tidb create table t c int b int as c query ok rows affected sec tidb show create table t table create table t create table t c int default null b int generated always as c virtual default null engine innodb default charset collate bin row in set sec what version of tidb are you using tidb server v or run select tidb version on tidb release version beta git commit hash git branch master utc build time ,1
+407568,27620894464.0,IssuesEvent,2023-03-10 00:01:55,google/osv.dev,https://api.github.com/repos/google/osv.dev,closed,Add a new data source contributor guide,documentation datasource,"Make learning how to contribute a new data source discoverable and documented. Primary example use case ""I am a Linux Distribution and want to contribute my security advisories in OSV format to OSV""
+
+This could conceivably be added to the FAQ.
+
+Questions that should be answered:
+
+- How do I supply my data?
+ - Git repo or GCS bucket
+- How do I correctly generate my data?
+ - Refer out to OSV Schema documentation and validation tooling
+- How do I get my data imported by OSV.dev?
+ - Direct to file a new GitHub Issue tagged `datasource`",1.0,"Add a new data source contributor guide - Make learning how to contribute a new data source discoverable and documented. Primary example use case ""I am a Linux Distribution and want to contribute my security advisories in OSV format to OSV""
+
+This could conceivably be added to the FAQ.
+
+Questions that should be answered:
+
+- How do I supply my data?
+ - Git repo or GCS bucket
+- How do I correctly generate my data?
+ - Refer out to OSV Schema documentation and validation tooling
+- How do I get my data imported by OSV.dev?
+ - Direct to file a new GitHub Issue tagged `datasource`",0,add a new data source contributor guide make learning how to contribute a new data source discoverable and documented primary example use case i am a linux distribution and want to contribute my security advisories in osv format to osv this could conceivably be added to the faq questions that should be answered how do i supply my data git repo or gcs bucket how do i correctly generate my data refer out to osv schema documentation and validation tooling how do i get my data imported by osv dev direct to file a new github issue tagged datasource ,0
+25781,5198865261.0,IssuesEvent,2017-01-23 19:18:46,spring-cloud/spring-cloud-stream,https://api.github.com/repos/spring-cloud/spring-cloud-stream,closed,PartitionKeyExtractorStrategy instances do not have access to application context,documentation in pr,"When selecting the partion of a kafka topic using a custom PartitionKeyExtractorStrategy, the instantiated objects are not initialized to use configuration values or beans from the application context. This would be very useful when selecting the partition based on a configurable value.
+
+I have a provided a [demo](https://github.com/spring-cloud/spring-cloud-stream/files/434525/demo.zip). When starting it, the logging shows that the inserted `@Value` is null and not properly initialized.
+
+If this is on purpose the documentation should provide more information what is initialized into the this object.
+",1.0,"PartitionKeyExtractorStrategy instances do not have access to application context - When selecting the partion of a kafka topic using a custom PartitionKeyExtractorStrategy, the instantiated objects are not initialized to use configuration values or beans from the application context. This would be very useful when selecting the partition based on a configurable value.
+
+I have a provided a [demo](https://github.com/spring-cloud/spring-cloud-stream/files/434525/demo.zip). When starting it, the logging shows that the inserted `@Value` is null and not properly initialized.
+
+If this is on purpose the documentation should provide more information what is initialized into the this object.
+",0,partitionkeyextractorstrategy instances do not have access to application context when selecting the partion of a kafka topic using a custom partitionkeyextractorstrategy the instantiated objects are not initialized to use configuration values or beans from the application context this would be very useful when selecting the partition based on a configurable value i have a provided a when starting it the logging shows that the inserted value is null and not properly initialized if this is on purpose the documentation should provide more information what is initialized into the this object ,0
+530031,15414987789.0,IssuesEvent,2021-03-05 01:32:19,zephyrproject-rtos/zephyr,https://api.github.com/repos/zephyrproject-rtos/zephyr,opened,[Coverity CID :219516] Improper use of negative value in tests/drivers/timer/nrf_rtc_timer/src/main.c,Coverity bug priority: low,"
+Static code scan issues found in file:
+
+https://github.com/zephyrproject-rtos/zephyr/tree/bd97359a5338b2542d19011b6d6aa1d8d1b9cc3f/tests/drivers/timer/nrf_rtc_timer/src/main.c
+
+Category: Integer handling issues
+Function: `test_stress`
+Component: Tests
+CID: [219516](https://scan9.coverity.com/reports.htm#v29726/p12996/mergedDefectId=219516)
+
+
+Details:
+
+https://github.com/zephyrproject-rtos/zephyr/blob/bd97359a5338b2542d19011b6d6aa1d8d1b9cc3f/tests/drivers/timer/nrf_rtc_timer/src/main.c#L278
+
+Please fix or provide comments in coverity using the link:
+
+https://scan9.coverity.com/reports.htm#v32951/p12996.
+
+Note: This issue was created automatically. Priority was set based on classification
+of the file affected and the impact field in coverity. Assignees were set using the CODEOWNERS file.
+",1.0,"[Coverity CID :219516] Improper use of negative value in tests/drivers/timer/nrf_rtc_timer/src/main.c -
+Static code scan issues found in file:
+
+https://github.com/zephyrproject-rtos/zephyr/tree/bd97359a5338b2542d19011b6d6aa1d8d1b9cc3f/tests/drivers/timer/nrf_rtc_timer/src/main.c
+
+Category: Integer handling issues
+Function: `test_stress`
+Component: Tests
+CID: [219516](https://scan9.coverity.com/reports.htm#v29726/p12996/mergedDefectId=219516)
+
+
+Details:
+
+https://github.com/zephyrproject-rtos/zephyr/blob/bd97359a5338b2542d19011b6d6aa1d8d1b9cc3f/tests/drivers/timer/nrf_rtc_timer/src/main.c#L278
+
+Please fix or provide comments in coverity using the link:
+
+https://scan9.coverity.com/reports.htm#v32951/p12996.
+
+Note: This issue was created automatically. Priority was set based on classification
+of the file affected and the impact field in coverity. Assignees were set using the CODEOWNERS file.
+",0, improper use of negative value in tests drivers timer nrf rtc timer src main c static code scan issues found in file category integer handling issues function test stress component tests cid details please fix or provide comments in coverity using the link note this issue was created automatically priority was set based on classification of the file affected and the impact field in coverity assignees were set using the codeowners file ,0
+16541,22494253185.0,IssuesEvent,2022-06-23 05:50:39,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,cast string as time behaviour is incompatible with MySQL,type/bug type/compatibility sig/execution severity/moderate,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```sql
+SELECT cast(""0000-00-00"" as TIME);
+```
+
+Related: https://github.com/go-sql-driver/mysql/pull/1331
+
+
+
+### 2. What did you expect to see? (Required)
+
+In MySQL 8.0
+
+```sql
+>SELECT cast(""0000-00-00"" as TIME);
++----------------------------+
+| cast(""0000-00-00"" as TIME) |
++----------------------------+
+| 00:00:00 |
++----------------------------+
+```
+
+### 3. What did you see instead (Required)
+
+In TiDB
+
+```sql
+>SELECT cast(""0000-00-00"" as TIME);
++----------------------------+
+| cast(""0000-00-00"" as TIME) |
++----------------------------+
+| |
++----------------------------+
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+
+```sql
+>select tidb_version()\G
+***************************[ 1. row ]***************************
+tidb_version() | Release Version: v6.1.0-alpha-360-gab26a287dc
+Edition: Community
+Git Commit Hash: ab26a287dcbe4186d327cfcaa74bf945db83a338
+Git Branch: master
+UTC Build Time: 2022-05-10 08:32:31
+GoVersion: go1.18
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+```",True,"cast string as time behaviour is incompatible with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```sql
+SELECT cast(""0000-00-00"" as TIME);
+```
+
+Related: https://github.com/go-sql-driver/mysql/pull/1331
+
+
+
+### 2. What did you expect to see? (Required)
+
+In MySQL 8.0
+
+```sql
+>SELECT cast(""0000-00-00"" as TIME);
++----------------------------+
+| cast(""0000-00-00"" as TIME) |
++----------------------------+
+| 00:00:00 |
++----------------------------+
+```
+
+### 3. What did you see instead (Required)
+
+In TiDB
+
+```sql
+>SELECT cast(""0000-00-00"" as TIME);
++----------------------------+
+| cast(""0000-00-00"" as TIME) |
++----------------------------+
+| |
++----------------------------+
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+
+```sql
+>select tidb_version()\G
+***************************[ 1. row ]***************************
+tidb_version() | Release Version: v6.1.0-alpha-360-gab26a287dc
+Edition: Community
+Git Commit Hash: ab26a287dcbe4186d327cfcaa74bf945db83a338
+Git Branch: master
+UTC Build Time: 2022-05-10 08:32:31
+GoVersion: go1.18
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+```",1,cast string as time behaviour is incompatible with mysql bug report please answer these questions before submitting your issue thanks minimal reproduce step required sql select cast as time related what did you expect to see required in mysql sql select cast as time cast as time what did you see instead required in tidb sql select cast as time cast as time what is your tidb version required sql select tidb version g tidb version release version alpha edition community git commit hash git branch master utc build time goversion race enabled false tikv min version check table before drop false ,1
+20723,30812356317.0,IssuesEvent,2023-08-01 11:17:30,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,WEIGHT_STRING() behaviour differs from MySQL,type/bug type/compatibility severity/minor compatibility-mysql8,"## Bug Report
+
+
+
+### 1. Minimal reproduce step (Required)
+
+Run this with `mysqlsh --column-type-info ...`:
+
+
+```sql
+SELECT WEIGHT_STRING('aéè€☺');
+```
+
+### 2. What did you expect to see? (Required)
+
+This is with MySQL 8.1.0:
+```
+sql> SELECT WEIGHT_STRING('aéè€☺');
+Field 1
+Name: `WEIGHT_STRING('aéè€☺')`
+Org_name: ``
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: Bytes
+DbType: VAR_STRING
+Collation: binary (63)
+Length: 320
+Decimals: 31
+Flags: BINARY
+
++------------------------+
+| WEIGHT_STRING('aéè€☺') |
++------------------------+
+| 0x1C471CAA1CAA1C2A094A |
++------------------------+
+1 row in set (0.0003 sec)
+```
+
+This is with MySQL 8.0.33 (and MySQL Client instead of MySQL Shell):
+```
+root [(none)] > SELECT WEIGHT_STRING('aéè€☺');
+Field 1: `WEIGHT_STRING('aéè€☺')`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: VAR_STRING
+Collation: binary (63)
+Length: 320
+Max_length: 10
+Decimals: 31
+Flags: BINARY
+
+
++------------------------------------------------------------+
+| WEIGHT_STRING('aéè€☺') |
++------------------------------------------------------------+
+| 0x1C471CAA1CAA1C2A094A |
++------------------------------------------------------------+
+1 row in set (0.01 sec)
+```
+
+### 3. What did you see instead (Required)
+
+```
+sql> SELECT WEIGHT_STRING('aéè€☺');
+Field 1
+Name: `WEIGHT_STRING('aéè€☺')`
+Org_name: ``
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: String ← Different, MySQL has Bytes
+DbType: VAR_STRING
+Collation: utf8mb4_bin (46) ← Different, MySQL has ""binary (63)""
+Length: 0 ← Different, MySQL has 320
+Decimals: 31
+Flags: NOT_NULL ← Different, MySQL has ""BINARY""
+
++------------------------+
+| WEIGHT_STRING('aéè€☺') |
++------------------------+
+| aéè€☺ |
++------------------------+
+1 row in set (0.0005 sec)
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+
+```
+Release Version: v7.3.0-alpha-224-g941415cfd0
+Edition: Community
+Git Commit Hash: 941415cfd007161df099c0d701140dd3962b87c2
+Git Branch: utf8mb4-0900-ai-ci
+UTC Build Time: 2023-08-01 10:58:52
+GoVersion: go1.20.6
+Race Enabled: false
+Check Table Before Drop: false
+Store: unistore
+```
+
+",True,"WEIGHT_STRING() behaviour differs from MySQL - ## Bug Report
+
+
+
+### 1. Minimal reproduce step (Required)
+
+Run this with `mysqlsh --column-type-info ...`:
+
+
+```sql
+SELECT WEIGHT_STRING('aéè€☺');
+```
+
+### 2. What did you expect to see? (Required)
+
+This is with MySQL 8.1.0:
+```
+sql> SELECT WEIGHT_STRING('aéè€☺');
+Field 1
+Name: `WEIGHT_STRING('aéè€☺')`
+Org_name: ``
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: Bytes
+DbType: VAR_STRING
+Collation: binary (63)
+Length: 320
+Decimals: 31
+Flags: BINARY
+
++------------------------+
+| WEIGHT_STRING('aéè€☺') |
++------------------------+
+| 0x1C471CAA1CAA1C2A094A |
++------------------------+
+1 row in set (0.0003 sec)
+```
+
+This is with MySQL 8.0.33 (and MySQL Client instead of MySQL Shell):
+```
+root [(none)] > SELECT WEIGHT_STRING('aéè€☺');
+Field 1: `WEIGHT_STRING('aéè€☺')`
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: VAR_STRING
+Collation: binary (63)
+Length: 320
+Max_length: 10
+Decimals: 31
+Flags: BINARY
+
+
++------------------------------------------------------------+
+| WEIGHT_STRING('aéè€☺') |
++------------------------------------------------------------+
+| 0x1C471CAA1CAA1C2A094A |
++------------------------------------------------------------+
+1 row in set (0.01 sec)
+```
+
+### 3. What did you see instead (Required)
+
+```
+sql> SELECT WEIGHT_STRING('aéè€☺');
+Field 1
+Name: `WEIGHT_STRING('aéè€☺')`
+Org_name: ``
+Catalog: `def`
+Database: ``
+Table: ``
+Org_table: ``
+Type: String ← Different, MySQL has Bytes
+DbType: VAR_STRING
+Collation: utf8mb4_bin (46) ← Different, MySQL has ""binary (63)""
+Length: 0 ← Different, MySQL has 320
+Decimals: 31
+Flags: NOT_NULL ← Different, MySQL has ""BINARY""
+
++------------------------+
+| WEIGHT_STRING('aéè€☺') |
++------------------------+
+| aéè€☺ |
++------------------------+
+1 row in set (0.0005 sec)
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+
+```
+Release Version: v7.3.0-alpha-224-g941415cfd0
+Edition: Community
+Git Commit Hash: 941415cfd007161df099c0d701140dd3962b87c2
+Git Branch: utf8mb4-0900-ai-ci
+UTC Build Time: 2023-08-01 10:58:52
+GoVersion: go1.20.6
+Race Enabled: false
+Check Table Before Drop: false
+Store: unistore
+```
+
+",1,weight string behaviour differs from mysql bug report minimal reproduce step required run this with mysqlsh column type info sql select weight string aéè€☺ what did you expect to see required this is with mysql sql select weight string aéè€☺ field name weight string aéè€☺ org name catalog def database table org table type bytes dbtype var string collation binary length decimals flags binary weight string aéè€☺ row in set sec this is with mysql and mysql client instead of mysql shell root select weight string aéè€☺ field weight string aéè€☺ catalog def database table org table type var string collation binary length max length decimals flags binary weight string aéè€☺ row in set sec what did you see instead required sql select weight string aéè€☺ field name weight string aéè€☺ org name catalog def database table org table type string ← different mysql has bytes dbtype var string collation bin ← different mysql has binary length ← different mysql has decimals flags not null ← different mysql has binary weight string aéè€☺ aéè€☺ row in set sec what is your tidb version required release version alpha edition community git commit hash git branch ai ci utc build time goversion race enabled false check table before drop false store unistore ,1
+217297,7320120708.0,IssuesEvent,2018-03-02 05:09:18,wso2/product-is,https://api.github.com/repos/wso2/product-is,closed,Better to include the DB that the new tables are introduced,Affected/5.5.0-Alpha Priority/High Type/Docs,"Better to include the DB that the new tables are introduced in this doc [1]
+
+[1] https://docs.wso2.com/display/IS550/Private+Key+JWT+Client+Authentication+for+OIDC
+
+Current doc mentions,
+
+A new table named IDN_OIDC_JTI has been introduced to store the JTI with the following columns.
+JWT_ID VARCHAR(255)
+EXP_TIME TIMESTAMP DEFAULT 0
+TIME_CREATED TIMESTAMP DEFAULT 0
+PRIMARY KEY (JWT_ID))
+
+These can be seen in the script inside identity.",1.0,"Better to include the DB that the new tables are introduced - Better to include the DB that the new tables are introduced in this doc [1]
+
+[1] https://docs.wso2.com/display/IS550/Private+Key+JWT+Client+Authentication+for+OIDC
+
+Current doc mentions,
+
+A new table named IDN_OIDC_JTI has been introduced to store the JTI with the following columns.
+JWT_ID VARCHAR(255)
+EXP_TIME TIMESTAMP DEFAULT 0
+TIME_CREATED TIMESTAMP DEFAULT 0
+PRIMARY KEY (JWT_ID))
+
+These can be seen in the script inside identity.",0,better to include the db that the new tables are introduced better to include the db that the new tables are introduced in this doc current doc mentions a new table named idn oidc jti has been introduced to store the jti with the following columns jwt id varchar exp time timestamp default time created timestamp default primary key jwt id these can be seen in the script inside identity ,0
+4342,7055046089.0,IssuesEvent,2018-01-04 05:37:50,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,table option PACK_KEYS compatibility in CREATE TABLE syntax,compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+`create table t (a int(11)) ENGINE=InnoDB DEFAULT CHARSET=latin1 PACK_KEYS=1`
+
+2. What did you expect to see?
+```
+mysql> create table t (a int(11)) ENGINE=InnoDB DEFAULT CHARSET=latin1 PACK_KEYS=1;
+Query OK, 0 rows affected (0.02 sec)
+```
+
+
+3. What did you see instead?
+```
+MySQL [gin]> create table t (a int(11)) ENGINE=InnoDB DEFAULT CHARSET=latin1 PACK_KEYS=1;
+ERROR 1105 (HY000): line 1 column 73 near ""=1"" (total length 75)
+MySQL [gin]> create table t (a int(11)) ENGINE=InnoDB DEFAULT CHARSET=latin1;
+Query OK, 0 rows affected (0.10 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+Release Version: v1.0.5
+Git Commit Hash: efb13f13b331b340147a63271161e7920eba7e96
+Git Branch: release-1.0
+UTC Build Time: 2017-12-26 01:45:54
+```
+",True,"table option PACK_KEYS compatibility in CREATE TABLE syntax - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+`create table t (a int(11)) ENGINE=InnoDB DEFAULT CHARSET=latin1 PACK_KEYS=1`
+
+2. What did you expect to see?
+```
+mysql> create table t (a int(11)) ENGINE=InnoDB DEFAULT CHARSET=latin1 PACK_KEYS=1;
+Query OK, 0 rows affected (0.02 sec)
+```
+
+
+3. What did you see instead?
+```
+MySQL [gin]> create table t (a int(11)) ENGINE=InnoDB DEFAULT CHARSET=latin1 PACK_KEYS=1;
+ERROR 1105 (HY000): line 1 column 73 near ""=1"" (total length 75)
+MySQL [gin]> create table t (a int(11)) ENGINE=InnoDB DEFAULT CHARSET=latin1;
+Query OK, 0 rows affected (0.10 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+Release Version: v1.0.5
+Git Commit Hash: efb13f13b331b340147a63271161e7920eba7e96
+Git Branch: release-1.0
+UTC Build Time: 2017-12-26 01:45:54
+```
+",1,table option pack keys compatibility in create table syntax please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error create table t a int engine innodb default charset pack keys what did you expect to see mysql create table t a int engine innodb default charset pack keys query ok rows affected sec what did you see instead mysql create table t a int engine innodb default charset pack keys error line column near total length mysql create table t a int engine innodb default charset query ok rows affected sec what version of tidb are you using tidb server v or run select tidb version on tidb release version git commit hash git branch release utc build time ,1
+58124,14239567841.0,IssuesEvent,2020-11-18 20:20:19,CDH-Studio/I-Talent,https://api.github.com/repos/CDH-Studio/I-Talent,closed,ASC-4 SESSION MANAGEMENT ,security control,"**ID:** ASC-4 SESSION MANAGEMENT
+
+**Description**
+
+If the application has no need to track user behavior prior to authentication, it is safer to defer generating and issuing session IDs until a user has successfully completed the authentication procedure.
+
+One of the core components of any application is the mechanism by which it controls and maintains the state for a user interacting with it. This is referred to as Session Management and is defined as the set of all controls governing state-full interaction between a user and the application. This control ensures that a verified application (1) creates sessions that are unique to each individual and cannot be guessed or shared and (2) invalidates sessions when they are no longer required and timed out during periods of inactivity.
+
+Session management go hand in hand with authorization.
+
+Session Management Best Practices
+1. Enforcing absolute session timeouts
+** If you’re storing session state at the server, you can alleviate the inconvenience of forcing users to start from scratch with their tasks by restoring their session state when they re-authenticate and receive a new session ID.
+** Destroy the expired session ID, but keep the session state around for later use.
+** Protected B applications should limit session IDs to two hours, while for Protected A (or lower) applications, a four hour limit is sufficient. Adjust these values based on the level of risk you’re willing to accept.
+** While you should specify an expiration timestamp on the session ID cookie itself, you must also enforce session timeouts on the server.
+2. Enforcing idle session timeouts
+** Best practice for Protected B applications is an idle timeout of no more than 15 minutes, and a 30-minute timeout for Protected A (or lower) application.
+3. Limiting session concurrency
+** The reasonable limit for your application will depend on the nature of the application.
+4. Mandating secure cookies
+** One of the attributes you can set on the cookie that holds your application’s encrypted session ID is the “Secure” flag, which mandate that the web client uses encrypted communications (SSL and HTTPS) when sending cookie back to the serer along with each request.
+5. Using the HttpOnly flag
+** The HttpOnly flag on a cookie instructs the client that the cookie is only to be used in communications over HTTP protocol. This effectively denies access to the cookie to any client-side code such as JavaScript.
+6. Using cryptographically random session IDs
+** Session ID should be of at least 128 bits in length and generated using secure pseudorandom number generator.
+** Use a cryptographically secure ransom number generator (CSPRNG). Random number sequences can be predictable, and not all random number generators are equal.
+7. Destroying invalidated session IDs
+** Invalidate the session ID on the server.
+** Immediately destroy any related client-side cookie value. Do this by including a Set-Cookie directives in the response with an expiration time set in the past.
+** Delete cookies when the browser closes.
+8. Using encrypted cookies
+** Encrypt any data you store in cookies on the web client.
+** Encrypt any data that is sent with a key that is not accessible to the client, so the client cannot decrypt it.
+** If session state information ever does have to leave the server-side, encrypt it.
+** Use a Hash-based Message Authentication Code (HMAC) to verify the integrity of state information received from the client.
+9. Logging out
+** Provide an explicit logout facility in your application’s UI
+10. Regenerating session IDs on authentication / privilege level change
+** When a user authenticates to a higher level (or even switches roles to access a different area), then the application should grant a new session ID with different rights or update the rights associated with the existing session ID. Updating the rights associated with a session ID is fraught with complexity and potential for introducing vulnerabilities into the application. Generally, it is safer to invalidate an older session ID and issue a new one any time a user changes authentication levels – upward or downward.
+11. Keep all session state information on the server-side
+** Keep as much as you can on the server. Ideally, keep all session state information at the server end.
+** Transmit as little as possible to the client. Ideally, don’t transmit anything other than opaque session ID.
+** Encrypt anything that is sent to the web client for storage and that needs to come back unmodified, using an encryption key that is not available to the client, because the client should never be able to decrypt the encrypted data.
+** Rely non-malleable cryptographic algorithms as a means to detect tampering; let decryption failures trigger immediate invalidation of the session.
+12. Make sure that your web application contains code that validates the session ID every time that protected data or functionality is being requested.
+
+Sources / References:
+1. Web Application Security, A Beginner's Guide by Bryan Sullivan and Vincent Liu
+
+**Evidence Required**
+If the application uses an existing session management framework, (e.g., IDM), please name the framework and do not provide evidence item #1.
+
+Please provide:
+
+1. Documentation explaining the session management policy
+
+The documentation must identify:
+- If the application enforces absolute session timeouts
+** After how long does the timeout occur?
+** Is the session timeout enforced on the server?
+** Is the session state kept on the server side?
+- If the application enforces idle session timeouts
+** After how long does the timeout occur?
+- If the application allow concurrent sessions
+** How many concurrent sessions are allowed
+- The security flags set on the cookie
+** Secure flag
+** HttpOnly flag
+** Domain flag
+** Path flag
+- How are cryptographically session IDs generated
+** Which cryptographically secure pseudo-random number generator (CSPRNG) is used?
+** How long are the session IDs?
+- How are session IDs invalidated
+** Are session IDs invalidated on the server?
+** Are Set-Cookie directives included in the response with an expiration time set in the past?
+** Are cookies deleted when the browser closes?
+- If encrypted cookies are used
+** Is the encryption key accessible to the client side?
+** Is a Hash-based Message Authentication Code (HMAC) used to verify the integrity of state information received from the client?
+- If the application proved an explicit logout facility in the application`s UI
+- If the application regenerates session IDs on authentication / privilege change
+- If all session state information kept on the server side
+- If the application validates the session ID every time protected data or a protected functionality is being requested
+- Where the sessions IDs are stored
+
+2. Quality Assurance (QA) test results related to session management (e.g., absolute and idle session timeouts, session concurrency, cookie attributes, session ID randomness, session ID destruction, etc)
+",True,"ASC-4 SESSION MANAGEMENT - **ID:** ASC-4 SESSION MANAGEMENT
+
+**Description**
+
+If the application has no need to track user behavior prior to authentication, it is safer to defer generating and issuing session IDs until a user has successfully completed the authentication procedure.
+
+One of the core components of any application is the mechanism by which it controls and maintains the state for a user interacting with it. This is referred to as Session Management and is defined as the set of all controls governing state-full interaction between a user and the application. This control ensures that a verified application (1) creates sessions that are unique to each individual and cannot be guessed or shared and (2) invalidates sessions when they are no longer required and timed out during periods of inactivity.
+
+Session management go hand in hand with authorization.
+
+Session Management Best Practices
+1. Enforcing absolute session timeouts
+** If you’re storing session state at the server, you can alleviate the inconvenience of forcing users to start from scratch with their tasks by restoring their session state when they re-authenticate and receive a new session ID.
+** Destroy the expired session ID, but keep the session state around for later use.
+** Protected B applications should limit session IDs to two hours, while for Protected A (or lower) applications, a four hour limit is sufficient. Adjust these values based on the level of risk you’re willing to accept.
+** While you should specify an expiration timestamp on the session ID cookie itself, you must also enforce session timeouts on the server.
+2. Enforcing idle session timeouts
+** Best practice for Protected B applications is an idle timeout of no more than 15 minutes, and a 30-minute timeout for Protected A (or lower) application.
+3. Limiting session concurrency
+** The reasonable limit for your application will depend on the nature of the application.
+4. Mandating secure cookies
+** One of the attributes you can set on the cookie that holds your application’s encrypted session ID is the “Secure” flag, which mandate that the web client uses encrypted communications (SSL and HTTPS) when sending cookie back to the serer along with each request.
+5. Using the HttpOnly flag
+** The HttpOnly flag on a cookie instructs the client that the cookie is only to be used in communications over HTTP protocol. This effectively denies access to the cookie to any client-side code such as JavaScript.
+6. Using cryptographically random session IDs
+** Session ID should be of at least 128 bits in length and generated using secure pseudorandom number generator.
+** Use a cryptographically secure ransom number generator (CSPRNG). Random number sequences can be predictable, and not all random number generators are equal.
+7. Destroying invalidated session IDs
+** Invalidate the session ID on the server.
+** Immediately destroy any related client-side cookie value. Do this by including a Set-Cookie directives in the response with an expiration time set in the past.
+** Delete cookies when the browser closes.
+8. Using encrypted cookies
+** Encrypt any data you store in cookies on the web client.
+** Encrypt any data that is sent with a key that is not accessible to the client, so the client cannot decrypt it.
+** If session state information ever does have to leave the server-side, encrypt it.
+** Use a Hash-based Message Authentication Code (HMAC) to verify the integrity of state information received from the client.
+9. Logging out
+** Provide an explicit logout facility in your application’s UI
+10. Regenerating session IDs on authentication / privilege level change
+** When a user authenticates to a higher level (or even switches roles to access a different area), then the application should grant a new session ID with different rights or update the rights associated with the existing session ID. Updating the rights associated with a session ID is fraught with complexity and potential for introducing vulnerabilities into the application. Generally, it is safer to invalidate an older session ID and issue a new one any time a user changes authentication levels – upward or downward.
+11. Keep all session state information on the server-side
+** Keep as much as you can on the server. Ideally, keep all session state information at the server end.
+** Transmit as little as possible to the client. Ideally, don’t transmit anything other than opaque session ID.
+** Encrypt anything that is sent to the web client for storage and that needs to come back unmodified, using an encryption key that is not available to the client, because the client should never be able to decrypt the encrypted data.
+** Rely non-malleable cryptographic algorithms as a means to detect tampering; let decryption failures trigger immediate invalidation of the session.
+12. Make sure that your web application contains code that validates the session ID every time that protected data or functionality is being requested.
+
+Sources / References:
+1. Web Application Security, A Beginner's Guide by Bryan Sullivan and Vincent Liu
+
+**Evidence Required**
+If the application uses an existing session management framework, (e.g., IDM), please name the framework and do not provide evidence item #1.
+
+Please provide:
+
+1. Documentation explaining the session management policy
+
+The documentation must identify:
+- If the application enforces absolute session timeouts
+** After how long does the timeout occur?
+** Is the session timeout enforced on the server?
+** Is the session state kept on the server side?
+- If the application enforces idle session timeouts
+** After how long does the timeout occur?
+- If the application allow concurrent sessions
+** How many concurrent sessions are allowed
+- The security flags set on the cookie
+** Secure flag
+** HttpOnly flag
+** Domain flag
+** Path flag
+- How are cryptographically session IDs generated
+** Which cryptographically secure pseudo-random number generator (CSPRNG) is used?
+** How long are the session IDs?
+- How are session IDs invalidated
+** Are session IDs invalidated on the server?
+** Are Set-Cookie directives included in the response with an expiration time set in the past?
+** Are cookies deleted when the browser closes?
+- If encrypted cookies are used
+** Is the encryption key accessible to the client side?
+** Is a Hash-based Message Authentication Code (HMAC) used to verify the integrity of state information received from the client?
+- If the application proved an explicit logout facility in the application`s UI
+- If the application regenerates session IDs on authentication / privilege change
+- If all session state information kept on the server side
+- If the application validates the session ID every time protected data or a protected functionality is being requested
+- Where the sessions IDs are stored
+
+2. Quality Assurance (QA) test results related to session management (e.g., absolute and idle session timeouts, session concurrency, cookie attributes, session ID randomness, session ID destruction, etc)
+",0,asc session management id asc session management description if the application has no need to track user behavior prior to authentication it is safer to defer generating and issuing session ids until a user has successfully completed the authentication procedure one of the core components of any application is the mechanism by which it controls and maintains the state for a user interacting with it this is referred to as session management and is defined as the set of all controls governing state full interaction between a user and the application this control ensures that a verified application creates sessions that are unique to each individual and cannot be guessed or shared and invalidates sessions when they are no longer required and timed out during periods of inactivity session management go hand in hand with authorization session management best practices enforcing absolute session timeouts if you’re storing session state at the server you can alleviate the inconvenience of forcing users to start from scratch with their tasks by restoring their session state when they re authenticate and receive a new session id destroy the expired session id but keep the session state around for later use protected b applications should limit session ids to two hours while for protected a or lower applications a four hour limit is sufficient adjust these values based on the level of risk you’re willing to accept while you should specify an expiration timestamp on the session id cookie itself you must also enforce session timeouts on the server enforcing idle session timeouts best practice for protected b applications is an idle timeout of no more than minutes and a minute timeout for protected a or lower application limiting session concurrency the reasonable limit for your application will depend on the nature of the application mandating secure cookies one of the attributes you can set on the cookie that holds your application’s encrypted session id is the “secure” flag which mandate that the web client uses encrypted communications ssl and https when sending cookie back to the serer along with each request using the httponly flag the httponly flag on a cookie instructs the client that the cookie is only to be used in communications over http protocol this effectively denies access to the cookie to any client side code such as javascript using cryptographically random session ids session id should be of at least bits in length and generated using secure pseudorandom number generator use a cryptographically secure ransom number generator csprng random number sequences can be predictable and not all random number generators are equal destroying invalidated session ids invalidate the session id on the server immediately destroy any related client side cookie value do this by including a set cookie directives in the response with an expiration time set in the past delete cookies when the browser closes using encrypted cookies encrypt any data you store in cookies on the web client encrypt any data that is sent with a key that is not accessible to the client so the client cannot decrypt it if session state information ever does have to leave the server side encrypt it use a hash based message authentication code hmac to verify the integrity of state information received from the client logging out provide an explicit logout facility in your application’s ui regenerating session ids on authentication privilege level change when a user authenticates to a higher level or even switches roles to access a different area then the application should grant a new session id with different rights or update the rights associated with the existing session id updating the rights associated with a session id is fraught with complexity and potential for introducing vulnerabilities into the application generally it is safer to invalidate an older session id and issue a new one any time a user changes authentication levels – upward or downward keep all session state information on the server side keep as much as you can on the server ideally keep all session state information at the server end transmit as little as possible to the client ideally don’t transmit anything other than opaque session id encrypt anything that is sent to the web client for storage and that needs to come back unmodified using an encryption key that is not available to the client because the client should never be able to decrypt the encrypted data rely non malleable cryptographic algorithms as a means to detect tampering let decryption failures trigger immediate invalidation of the session make sure that your web application contains code that validates the session id every time that protected data or functionality is being requested sources references web application security a beginner s guide by bryan sullivan and vincent liu evidence required if the application uses an existing session management framework e g idm please name the framework and do not provide evidence item please provide documentation explaining the session management policy the documentation must identify if the application enforces absolute session timeouts after how long does the timeout occur is the session timeout enforced on the server is the session state kept on the server side if the application enforces idle session timeouts after how long does the timeout occur if the application allow concurrent sessions how many concurrent sessions are allowed the security flags set on the cookie secure flag httponly flag domain flag path flag how are cryptographically session ids generated which cryptographically secure pseudo random number generator csprng is used how long are the session ids how are session ids invalidated are session ids invalidated on the server are set cookie directives included in the response with an expiration time set in the past are cookies deleted when the browser closes if encrypted cookies are used is the encryption key accessible to the client side is a hash based message authentication code hmac used to verify the integrity of state information received from the client if the application proved an explicit logout facility in the application s ui if the application regenerates session ids on authentication privilege change if all session state information kept on the server side if the application validates the session id every time protected data or a protected functionality is being requested where the sessions ids are stored quality assurance qa test results related to session management e g absolute and idle session timeouts session concurrency cookie attributes session id randomness session id destruction etc ,0
+68991,8365104696.0,IssuesEvent,2018-10-04 02:57:50,ChrisNZL/Tallowmere2,https://api.github.com/repos/ChrisNZL/Tallowmere2,closed,Flash of Light + Life Leech = OP,bug design consideration,"Scenario: You get hit, enemies get hit with Flash of Light in return, and you get healed from the enemies receiving damage.
+
+Currently, Life Leech is a passive trait you can invest points into - not sure I want this to stay or not.
+
+If Life Leech is to stay, it might need a cooldown, or only a small chance to proc, or perhaps just should not proc with Flash of Light.",1.0,"Flash of Light + Life Leech = OP - Scenario: You get hit, enemies get hit with Flash of Light in return, and you get healed from the enemies receiving damage.
+
+Currently, Life Leech is a passive trait you can invest points into - not sure I want this to stay or not.
+
+If Life Leech is to stay, it might need a cooldown, or only a small chance to proc, or perhaps just should not proc with Flash of Light.",0,flash of light life leech op scenario you get hit enemies get hit with flash of light in return and you get healed from the enemies receiving damage currently life leech is a passive trait you can invest points into not sure i want this to stay or not if life leech is to stay it might need a cooldown or only a small chance to proc or perhaps just should not proc with flash of light ,0
+68560,14936775497.0,IssuesEvent,2021-01-25 13:49:44,RG4421/vue-fusioncharts,https://api.github.com/repos/RG4421/vue-fusioncharts,opened,"CVE-2019-10747 (High) detected in set-value-2.0.0.tgz, set-value-0.4.3.tgz",security vulnerability,"## CVE-2019-10747 - High Severity Vulnerability
+ Vulnerable Libraries - set-value-2.0.0.tgz, set-value-0.4.3.tgz
+
+
+set-value-2.0.0.tgz
+
+
Create nested values and any intermediaries using dot notation (`'a.b.c'`) paths.
-Denial of service vulnerability in ASP.NET Core when a malformed request is terminated.
+set-value is vulnerable to Prototype Pollution in versions lower than 3.0.1. The function mixin-deep could be tricked into adding or modifying properties of Object.prototype using any of the constructor, prototype and _proto_ payloads.
-
-A security feature bypass vulnerability exists in the way Microsoft ASP.NET Core parses encoded cookie names.The ASP.NET Core cookie parser decodes entire cookie strings which could allow a malicious attacker to set a second cookie with the name being percent encoded.The security update addresses the vulnerability by fixing the way the ASP.NET Core cookie parser handles encoded names., aka 'Microsoft ASP.NET Core Security Feature Bypass Vulnerability'.
+set-value is vulnerable to Prototype Pollution in versions lower than 3.0.1. The function mixin-deep could be tricked into adding or modifying properties of Object.prototype using any of the constructor, prototype and _proto_ payloads.
-
-
+
-
+",0,cve high detected in set value tgz set value tgz cve high severity vulnerability vulnerable libraries set value tgz set value tgz set value tgz create nested values and any intermediaries using dot notation a b c paths library home page a href path to dependency file vue fusioncharts package json path to vulnerable library vue fusioncharts node modules set value package json dependency hierarchy webpack dev server tgz root library chokidar tgz braces tgz snapdragon tgz base tgz cache base tgz x set value tgz vulnerable library set value tgz create nested values and any intermediaries using dot notation a b c paths library home page a href path to dependency file vue fusioncharts package json path to vulnerable library vue fusioncharts node modules union value node modules set value package json dependency hierarchy webpack dev server tgz root library chokidar tgz braces tgz snapdragon tgz base tgz cache base tgz union value tgz x set value tgz vulnerable library found in head commit a href found in base branch master vulnerability details set value is vulnerable to prototype pollution in versions lower than the function mixin deep could be tricked into adding or modifying properties of object prototype using any of the constructor prototype and proto payloads publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution isopenpronvulnerability true ispackagebased true isdefaultbranch true packages vulnerabilityidentifier cve vulnerabilitydetails set value is vulnerable to prototype pollution in versions lower than the function mixin deep could be tricked into adding or modifying properties of object prototype using any of the constructor prototype and proto payloads vulnerabilityurl ,0
+321373,27523456765.0,IssuesEvent,2023-03-06 16:26:09,Automattic/wp-calypso,https://api.github.com/repos/Automattic/wp-calypso,opened,Medium Woo: Verify upgrades from Free trial,Testing Woo Express,"Once #74119 and #74120 are complete, we want to verify upgrading from the Woo Express free trial.
+
+First create a new trial site by visiting http://calypso.localhost:3000/setup/wooexpress.
+
+Then go through the upgrade process by manually adding the Medium plan to the cart and checkin gout `http://calypso.localhost:3000/checkout/:siteSlug/wooexpress-medium-bundle`.
+
+Things to verify:
+
+TBD",1.0,"Medium Woo: Verify upgrades from Free trial - Once #74119 and #74120 are complete, we want to verify upgrading from the Woo Express free trial.
+
+First create a new trial site by visiting http://calypso.localhost:3000/setup/wooexpress.
+
+Then go through the upgrade process by manually adding the Medium plan to the cart and checkin gout `http://calypso.localhost:3000/checkout/:siteSlug/wooexpress-medium-bundle`.
+
+Things to verify:
+
+TBD",0,medium woo verify upgrades from free trial once and are complete we want to verify upgrading from the woo express free trial first create a new trial site by visiting then go through the upgrade process by manually adding the medium plan to the cart and checkin gout things to verify tbd,0
+4324,7045264520.0,IssuesEvent,2018-01-01 17:09:00,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,[compatibility] select cast(121 as date);,compatibility,"## 1. What did you do?
+
+```sql
+select cast(121 as date);
+```
+
+
+## 2. What did you expect to see?
+
+```sql
+MySQL > select cast(121 as date);
++-------------------+
+| cast(121 as date) |
++-------------------+
+| 2000-01-21 |
++-------------------+
+1 row in set (0.00 sec)
+```
+
+## 3. What did you see instead?
+
+```sql
+TiDB > select cast(121 as date);
+ERROR 1105 (HY000): invalid time format
+```
+
+
+## 4. What version of TiDB are you using (`tidb-server -V`)?
+
+```sh
+$./bin/tidb-server -V
+Release Version: 0.8.0
+Git Commit Hash: 986fb645f3654801afb4da7e1fc72a6aff5fa2e3
+Git Commit Branch: master
+UTC Build Time: 2017-08-24 05:22:35
+```
+",True,"[compatibility] select cast(121 as date); - ## 1. What did you do?
+
+```sql
+select cast(121 as date);
+```
+
+
+## 2. What did you expect to see?
+
+```sql
+MySQL > select cast(121 as date);
++-------------------+
+| cast(121 as date) |
++-------------------+
+| 2000-01-21 |
++-------------------+
+1 row in set (0.00 sec)
+```
+
+## 3. What did you see instead?
+
+```sql
+TiDB > select cast(121 as date);
+ERROR 1105 (HY000): invalid time format
+```
+
+
+## 4. What version of TiDB are you using (`tidb-server -V`)?
+
+```sh
+$./bin/tidb-server -V
+Release Version: 0.8.0
+Git Commit Hash: 986fb645f3654801afb4da7e1fc72a6aff5fa2e3
+Git Commit Branch: master
+UTC Build Time: 2017-08-24 05:22:35
+```
+",1, select cast as date what did you do sql select cast as date what did you expect to see sql mysql select cast as date cast as date row in set sec what did you see instead sql tidb select cast as date error invalid time format what version of tidb are you using tidb server v sh bin tidb server v release version git commit hash git commit branch master utc build time ,1
+5274,7802456618.0,IssuesEvent,2018-06-10 12:49:38,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Add support for alter table convert to syntax,compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```
+mysql > create table user(id int);
+mysql> alter table user CONVERT TO CHARACTER SET utf8mb4 COLLATE utf8mb4_bin;
+```
+
+2. What did you expect to see?
+
+```
+mysql> alter table user CONVERT TO CHARACTER SET utf8mb4 COLLATE utf8mb4_bin;
+Query OK, 0 rows affected (0.09 sec)
+Records: 0 Duplicates: 0 Warnings: 0
+```
+
+3. What did you see instead?
+
+```
+mysql> alter table user CONVERT TO CHARACTER SET utf8mb4 COLLATE utf8mb4_bin;
+ERROR 1105 (HY000): line 1 column 25 near "" TO CHARACTER SET utf8mb4 COLLATE utf8mb4_bin"" (total length 70)
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+tidb_version(): Release Version: v1.1.0-alpha-293-g0b5c0cf9
+Git Commit Hash: 0b5c0cf94d852901f8e2392917a97d85eb851a55
+Git Branch: master
+UTC Build Time: 2018-01-02 07:53:48
+```
+
+Ref:
+```
+ALTER TABLE tbl_name
+ | CONVERT TO CHARACTER SET charset_name [COLLATE collation_name]
+```",True,"Add support for alter table convert to syntax - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```
+mysql > create table user(id int);
+mysql> alter table user CONVERT TO CHARACTER SET utf8mb4 COLLATE utf8mb4_bin;
+```
+
+2. What did you expect to see?
+
+```
+mysql> alter table user CONVERT TO CHARACTER SET utf8mb4 COLLATE utf8mb4_bin;
+Query OK, 0 rows affected (0.09 sec)
+Records: 0 Duplicates: 0 Warnings: 0
+```
+
+3. What did you see instead?
+
+```
+mysql> alter table user CONVERT TO CHARACTER SET utf8mb4 COLLATE utf8mb4_bin;
+ERROR 1105 (HY000): line 1 column 25 near "" TO CHARACTER SET utf8mb4 COLLATE utf8mb4_bin"" (total length 70)
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+tidb_version(): Release Version: v1.1.0-alpha-293-g0b5c0cf9
+Git Commit Hash: 0b5c0cf94d852901f8e2392917a97d85eb851a55
+Git Branch: master
+UTC Build Time: 2018-01-02 07:53:48
+```
+
+Ref:
+```
+ALTER TABLE tbl_name
+ | CONVERT TO CHARACTER SET charset_name [COLLATE collation_name]
+```",1,add support for alter table convert to syntax please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error mysql create table user id int mysql alter table user convert to character set collate bin what did you expect to see mysql alter table user convert to character set collate bin query ok rows affected sec records duplicates warnings what did you see instead mysql alter table user convert to character set collate bin error line column near to character set collate bin total length what version of tidb are you using tidb server v or run select tidb version on tidb tidb version release version alpha git commit hash git branch master utc build time ref alter table tbl name convert to character set charset name ,1
+8794,10737940463.0,IssuesEvent,2019-10-29 14:00:08,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,"TIMESTAMP literal should produce a DATETIME, not TIMESTAMP",component/expression type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```sql
+SELECT TIMESTAMP '9999-01-01 00:00:00';
+```
+
+2. What did you expect to see?
+
+```
+mysql> SELECT TIMESTAMP '9999-01-01 00:00:00';
++---------------------------------+
+| TIMESTAMP '9999-01-01 00:00:00' |
++---------------------------------+
+| 9999-01-01 00:00:00 |
++---------------------------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> SELECT TIMESTAMP '9999-01-01 00:00:00';
+ERROR 1292 (22007): invalid time format: '{9999 1 1 0 0 0 0}'
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+A recent master version
+
+```
+mysql> select tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v4.0.0-alpha-532-ge168fd93f
+Git Commit Hash: e168fd93f68a8e24a24aaa09eb3df5acc9c0c77c
+Git Branch: master
+UTC Build Time: 2019-10-16 07:23:53
+GoVersion: go version go1.13.1 linux/amd64
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+1 row in set (0.00 sec)
+```
+
+
+
+**Note:** According to https://dev.mysql.com/doc/refman/5.6/en/date-and-time-literals.html,
+
+> The `TIMESTAMP` syntax produces a `DATETIME` value in MySQL because `DATETIME` has a range that more closely corresponds to the standard SQL `TIMESTAMP` type, which has a year range from 0001 to 9999. (The MySQL `TIMESTAMP` year range is 1970 to 2038.) ",True,"TIMESTAMP literal should produce a DATETIME, not TIMESTAMP - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```sql
+SELECT TIMESTAMP '9999-01-01 00:00:00';
+```
+
+2. What did you expect to see?
+
+```
+mysql> SELECT TIMESTAMP '9999-01-01 00:00:00';
++---------------------------------+
+| TIMESTAMP '9999-01-01 00:00:00' |
++---------------------------------+
+| 9999-01-01 00:00:00 |
++---------------------------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> SELECT TIMESTAMP '9999-01-01 00:00:00';
+ERROR 1292 (22007): invalid time format: '{9999 1 1 0 0 0 0}'
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+A recent master version
+
+```
+mysql> select tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v4.0.0-alpha-532-ge168fd93f
+Git Commit Hash: e168fd93f68a8e24a24aaa09eb3df5acc9c0c77c
+Git Branch: master
+UTC Build Time: 2019-10-16 07:23:53
+GoVersion: go version go1.13.1 linux/amd64
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+1 row in set (0.00 sec)
+```
+
+
+
+**Note:** According to https://dev.mysql.com/doc/refman/5.6/en/date-and-time-literals.html,
+
+> The `TIMESTAMP` syntax produces a `DATETIME` value in MySQL because `DATETIME` has a range that more closely corresponds to the standard SQL `TIMESTAMP` type, which has a year range from 0001 to 9999. (The MySQL `TIMESTAMP` year range is 1970 to 2038.) ",1,timestamp literal should produce a datetime not timestamp bug report please answer these questions before submitting your issue thanks what did you do sql select timestamp what did you expect to see mysql select timestamp timestamp row in set sec what did you see instead mysql select timestamp error invalid time format what version of tidb are you using tidb server v or run select tidb version on tidb a recent master version mysql select tidb version g row tidb version release version alpha git commit hash git branch master utc build time goversion go version linux race enabled false tikv min version check table before drop false row in set sec note according to the timestamp syntax produces a datetime value in mysql because datetime has a range that more closely corresponds to the standard sql timestamp type which has a year range from to the mysql timestamp year range is to ,1
+12222,14432854792.0,IssuesEvent,2020-12-07 03:11:15,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Support implicit primary key,type/compatibility type/duplicate type/enhancement,"## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+
+In MySQL 8.0, a table with no explicit primary key may still have an effective implicit primary key if it has any UNIQUE indexes on `NOT NULL` columns. In this case, the first such index places the same constraint on table rows as an explicit primary key and that index cannot be made invisible. Consider the following table definition:
+```sql
+CREATE TABLE t2 (
+ i INT NOT NULL,
+ j INT NOT NULL,
+ UNIQUE j_idx (j)
+) ENGINE = InnoDB;
+```
+The key `j_idx` will became a primary key, even if we do not assign `primary key` explicitly.
+
+**Describe the feature you'd like:**
+
+
+In MySQL 8.0
+```
+mysql> show create table t;
++-------+--------------------------------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+--------------------------------------------------------------------------------------------------------------------------------------+
+| t | CREATE TABLE `t` (
+ `a` int(11) NOT NULL,
+ UNIQUE KEY `a` (`a`)
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_unicode_ci |
++-------+--------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+
+mysql> show keys from t;
++-------+------------+----------+--------------+-------------+-----------+-------------+----------+--------+------+------------+---------+---------------+---------+------------+
+| Table | Non_unique | Key_name | Seq_in_index | Column_name | Collation | Cardinality | Sub_part | Packed | Null | Index_type | Comment | Index_comment | Visible | Expression |
++-------+------------+----------+--------------+-------------+-----------+-------------+----------+--------+------+------------+---------+---------------+---------+------------+
+| t | 0 | a | 1 | a | A | 0 | NULL | NULL | | BTREE | | | YES | NULL |
++-------+------------+----------+--------------+-------------+-----------+-------------+----------+--------+------+------------+---------+---------------+---------+------------+
+1 row in set (0.00 sec)
+
+mysql> desc t;
++-------+---------+------+-----+---------+-------+
+| Field | Type | Null | Key | Default | Extra |
++-------+---------+------+-----+---------+-------+
+| a | int(11) | NO | PRI | NULL | |
++-------+---------+------+-----+---------+-------+
+1 row in set (0.01 sec)
+mysql> alter table t alter index a invisible;
+ERROR 3522 (HY000): A primary key index cannot be invisible
+
+```
+
+In TiDB:
+```
+mysql> create table t (a int not null, unique (a));
+Query OK, 0 rows affected (0.11 sec)
+
+mysql> show create table t;
++-------+-------------------------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+-------------------------------------------------------------------------------------------------------------------------------+
+| t | CREATE TABLE `t` (
+ `a` int(11) NOT NULL,
+ UNIQUE KEY `a` (`a`)
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_bin |
++-------+-------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+
+mysql> desc t;
++-------+---------+------+------+---------+-------+
+| Field | Type | Null | Key | Default | Extra |
++-------+---------+------+------+---------+-------+
+| a | int(11) | NO | UNI | NULL | |
++-------+---------+------+------+---------+-------+
+1 row in set (0.00 sec)
+
+```
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+
+
+[MySQL document](https://dev.mysql.com/doc/refman/8.0/en/invisible-indexes.html)",True,"Support implicit primary key - ## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+
+In MySQL 8.0, a table with no explicit primary key may still have an effective implicit primary key if it has any UNIQUE indexes on `NOT NULL` columns. In this case, the first such index places the same constraint on table rows as an explicit primary key and that index cannot be made invisible. Consider the following table definition:
+```sql
+CREATE TABLE t2 (
+ i INT NOT NULL,
+ j INT NOT NULL,
+ UNIQUE j_idx (j)
+) ENGINE = InnoDB;
+```
+The key `j_idx` will became a primary key, even if we do not assign `primary key` explicitly.
+
+**Describe the feature you'd like:**
+
+
+In MySQL 8.0
+```
+mysql> show create table t;
++-------+--------------------------------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+--------------------------------------------------------------------------------------------------------------------------------------+
+| t | CREATE TABLE `t` (
+ `a` int(11) NOT NULL,
+ UNIQUE KEY `a` (`a`)
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_unicode_ci |
++-------+--------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+
+mysql> show keys from t;
++-------+------------+----------+--------------+-------------+-----------+-------------+----------+--------+------+------------+---------+---------------+---------+------------+
+| Table | Non_unique | Key_name | Seq_in_index | Column_name | Collation | Cardinality | Sub_part | Packed | Null | Index_type | Comment | Index_comment | Visible | Expression |
++-------+------------+----------+--------------+-------------+-----------+-------------+----------+--------+------+------------+---------+---------------+---------+------------+
+| t | 0 | a | 1 | a | A | 0 | NULL | NULL | | BTREE | | | YES | NULL |
++-------+------------+----------+--------------+-------------+-----------+-------------+----------+--------+------+------------+---------+---------------+---------+------------+
+1 row in set (0.00 sec)
+
+mysql> desc t;
++-------+---------+------+-----+---------+-------+
+| Field | Type | Null | Key | Default | Extra |
++-------+---------+------+-----+---------+-------+
+| a | int(11) | NO | PRI | NULL | |
++-------+---------+------+-----+---------+-------+
+1 row in set (0.01 sec)
+mysql> alter table t alter index a invisible;
+ERROR 3522 (HY000): A primary key index cannot be invisible
+
+```
+
+In TiDB:
+```
+mysql> create table t (a int not null, unique (a));
+Query OK, 0 rows affected (0.11 sec)
+
+mysql> show create table t;
++-------+-------------------------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+-------------------------------------------------------------------------------------------------------------------------------+
+| t | CREATE TABLE `t` (
+ `a` int(11) NOT NULL,
+ UNIQUE KEY `a` (`a`)
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_bin |
++-------+-------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+
+mysql> desc t;
++-------+---------+------+------+---------+-------+
+| Field | Type | Null | Key | Default | Extra |
++-------+---------+------+------+---------+-------+
+| a | int(11) | NO | UNI | NULL | |
++-------+---------+------+------+---------+-------+
+1 row in set (0.00 sec)
+
+```
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+
+
+[MySQL document](https://dev.mysql.com/doc/refman/8.0/en/invisible-indexes.html)",1,support implicit primary key feature request is your feature request related to a problem please describe in mysql a table with no explicit primary key may still have an effective implicit primary key if it has any unique indexes on not null columns in this case the first such index places the same constraint on table rows as an explicit primary key and that index cannot be made invisible consider the following table definition sql create table i int not null j int not null unique j idx j engine innodb the key j idx will became a primary key even if we do not assign primary key explicitly describe the feature you d like in mysql mysql show create table t table create table t create table t a int not null unique key a a engine innodb default charset collate unicode ci row in set sec mysql show keys from t table non unique key name seq in index column name collation cardinality sub part packed null index type comment index comment visible expression t a a a null null btree yes null row in set sec mysql desc t field type null key default extra a int no pri null row in set sec mysql alter table t alter index a invisible error a primary key index cannot be invisible in tidb mysql create table t a int not null unique a query ok rows affected sec mysql show create table t table create table t create table t a int not null unique key a a engine innodb default charset collate bin row in set sec mysql desc t field type null key default extra a int no uni null row in set sec teachability documentation adoption migration strategy ,1
+50252,3006277387.0,IssuesEvent,2015-07-27 09:21:11,Itseez/opencv,https://api.github.com/repos/Itseez/opencv,opened,Allowing double type support if possible,auto-transferred category: core feature priority: normal,"Transferred from http://code.opencv.org/issues/2671
+```
+|| Ming-Ming Cheng on 2012-12-28 22:41
+|| Priority: Normal
+|| Affected: None
+|| Category: core
+|| Tracker: Feature
+|| Difficulty: None
+|| PR:
+|| Platform: None / None
+```
- CVE-2021-1723
+Allowing double type support if possible
+-----------
+```
+For 64 bit machine, which is the major type currently, operations on double is faster/equal to operations on float. Since the memory difference between double and float is not important for many people, I tried to use double in my code anywhere where float is used before so that don't care too much about type conversion.
+
+A problem is that, some opencv functions only support float (CV_32F). I feel strange why don't them support for double (CV_64F). One example of this function is cvtColor.
+```
+History
+-------
+##### Alexander Smorkalov on 2012-12-29 08:16
+```
+It is very rare feature for computer vision algorithm. But if you have any suggestions, you can contribute to OpenCV via Github pull request. See this page for more details: https://help.github.com/articles/using-pull-requests
+- Category set to core
+```
+##### Ming-Ming Cheng on 2013-04-11 11:02
+```
+Thank you very much for the reply. I agree that most computer vision algorithms needs only float. I just feel that I can consistently use double since I typically don't care about the memory cost introduced by this. Consistently using double, like what was done in Matlab, avoids possible data type conversions when double is required. Modern 64bit computers process double at similar or even more efficiency than float.
+
+Alexander Smorkalov wrote:
+> It is very rare feature for computer vision algorithm. But if you have any suggestions, you can contribute to OpenCV via Github pull request. See this page for more details: https://help.github.com/articles/using-pull-requests
+```",1.0,"Allowing double type support if possible - Transferred from http://code.opencv.org/issues/2671
+```
+|| Ming-Ming Cheng on 2012-12-28 22:41
+|| Priority: Normal
+|| Affected: None
+|| Category: core
+|| Tracker: Feature
+|| Difficulty: None
+|| PR:
+|| Platform: None / None
+```
-### Vulnerable Library - microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
+Allowing double type support if possible
+-----------
+```
+For 64 bit machine, which is the major type currently, operations on double is faster/equal to operations on float. Since the memory difference between double and float is not important for many people, I tried to use double in my code anywhere where float is used before so that don't care too much about type conversion.
+
+A problem is that, some opencv functions only support float (CV_32F). I feel strange why don't them support for double (CV_64F). One example of this function is cvtColor.
+```
-
Core components of ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
+History
+-------
+##### Alexander Smorkalov on 2012-12-29 08:16
+```
+It is very rare feature for computer vision algorithm. But if you have any suggestions, you can contribute to OpenCV via Github pull request. See this page for more details: https://help.github.com/articles/using-pull-requests
+- Category set to core
+```
+##### Ming-Ming Cheng on 2013-04-11 11:02
+```
+Thank you very much for the reply. I agree that most computer vision algorithms needs only float. I just feel that I can consistently use double since I typically don't care about the memory cost introduced by this. Consistently using double, like what was done in Matlab, avoids possible data type conversions when double is required. Modern 64bit computers process double at similar or even more efficiency than float.
+
+Alexander Smorkalov wrote:
+> It is very rare feature for computer vision algorithm. But if you have any suggestions, you can contribute to OpenCV via Github pull request. See this page for more details: https://help.github.com/articles/using-pull-requests
+```",0,allowing double type support if possible transferred from ming ming cheng on priority normal affected none category core tracker feature difficulty none pr platform none none allowing double type support if possible for bit machine which is the major type currently operations on double is faster equal to operations on float since the memory difference between double and float is not important for many people i tried to use double in my code anywhere where float is used before so that don t care too much about type conversion a problem is that some opencv functions only support float cv i feel strange why don t them support for double cv one example of this function is cvtcolor history alexander smorkalov on it is very rare feature for computer vision algorithm but if you have any suggestions you can contribute to opencv via github pull request see this page for more details category set to core ming ming cheng on thank you very much for the reply i agree that most computer vision algorithms needs only float i just feel that i can consistently use double since i typically don t care about the memory cost introduced by this consistently using double like what was done in matlab avoids possible data type conversions when double is required modern computers process double at similar or even more efficiency than float alexander smorkalov wrote it is very rare feature for computer vision algorithm but if you have any suggestions you can contribute to opencv via github pull request see this page for more details ,0
+13897,16624236684.0,IssuesEvent,2021-06-03 07:33:48,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,infer functional dependencies from filters / join conditions and use them for only_full_group_by check,sig/planner type/compatibility type/enhancement,"## Development Task
+
+Below is the output from mysql 5.7:
+
+```
+MySQL [test]> create table t1(a int not null);
+Query OK, 0 rows affected (0.09 sec)
+
+MySQL [test]> insert into t1 values(1);
+Query OK, 1 row affected (0.00 sec)
+
+MySQL [test]> create table t2(a int not null);
+Query OK, 0 rows affected (0.02 sec)
+
+MySQL [test]> insert into t2 values(1);
+Query OK, 1 row affected (0.00 sec)
+
+MySQL [test]> select t1.a from t1 join t2 on t1.a = t2.a group by t2.a;
++---+
+| a |
++---+
+| 1 |
++---+
+1 row in set (0.01 sec)
+
+MySQL [test]> select t1.a from t1 left join t2 on t1.a = t2.a group by t2.a;
+ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column 'test.t1.a' which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by
+
+MySQL [test]> select t1.a from t1 join t2 on t1.a = 1 and 2 = t2.a group by t2.a;
+Empty set (0.00 sec)
+
+MySQL [test]> select t1.a from t1 join t2 on t1.a = 1 and 2 < t2.a group by t2.a;
+Empty set (0.00 sec)
+
+MySQL [test]> select t1.a from t1 join t2 on t1.a > 1 and 2 = t2.a group by t2.a;
+ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column 'test.t1.a' which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by
+
+MySQL [test]> select t1.a from t1 join t2 using(a) group by t2.a;
++---+
+| a |
++---+
+| 1 |
++---+
+1 row in set (0.00 sec)
+
+MySQL [test]> select t1.a from t1 left join t2 using(a) group by t2.a;
+ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column 'test.t1.a' which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by
+```
+
+We can see that, MySQL infers functional dependencies from filters and join conditions, and uses them for only_full_group_by check. Compared with MySQL, TiDB uses a pretty naive approach for only_full_group_by check, and TiDB would report error for all the above SELECT statements.
+
+PostgreSQL(12 devel) has same loose check as TiDB.",True,"infer functional dependencies from filters / join conditions and use them for only_full_group_by check - ## Development Task
+
+Below is the output from mysql 5.7:
+
+```
+MySQL [test]> create table t1(a int not null);
+Query OK, 0 rows affected (0.09 sec)
+
+MySQL [test]> insert into t1 values(1);
+Query OK, 1 row affected (0.00 sec)
+
+MySQL [test]> create table t2(a int not null);
+Query OK, 0 rows affected (0.02 sec)
+
+MySQL [test]> insert into t2 values(1);
+Query OK, 1 row affected (0.00 sec)
+
+MySQL [test]> select t1.a from t1 join t2 on t1.a = t2.a group by t2.a;
++---+
+| a |
++---+
+| 1 |
++---+
+1 row in set (0.01 sec)
+
+MySQL [test]> select t1.a from t1 left join t2 on t1.a = t2.a group by t2.a;
+ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column 'test.t1.a' which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by
+
+MySQL [test]> select t1.a from t1 join t2 on t1.a = 1 and 2 = t2.a group by t2.a;
+Empty set (0.00 sec)
+
+MySQL [test]> select t1.a from t1 join t2 on t1.a = 1 and 2 < t2.a group by t2.a;
+Empty set (0.00 sec)
+
+MySQL [test]> select t1.a from t1 join t2 on t1.a > 1 and 2 = t2.a group by t2.a;
+ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column 'test.t1.a' which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by
+
+MySQL [test]> select t1.a from t1 join t2 using(a) group by t2.a;
++---+
+| a |
++---+
+| 1 |
++---+
+1 row in set (0.00 sec)
+
+MySQL [test]> select t1.a from t1 left join t2 using(a) group by t2.a;
+ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column 'test.t1.a' which is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by
+```
+
+We can see that, MySQL infers functional dependencies from filters and join conditions, and uses them for only_full_group_by check. Compared with MySQL, TiDB uses a pretty naive approach for only_full_group_by check, and TiDB would report error for all the above SELECT statements.
+
+PostgreSQL(12 devel) has same loose check as TiDB.",1,infer functional dependencies from filters join conditions and use them for only full group by check development task below is the output from mysql mysql create table a int not null query ok rows affected sec mysql insert into values query ok row affected sec mysql create table a int not null query ok rows affected sec mysql insert into values query ok row affected sec mysql select a from join on a a group by a a row in set sec mysql select a from left join on a a group by a error expression of select list is not in group by clause and contains nonaggregated column test a which is not functionally dependent on columns in group by clause this is incompatible with sql mode only full group by mysql select a from join on a and a group by a empty set sec mysql select a from join on a and a group by a empty set sec mysql select a from join on a and a group by a error expression of select list is not in group by clause and contains nonaggregated column test a which is not functionally dependent on columns in group by clause this is incompatible with sql mode only full group by mysql select a from join using a group by a a row in set sec mysql select a from left join using a group by a error expression of select list is not in group by clause and contains nonaggregated column test a which is not functionally dependent on columns in group by clause this is incompatible with sql mode only full group by we can see that mysql infers functional dependencies from filters and join conditions and uses them for only full group by check compared with mysql tidb uses a pretty naive approach for only full group by check and tidb would report error for all the above select statements postgresql devel has same loose check as tidb ,1
+78061,15569913535.0,IssuesEvent,2021-03-17 01:17:06,suxSx/opensource-tracker,https://api.github.com/repos/suxSx/opensource-tracker,opened,CVE-2020-10177 (Medium) detected in Pillow-6.2.1-cp27-cp27mu-manylinux1_x86_64.whl,security vulnerability,"## CVE-2020-10177 - Medium Severity Vulnerability
+ Vulnerable Library - Pillow-6.2.1-cp27-cp27mu-manylinux1_x86_64.whl
+
+
-Microsoft is releasing this security advisory to provide information about a vulnerability in .NET Core 3.1 and .NET 6.0. An information disclosure vulnerability exists in .NET Core 3.1 and .NET 6.0 that could lead to unauthorized access of privileged information.
-
-## Affected software
-
-* Any .NET 6.0 application running on .NET 6.0.7 or earlier.
-* Any .NET Core 3.1 applicaiton running on .NET Core 3.1.27 or earlier.
-
-## Patches
-
-* If you're using .NET 6.0, you should download and install Runtime 6.0.8 or SDK 6.0.108 (for Visual Studio 2022 v17.1) from https://dotnet.microsoft.com/download/dotnet-core/6.0.
-* If you're using .NET Core 3.1, you should download and install Runtime 3.1.28 (for Visual Studio 2019 v16.9) from https://dotnet.microsoft.com/download/dotnet-core/3.1.
+Pillow before 7.1.0 has multiple out-of-bounds reads in libImaging/FliDecode.c.
-
-
+
-",True,"dotnetcore-sample-1.0.0: 7 vulnerabilities (highest severity is: 8.8) - autoclosed - Vulnerable Library - dotnetcore-sample-1.0.0
+***
+Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",0,cve medium detected in pillow whl cve medium severity vulnerability vulnerable library pillow whl python imaging library fork library home page a href path to dependency file opensource tracker requirements txt path to vulnerable library opensource tracker requirements txt dependency hierarchy x pillow whl vulnerable library vulnerability details pillow before has multiple out of bounds reads in libimaging flidecode c publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact none availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource ,0
+6088,8516784246.0,IssuesEvent,2018-11-01 04:49:23,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Make `max_prepared_stmt_count` work,for new contributors help wanted type/compatibility,"## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+
+`max_prepared_stmt_count` is a variable ported from mysql.
+
+It controls that how many PREPARE statement tidb can store at one time. It can be used in environments where there is the potential for denial-of-service attacks based on running the server out of memory by preparing huge numbers of statements.
+
+It can disable the prepare statement if we set it to zero.
+
+Currently we have ported it. But not actually make it work.
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+
+
+https://dev.mysql.com/doc/refman/8.0/en/server-system-variables.html#sysvar_max_prepared_stmt_count",True,"Make `max_prepared_stmt_count` work - ## Feature Request
+
+**Is your feature request related to a problem? Please describe:**
+
+
+`max_prepared_stmt_count` is a variable ported from mysql.
+
+It controls that how many PREPARE statement tidb can store at one time. It can be used in environments where there is the potential for denial-of-service attacks based on running the server out of memory by preparing huge numbers of statements.
+
+It can disable the prepare statement if we set it to zero.
+
+Currently we have ported it. But not actually make it work.
+
+**Teachability, Documentation, Adoption, Migration Strategy:**
+
+
+https://dev.mysql.com/doc/refman/8.0/en/server-system-variables.html#sysvar_max_prepared_stmt_count",1,make max prepared stmt count work feature request is your feature request related to a problem please describe max prepared stmt count is a variable ported from mysql it controls that how many prepare statement tidb can store at one time it can be used in environments where there is the potential for denial of service attacks based on running the server out of memory by preparing huge numbers of statements it can disable the prepare statement if we set it to zero currently we have ported it but not actually make it work teachability documentation adoption migration strategy ,1
+3132,6060763639.0,IssuesEvent,2017-06-14 03:18:49,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,different result when query `select cast(-1 as unsigned)`,compatibility,"1. What did you do?
+``` sql
+select cast(-1 as unsigned);
+```
+
+2. What did you expect to see?
+```sql
+mysql> select cast(-1 as unsigned);
++----------------------+
+| cast(-1 as unsigned) |
++----------------------+
+| 18446744073709551615 |
++----------------------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+``` sql
+mysql> select cast(-1 as unsigned);
+ERROR 1690 (22003): constant -1 overflows bigint
+```
+
+
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+>Git Commit Hash: 7a9f4a61e68c8cddeb3967a83e9a8e170700a9a9
+UTC Build Time: 2017-06-08 02:35:04
+
+",True,"different result when query `select cast(-1 as unsigned)` - 1. What did you do?
+``` sql
+select cast(-1 as unsigned);
+```
+
+2. What did you expect to see?
+```sql
+mysql> select cast(-1 as unsigned);
++----------------------+
+| cast(-1 as unsigned) |
++----------------------+
+| 18446744073709551615 |
++----------------------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+``` sql
+mysql> select cast(-1 as unsigned);
+ERROR 1690 (22003): constant -1 overflows bigint
+```
+
+
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+>Git Commit Hash: 7a9f4a61e68c8cddeb3967a83e9a8e170700a9a9
+UTC Build Time: 2017-06-08 02:35:04
+
+",1,different result when query select cast as unsigned what did you do sql select cast as unsigned what did you expect to see sql mysql select cast as unsigned cast as unsigned row in set sec what did you see instead sql mysql select cast as unsigned error constant overflows bigint what version of tidb are you using tidb server v git commit hash utc build time ,1
+3381,6346720339.0,IssuesEvent,2017-07-28 03:33:37,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Built-in function CHARSET not supported,compatibility rc3.1,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```sql
+CREATE TABLE t1 (user varchar(255) NOT NULL default '') ENGINE=MyISAM DEFAULT CHARSET=latin1;
+INSERT INTO t1 VALUES ('one'),('two');
+SELECT CHARSET('a');
+```
+
+2. What did you expect to see?
+
+```
++--------------+
+| CHARSET('a') |
++--------------+
+| utf8 |
++--------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+ERROR 1305 (42000): FUNCTION CHARSET does not exist
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"Built-in function CHARSET not supported - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```sql
+CREATE TABLE t1 (user varchar(255) NOT NULL default '') ENGINE=MyISAM DEFAULT CHARSET=latin1;
+INSERT INTO t1 VALUES ('one'),('two');
+SELECT CHARSET('a');
+```
+
+2. What did you expect to see?
+
+```
++--------------+
+| CHARSET('a') |
++--------------+
+| utf8 |
++--------------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+ERROR 1305 (42000): FUNCTION CHARSET does not exist
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,built in function charset not supported please answer these questions before submitting your issue thanks what did you do sql create table user varchar not null default engine myisam default charset insert into values one two select charset a what did you expect to see charset a row in set sec what did you see instead error function charset does not exist what version of tidb are you using tidb server v ,1
+7137,9421808134.0,IssuesEvent,2019-04-11 07:51:57,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,`monthname` is not compatible with Mysql,for new contributors help wanted type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+select monthname(str_to_date(null, '%m')), monthname(str_to_date(null, '%m')),
+ monthname(str_to_date(1, '%m')), monthname(str_to_date(0, '%m'));
+```
+
+2. What did you expect to see?
+In Mysql
+```
+mysql> select monthname(str_to_date(null, '%m')), monthname(str_to_date(null, '%m')),
+ -> monthname(str_to_date(1, '%m')), monthname(str_to_date(0, '%m'));
++------------------------------------+------------------------------------+---------------------------------+---------------------------------+
+| monthname(str_to_date(null, '%m')) | monthname(str_to_date(null, '%m')) | monthname(str_to_date(1, '%m')) | monthname(str_to_date(0, '%m')) |
++------------------------------------+------------------------------------+---------------------------------+---------------------------------+
+| NULL | NULL | NULL | NULL |
++------------------------------------+------------------------------------+---------------------------------+---------------------------------+
+1 row in set, 2 warnings (0.00 sec)
+```
+
+
+3. What did you see instead?
+In TiDB
+```
+mysql> select monthname(str_to_date(null, '%m')), monthname(str_to_date(null, '%m')),
+ -> monthname(str_to_date(1, '%m')), monthname(str_to_date(0, '%m'));
++------------------------------------+------------------------------------+---------------------------------+---------------------------------+
+| monthname(str_to_date(null, '%m')) | monthname(str_to_date(null, '%m')) | monthname(str_to_date(1, '%m')) | monthname(str_to_date(0, '%m')) |
++------------------------------------+------------------------------------+---------------------------------+---------------------------------+
+| NULL | NULL | January | NULL |
++------------------------------------+------------------------------------+---------------------------------+---------------------------------+
+1 row in set, 1 warning (0.00 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-212-g0681b8125
+Git Commit Hash: 0681b8125080045ee0d4747ce61923164c6f2dd1
+Git Branch: master
+UTC Build Time: 2019-03-14 04:39:19
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+```
+",True,"`monthname` is not compatible with Mysql - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+select monthname(str_to_date(null, '%m')), monthname(str_to_date(null, '%m')),
+ monthname(str_to_date(1, '%m')), monthname(str_to_date(0, '%m'));
+```
+
+2. What did you expect to see?
+In Mysql
+```
+mysql> select monthname(str_to_date(null, '%m')), monthname(str_to_date(null, '%m')),
+ -> monthname(str_to_date(1, '%m')), monthname(str_to_date(0, '%m'));
++------------------------------------+------------------------------------+---------------------------------+---------------------------------+
+| monthname(str_to_date(null, '%m')) | monthname(str_to_date(null, '%m')) | monthname(str_to_date(1, '%m')) | monthname(str_to_date(0, '%m')) |
++------------------------------------+------------------------------------+---------------------------------+---------------------------------+
+| NULL | NULL | NULL | NULL |
++------------------------------------+------------------------------------+---------------------------------+---------------------------------+
+1 row in set, 2 warnings (0.00 sec)
+```
+
+
+3. What did you see instead?
+In TiDB
+```
+mysql> select monthname(str_to_date(null, '%m')), monthname(str_to_date(null, '%m')),
+ -> monthname(str_to_date(1, '%m')), monthname(str_to_date(0, '%m'));
++------------------------------------+------------------------------------+---------------------------------+---------------------------------+
+| monthname(str_to_date(null, '%m')) | monthname(str_to_date(null, '%m')) | monthname(str_to_date(1, '%m')) | monthname(str_to_date(0, '%m')) |
++------------------------------------+------------------------------------+---------------------------------+---------------------------------+
+| NULL | NULL | January | NULL |
++------------------------------------+------------------------------------+---------------------------------+---------------------------------+
+1 row in set, 1 warning (0.00 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-212-g0681b8125
+Git Commit Hash: 0681b8125080045ee0d4747ce61923164c6f2dd1
+Git Branch: master
+UTC Build Time: 2019-03-14 04:39:19
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+```
+",1, monthname is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error select monthname str to date null m monthname str to date null m monthname str to date m monthname str to date m what did you expect to see in mysql mysql select monthname str to date null m monthname str to date null m monthname str to date m monthname str to date m monthname str to date null m monthname str to date null m monthname str to date m monthname str to date m null null null null row in set warnings sec what did you see instead in tidb mysql select monthname str to date null m monthname str to date null m monthname str to date m monthname str to date m monthname str to date null m monthname str to date null m monthname str to date m monthname str to date m null null january null row in set warning sec what version of tidb are you using tidb server v or run select tidb version on tidb tidb version release version beta git commit hash git branch master utc build time goversion go version darwin race enabled false tikv min version alpha check table before drop false ,1
+13244,15608308865.0,IssuesEvent,2021-03-19 10:26:32,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,The result of bitwise OR is incorrect ,sig/execution type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+```mysql
+create table t1(col1 float);
+insert into t1 values(3|111111114);
+```
+
+
+### 2. What did you expect to see? (Required)
+```mysql
+mysql> select * from t1;
++-----------+
+| col1 |
++-----------+
+| 111111000 |
++-----------+
+1 row in set (0.06 sec)
+
+```
+### 3. What did you see instead (Required)
+```mysql
+MySQL [test]> select * from t1;
++-----------+
+| col1 |
++-----------+
+| 111111110 |
++-----------+
+1 row in set (0.00 sec)
+
+
+```
+### 4. What is your TiDB version? (Required)
+```mysql
+Release Version: v4.0.11
+Edition: Community
+Git Commit Hash: 058e52ad7c1b477147dcb933b3f1b3b2be31e998
+Git Branch: heads/refs/tags/v4.0.11
+UTC Build Time: 2021-02-25 04:33:58
+GoVersion: go1.13
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+```
+
+
+",True,"The result of bitwise OR is incorrect - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+```mysql
+create table t1(col1 float);
+insert into t1 values(3|111111114);
+```
+
+
+### 2. What did you expect to see? (Required)
+```mysql
+mysql> select * from t1;
++-----------+
+| col1 |
++-----------+
+| 111111000 |
++-----------+
+1 row in set (0.06 sec)
+
+```
+### 3. What did you see instead (Required)
+```mysql
+MySQL [test]> select * from t1;
++-----------+
+| col1 |
++-----------+
+| 111111110 |
++-----------+
+1 row in set (0.00 sec)
+
+
+```
+### 4. What is your TiDB version? (Required)
+```mysql
+Release Version: v4.0.11
+Edition: Community
+Git Commit Hash: 058e52ad7c1b477147dcb933b3f1b3b2be31e998
+Git Branch: heads/refs/tags/v4.0.11
+UTC Build Time: 2021-02-25 04:33:58
+GoVersion: go1.13
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false
+```
+
+
+",1,the result of bitwise or is incorrect bug report please answer these questions before submitting your issue thanks minimal reproduce step required mysql create table float insert into values what did you expect to see required mysql mysql select from row in set sec what did you see instead required mysql mysql select from row in set sec what is your tidb version required mysql release version edition community git commit hash git branch heads refs tags utc build time goversion race enabled false tikv min version check table before drop false ,1
+515490,14964192102.0,IssuesEvent,2021-01-27 11:37:06,StrangeLoopGames/EcoIssues,https://api.github.com/repos/StrangeLoopGames/EcoIssues,opened,[0.9.2 Release-143]Tree and dead animal teleports vertically on each Block Update,Category: Gameplay Priority: Low Type: Bug,"Build: 0.9.2 Release-143
-
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/system.security.cryptography.xml/4.4.0/system.security.cryptography.xml.4.4.0.nupkg
-
+Issue: When a tree is lying down on the top of a crafted block, such as pipes, lumbers, etc, it teleports vertically on every block update. However, it needs to happen near the said tree.
+Condition to trigger the issue: The tree or the body of a dead animal must be on the top of a crafted material and is not touching the solid ground.
-
+Note:
+- This also happens with animals' dead bodies or corpses but is not happening with mining resources.
+- The issue becomes less apparent if some parts of the Tree or the dead body are touching the solid ground. In this case, there's still some noticeable movement in every block update.
+- Potentially related to #12099 with different conditions.
-## Vulnerabilities
+Repro:
+1. Log in to the game as usual.
+2. Craft pipes or logs, ex. Iron Pipe or Hewn Log.
+3. Place it around a Tree or in a fashion where it will catch the Tree after cutting it. (What's important here is that the tree will be on the top of the crafted block.)
+4. Make any block update around the tree and observe. For example, digging some dirt.
-| CVE | Severity | CVSS | Dependency | Type | Fixed in (dotnetcore-sample version) | Remediation Available |
-| ------------- | ------------- | ----- | ----- | ----- | ------------- | --- |
-| [CVE-2018-0787](https://www.mend.io/vulnerability-database/CVE-2018-0787) | High | 8.8 | detected in multiple dependencies | Transitive | N/A* | ❌ |
-| [WS-2018-0608](https://github.com/aspnet/Announcements/issues/300) | High | 7.5 | detected in multiple dependencies | Transitive | N/A* | ❌ |
-| [CVE-2018-0808](https://www.mend.io/vulnerability-database/CVE-2018-0808) | High | 7.5 | detected in multiple dependencies | Transitive | N/A* | ❌ |
-| [WS-2018-0607](https://github.com/aspnet/Announcements/issues/311) | High | 7.5 | microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg | Transitive | N/A* | ❌ |
-| [CVE-2020-1045](https://www.mend.io/vulnerability-database/CVE-2020-1045) | High | 7.5 | microsoft.aspnetcore.http.2.0.0.nupkg | Transitive | N/A* | ❌ |
-| [CVE-2021-1723](https://www.mend.io/vulnerability-database/CVE-2021-1723) | High | 7.5 | microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg | Transitive | N/A* | ❌ |
-| [CVE-2022-34716](https://www.mend.io/vulnerability-database/CVE-2022-34716) | Medium | 5.9 | system.security.cryptography.xml.4.4.0.nupkg | Transitive | N/A* | ❌ |
-
*For some transitive vulnerabilities, there is no version of direct dependency with a fix. Check the section ""Details"" below to see if there is a version of transitive dependency where vulnerability is fixed.
+Result: The Tree teleports vertically in every block update near it.
-## Details
-
+Video
+Tree Teleporting Vertically
+https://images.zenhubusercontent.com/42199084/fca49780-3474-47f0-b089-d35208ea40fb/2021_01_27_16_59.mp4
- CVE-2018-0787
+Animal Dead Body moving slightly in every block update
+https://images.zenhubusercontent.com/42199084/ae749547-8192-41e8-8ced-3c927ad0291f/2021_01_27_17_22.mp4",1.0,"[0.9.2 Release-143]Tree and dead animal teleports vertically on each Block Update - Build: 0.9.2 Release-143
+Issue: When a tree is lying down on the top of a crafted block, such as pipes, lumbers, etc, it teleports vertically on every block update. However, it needs to happen near the said tree.
-### Vulnerable Libraries - microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg, microsoft.aspnetcore.httpoverrides.2.0.0.nupkg
-
+Condition to trigger the issue: The tree or the body of a dead animal must be on the top of a crafted material and is not touching the solid ground.
+Note:
+- This also happens with animals' dead bodies or corpses but is not happening with mining resources.
+- The issue becomes less apparent if some parts of the Tree or the dead body are touching the solid ground. In this case, there's still some noticeable movement in every block update.
+- Potentially related to #12099 with different conditions.
-### microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
+Repro:
+1. Log in to the game as usual.
+2. Craft pipes or logs, ex. Iron Pipe or Hewn Log.
+3. Place it around a Tree or in a fashion where it will catch the Tree after cutting it. (What's important here is that the tree will be on the top of the crafted block.)
+4. Make any block update around the tree and observe. For example, digging some dirt.
-
Core components of ASP.NET Core Kestrel cross-platform web server.
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
-
+Result: The Tree teleports vertically in every block update near it.
-Dependency Hierarchy:
- - dotnetcore-sample-1.0.0 (Root Library)
- - microsoft.aspnetcore.2.0.0.nupkg
- - microsoft.aspnetcore.server.kestrel.2.0.0.nupkg
- - :x: **microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg** (Vulnerable Library)
+Video
+Tree Teleporting Vertically
+https://images.zenhubusercontent.com/42199084/fca49780-3474-47f0-b089-d35208ea40fb/2021_01_27_16_59.mp4
-### microsoft.aspnetcore.httpoverrides.2.0.0.nupkg
+Animal Dead Body moving slightly in every block update
+https://images.zenhubusercontent.com/42199084/ae749547-8192-41e8-8ced-3c927ad0291f/2021_01_27_17_22.mp4",0, tree and dead animal teleports vertically on each block update build release issue when a tree is lying down on the top of a crafted block such as pipes lumbers etc it teleports vertically on every block update however it needs to happen near the said tree condition to trigger the issue the tree or the body of a dead animal must be on the top of a crafted material and is not touching the solid ground note this also happens with animals dead bodies or corpses but is not happening with mining resources the issue becomes less apparent if some parts of the tree or the dead body are touching the solid ground in this case there s still some noticeable movement in every block update potentially related to with different conditions repro log in to the game as usual craft pipes or logs ex iron pipe or hewn log place it around a tree or in a fashion where it will catch the tree after cutting it what s important here is that the tree will be on the top of the crafted block make any block update around the tree and observe for example digging some dirt result the tree teleports vertically in every block update near it video tree teleporting vertically animal dead body moving slightly in every block update ,0
+4826,7447210836.0,IssuesEvent,2018-03-28 11:45:27,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,scientific notation compatibility,compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+exec `select 1e18;`
+
+2. What did you expect to see?
+
+```
+mysql> select 1e18;
++------+
+| 1e18 |
++------+
+| 1e18 |
++------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+mysql> select 1e18;
++---------------------+
+| 1e18 |
++---------------------+
+| 1000000000000000000 |
++---------------------+
+1 row in set (0.00 sec)
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"scientific notation compatibility - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+exec `select 1e18;`
+
+2. What did you expect to see?
+
+```
+mysql> select 1e18;
++------+
+| 1e18 |
++------+
+| 1e18 |
++------+
+1 row in set (0.00 sec)
+```
+
+3. What did you see instead?
+
+mysql> select 1e18;
++---------------------+
+| 1e18 |
++---------------------+
+| 1000000000000000000 |
++---------------------+
+1 row in set (0.00 sec)
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,scientific notation compatibility please answer these questions before submitting your issue thanks what did you do exec select what did you expect to see mysql select row in set sec what did you see instead mysql select row in set sec what version of tidb are you using tidb server v ,1
+6252,8641571142.0,IssuesEvent,2018-11-24 19:10:03,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,incorrect result of cast double to datetime,help wanted type/compatibility,"## 1. What did you do?
+```sql
+select cast(20040101.01234567 as datetime(3));
+```
+
+
+## 2. What did you expect to see?
+
+```sql
+MySQL > select cast(20040101.01234567 as datetime(3));
++----------------------------------------+
+| cast(20040101.01234567 as datetime(3)) |
++----------------------------------------+
+| 2004-01-01 00:00:00.000 |
++----------------------------------------+
+1 row in set (0.00 sec)
+```
+
+## 3. What did you see instead?
+
+```sql
+TiDB > select cast(20040101.01234567 as datetime(3));
++----------------------------------------+
+| cast(20040101.01234567 as datetime(3)) |
++----------------------------------------+
+| 2004-01-01 00:00:00.012 |
++----------------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+## 4. What version of TiDB are you using (`tidb-server -V`)?
+
+```sh
+$./bin/tidb-server -V
+Release Version: 0.9.0
+Git Commit Hash: 31a48f8d757630bba930973b66a380103d038c3c
+Git Commit Branch: master
+UTC Build Time: 2017-09-07 06:37:43
+```
+",True,"incorrect result of cast double to datetime - ## 1. What did you do?
+```sql
+select cast(20040101.01234567 as datetime(3));
+```
+
+
+## 2. What did you expect to see?
+
+```sql
+MySQL > select cast(20040101.01234567 as datetime(3));
++----------------------------------------+
+| cast(20040101.01234567 as datetime(3)) |
++----------------------------------------+
+| 2004-01-01 00:00:00.000 |
++----------------------------------------+
+1 row in set (0.00 sec)
+```
+
+## 3. What did you see instead?
+
+```sql
+TiDB > select cast(20040101.01234567 as datetime(3));
++----------------------------------------+
+| cast(20040101.01234567 as datetime(3)) |
++----------------------------------------+
+| 2004-01-01 00:00:00.012 |
++----------------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+## 4. What version of TiDB are you using (`tidb-server -V`)?
+
+```sh
+$./bin/tidb-server -V
+Release Version: 0.9.0
+Git Commit Hash: 31a48f8d757630bba930973b66a380103d038c3c
+Git Commit Branch: master
+UTC Build Time: 2017-09-07 06:37:43
+```
+",1,incorrect result of cast double to datetime what did you do sql select cast as datetime what did you expect to see sql mysql select cast as datetime cast as datetime row in set sec what did you see instead sql tidb select cast as datetime cast as datetime row in set sec what version of tidb are you using tidb server v sh bin tidb server v release version git commit hash git commit branch master utc build time ,1
+66224,8896208086.0,IssuesEvent,2019-01-16 10:48:16,geosolutions-it/MapStore2,https://api.github.com/repos/geosolutions-it/MapStore2,opened,User Guide - RtD Custom theme,Documentation User Guide investigation,"### Description
+Custom theme for the read the doc user guide.
+
+### Other useful information (optional):
+",1.0,"User Guide - RtD Custom theme - ### Description
+Custom theme for the read the doc user guide.
+
+### Other useful information (optional):
+",0,user guide rtd custom theme description custom theme for the read the doc user guide other useful information optional ,0
+7270,9536898762.0,IssuesEvent,2019-04-30 10:59:38,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,JSON_CONTAIN is not same with mysql.,help wanted type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```SQL
+drop table if exists jemp;
+CREATE TABLE jemp (
+ `id` int(10) unsigned NOT NULL AUTO_INCREMENT,
+ `category` JSON,
+ `tags` JSON,
+ PRIMARY KEY (`id`)
+);
+INSERT INTO `jemp` (category, tags) VALUES ('{""id"": 1, ""name"": ""TiDB""}', '[1, 2, 3]');
+INSERT INTO `jemp` (category, tags) VALUES (JSON_OBJECT(""id"", 2, ""name"", ""pingcap.com""), JSON_ARRAY(1, 3, 5));
+SELECT * FROM jemp WHERE JSON_CONTAINS(category, 1, '$.id');
+```
+
+2. What did you expect to see?
+
+## In MySQL
+```SQL
+mysql> drop table if exists jemp;
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> CREATE TABLE jemp (
+ -> `id` int(10) unsigned NOT NULL AUTO_INCREMENT,
+ -> `category` JSON,
+ -> `tags` JSON,
+ -> PRIMARY KEY (`id`)
+ -> );
+Query OK, 0 rows affected (0.03 sec)
+
+mysql> INSERT INTO `jemp` (category, tags) VALUES ('{""id"": 1, ""name"": ""TiDB""}', '[1, 2, 3]');
+Query OK, 1 row affected (0.01 sec)
+
+mysql> INSERT INTO `jemp` (category, tags) VALUES (JSON_OBJECT(""id"", 2, ""name"", ""pingcap.com""), JSON_ARRAY(1, 3, 5));
+Query OK, 1 row affected (0.00 sec)
+
+mysql> SELECT * FROM jemp WHERE JSON_CONTAINS(category, 1, '$.id');
+ERROR 3146 (22032): Invalid data type for JSON data in argument 2 to function json_contains; a JSON string or JSON type is required.
+
+mysql> select version();
++-------------------------+
+| version() |
++-------------------------+
+| 5.7.25-0ubuntu0.18.04.2 |
++-------------------------+
+1 row in set (0.00 sec)
+
+```
+
+
+3. What did you see instead?
+## In TiDB
+
+```SQL
+mysql> drop table if exists jemp;
+Query OK, 0 rows affected (0.03 sec)
+
+mysql> CREATE TABLE jemp (
+ -> `id` int(10) unsigned NOT NULL AUTO_INCREMENT,
+ -> `category` JSON,
+ -> `tags` JSON,
+ -> PRIMARY KEY (`id`)
+ -> );
+Query OK, 0 rows affected (0.03 sec)
+
+mysql> INSERT INTO `jemp` (category, tags) VALUES ('{""id"": 1, ""name"": ""TiDB""}', '[1, 2, 3]');
+Query OK, 1 row affected (0.01 sec)
+
+mysql> INSERT INTO `jemp` (category, tags) VALUES (JSON_OBJECT(""id"", 2, ""name"", ""pingcap.com""), JSON_ARRAY(1, 3, 5));
+Query OK, 1 row affected (0.00 sec)
+
+mysql> SELECT * FROM jemp WHERE JSON_CONTAINS(category, 1, '$.id');
++----+---------------------------+-----------+
+| id | category | tags |
++----+---------------------------+-----------+
+| 1 | {""id"": 1, ""name"": ""TiDB""} | [1, 2, 3] |
++----+---------------------------+-----------+
+1 row in set (0.01 sec)
+
+```
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+mysql> select tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v3.0.0-beta-295-g97f88f70d
+Git Commit Hash: 97f88f70d56e69d6aef584b2bd4c9ada2ce26598
+Git Branch: master
+UTC Build Time: 2019-03-29 07:34:36
+GoVersion: go version go1.12.1 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false
+1 row in set (0.00 sec)
+```
+",True,"JSON_CONTAIN is not same with mysql. - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```SQL
+drop table if exists jemp;
+CREATE TABLE jemp (
+ `id` int(10) unsigned NOT NULL AUTO_INCREMENT,
+ `category` JSON,
+ `tags` JSON,
+ PRIMARY KEY (`id`)
+);
+INSERT INTO `jemp` (category, tags) VALUES ('{""id"": 1, ""name"": ""TiDB""}', '[1, 2, 3]');
+INSERT INTO `jemp` (category, tags) VALUES (JSON_OBJECT(""id"", 2, ""name"", ""pingcap.com""), JSON_ARRAY(1, 3, 5));
+SELECT * FROM jemp WHERE JSON_CONTAINS(category, 1, '$.id');
+```
+
+2. What did you expect to see?
+
+## In MySQL
+```SQL
+mysql> drop table if exists jemp;
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> CREATE TABLE jemp (
+ -> `id` int(10) unsigned NOT NULL AUTO_INCREMENT,
+ -> `category` JSON,
+ -> `tags` JSON,
+ -> PRIMARY KEY (`id`)
+ -> );
+Query OK, 0 rows affected (0.03 sec)
+
+mysql> INSERT INTO `jemp` (category, tags) VALUES ('{""id"": 1, ""name"": ""TiDB""}', '[1, 2, 3]');
+Query OK, 1 row affected (0.01 sec)
+
+mysql> INSERT INTO `jemp` (category, tags) VALUES (JSON_OBJECT(""id"", 2, ""name"", ""pingcap.com""), JSON_ARRAY(1, 3, 5));
+Query OK, 1 row affected (0.00 sec)
+
+mysql> SELECT * FROM jemp WHERE JSON_CONTAINS(category, 1, '$.id');
+ERROR 3146 (22032): Invalid data type for JSON data in argument 2 to function json_contains; a JSON string or JSON type is required.
+
+mysql> select version();
++-------------------------+
+| version() |
++-------------------------+
+| 5.7.25-0ubuntu0.18.04.2 |
++-------------------------+
+1 row in set (0.00 sec)
+
+```
+
+
+3. What did you see instead?
+## In TiDB
+
+```SQL
+mysql> drop table if exists jemp;
+Query OK, 0 rows affected (0.03 sec)
+
+mysql> CREATE TABLE jemp (
+ -> `id` int(10) unsigned NOT NULL AUTO_INCREMENT,
+ -> `category` JSON,
+ -> `tags` JSON,
+ -> PRIMARY KEY (`id`)
+ -> );
+Query OK, 0 rows affected (0.03 sec)
+
+mysql> INSERT INTO `jemp` (category, tags) VALUES ('{""id"": 1, ""name"": ""TiDB""}', '[1, 2, 3]');
+Query OK, 1 row affected (0.01 sec)
+
+mysql> INSERT INTO `jemp` (category, tags) VALUES (JSON_OBJECT(""id"", 2, ""name"", ""pingcap.com""), JSON_ARRAY(1, 3, 5));
+Query OK, 1 row affected (0.00 sec)
+
+mysql> SELECT * FROM jemp WHERE JSON_CONTAINS(category, 1, '$.id');
++----+---------------------------+-----------+
+| id | category | tags |
++----+---------------------------+-----------+
+| 1 | {""id"": 1, ""name"": ""TiDB""} | [1, 2, 3] |
++----+---------------------------+-----------+
+1 row in set (0.01 sec)
+
+```
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+mysql> select tidb_version()\G
+*************************** 1. row ***************************
+tidb_version(): Release Version: v3.0.0-beta-295-g97f88f70d
+Git Commit Hash: 97f88f70d56e69d6aef584b2bd4c9ada2ce26598
+Git Branch: master
+UTC Build Time: 2019-03-29 07:34:36
+GoVersion: go version go1.12.1 linux/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false
+1 row in set (0.00 sec)
+```
+",1,json contain is not same with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql drop table if exists jemp create table jemp id int unsigned not null auto increment category json tags json primary key id insert into jemp category tags values id name tidb insert into jemp category tags values json object id name pingcap com json array select from jemp where json contains category id what did you expect to see in mysql sql mysql drop table if exists jemp query ok rows affected sec mysql create table jemp id int unsigned not null auto increment category json tags json primary key id query ok rows affected sec mysql insert into jemp category tags values id name tidb query ok row affected sec mysql insert into jemp category tags values json object id name pingcap com json array query ok row affected sec mysql select from jemp where json contains category id error invalid data type for json data in argument to function json contains a json string or json type is required mysql select version version row in set sec what did you see instead in tidb sql mysql drop table if exists jemp query ok rows affected sec mysql create table jemp id int unsigned not null auto increment category json tags json primary key id query ok rows affected sec mysql insert into jemp category tags values id name tidb query ok row affected sec mysql insert into jemp category tags values json object id name pingcap com json array query ok row affected sec mysql select from jemp where json contains category id id category tags id name tidb row in set sec what version of tidb are you using tidb server v or run select tidb version on tidb mysql select tidb version g row tidb version release version beta git commit hash git branch master utc build time goversion go version linux race enabled false tikv min version alpha check table before drop false row in set sec ,1
+490,7868920385.0,IssuesEvent,2018-06-24 06:47:53,dotnet/roslyn,https://api.github.com/repos/dotnet/roslyn,closed,OperationCanceledException during Formatting,Area-IDE Bug Tenet-Reliability,"A customer found this in their activity log after editing JS/TS in a session with responsiveness issues.
+
+```
+System.OperationCanceledException: The operation was canceled.
+ at System.Threading.CancellationToken.ThrowOperationCanceledException()
+ at System.Threading.Tasks.Task.Wait(Int32 millisecondsTimeout, CancellationToken cancellationToken)
+ at Roslyn.Utilities.TaskExtensions.WaitAndGetResult_CanCallOnBackground[T](Task`1 task, CancellationToken cancellationToken)
+ at Microsoft.CodeAnalysis.Editor.Implementation.Formatting.FormatCommandHandler.ExecuteReturnOrTypeCommand(EditorCommandArgs args, Action nextHandler, CancellationToken cancellationToken)
+ at Microsoft.CodeAnalysis.Editor.Implementation.Formatting.FormatCommandHandler.ExecuteCommand(ReturnKeyCommandArgs args, Action nextHandler, CommandExecutionContext context)
+ at Microsoft.VisualStudio.Commanding.CommandHandlerExtensions.ExecuteCommand[T](ICommandHandler commandHandler, T args, Action nextCommandHandler, CommandExecutionContext executionContext)
+ at Microsoft.VisualStudio.UI.Text.Commanding.Implementation.EditorCommandHandlerService.<>c__DisplayClass14_1`1.<Execute>b__1()
+ at Microsoft.VisualStudio.Text.Utilities.GuardedOperations.CallExtensionPoint(Object errorSource, Action call)
+--- End of stack trace from previous location where exception was thrown ---
+ at Microsoft.VisualStudio.Telemetry.WindowsErrorReporting.WatsonReport.GetClrWatsonExceptionInfo(Exception exceptionObject)
+```
+
+My guess is that JS/TS formatting was too slow and either the user or a timeout attempted to cancel the operation. Perhaps OperationCanceledException is not supposed to bubble out of a command handler?",True,"OperationCanceledException during Formatting - A customer found this in their activity log after editing JS/TS in a session with responsiveness issues.
+
+```
+System.OperationCanceledException: The operation was canceled.
+ at System.Threading.CancellationToken.ThrowOperationCanceledException()
+ at System.Threading.Tasks.Task.Wait(Int32 millisecondsTimeout, CancellationToken cancellationToken)
+ at Roslyn.Utilities.TaskExtensions.WaitAndGetResult_CanCallOnBackground[T](Task`1 task, CancellationToken cancellationToken)
+ at Microsoft.CodeAnalysis.Editor.Implementation.Formatting.FormatCommandHandler.ExecuteReturnOrTypeCommand(EditorCommandArgs args, Action nextHandler, CancellationToken cancellationToken)
+ at Microsoft.CodeAnalysis.Editor.Implementation.Formatting.FormatCommandHandler.ExecuteCommand(ReturnKeyCommandArgs args, Action nextHandler, CommandExecutionContext context)
+ at Microsoft.VisualStudio.Commanding.CommandHandlerExtensions.ExecuteCommand[T](ICommandHandler commandHandler, T args, Action nextCommandHandler, CommandExecutionContext executionContext)
+ at Microsoft.VisualStudio.UI.Text.Commanding.Implementation.EditorCommandHandlerService.<>c__DisplayClass14_1`1.<Execute>b__1()
+ at Microsoft.VisualStudio.Text.Utilities.GuardedOperations.CallExtensionPoint(Object errorSource, Action call)
+--- End of stack trace from previous location where exception was thrown ---
+ at Microsoft.VisualStudio.Telemetry.WindowsErrorReporting.WatsonReport.GetClrWatsonExceptionInfo(Exception exceptionObject)
+```
+
+My guess is that JS/TS formatting was too slow and either the user or a timeout attempted to cancel the operation. Perhaps OperationCanceledException is not supposed to bubble out of a command handler?",0,operationcanceledexception during formatting a customer found this in their activity log after editing js ts in a session with responsiveness issues system operationcanceledexception the operation was canceled at system threading cancellationtoken throwoperationcanceledexception at system threading tasks task wait millisecondstimeout cancellationtoken cancellationtoken at roslyn utilities taskextensions waitandgetresult cancallonbackground task task cancellationtoken cancellationtoken at microsoft codeanalysis editor implementation formatting formatcommandhandler executereturnortypecommand editorcommandargs args action nexthandler cancellationtoken cancellationtoken at microsoft codeanalysis editor implementation formatting formatcommandhandler executecommand returnkeycommandargs args action nexthandler commandexecutioncontext context at microsoft visualstudio commanding commandhandlerextensions executecommand icommandhandler commandhandler t args action nextcommandhandler commandexecutioncontext executioncontext at microsoft visualstudio ui text commanding implementation editorcommandhandlerservice lt gt c lt execute gt b at microsoft visualstudio text utilities guardedoperations callextensionpoint object errorsource action call end of stack trace from previous location where exception was thrown at microsoft visualstudio telemetry windowserrorreporting watsonreport getclrwatsonexceptioninfo exception exceptionobject my guess is that js ts formatting was too slow and either the user or a timeout attempted to cancel the operation perhaps operationcanceledexception is not supposed to bubble out of a command handler ,0
+11030,13065156815.0,IssuesEvent,2020-07-30 19:19:18,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,no support of type `long`,type/compatibility,"
+
+
+In MySQL:
+``` sql
+mysql> create table t (a long not null);
+Query OK, 0 rows affected (0.03 sec)
+```
+
+In TiDB:
+``` sql
+tidb> create table t (a long not null);
+ERROR 1105 (HY000): line 0 column 22 near "" not null)"" (total length 32)
+```
+
+
+What version of TiDB are you using (`tidb-server -V`)?
+
+```
+Git Commit Hash: 91fa992f1da80f1065891bb80d81b7f20a883ef7
+UTC Build Time: 2017-07-28 04:30:15
+```",True,"no support of type `long` -
+
+
+In MySQL:
+``` sql
+mysql> create table t (a long not null);
+Query OK, 0 rows affected (0.03 sec)
+```
+
+In TiDB:
+``` sql
+tidb> create table t (a long not null);
+ERROR 1105 (HY000): line 0 column 22 near "" not null)"" (total length 32)
+```
+
+
+What version of TiDB are you using (`tidb-server -V`)?
+
+```
+Git Commit Hash: 91fa992f1da80f1065891bb80d81b7f20a883ef7
+UTC Build Time: 2017-07-28 04:30:15
+```",1,no support of type long in mysql sql mysql create table t a long not null query ok rows affected sec in tidb sql tidb create table t a long not null error line column near not null total length what version of tidb are you using tidb server v git commit hash utc build time ,1
+6993,9285409420.0,IssuesEvent,2019-03-21 07:00:31,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,`str_to_date` is not compatible with MySQL,for new contributors help wanted type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+create table t1 (date char(30), format char(30) not null);
+insert into t1 values
+('2003-01-02 10:11:12 PM', '%Y-%m-%d %H:%i:%S %p'),
+('10:20:10AM', '%H:%i:%s%p');
+select date,format,str_to_date(date, format) as str_to_date from t1;
+```
+
+2. What did you expect to see?
+In Mysql
+```
+mysql> create table t1 (date char(30), format char(30) not null);
+Query OK, 0 rows affected (0.02 sec)
+
+mysql> insert into t1 values
+ -> ('2003-01-02 10:11:12 PM', '%Y-%m-%d %H:%i:%S %p'),
+ -> ('10:20:10AM', '%H:%i:%s%p');
+Query OK, 2 rows affected (0.00 sec)
+Records: 2 Duplicates: 0 Warnings: 0
+
+mysql> select date,format,str_to_date(date, format) as str_to_date from t1;
++------------------------+----------------------+-------------+
+| date | format | str_to_date |
++------------------------+----------------------+-------------+
+| 2003-01-02 10:11:12 PM | %Y-%m-%d %H:%i:%S %p | NULL |
+| 10:20:10AM | %H:%i:%s%p | NULL |
++------------------------+----------------------+-------------+
+2 rows in set, 4 warnings (0.00 sec)
+```
+
+
+3. What did you see instead?
+In TiDB
+```
+mysql> create table t1 (date char(30), format char(30) not null);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> insert into t1 values
+ -> ('2003-01-02 10:11:12 PM', '%Y-%m-%d %H:%i:%S %p'),
+ -> ('10:20:10AM', '%H:%i:%s%p');
+Query OK, 2 rows affected (0.01 sec)
+Records: 2 Duplicates: 0 Warnings: 0
+
+mysql> select date,format,str_to_date(date, format) as str_to_date from t1;
++------------------------+----------------------+----------------------------+
+| date | format | str_to_date |
++------------------------+----------------------+----------------------------+
+| 2003-01-02 10:11:12 PM | %Y-%m-%d %H:%i:%S %p | 2003-01-02 22:11:12.000000 |
+| 10:20:10AM | %H:%i:%s%p | 0000-00-00 10:20:10.000000 |
++------------------------+----------------------+----------------------------+
+2 rows in set (0.00 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-227-g06183393e-dirty
+Git Commit Hash: 06183393ed536aa248248b72d4bf9f5010947f66
+Git Branch: master
+UTC Build Time: 2019-03-15 08:22:53
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+```
+",True,"`str_to_date` is not compatible with MySQL - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+create table t1 (date char(30), format char(30) not null);
+insert into t1 values
+('2003-01-02 10:11:12 PM', '%Y-%m-%d %H:%i:%S %p'),
+('10:20:10AM', '%H:%i:%s%p');
+select date,format,str_to_date(date, format) as str_to_date from t1;
+```
+
+2. What did you expect to see?
+In Mysql
+```
+mysql> create table t1 (date char(30), format char(30) not null);
+Query OK, 0 rows affected (0.02 sec)
+
+mysql> insert into t1 values
+ -> ('2003-01-02 10:11:12 PM', '%Y-%m-%d %H:%i:%S %p'),
+ -> ('10:20:10AM', '%H:%i:%s%p');
+Query OK, 2 rows affected (0.00 sec)
+Records: 2 Duplicates: 0 Warnings: 0
+
+mysql> select date,format,str_to_date(date, format) as str_to_date from t1;
++------------------------+----------------------+-------------+
+| date | format | str_to_date |
++------------------------+----------------------+-------------+
+| 2003-01-02 10:11:12 PM | %Y-%m-%d %H:%i:%S %p | NULL |
+| 10:20:10AM | %H:%i:%s%p | NULL |
++------------------------+----------------------+-------------+
+2 rows in set, 4 warnings (0.00 sec)
+```
+
+
+3. What did you see instead?
+In TiDB
+```
+mysql> create table t1 (date char(30), format char(30) not null);
+Query OK, 0 rows affected (0.01 sec)
+
+mysql> insert into t1 values
+ -> ('2003-01-02 10:11:12 PM', '%Y-%m-%d %H:%i:%S %p'),
+ -> ('10:20:10AM', '%H:%i:%s%p');
+Query OK, 2 rows affected (0.01 sec)
+Records: 2 Duplicates: 0 Warnings: 0
+
+mysql> select date,format,str_to_date(date, format) as str_to_date from t1;
++------------------------+----------------------+----------------------------+
+| date | format | str_to_date |
++------------------------+----------------------+----------------------------+
+| 2003-01-02 10:11:12 PM | %Y-%m-%d %H:%i:%S %p | 2003-01-02 22:11:12.000000 |
+| 10:20:10AM | %H:%i:%s%p | 0000-00-00 10:20:10.000000 |
++------------------------+----------------------+----------------------------+
+2 rows in set (0.00 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-227-g06183393e-dirty
+Git Commit Hash: 06183393ed536aa248248b72d4bf9f5010947f66
+Git Branch: master
+UTC Build Time: 2019-03-15 08:22:53
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+```
+",1, str to date is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error create table date char format char not null insert into values pm y m d h i s p h i s p select date format str to date date format as str to date from what did you expect to see in mysql mysql create table date char format char not null query ok rows affected sec mysql insert into values pm y m d h i s p h i s p query ok rows affected sec records duplicates warnings mysql select date format str to date date format as str to date from date format str to date pm y m d h i s p null h i s p null rows in set warnings sec what did you see instead in tidb mysql create table date char format char not null query ok rows affected sec mysql insert into values pm y m d h i s p h i s p query ok rows affected sec records duplicates warnings mysql select date format str to date date format as str to date from date format str to date pm y m d h i s p h i s p rows in set sec what version of tidb are you using tidb server v or run select tidb version on tidb tidb version release version beta dirty git commit hash git branch master utc build time goversion go version darwin race enabled false tikv min version alpha check table before drop false ,1
+26536,13047320747.0,IssuesEvent,2020-07-29 10:30:00,polsys/ennemi,https://api.github.com/repos/polsys/ennemi,opened,Drop support for Python 3.6,maintenance performance,"Related to #59. Should be done in 1.1 as NumPy is also dropping 3.6 support by then. Not going to drop support in 1.0 because at least Ubuntu 18.04 LTS uses 3.6 as its default interpreter.
+
+- [ ] By using `from __future__ import annotations`, we should get a performance benefit and simplify the annotations (will still need to check if e.g. `list` becomes a synonym for `typing.List` already in 3.7)
+- [ ] Other changes we can take advantage of?",True,"Drop support for Python 3.6 - Related to #59. Should be done in 1.1 as NumPy is also dropping 3.6 support by then. Not going to drop support in 1.0 because at least Ubuntu 18.04 LTS uses 3.6 as its default interpreter.
+
+- [ ] By using `from __future__ import annotations`, we should get a performance benefit and simplify the annotations (will still need to check if e.g. `list` becomes a synonym for `typing.List` already in 3.7)
+- [ ] Other changes we can take advantage of?",0,drop support for python related to should be done in as numpy is also dropping support by then not going to drop support in because at least ubuntu lts uses as its default interpreter by using from future import annotations we should get a performance benefit and simplify the annotations will still need to check if e g list becomes a synonym for typing list already in other changes we can take advantage of ,0
+238054,19694490725.0,IssuesEvent,2022-01-12 10:40:01,dotnet/sdk,https://api.github.com/repos/dotnet/sdk,closed,"With .NET 7 x86 SDK, Testhost process exited with error: It was not possible to find any compatible framework version",Area-DotNet Test untriaged,"**--Repro Steps---**
+1. Install .NET 7 x86 SDK(https://github.com/dotnet/installer) on Win x64 OS
+2. Create a UT project and run it
+
+**--Expected Result --**
+1. dotnet test works fine
+
+**--Actual Result--**
+1. Testhost process exited with error: It was not possible to find any compatible framework version
+The framework 'Microsoft.NETCore.App', version '7.0.0-alpha.1.22059.2' (x64) was not found.
+
+
+**--Note--**
+It didnot repro with .NET 6 x86 SDK
+
+**Dotnet info**
+c:\6t>dotnet --info
+.NET SDK (reflecting any global.json):
+ Version: 7.0.100-alpha.1.22060.7
+ Commit: 4a2d57a652
+
+Runtime Environment:
+ OS Name: Windows
+ OS Version: 10.0.22000
+ OS Platform: Windows
+ RID: win10-x86
+ Base Path: C:\Program Files (x86)\dotnet\sdk\7.0.100-alpha.1.22060.7\
+
+Host (useful for support):
+ Version: 7.0.0-alpha.1.22059.2
+ Commit: a2af629476
+
+.NET SDKs installed:
+ 6.0.200-preview.22055.18 [C:\Program Files (x86)\dotnet\sdk]
+ 7.0.100-alpha.1.22060.7 [C:\Program Files (x86)\dotnet\sdk]
+
+.NET runtimes installed:
+ Microsoft.AspNetCore.App 6.0.1 [C:\Program Files (x86)\dotnet\shared\Microsoft.AspNetCore.App]
+ Microsoft.AspNetCore.App 7.0.0-alpha.1.22057.17 [C:\Program Files (x86)\dotnet\shared\Microsoft.AspNetCore.App]
+ Microsoft.NETCore.App 6.0.1 [C:\Program Files (x86)\dotnet\shared\Microsoft.NETCore.App]
+ Microsoft.NETCore.App 7.0.0-alpha.1.22059.2 [C:\Program Files (x86)\dotnet\shared\Microsoft.NETCore.App]
+ Microsoft.WindowsDesktop.App 6.0.1 [C:\Program Files (x86)\dotnet\shared\Microsoft.WindowsDesktop.App]
+ Microsoft.WindowsDesktop.App 7.0.0-alpha.1.22055.1 [C:\Program Files (x86)\dotnet\shared\Microsoft.WindowsDesktop.App]
+
+To install additional .NET runtimes or SDKs:
+ https://aka.ms/dotnet-download
+",1.0,"With .NET 7 x86 SDK, Testhost process exited with error: It was not possible to find any compatible framework version - **--Repro Steps---**
+1. Install .NET 7 x86 SDK(https://github.com/dotnet/installer) on Win x64 OS
+2. Create a UT project and run it
+
+**--Expected Result --**
+1. dotnet test works fine
+
+**--Actual Result--**
+1. Testhost process exited with error: It was not possible to find any compatible framework version
+The framework 'Microsoft.NETCore.App', version '7.0.0-alpha.1.22059.2' (x64) was not found.
+
+
+**--Note--**
+It didnot repro with .NET 6 x86 SDK
+
+**Dotnet info**
+c:\6t>dotnet --info
+.NET SDK (reflecting any global.json):
+ Version: 7.0.100-alpha.1.22060.7
+ Commit: 4a2d57a652
+
+Runtime Environment:
+ OS Name: Windows
+ OS Version: 10.0.22000
+ OS Platform: Windows
+ RID: win10-x86
+ Base Path: C:\Program Files (x86)\dotnet\sdk\7.0.100-alpha.1.22060.7\
+
+Host (useful for support):
+ Version: 7.0.0-alpha.1.22059.2
+ Commit: a2af629476
+
+.NET SDKs installed:
+ 6.0.200-preview.22055.18 [C:\Program Files (x86)\dotnet\sdk]
+ 7.0.100-alpha.1.22060.7 [C:\Program Files (x86)\dotnet\sdk]
+
+.NET runtimes installed:
+ Microsoft.AspNetCore.App 6.0.1 [C:\Program Files (x86)\dotnet\shared\Microsoft.AspNetCore.App]
+ Microsoft.AspNetCore.App 7.0.0-alpha.1.22057.17 [C:\Program Files (x86)\dotnet\shared\Microsoft.AspNetCore.App]
+ Microsoft.NETCore.App 6.0.1 [C:\Program Files (x86)\dotnet\shared\Microsoft.NETCore.App]
+ Microsoft.NETCore.App 7.0.0-alpha.1.22059.2 [C:\Program Files (x86)\dotnet\shared\Microsoft.NETCore.App]
+ Microsoft.WindowsDesktop.App 6.0.1 [C:\Program Files (x86)\dotnet\shared\Microsoft.WindowsDesktop.App]
+ Microsoft.WindowsDesktop.App 7.0.0-alpha.1.22055.1 [C:\Program Files (x86)\dotnet\shared\Microsoft.WindowsDesktop.App]
+
+To install additional .NET runtimes or SDKs:
+ https://aka.ms/dotnet-download
+",0,with net sdk testhost process exited with error it was not possible to find any compatible framework version repro steps install net sdk on win os create a ut project and run it expected result dotnet test works fine actual result testhost process exited with error it was not possible to find any compatible framework version the framework microsoft netcore app version alpha was not found note it didnot repro with net sdk dotnet info c dotnet info net sdk reflecting any global json version alpha commit runtime environment os name windows os version os platform windows rid base path c program files dotnet sdk alpha host useful for support version alpha commit net sdks installed preview alpha net runtimes installed microsoft aspnetcore app microsoft aspnetcore app alpha microsoft netcore app microsoft netcore app alpha microsoft windowsdesktop app microsoft windowsdesktop app alpha to install additional net runtimes or sdks ,0
+18507,25714264128.0,IssuesEvent,2022-12-07 09:14:14,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,enable foreign_key_checks variable by default ,type/compatibility,"## Dev Task
+
+The default value of `foreign_key_checks` in MySQL is `true`, but TiDB is `false`. Since TiDB already supported foreign key, PM @easonn7 thinks the default value of `foreign_key_checks` should be consistent with MySQL.",True,"enable foreign_key_checks variable by default - ## Dev Task
+
+The default value of `foreign_key_checks` in MySQL is `true`, but TiDB is `false`. Since TiDB already supported foreign key, PM @easonn7 thinks the default value of `foreign_key_checks` should be consistent with MySQL.",1,enable foreign key checks variable by default dev task the default value of foreign key checks in mysql is true but tidb is false since tidb already supported foreign key pm thinks the default value of foreign key checks should be consistent with mysql ,1
+19659,11269018401.0,IssuesEvent,2020-01-14 07:54:49,Azure/azure-cli,https://api.github.com/repos/Azure/azure-cli,closed,Cannot create custom metric alert via azure cli.,Feature Request Monitor Monitor - Alerts Service Attention,"Note: this pertains to
+https://docs.microsoft.com/en-us/cli/azure/monitor/metrics?view=azure-cli-latest#az-monitor-metrics-list-definitions
+and
+https://docs.microsoft.com/en-us/cli/azure/monitor/metrics/alert?view=azure-cli-latest#az-monitor-metrics-alert-create
+
+**Describe the bug**
+I ran
+```
+$aiid = ""/subscriptions/CENSORED/resourceGroups/CENSORED/providers/microsoft.insights/components/CENSORED""
+az monitor metrics list-definitions --resource $aiid
+```
+and expected to see my custom metric definitions (in custom namespaces), but didn't found any custom metrics.
+
+**To Reproduce**
+Log a custom metric from the source code using ApplicationIsnights. Observe you can create an alert using it it via azure portal, or view it in metrics view in AI. However, it is not listed via `list-definitions`, nor you can create an alert via Azure CLI using it, as it is not found.
+
+**Expected behavior**
+The custom metric (and its namespace) to be listed, and accepted when creating an alert with `az monitor metrics alert create`.
+
+**Environment summary**
+```
+az --version
+azure-cli 2.0.66
+```
+
+**Additional context**
+Confirmed the custom metrics also cannot be found via
+```
+Get-AzMetricDefinition -ResourceId $aiid
+```
+",1.0,"Cannot create custom metric alert via azure cli. - Note: this pertains to
+https://docs.microsoft.com/en-us/cli/azure/monitor/metrics?view=azure-cli-latest#az-monitor-metrics-list-definitions
+and
+https://docs.microsoft.com/en-us/cli/azure/monitor/metrics/alert?view=azure-cli-latest#az-monitor-metrics-alert-create
+
+**Describe the bug**
+I ran
+```
+$aiid = ""/subscriptions/CENSORED/resourceGroups/CENSORED/providers/microsoft.insights/components/CENSORED""
+az monitor metrics list-definitions --resource $aiid
+```
+and expected to see my custom metric definitions (in custom namespaces), but didn't found any custom metrics.
+
+**To Reproduce**
+Log a custom metric from the source code using ApplicationIsnights. Observe you can create an alert using it it via azure portal, or view it in metrics view in AI. However, it is not listed via `list-definitions`, nor you can create an alert via Azure CLI using it, as it is not found.
+
+**Expected behavior**
+The custom metric (and its namespace) to be listed, and accepted when creating an alert with `az monitor metrics alert create`.
+
+**Environment summary**
+```
+az --version
+azure-cli 2.0.66
+```
+
+**Additional context**
+Confirmed the custom metrics also cannot be found via
+```
+Get-AzMetricDefinition -ResourceId $aiid
+```
+",0,cannot create custom metric alert via azure cli note this pertains to and describe the bug i ran aiid subscriptions censored resourcegroups censored providers microsoft insights components censored az monitor metrics list definitions resource aiid and expected to see my custom metric definitions in custom namespaces but didn t found any custom metrics to reproduce log a custom metric from the source code using applicationisnights observe you can create an alert using it it via azure portal or view it in metrics view in ai however it is not listed via list definitions nor you can create an alert via azure cli using it as it is not found expected behavior the custom metric and its namespace to be listed and accepted when creating an alert with az monitor metrics alert create environment summary az version azure cli additional context confirmed the custom metrics also cannot be found via get azmetricdefinition resourceid aiid ,0
+61628,17023743636.0,IssuesEvent,2021-07-03 03:36:26,tomhughes/trac-tickets,https://api.github.com/repos/tomhughes/trac-tickets,closed,"can't create table - ERROR: type ""hstore"" does not exist",Component: osmosis Priority: minor Resolution: invalid Type: defect,"**[Submitted to the original trac issue database at 4.02pm, Monday, 29th August 2011]**
-
ASP.NET Core basic middleware for supporting HTTP method overrides. Includes:
-* X-Forwarded-* header...
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.httpoverrides/2.0.0/microsoft.aspnetcore.httpoverrides.2.0.0.nupkg
+Hi,
+
+I am trying to create a new database under postgresql 9.1rc1 with osmosis 0.39 and
+
+psql -d osm -f pgsnapshot_schema_0.6.sql
+
+
+getting the error message
+psql:pgsnapshot_schema_0.6.sql:52: ERROR: type ""hstore"" does not exist
+
+",1.0,"can't create table - ERROR: type ""hstore"" does not exist - **[Submitted to the original trac issue database at 4.02pm, Monday, 29th August 2011]**
+
+Hi,
+
+I am trying to create a new database under postgresql 9.1rc1 with osmosis 0.39 and
+
+psql -d osm -f pgsnapshot_schema_0.6.sql
+
+
+getting the error message
+psql:pgsnapshot_schema_0.6.sql:52: ERROR: type ""hstore"" does not exist
+
+",0,can t create table error type hstore does not exist hi i am trying to create a new database under postgresql with osmosis and psql d osm f pgsnapshot schema sql getting the error message psql pgsnapshot schema sql error type hstore does not exist ,0
+830603,32018798984.0,IssuesEvent,2023-09-22 01:29:51,steedos/steedos-platform,https://api.github.com/repos/steedos/steedos-platform,closed,[Bug]: 软件包中扩展设置菜单,点击菜单中自定义的选项卡未显示微页面,bug done priority: High,"### Description
+
+
+
+
+
+admin.app.yml中添加新的tab_items指向自定义的应用程序微页面
+点击菜单中的选项卡,微页面未显示
+
+### Steps To Reproduce 重现步骤
+
+1. 新建 应用程序 微页面 admin_pm_card
+2. 新建 选项卡 admin_pm_card
+3. admin.app.yml中配置
+```yml
+code: admin
+name: admin_pm
+tab_items:
+ admin_pm_card:
+ group: app_settings
+ index: 50
+```
+
+
+### Version 版本
+
+2.5.13-beta.22",1.0,"[Bug]: 软件包中扩展设置菜单,点击菜单中自定义的选项卡未显示微页面 - ### Description
+
+
+
+
+
+admin.app.yml中添加新的tab_items指向自定义的应用程序微页面
+点击菜单中的选项卡,微页面未显示
+
+### Steps To Reproduce 重现步骤
+
+1. 新建 应用程序 微页面 admin_pm_card
+2. 新建 选项卡 admin_pm_card
+3. admin.app.yml中配置
+```yml
+code: admin
+name: admin_pm
+tab_items:
+ admin_pm_card:
+ group: app_settings
+ index: 50
+```
+
+
+### Version 版本
+
+2.5.13-beta.22",0, 软件包中扩展设置菜单,点击菜单中自定义的选项卡未显示微页面 description admin app yml中添加新的tab items指向自定义的应用程序微页面 点击菜单中的选项卡,微页面未显示 steps to reproduce 重现步骤 新建 应用程序 微页面 admin pm card 新建 选项卡 admin pm card admin app yml中配置 yml code admin name admin pm tab items admin pm card group app settings index version 版本 beta ,0
+136191,19721781888.0,IssuesEvent,2022-01-13 16:00:54,elastic/kibana,https://api.github.com/repos/elastic/kibana,opened,[Maps][Meta] Usability issues on LAYERS and the layer config modal flyouts,bug discuss Team:Geo triage_needed design,"**Kibana version:**
+8
+
+**1. LAYERS panel flies left and right, when the layer config sidebar comes and goes**
+A UI principle is that hotspots, buttons and other affordances are not supposed to fly out from underneath the user's pointer on activation. Right now, when clicking the little pencil icon, the entire LAYERS panel flies away from underneath the pointer
+Irrespective of this, and the current jank (see below) it is jarring to see the panel fly left and right anyway.
+
+**2. LAYERS panel fly is tweened in one direction but sudden in the other**
+It should be consistent. It doesn't feel like the difference in behavior is due to more jank in one direction than in the other, but maybe it is
+
+**3. UI and sometimes the entire browser (tab switch etc.) are blocked for several seconds after common interactions**
+Clicking on the little pencil will elicit the flyout of the right sidebar layer config panel. It moves/resizes the actual map view, which I think is the culprit. A consequence is that even when the user gets a jankily sliding out config panel, not even the scrolling of the sidebar works, for numerous seconds. Other things are blocked too. Suggested solution: such interactions should not resize/alter the actual map layer. Mapbox/Maplibre are rather heavy and expensive components so the jank/freeze cost isn't even commensurate with the actual rendering task. Let's talk if someone is on the opinion that blocking the UI this way is still OK UX
+
+**4. Easy loss of layer config changes**
+Steps to reproduce:
+1. Painstakingly configure a layer
+2. Multitask: fill a gh report, check out weather.com etc
+3. Come back and absent-mindedly make the config sidebar go away with the bottom left button (which surely says Cancel but it'd be nice to ask for user confirmation to help avoid lost config)
+An alternative is that instead of our heavy (and to me, ill understood) adherence to the ""Apply/Cancel"" pattern, we'd have proper undo/redo
+
+
+",1.0,"[Maps][Meta] Usability issues on LAYERS and the layer config modal flyouts - **Kibana version:**
+8
+
+**1. LAYERS panel flies left and right, when the layer config sidebar comes and goes**
+A UI principle is that hotspots, buttons and other affordances are not supposed to fly out from underneath the user's pointer on activation. Right now, when clicking the little pencil icon, the entire LAYERS panel flies away from underneath the pointer
+Irrespective of this, and the current jank (see below) it is jarring to see the panel fly left and right anyway.
+
+**2. LAYERS panel fly is tweened in one direction but sudden in the other**
+It should be consistent. It doesn't feel like the difference in behavior is due to more jank in one direction than in the other, but maybe it is
+
+**3. UI and sometimes the entire browser (tab switch etc.) are blocked for several seconds after common interactions**
+Clicking on the little pencil will elicit the flyout of the right sidebar layer config panel. It moves/resizes the actual map view, which I think is the culprit. A consequence is that even when the user gets a jankily sliding out config panel, not even the scrolling of the sidebar works, for numerous seconds. Other things are blocked too. Suggested solution: such interactions should not resize/alter the actual map layer. Mapbox/Maplibre are rather heavy and expensive components so the jank/freeze cost isn't even commensurate with the actual rendering task. Let's talk if someone is on the opinion that blocking the UI this way is still OK UX
+
+**4. Easy loss of layer config changes**
+Steps to reproduce:
+1. Painstakingly configure a layer
+2. Multitask: fill a gh report, check out weather.com etc
+3. Come back and absent-mindedly make the config sidebar go away with the bottom left button (which surely says Cancel but it'd be nice to ask for user confirmation to help avoid lost config)
+An alternative is that instead of our heavy (and to me, ill understood) adherence to the ""Apply/Cancel"" pattern, we'd have proper undo/redo
+
+
+",0, usability issues on layers and the layer config modal flyouts kibana version layers panel flies left and right when the layer config sidebar comes and goes a ui principle is that hotspots buttons and other affordances are not supposed to fly out from underneath the user s pointer on activation right now when clicking the little pencil icon the entire layers panel flies away from underneath the pointer irrespective of this and the current jank see below it is jarring to see the panel fly left and right anyway layers panel fly is tweened in one direction but sudden in the other it should be consistent it doesn t feel like the difference in behavior is due to more jank in one direction than in the other but maybe it is ui and sometimes the entire browser tab switch etc are blocked for several seconds after common interactions clicking on the little pencil will elicit the flyout of the right sidebar layer config panel it moves resizes the actual map view which i think is the culprit a consequence is that even when the user gets a jankily sliding out config panel not even the scrolling of the sidebar works for numerous seconds other things are blocked too suggested solution such interactions should not resize alter the actual map layer mapbox maplibre are rather heavy and expensive components so the jank freeze cost isn t even commensurate with the actual rendering task let s talk if someone is on the opinion that blocking the ui this way is still ok ux easy loss of layer config changes steps to reproduce painstakingly configure a layer multitask fill a gh report check out weather com etc come back and absent mindedly make the config sidebar go away with the bottom left button which surely says cancel but it d be nice to ask for user confirmation to help avoid lost config an alternative is that instead of our heavy and to me ill understood adherence to the apply cancel pattern we d have proper undo redo ,0
+9734,11783446045.0,IssuesEvent,2020-03-17 05:36:55,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,window function: group_concat error message is not compatible,challenge-program-2 component/planner difficulty/easy good-first-issue help-wanted type/bug type/compatibility,"## Description
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```mysql
+mysql> select group_concat('3') over ();
+ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your TiDB version for the right syntax to use line 1 column 29 near ""over ()""
+```
+
+2. What did you expect to see?
+
+```
+mysql> select group_concat('3') over ();
+ERROR 1235 (42000): This version of MySQL doesn't yet support 'group_concat as window function'
+```
+
+## Score
+
+* 50
+
+## Mentor(s)
+
+* @SunRunAway
+
+Contact the mentors: **#tidb-challenge-program** channel in [TiDB Community](https://join.slack.com/t/tidbcommunity/shared_invite/enQtNzc0MzI4ODExMDc4LWYwYmIzMjZkYzJiNDUxMmZlN2FiMGJkZjAyMzQ5NGU0NGY0NzI3NTYwMjAyNGQ1N2I2ZjAxNzc1OGUwYWM0NzE) Slack Workspace
+
+## Recommended Skills
+
+* Golang Programming.
+* Be familiar with window function and TiDB Parser.
+
+## Learning Materials
+
+* Chinese: [TiDB 精选技术讲解文章](https://github.com/pingcap/presentations/blob/master/hackathon-2019/reference-document-of-hackathon-2019.md)
+* English: [Awesome-Database-Learning](https://github.com/pingcap/awesome-database-learning)",True,"window function: group_concat error message is not compatible - ## Description
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```mysql
+mysql> select group_concat('3') over ();
+ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your TiDB version for the right syntax to use line 1 column 29 near ""over ()""
+```
+
+2. What did you expect to see?
+
+```
+mysql> select group_concat('3') over ();
+ERROR 1235 (42000): This version of MySQL doesn't yet support 'group_concat as window function'
+```
+
+## Score
+
+* 50
+
+## Mentor(s)
+
+* @SunRunAway
+
+Contact the mentors: **#tidb-challenge-program** channel in [TiDB Community](https://join.slack.com/t/tidbcommunity/shared_invite/enQtNzc0MzI4ODExMDc4LWYwYmIzMjZkYzJiNDUxMmZlN2FiMGJkZjAyMzQ5NGU0NGY0NzI3NTYwMjAyNGQ1N2I2ZjAxNzc1OGUwYWM0NzE) Slack Workspace
+
+## Recommended Skills
+
+* Golang Programming.
+* Be familiar with window function and TiDB Parser.
+
+## Learning Materials
+
+* Chinese: [TiDB 精选技术讲解文章](https://github.com/pingcap/presentations/blob/master/hackathon-2019/reference-document-of-hackathon-2019.md)
+* English: [Awesome-Database-Learning](https://github.com/pingcap/awesome-database-learning)",1,window function group concat error message is not compatible description please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error mysql mysql select group concat over error you have an error in your sql syntax check the manual that corresponds to your tidb version for the right syntax to use line column near over what did you expect to see mysql select group concat over error this version of mysql doesn t yet support group concat as window function score mentor s sunrunaway contact the mentors tidb challenge program channel in slack workspace recommended skills golang programming be familiar with window function and tidb parser learning materials chinese english ,1
+261678,27810334238.0,IssuesEvent,2023-03-18 03:14:40,KOSASIH/SilkRoad,https://api.github.com/repos/KOSASIH/SilkRoad,closed,jquery-1.12.0.min.js: 4 vulnerabilities (highest severity is: 6.1),Mend: dependency security vulnerability," Vulnerable Library - jquery-1.12.0.min.js
+
+
-ASP.NET Core 1.0. 1.1, and 2.0 allow an elevation of privilege vulnerability due to how web applications that are created from templates validate web requests, aka ""ASP.NET Core Elevation Of Privilege Vulnerability"".
+In jQuery versions greater than or equal to 1.0.3 and before 3.5.0, passing HTML containing
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.transport.abstractions/2.0.0/microsoft.aspnetcore.server.kestrel.transport.abstractions.2.0.0.nupkg
-
+Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
+
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.transport.libuv/2.0.0/microsoft.aspnetcore.server.kestrel.transport.libuv.2.0.0.nupkg
-A vulnerability was discovered in versions 2.x of ASP.NET Core where a specially crafted request can cause excess resource consumption in Kestrel.
+In jQuery versions greater than or equal to 1.2 and before 3.5.0, passing HTML from untrusted sources - even after sanitizing it - to one of jQuery's DOM manipulation methods (i.e. .html(), .append(), and others) may execute untrusted code. This problem is patched in jQuery 3.5.0.
-
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.iisintegration/2.0.0/microsoft.aspnetcore.server.iisintegration.2.0.0.nupkg
-
+Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
+
-ASP.NET Core 1.0. 1.1, and 2.0 allow an elevation of privilege vulnerability due to how ASP.NET web applications handle web requests, aka ""ASP.NET Core Elevation Of Privilege Vulnerability"". This CVE is unique from CVE-2018-0784.
+jQuery before 3.0.0 is vulnerable to Cross-site Scripting (XSS) attacks when a cross-domain Ajax request is performed without the dataType option, causing text/javascript responses to be executed.
-
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
-Denial of service vulnerability in ASP.NET Core when a malformed request is terminated.
+jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.
-
-
- CVE-2020-1045
+Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
+",True,"jquery-1.12.0.min.js: 4 vulnerabilities (highest severity is: 6.1) - Vulnerable Library - jquery-1.12.0.min.js
+
-A security feature bypass vulnerability exists in the way Microsoft ASP.NET Core parses encoded cookie names.The ASP.NET Core cookie parser decodes entire cookie strings which could allow a malicious attacker to set a second cookie with the name being percent encoded.The security update addresses the vulnerability by fixing the way the ASP.NET Core cookie parser handles encoded names., aka 'Microsoft ASP.NET Core Security Feature Bypass Vulnerability'.
+In jQuery versions greater than or equal to 1.0.3 and before 3.5.0, passing HTML containing
Path to dependency file: /TopLevel/Project1/pipelines-dotnet-core/dotnetcore-tests/dotnetcore-tests.csproj
-
Path to vulnerable library: /home/wss-scanner/.nuget/packages/microsoft.aspnetcore.server.kestrel.core/2.0.0/microsoft.aspnetcore.server.kestrel.core.2.0.0.nupkg
-ASP.NET Core and Visual Studio Denial of Service Vulnerability
+In jQuery versions greater than or equal to 1.2 and before 3.5.0, passing HTML from untrusted sources - even after sanitizing it - to one of jQuery's DOM manipulation methods (i.e. .html(), .append(), and others) may execute untrusted code. This problem is patched in jQuery 3.5.0.
-
-Microsoft is releasing this security advisory to provide information about a vulnerability in .NET Core 3.1 and .NET 6.0. An information disclosure vulnerability exists in .NET Core 3.1 and .NET 6.0 that could lead to unauthorized access of privileged information.
+jQuery before 3.0.0 is vulnerable to Cross-site Scripting (XSS) attacks when a cross-domain Ajax request is performed without the dataType option, causing text/javascript responses to be executed.
-## Affected software
-
-* Any .NET 6.0 application running on .NET 6.0.7 or earlier.
-* Any .NET Core 3.1 applicaiton running on .NET Core 3.1.27 or earlier.
-
-## Patches
-
-* If you're using .NET 6.0, you should download and install Runtime 6.0.8 or SDK 6.0.108 (for Visual Studio 2022 v17.1) from https://dotnet.microsoft.com/download/dotnet-core/6.0.
-* If you're using .NET Core 3.1, you should download and install Runtime 3.1.28 (for Visual Studio 2019 v16.9) from https://dotnet.microsoft.com/download/dotnet-core/3.1.
-
-
-",0,dotnetcore sample vulnerabilities highest severity is autoclosed vulnerable library dotnetcore sample path to vulnerable library home wss scanner nuget packages system security cryptography xml system security cryptography xml nupkg found in head commit a href vulnerabilities cve severity cvss dependency type fixed in dotnetcore sample version remediation available high detected in multiple dependencies transitive n a high detected in multiple dependencies transitive n a high detected in multiple dependencies transitive n a high microsoft aspnetcore server kestrel core nupkg transitive n a high microsoft aspnetcore http nupkg transitive n a high microsoft aspnetcore server kestrel core nupkg transitive n a medium system security cryptography xml nupkg transitive n a for some transitive vulnerabilities there is no version of direct dependency with a fix check the section details below to see if there is a version of transitive dependency where vulnerability is fixed details cve vulnerable libraries microsoft aspnetcore server kestrel core nupkg microsoft aspnetcore httpoverrides nupkg microsoft aspnetcore server kestrel core nupkg core components of asp net core kestrel cross platform web server library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore server kestrel core microsoft aspnetcore server kestrel core nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg x microsoft aspnetcore server kestrel core nupkg vulnerable library microsoft aspnetcore httpoverrides nupkg asp net core basic middleware for supporting http method overrides includes x forwarded header library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore httpoverrides microsoft aspnetcore httpoverrides nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server iisintegration nupkg x microsoft aspnetcore httpoverrides nupkg vulnerable library found in head commit a href found in base branch main vulnerability details asp net core and allow an elevation of privilege vulnerability due to how web applications that are created from templates validate web requests aka asp net core elevation of privilege vulnerability publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution microsoft aspnetcore httpoverrides microsoft aspnetcore server kestrel core ws vulnerable libraries microsoft aspnetcore server kestrel core nupkg microsoft aspnetcore server kestrel transport abstractions nupkg microsoft aspnetcore server kestrel transport libuv nupkg microsoft aspnetcore server kestrel core nupkg core components of asp net core kestrel cross platform web server library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore server kestrel core microsoft aspnetcore server kestrel core nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg x microsoft aspnetcore server kestrel core nupkg vulnerable library microsoft aspnetcore server kestrel transport abstractions nupkg transport abstractions for the asp net core kestrel cross platform web server library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore server kestrel transport abstractions microsoft aspnetcore server kestrel transport abstractions nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg microsoft aspnetcore server kestrel transport libuv nupkg x microsoft aspnetcore server kestrel transport abstractions nupkg vulnerable library microsoft aspnetcore server kestrel transport libuv nupkg libuv transport for the asp net core kestrel cross platform web server library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore server kestrel transport libuv microsoft aspnetcore server kestrel transport libuv nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg x microsoft aspnetcore server kestrel transport libuv nupkg vulnerable library found in head commit a href found in base branch main vulnerability details a vulnerability was discovered in versions x of asp net core where a specially crafted request can cause excess resource consumption in kestrel publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution microsoft aspnetcore server kestrel core microsoft aspnetcore server kestrel transport abstractions microsoft aspnetcore server kestrel transport libuv microsoft aspnetcore all cve vulnerable libraries microsoft aspnetcore server iisintegration nupkg microsoft aspnetcore hosting nupkg microsoft aspnetcore server iisintegration nupkg asp net core components for working with the iis aspnetcoremodule library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore server iisintegration microsoft aspnetcore server iisintegration nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg x microsoft aspnetcore server iisintegration nupkg vulnerable library microsoft aspnetcore hosting nupkg asp net core hosting infrastructure and startup logic for web applications library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore hosting microsoft aspnetcore hosting nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg x microsoft aspnetcore hosting nupkg vulnerable library found in head commit a href found in base branch main vulnerability details asp net core and allow an elevation of privilege vulnerability due to how asp net web applications handle web requests aka asp net core elevation of privilege vulnerability this cve is unique from cve publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution microsoft aspnetcore server iisintegration microsoft aspnetcore hosting ws vulnerable library microsoft aspnetcore server kestrel core nupkg core components of asp net core kestrel cross platform web server library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore server kestrel core microsoft aspnetcore server kestrel core nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg x microsoft aspnetcore server kestrel core nupkg vulnerable library found in head commit a href found in base branch main vulnerability details denial of service vulnerability in asp net core when a malformed request is terminated publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution microsoft aspnetcore server kestrel core cve vulnerable library microsoft aspnetcore http nupkg asp net core default http feature implementations library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore http microsoft aspnetcore http nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg microsoft aspnetcore hosting nupkg x microsoft aspnetcore http nupkg vulnerable library found in head commit a href found in base branch main vulnerability details a security feature bypass vulnerability exists in the way microsoft asp net core parses encoded cookie names the asp net core cookie parser decodes entire cookie strings which could allow a malicious attacker to set a second cookie with the name being percent encoded the security update addresses the vulnerability by fixing the way the asp net core cookie parser handles encoded names aka microsoft asp net core security feature bypass vulnerability publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact high availability impact none for more information on scores click a href suggested fix type upgrade version release date fix resolution microsoft aspnetcore app microsoft aspnetcore all microsoft netcore app microsoft aspnetcore http cve vulnerable library microsoft aspnetcore server kestrel core nupkg core components of asp net core kestrel cross platform web server library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages microsoft aspnetcore server kestrel core microsoft aspnetcore server kestrel core nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore nupkg microsoft aspnetcore server kestrel nupkg x microsoft aspnetcore server kestrel core nupkg vulnerable library found in head commit a href found in base branch main vulnerability details asp net core and visual studio denial of service vulnerability publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution microsoft aspnetcore app runtime win livereloadserver plugga core maple branch module microsoft aspnetcore components webassembly server rc aspnetcoreruntime aspnetcoreruntime microsoft aspnetcore app runtime osx grazedocs microsoft aspnetcore app runtime linux musl arm microsoft aspnetcore app runtime linux musl yhwins template microsoft aspnetcore app runtime linux musl microsoft aspnetcore app runtime linux microsoft aspnetcore app ref rc microsoft aspnetcore blazor devserver microsoft aspnetcore app runtime linux arm microsoft aspnetcore app runtime linux stankins console toolbelt blazor devserver withcsslivereloader rc dragonfire server alpha poextractor orchardcore microsoft aspnetcore app runtime win arm microsoft aspnetcore app runtime win microsoft aspnetcore app runtime win hulu template api aspnetcoreruntime aspnetcoreruntime microsoft aspnetcore components webassembly devserver rc microsoft aspnetcore app runtime win lingman webapi cve vulnerable library system security cryptography xml nupkg provides classes to support the creation and validation of xml digital signatures the classes in th library home page a href path to dependency file toplevel pipelines dotnet core dotnetcore tests dotnetcore tests csproj path to vulnerable library home wss scanner nuget packages system security cryptography xml system security cryptography xml nupkg dependency hierarchy dotnetcore sample root library microsoft aspnetcore mvc nupkg microsoft aspnetcore mvc viewfeatures nupkg microsoft aspnetcore antiforgery nupkg microsoft aspnetcore dataprotection nupkg x system security cryptography xml nupkg vulnerable library found in head commit a href found in base branch main vulnerability details microsoft is releasing this security advisory to provide information about a vulnerability in net core and net an information disclosure vulnerability exists in net core and net that could lead to unauthorized access of privileged information affected software any net application running on net or earlier any net core applicaiton running on net core or earlier patches if you re using net you should download and install runtime or sdk for visual studio from if you re using net core you should download and install runtime for visual studio from publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact none availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution microsoft aspnetcore app runtime linux arm microsoft aspnetcore app runtime linux microsoft aspnetcore app runtime linux musl arm microsoft aspnetcore app runtime linux musl microsoft aspnetcore app runtime linux musl microsoft aspnetcore app runtime linux microsoft aspnetcore app runtime osx microsoft aspnetcore app runtime win arm microsoft aspnetcore app runtime win microsoft aspnetcore app runtime win microsoft aspnetcore app runtime win system security cryptography xml ,0
-19269,26766613367.0,IssuesEvent,2023-01-31 11:05:57,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Column names incorrect when using a non default delimiter,type/compatibility sig/sql-infra type/feature-request severity/minor compatibility-mysql8 affects-6.4 affects-6.5,"## Bug Report
-
-This is with MySQL Shell 8.0 as client. I would expect that this also happens with MySQL Client.
-```
-sql> delimiter $$
-
-sql> SELECT 1; SELECT 2; $$
-+--------------+
-| 1; SELECT 2; |
-+--------------+
-| 1 |
-+--------------+
-1 row in set (0.0004 sec)
-
-+----+
-| 2; |
-+----+
-| 2 |
-+----+
-1 row in set (0.0004 sec)
-
-sql> SELECT 1 AS 'a'; SELECT 2 AS 'b'; $$
-+---+
-| a |
-+---+
-| 1 |
-+---+
-1 row in set (0.0004 sec)
-
-+---+
-| b |
-+---+
-| 2 |
-+---+
-1 row in set (0.0004 sec)
-
-sql> delimiter ;
-
-sql> SELECT tidb_version()\G
-*************************** 1. row ***************************
-tidb_version(): Release Version: v6.4.0
-Edition: Community
-Git Commit Hash: cf36a9ce2fe1039db3cf3444d51930b887df18a1
-Git Branch: heads/refs/tags/v6.4.0
-UTC Build Time: 2022-11-13 05:25:30
-GoVersion: go1.19.2
-Race Enabled: false
-TiKV Min Version: 6.2.0-alpha
-Check Table Before Drop: false
-Store: tikv
-1 row in set (0.0003 sec)
-```
-
-I expected this to have the same column names as when the default delimiter is used:
-```
-sql> SELECT 1; SELECT 2;
-+---+
-| 1 |
-+---+
-| 1 |
-+---+
-1 row in set (0.0006 sec)
-+---+
-| 2 |
-+---+
-| 2 |
-+---+
-1 row in set (0.0002 sec)
-```",True,"Column names incorrect when using a non default delimiter - ## Bug Report
-
-This is with MySQL Shell 8.0 as client. I would expect that this also happens with MySQL Client.
-
-```
-sql> delimiter $$
-
-sql> SELECT 1; SELECT 2; $$
-+--------------+
-| 1; SELECT 2; |
-+--------------+
-| 1 |
-+--------------+
-1 row in set (0.0004 sec)
-
-+----+
-| 2; |
-+----+
-| 2 |
-+----+
-1 row in set (0.0004 sec)
-
-sql> SELECT 1 AS 'a'; SELECT 2 AS 'b'; $$
-+---+
-| a |
-+---+
-| 1 |
-+---+
-1 row in set (0.0004 sec)
-
-+---+
-| b |
-+---+
-| 2 |
-+---+
-1 row in set (0.0004 sec)
-
-sql> delimiter ;
-
-sql> SELECT tidb_version()\G
-*************************** 1. row ***************************
-tidb_version(): Release Version: v6.4.0
-Edition: Community
-Git Commit Hash: cf36a9ce2fe1039db3cf3444d51930b887df18a1
-Git Branch: heads/refs/tags/v6.4.0
-UTC Build Time: 2022-11-13 05:25:30
-GoVersion: go1.19.2
-Race Enabled: false
-TiKV Min Version: 6.2.0-alpha
-Check Table Before Drop: false
-Store: tikv
-1 row in set (0.0003 sec)
-```
+Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
+
-I expected this to have the same column names as when the default delimiter is used:
-```
-sql> SELECT 1; SELECT 2;
-+---+
-| 1 |
-+---+
-| 1 |
-+---+
-1 row in set (0.0006 sec)
-+---+
-| 2 |
-+---+
-| 2 |
-+---+
-1 row in set (0.0002 sec)
-```",1,column names incorrect when using a non default delimiter bug report this is with mysql shell as client i would expect that this also happens with mysql client sql delimiter sql select select select row in set sec row in set sec sql select as a select as b a row in set sec b row in set sec sql delimiter sql select tidb version g row tidb version release version edition community git commit hash git branch heads refs tags utc build time goversion race enabled false tikv min version alpha check table before drop false store tikv row in set sec i expected this to have the same column names as when the default delimiter is used sql select select row in set sec row in set sec ,1
-38730,5002728904.0,IssuesEvent,2016-12-11 15:08:59,HeitzmanCo/ChristChurchRaleigh-Theme,https://api.github.com/repos/HeitzmanCo/ChristChurchRaleigh-Theme,closed,Put the blue bar back.,design,I like it. Can I see the one with the circle in the middle (where the chicken goes?),1.0,Put the blue bar back. - I like it. Can I see the one with the circle in the middle (where the chicken goes?),0,put the blue bar back i like it can i see the one with the circle in the middle where the chicken goes ,0
-170429,14260029849.0,IssuesEvent,2020-11-20 09:13:49,jfm1006/GESPRO_PracticaGestionTareas_2021,https://api.github.com/repos/jfm1006/GESPRO_PracticaGestionTareas_2021,closed,Pasar anexos a latex,documentation," **Anexos**
-- [x] Plan del proyecto software
-- [x] Especificación de Requisitos
-- [x] Especificación de diseño
-- [x] Manual del programador
-- [x] Manual de usuario
+ CVE-2019-11358
-Expresión regular para corregir las referencias:
-- Buscar: (\{\[\})([\w:\\]+)(\{\]\}\\\_)
-- Reemplazar por: \\citep{\2}
+### Vulnerable Library - jquery-1.12.0.min.js
-Ej: {[}art:campbell2005{]}\_ -> \citep{art:campbell2005}
+
+
-- Buscar: (\\includegraphics{..\/..\/img\/)(\w*)(.\w*\})
-- Reemplazar por: \\imagen{\2}{descripción...}
+
-Ej: \includegraphics{../../img/s2.png} -> \imagen{s2}{descripción...}}",1.0,"Pasar anexos a latex - **Anexos**
-- [x] Plan del proyecto software
-- [x] Especificación de Requisitos
-- [x] Especificación de diseño
-- [x] Manual del programador
-- [x] Manual de usuario
+### Vulnerability Details
+
+
+jQuery before 3.4.0, as used in Drupal, Backdrop CMS, and other products, mishandles jQuery.extend(true, {}, ...) because of Object.prototype pollution. If an unsanitized source object contained an enumerable __proto__ property, it could extend the native Object.prototype.
-Expresión regular para corregir las referencias:
+
+For more information on CVSS3 Scores, click here.
+
-- Buscar: (\\includegraphics{..\/..\/img\/)(\w*)(.\w*\})
-- Reemplazar por: \\imagen{\2}{descripción...}
+
-Ej: \includegraphics{../../img/s2.png} -> \imagen{s2}{descripción...}}",0,pasar anexos a latex anexos plan del proyecto software especificación de requisitos especificación de diseño manual del programador manual de usuario expresión regular para corregir las referencias buscar reemplazar por citep ej citep art expresión regular para corregir las imágenes buscar includegraphics img w w reemplazar por imagen descripción ej includegraphics img png imagen descripción ,0
-16349,22037681061.0,IssuesEvent,2022-05-28 21:22:50,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,no warning info for config deleted and change to system variable,type/bug type/compatibility component/config sig/sql-infra severity/moderate may-affects-4.0 may-affects-5.1 may-affects-5.2 may-affects-5.3 may-affects-5.4 may-affects-5.0 may-affects-6.0 affects-6.1,"## Bug Report
-
-Please answer these questions before submitting your issue. Thanks!
-
-### 1. Minimal reproduce step (Required)
-
-1. install v6.0.0 include following config:
-server_configs:
- tidb:
- enable-batch-dml: true
- experimental.enable-global-kill: false
- log.query-log-max-len: 4000
- mem-quota-query: 0
- oom-action: log
- performance.committer-concurrency: 120
- performance.run-auto-analyze: true
- performance.txn-entry-size-limit: 6000000
- performance.txn-total-size-limit: 6000000
- prepared-plan-cache.capacity: 2000
- prepared-plan-cache.enabled: true
- security.require-secure-transport: false
-2. upgrade to v6.1.0 nightly
-
-### 2. What did you expect to see? (Required)
-according to the discussion with PM, when the old cluster includes the above configs, during upgrade, the tidb node should report
-a warning to tell the user that these configs have been deleted and converted to system variables.
-
-### 3. What did you see instead (Required)
-no waring found
-+ [ Serial ] - InitConfig: cluster=local, user=tidb, host=172.16.5.101, path=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache/tidb-4000.service, deploy_dir=/home/tidb/deploy/tidb-4000, data_dir=[], log_dir=/home/tidb/deploy/tidb-4000/log, cache_dir=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache
-+ [ Serial ] - InitConfig: cluster=local, user=tidb, host=172.16.5.101, path=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache/tidb-14000.service, deploy_dir=/home/tidb/deploy/tidb-14000, data_dir=[], log_dir=/home/tidb/deploy/tidb-14000/log, cache_dir=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache
-
-
-### 4. What is your TiDB version? (Required)
-
-Git Commit Hash: 388b3c79cc3a313aee59334ebe6fc7dc451769c3
-Git Branch: heads/refs/tags/v6.1.0-alpha
-UTC Build Time: 2022-05-22 15:03:09
-
-",True,"no warning info for config deleted and change to system variable - ## Bug Report
-
-Please answer these questions before submitting your issue. Thanks!
-
-### 1. Minimal reproduce step (Required)
-
-1. install v6.0.0 include following config:
-server_configs:
- tidb:
- enable-batch-dml: true
- experimental.enable-global-kill: false
- log.query-log-max-len: 4000
- mem-quota-query: 0
- oom-action: log
- performance.committer-concurrency: 120
- performance.run-auto-analyze: true
- performance.txn-entry-size-limit: 6000000
- performance.txn-total-size-limit: 6000000
- prepared-plan-cache.capacity: 2000
- prepared-plan-cache.enabled: true
- security.require-secure-transport: false
-2. upgrade to v6.1.0 nightly
-
-### 2. What did you expect to see? (Required)
-according to the discussion with PM, when the old cluster includes the above configs, during upgrade, the tidb node should report
-a warning to tell the user that these configs have been deleted and converted to system variables.
-
-### 3. What did you see instead (Required)
-no waring found
-+ [ Serial ] - InitConfig: cluster=local, user=tidb, host=172.16.5.101, path=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache/tidb-4000.service, deploy_dir=/home/tidb/deploy/tidb-4000, data_dir=[], log_dir=/home/tidb/deploy/tidb-4000/log, cache_dir=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache
-+ [ Serial ] - InitConfig: cluster=local, user=tidb, host=172.16.5.101, path=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache/tidb-14000.service, deploy_dir=/home/tidb/deploy/tidb-14000, data_dir=[], log_dir=/home/tidb/deploy/tidb-14000/log, cache_dir=/home/tidb/.tiup/storage/cluster/clusters/local/config-cache
-
-
-### 4. What is your TiDB version? (Required)
-
-Git Commit Hash: 388b3c79cc3a313aee59334ebe6fc7dc451769c3
-Git Branch: heads/refs/tags/v6.1.0-alpha
-UTC Build Time: 2022-05-22 15:03:09
+### Suggested Fix
+
-",1,no warning info for config deleted and change to system variable bug report please answer these questions before submitting your issue thanks minimal reproduce step required install include following config server configs tidb enable batch dml true experimental enable global kill false log query log max len mem quota query oom action log performance committer concurrency performance run auto analyze true performance txn entry size limit performance txn total size limit prepared plan cache capacity prepared plan cache enabled true security require secure transport false upgrade to nightly what did you expect to see required according to the discussion with pm when the old cluster includes the above configs during upgrade the tidb node should report a warning to tell the user that these configs have been deleted and converted to system variables what did you see instead required no waring found initconfig cluster local user tidb host path home tidb tiup storage cluster clusters local config cache tidb service deploy dir home tidb deploy tidb data dir log dir home tidb deploy tidb log cache dir home tidb tiup storage cluster clusters local config cache initconfig cluster local user tidb host path home tidb tiup storage cluster clusters local config cache tidb service deploy dir home tidb deploy tidb data dir log dir home tidb deploy tidb log cache dir home tidb tiup storage cluster clusters local config cache what is your tidb version required git commit hash git branch heads refs tags alpha utc build time ,1
-473821,13648131595.0,IssuesEvent,2020-09-26 07:29:38,TerryCavanagh/diceydungeonsbeta,https://api.github.com/repos/TerryCavanagh/diceydungeonsbeta,closed,"Downgraded Bronze Cauldron's description just says ""(reuseable)""",High Priority release candidate v0.1,"
-Will update with a screenshot if it happens again, but I think it's because the equipment.csv description is incomplete",1.0,"Downgraded Bronze Cauldron's description just says ""(reuseable)"" - 
-Will update with a screenshot if it happens again, but I think it's because the equipment.csv description is incomplete",0,downgraded bronze cauldron s description just says reuseable will update with a screenshot if it happens again but i think it s because the equipment csv description is incomplete,0
-389593,11504288053.0,IssuesEvent,2020-02-12 22:56:01,cuappdev/pollo-ios,https://api.github.com/repos/cuappdev/pollo-ios,opened,Deleting question on professor side records incorrect index,Priority: High Type: Bug,"If I have 3 polls and I delete the 2nd poll (currently at 2/3), the current behavior is to slide the next poll into my current position (so I would expect to be at 2/2). However, the indexing leaves me at (1/2). This is bad because let's say I delete the 2nd poll (2/3) and try to delete the live poll (2/2), the app thinks I'm at 1/2 and will delete the first poll I didn't mean to delete.",1.0,"Deleting question on professor side records incorrect index - If I have 3 polls and I delete the 2nd poll (currently at 2/3), the current behavior is to slide the next poll into my current position (so I would expect to be at 2/2). However, the indexing leaves me at (1/2). This is bad because let's say I delete the 2nd poll (2/3) and try to delete the live poll (2/2), the app thinks I'm at 1/2 and will delete the first poll I didn't mean to delete.",0,deleting question on professor side records incorrect index if i have polls and i delete the poll currently at the current behavior is to slide the next poll into my current position so i would expect to be at however the indexing leaves me at this is bad because let s say i delete the poll and try to delete the live poll the app thinks i m at and will delete the first poll i didn t mean to delete ,0
-4323,7045264199.0,IssuesEvent,2018-01-01 17:08:42,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,invalid time cast bug.,compatibility help wanted,"Please answer these questions before submitting your issue. Thanks!
+
-1. What did you do?
+
-`select cast('239010' as time);`
+
-2. What did you expect to see?
+Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
+",0,jquery min js vulnerabilities highest severity is vulnerable library jquery min js javascript library for dom operations library home page a href path to dependency file content css index htm path to vulnerable library content css index htm found in head commit a href vulnerabilities cve severity cvss dependency type fixed in jquery version remediation available medium jquery min js direct jquery jquery rails medium jquery min js direct jquery medium jquery min js direct jquery medium jquery min js direct jquery details cve vulnerable library jquery min js javascript library for dom operations library home page a href path to dependency file content css index htm path to vulnerable library content css index htm dependency hierarchy x jquery min js vulnerable library found in head commit a href found in base branch main vulnerability details in jquery versions greater than or equal to and before passing html containing elements from untrusted sources even after sanitizing it to one of jquery s dom manipulation methods i e html append and others may execute untrusted code this problem is patched in jquery publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution jquery jquery rails step up your open source security game with mend cve vulnerable library jquery min js javascript library for dom operations library home page a href path to dependency file content css index htm path to vulnerable library content css index htm dependency hierarchy x jquery min js vulnerable library found in head commit a href found in base branch main vulnerability details in jquery versions greater than or equal to and before passing html from untrusted sources even after sanitizing it to one of jquery s dom manipulation methods i e html append and others may execute untrusted code this problem is patched in jquery publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution jquery step up your open source security game with mend cve vulnerable library jquery min js javascript library for dom operations library home page a href path to dependency file content css index htm path to vulnerable library content css index htm dependency hierarchy x jquery min js vulnerable library found in head commit a href found in base branch main vulnerability details jquery before is vulnerable to cross site scripting xss attacks when a cross domain ajax request is performed without the datatype option causing text javascript responses to be executed publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution jquery step up your open source security game with mend cve vulnerable library jquery min js javascript library for dom operations library home page a href path to dependency file content css index htm path to vulnerable library content css index htm dependency hierarchy x jquery min js vulnerable library found in head commit a href found in base branch main vulnerability details jquery before as used in drupal backdrop cms and other products mishandles jquery extend true because of object prototype pollution if an unsanitized source object contained an enumerable proto property it could extend the native object prototype publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution jquery step up your open source security game with mend ,0
+205952,23364687278.0,IssuesEvent,2022-08-10 14:28:50,jgeraigery/Baragon---TEST,https://api.github.com/repos/jgeraigery/Baragon---TEST,opened,jetty-server-9.4.18.v20190429.jar: 5 vulnerabilities (highest severity is: 7.5),security vulnerability," Vulnerable Library - jetty-server-9.4.18.v20190429.jar
-```
-mysql> select cast('239010' as time);
-+------------------------+
-| cast('239010' as time) |
-+------------------------+
-| NULL |
-+------------------------+
-1 row in set, 1 warning (0.00 sec)
-
-mysql> show warnings;
-+---------+------+------------------------------------------+
-| Level | Code | Message |
-+---------+------+------------------------------------------+
-| Warning | 1292 | Truncated incorrect time value: '239010' |
-+---------+------+------------------------------------------+
-1 row in set (0.04 sec)
-```
+
Path to vulnerable library: /home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/sitory/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar
+
-3. What did you see instead?
-```
-mysql> select cast('239010' as time);
-+------------------------+
-| cast('239010' as time) |
-+------------------------+
-| 24:30:10 |
-+------------------------+
-1 row in set (0.00 sec)
-```
+
Path to dependency file: /BaragonAgentService/pom.xml
+
Path to vulnerable library: /home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-io/9.4.18.v20190429/jetty-io-9.4.18.v20190429.jar,/home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-io/9.4.18.v20190429/jetty-io-9.4.18.v20190429.jar,/home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-io/9.4.18.v20190429/jetty-io-9.4.18.v20190429.jar
+
-```
-mysql> select cast('239010' as time);
-+------------------------+
-| cast('239010' as time) |
-+------------------------+
-| 24:30:10 |
-+------------------------+
-1 row in set (0.00 sec)
-```
+Dependency Hierarchy:
+ - jetty-server-9.4.18.v20190429.jar (Root Library)
+ - :x: **jetty-io-9.4.18.v20190429.jar** (Vulnerable Library)
+
+
+
-4. What version of TiDB are you using (`tidb-server -V`)?
+### Vulnerability Details
+
+
+In Eclipse Jetty 7.2.2 to 9.4.38, 10.0.0.alpha0 to 10.0.1, and 11.0.0.alpha0 to 11.0.1, CPU usage can reach 100% upon receiving a large invalid TLS frame.
-```
-Release Version: 0.8.0
-Git Commit Hash: ae512b3e3e66eb2464be71d42cc61cbd2302b302
-Git Branch: master
-UTC Build Time: 2017-08-20 09:27:45
-```",1,invalid time cast bug please answer these questions before submitting your issue thanks what did you do select cast as time what did you expect to see mysql select cast as time cast as time null row in set warning sec mysql show warnings level code message warning truncated incorrect time value row in set sec what did you see instead mysql select cast as time cast as time row in set sec what version of tidb are you using tidb server v release version git commit hash git branch master utc build time ,1
-20759,27492774604.0,IssuesEvent,2023-03-04 20:38:42,Azure/azure-sdk-tools,https://api.github.com/repos/Azure/azure-sdk-tools,closed,"Define role, responsibilities, and more for Service buddy",Engagement Experience WS: Process Tools & Automation,"The purpose of this Epic is to focus on defining the roles and responsibilities, tools for people to do their job, and mechanisms to build in accountability for the service buddy for Cadl ",1.0,"Define role, responsibilities, and more for Service buddy - The purpose of this Epic is to focus on defining the roles and responsibilities, tools for people to do their job, and mechanisms to build in accountability for the service buddy for Cadl ",0,define role responsibilities and more for service buddy the purpose of this epic is to focus on defining the roles and responsibilities tools for people to do their job and mechanisms to build in accountability for the service buddy for cadl ,0
-6415,8713685984.0,IssuesEvent,2018-12-07 03:55:51,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Character set name is case sensitive in TiDB,type/compatibility,"## Bug Report
+
Direct dependency fix Resolution (org.eclipse.jetty:jetty-server): 9.4.39.v20210325
-Can't recognize UTF8, if I change to utf8, it can be created
+
-Is there a parameter that can be controlled case-sensitive
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-1.0.8 to 2.0.8
-",True,"Character set name is case sensitive in TiDB - ## Bug Report
-Please answer these questions before submitting your issue. Thanks!
+:rescue_worker_helmet: Automatic Remediation is available for this issue
+
-1. What did you do?
+ CVE-2021-28169
-I use mydumper from version 1. 0 dumper to version 2. 0. 8.for example, character sets are case-sensitive.
+### Vulnerable Library - jetty-server-9.4.18.v20190429.jar
-2. What did you expect to see?
-I can loader to 2.0.8
+
Path to vulnerable library: /home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/sitory/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar
+
-3. What did you see instead?
-dumper sql:
-create table test
-(id int)
-ENGINE=InnoDB DEFAULT CHARSET=UTF8 COLLATE=UTF8_BIN;
+Dependency Hierarchy:
+ - :x: **jetty-server-9.4.18.v20190429.jar** (Vulnerable Library)
+
+
-Can't recognize UTF8, if I change to utf8, it can be created
+
-Is there a parameter that can be controlled case-sensitive
+### Vulnerability Details
+
+
+For Eclipse Jetty versions <= 9.4.40, <= 10.0.2, <= 11.0.2, it is possible for requests to the ConcatServlet with a doubly encoded path to access protected resources within the WEB-INF directory. For example a request to `/concat?/%2557EB-INF/web.xml` can retrieve the web.xml file. This can reveal sensitive information regarding the implementation of a web application.
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-1.0.8 to 2.0.8
-",1,character set name is case sensitive in tidb bug report please answer these questions before submitting your issue thanks what did you do i use mydumper from version dumper to version for example character sets are case sensitive what did you expect to see i can loader to what did you see instead dumper sql create table test id int engine innodb default charset collate bin can t recognize if i change to it can be created is there a parameter that can be controlled case sensitive what version of tidb are you using tidb server v or run select tidb version on tidb to ,1
-226852,18044983162.0,IssuesEvent,2021-09-18 18:40:03,skyjake/lagrange,https://api.github.com/repos/skyjake/lagrange,closed,Broken text rendering,bug needs testing,"Lagrange sometimes fails at rendering text (missing characters and lines out of place; see images) in the main text display, side interfaces, and context menus.
-This is somehow dependent on text scaling: text rendering frequently breaks down or fixes itself when zoom-level is changed.
+
+
-Things I have tried that don't fix it:
-* changing the font
-* enabling ""monospace body""
-* changing line width
-* disabling ""wrap plain text""
+
-This happens on Lagrange 1.5.2, installed on Windows 7 from `lagrange_v1.5.2_windows-x64_setup.exe`.
+### CVSS 3 Score Details (5.3)
+
-
-
-",1.0,"Broken text rendering - Lagrange sometimes fails at rendering text (missing characters and lines out of place; see images) in the main text display, side interfaces, and context menus.
-This is somehow dependent on text scaling: text rendering frequently breaks down or fixes itself when zoom-level is changed.
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Network
+ - Attack Complexity: Low
+ - Privileges Required: None
+ - User Interaction: None
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: Low
+ - Integrity Impact: None
+ - Availability Impact: None
+
+For more information on CVSS3 Scores, click here.
+
-Things I have tried that don't fix it:
-* changing the font
-* enabling ""monospace body""
-* changing line width
-* disabling ""wrap plain text""
+
-This happens on Lagrange 1.5.2, installed on Windows 7 from `lagrange_v1.5.2_windows-x64_setup.exe`.
+### Suggested Fix
+
-
-
-",0,broken text rendering lagrange sometimes fails at rendering text missing characters and lines out of place see images in the main text display side interfaces and context menus this is somehow dependent on text scaling text rendering frequently breaks down or fixes itself when zoom level is changed things i have tried that don t fix it changing the font enabling monospace body changing line width disabling wrap plain text this happens on lagrange installed on windows from lagrange windows setup exe ,0
-5647,8126480512.0,IssuesEvent,2018-08-17 02:29:36,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,"When the field list of the select statement contains the Enum type, the client will report an error",component/expression for new contributors help wanted status/TODO type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
Path to vulnerable library: /home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/sitory/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar
+
-The client reported the following error message:
+Dependency Hierarchy:
+ - :x: **jetty-server-9.4.18.v20190429.jar** (Vulnerable Library)
+
+
-```
-Exception in thread ""main"" java.sql.SQLException: Unknown type '247' in column '1' of '2' in binary-encoded result set.
- at com.mysql.cj.jdbc.exceptions.SQLError.createSQLException(SQLError.java:545)
- at com.mysql.cj.jdbc.exceptions.SQLError.createSQLException(SQLError.java:513)
- at com.mysql.cj.jdbc.exceptions.SQLExceptionsMapping.translateException(SQLExceptionsMapping.java:115)
- at com.mysql.cj.jdbc.ServerPreparedStatement.serverExecute(ServerPreparedStatement.java:1299)
- at com.mysql.cj.jdbc.ServerPreparedStatement.executeInternal(ServerPreparedStatement.java:701)
- at com.mysql.cj.jdbc.PreparedStatement.executeQuery(PreparedStatement.java:1923)
- at com.apusic.test.CursorExample.main(CursorExample.java:27)
-```
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+### Vulnerability Details
+
+
+In Eclipse Jetty version 9.4.0.RC0 to 9.4.34.v20201102, 10.0.0.alpha0 to 10.0.0.beta2, and 11.0.0.alpha0 to 11.0.0.beta2, if GZIP request body inflation is enabled and requests from different clients are multiplexed onto a single connection, and if an attacker can send a request with a body that is received entirely but not consumed by the application, then a subsequent request on the same connection will see that body prepended to its body. The attacker will not see any data but may inject data into the body of the subsequent request.
-----------------------------------------------------------------------------------------------------------------+
-| Release Version: v2.1.0-alpha-75-g41f8ac195
-Git Commit Hash: 41f8ac19523386d0eb6ca871397f49f834958169
-Git Branch: master
-UTC Build Time: 2018-06-26 07:08:04
-GoVersion: go version go1.10.1 darwin/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e |
-+------------------------------------------------------------------------------------",True,"When the field list of the select statement contains the Enum type, the client will report an error - Please answer these questions before submitting your issue. Thanks!
+
+
-1. What did you do?
+
-When I use Server Prepared Statements, that is set `useServerPrepStmts=true`, if the select statement's field list contains the `Enum` type, the client will report an error.
+### CVSS 3 Score Details (4.8)
+
+For more information on CVSS3 Scores, click here.
+
-2. What did you expect to see?
+
-I expect the TiDB to return the correct query result.
+### Suggested Fix
+
-The client reported the following error message:
+
-```
-Exception in thread ""main"" java.sql.SQLException: Unknown type '247' in column '1' of '2' in binary-encoded result set.
- at com.mysql.cj.jdbc.exceptions.SQLError.createSQLException(SQLError.java:545)
- at com.mysql.cj.jdbc.exceptions.SQLError.createSQLException(SQLError.java:513)
- at com.mysql.cj.jdbc.exceptions.SQLExceptionsMapping.translateException(SQLExceptionsMapping.java:115)
- at com.mysql.cj.jdbc.ServerPreparedStatement.serverExecute(ServerPreparedStatement.java:1299)
- at com.mysql.cj.jdbc.ServerPreparedStatement.executeInternal(ServerPreparedStatement.java:701)
- at com.mysql.cj.jdbc.PreparedStatement.executeQuery(PreparedStatement.java:1923)
- at com.apusic.test.CursorExample.main(CursorExample.java:27)
-```
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-----------------------------------------------------------------------------------------------------------------+
-| Release Version: v2.1.0-alpha-75-g41f8ac195
-Git Commit Hash: 41f8ac19523386d0eb6ca871397f49f834958169
-Git Branch: master
-UTC Build Time: 2018-06-26 07:08:04
-GoVersion: go version go1.10.1 darwin/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e |
-+------------------------------------------------------------------------------------",1,when the field list of the select statement contains the enum type the client will report an error please answer these questions before submitting your issue thanks what did you do when i use server prepared statements that is set useserverprepstmts true if the select statement s field list contains the enum type the client will report an error create table shirts name varchar size enum small medium large insert into shirts name size values dress shirt large t shirt medium polo shirt small mysql desc shirts field type null key default extra name varchar yes null size enum small medium large yes null java code snippet: string db url jdbc mysql xxx xxx xxxx xxx test properties info new properties info setproperty user root info setproperty password info setproperty useserverprepstmts true connection conn drivermanager getconnection db url info string sql select name size from shirts where name preparedstatement preparedstatement conn preparestatement sql preparedstatement setstring t shirt resultset resultset preparedstatement executequery while resultset next string name resultset getstring name string size resultset getstring size system out println name size mysql connector j version: mysql mysql connector java what did you expect to see i expect the tidb to return the correct query result what did you see instead the client reported the following error message exception in thread main java sql sqlexception unknown type in column of in binary encoded result set at com mysql cj jdbc exceptions sqlerror createsqlexception sqlerror java at com mysql cj jdbc exceptions sqlerror createsqlexception sqlerror java at com mysql cj jdbc exceptions sqlexceptionsmapping translateexception sqlexceptionsmapping java at com mysql cj jdbc serverpreparedstatement serverexecute serverpreparedstatement java at com mysql cj jdbc serverpreparedstatement executeinternal serverpreparedstatement java at com mysql cj jdbc preparedstatement executequery preparedstatement java at com apusic test cursorexample main cursorexample java what version of tidb are you using tidb server v or run select tidb version on tidb release version alpha git commit hash git branch master utc build time goversion go version darwin race enabled false tikv min version alpha ,1
-110995,13996339299.0,IssuesEvent,2020-10-28 05:39:51,ajency/Dhanda-App,https://api.github.com/repos/ajency/Dhanda-App,closed,"No categories for DAILY,WORK BASIS,WEEKLY,WORKBASIS",Assigned to QA Design Issue bug,"There are no categories for DAILY,WORK BASIS,WEEKLY,WORKBASIS
+:rescue_worker_helmet: Automatic Remediation is available for this issue
+
-Description-As the staff must be segregated into such category like in case of monthly and hourly staff but the Daily ,weekly and work basis dont have category and are put under one category of monthly
-
-",1.0,"No categories for DAILY,WORK BASIS,WEEKLY,WORKBASIS - There are no categories for DAILY,WORK BASIS,WEEKLY,WORKBASIS
+ CVE-2021-34428
-Description-As the staff must be segregated into such category like in case of monthly and hourly staff but the Daily ,weekly and work basis dont have category and are put under one category of monthly
-
-",0,no categories for daily work basis weekly workbasis there are no categories for daily work basis weekly workbasis description as the staff must be segregated into such category like in case of monthly and hourly staff but the daily weekly and work basis dont have category and are put under one category of monthly ,0
-3210,9213817246.0,IssuesEvent,2019-03-10 15:09:07,jimkyndemeyer/js-graphql-intellij-plugin,https://api.github.com/repos/jimkyndemeyer/js-graphql-intellij-plugin,closed,Support for multiple schemas (on multiple endpoints),enhancement v2-alpha v2-architecture,"I need to access two different graphql endpoints from a project, where each endpoint has a different schema.
-I'm currently keeping two different copies of graphql.config.json that I swap between as needed.
+### Vulnerable Library - jetty-server-9.4.18.v20190429.jar
-Is there a better way to handle this? If not, consider this an enhancement request.",1.0,"Support for multiple schemas (on multiple endpoints) - I need to access two different graphql endpoints from a project, where each endpoint has a different schema.
+
Path to vulnerable library: /home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/sitory/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar
+
-I'm currently keeping two different copies of graphql.config.json that I swap between as needed.
+Dependency Hierarchy:
+ - :x: **jetty-server-9.4.18.v20190429.jar** (Vulnerable Library)
+
+
-Is there a better way to handle this? If not, consider this an enhancement request.",0,support for multiple schemas on multiple endpoints i need to access two different graphql endpoints from a project where each endpoint has a different schema i m currently keeping two different copies of graphql config json that i swap between as needed is there a better way to handle this if not consider this an enhancement request ,0
-411812,12032337110.0,IssuesEvent,2020-04-13 11:53:54,mir-dataset-loaders/mirdata,https://api.github.com/repos/mir-dataset-loaders/mirdata,closed,"`module.load_*` should raise `IOError`, not return `None`",priority question,"raised by @rabitt in a meeting today
+
-Many of the module-specific loaders, e.g. `orchset.load_melody`, return `None` if the argument does not exist. This can be confusing in the sense that it may suggest that the file exists but that there is no annotation for this file, or that the annotation is not applicable (non-melodic music, following my example above).
+### Vulnerability Details
+
+
+For Eclipse Jetty versions <= 9.4.40, <= 10.0.2, <= 11.0.2, if an exception is thrown from the SessionListener#sessionDestroyed() method, then the session ID is not invalidated in the session ID manager. On deployments with clustered sessions and multiple contexts this can result in a session not being invalidated. This can result in an application used on a shared computer being left logged in.
-She now recommends raising an `IOError`.
+
+
-This is a breaking change so i wouldn't recommend it for v0.2
-But we can deprecate it in v0.2 and change the behavior in v0.3
+
-@rabitt what should we do for people providing new loaders? Should we tell them to work with the old or the new convention?
-This affects `new_loader.md` (excerpt below):
+### CVSS 3 Score Details (3.5)
+
-```
-# -- Write any necessary loader functions for loading the dataset's data
-def load_annotation(annotation_path):
- if not os.path.exists(annotation_path):
- return None
-```",1.0,"`module.load_*` should raise `IOError`, not return `None` - raised by @rabitt in a meeting today
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Physical
+ - Attack Complexity: Low
+ - Privileges Required: None
+ - User Interaction: None
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: Low
+ - Integrity Impact: Low
+ - Availability Impact: None
+
+For more information on CVSS3 Scores, click here.
+
-Many of the module-specific loaders, e.g. `orchset.load_melody`, return `None` if the argument does not exist. This can be confusing in the sense that it may suggest that the file exists but that there is no annotation for this file, or that the annotation is not applicable (non-melodic music, following my example above).
+
-She now recommends raising an `IOError`.
+### Suggested Fix
+
-This is a breaking change so i wouldn't recommend it for v0.2
-But we can deprecate it in v0.2 and change the behavior in v0.3
+
-@rabitt what should we do for people providing new loaders? Should we tell them to work with the old or the new convention?
-This affects `new_loader.md` (excerpt below):
+
-```
-# -- Write any necessary loader functions for loading the dataset's data
-def load_annotation(annotation_path):
- if not os.path.exists(annotation_path):
- return None
-```",0, module load should raise ioerror not return none raised by rabitt in a meeting today many of the module specific loaders e g orchset load melody return none if the argument does not exist this can be confusing in the sense that it may suggest that the file exists but that there is no annotation for this file or that the annotation is not applicable non melodic music following my example above she now recommends raising an ioerror this is a breaking change so i wouldn t recommend it for but we can deprecate it in and change the behavior in rabitt what should we do for people providing new loaders should we tell them to work with the old or the new convention this affects new loader md excerpt below write any necessary loader functions for loading the dataset s data def load annotation annotation path if not os path exists annotation path return none ,0
-5570,8049273217.0,IssuesEvent,2018-08-01 09:35:12,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Check how MySQL sort privilege cache items exactly,help wanted type/compatibility,"https://github.com/pingcap/tidb/pull/7211 try to sort the user records according to the document https://dev.mysql.com/doc/refman/5.5/en/connection-access.html
+
-The document missing many details, so maybe we should check the MySQL source code to see how to do it.",True,"Check how MySQL sort privilege cache items exactly - https://github.com/pingcap/tidb/pull/7211 try to sort the user records according to the document https://dev.mysql.com/doc/refman/5.5/en/connection-access.html
-The document missing many details, so maybe we should check the MySQL source code to see how to do it.",1,check how mysql sort privilege cache items exactly try to sort the user records according to the document the document missing many details so maybe we should check the mysql source code to see how to do it ,1
-192560,14620553142.0,IssuesEvent,2020-12-22 19:56:36,github-vet/rangeloop-pointer-findings,https://api.github.com/repos/github-vet/rangeloop-pointer-findings,closed,pbolla0818/oci_terraform: oci/budget_budget_test.go; 14 LoC,fresh small test,"
-Found a possible issue in [pbolla0818/oci_terraform](https://www.github.com/pbolla0818/oci_terraform) at [oci/budget_budget_test.go](https://github.com/pbolla0818/oci_terraform/blob/c233d54c5fe32f12c234d6dceefba0a9b4ab3022/oci/budget_budget_test.go#L477-L490)
+:rescue_worker_helmet: Automatic Remediation is available for this issue
+
-Below is the message reported by the analyzer for this snippet of code. Beware that the analyzer only reports the first
-issue it finds, so please do not limit your consideration to the contents of the below message.
+ CVE-2022-2047
-> reference to budgetId is reassigned at line 481
-[Click here to see the code in its original context.](https://github.com/pbolla0818/oci_terraform/blob/c233d54c5fe32f12c234d6dceefba0a9b4ab3022/oci/budget_budget_test.go#L477-L490)
+### Vulnerable Library - jetty-server-9.4.18.v20190429.jar
-
-Click here to show the 14 line(s) of Go which triggered the analyzer.
+
Path to vulnerable library: /home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/sitory/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar
+
-```go
- for _, budgetId := range budgetIds {
- if ok := SweeperDefaultResourceId[budgetId]; !ok {
- deleteBudgetRequest := oci_budget.DeleteBudgetRequest{}
+Dependency Hierarchy:
+ - :x: **jetty-server-9.4.18.v20190429.jar** (Vulnerable Library)
+
+
- deleteBudgetRequest.BudgetId = &budgetId
+
- deleteBudgetRequest.RequestMetadata.RetryPolicy = getRetryPolicy(true, ""budget"")
- _, error := budgetClient.DeleteBudget(context.Background(), deleteBudgetRequest)
- if error != nil {
- fmt.Printf(""Error deleting Budget %s %s, It is possible that the resource is already deleted. Please verify manually \n"", budgetId, error)
- continue
- }
- }
- }
+### Vulnerability Details
+
+
+In Eclipse Jetty versions 9.4.0 thru 9.4.46, and 10.0.0 thru 10.0.9, and 11.0.0 thru 11.0.9 versions, the parsing of the authority segment of an http scheme URI, the Jetty HttpURI class improperly detects an invalid input as a hostname. This can lead to failures in a Proxy scenario.
-```
-
+
-Leave a reaction on this issue to contribute to the project by classifying this instance as a **Bug** :-1:, **Mitigated** :+1:, or **Desirable Behavior** :rocket:
-See the descriptions of the classifications [here](https://github.com/github-vet/rangeclosure-findings#how-can-i-help) for more information.
+
-commit ID: c233d54c5fe32f12c234d6dceefba0a9b4ab3022
-",1.0,"pbolla0818/oci_terraform: oci/budget_budget_test.go; 14 LoC -
-Found a possible issue in [pbolla0818/oci_terraform](https://www.github.com/pbolla0818/oci_terraform) at [oci/budget_budget_test.go](https://github.com/pbolla0818/oci_terraform/blob/c233d54c5fe32f12c234d6dceefba0a9b4ab3022/oci/budget_budget_test.go#L477-L490)
+### CVSS 3 Score Details (2.7)
+
-Below is the message reported by the analyzer for this snippet of code. Beware that the analyzer only reports the first
-issue it finds, so please do not limit your consideration to the contents of the below message.
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Network
+ - Attack Complexity: Low
+ - Privileges Required: High
+ - User Interaction: None
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: None
+ - Integrity Impact: Low
+ - Availability Impact: None
+
+For more information on CVSS3 Scores, click here.
+
-> reference to budgetId is reassigned at line 481
+
-[Click here to see the code in its original context.](https://github.com/pbolla0818/oci_terraform/blob/c233d54c5fe32f12c234d6dceefba0a9b4ab3022/oci/budget_budget_test.go#L477-L490)
+### Suggested Fix
+
-
-Click here to show the 14 line(s) of Go which triggered the analyzer.
+
-```go
- for _, budgetId := range budgetIds {
- if ok := SweeperDefaultResourceId[budgetId]; !ok {
- deleteBudgetRequest := oci_budget.DeleteBudgetRequest{}
+
- deleteBudgetRequest.BudgetId = &budgetId
+
- deleteBudgetRequest.RequestMetadata.RetryPolicy = getRetryPolicy(true, ""budget"")
- _, error := budgetClient.DeleteBudget(context.Background(), deleteBudgetRequest)
- if error != nil {
- fmt.Printf(""Error deleting Budget %s %s, It is possible that the resource is already deleted. Please verify manually \n"", budgetId, error)
- continue
- }
- }
- }
-```
+:rescue_worker_helmet: Automatic Remediation is available for this issue
-Leave a reaction on this issue to contribute to the project by classifying this instance as a **Bug** :-1:, **Mitigated** :+1:, or **Desirable Behavior** :rocket:
-See the descriptions of the classifications [here](https://github.com/github-vet/rangeclosure-findings#how-can-i-help) for more information.
+***
-commit ID: c233d54c5fe32f12c234d6dceefba0a9b4ab3022
-",0, oci terraform oci budget budget test go loc found a possible issue in at below is the message reported by the analyzer for this snippet of code beware that the analyzer only reports the first issue it finds so please do not limit your consideration to the contents of the below message reference to budgetid is reassigned at line click here to show the line s of go which triggered the analyzer go for budgetid range budgetids if ok sweeperdefaultresourceid ok deletebudgetrequest oci budget deletebudgetrequest deletebudgetrequest budgetid budgetid deletebudgetrequest requestmetadata retrypolicy getretrypolicy true budget error budgetclient deletebudget context background deletebudgetrequest if error nil fmt printf error deleting budget s s it is possible that the resource is already deleted please verify manually n budgetid error continue leave a reaction on this issue to contribute to the project by classifying this instance as a bug mitigated or desirable behavior rocket see the descriptions of the classifications for more information commit id ,0
-144718,11627883384.0,IssuesEvent,2020-02-27 17:16:30,dhowe/spectre,https://api.github.com/repos/dhowe/spectre,closed,Insight: sliders don’t activate the next button on touch screen,CRITICAL needs-verification test-on-touchscreen,"This works correctly in touch-screen simulation (see below). @billposters Are you saying that when you drag the slider, the 'next' button does not become active (and turn blue)?
+
:rescue_worker_helmet: Automatic Remediation is available for this issue.
Path to vulnerable library: /home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/sitory/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar
+
-
-",1.0,"Insight: sliders don’t activate the next button on touch screen - This works correctly in touch-screen simulation (see below). @billposters Are you saying that when you drag the slider, the 'next' button does not become active (and turn blue)?
+
-
-",0,insight sliders don’t activate the next button on touch screen this works correctly in touch screen simulation see below billposters are you saying that when you drag the slider the next button does not become active and turn blue ,0
-16544,22497246529.0,IssuesEvent,2022-06-23 08:40:39,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Bad error message for numeric conversion,type/compatibility severity/moderate component/executor compatibility-mysql8,"## Bug Report
+## Vulnerabilities
-Please answer these questions before submitting your issue. Thanks!
+| CVE | Severity | CVSS | Dependency | Type | Fixed in | Remediation Available |
+| ------------- | ------------- | ----- | ----- | ----- | --- | --- |
+| [CVE-2021-28165](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-28165) | High | 7.5 | jetty-io-9.4.18.v20190429.jar | Transitive | 9.4.39.v20210325 | ✅ |
+| [CVE-2021-28169](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-28169) | Medium | 5.3 | jetty-server-9.4.18.v20190429.jar | Direct | 9.4.41.v20210516 | ✅ |
+| [CVE-2020-27218](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-27218) | Medium | 4.8 | jetty-server-9.4.18.v20190429.jar | Direct | 9.4.35.v20201120 | ✅ |
+| [CVE-2021-34428](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-34428) | Low | 3.5 | jetty-server-9.4.18.v20190429.jar | Direct | 9.4.41.v20210516 | ✅ |
+| [CVE-2022-2047](https://vuln.whitesourcesoftware.com/vulnerability/CVE-2022-2047) | Low | 2.7 | jetty-server-9.4.18.v20190429.jar | Direct | 9.4.47.v20220610 | ✅ |
-### 1. Minimal reproduce step (Required)
-```sql
-DROP TABLE IF EXISTS t0;
-CREATE TABLE t0 (c0 DECIMAL);
-INSERT INTO t0 VALUES (1);
-SELECT * FROM t0 WHERE t0.c0 > 'a';
-SHOW WARNINGS;
-```
-
-
-### 2. What did you expect to see? (Required)
-A specific type of error for external applications like MySQL.
-```sql
-+---------+------+----------------------------------------+
-| Level | Code | Message |
-+---------+------+----------------------------------------+
-| Warning | 1292 | Truncated incorrect DECIMAL value: 'a' |
-+---------+------+----------------------------------------+
-1 row in set (0.00 sec)
-```
-### 3. What did you see instead (Required)
-```sql
-+---------+------+------------+
-| Level | Code | Message |
-+---------+------+------------+
-| Warning | 8029 | Bad Number |
-+---------+------+------------+
-1 row in set (0.00 sec)
-```
-### 4. What is your TiDB version? (Required)
-```sql
-+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version()
-
- |
-+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v5.4.0
-Edition: Community
-Git Commit Hash: 55f3b24c1c9f506bd652ef1d162283541e428872
-Git Branch: heads/refs/tags/v5.4.0
-UTC Build Time: 2022-01-25 08:39:26
-GoVersion: go1.16.4
-Race Enabled: false
-TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
-Check Table Before Drop: false |
-+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-1 row in set (0.00 sec)
-```
-
-",True,"Bad error message for numeric conversion - ## Bug Report
+## Details
-Please answer these questions before submitting your issue. Thanks!
+
-### 1. Minimal reproduce step (Required)
-```sql
-DROP TABLE IF EXISTS t0;
-CREATE TABLE t0 (c0 DECIMAL);
-INSERT INTO t0 VALUES (1);
-SELECT * FROM t0 WHERE t0.c0 > 'a';
-SHOW WARNINGS;
-```
-
-
-### 2. What did you expect to see? (Required)
-A specific type of error for external applications like MySQL.
-```sql
-+---------+------+----------------------------------------+
-| Level | Code | Message |
-+---------+------+----------------------------------------+
-| Warning | 1292 | Truncated incorrect DECIMAL value: 'a' |
-+---------+------+----------------------------------------+
-1 row in set (0.00 sec)
-```
-### 3. What did you see instead (Required)
-```sql
-+---------+------+------------+
-| Level | Code | Message |
-+---------+------+------------+
-| Warning | 8029 | Bad Number |
-+---------+------+------------+
-1 row in set (0.00 sec)
-```
-### 4. What is your TiDB version? (Required)
-```sql
-+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version()
-
- |
-+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v5.4.0
-Edition: Community
-Git Commit Hash: 55f3b24c1c9f506bd652ef1d162283541e428872
-Git Branch: heads/refs/tags/v5.4.0
-UTC Build Time: 2022-01-25 08:39:26
-GoVersion: go1.16.4
-Race Enabled: false
-TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
-Check Table Before Drop: false |
-+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-1 row in set (0.00 sec)
-```
-
+ CVE-2021-28165
-",1,bad error message for numeric conversion bug report please answer these questions before submitting your issue thanks minimal reproduce step required sql drop table if exists create table decimal insert into values select from where a show warnings what did you expect to see required a specific type of error for external applications like mysql sql level code message warning truncated incorrect decimal value a row in set sec what did you see instead required sql level code message warning bad number row in set sec what is your tidb version required sql tidb version release version edition community git commit hash git branch heads refs tags utc build time goversion race enabled false tikv min version check table before drop false row in set sec ,1
-15229,19325304162.0,IssuesEvent,2021-12-14 10:38:36,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,JSON_EXTRACT function does not get the expected result,type/bug type/compatibility severity/moderate component/executor,"## Bug Report
-Please answer these questions before submitting your issue. Thanks!
+### Vulnerable Library - jetty-io-9.4.18.v20190429.jar
-### 1. Minimal reproduce step (Required)
+
Path to dependency file: /BaragonAgentService/pom.xml
+
Path to vulnerable library: /home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-io/9.4.18.v20190429/jetty-io-9.4.18.v20190429.jar,/home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-io/9.4.18.v20190429/jetty-io-9.4.18.v20190429.jar,/home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-io/9.4.18.v20190429/jetty-io-9.4.18.v20190429.jar
+
-### 2. What did you expect to see? (Required)
+
-""TiDB""
+### Vulnerability Details
+
+
+In Eclipse Jetty 7.2.2 to 9.4.38, 10.0.0.alpha0 to 10.0.1, and 11.0.0.alpha0 to 11.0.1, CPU usage can reach 100% upon receiving a large invalid TLS frame.
-### 3. What did you see instead (Required)
+
+
-{""$type"": ""TiDB""}
+
-### 4. What is your TiDB version? (Required)
+### CVSS 3 Score Details (7.5)
+
-5.7.25-TiDB-v5.1.0",True,"JSON_EXTRACT function does not get the expected result - ## Bug Report
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Network
+ - Attack Complexity: Low
+ - Privileges Required: None
+ - User Interaction: None
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: None
+ - Integrity Impact: None
+ - Availability Impact: High
+
+For more information on CVSS3 Scores, click here.
+
-Please answer these questions before submitting your issue. Thanks!
-
-### 1. Minimal reproduce step (Required)
-
-```sql
-SELECT JSON_EXTRACT('{""properties"": {""$type"": ""TiDB""}}','$.properties.$type')
-```
-
-### 2. What did you expect to see? (Required)
-
-""TiDB""
+
-### 3. What did you see instead (Required)
+### Suggested Fix
+
Direct dependency fix Resolution (org.eclipse.jetty:jetty-server): 9.4.39.v20210325
-### 4. What is your TiDB version? (Required)
+
-5.7.25-TiDB-v5.1.0",1,json extract function does not get the expected result bug report please answer these questions before submitting your issue thanks minimal reproduce step required sql select json extract properties type tidb properties type what did you expect to see required tidb what did you see instead required type tidb what is your tidb version required tidb ,1
-7434,9674066855.0,IssuesEvent,2019-05-22 09:03:30,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,`LOAD DATA LOCAL INFILE` with IGNORE will report an error,for new contributors help wanted type/compatibility,"## Bug Report
+
-Please answer these questions before submitting your issue. Thanks!
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+:rescue_worker_helmet: Automatic Remediation is available for this issue
+
-run `load data` with `ignore` will occur an error
+ CVE-2021-28169
-`
-mysql -h {host} -P {port} -u root --local-infile=1 -p{password} -D SCALIFIED -e LOAD DATA LOCAL INFILE 'SCALIFIED.T_STU' IGNORE INTO TABLE SCALIFIED.T_STU FIELDS TERMINATED BY '\t' LINES TERMINATED BY '\n';
-`
-the command run against mysql successfully.
+### Vulnerable Library - jetty-server-9.4.18.v20190429.jar
+
Path to vulnerable library: /home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/sitory/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar
+
-2. What did you expect to see?
+
-load data into tidb successfully.
+### Vulnerability Details
+
+
+For Eclipse Jetty versions <= 9.4.40, <= 10.0.2, <= 11.0.2, it is possible for requests to the ConcatServlet with a doubly encoded path to access protected resources within the WEB-INF directory. For example a request to `/concat?/%2557EB-INF/web.xml` can retrieve the web.xml file. This can reveal sensitive information regarding the implementation of a web application.
-3. What did you see instead?
+
+
-error occurs.
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+### CVSS 3 Score Details (5.3)
+
+For more information on CVSS3 Scores, click here.
+
-Please answer these questions before submitting your issue. Thanks!
+
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+### Suggested Fix
+
-run `load data` with `ignore` will occur an error
+
-`
-mysql -h {host} -P {port} -u root --local-infile=1 -p{password} -D SCALIFIED -e LOAD DATA LOCAL INFILE 'SCALIFIED.T_STU' IGNORE INTO TABLE SCALIFIED.T_STU FIELDS TERMINATED BY '\t' LINES TERMINATED BY '\n';
-`
+
-the command run against mysql successfully.
+
+:rescue_worker_helmet: Automatic Remediation is available for this issue
+
-2. What did you expect to see?
+ CVE-2020-27218
-load data into tidb successfully.
-3. What did you see instead?
+### Vulnerable Library - jetty-server-9.4.18.v20190429.jar
-error occurs.
+
Path to vulnerable library: /home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/sitory/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+Dependency Hierarchy:
+ - :x: **jetty-server-9.4.18.v20190429.jar** (Vulnerable Library)
+
+
-v2.1.4",1, load data local infile with ignore will report an error bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error run load data with ignore will occur an error mysql h host p port u root local infile p password d scalified e load data local infile scalified t stu ignore into table scalified t stu fields terminated by t lines terminated by n the command run against mysql successfully what did you expect to see load data into tidb successfully what did you see instead error occurs what version of tidb are you using tidb server v or run select tidb version on tidb ,1
-143373,11551049555.0,IssuesEvent,2020-02-19 00:12:44,Team1559/2020-InfiniteRecharge,https://api.github.com/repos/Team1559/2020-InfiniteRecharge,closed,Chassis tuning at full robot weight,Test Tuning,Re-tune velocity mode once the robot is assembled. Adjust PIDF coefficients as well as ramp rates and current limits.,1.0,Chassis tuning at full robot weight - Re-tune velocity mode once the robot is assembled. Adjust PIDF coefficients as well as ramp rates and current limits.,0,chassis tuning at full robot weight re tune velocity mode once the robot is assembled adjust pidf coefficients as well as ramp rates and current limits ,0
-3419,6392908898.0,IssuesEvent,2017-08-04 05:09:30,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Function `encrypt` not supported,compatibility rc3.1,"Please answer these questions before submitting your issue. Thanks!
+
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+### Vulnerability Details
+
+
+In Eclipse Jetty version 9.4.0.RC0 to 9.4.34.v20201102, 10.0.0.alpha0 to 10.0.0.beta2, and 11.0.0.alpha0 to 11.0.0.beta2, if GZIP request body inflation is enabled and requests from different clients are multiplexed onto a single connection, and if an attacker can send a request with a body that is received entirely but not consumed by the application, then a subsequent request on the same connection will see that body prepended to its body. The attacker will not see any data but may inject data into the body of the subsequent request.
-```sql
-select length(encrypt('foo', 'ff')) <> 0;
-```
+
+
-2. What did you expect to see?
+
-```
-length(encrypt('foo', 'ff')) <> 0
-1
-```
+### CVSS 3 Score Details (4.8)
+
-3. What did you see instead?
+Base Score Metrics:
+- Exploitability Metrics:
+ - Attack Vector: Network
+ - Attack Complexity: High
+ - Privileges Required: None
+ - User Interaction: None
+ - Scope: Unchanged
+- Impact Metrics:
+ - Confidentiality Impact: None
+ - Integrity Impact: Low
+ - Availability Impact: Low
+
+For more information on CVSS3 Scores, click here.
+
-```
-ERROR 1305 (42000) at line 1: FUNCTION ENCRYPT does not exist
-```
+
-4. What version of TiDB are you using (`tidb-server -V`)?
+### Suggested Fix
+
-",True,"Function `encrypt` not supported - Please answer these questions before submitting your issue. Thanks!
+
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+
-```sql
-select length(encrypt('foo', 'ff')) <> 0;
-```
+
-2. What did you expect to see?
-```
-length(encrypt('foo', 'ff')) <> 0
-1
-```
+:rescue_worker_helmet: Automatic Remediation is available for this issue
+
-3. What did you see instead?
+ CVE-2021-34428
-```
-ERROR 1305 (42000) at line 1: FUNCTION ENCRYPT does not exist
-```
-4. What version of TiDB are you using (`tidb-server -V`)?
+### Vulnerable Library - jetty-server-9.4.18.v20190429.jar
-",1,function encrypt not supported please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql select length encrypt foo ff what did you expect to see length encrypt foo ff what did you see instead error at line function encrypt does not exist what version of tidb are you using tidb server v ,1
-7609,9859060291.0,IssuesEvent,2019-06-20 08:44:51,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Window function panicked when range bound is time type,component/executor type/bug type/compatibility,"## Bug Report
+
Path to vulnerable library: /home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/sitory/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar
+
-Please answer these questions before submitting your issue. Thanks!
+Dependency Hierarchy:
+ - :x: **jetty-server-9.4.18.v20190429.jar** (Vulnerable Library)
+
+
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-```
-CREATE TABLE `t_time` (
- `t` time DEFAULT NULL,
- `ts` timestamp NULL DEFAULT NULL
-)
-INSERT INTO t_time VALUES ('12:30', '2016-07-05 08:30:42');
-SELECT t, FIRST_VALUE(t) OVER (ORDER BY t RANGE BETWEEN INTERVAL 2 HOUR PRECEDING AND INTERVAL 2 HOUR_MINUTE PRECEDING) FROM t_time;
-```
+
-2. What did you expect to see?
+### Vulnerability Details
+
+
+For Eclipse Jetty versions <= 9.4.40, <= 10.0.2, <= 11.0.2, if an exception is thrown from the SessionListener#sessionDestroyed() method, then the session ID is not invalidated in the session ID manager. On deployments with clustered sessions and multiple contexts this can result in a session not being invalidated. This can result in an application used on a shared computer being left logged in.
-Execute successfully.
+
+For more information on CVSS3 Scores, click here.
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
-",True,"Window function panicked when range bound is time type - ## Bug Report
+### Suggested Fix
+
-Please answer these questions before submitting your issue. Thanks!
+
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-```
-CREATE TABLE `t_time` (
- `t` time DEFAULT NULL,
- `ts` timestamp NULL DEFAULT NULL
-)
-INSERT INTO t_time VALUES ('12:30', '2016-07-05 08:30:42');
-SELECT t, FIRST_VALUE(t) OVER (ORDER BY t RANGE BETWEEN INTERVAL 2 HOUR PRECEDING AND INTERVAL 2 HOUR_MINUTE PRECEDING) FROM t_time;
-```
+
-2. What did you expect to see?
+
-Execute successfully.
-3. What did you see instead?
+:rescue_worker_helmet: Automatic Remediation is available for this issue
+
-Panicked.
+ CVE-2022-2047
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+### Vulnerable Library - jetty-server-9.4.18.v20190429.jar
-",1,window function panicked when range bound is time type bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error create table t time t time default null ts timestamp null default null insert into t time values select t first value t over order by t range between interval hour preceding and interval hour minute preceding from t time what did you expect to see execute successfully what did you see instead panicked what version of tidb are you using tidb server v or run select tidb version on tidb ,1
-19384,26903946824.0,IssuesEvent,2023-02-06 17:32:02,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Column defaults in ComFieldList response violate protocol,type/bug type/compatibility component/mysql-protocol severity/minor compatibility-mysql8,"## Bug Report
+
Path to vulnerable library: /home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/sitory/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar,/home/wss-scanner/.m2/repository/org/eclipse/jetty/jetty-server/9.4.18.v20190429/jetty-server-9.4.18.v20190429.jar
+
-The `mysql.ComFieldList` returns default values for columns. However this isn't fully implemented in TiDB, so it won't send the actual defaults and it also seems to violate the protocol.
+Dependency Hierarchy:
+ - :x: **jetty-server-9.4.18.v20190429.jar** (Vulnerable Library)
+
+
-### 1. Minimal reproduce step (Required)
+
-Send a field list query, e.g. by connecting without database and running `use test` in the MySQL Client.
-Dump and inspect traffic with Wireshark
+### Vulnerability Details
+
+
+In Eclipse Jetty versions 9.4.0 thru 9.4.46, and 10.0.0 thru 10.0.9, and 11.0.0 thru 11.0.9 versions, the parsing of the authority segment of an http scheme URI, the Jetty HttpURI class improperly detects an invalid input as a hostname. This can lead to failures in a Proxy scenario.
-### 2. What did you expect to see? (Required)
+
+For more information on CVSS3 Scores, click here.
+
-### 4. What is your TiDB version? (Required)
+
-```
-$ ./bin/tidb-server -V
-Release Version: v6.6.0-alpha-274-g1e0956d5b
-Edition: Community
-Git Commit Hash: 1e0956d5ba41182e603295e02ae8f767d62979e4
-Git Branch: master
-UTC Build Time: 2023-01-22 23:13:24
-GoVersion: go1.19.5
-Race Enabled: false
-TiKV Min Version: 6.2.0-alpha
-Check Table Before Drop: false
-Store: unistore
-```",True,"Column defaults in ComFieldList response violate protocol - ## Bug Report
+### Suggested Fix
+
-The `mysql.ComFieldList` returns default values for columns. However this isn't fully implemented in TiDB, so it won't send the actual defaults and it also seems to violate the protocol.
+
-### 1. Minimal reproduce step (Required)
+
-Send a field list query, e.g. by connecting without database and running `use test` in the MySQL Client.
-Dump and inspect traffic with Wireshark
+
-### 2. What did you expect to see? (Required)
-Proper column defaults
+:rescue_worker_helmet: Automatic Remediation is available for this issue
+
-### 3. What did you see instead (Required)
+***
-Too many zeros being written.
+
:rescue_worker_helmet: Automatic Remediation is available for this issue.
",0,jetty server jar vulnerabilities highest severity is vulnerable library jetty server jar the core jetty server artifact library home page a href path to dependency file baragondata pom xml path to vulnerable library home wss scanner repository org eclipse jetty jetty server jetty server jar sitory org eclipse jetty jetty server jetty server jar home wss scanner repository org eclipse jetty jetty server jetty server jar found in head commit a href vulnerabilities cve severity cvss dependency type fixed in remediation available high jetty io jar transitive medium jetty server jar direct medium jetty server jar direct low jetty server jar direct low jetty server jar direct details cve vulnerable library jetty io jar the eclipse jetty project library home page a href path to dependency file baragonagentservice pom xml path to vulnerable library home wss scanner repository org eclipse jetty jetty io jetty io jar home wss scanner repository org eclipse jetty jetty io jetty io jar home wss scanner repository org eclipse jetty jetty io jetty io jar dependency hierarchy jetty server jar root library x jetty io jar vulnerable library found in head commit a href found in base branch master vulnerability details in eclipse jetty to to and to cpu usage can reach upon receiving a large invalid tls frame publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution org eclipse jetty jetty io direct dependency fix resolution org eclipse jetty jetty server rescue worker helmet automatic remediation is available for this issue cve vulnerable library jetty server jar the core jetty server artifact library home page a href path to dependency file baragondata pom xml path to vulnerable library home wss scanner repository org eclipse jetty jetty server jetty server jar sitory org eclipse jetty jetty server jetty server jar home wss scanner repository org eclipse jetty jetty server jetty server jar dependency hierarchy x jetty server jar vulnerable library found in head commit a href found in base branch master vulnerability details for eclipse jetty versions it is possible for requests to the concatservlet with a doubly encoded path to access protected resources within the web inf directory for example a request to concat inf web xml can retrieve the web xml file this can reveal sensitive information regarding the implementation of a web application publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact low integrity impact none availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution rescue worker helmet automatic remediation is available for this issue cve vulnerable library jetty server jar the core jetty server artifact library home page a href path to dependency file baragondata pom xml path to vulnerable library home wss scanner repository org eclipse jetty jetty server jetty server jar sitory org eclipse jetty jetty server jetty server jar home wss scanner repository org eclipse jetty jetty server jetty server jar dependency hierarchy x jetty server jar vulnerable library found in head commit a href found in base branch master vulnerability details in eclipse jetty version to to and to if gzip request body inflation is enabled and requests from different clients are multiplexed onto a single connection and if an attacker can send a request with a body that is received entirely but not consumed by the application then a subsequent request on the same connection will see that body prepended to its body the attacker will not see any data but may inject data into the body of the subsequent request publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact low availability impact low for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution rescue worker helmet automatic remediation is available for this issue cve vulnerable library jetty server jar the core jetty server artifact library home page a href path to dependency file baragondata pom xml path to vulnerable library home wss scanner repository org eclipse jetty jetty server jetty server jar sitory org eclipse jetty jetty server jetty server jar home wss scanner repository org eclipse jetty jetty server jetty server jar dependency hierarchy x jetty server jar vulnerable library found in head commit a href found in base branch master vulnerability details for eclipse jetty versions if an exception is thrown from the sessionlistener sessiondestroyed method then the session id is not invalidated in the session id manager on deployments with clustered sessions and multiple contexts this can result in a session not being invalidated this can result in an application used on a shared computer being left logged in publish date url a href cvss score details base score metrics exploitability metrics attack vector physical attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution rescue worker helmet automatic remediation is available for this issue cve vulnerable library jetty server jar the core jetty server artifact library home page a href path to dependency file baragondata pom xml path to vulnerable library home wss scanner repository org eclipse jetty jetty server jetty server jar sitory org eclipse jetty jetty server jetty server jar home wss scanner repository org eclipse jetty jetty server jetty server jar dependency hierarchy x jetty server jar vulnerable library found in head commit a href found in base branch master vulnerability details in eclipse jetty versions thru and thru and thru versions the parsing of the authority segment of an http scheme uri the jetty httpuri class improperly detects an invalid input as a hostname this can lead to failures in a proxy scenario publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required high user interaction none scope unchanged impact metrics confidentiality impact none integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution rescue worker helmet automatic remediation is available for this issue rescue worker helmet automatic remediation is available for this issue ,0
+7334,9577312403.0,IssuesEvent,2019-05-07 11:21:08,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,`unix_timestamp` is not compatible with Mysql,for new contributors help wanted type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+select @a:=FROM_UNIXTIME(1);
+select unix_timestamp(@a);
+```
+
+2. What did you expect to see?
+In Mysql
+```
+mysql> select @a:=FROM_UNIXTIME(1);
++----------------------+
+| @a:=FROM_UNIXTIME(1) |
++----------------------+
+| 1970-01-01 08:00:01 |
++----------------------+
+1 row in set (0.00 sec)
+
+mysql> select unix_timestamp(@a);
++--------------------+
+| unix_timestamp(@a) |
++--------------------+
+| 1 |
++--------------------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+In TiDB
+```
+mysql> select @a:=FROM_UNIXTIME(1);
++----------------------+
+| @a:=FROM_UNIXTIME(1) |
++----------------------+
+| 1970-01-01 08:00:01 |
++----------------------+
+1 row in set (0.00 sec)
+
+mysql> select unix_timestamp(@a);
++--------------------+
+| unix_timestamp(@a) |
++--------------------+
+| 1.000000 |
++--------------------+
+1 row in set (0.01 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-212-g0681b8125
+Git Commit Hash: 0681b8125080045ee0d4747ce61923164c6f2dd1
+Git Branch: master
+UTC Build Time: 2019-03-14 04:39:19
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+```
+
+",True,"`unix_timestamp` is not compatible with Mysql - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+select @a:=FROM_UNIXTIME(1);
+select unix_timestamp(@a);
+```
+
+2. What did you expect to see?
+In Mysql
+```
+mysql> select @a:=FROM_UNIXTIME(1);
++----------------------+
+| @a:=FROM_UNIXTIME(1) |
++----------------------+
+| 1970-01-01 08:00:01 |
++----------------------+
+1 row in set (0.00 sec)
+
+mysql> select unix_timestamp(@a);
++--------------------+
+| unix_timestamp(@a) |
++--------------------+
+| 1 |
++--------------------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+In TiDB
+```
+mysql> select @a:=FROM_UNIXTIME(1);
++----------------------+
+| @a:=FROM_UNIXTIME(1) |
++----------------------+
+| 1970-01-01 08:00:01 |
++----------------------+
+1 row in set (0.00 sec)
+
+mysql> select unix_timestamp(@a);
++--------------------+
+| unix_timestamp(@a) |
++--------------------+
+| 1.000000 |
++--------------------+
+1 row in set (0.01 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v3.0.0-beta-212-g0681b8125
+Git Commit Hash: 0681b8125080045ee0d4747ce61923164c6f2dd1
+Git Branch: master
+UTC Build Time: 2019-03-14 04:39:19
+GoVersion: go version go1.12 darwin/amd64
+Race Enabled: false
+TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
+Check Table Before Drop: false |
++------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+```
+
+",1, unix timestamp is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error select a from unixtime select unix timestamp a what did you expect to see in mysql mysql select a from unixtime a from unixtime row in set sec mysql select unix timestamp a unix timestamp a row in set sec what did you see instead in tidb mysql select a from unixtime a from unixtime row in set sec mysql select unix timestamp a unix timestamp a row in set sec what version of tidb are you using tidb server v or run select tidb version on tidb tidb version release version beta git commit hash git branch master utc build time goversion go version darwin race enabled false tikv min version alpha check table before drop false ,1
+5751,8205166684.0,IssuesEvent,2018-09-03 09:16:04,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,type bit could have null as its default value,type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```sql
+CREATE TABLE testAllTypes (
+ field_1 BIT NULL DEFAULT NULL
+ ,field_2 TINYINT NULL DEFAULT NULL
+ ,field_3 TINYINT UNSIGNED NULL DEFAULT NULL
+ ,field_4 BIGINT NULL DEFAULT NULL
+ ,field_5 BIGINT UNSIGNED NULL DEFAULT NULL
+ ,field_6 MEDIUMBLOB NULL DEFAULT NULL
+ ,field_7 LONGBLOB NULL DEFAULT NULL
+ ,field_8 BLOB NULL DEFAULT NULL
+ ,field_9 TINYBLOB NULL DEFAULT NULL
+ ,field_10 VARBINARY(255) NULL DEFAULT NULL
+ ,field_11 BINARY(255) NULL DEFAULT NULL
+ ,field_12 MEDIUMTEXT NULL DEFAULT NULL
+ ,field_13 LONGTEXT NULL DEFAULT NULL
+ ,field_14 TEXT NULL DEFAULT NULL
+ ,field_15 TINYTEXT NULL DEFAULT NULL
+ ,field_16 CHAR(255) NULL DEFAULT NULL
+ ,field_17 NUMERIC NULL DEFAULT NULL
+ ,field_18 DECIMAL NULL DEFAULT NULL
+ ,field_19 INTEGER NULL DEFAULT NULL
+ ,field_20 INTEGER UNSIGNED NULL DEFAULT NULL
+ ,field_21 INT NULL DEFAULT NULL
+ ,field_22 INT UNSIGNED NULL DEFAULT NULL
+ ,field_23 MEDIUMINT NULL DEFAULT NULL
+ ,field_24 MEDIUMINT UNSIGNED NULL DEFAULT NULL
+ ,field_25 SMALLINT NULL DEFAULT NULL
+ ,field_26 SMALLINT UNSIGNED NULL DEFAULT NULL
+ ,field_27 FLOAT NULL DEFAULT NULL
+ ,field_28 DOUBLE NULL DEFAULT NULL
+ ,field_29 DOUBLE PRECISION NULL DEFAULT NULL
+ ,field_30 REAL NULL DEFAULT NULL
+ ,field_31 VARCHAR(255) NULL DEFAULT NULL
+ ,field_32 DATE NULL DEFAULT NULL
+ ,field_33 TIME NULL DEFAULT NULL
+ ,field_34 DATETIME NULL DEFAULT NULL
+ ,field_35 TIMESTAMP NULL DEFAULT NULL
+);
+```
+
+2. What did you expect to see?
+No error.
+
+
+3. What did you see instead?
+ERROR 1067 (42000): Invalid default value for 'field_1'
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+e04f74b031f5b47dba79537e7780356bc96745c5
+",True,"type bit could have null as its default value - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```sql
+CREATE TABLE testAllTypes (
+ field_1 BIT NULL DEFAULT NULL
+ ,field_2 TINYINT NULL DEFAULT NULL
+ ,field_3 TINYINT UNSIGNED NULL DEFAULT NULL
+ ,field_4 BIGINT NULL DEFAULT NULL
+ ,field_5 BIGINT UNSIGNED NULL DEFAULT NULL
+ ,field_6 MEDIUMBLOB NULL DEFAULT NULL
+ ,field_7 LONGBLOB NULL DEFAULT NULL
+ ,field_8 BLOB NULL DEFAULT NULL
+ ,field_9 TINYBLOB NULL DEFAULT NULL
+ ,field_10 VARBINARY(255) NULL DEFAULT NULL
+ ,field_11 BINARY(255) NULL DEFAULT NULL
+ ,field_12 MEDIUMTEXT NULL DEFAULT NULL
+ ,field_13 LONGTEXT NULL DEFAULT NULL
+ ,field_14 TEXT NULL DEFAULT NULL
+ ,field_15 TINYTEXT NULL DEFAULT NULL
+ ,field_16 CHAR(255) NULL DEFAULT NULL
+ ,field_17 NUMERIC NULL DEFAULT NULL
+ ,field_18 DECIMAL NULL DEFAULT NULL
+ ,field_19 INTEGER NULL DEFAULT NULL
+ ,field_20 INTEGER UNSIGNED NULL DEFAULT NULL
+ ,field_21 INT NULL DEFAULT NULL
+ ,field_22 INT UNSIGNED NULL DEFAULT NULL
+ ,field_23 MEDIUMINT NULL DEFAULT NULL
+ ,field_24 MEDIUMINT UNSIGNED NULL DEFAULT NULL
+ ,field_25 SMALLINT NULL DEFAULT NULL
+ ,field_26 SMALLINT UNSIGNED NULL DEFAULT NULL
+ ,field_27 FLOAT NULL DEFAULT NULL
+ ,field_28 DOUBLE NULL DEFAULT NULL
+ ,field_29 DOUBLE PRECISION NULL DEFAULT NULL
+ ,field_30 REAL NULL DEFAULT NULL
+ ,field_31 VARCHAR(255) NULL DEFAULT NULL
+ ,field_32 DATE NULL DEFAULT NULL
+ ,field_33 TIME NULL DEFAULT NULL
+ ,field_34 DATETIME NULL DEFAULT NULL
+ ,field_35 TIMESTAMP NULL DEFAULT NULL
+);
+```
+
+2. What did you expect to see?
+No error.
+
+
+3. What did you see instead?
+ERROR 1067 (42000): Invalid default value for 'field_1'
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+e04f74b031f5b47dba79537e7780356bc96745c5
+",1,type bit could have null as its default value please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql create table testalltypes field bit null default null field tinyint null default null field tinyint unsigned null default null field bigint null default null field bigint unsigned null default null field mediumblob null default null field longblob null default null field blob null default null field tinyblob null default null field varbinary null default null field binary null default null field mediumtext null default null field longtext null default null field text null default null field tinytext null default null field char null default null field numeric null default null field decimal null default null field integer null default null field integer unsigned null default null field int null default null field int unsigned null default null field mediumint null default null field mediumint unsigned null default null field smallint null default null field smallint unsigned null default null field float null default null field double null default null field double precision null default null field real null default null field varchar null default null field date null default null field time null default null field datetime null default null field timestamp null default null what did you expect to see no error what did you see instead error invalid default value for field what version of tidb are you using tidb server v or run select tidb version on tidb ,1
+12186,14370907407.0,IssuesEvent,2020-12-01 11:46:50,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Index name too long for anonymous index,severity/moderate sig/DDL status/help-wanted type/bug type/compatibility,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+create table ttttt(bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb int, b int);
+alter table ttttt add index bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb(b);
+alter table ttttt add index (bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb);
+```
+
+2. What did you expect to see?
+```
+mysql> alter table ttttt add index (bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb);
+Query OK, 0 rows affected (0.04 sec)
+Records: 0 Duplicates: 0 Warnings: 0
+
+mysql> show create table ttttt;
++-------+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| ttttt | CREATE TABLE `ttttt` (
+ `bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb` int(11) DEFAULT NULL,
+ `b` int(11) DEFAULT NULL,
+ KEY `bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb` (`b`),
+ KEY `bbbbbbbbbbbbbbbbbbbbbbbbbbbbbb_2` (`bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb`)
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci |
++-------+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+```
+TiDB> alter table ttttt add index (bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb);
+[ddl:1059]Identifier name 'bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb_2' is too long
+```
+
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+TiDB> select tidb_version();
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v4.0.0-alpha-677-g18e42cfd2
+Git Commit Hash: 18e42cfd233fa04850c24469c413237e38f02726
+Git Branch: feature/wasm
+UTC Build Time: 2019-11-28 08:41:07
+GoVersion: go version go1.13.4 linux/amd64
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false |
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+",True,"Index name too long for anonymous index - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+create table ttttt(bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb int, b int);
+alter table ttttt add index bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb(b);
+alter table ttttt add index (bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb);
+```
+
+2. What did you expect to see?
+```
+mysql> alter table ttttt add index (bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb);
+Query OK, 0 rows affected (0.04 sec)
+Records: 0 Duplicates: 0 Warnings: 0
+
+mysql> show create table ttttt;
++-------+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| ttttt | CREATE TABLE `ttttt` (
+ `bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb` int(11) DEFAULT NULL,
+ `b` int(11) DEFAULT NULL,
+ KEY `bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb` (`b`),
+ KEY `bbbbbbbbbbbbbbbbbbbbbbbbbbbbbb_2` (`bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb`)
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci |
++-------+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+
+3. What did you see instead?
+```
+TiDB> alter table ttttt add index (bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb);
+[ddl:1059]Identifier name 'bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb_2' is too long
+```
+
+
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+```
+TiDB> select tidb_version();
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| tidb_version() |
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+| Release Version: v4.0.0-alpha-677-g18e42cfd2
+Git Commit Hash: 18e42cfd233fa04850c24469c413237e38f02726
+Git Branch: feature/wasm
+UTC Build Time: 2019-11-28 08:41:07
+GoVersion: go version go1.13.4 linux/amd64
+Race Enabled: false
+TiKV Min Version: v3.0.0-60965b006877ca7234adaced7890d7b029ed1306
+Check Table Before Drop: false |
++-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
+1 row in set (0.00 sec)
+```
+",1,index name too long for anonymous index bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error create table ttttt bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb int b int alter table ttttt add index bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb b alter table ttttt add index bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb what did you expect to see mysql alter table ttttt add index bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb query ok rows affected sec records duplicates warnings mysql show create table ttttt table create table ttttt create table ttttt bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb int default null b int default null key bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb b key bbbbbbbbbbbbbbbbbbbbbbbbbbbbbb bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb engine innodb default charset collate ai ci row in set sec what did you see instead tidb alter table ttttt add index bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb identifier name bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb is too long what version of tidb are you using tidb server v or run select tidb version on tidb tidb select tidb version tidb version release version alpha git commit hash git branch feature wasm utc build time goversion go version linux race enabled false tikv min version check table before drop false row in set sec ,1
+20780,3836245386.0,IssuesEvent,2016-04-01 17:15:51,mapbox/rasterio,https://api.github.com/repos/mapbox/rasterio,closed,CLI testing on Windows,cli testing,"@geowurster @brendan-ward I'm having second thoughts about our current cli testing pattern. It's good to test that our plugin framework works, but we don't need to test it over and over again. What would you think about going back to
+
+```
+result = runner.invoke(rasterio.rio.convert.clip,
+ ['tests/data/shade.tif', output, '--bounds'] + TEST_BBOX, ...)
+```
+
+so that Brendan can run the tests on Windows?",1.0,"CLI testing on Windows - @geowurster @brendan-ward I'm having second thoughts about our current cli testing pattern. It's good to test that our plugin framework works, but we don't need to test it over and over again. What would you think about going back to
+
+```
+result = runner.invoke(rasterio.rio.convert.clip,
+ ['tests/data/shade.tif', output, '--bounds'] + TEST_BBOX, ...)
+```
+
+so that Brendan can run the tests on Windows?",0,cli testing on windows geowurster brendan ward i m having second thoughts about our current cli testing pattern it s good to test that our plugin framework works but we don t need to test it over and over again what would you think about going back to result runner invoke rasterio rio convert clip test bbox so that brendan can run the tests on windows ,0
+178182,29512279526.0,IssuesEvent,2023-06-04 03:55:38,sboxgame/issues,https://api.github.com/repos/sboxgame/issues,opened,ClientInput Unmanaged struct Support,api design,"### What it is?
-### 4. What is your TiDB version? (Required)
+Currently we are unable to use a Unmanaged struct with a client input property. which is quite annoying.
+
+I'd like to futher add that maybe it would be also cool to have something similar to INetworkSerializer but for sending input commands.
-```
-$ ./bin/tidb-server -V
-Release Version: v6.6.0-alpha-274-g1e0956d5b
-Edition: Community
-Git Commit Hash: 1e0956d5ba41182e603295e02ae8f767d62979e4
-Git Branch: master
-UTC Build Time: 2023-01-22 23:13:24
-GoVersion: go1.19.5
-Race Enabled: false
-TiKV Min Version: 6.2.0-alpha
-Check Table Before Drop: false
-Store: unistore
-```",1,column defaults in comfieldlist response violate protocol bug report the mysql comfieldlist returns default values for columns however this isn t fully implemented in tidb so it won t send the actual defaults and it also seems to violate the protocol minimal reproduce step required send a field list query e g by connecting without database and running use test in the mysql client dump and inspect traffic with wireshark what did you expect to see required proper column defaults what did you see instead required too many zeros being written what is your tidb version required bin tidb server v release version alpha edition community git commit hash git branch master utc build time goversion race enabled false tikv min version alpha check table before drop false store unistore ,1
-8679,10605931139.0,IssuesEvent,2019-10-10 21:40:12,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Navicat fails to connect (due to missing mysql.proc_priv table),help wanted type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+### What should it be?
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+Should work, currently it just throws an error saying your type doesn't work with Client Input.",1.0,"ClientInput Unmanaged struct Support - ### What it is?
- SELECT * FROM mysql.procs_priv;
+Currently we are unable to use a Unmanaged struct with a client input property. which is quite annoying.
+
+I'd like to futher add that maybe it would be also cool to have something similar to INetworkSerializer but for sending input commands.
-2. What did you expect to see?
-
-Host Db User Routine_name Routine_type Grantor Proc_priv Timestamp
+### What should it be?
-3. What did you see instead?
-[Err] 1146 - Table 'mysql.procs_priv' doesn't exist
+Should work, currently it just throws an error saying your type doesn't work with Client Input.",0,clientinput unmanaged struct support what it is currently we are unable to use a unmanaged struct with a client input property which is quite annoying i d like to futher add that maybe it would be also cool to have something similar to inetworkserializer but for sending input commands what should it be should work currently it just throws an error saying your type doesn t work with client input ,0
+190923,22173483766.0,IssuesEvent,2022-06-06 05:19:36,Satheesh575555/linux-4.19.72,https://api.github.com/repos/Satheesh575555/linux-4.19.72,reopened,CVE-2021-30002 (Medium) detected in linuxlinux-4.19.236,security vulnerability,"## CVE-2021-30002 - Medium Severity Vulnerability
+ Vulnerable Library - linuxlinux-4.19.236
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-1.1.0-dev.2
+
Found in base branch: master
+
+
+ Vulnerable Source Files (2)
+
+
-TiDB don't have t mysql.proc_priv table. Navicat have failed to login in TiDB with non-root user because it got an error by sending such sql query.",True,"Navicat fails to connect (due to missing mysql.proc_priv table) - Please answer these questions before submitting your issue. Thanks!
-
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-
- SELECT * FROM mysql.procs_priv;
+ /drivers/media/v4l2-core/v4l2-ioctl.c
+ /drivers/media/v4l2-core/v4l2-ioctl.c
+
+
+
+
+
+
+ Vulnerability Details
+
+
+An issue was discovered in the Linux kernel before 5.11.3 when a webcam device exists. video_usercopy in drivers/media/v4l2-core/v4l2-ioctl.c has a memory leak for large arguments, aka CID-fb18802a338b.
-2. What did you expect to see?
-
-Host Db User Routine_name Routine_type Grantor Proc_priv Timestamp
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-1.1.0-dev.2
+
+
+
-TiDB don't have t mysql.proc_priv table. Navicat have failed to login in TiDB with non-root user because it got an error by sending such sql query.",1,navicat fails to connect due to missing mysql proc priv table please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error select from mysql procs priv what did you expect to see host db user routine name routine type grantor proc priv timestamp what did you see instead table mysql procs priv doesn t exist what version of tidb are you using tidb server v or run select tidb version on tidb dev tidb don t have t mysql proc priv table navicat have failed to login in tidb with non root user because it got an error by sending such sql query ,1
-193019,14635237919.0,IssuesEvent,2020-12-24 07:42:00,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,executor_test.go:testSuiteP2.TestPointUpdatePreparedPlan failed,component/test,"executor_test.go:testSuiteP2.TestPointUpdatePreparedPlan
+***
+Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",True,"CVE-2021-30002 (Medium) detected in linuxlinux-4.19.236 - ## CVE-2021-30002 - Medium Severity Vulnerability
+ Vulnerable Library - linuxlinux-4.19.236
+
-Latest failed builds:
-https://internal.pingcap.net/idc-jenkins/job/tidb_ghpr_unit_test/31968/display/redirect
-https://internal.pingcap.net/idc-jenkins/job/tidb_ghpr_unit_test/31876/display/redirect
-https://internal.pingcap.net/idc-jenkins/job/tidb_ghpr_unit_test/31961/display/redirect
-",0,executor test go testpointupdatepreparedplan failed executor test go testpointupdatepreparedplan latest failed builds ,0
-3476,6460255882.0,IssuesEvent,2017-08-16 03:12:06,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Built-in function TIME_FORMAT not supported,compatibility rc3.1,"Please answer these questions before submitting your issue. Thanks!
+
Found in base branch: master
+
+
+ Vulnerable Source Files (2)
+
+
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+ /drivers/media/v4l2-core/v4l2-ioctl.c
+ /drivers/media/v4l2-core/v4l2-ioctl.c
+
+
+
+
+
+
+ Vulnerability Details
+
+
+An issue was discovered in the Linux kernel before 5.11.3 when a webcam device exists. video_usercopy in drivers/media/v4l2-core/v4l2-ioctl.c has a memory leak for large arguments, aka CID-fb18802a338b.
-```sql
-select TIME_FORMAT(""24:00:00"", '%r');
-```
+
-3. What did you see instead?
+
+
+
-ERROR 1305 (42000): FUNCTION TIME_FORMAT does not exist
+***
+Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",0,cve medium detected in linuxlinux cve medium severity vulnerability vulnerable library linuxlinux the linux kernel library home page a href found in head commit a href found in base branch master vulnerable source files drivers media core ioctl c drivers media core ioctl c vulnerability details an issue was discovered in the linux kernel before when a webcam device exists video usercopy in drivers media core ioctl c has a memory leak for large arguments aka cid publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource ,0
+8678,10605803336.0,IssuesEvent,2019-10-10 21:21:08,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,SQL_BIG_RESULT syntax support.,type/compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```
+CREATE TABLE t1 (
+ spID int(10) unsigned,
+ userID int(10) unsigned,
+ score smallint(5) unsigned,
+ key (spid),
+ key (score)
+);
+
+select sql_big_result spid,sum(userid) from t1 group by spid;
+```
+
+
+2. What did you expect to see?
+
+```
+mysql> select sql_big_result spid,sum(userid) from t1 group by spid;
+Empty set (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> select sql_big_result spid,sum(userid) from t1 group by spid;
+ERROR 1054 (42S22): Unknown column 'sql_big_result' in 'field list'
+mysql> select spid,sum(userid) from t1 group by spid;
+Empty set (0.01 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+```
+Release Version: 0.9.0
+Git Commit Hash: a7aaa64c76b5a1e5bb66caf94b888515cc334cf1
+Git Branch: master
+UTC Build Time: 2017-10-10 08:44:43
+```
+",True,"SQL_BIG_RESULT syntax support. - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+
+```
+CREATE TABLE t1 (
+ spID int(10) unsigned,
+ userID int(10) unsigned,
+ score smallint(5) unsigned,
+ key (spid),
+ key (score)
+);
+
+select sql_big_result spid,sum(userid) from t1 group by spid;
+```
+
+
+2. What did you expect to see?
+
+```
+mysql> select sql_big_result spid,sum(userid) from t1 group by spid;
+Empty set (0.00 sec)
+```
+
+3. What did you see instead?
+
+```
+mysql> select sql_big_result spid,sum(userid) from t1 group by spid;
+ERROR 1054 (42S22): Unknown column 'sql_big_result' in 'field list'
+mysql> select spid,sum(userid) from t1 group by spid;
+Empty set (0.01 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+```
+Release Version: 0.9.0
+Git Commit Hash: a7aaa64c76b5a1e5bb66caf94b888515cc334cf1
+Git Branch: master
+UTC Build Time: 2017-10-10 08:44:43
+```
+",1,sql big result syntax support please answer these questions before submitting your issue thanks what did you do create table spid int unsigned userid int unsigned score smallint unsigned key spid key score select sql big result spid sum userid from group by spid what did you expect to see mysql select sql big result spid sum userid from group by spid empty set sec what did you see instead mysql select sql big result spid sum userid from group by spid error unknown column sql big result in field list mysql select spid sum userid from group by spid empty set sec what version of tidb are you using tidb server v release version git commit hash git branch master utc build time ,1
+220926,16990471664.0,IssuesEvent,2021-06-30 19:42:49,htw-pv3/pvlib-python-pv3,https://api.github.com/repos/htw-pv3/pvlib-python-pv3,closed,Rework scripts and modules,documentation help wanted question,"The code will be in different .py files.
+We will use jupyter only for the visualisation of the results.
+",1.0,"Rework scripts and modules - The code will be in different .py files.
+We will use jupyter only for the visualisation of the results.
+",0,rework scripts and modules the code will be in different py files we will use jupyter only for the visualisation of the results ,0
+306016,9379635503.0,IssuesEvent,2019-04-04 15:19:03,R-Stefano/academAI,https://api.github.com/repos/R-Stefano/academAI,closed,Database,assigned priority,"We need to store the questions, the answers and the rating given by the user to the answers.
+",1.0,"Database - We need to store the questions, the answers and the rating given by the user to the answers.
+",0,database we need to store the questions the answers and the rating given by the user to the answers ,0
+11930,14060443330.0,IssuesEvent,2020-11-03 06:01:32,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Behavior on VARCHAR data type of comparison operator '=' is different from mysql,challenge-program severity/major sig/planner status/help-wanted type/bug type/compatibility type/duplicate,"## Description
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+create table t (a char(10), b varchar(10), c binary(10), d varbinary(10));
+insert into t values ('text ','text ','text ','text '); <-----there're trailing spaces
+
+mysql> desc t;
++-------+---------------+------+-----+---------+-------+
+| Field | Type | Null | Key | Default | Extra |
++-------+---------------+------+-----+---------+-------+
+| a | char(10) | YES | | NULL | |
+| b | varchar(10) | YES | | NULL | |
+| c | binary(10) | YES | | NULL | |
+| d | varbinary(10) | YES | | NULL | |
++-------+---------------+------+-----+---------+-------+
+4 rows in set (0.00 sec)
+
+mysql> select * from t;
++------+--------+------------+--------+
+| a | b | c | d |
++------+--------+------------+--------+
+| text | text | text | text |
++------+--------+------------+--------+
+1 row in set (0.00 sec)
+```
+
+
+2. What did you expect to see?
+
+MySQL
+```
+mysql> select * from t where a = 'text';
++------+--------+------------+--------+
+| a | b | c | d |
++------+--------+------------+--------+
+| text | text | text | text |
++------+--------+------------+--------+
+1 row in set (0.00 sec)
+
+mysql> select * from t where b = 'text';
++------+--------+------------+--------+
+| a | b | c | d |
++------+--------+------------+--------+
+| text | text | text | text |
++------+--------+------------+--------+
+1 row in set (0.00 sec)
+
+mysql> select * from t where c = 'text';
+Empty set (0.00 sec)
+
+mysql> select * from t where d = 'text';
+Empty set (0.00 sec)
+```
+
+3. What did you see instead?
+
+TiDB treats CHAR and VARCHAR in different ways, so I guess operator '=' is not designed to strictly compare the trailing spaces.
+```
+MySQL [gin]> select * from t where a='text';
++------+--------+------------+--------+
+| a | b | c | d |
++------+--------+------------+--------+
+| text | text | text | text |
++------+--------+------------+--------+
+1 row in set (0.00 sec)
+
+MySQL [gin]> select * from t where b='text';
+Empty set (0.00 sec)
+
+MySQL [gin]> select * from t where c='text';
+Empty set (0.01 sec)
+
+MySQL [gin]> select * from t where d='text';
+Empty set (0.00 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+Git Commit Hash: 365e4ab491b683a69c2004f30b1ae4f86256e2ad
+Git Commit Branch: master
+UTC Build Time: 2017-08-16 01:24:27
-4. What version of TiDB are you using (`tidb-server -V`)?
+## SIG slack channel
-",True,"Built-in function TIME_FORMAT not supported - Please answer these questions before submitting your issue. Thanks!
+ [#sig-planner](https://slack.tidb.io/invite?team=tidb-community&channel=sig-planner&ref=high-performance)
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
+## Score
-```sql
-select TIME_FORMAT(""24:00:00"", '%r');
-```
+- 900
-2. What did you expect to see?
+## Mentor
-```
-+-------------------------------+
-| TIME_FORMAT(""24:00:00"", '%r') |
-+-------------------------------+
-| 12:00:00 AM |
-+-------------------------------+
-1 row in set (0.00 sec)
-```
+* @lzmhhh123
+",True,"Behavior on VARCHAR data type of comparison operator '=' is different from mysql - ## Description
+Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+create table t (a char(10), b varchar(10), c binary(10), d varbinary(10));
+insert into t values ('text ','text ','text ','text '); <-----there're trailing spaces
+
+mysql> desc t;
++-------+---------------+------+-----+---------+-------+
+| Field | Type | Null | Key | Default | Extra |
++-------+---------------+------+-----+---------+-------+
+| a | char(10) | YES | | NULL | |
+| b | varchar(10) | YES | | NULL | |
+| c | binary(10) | YES | | NULL | |
+| d | varbinary(10) | YES | | NULL | |
++-------+---------------+------+-----+---------+-------+
+4 rows in set (0.00 sec)
+
+mysql> select * from t;
++------+--------+------------+--------+
+| a | b | c | d |
++------+--------+------------+--------+
+| text | text | text | text |
++------+--------+------------+--------+
+1 row in set (0.00 sec)
+```
+
+
+2. What did you expect to see?
+
+MySQL
+```
+mysql> select * from t where a = 'text';
++------+--------+------------+--------+
+| a | b | c | d |
++------+--------+------------+--------+
+| text | text | text | text |
++------+--------+------------+--------+
+1 row in set (0.00 sec)
+
+mysql> select * from t where b = 'text';
++------+--------+------------+--------+
+| a | b | c | d |
++------+--------+------------+--------+
+| text | text | text | text |
++------+--------+------------+--------+
+1 row in set (0.00 sec)
+
+mysql> select * from t where c = 'text';
+Empty set (0.00 sec)
+
+mysql> select * from t where d = 'text';
+Empty set (0.00 sec)
+```
+
+3. What did you see instead?
+
+TiDB treats CHAR and VARCHAR in different ways, so I guess operator '=' is not designed to strictly compare the trailing spaces.
+```
+MySQL [gin]> select * from t where a='text';
++------+--------+------------+--------+
+| a | b | c | d |
++------+--------+------------+--------+
+| text | text | text | text |
++------+--------+------------+--------+
+1 row in set (0.00 sec)
+
+MySQL [gin]> select * from t where b='text';
+Empty set (0.00 sec)
+
+MySQL [gin]> select * from t where c='text';
+Empty set (0.01 sec)
+
+MySQL [gin]> select * from t where d='text';
+Empty set (0.00 sec)
+```
+
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+Git Commit Hash: 365e4ab491b683a69c2004f30b1ae4f86256e2ad
+Git Commit Branch: master
+UTC Build Time: 2017-08-16 01:24:27
-3. What did you see instead?
+## SIG slack channel
-ERROR 1305 (42000): FUNCTION TIME_FORMAT does not exist
+ [#sig-planner](https://slack.tidb.io/invite?team=tidb-community&channel=sig-planner&ref=high-performance)
-4. What version of TiDB are you using (`tidb-server -V`)?
+## Score
-",1,built in function time format not supported please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql select time format r what did you expect to see time format r am row in set sec what did you see instead error function time format does not exist what version of tidb are you using tidb server v ,1
-3500,6485730661.0,IssuesEvent,2017-08-19 13:18:43,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,type inference of `@@GLOBAL.sql_mode` and `@@SESSION.sql_mode` is incorrect,compatibility easy,"## 1. What did you do?
-
-result type's `Collation` and `Type` of `@@GLOBAL.sql_mode` and `@@SESSION.sql_mode` is incorrect
-
-## 2. What did you expect to see?
-
-```sql
-MySQL > SELECT @@GLOBAL.sql_mode;
-Field 1: `@@GLOBAL.sql_mode`
-Catalog: `def`
-Database: ``
-Table: ``
-Org_table: ``
-Type: VAR_STRING
-Collation: utf8_general_ci (33)
-Length: 411
-Max_length: 137
-Decimals: 31
-Flags:
-
-
-+-------------------------------------------------------------------------------------------------------------------------------------------+
-| @@GLOBAL.sql_mode |
-+-------------------------------------------------------------------------------------------------------------------------------------------+
-| ONLY_FULL_GROUP_BY,STRICT_TRANS_TABLES,NO_ZERO_IN_DATE,NO_ZERO_DATE,ERROR_FOR_DIVISION_BY_ZERO,NO_AUTO_CREATE_USER,NO_ENGINE_SUBSTITUTION |
-+-------------------------------------------------------------------------------------------------------------------------------------------+
-1 row in set (0.00 sec)
-```
+- 900
-```sql
-MySQL > SELECT @@SESSION.sql_mode;
-Field 1: `@@SESSION.sql_mode`
-Catalog: `def`
-Database: ``
-Table: ``
-Org_table: ``
-Type: VAR_STRING
-Collation: utf8_general_ci (33)
-Length: 411
-Max_length: 137
-Decimals: 31
-Flags:
-
-
-+-------------------------------------------------------------------------------------------------------------------------------------------+
-| @@SESSION.sql_mode |
-+-------------------------------------------------------------------------------------------------------------------------------------------+
-| ONLY_FULL_GROUP_BY,STRICT_TRANS_TABLES,NO_ZERO_IN_DATE,NO_ZERO_DATE,ERROR_FOR_DIVISION_BY_ZERO,NO_AUTO_CREATE_USER,NO_ENGINE_SUBSTITUTION |
-+-------------------------------------------------------------------------------------------------------------------------------------------+
-1 row in set (0.00 sec)
-```
+## Mentor
-## 3. What did you see instead?
-
-```sql
-TiDB > SELECT @@GLOBAL.sql_mode;
-Field 1: `@@GLOBAL.sql_mode`
-Catalog: `def`
-Database: ``
-Table: ``
-Org_table: ``
-Type: STRING
-Collation: ? (0)
-Length: 0
-Max_length: 42
-Decimals: 31
-Flags:
-
-
-+--------------------------------------------+
-| @@GLOBAL.sql_mode |
-+--------------------------------------------+
-| STRICT_TRANS_TABLES,NO_ENGINE_SUBSTITUTION |
-+--------------------------------------------+
-1 row in set (0.00 sec)
-```
+* @lzmhhh123
+",1,behavior on varchar data type of comparison operator is different from mysql description please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error create table t a char b varchar c binary d varbinary insert into t values text text text text there re trailing spaces mysql desc t field type null key default extra a char yes null b varchar yes null c binary yes null d varbinary yes null rows in set sec mysql select from t a b c d text text text text row in set sec what did you expect to see mysql mysql select from t where a text a b c d text text text text row in set sec mysql select from t where b text a b c d text text text text row in set sec mysql select from t where c text empty set sec mysql select from t where d text empty set sec what did you see instead tidb treats char and varchar in different ways so i guess operator is not designed to strictly compare the trailing spaces mysql select from t where a text a b c d text text text text row in set sec mysql select from t where b text empty set sec mysql select from t where c text empty set sec mysql select from t where d text empty set sec what version of tidb are you using tidb server v git commit hash git commit branch master utc build time sig slack channel score mentor ,1
+281975,24441725469.0,IssuesEvent,2022-10-06 14:59:56,hashicorp/nomad,https://api.github.com/repos/hashicorp/nomad,closed,false positive on semgrep rule for time in FSM around metrics,theme/testing theme/flaky-tests,"From https://github.com/hashicorp/nomad/runs/7680883904?check_suite_focus=true, the `no-time-in-fsm` rule triggers on the metrics, which aren't persisted to raft.
+
+```
+nomad/fsm.go
+ semgrep.no-time-in-fsm
+ time.Now() should not be called from within the Server's FSM. Apply Raft log messages to the
+ State Store must be deterministic so that each server contains exactly the same state. Since
+ time drifts between nodes, it must be set before the Raft log message is applied so that all
+ Raft members see the same timestamp.
+
+ 20[42](https://github.com/hashicorp/nomad/runs/7680883904?check_suite_focus=true#step:4:43)┆ defer metrics.MeasureSinceWithLabels([]string{""nomad"", ""fsm"", ""apply_sv_operation""}, time.Now(),
+```
+
+(Opening an issue rather than just fixing it because I might not get a chance to hit this before I'm out next week.)",2.0,"false positive on semgrep rule for time in FSM around metrics - From https://github.com/hashicorp/nomad/runs/7680883904?check_suite_focus=true, the `no-time-in-fsm` rule triggers on the metrics, which aren't persisted to raft.
+
+```
+nomad/fsm.go
+ semgrep.no-time-in-fsm
+ time.Now() should not be called from within the Server's FSM. Apply Raft log messages to the
+ State Store must be deterministic so that each server contains exactly the same state. Since
+ time drifts between nodes, it must be set before the Raft log message is applied so that all
+ Raft members see the same timestamp.
+
+ 20[42](https://github.com/hashicorp/nomad/runs/7680883904?check_suite_focus=true#step:4:43)┆ defer metrics.MeasureSinceWithLabels([]string{""nomad"", ""fsm"", ""apply_sv_operation""}, time.Now(),
+```
+
+(Opening an issue rather than just fixing it because I might not get a chance to hit this before I'm out next week.)",0,false positive on semgrep rule for time in fsm around metrics from the no time in fsm rule triggers on the metrics which aren t persisted to raft nomad fsm go semgrep no time in fsm time now should not be called from within the server s fsm apply raft log messages to the state store must be deterministic so that each server contains exactly the same state since time drifts between nodes it must be set before the raft log message is applied so that all raft members see the same timestamp defer metrics measuresincewithlabels string nomad fsm apply sv operation time now opening an issue rather than just fixing it because i might not get a chance to hit this before i m out next week ,0
+19167,4349520539.0,IssuesEvent,2016-07-30 16:33:48,OfficeDev/office-ui-fabric,https://api.github.com/repos/OfficeDev/office-ui-fabric,closed,Update icon samples page to MDL2 class names,documentation,The current icon samples page bundled with the repo (http://localhost:2020/Samples/Icons/index.html) still uses the old icon class names.,1.0,Update icon samples page to MDL2 class names - The current icon samples page bundled with the repo (http://localhost:2020/Samples/Icons/index.html) still uses the old icon class names.,0,update icon samples page to class names the current icon samples page bundled with the repo still uses the old icon class names ,0
+171076,20917322614.0,IssuesEvent,2022-03-24 14:28:33,wagner-deoliveira/proofy-react-app,https://api.github.com/repos/wagner-deoliveira/proofy-react-app,closed,CVE-2021-44906 (High) detected in minimist-1.2.5.tgz - autoclosed,security vulnerability,"## CVE-2021-44906 - High Severity Vulnerability
+ Vulnerable Library - minimist-1.2.5.tgz
-```sql
-TiDB > SELECT @@SESSION.sql_mode;
-Field 1: `@@SESSION.sql_mode`
-Catalog: `def`
-Database: ``
-Table: ``
-Org_table: ``
-Type: STRING
-Collation: ? (0)
-Length: 0
-Max_length: 42
-Decimals: 31
-Flags:
-
-
-+--------------------------------------------+
-| @@SESSION.sql_mode |
-+--------------------------------------------+
-| STRICT_TRANS_TABLES,NO_ENGINE_SUBSTITUTION |
-+--------------------------------------------+
-1 row in set (0.00 sec)
-```
+
+
+Minimist <=1.2.5 is vulnerable to Prototype Pollution via file index.js, function setKey() (lines 69-95).
-",True,"type inference of `@@GLOBAL.sql_mode` and `@@SESSION.sql_mode` is incorrect - ## 1. What did you do?
+
-",1,type inference of global sql mode and session sql mode is incorrect what did you do result type s collation and type of global sql mode and session sql mode is incorrect what did you expect to see sql mysql select global sql mode field global sql mode catalog def database table org table type var string collation general ci length max length decimals flags global sql mode only full group by strict trans tables no zero in date no zero date error for division by zero no auto create user no engine substitution row in set sec sql mysql select session sql mode field session sql mode catalog def database table org table type var string collation general ci length max length decimals flags session sql mode only full group by strict trans tables no zero in date no zero date error for division by zero no auto create user no engine substitution row in set sec what did you see instead sql tidb select global sql mode field global sql mode catalog def database table org table type string collation length max length decimals flags global sql mode strict trans tables no engine substitution row in set sec sql tidb select session sql mode field session sql mode catalog def database table org table type string collation length max length decimals flags session sql mode strict trans tables no engine substitution row in set sec what version of tidb are you using tidb server v ,1
-4994,7600556755.0,IssuesEvent,2018-04-28 03:29:55,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,"Support ""ALTER TABLE ti1 AUTO_INCREMENT 3""",DDL compatibility help wanted,"```
-CREATE TABLE ti1(a INT NOT NULL, b INT, c INT) engine=InnoDB;
-ALTER TABLE ti1 AUTO_INCREMENT 3;
-```
-
-report `line 1 column 32 near "";"" (total length 33)`",True,"Support ""ALTER TABLE ti1 AUTO_INCREMENT 3"" - ```
-CREATE TABLE ti1(a INT NOT NULL, b INT, c INT) engine=InnoDB;
-ALTER TABLE ti1 AUTO_INCREMENT 3;
-```
-
-report `line 1 column 32 near "";"" (total length 33)`",1,support alter table auto increment create table a int not null b int c int engine innodb alter table auto increment report line column near total length ,1
-11625,13672437994.0,IssuesEvent,2020-09-29 08:30:18,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,_utf8mb4 not supported,type/compatibility,"Please answer these questions before submitting your issue. Thanks!
-
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-
-```sql
-select left(_utf8mb4 0xD0B0D0B1D0B2, 1);
-select right(_utf8mb4 0xD0B0D0B2D0B2, 1);
-```
-
-2. What did you expect to see?
-
-```
-+----------------------------------+
-| left(_utf8mb4 0xD0B0D0B1D0B2, 1) |
-+----------------------------------+
-| а |
-+----------------------------------+
-1 row in set (0.00 sec)
-
-+-----------------------------------+
-| right(_utf8mb4 0xD0B0D0B2D0B2, 1) |
-+-----------------------------------+
-| в |
-+-----------------------------------+
-1 row in set (0.00 sec)
-```
-
-3. What did you see instead?
-
-ERROR 1105 (HY000): line 0 column 35 near "", 1)"" (total length 39)
-
-4. What version of TiDB are you using (`tidb-server -V`)?
-
-",True,"_utf8mb4 not supported - Please answer these questions before submitting your issue. Thanks!
-
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-
-```sql
-select left(_utf8mb4 0xD0B0D0B1D0B2, 1);
-select right(_utf8mb4 0xD0B0D0B2D0B2, 1);
-```
-
-2. What did you expect to see?
-
-```
-+----------------------------------+
-| left(_utf8mb4 0xD0B0D0B1D0B2, 1) |
-+----------------------------------+
-| а |
-+----------------------------------+
-1 row in set (0.00 sec)
-
-+-----------------------------------+
-| right(_utf8mb4 0xD0B0D0B2D0B2, 1) |
-+-----------------------------------+
-| в |
-+-----------------------------------+
-1 row in set (0.00 sec)
-```
-
-3. What did you see instead?
-
-ERROR 1105 (HY000): line 0 column 35 near "", 1)"" (total length 39)
-
-4. What version of TiDB are you using (`tidb-server -V`)?
-
-",1, not supported please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql select left select right what did you expect to see left а row in set sec right в row in set sec what did you see instead error line column near total length what version of tidb are you using tidb server v ,1
-42246,17090646116.0,IssuesEvent,2021-07-08 16:58:20,microsoft/BotFramework-Composer,https://api.github.com/repos/microsoft/BotFramework-Composer,reopened,"BUG ""Luis build failed: Cannot read property 'utterances' of undefined"" after training on LUIS.ai",Bot Services Support Type: Bug customer-replied-to customer-reported,"## Describe the bug
-
-Hello! I'm sorry to open another ticket despite having another one opened for another issue, but this one seems like a bigger problem.
-
-When I create any bot (both C# and Node.js) on Composer, if I create the apps on luis.ai through composer (by creating dialogs and entities) as shown on the picture below:
-
-
-
-After I train and publish the AI through LUIS.ai, the bot on Composer becomes unresponsible, I can't even start the bot because of the following error message:
-
-
-
-I saw some topics on the error and they ended on the agreement that the ""solution"" is to delete the conversation apps on Luis.ai and recreate them again through Composer (by restarting the bot). This made the trick for me, the bot works now but I lost all my work on LUIS.ai. What is the point of training an AI through LUIS if I can't use it on Composer after that? Am I missing something?
-
-Is there another solution to this bug?
-
-## Version
-2.0
-## Browser
-
-
-
-- [ ] Electron distribution
-- [ ] Chrome
-- [ ] Safari
-- [ ] Firefox
-- [ X] Edge
-
-## OS
-
-
-
-- [ ] macOS
-- [X ] Windows
-- [ ] Ubuntu
-
-## To Reproduce
-
-Steps to reproduce the behavior:
-
-1. Create an empty bot on composer
-2. Create some dialogs and entities
-3. Connect to luis.ai through the bot settings -> development resources button
-4. Train the AI on luis.ai and publish a new version of the AI
-5. Try to restart the bot
-
-## Expected behavior
-
-Bot restarts with new AI from luis.ai
-
-## Screenshots
-
-
-
-## Additional context
-
-I love the application, Composer and the fast replies Microsoft gives on Github. I truly hope these bugs get fixed because Composer is a great platform for chatbot development",1.0,"BUG ""Luis build failed: Cannot read property 'utterances' of undefined"" after training on LUIS.ai - ## Describe the bug
-
-Hello! I'm sorry to open another ticket despite having another one opened for another issue, but this one seems like a bigger problem.
-
-When I create any bot (both C# and Node.js) on Composer, if I create the apps on luis.ai through composer (by creating dialogs and entities) as shown on the picture below:
-
-
-
-After I train and publish the AI through LUIS.ai, the bot on Composer becomes unresponsible, I can't even start the bot because of the following error message:
-
-
-
-I saw some topics on the error and they ended on the agreement that the ""solution"" is to delete the conversation apps on Luis.ai and recreate them again through Composer (by restarting the bot). This made the trick for me, the bot works now but I lost all my work on LUIS.ai. What is the point of training an AI through LUIS if I can't use it on Composer after that? Am I missing something?
-
-Is there another solution to this bug?
-
-## Version
-2.0
-## Browser
-
-
-
-- [ ] Electron distribution
-- [ ] Chrome
-- [ ] Safari
-- [ ] Firefox
-- [ X] Edge
-
-## OS
-
-
-
-- [ ] macOS
-- [X ] Windows
-- [ ] Ubuntu
-
-## To Reproduce
-
-Steps to reproduce the behavior:
-
-1. Create an empty bot on composer
-2. Create some dialogs and entities
-3. Connect to luis.ai through the bot settings -> development resources button
-4. Train the AI on luis.ai and publish a new version of the AI
-5. Try to restart the bot
-
-## Expected behavior
-
-Bot restarts with new AI from luis.ai
-
-## Screenshots
-
-
-
-## Additional context
-
-I love the application, Composer and the fast replies Microsoft gives on Github. I truly hope these bugs get fixed because Composer is a great platform for chatbot development",0,bug luis build failed cannot read property utterances of undefined after training on luis ai describe the bug hello i m sorry to open another ticket despite having another one opened for another issue but this one seems like a bigger problem when i create any bot both c and node js on composer if i create the apps on luis ai through composer by creating dialogs and entities as shown on the picture below after i train and publish the ai through luis ai the bot on composer becomes unresponsible i can t even start the bot because of the following error message i saw some topics on the error and they ended on the agreement that the solution is to delete the conversation apps on luis ai and recreate them again through composer by restarting the bot this made the trick for me the bot works now but i lost all my work on luis ai what is the point of training an ai through luis if i can t use it on composer after that am i missing something is there another solution to this bug version browser electron distribution chrome safari firefox edge os macos windows ubuntu to reproduce steps to reproduce the behavior create an empty bot on composer create some dialogs and entities connect to luis ai through the bot settings development resources button train the ai on luis ai and publish a new version of the ai try to restart the bot expected behavior bot restarts with new ai from luis ai screenshots additional context i love the application composer and the fast replies microsoft gives on github i truly hope these bugs get fixed because composer is a great platform for chatbot development,0
-6991,9284638287.0,IssuesEvent,2019-03-21 02:41:43,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Need to check and fix more types in `shou (full) columns`,type/compatibility,"## General Question
-
-
-As https://github.com/pingcap/tidb/pull/9810 discussed, we should check more types in `show columns` and ` show full columns`, and fix it!",True,"Need to check and fix more types in `shou (full) columns` - ## General Question
-
-
-As https://github.com/pingcap/tidb/pull/9810 discussed, we should check more types in `show columns` and ` show full columns`, and fix it!",1,need to check and fix more types in shou full columns general question as discussed we should check more types in show columns and show full columns and fix it ,1
-13939,3788390898.0,IssuesEvent,2016-03-21 14:37:02,tarbell-project/tarbell,https://api.github.com/repos/tarbell-project/tarbell,closed,Context variables only work in HTML files,in progress tag: documentation,"Should probably cut [this whole section](http://tarbell.readthedocs.org/en/1.0.5/build.html#where-can-context-variables-be-used) from the docs, or slim it way down, since javascript and CSS files are no longer rendered as templates (until we make that configurable).",1.0,"Context variables only work in HTML files - Should probably cut [this whole section](http://tarbell.readthedocs.org/en/1.0.5/build.html#where-can-context-variables-be-used) from the docs, or slim it way down, since javascript and CSS files are no longer rendered as templates (until we make that configurable).",0,context variables only work in html files should probably cut from the docs or slim it way down since javascript and css files are no longer rendered as templates until we make that configurable ,0
-3790,6653174894.0,IssuesEvent,2017-09-29 07:09:11,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,No length limitation for comment of index,compatibility,"Please answer these questions before submitting your issue. Thanks!
-
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-
-```sql
-CREATE TABLE t1 (id INT);
-CREATE INDEX id_index ON t1 (id) COMMENT 'MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD';
-```
-
-2. What did you expect to see?
-
-ERROR 1688 (HY000) at line 1: Comment for index 'id_index' is too long (max = 1024)
-
-3. What did you see instead?
-
-Query OK, 0 rows affected (0.05 sec)
-
-4. What version of TiDB are you using (`tidb-server -V`)?
-
-",True,"No length limitation for comment of index - Please answer these questions before submitting your issue. Thanks!
-
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-
-```sql
-CREATE TABLE t1 (id INT);
-CREATE INDEX id_index ON t1 (id) COMMENT 'MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD=40MERGE_THRESHOLD';
-```
-
-2. What did you expect to see?
-
-ERROR 1688 (HY000) at line 1: Comment for index 'id_index' is too long (max = 1024)
-
-3. What did you see instead?
-
-Query OK, 0 rows affected (0.05 sec)
-
-4. What version of TiDB are you using (`tidb-server -V`)?
-
-",1,no length limitation for comment of index please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql create table id int create index id index on id comment merge threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold threshold what did you expect to see error at line comment for index id index is too long max what did you see instead query ok rows affected sec what version of tidb are you using tidb server v ,1
-6231,8633471784.0,IssuesEvent,2018-11-22 13:58:19,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,support show hash partition table.,help wanted type/compatibility,"## Bug Report
-
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-```sql
-set @@session.tidb_enable_table_partition = 'on';
-create table th (
- a int,
- b int
-) partition by hash(a) partitions 4;
-```
-
-2. What did you expect to see?
-mysql:
-```sql
-mysql root@127.0.0.1:test> show create table th;
-+-------+----------------------------------------+
-| Table | Create Table |
-+-------+----------------------------------------+
-| th | CREATE TABLE `th` ( |
-| | `a` int(11) DEFAULT NULL, |
-| | `b` int(11) DEFAULT NULL |
-| | ) ENGINE=InnoDB DEFAULT CHARSET=latin1 |
-| | /*!50100 PARTITION BY HASH (a) |
-| | PARTITIONS 4 */ |
-+-------+----------------------------------------+
-```
-
-or
-```sql
-mysql root@127.0.0.1:test> show create table th;
-+-------+----------------------------------------+
-| Table | Create Table |
-+-------+----------------------------------------+
-| th | CREATE TABLE `th` ( |
-| | `a` int(11) DEFAULT NULL, |
-| | `b` int(11) DEFAULT NULL |
-| | ) ENGINE=InnoDB DEFAULT CHARSET=latin1 |
-| | PARTITION BY HASH (a) |
-| | PARTITIONS 4 |
-+-------+----------------------------------------+
-```
-
-3. What did you see instead?
-```sql
-+-------+-------------------------------------------------------------+
-| Table | Create Table |
-+-------+-------------------------------------------------------------+
-| th | CREATE TABLE `th` ( |
-| | `a` int(11) DEFAULT NULL, |
-| | `b` int(11) DEFAULT NULL |
-| | ) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_bin |
-| | PARTITION BY HASH ( `a` ) ( |
-| | PARTITION VALUES LESS THAN (), |
-| | PARTITION VALUES LESS THAN (), |
-| | PARTITION VALUES LESS THAN (), |
-| | PARTITION VALUES LESS THAN () |
-| | ) |
-+-------+-------------------------------------------------------------+
-```
-
-
-Related issue:
-https://github.com/pingcap/tidb/issues/7907
-
-",True,"support show hash partition table. - ## Bug Report
-
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-```sql
-set @@session.tidb_enable_table_partition = 'on';
-create table th (
- a int,
- b int
-) partition by hash(a) partitions 4;
-```
-
-2. What did you expect to see?
-mysql:
-```sql
-mysql root@127.0.0.1:test> show create table th;
-+-------+----------------------------------------+
-| Table | Create Table |
-+-------+----------------------------------------+
-| th | CREATE TABLE `th` ( |
-| | `a` int(11) DEFAULT NULL, |
-| | `b` int(11) DEFAULT NULL |
-| | ) ENGINE=InnoDB DEFAULT CHARSET=latin1 |
-| | /*!50100 PARTITION BY HASH (a) |
-| | PARTITIONS 4 */ |
-+-------+----------------------------------------+
-```
-
-or
-```sql
-mysql root@127.0.0.1:test> show create table th;
-+-------+----------------------------------------+
-| Table | Create Table |
-+-------+----------------------------------------+
-| th | CREATE TABLE `th` ( |
-| | `a` int(11) DEFAULT NULL, |
-| | `b` int(11) DEFAULT NULL |
-| | ) ENGINE=InnoDB DEFAULT CHARSET=latin1 |
-| | PARTITION BY HASH (a) |
-| | PARTITIONS 4 |
-+-------+----------------------------------------+
-```
-
-3. What did you see instead?
-```sql
-+-------+-------------------------------------------------------------+
-| Table | Create Table |
-+-------+-------------------------------------------------------------+
-| th | CREATE TABLE `th` ( |
-| | `a` int(11) DEFAULT NULL, |
-| | `b` int(11) DEFAULT NULL |
-| | ) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_bin |
-| | PARTITION BY HASH ( `a` ) ( |
-| | PARTITION VALUES LESS THAN (), |
-| | PARTITION VALUES LESS THAN (), |
-| | PARTITION VALUES LESS THAN (), |
-| | PARTITION VALUES LESS THAN () |
-| | ) |
-+-------+-------------------------------------------------------------+
-```
-
-
-Related issue:
-https://github.com/pingcap/tidb/issues/7907
-
-",1,support show hash partition table bug report what did you do if possible provide a recipe for reproducing the error sql set session tidb enable table partition on create table th a int b int partition by hash a partitions what did you expect to see mysql sql mysql root test show create table th table create table th create table th a int default null b int default null engine innodb default charset partition by hash a partitions or sql mysql root test show create table th table create table th create table th a int default null b int default null engine innodb default charset partition by hash a partitions what did you see instead sql table create table th create table th a int default null b int default null engine innodb default charset collate bin partition by hash a partition values less than partition values less than partition values less than partition values less than related issue ,1
-301266,9218166044.0,IssuesEvent,2019-03-11 12:44:15,rism-ch/muscat,https://api.github.com/repos/rism-ch/muscat,opened,Prevent source.id == source.source_id,Bug First priority Source,"if you add a 773 with the same id as the source, it will become the parent of itself.
-We need:
-
- - [ ] Prevent it in the backend
- - [ ] Add it to the validation",1.0,"Prevent source.id == source.source_id - if you add a 773 with the same id as the source, it will become the parent of itself.
-We need:
-
- - [ ] Prevent it in the backend
- - [ ] Add it to the validation",0,prevent source id source source id if you add a with the same id as the source it will become the parent of itself we need prevent it in the backend add it to the validation,0
-8680,10606147953.0,IssuesEvent,2019-10-10 22:19:36,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,tidb gives error while mysql gives warning when time is invalid,help wanted type/compatibility,"Please answer these questions before submitting your issue. Thanks!
-
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-
-```sql
-CREATE TABLE t1 (
- a INT,
- ts TIMESTAMP DEFAULT NOW(),
- PRIMARY KEY (ts)
- );
-SELECT * FROM t1 WHERE ts = '2008-12-31 23:59:60';
-```
-
-2. What did you expect to see?
-
-mysql:
-
-```
-mysql> SELECT * FROM t1 WHERE ts = '2008-12-31 23:59:60';
-Empty set, 2 warnings (0.00 sec)
-
-mysql> show warnings;
-+---------+------+--------------------------------------------------------------------------+
-| Level | Code | Message |
-+---------+------+--------------------------------------------------------------------------+
-| Warning | 1292 | Incorrect datetime value: '2008-12-31 23:59:60' for column 'ts' at row 1 |
-| Warning | 1292 | Incorrect datetime value: '2008-12-31 23:59:60' for column 'ts' at row 1 |
-+---------+------+--------------------------------------------------------------------------+
-2 rows in set (0.00 sec)
-```
-
-3. What did you see instead?
-
-tidb:
-
-```
-mysql> SELECT * FROM t1 WHERE ts = '2008-12-31 23:59:60';
-ERROR 1292 (22007): invalid time format: '60'
-```
-
-
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-
-```
-Release Version: v2.0.3
-Git Commit Hash: e4878329f0c69d7b810b8b40fb3b8071c69b5e02
-Git Commit Branch: HEAD
-UTC Build Time: 2018-06-29 11:43:51
-GoVersion: go version go1.10.3 darwin/amd64
-TiKV Min Version: 2.0.0-rc.4.1
-```",True,"tidb gives error while mysql gives warning when time is invalid - Please answer these questions before submitting your issue. Thanks!
-
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-
-```sql
-CREATE TABLE t1 (
- a INT,
- ts TIMESTAMP DEFAULT NOW(),
- PRIMARY KEY (ts)
- );
-SELECT * FROM t1 WHERE ts = '2008-12-31 23:59:60';
-```
-
-2. What did you expect to see?
-
-mysql:
-
-```
-mysql> SELECT * FROM t1 WHERE ts = '2008-12-31 23:59:60';
-Empty set, 2 warnings (0.00 sec)
-
-mysql> show warnings;
-+---------+------+--------------------------------------------------------------------------+
-| Level | Code | Message |
-+---------+------+--------------------------------------------------------------------------+
-| Warning | 1292 | Incorrect datetime value: '2008-12-31 23:59:60' for column 'ts' at row 1 |
-| Warning | 1292 | Incorrect datetime value: '2008-12-31 23:59:60' for column 'ts' at row 1 |
-+---------+------+--------------------------------------------------------------------------+
-2 rows in set (0.00 sec)
-```
-
-3. What did you see instead?
+
+
+
-tidb:
+***
+Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)",0,cve high detected in minimist tgz autoclosed cve high severity vulnerability vulnerable library minimist tgz parse argument options library home page a href path to dependency file package json path to vulnerable library node modules minimist package json dependency hierarchy babel loader tgz root library loader utils tgz tgz x minimist tgz vulnerable library found in head commit a href found in base branch master vulnerability details minimist is vulnerable to prototype pollution via file index js function setkey lines publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution bumperlane public service contracts prerelease cloudscribe templates virteom tenant mobile bluetooth prerelease showingvault dotnet sdk prerelease envisia dotnet templates yarnpkg yarn virteom tenant mobile framework uwp prerelease virteom tenant mobile framework ios prerelease bumperlane public api clientmodule prerelease vuejs netcore dianoga virteom tenant mobile bluetooth ios prerelease virteom public utilities prerelease indianadavy vuejswebapitemplate csharp nordron angulartemplate virteom tenant mobile framework prerelease virteom tenant mobile bluetooth android prerelease dotnet scaffold raml parser corevuewebtest dotnetng template sitecoremaster truedynamicplaceholders virteom tenant mobile framework android prerelease fable template elmish react blazorpolyfill build fable snowpack template bumperlane public api client prerelease yarn msbuild blazor tailwindcss bunit bridge aws tslint safe template gr pagerender razor midiator webclient step up your open source security game with whitesource ,0
+5073,3899915445.0,IssuesEvent,2016-04-18 01:01:20,lionheart/openradar-mirror,https://api.github.com/repos/lionheart/openradar-mirror,opened,12877313: Debugger line highlight is too light on dark backgrounds,classification:ui/usability reproducible:always,"#### Description
-```
-mysql> SELECT * FROM t1 WHERE ts = '2008-12-31 23:59:60';
-ERROR 1292 (22007): invalid time format: '60'
-```
+Summary:
+When using a font and colour theme that has a dark background, the debugger's line highlight does not adapt and as a result the text it's highlighting is difficult to read.
+Steps to Reproduce:
+1. Select a font and colour theme that has a black or dark background;
+2. Set a breakpoint somewhere in your code;
+3. Run the project, and trigger the breakpoint.
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+Expected Results:
+The line highlight colour adapts so that whatever is highlighted is still readable.
-```
-Release Version: v2.0.3
-Git Commit Hash: e4878329f0c69d7b810b8b40fb3b8071c69b5e02
-Git Commit Branch: HEAD
-UTC Build Time: 2018-06-29 11:43:51
-GoVersion: go version go1.10.3 darwin/amd64
-TiKV Min Version: 2.0.0-rc.4.1
-```",1,tidb gives error while mysql gives warning when time is invalid please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql create table a int ts timestamp default now primary key ts select from where ts what did you expect to see mysql mysql select from where ts empty set warnings sec mysql show warnings level code message warning incorrect datetime value for column ts at row warning incorrect datetime value for column ts at row rows in set sec what did you see instead tidb mysql select from where ts error invalid time format what version of tidb are you using tidb server v or run select tidb version on tidb release version git commit hash git commit branch head utc build time goversion go version darwin tikv min version rc ,1
-5094,7702926353.0,IssuesEvent,2018-05-21 05:59:49,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,inconsistent create table behavior when set timestamp col default value to 0,compatibility,"Please answer these questions before submitting your issue. Thanks!
+Actual Results:
+The line highlight colour is too light for the light coloured text, and it becomes difficult to read.
-1. What did you do?
-``` go
-create table t(a timestamp not null default 0);
-```
-2. What did you expect to see?
-``` go
-mysql(127.0.0.1)> create table t(a timestamp null default 0);
-ERROR 1067 (42000): Invalid default value for 'a'
-```
+Regression:
+This seems to have been a problem for at least a few major Xcode releases now.
+Notes:
+Example: http://cl.ly/image/1p0A2m1d2E2X
-3. What did you see instead?
-```go
-tidb(127.0.0.1)> create table t (a timestamp null default 0);
-Query OK, 0 rows affected (0.13 sec)
-```
+-
+Product Version: 4.6.x
+Created: 2012-12-13T21:43:48.625441
+Originated: 2016-04-18T00:00:00
+Open Radar Link: http://www.openradar.me/12877313",True,"12877313: Debugger line highlight is too light on dark backgrounds - #### Description
+Summary:
+When using a font and colour theme that has a dark background, the debugger's line highlight does not adapt and as a result the text it's highlighting is difficult to read.
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-```go
-tidb(127.0.0.1)> select tidb_version();
-+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v2.0.0-rc.3-12-gb6b708aa4
-Git Commit Hash: b6b708aa4369f89147a3f9a31a9daff38c489999
-Git Branch: master
-UTC Build Time: 2018-04-03 08:14:49
-GoVersion: go version go1.9.5 linux/amd64
-TiKV Min Version: 1.1.0-dev.2 |
-+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-```
-",True,"inconsistent create table behavior when set timestamp col default value to 0 - Please answer these questions before submitting your issue. Thanks!
+Steps to Reproduce:
+1. Select a font and colour theme that has a black or dark background;
+2. Set a breakpoint somewhere in your code;
+3. Run the project, and trigger the breakpoint.
-1. What did you do?
-``` go
-create table t(a timestamp not null default 0);
-```
+Expected Results:
+The line highlight colour adapts so that whatever is highlighted is still readable.
-2. What did you expect to see?
-``` go
-mysql(127.0.0.1)> create table t(a timestamp null default 0);
-ERROR 1067 (42000): Invalid default value for 'a'
-```
+Actual Results:
+The line highlight colour is too light for the light coloured text, and it becomes difficult to read.
-3. What did you see instead?
-```go
-tidb(127.0.0.1)> create table t (a timestamp null default 0);
-Query OK, 0 rows affected (0.13 sec)
-```
+Regression:
+This seems to have been a problem for at least a few major Xcode releases now.
+Notes:
+Example: http://cl.ly/image/1p0A2m1d2E2X
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-```go
-tidb(127.0.0.1)> select tidb_version();
-+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v2.0.0-rc.3-12-gb6b708aa4
-Git Commit Hash: b6b708aa4369f89147a3f9a31a9daff38c489999
-Git Branch: master
-UTC Build Time: 2018-04-03 08:14:49
-GoVersion: go version go1.9.5 linux/amd64
-TiKV Min Version: 1.1.0-dev.2 |
-+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-```
-",1,inconsistent create table behavior when set timestamp col default value to please answer these questions before submitting your issue thanks what did you do go create table t a timestamp not null default what did you expect to see go mysql create table t a timestamp null default error invalid default value for a what did you see instead go tidb create table t a timestamp null default query ok rows affected sec what version of tidb are you using tidb server v or run select tidb version on tidb go tidb select tidb version tidb version release version rc git commit hash git branch master utc build time goversion go version linux tikv min version dev ,1
-69114,14970070454.0,IssuesEvent,2021-01-27 19:04:02,jgeraigery/experian-java,https://api.github.com/repos/jgeraigery/experian-java,closed,CVE-2019-14893 (High) detected in jackson-databind-2.9.2.jar - autoclosed,security vulnerability,"## CVE-2019-14893 - High Severity Vulnerability
- Vulnerable Library - jackson-databind-2.9.2.jar
+-
+Product Version: 4.6.x
+Created: 2012-12-13T21:43:48.625441
+Originated: 2016-04-18T00:00:00
+Open Radar Link: http://www.openradar.me/12877313",0, debugger line highlight is too light on dark backgrounds description summary when using a font and colour theme that has a dark background the debugger s line highlight does not adapt and as a result the text it s highlighting is difficult to read steps to reproduce select a font and colour theme that has a black or dark background set a breakpoint somewhere in your code run the project and trigger the breakpoint expected results the line highlight colour adapts so that whatever is highlighted is still readable actual results the line highlight colour is too light for the light coloured text and it becomes difficult to read regression this seems to have been a problem for at least a few major xcode releases now notes example product version x created originated open radar link ,0
+16271,21897365190.0,IssuesEvent,2022-05-20 09:55:40,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Don't display `flen` in `show create table` for type `int`,compatibility-mysql8,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```
+create table t(a int);
+show create table t;
+```
+### 2. What did you expect to see? (Required)
+
+```
+mysql> show create table t;
++-------+--------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+--------------------------------------------------------------------------------------------------------------+
+| t | CREATE TABLE `t` (
+ `a` int DEFAULT NULL
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci |
++-------+--------------------------------------------------------------------------------------------------------------+
+```
+
+### 3. What did you see instead (Required)
+```
+mysql> show create table t;
++-------+--------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+--------------------------------------------------------------------------------------------------------------+
+| t | CREATE TABLE `t` (
+ `a` int(11) DEFAULT NULL
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci |
++-------+--------------------------------------------------------------------------------------------------------------+
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+
+",True,"Don't display `flen` in `show create table` for type `int` - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+
+```
+create table t(a int);
+show create table t;
+```
+### 2. What did you expect to see? (Required)
+
+```
+mysql> show create table t;
++-------+--------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+--------------------------------------------------------------------------------------------------------------+
+| t | CREATE TABLE `t` (
+ `a` int DEFAULT NULL
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci |
++-------+--------------------------------------------------------------------------------------------------------------+
+```
+
+### 3. What did you see instead (Required)
+```
+mysql> show create table t;
++-------+--------------------------------------------------------------------------------------------------------------+
+| Table | Create Table |
++-------+--------------------------------------------------------------------------------------------------------------+
+| t | CREATE TABLE `t` (
+ `a` int(11) DEFAULT NULL
+) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci |
++-------+--------------------------------------------------------------------------------------------------------------+
+```
+
+### 4. What is your TiDB version? (Required)
+
+
+
+",1,don t display flen in show create table for type int bug report please answer these questions before submitting your issue thanks minimal reproduce step required create table t a int show create table t what did you expect to see required mysql show create table t table create table t create table t a int default null engine innodb default charset collate ai ci what did you see instead required mysql show create table t table create table t create table t a int default null engine innodb default charset collate ai ci what is your tidb version required ,1
+14538,17629423369.0,IssuesEvent,2021-08-19 05:28:01,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,`extract` result incompatible with mysql ,type/bug type/compatibility sig/execution severity/critical,"## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+```sql
+select extract(hour_second from ""-838:59:59.00"");
+```
+
+
+### 2. What did you expect to see? (Required)
+```sql
+mysql> select extract(hour_second from ""-838:59:59.00"");
++-------------------------------------------+
+| extract(hour_second from ""-838:59:59.00"") |
++-------------------------------------------+
+| -8385959 |
++-------------------------------------------+
+1 row in set (0.22 sec)
+```
+### 3. What did you see instead (Required)
+```sql
+MySQL > select extract(hour_second from ""-838:59:59.00"");
++-------------------------------------------+
+| extract(hour_second from ""-838:59:59.00"") |
++-------------------------------------------+
+| 8385959 |
++-------------------------------------------+
+1 row in set
+Time: 0.051s
+```
+### 4. What is your TiDB version? (Required)
+v5.0.3, v4.0.14,
+master: da8bb5ea8c00bcbbb10afd0ae41a42fa
+release-5.2.0: 4c68defe055a7040280
+
+
+",True,"`extract` result incompatible with mysql - ## Bug Report
+
+Please answer these questions before submitting your issue. Thanks!
+
+### 1. Minimal reproduce step (Required)
+```sql
+select extract(hour_second from ""-838:59:59.00"");
+```
+
+
+### 2. What did you expect to see? (Required)
+```sql
+mysql> select extract(hour_second from ""-838:59:59.00"");
++-------------------------------------------+
+| extract(hour_second from ""-838:59:59.00"") |
++-------------------------------------------+
+| -8385959 |
++-------------------------------------------+
+1 row in set (0.22 sec)
+```
+### 3. What did you see instead (Required)
+```sql
+MySQL > select extract(hour_second from ""-838:59:59.00"");
++-------------------------------------------+
+| extract(hour_second from ""-838:59:59.00"") |
++-------------------------------------------+
+| 8385959 |
++-------------------------------------------+
+1 row in set
+Time: 0.051s
+```
+### 4. What is your TiDB version? (Required)
+v5.0.3, v4.0.14,
+master: da8bb5ea8c00bcbbb10afd0ae41a42fa
+release-5.2.0: 4c68defe055a7040280
+
+
+",1, extract result incompatible with mysql bug report please answer these questions before submitting your issue thanks minimal reproduce step required sql select extract hour second from what did you expect to see required sql mysql select extract hour second from extract hour second from row in set sec what did you see instead required sql mysql select extract hour second from extract hour second from row in set time what is your tidb version required master release ,1
+55425,14451298226.0,IssuesEvent,2020-12-08 10:46:36,NREL/EnergyPlus,https://api.github.com/repos/NREL/EnergyPlus,opened,Severe error calculated density of air is negative,Defect,"Issue overview
+--------------
+
+user reported on unmet hours that he got the following error:
+
+```
+** Severe ** PsyRhoAirFnPbTdbW: RhoAir (Density of Air) is calculated <= 0 [-9.04677].
+** ~~~ ** pb =[101100.00], tdb=[-312.09], w=[0.0000000].
+** ~~~ ** Routine=CorrectZoneHumRat, During Warmup, Environment=DSDAYTANGIER COOLING 0.4%, at Simulation time=08/21 00:12 - 00:13
+** Fatal ** Program terminates due to preceding condition.
+```
+
+user supplied the file, which was at E+ 8.7. I updated the file to v9.4 and instead of getting this severe I am getting an actual crash, which isn't something we want to happen, even if it is later found the defect file had problems.
+
+```
+Performing Zone Sizing Simulation
+...for Sizing Period: #1 DSDAYTANGIER COOLING 0.4%
+Warming up
+Warming up
+Warming up
+Performing Zone Sizing Simulation
+...for Sizing Period: #2 DSDAYTANGIER HEATING 99.6%
+Calculating System sizing
+...for Sizing Period: #1 DSDAYTANGIER COOLING 0.4%
+Calculating System sizing
+...for Sizing Period: #2 DSDAYTANGIER HEATING 99.6%
+Adjusting Air System Sizing
+Adjusting Standard 62.1 Ventilation Sizing
+Initializing Simulation
+double free or corruption (out)
+Aborted (core dumped)
+```
+
+
+### Details
+Some additional details for this issue (if relevant):
+ - Platform (Operating system, version)
+ - Version of EnergyPlus (if using an intermediate build, include SHA)
+ - Unmethours link: https://unmethours.com/question/49383/severe-error-calculated-density-of-air-is-negative/
+
+
+Backtrace
+
+```
+(lldb) bt
+* thread #1, name = 'energyplus', stop reason = hit program assert
+ frame #0: 0x00007ffff11c7fb7 libc.so.6`__GI_raise(sig=) at raise.c:51
+ frame #1: 0x00007ffff11c9921 libc.so.6`__GI_abort at abort.c:79
+ frame #2: 0x00007ffff11b948a libc.so.6`__assert_fail_base(fmt=""%s%s%s:%u: %s%sAssertion `%s' failed.\n%n"", assertion=""contains( i )"", file=""/home/julien/Software/Others/EnergyPlus/third_party/ObjexxFCL/src/ObjexxFCL/Array1.hh"", line=1172, function=""T& ObjexxFCL::Array1< >::operator()(int) [with T = EnergyPlus::WaterThermalTanks::StratifiedNodeData]"") at assert.c:92
+ frame #3: 0x00007ffff11b9502 libc.so.6`__GI___assert_fail(assertion=, file=, line=, function=) at assert.c:101
+ * frame #4: 0x00007ffff4d1a4b1 libenergyplusapi.so.9.4.0`ObjexxFCL::Array1::operator(this=0x00005555564ff530, i=0)(int) at Array1.hh:1172
+ frame #5: 0x00007ffff4cea195 libenergyplusapi.so.9.4.0`EnergyPlus::WaterThermalTanks::WaterThermalTankData::CalcWaterThermalTankStratified(this=0x00005555564ff100, state=0x00007fffffffbdf0) at WaterThermalTanks.cc:7218
+ frame #6: 0x00007ffff4d11882 libenergyplusapi.so.9.4.0`EnergyPlus::WaterThermalTanks::WaterThermalTankData::CalcStandardRatings(this=0x00005555564ff100, state=0x00007fffffffbdf0) at WaterThermalTanks.cc:11451
+ frame #7: 0x00007ffff4ce47d4 libenergyplusapi.so.9.4.0`EnergyPlus::WaterThermalTanks::WaterThermalTankData::initialize(this=0x00005555564ff100, state=0x00007fffffffbdf0, FirstHVACIteration=true) at WaterThermalTanks.cc:6183
+ frame #8: 0x00007ffff4c8c218 libenergyplusapi.so.9.4.0`EnergyPlus::WaterThermalTanks::WaterThermalTankData::onInitLoopEquip(this=0x00005555564ff100, state=0x00007fffffffbdf0, calledFromLocation=0x0000555555e45098) at WaterThermalTanks.cc:164
+ frame #9: 0x00007ffff5ffa702 libenergyplusapi.so.9.4.0`EnergyPlus::DataPlant::CompData::simulate(this=0x0000555555e44f00, state=0x00007fffffffbdf0, FirstHVACIteration=true, InitLoopEquip=0x00007ffff7d6fbdf, GetCompSizFac=true) at Component.cc:119
+ frame #10: 0x00007ffff5cf1f1a libenergyplusapi.so.9.4.0`EnergyPlus::PlantManager::InitializeLoops(state=0x00007fffffffbdf0, FirstHVACIteration=true) at PlantManager.cc:2204
+ frame #11: 0x00007ffff5cdbd1a libenergyplusapi.so.9.4.0`EnergyPlus::PlantManager::ManagePlantLoops(state=0x00007fffffffbdf0, FirstHVACIteration=true, SimAirLoops=0x00007ffff7d77439, SimZoneEquipment=0x00007ffff7d7743c, SimNonZoneEquipment=0x00007ffff7d7743d, SimPlantLoops=0x00007ffff7d7743b, SimElecCircuits=0x00007ffff7d7743a) at PlantManager.cc:222
+ frame #12: 0x00007ffff5827b00 libenergyplusapi.so.9.4.0`EnergyPlus::HVACManager::SimSelectedEquipment(state=0x00007fffffffbdf0, SimAirLoops=0x00007ffff7d77439, SimZoneEquipment=0x00007ffff7d7743c, SimNonZoneEquipment=0x00007ffff7d7743d, SimPlantLoops=0x00007ffff7d7743b, SimElecCircuits=0x00007ffff7d7743a, FirstHVACIteration=0x00007fffffffae2e, LockPlantFlows=false) at HVACManager.cc:1832
+ frame #13: 0x00007ffff581d054 libenergyplusapi.so.9.4.0`EnergyPlus::HVACManager::SimHVAC(state=0x00007fffffffbdf0) at HVACManager.cc:842
+ frame #14: 0x00007ffff58197f4 libenergyplusapi.so.9.4.0`EnergyPlus::HVACManager::ManageHVAC(state=0x00007fffffffbdf0) at HVACManager.cc:358
+ frame #15: 0x00007ffff5a1457a libenergyplusapi.so.9.4.0`EnergyPlus::HeatBalanceAirManager::CalcHeatBalanceAir(state=0x00007fffffffbdf0) at HeatBalanceAirManager.cc:4356
+ frame #16: 0x00007ffff59b9f7f libenergyplusapi.so.9.4.0`EnergyPlus::HeatBalanceAirManager::ManageAirHeatBalance(state=0x00007fffffffbdf0) at HeatBalanceAirManager.cc:204
+ frame #17: 0x00007ffff3e451ee libenergyplusapi.so.9.4.0`EnergyPlus::HeatBalanceSurfaceManager::ManageSurfaceHeatBalance(state=0x00007fffffffbdf0) at HeatBalanceSurfaceManager.cc:281
+ frame #18: 0x00007ffff5a33c72 libenergyplusapi.so.9.4.0`EnergyPlus::HeatBalanceManager::ManageHeatBalance(state=0x00007fffffffbdf0) at HeatBalanceManager.cc:363
+ frame #19: 0x00007ffff47f9269 libenergyplusapi.so.9.4.0`EnergyPlus::SimulationManager::SetupSimulation(state=0x00007fffffffbdf0, ErrorsFound=0x00007fffffffbc23) at SimulationManager.cc:2111
+ frame #20: 0x00007ffff47ea196 libenergyplusapi.so.9.4.0`EnergyPlus::SimulationManager::ManageSimulation(state=0x00007fffffffbdf0) at SimulationManager.cc:366
+ frame #21: 0x00007ffff3a08570 libenergyplusapi.so.9.4.0`RunEnergyPlus(state=0x00007fffffffbdf0, filepath=""\xe0\xbd\xff\xff\xff\U0000007f""...) at EnergyPlusPgm.cc:400
+ frame #22: 0x00007ffff3a07a17 libenergyplusapi.so.9.4.0`EnergyPlusPgm(state=0x00007fffffffbdf0, filepath=""\xe0\xbd\xff\xff\xff\U0000007f""...) at EnergyPlusPgm.cc:224
+ frame #23: 0x000055555578ef66 energyplus`main(argc=6, argv=0x00007fffffffccc8) at main.cc:60
+ frame #24: 0x00007ffff11aabf7 libc.so.6`__libc_start_main(main=(energyplus`main at main.cc:56), argc=6, argv=0x00007fffffffccc8, init=, fini=, rtld_fini=, stack_end=0x00007fffffffccb8) at libc-start.c:310
+ frame #25: 0x000055555578ec8a energyplus`_start + 42
+```
+
+
+### Checklist
+Add to this list or remove from it as applicable. This is a simple templated set of guidelines.
+ - [x] Defect file added (list location of defect file here)
+ - [ ] Ticket added to Pivotal for defect (development team task)
+ - [ ] Pull request created (the pull request will have additional tasks related to reviewing changes that fix this defect)
+
+",1.0,"Severe error calculated density of air is negative - Issue overview
+--------------
+
+user reported on unmet hours that he got the following error:
+
+```
+** Severe ** PsyRhoAirFnPbTdbW: RhoAir (Density of Air) is calculated <= 0 [-9.04677].
+** ~~~ ** pb =[101100.00], tdb=[-312.09], w=[0.0000000].
+** ~~~ ** Routine=CorrectZoneHumRat, During Warmup, Environment=DSDAYTANGIER COOLING 0.4%, at Simulation time=08/21 00:12 - 00:13
+** Fatal ** Program terminates due to preceding condition.
+```
+
+user supplied the file, which was at E+ 8.7. I updated the file to v9.4 and instead of getting this severe I am getting an actual crash, which isn't something we want to happen, even if it is later found the defect file had problems.
+
+```
+Performing Zone Sizing Simulation
+...for Sizing Period: #1 DSDAYTANGIER COOLING 0.4%
+Warming up
+Warming up
+Warming up
+Performing Zone Sizing Simulation
+...for Sizing Period: #2 DSDAYTANGIER HEATING 99.6%
+Calculating System sizing
+...for Sizing Period: #1 DSDAYTANGIER COOLING 0.4%
+Calculating System sizing
+...for Sizing Period: #2 DSDAYTANGIER HEATING 99.6%
+Adjusting Air System Sizing
+Adjusting Standard 62.1 Ventilation Sizing
+Initializing Simulation
+double free or corruption (out)
+Aborted (core dumped)
+```
+
+
+### Details
+Some additional details for this issue (if relevant):
+ - Platform (Operating system, version)
+ - Version of EnergyPlus (if using an intermediate build, include SHA)
+ - Unmethours link: https://unmethours.com/question/49383/severe-error-calculated-density-of-air-is-negative/
+
+
+Backtrace
+
+```
+(lldb) bt
+* thread #1, name = 'energyplus', stop reason = hit program assert
+ frame #0: 0x00007ffff11c7fb7 libc.so.6`__GI_raise(sig=) at raise.c:51
+ frame #1: 0x00007ffff11c9921 libc.so.6`__GI_abort at abort.c:79
+ frame #2: 0x00007ffff11b948a libc.so.6`__assert_fail_base(fmt=""%s%s%s:%u: %s%sAssertion `%s' failed.\n%n"", assertion=""contains( i )"", file=""/home/julien/Software/Others/EnergyPlus/third_party/ObjexxFCL/src/ObjexxFCL/Array1.hh"", line=1172, function=""T& ObjexxFCL::Array1< >::operator()(int) [with T = EnergyPlus::WaterThermalTanks::StratifiedNodeData]"") at assert.c:92
+ frame #3: 0x00007ffff11b9502 libc.so.6`__GI___assert_fail(assertion=, file=, line=, function=) at assert.c:101
+ * frame #4: 0x00007ffff4d1a4b1 libenergyplusapi.so.9.4.0`ObjexxFCL::Array1::operator(this=0x00005555564ff530, i=0)(int) at Array1.hh:1172
+ frame #5: 0x00007ffff4cea195 libenergyplusapi.so.9.4.0`EnergyPlus::WaterThermalTanks::WaterThermalTankData::CalcWaterThermalTankStratified(this=0x00005555564ff100, state=0x00007fffffffbdf0) at WaterThermalTanks.cc:7218
+ frame #6: 0x00007ffff4d11882 libenergyplusapi.so.9.4.0`EnergyPlus::WaterThermalTanks::WaterThermalTankData::CalcStandardRatings(this=0x00005555564ff100, state=0x00007fffffffbdf0) at WaterThermalTanks.cc:11451
+ frame #7: 0x00007ffff4ce47d4 libenergyplusapi.so.9.4.0`EnergyPlus::WaterThermalTanks::WaterThermalTankData::initialize(this=0x00005555564ff100, state=0x00007fffffffbdf0, FirstHVACIteration=true) at WaterThermalTanks.cc:6183
+ frame #8: 0x00007ffff4c8c218 libenergyplusapi.so.9.4.0`EnergyPlus::WaterThermalTanks::WaterThermalTankData::onInitLoopEquip(this=0x00005555564ff100, state=0x00007fffffffbdf0, calledFromLocation=0x0000555555e45098) at WaterThermalTanks.cc:164
+ frame #9: 0x00007ffff5ffa702 libenergyplusapi.so.9.4.0`EnergyPlus::DataPlant::CompData::simulate(this=0x0000555555e44f00, state=0x00007fffffffbdf0, FirstHVACIteration=true, InitLoopEquip=0x00007ffff7d6fbdf, GetCompSizFac=true) at Component.cc:119
+ frame #10: 0x00007ffff5cf1f1a libenergyplusapi.so.9.4.0`EnergyPlus::PlantManager::InitializeLoops(state=0x00007fffffffbdf0, FirstHVACIteration=true) at PlantManager.cc:2204
+ frame #11: 0x00007ffff5cdbd1a libenergyplusapi.so.9.4.0`EnergyPlus::PlantManager::ManagePlantLoops(state=0x00007fffffffbdf0, FirstHVACIteration=true, SimAirLoops=0x00007ffff7d77439, SimZoneEquipment=0x00007ffff7d7743c, SimNonZoneEquipment=0x00007ffff7d7743d, SimPlantLoops=0x00007ffff7d7743b, SimElecCircuits=0x00007ffff7d7743a) at PlantManager.cc:222
+ frame #12: 0x00007ffff5827b00 libenergyplusapi.so.9.4.0`EnergyPlus::HVACManager::SimSelectedEquipment(state=0x00007fffffffbdf0, SimAirLoops=0x00007ffff7d77439, SimZoneEquipment=0x00007ffff7d7743c, SimNonZoneEquipment=0x00007ffff7d7743d, SimPlantLoops=0x00007ffff7d7743b, SimElecCircuits=0x00007ffff7d7743a, FirstHVACIteration=0x00007fffffffae2e, LockPlantFlows=false) at HVACManager.cc:1832
+ frame #13: 0x00007ffff581d054 libenergyplusapi.so.9.4.0`EnergyPlus::HVACManager::SimHVAC(state=0x00007fffffffbdf0) at HVACManager.cc:842
+ frame #14: 0x00007ffff58197f4 libenergyplusapi.so.9.4.0`EnergyPlus::HVACManager::ManageHVAC(state=0x00007fffffffbdf0) at HVACManager.cc:358
+ frame #15: 0x00007ffff5a1457a libenergyplusapi.so.9.4.0`EnergyPlus::HeatBalanceAirManager::CalcHeatBalanceAir(state=0x00007fffffffbdf0) at HeatBalanceAirManager.cc:4356
+ frame #16: 0x00007ffff59b9f7f libenergyplusapi.so.9.4.0`EnergyPlus::HeatBalanceAirManager::ManageAirHeatBalance(state=0x00007fffffffbdf0) at HeatBalanceAirManager.cc:204
+ frame #17: 0x00007ffff3e451ee libenergyplusapi.so.9.4.0`EnergyPlus::HeatBalanceSurfaceManager::ManageSurfaceHeatBalance(state=0x00007fffffffbdf0) at HeatBalanceSurfaceManager.cc:281
+ frame #18: 0x00007ffff5a33c72 libenergyplusapi.so.9.4.0`EnergyPlus::HeatBalanceManager::ManageHeatBalance(state=0x00007fffffffbdf0) at HeatBalanceManager.cc:363
+ frame #19: 0x00007ffff47f9269 libenergyplusapi.so.9.4.0`EnergyPlus::SimulationManager::SetupSimulation(state=0x00007fffffffbdf0, ErrorsFound=0x00007fffffffbc23) at SimulationManager.cc:2111
+ frame #20: 0x00007ffff47ea196 libenergyplusapi.so.9.4.0`EnergyPlus::SimulationManager::ManageSimulation(state=0x00007fffffffbdf0) at SimulationManager.cc:366
+ frame #21: 0x00007ffff3a08570 libenergyplusapi.so.9.4.0`RunEnergyPlus(state=0x00007fffffffbdf0, filepath=""\xe0\xbd\xff\xff\xff\U0000007f""...) at EnergyPlusPgm.cc:400
+ frame #22: 0x00007ffff3a07a17 libenergyplusapi.so.9.4.0`EnergyPlusPgm(state=0x00007fffffffbdf0, filepath=""\xe0\xbd\xff\xff\xff\U0000007f""...) at EnergyPlusPgm.cc:224
+ frame #23: 0x000055555578ef66 energyplus`main(argc=6, argv=0x00007fffffffccc8) at main.cc:60
+ frame #24: 0x00007ffff11aabf7 libc.so.6`__libc_start_main(main=(energyplus`main at main.cc:56), argc=6, argv=0x00007fffffffccc8, init=, fini=, rtld_fini=, stack_end=0x00007fffffffccb8) at libc-start.c:310
+ frame #25: 0x000055555578ec8a energyplus`_start + 42
+```
+
+
+### Checklist
+Add to this list or remove from it as applicable. This is a simple templated set of guidelines.
+ - [x] Defect file added (list location of defect file here)
+ - [ ] Ticket added to Pivotal for defect (development team task)
+ - [ ] Pull request created (the pull request will have additional tasks related to reviewing changes that fix this defect)
+
+",0,severe error calculated density of air is negative issue overview user reported on unmet hours that he got the following error severe psyrhoairfnpbtdbw rhoair density of air is calculated pb tdb w routine correctzonehumrat during warmup environment dsdaytangier cooling at simulation time fatal program terminates due to preceding condition user supplied the file which was at e i updated the file to and instead of getting this severe i am getting an actual crash which isn t something we want to happen even if it is later found the defect file had problems performing zone sizing simulation for sizing period dsdaytangier cooling warming up warming up warming up performing zone sizing simulation for sizing period dsdaytangier heating calculating system sizing for sizing period dsdaytangier cooling calculating system sizing for sizing period dsdaytangier heating adjusting air system sizing adjusting standard ventilation sizing initializing simulation double free or corruption out aborted core dumped details some additional details for this issue if relevant platform operating system version version of energyplus if using an intermediate build include sha unmethours link backtrace lldb bt thread name energyplus stop reason hit program assert frame libc so gi raise sig at raise c frame libc so gi abort at abort c frame libc so assert fail base fmt s s s u s sassertion s failed n n assertion contains i file home julien software others energyplus third party objexxfcl src objexxfcl hh line function t objexxfcl operator int at assert c frame libc so gi assert fail assertion file line function at assert c frame libenergyplusapi so objexxfcl operator this i int at hh frame libenergyplusapi so energyplus waterthermaltanks waterthermaltankdata calcwaterthermaltankstratified this state at waterthermaltanks cc frame libenergyplusapi so energyplus waterthermaltanks waterthermaltankdata calcstandardratings this state at waterthermaltanks cc frame libenergyplusapi so energyplus waterthermaltanks waterthermaltankdata initialize this state firsthvaciteration true at waterthermaltanks cc frame libenergyplusapi so energyplus waterthermaltanks waterthermaltankdata oninitloopequip this state calledfromlocation at waterthermaltanks cc frame libenergyplusapi so energyplus dataplant compdata simulate this state firsthvaciteration true initloopequip getcompsizfac true at component cc frame libenergyplusapi so energyplus plantmanager initializeloops state firsthvaciteration true at plantmanager cc frame libenergyplusapi so energyplus plantmanager manageplantloops state firsthvaciteration true simairloops simzoneequipment simnonzoneequipment simplantloops simeleccircuits at plantmanager cc frame libenergyplusapi so energyplus hvacmanager simselectedequipment state simairloops simzoneequipment simnonzoneequipment simplantloops simeleccircuits firsthvaciteration lockplantflows false at hvacmanager cc frame libenergyplusapi so energyplus hvacmanager simhvac state at hvacmanager cc frame libenergyplusapi so energyplus hvacmanager managehvac state at hvacmanager cc frame libenergyplusapi so energyplus heatbalanceairmanager calcheatbalanceair state at heatbalanceairmanager cc frame libenergyplusapi so energyplus heatbalanceairmanager manageairheatbalance state at heatbalanceairmanager cc frame libenergyplusapi so energyplus heatbalancesurfacemanager managesurfaceheatbalance state at heatbalancesurfacemanager cc frame libenergyplusapi so energyplus heatbalancemanager manageheatbalance state at heatbalancemanager cc frame libenergyplusapi so energyplus simulationmanager setupsimulation state errorsfound at simulationmanager cc frame libenergyplusapi so energyplus simulationmanager managesimulation state at simulationmanager cc frame libenergyplusapi so runenergyplus state filepath xbd xff xff xff at energypluspgm cc frame libenergyplusapi so energypluspgm state filepath xbd xff xff xff at energypluspgm cc frame energyplus main argc argv at main cc frame libc so libc start main main energyplus main at main cc argc argv init fini rtld fini stack end at libc start c frame energyplus start checklist add to this list or remove from it as applicable this is a simple templated set of guidelines defect file added list location of defect file here ticket added to pivotal for defect development team task pull request created the pull request will have additional tasks related to reviewing changes that fix this defect ,0
+59318,14379592715.0,IssuesEvent,2020-12-02 00:43:37,gate5/react-16.0.0,https://api.github.com/repos/gate5/react-16.0.0,opened,CVE-2019-3859 (High) detected in https://source.codeaurora.org/quic/qsdk/libssh2/libssh2-1.7.0,security vulnerability,"## CVE-2019-3859 - High Severity Vulnerability
+ Vulnerable Library - https://source.codeaurora.org/quic/qsdk/libssh2/libssh2-1.7.0
+
-
General data-binding functionality for Jackson: works on core streaming API
-A flaw was discovered in FasterXML jackson-databind in all versions before 2.9.10 and 2.10.0, where it would permit polymorphic deserialization of malicious objects using the xalan JNDI gadget when used in conjunction with polymorphic type handling methods such as `enableDefaultTyping()` or when @JsonTypeInfo is using `Id.CLASS` or `Id.MINIMAL_CLASS` or in any other way which ObjectMapper.readValue might instantiate objects from unsafe sources. An attacker could use this flaw to execute arbitrary code.
+An out of bounds read flaw was discovered in libssh2 before 1.8.1 in the _libssh2_packet_require and _libssh2_packet_requirev functions. A remote attacker who compromises a SSH server may be able to cause a Denial of Service or read data in the client memory.
-
+",True,"CVE-2019-3859 (High) detected in https://source.codeaurora.org/quic/qsdk/libssh2/libssh2-1.7.0 - ## CVE-2019-3859 - High Severity Vulnerability
+ Vulnerable Library - https://source.codeaurora.org/quic/qsdk/libssh2/libssh2-1.7.0
+
-***
-:rescue_worker_helmet: Automatic Remediation is available for this issue
-",True,"CVE-2019-14893 (High) detected in jackson-databind-2.9.2.jar - autoclosed - ## CVE-2019-14893 - High Severity Vulnerability
- Vulnerable Library - jackson-databind-2.9.2.jar
-
-
General data-binding functionality for Jackson: works on core streaming API
-A flaw was discovered in FasterXML jackson-databind in all versions before 2.9.10 and 2.10.0, where it would permit polymorphic deserialization of malicious objects using the xalan JNDI gadget when used in conjunction with polymorphic type handling methods such as `enableDefaultTyping()` or when @JsonTypeInfo is using `Id.CLASS` or `Id.MINIMAL_CLASS` or in any other way which ObjectMapper.readValue might instantiate objects from unsafe sources. An attacker could use this flaw to execute arbitrary code.
+An out of bounds read flaw was discovered in libssh2 before 1.8.1 in the _libssh2_packet_require and _libssh2_packet_requirev functions. A remote attacker who compromises a SSH server may be able to cause a Denial of Service or read data in the client memory.
-
+",0,cve high detected in cve high severity vulnerability vulnerable library library home page a href found in head commit a href vulnerable source files react scripts bench node modules nodegit vendor src session c react scripts bench node modules nodegit vendor src session c react scripts bench node modules nodegit vendor src session c vulnerability details an out of bounds read flaw was discovered in before in the packet require and packet requirev functions a remote attacker who compromises a ssh server may be able to cause a denial of service or read data in the client memory publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution ,0
+4044,6889458636.0,IssuesEvent,2017-11-22 10:26:37,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,Check the index validity when executing `use index ...`,compatibility help wanted,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+create table tt(a int);
+select count(*) from tt use index (idx);
+```
+
+2. What did you expect to see?
+```
+mysql> select count(*) from tt use index (idx);
+ERROR 1176 (42000): Key 'idx' doesn't exist in table 'tt'
+```
+
+
+3. What did you see instead?
+```
+tidb> select count(*) from tt use index (idx);
++----------+
+| count(*) |
++----------+
+| 0 |
++----------+
+1 row in set (0.00 sec)
+```
+
+",True,"Check the index validity when executing `use index ...` - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+```
+create table tt(a int);
+select count(*) from tt use index (idx);
+```
+
+2. What did you expect to see?
+```
+mysql> select count(*) from tt use index (idx);
+ERROR 1176 (42000): Key 'idx' doesn't exist in table 'tt'
+```
+
+
+3. What did you see instead?
+```
+tidb> select count(*) from tt use index (idx);
++----------+
+| count(*) |
++----------+
+| 0 |
++----------+
+1 row in set (0.00 sec)
+```
+
+",1,check the index validity when executing use index please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error create table tt a int select count from tt use index idx what did you expect to see mysql select count from tt use index idx error key idx doesn t exist in table tt what did you see instead tidb select count from tt use index idx count row in set sec ,1
+48478,12199122032.0,IssuesEvent,2020-04-30 00:41:35,kwk/test-llvm-bz-import-5,https://api.github.com/repos/kwk/test-llvm-bz-import-5,opened,recipe for target all failed on i686-pc-cygwin on Vista 32bit with Cygwin,BZ-BUG-STATUS: NEW Build scripts/Makefiles dummy import from bugzilla,This issue was imported from Bugzilla https://bugs.llvm.org/show_bug.cgi?id=15862.,1.0,recipe for target all failed on i686-pc-cygwin on Vista 32bit with Cygwin - This issue was imported from Bugzilla https://bugs.llvm.org/show_bug.cgi?id=15862.,0,recipe for target all failed on pc cygwin on vista with cygwin this issue was imported from bugzilla ,0
+5687,8150356247.0,IssuesEvent,2018-08-22 12:45:05,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,blob/text/int length isn't accuracy in columnm metadata,help wanted type/compatibility,"1. What did you do?
+
+connection tidb with `--column-type-info`
+
+```
+create table bitest(b blob(2));
+select * from bitest;
+```
+
+2. What did you expect to see?
+
+```
+Length: 255
+```
+
+3. What did you see instead?
+
+```
+Length: 8
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+2.0.6
+```
+
+ref #7463 ",True,"blob/text/int length isn't accuracy in columnm metadata - 1. What did you do?
+
+connection tidb with `--column-type-info`
+
+```
+create table bitest(b blob(2));
+select * from bitest;
+```
+
+2. What did you expect to see?
+
+```
+Length: 255
+```
+
+3. What did you see instead?
+
+```
+Length: 8
+```
+
+4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
+
+```
+2.0.6
+```
+
+ref #7463 ",1,blob text int length isn t accuracy in columnm metadata what did you do connection tidb with column type info create table bitest b blob select from bitest what did you expect to see length what did you see instead length what version of tidb are you using tidb server v or run select tidb version on tidb ref ,1
+3650,6529459085.0,IssuesEvent,2017-08-30 11:45:07,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,builtin HOUR() compability.,compatibility,"MySQL:
+
+```
+mysql> SELECT HOUR('9999999:59:59');
++-----------------------+
+| HOUR('9999999:59:59') |
++-----------------------+
+| 838 |
++-----------------------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> show warnings;
++---------+------+-------------------------------------------------+
+| Level | Code | Message |
++---------+------+-------------------------------------------------+
+| Warning | 1292 | Truncated incorrect time value: '9999999:59:59' |
++---------+------+-------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+TiDB:
+
+```
+mysql> SELECT HOUR('9999999:59:59');
++-----------------------+
+| HOUR('9999999:59:59') |
++-----------------------+
+| NULL |
++-----------------------+
+1 row in set (0.00 sec)
+```",True,"builtin HOUR() compability. - MySQL:
+
+```
+mysql> SELECT HOUR('9999999:59:59');
++-----------------------+
+| HOUR('9999999:59:59') |
++-----------------------+
+| 838 |
++-----------------------+
+1 row in set, 1 warning (0.00 sec)
+
+mysql> show warnings;
++---------+------+-------------------------------------------------+
+| Level | Code | Message |
++---------+------+-------------------------------------------------+
+| Warning | 1292 | Truncated incorrect time value: '9999999:59:59' |
++---------+------+-------------------------------------------------+
+1 row in set (0.00 sec)
+```
+
+TiDB:
+
+```
+mysql> SELECT HOUR('9999999:59:59');
++-----------------------+
+| HOUR('9999999:59:59') |
++-----------------------+
+| NULL |
++-----------------------+
+1 row in set (0.00 sec)
+```",1,builtin hour compability mysql mysql select hour hour row in set warning sec mysql show warnings level code message warning truncated incorrect time value row in set sec tidb mysql select hour hour null row in set sec ,1
+834,2516543687.0,IssuesEvent,2015-01-16 04:53:50,ars096/forest,https://api.github.com/repos/ars096/forest,closed,rxrot : Check the cosmos limit is working,test,"forest/rxrot
+Check the COSMOS limit is working good.",1.0,"rxrot : Check the cosmos limit is working - forest/rxrot
+Check the COSMOS limit is working good.",0,rxrot check the cosmos limit is working forest rxrot check the cosmos limit is working good ,0
+4824,7445370429.0,IssuesEvent,2018-03-28 04:05:34,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,check invalid charset when create database.,DDL compatibility help wanted todo,"MySQL:
+
+```
+mysql> create database test1 character set uft8;
+ERROR 1115 (42000): Unknown character set: 'uft8'
+```
+
+TiDB:
+
+```
+mysql> create database test1 character set uft8;
+Query OK, 0 rows affected (0.08 sec)
+
+mysql> show create database test1;
++----------+-----------------------------------------------------------------+
+| Database | Create Database |
++----------+-----------------------------------------------------------------+
+| test1 | CREATE DATABASE `test1` /* !40100 DEFAULT CHARACTER SET uft8 */ |
++----------+-----------------------------------------------------------------+
+1 row in set (0.00 sec)
+```",True,"check invalid charset when create database. - MySQL:
+
+```
+mysql> create database test1 character set uft8;
+ERROR 1115 (42000): Unknown character set: 'uft8'
+```
+
+TiDB:
+
+```
+mysql> create database test1 character set uft8;
+Query OK, 0 rows affected (0.08 sec)
+
+mysql> show create database test1;
++----------+-----------------------------------------------------------------+
+| Database | Create Database |
++----------+-----------------------------------------------------------------+
+| test1 | CREATE DATABASE `test1` /* !40100 DEFAULT CHARACTER SET uft8 */ |
++----------+-----------------------------------------------------------------+
+1 row in set (0.00 sec)
+```",1,check invalid charset when create database mysql mysql create database character set error unknown character set tidb mysql create database character set query ok rows affected sec mysql show create database database create database create database default character set row in set sec ,1
+3711,6564638315.0,IssuesEvent,2017-09-08 03:04:16,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,opened,Arithmetic results are not consistent with MySQL when overflow occurs,compatibility,"Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+SET @a:=999999999999999;
+select @a + @a; -- 1999999999999998
+SET @a:=9999999999999999;
+select @a + @a; -- 20000000000000000
+SET @a:=99999999999999999;
+select @a + @a; -- 20000000000000000
+select @a * @a; -- 1000000000000000000000000000000000000
+SELECT -@a - @a; -- -2000000000000000000
+SELECT @a / 0.5; -- 2000000000000000000
+```
+
+2. What did you expect to see?
+
+```
+@a + @a
+1999999999999998
+@a + @a
+19999999999999998
+@a + @a
+199999999999999998
+ERROR 1690 (22003) at line 7: BIGINT value is out of range in '((@`a`) * (@`a`))'
+-@a - @a
+-199999999999999998
+@a / 0.5
+199999999999999998.0000
+```
+
+3. What did you see instead?
+
+```
+@a + @a
+1999999999999998
+@a + @a
+20000000000000000
+@a + @a
+200000000000000000
+@a * @a
+10000000000000000000000000000000000
+-@a - @a
+-200000000000000000
+@a / 0.5
+200000000000000000
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",True,"Arithmetic results are not consistent with MySQL when overflow occurs - Please answer these questions before submitting your issue. Thanks!
+
+1. What did you do?
+If possible, provide a recipe for reproducing the error.
+
+```sql
+SET @a:=999999999999999;
+select @a + @a; -- 1999999999999998
+SET @a:=9999999999999999;
+select @a + @a; -- 20000000000000000
+SET @a:=99999999999999999;
+select @a + @a; -- 20000000000000000
+select @a * @a; -- 1000000000000000000000000000000000000
+SELECT -@a - @a; -- -2000000000000000000
+SELECT @a / 0.5; -- 2000000000000000000
+```
+
+2. What did you expect to see?
+
+```
+@a + @a
+1999999999999998
+@a + @a
+19999999999999998
+@a + @a
+199999999999999998
+ERROR 1690 (22003) at line 7: BIGINT value is out of range in '((@`a`) * (@`a`))'
+-@a - @a
+-199999999999999998
+@a / 0.5
+199999999999999998.0000
+```
+
+3. What did you see instead?
+
+```
+@a + @a
+1999999999999998
+@a + @a
+20000000000000000
+@a + @a
+200000000000000000
+@a * @a
+10000000000000000000000000000000000
+-@a - @a
+-200000000000000000
+@a / 0.5
+200000000000000000
+```
+
+4. What version of TiDB are you using (`tidb-server -V`)?
+
+",1,arithmetic results are not consistent with mysql when overflow occurs please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error sql set a select a a set a select a a set a select a a select a a select a a select a what did you expect to see a a a a a a error at line bigint value is out of range in a a a a a what did you see instead a a a a a a a a a a a what version of tidb are you using tidb server v ,1
+113018,11785331063.0,IssuesEvent,2020-03-17 10:06:47,oemof/oemof,https://api.github.com/repos/oemof/oemof,closed,Broken apidocs of tools.economics.annuity,bug documentation,"The api reference of tools.economics annuity is broken. Some text about DSM appears, which is strange.
+
+https://oemof.readthedocs.io/en/features-add_nonconvexinvestmentflow/api/oemof.tools.html#oemof.tools.economics.annuity
+
+ It might have to do with the missing indent of the math sections.",1.0,"Broken apidocs of tools.economics.annuity - The api reference of tools.economics annuity is broken. Some text about DSM appears, which is strange.
+
+https://oemof.readthedocs.io/en/features-add_nonconvexinvestmentflow/api/oemof.tools.html#oemof.tools.economics.annuity
+
+ It might have to do with the missing indent of the math sections.",0,broken apidocs of tools economics annuity the api reference of tools economics annuity is broken some text about dsm appears which is strange it might have to do with the missing indent of the math sections ,0
+431609,30242795370.0,IssuesEvent,2023-07-06 14:31:15,tusharparimi/audio-control,https://api.github.com/repos/tusharparimi/audio-control,opened,pybluez in windows,documentation,"- for detecting button presses on bluetooth headphones
+- in windows does not have support for L2CAP protocol which my headphones use for AVRCP(bluetooth profile for Audio/Video Remote Control)
+- RFCOMM is only protocol supported in windows which my bluetooth uses for headset connection service. This was seen to detect some button presses.
+- Another problem is headphones need to make a new connection if they are aready connected to laptop it does not work.",1.0,"pybluez in windows - - for detecting button presses on bluetooth headphones
+- in windows does not have support for L2CAP protocol which my headphones use for AVRCP(bluetooth profile for Audio/Video Remote Control)
+- RFCOMM is only protocol supported in windows which my bluetooth uses for headset connection service. This was seen to detect some button presses.
+- Another problem is headphones need to make a new connection if they are aready connected to laptop it does not work.",0,pybluez in windows for detecting button presses on bluetooth headphones in windows does not have support for protocol which my headphones use for avrcp bluetooth profile for audio video remote control rfcomm is only protocol supported in windows which my bluetooth uses for headset connection service this was seen to detect some button presses another problem is headphones need to make a new connection if they are aready connected to laptop it does not work ,0
+785983,27630244886.0,IssuesEvent,2023-03-10 10:17:07,Avaiga/taipy-gui,https://api.github.com/repos/Avaiga/taipy-gui,closed,Dynamic property for traces - Charts,📈 Improvement Gui: Back-End 🟧 Priority: High,"**Description**
+Sometimes, the number of traces in a Dataframe is not known. Thus, it is compulsory to create a Partial to handle it. It is making it a bit complex to use charts this way. The goal would be to simplify this use case of charts.
+
+**Acceptance Criteria**
+- [ ] Ensure new code is unit tested, and check code coverage is at least 90%
+- [ ] Propagate any change on the demos and run all of them to ensure there is no breaking change
+- [ ] Ensure any change is well documented
+",1.0,"Dynamic property for traces - Charts - **Description**
+Sometimes, the number of traces in a Dataframe is not known. Thus, it is compulsory to create a Partial to handle it. It is making it a bit complex to use charts this way. The goal would be to simplify this use case of charts.
+
+**Acceptance Criteria**
+- [ ] Ensure new code is unit tested, and check code coverage is at least 90%
+- [ ] Propagate any change on the demos and run all of them to ensure there is no breaking change
+- [ ] Ensure any change is well documented
+",0,dynamic property for traces charts description sometimes the number of traces in a dataframe is not known thus it is compulsory to create a partial to handle it it is making it a bit complex to use charts this way the goal would be to simplify this use case of charts acceptance criteria ensure new code is unit tested and check code coverage is at least propagate any change on the demos and run all of them to ensure there is no breaking change ensure any change is well documented ,0
+32896,12151966017.0,IssuesEvent,2020-04-24 21:06:00,LevyForchh/karate,https://api.github.com/repos/LevyForchh/karate,opened,CVE-2020-10672 (High) detected in multiple libraries,security vulnerability,"## CVE-2020-10672 - High Severity Vulnerability
+ Vulnerable Libraries - jackson-databind-2.8.5.jar, jackson-databind-2.9.8.jar, jackson-databind-2.8.8.jar
+
-***
-:rescue_worker_helmet: Automatic Remediation is available for this issue
-",0,cve high detected in jackson databind jar autoclosed cve high severity vulnerability vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file experian java mavenworkspace bis services lib bis services base pom xml path to vulnerable library canner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a flaw was discovered in fasterxml jackson databind in all versions before and where it would permit polymorphic deserialization of malicious objects using the xalan jndi gadget when used in conjunction with polymorphic type handling methods such as enabledefaulttyping or when jsontypeinfo is using id class or id minimal class or in any other way which objectmapper readvalue might instantiate objects from unsafe sources an attacker could use this flaw to execute arbitrary code publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind rescue worker helmet automatic remediation is available for this issue isopenpronvulnerability true ispackagebased true isdefaultbranch true packages vulnerabilityidentifier cve vulnerabilitydetails a flaw was discovered in fasterxml jackson databind in all versions before and where it would permit polymorphic deserialization of malicious objects using the xalan jndi gadget when used in conjunction with polymorphic type handling methods such as enabledefaulttyping or when jsontypeinfo is using id class or id minimal class or in any other way which objectmapper readvalue might instantiate objects from unsafe sources an attacker could use this flaw to execute arbitrary code vulnerabilityurl ,0
-7028,9305281659.0,IssuesEvent,2019-03-25 05:47:18,pingcap/tidb,https://api.github.com/repos/pingcap/tidb,closed,`TIME_FORMAT` is not compatible with MySQL,for new contributors help wanted type/bug type/compatibility,"## Bug Report
-
-Please answer these questions before submitting your issue. Thanks!
+jackson-databind-2.8.5.jar
-1. What did you do?
-If possible, provide a recipe for reproducing the error.
-```
-SELECT TIME_FORMAT(""24:00:00"", '%r');
-SELECT TIME_FORMAT(""25:00:00"", '%r');
-SELECT TIME_FORMAT(""24:00:00"", '%l %p');
-```
+
General data-binding functionality for Jackson: works on core streaming API
Path to dependency file: /tmp/ws-scm/karate/examples/jobserver/build.gradle
+
Path to vulnerable library: /root/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.8.5/b3035f37e674c04dafe36a660c3815cc59f764e2/jackson-databind-2.8.5.jar,/root/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.8.5/b3035f37e674c04dafe36a660c3815cc59f764e2/jackson-databind-2.8.5.jar
+
-2. What did you expect to see?
-In Mysql
-```
-mysql> SELECT TIME_FORMAT(""24:00:00"", '%r');
-+-------------------------------+
-| TIME_FORMAT(""24:00:00"", '%r') |
-+-------------------------------+
-| 12:00:00 AM |
-+-------------------------------+
-1 row in set (0.00 sec)
-
-mysql> SELECT TIME_FORMAT(""25:00:00"", '%r');
-+-------------------------------+
-| TIME_FORMAT(""25:00:00"", '%r') |
-+-------------------------------+
-| 01:00:00 AM |
-+-------------------------------+
-1 row in set (0.00 sec)
-
-mysql> SELECT TIME_FORMAT(""24:00:00"", '%l %p');
-+----------------------------------+
-| TIME_FORMAT(""24:00:00"", '%l %p') |
-+----------------------------------+
-| 12 AM |
-+----------------------------------+
-1 row in set (0.00 sec)
-```
+Dependency Hierarchy:
+ - cucumber-reporting-3.8.0.jar (Root Library)
+ - :x: **jackson-databind-2.8.5.jar** (Vulnerable Library)
+
+jackson-databind-2.9.8.jar
+
General data-binding functionality for Jackson: works on core streaming API
Path to dependency file: /tmp/ws-scm/karate/examples/gatling/build.gradle
+
Path to vulnerable library: /tmp/ws-ua_20200424203206/downloadResource_81a2693a-3427-4530-b432-dc290b928912/20200424203251/jackson-databind-2.9.8.jar,/tmp/ws-ua_20200424203206/downloadResource_81a2693a-3427-4530-b432-dc290b928912/20200424203251/jackson-databind-2.9.8.jar
+
-3. What did you see instead?
-In TiDB
-```
-mysql> SELECT TIME_FORMAT(""24:00:00"", '%r');
-+-------------------------------+
-| TIME_FORMAT(""24:00:00"", '%r') |
-+-------------------------------+
-| 12:00:00 PM |
-+-------------------------------+
-1 row in set (0.00 sec)
-
-mysql> SELECT TIME_FORMAT(""25:00:00"", '%r');
-+-------------------------------+
-| TIME_FORMAT(""25:00:00"", '%r') |
-+-------------------------------+
-| 13:00:00 PM |
-+-------------------------------+
-1 row in set (0.00 sec)
-
-mysql> SELECT TIME_FORMAT(""24:00:00"", '%l %p');
-+----------------------------------+
-| TIME_FORMAT(""24:00:00"", '%l %p') |
-+----------------------------------+
-| 0 AM |
-+----------------------------------+
-1 row in set (0.00 sec)
-```
+Dependency Hierarchy:
+ - karate-gatling-0.9.5.jar (Root Library)
+ - gatling-charts-highcharts-3.0.2.jar
+ - gatling-charts-3.0.2.jar
+ - gatling-core-3.0.2.jar
+ - :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
+
+jackson-databind-2.8.8.jar
+
General data-binding functionality for Jackson: works on core streaming API
Path to dependency file: /tmp/ws-scm/karate/karate-demo/build.gradle
+
Path to vulnerable library: /root/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.8.8/bf88c7b27e95cbadce4e7c316a56c3efffda8026/jackson-databind-2.8.8.jar,/root/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.8.8/bf88c7b27e95cbadce4e7c316a56c3efffda8026/jackson-databind-2.8.8.jar
+
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-```
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v3.0.0-beta-227-g06183393e-dirty
-Git Commit Hash: 06183393ed536aa248248b72d4bf9f5010947f66
-Git Branch: master
-UTC Build Time: 2019-03-15 08:22:53
-GoVersion: go version go1.12 darwin/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false |
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-```
+Dependency Hierarchy:
+ - spring-boot-starter-web-1.5.3.RELEASE.jar (Root Library)
+ - :x: **jackson-databind-2.8.8.jar** (Vulnerable Library)
+
-",True,"`TIME_FORMAT` is not compatible with MySQL - ## Bug Report
+
+
+FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.aries.transaction.jms.internal.XaPooledConnectionFactory (aka aries.transaction.jms).
-Please answer these questions before submitting your issue. Thanks!
+
+
+
+
-3. What did you see instead?
-In TiDB
-```
-mysql> SELECT TIME_FORMAT(""24:00:00"", '%r');
-+-------------------------------+
-| TIME_FORMAT(""24:00:00"", '%r') |
-+-------------------------------+
-| 12:00:00 PM |
-+-------------------------------+
-1 row in set (0.00 sec)
-
-mysql> SELECT TIME_FORMAT(""25:00:00"", '%r');
-+-------------------------------+
-| TIME_FORMAT(""25:00:00"", '%r') |
-+-------------------------------+
-| 13:00:00 PM |
-+-------------------------------+
-1 row in set (0.00 sec)
-
-mysql> SELECT TIME_FORMAT(""24:00:00"", '%l %p');
-+----------------------------------+
-| TIME_FORMAT(""24:00:00"", '%l %p') |
-+----------------------------------+
-| 0 AM |
-+----------------------------------+
-1 row in set (0.00 sec)
-```
+",True,"CVE-2020-10672 (High) detected in multiple libraries - ## CVE-2020-10672 - High Severity Vulnerability
+ Vulnerable Libraries - jackson-databind-2.8.5.jar, jackson-databind-2.9.8.jar, jackson-databind-2.8.8.jar
+
+jackson-databind-2.8.5.jar
-4. What version of TiDB are you using (`tidb-server -V` or run `select tidb_version();` on TiDB)?
-```
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| tidb_version() |
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-| Release Version: v3.0.0-beta-227-g06183393e-dirty
-Git Commit Hash: 06183393ed536aa248248b72d4bf9f5010947f66
-Git Branch: master
-UTC Build Time: 2019-03-15 08:22:53
-GoVersion: go version go1.12 darwin/amd64
-Race Enabled: false
-TiKV Min Version: 2.1.0-alpha.1-ff3dd160846b7d1aed9079c389fc188f7f5ea13e
-Check Table Before Drop: false |
-+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
-```
+
General data-binding functionality for Jackson: works on core streaming API
Path to dependency file: /tmp/ws-scm/karate/examples/jobserver/build.gradle
+
Path to vulnerable library: /root/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.8.5/b3035f37e674c04dafe36a660c3815cc59f764e2/jackson-databind-2.8.5.jar,/root/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.8.5/b3035f37e674c04dafe36a660c3815cc59f764e2/jackson-databind-2.8.5.jar
+
-",1, time format is not compatible with mysql bug report please answer these questions before submitting your issue thanks what did you do if possible provide a recipe for reproducing the error select time format r select time format r select time format l p what did you expect to see in mysql mysql select time format r time format r am row in set sec mysql select time format r time format r am row in set sec mysql select time format l p time format l p am row in set sec what did you see instead in tidb mysql select time format r time format r pm row in set sec mysql select time format r time format r pm row in set sec mysql select time format l p time format l p am row in set sec what version of tidb are you using tidb server v or run select tidb version on tidb tidb version release version beta dirty git commit hash git branch master utc build time goversion go version darwin race enabled false tikv min version alpha check table before drop false ,1
-563355,16681158968.0,IssuesEvent,2021-06-08 00:02:47,ThePyrotechnic/rocketleague-spotify,https://api.github.com/repos/ThePyrotechnic/rocketleague-spotify,closed,Authenticate with the user's Steam account,high priority,"In order to release publicly, the API must implement the [Steam OpenID flow](https://partner.steamgames.com/doc/features/auth#website) in order to authenticate all API calls and prevent users from altering each other's settings.",1.0,"Authenticate with the user's Steam account - In order to release publicly, the API must implement the [Steam OpenID flow](https://partner.steamgames.com/doc/features/auth#website) in order to authenticate all API calls and prevent users from altering each other's settings.",0,authenticate with the user s steam account in order to release publicly the api must implement the in order to authenticate all api calls and prevent users from altering each other s settings ,0
-183023,31141929913.0,IssuesEvent,2023-08-16 01:14:41,MetaMask/metamask-extension,https://api.github.com/repos/MetaMask/metamask-extension,opened,Replace deprecated Callout component with BannerAlert from the component-library,good first issue team-design-system,"
-### Description
+Dependency Hierarchy:
+ - cucumber-reporting-3.8.0.jar (Root Library)
+ - :x: **jackson-databind-2.8.5.jar** (Vulnerable Library)
+
+jackson-databind-2.9.8.jar
-Currently, the extension is using an outdated `Callout` component, which needs to be replaced with the new `BannerAlert` component.
+
General data-binding functionality for Jackson: works on core streaming API
Path to dependency file: /tmp/ws-scm/karate/examples/gatling/build.gradle
+
Path to vulnerable library: /tmp/ws-ua_20200424203206/downloadResource_81a2693a-3427-4530-b432-dc290b928912/20200424203251/jackson-databind-2.9.8.jar,/tmp/ws-ua_20200424203206/downloadResource_81a2693a-3427-4530-b432-dc290b928912/20200424203251/jackson-databind-2.9.8.jar
+
-This is a massive undertaking by itself and creating a single PR would be too large. Smaller PRs can be submitted against this issue to ensure easier review and gradual improvements.
+Dependency Hierarchy:
+ - karate-gatling-0.9.5.jar (Root Library)
+ - gatling-charts-highcharts-3.0.2.jar
+ - gatling-charts-3.0.2.jar
+ - gatling-core-3.0.2.jar
+ - :x: **jackson-databind-2.9.8.jar** (Vulnerable Library)
+
Path to dependency file: /tmp/ws-scm/karate/karate-demo/build.gradle
+
Path to vulnerable library: /root/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.8.8/bf88c7b27e95cbadce4e7c316a56c3efffda8026/jackson-databind-2.8.8.jar,/root/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.8.8/bf88c7b27e95cbadce4e7c316a56c3efffda8026/jackson-databind-2.8.8.jar
+
-- Replace instances of `Callout` component (`ui/components/ui/callout/callout.js`) with `BannerAlert` component (`ui/components/component-library/banner-alert/banner-alert.js`)
-- Component APIs are slightly different so ensure all props have been migrated appropriately
+Dependency Hierarchy:
+ - spring-boot-starter-web-1.5.3.RELEASE.jar (Root Library)
+ - :x: **jackson-databind-2.8.8.jar** (Vulnerable Library)
+
+
+FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.aries.transaction.jms.internal.XaPooledConnectionFactory (aka aries.transaction.jms).
-- Instances of `Callout` component are completely replaced with the new `BannerAlert` component
-- The component APIs are updated to reflect the changes in the new `Callout`` component and there is no functional changes or visual regression
-- Each Pull Request (PR) should include **no more than 3 files**
-- The code changes should pass Jest tests, linting, and Storybook without any errors.
-- The PR must include before and after screenshots of the UI to ensure there are no visual regressions.
+
-Good first issue for: External contributors who are familiar with running the extension locally, have knowledge of React, component props, Jest tests, linting, and Storybook, and want to contribute to improving the cohesiveness of UI in the extension
-",1.0,"Replace deprecated Callout component with BannerAlert from the component-library -
-### Description
+
+
+
-Currently, the extension is using an outdated `Callout` component, which needs to be replaced with the new `BannerAlert` component.
+",0,cve high detected in multiple libraries cve high severity vulnerability vulnerable libraries jackson databind jar jackson databind jar jackson databind jar jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file tmp ws scm karate examples jobserver build gradle path to vulnerable library root gradle caches modules files com fasterxml jackson core jackson databind jackson databind jar root gradle caches modules files com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy cucumber reporting jar root library x jackson databind jar vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file tmp ws scm karate examples gatling build gradle path to vulnerable library tmp ws ua downloadresource jackson databind jar tmp ws ua downloadresource jackson databind jar dependency hierarchy karate gatling jar root library gatling charts highcharts jar gatling charts jar gatling core jar x jackson databind jar vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file tmp ws scm karate karate demo build gradle path to vulnerable library root gradle caches modules files com fasterxml jackson core jackson databind jackson databind jar root gradle caches modules files com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library x jackson databind jar vulnerable library found in head commit a href vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to org apache aries transaction jms internal xapooledconnectionfactory aka aries transaction jms publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution jackson databind isopenpronvulnerability false ispackagebased true isdefaultbranch true packages vulnerabilityidentifier cve vulnerabilitydetails fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to org apache aries transaction jms internal xapooledconnectionfactory aka aries transaction jms vulnerabilityurl ,0
+567928,16919758768.0,IssuesEvent,2021-06-25 02:32:53,openmsupply/remote-server,https://api.github.com/repos/openmsupply/remote-server,opened,Epic: stocktake,epic priority: normal,"Epic for implementing functionality for basic stocktake workflow.
+
+Activity diagram:
+
+TODO.",1.0,"Epic: stocktake - Epic for implementing functionality for basic stocktake workflow.
+
+Activity diagram:
+
+TODO.",0,epic stocktake epic for implementing functionality for basic stocktake workflow activity diagram todo ,0
+345280,10360783755.0,IssuesEvent,2019-09-06 08:29:37,webcompat/web-bugs,https://api.github.com/repos/webcompat/web-bugs,closed,www.amazon.com - site is not usable,browser-firefox-mobile engine-gecko priority-critical,"
+
+
-This is a massive undertaking by itself and creating a single PR would be too large. Smaller PRs can be submitted against this issue to ensure easier review and gradual improvements.
+**URL**: https://www.amazon.com/OfficeTec-Computer-Speakers-Compact-System/dp/B0728GR6HK/ref=redir_mobile_desktop?_encoding=UTF8&m=A1KY37TQPDWTK3
-### Technical Details
+**Browser / Version**: Firefox Mobile 68.0
+**Operating System**: Android 8.1.0
+**Tested Another Browser**: Yes
-- Replace instances of `Callout` component (`ui/components/ui/callout/callout.js`) with `BannerAlert` component (`ui/components/component-library/banner-alert/banner-alert.js`)
-- Component APIs are slightly different so ensure all props have been migrated appropriately
+**Problem type**: Site is not usable
+**Description**: hyperlinks are mia and only work on desktop mode.
+**Steps to Reproduce**:
+Hyperlinks are MIA on Amazon.
+[](https://webcompat.com/uploads/2019/9/e86bc7c2-5e02-4c69-8377-a77bc8988164.jpeg)
-### Acceptance Criteria
+
+Browser Configuration
+
+
mixed active content blocked: false
image.mem.shared: true
buildID: 20190902144652
tracking content blocked: false
gfx.webrender.blob-images: true
hasTouchScreen: true
mixed passive content blocked: false
gfx.webrender.enabled: false
gfx.webrender.all: false
channel: beta
+
+
Console Messages:
+
+[u'[JavaScript Warning: ""Cross-Origin Request Blocked: The Same Origin Policy disallows reading the remote resource at https://images-na.ssl-images-amazon.com/images/G/01/ape/sf/desktop/DAsf-1.50.ee85cea._V437939081_.js?csm_attribution=APE-SafeFrame. (Reason: CORS request did not succeed).""]', u'[JavaScript Warning: ""Loading failed for the